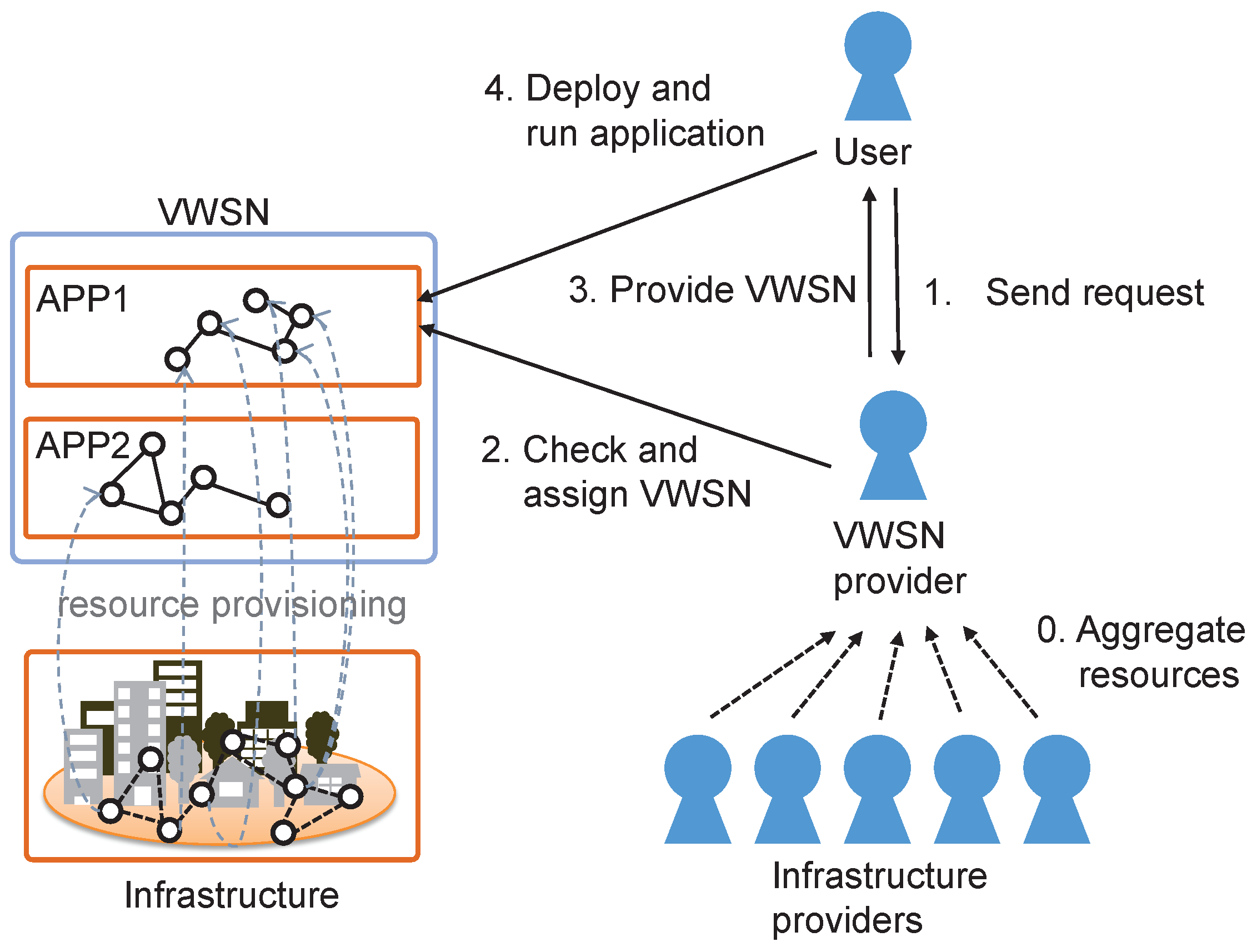
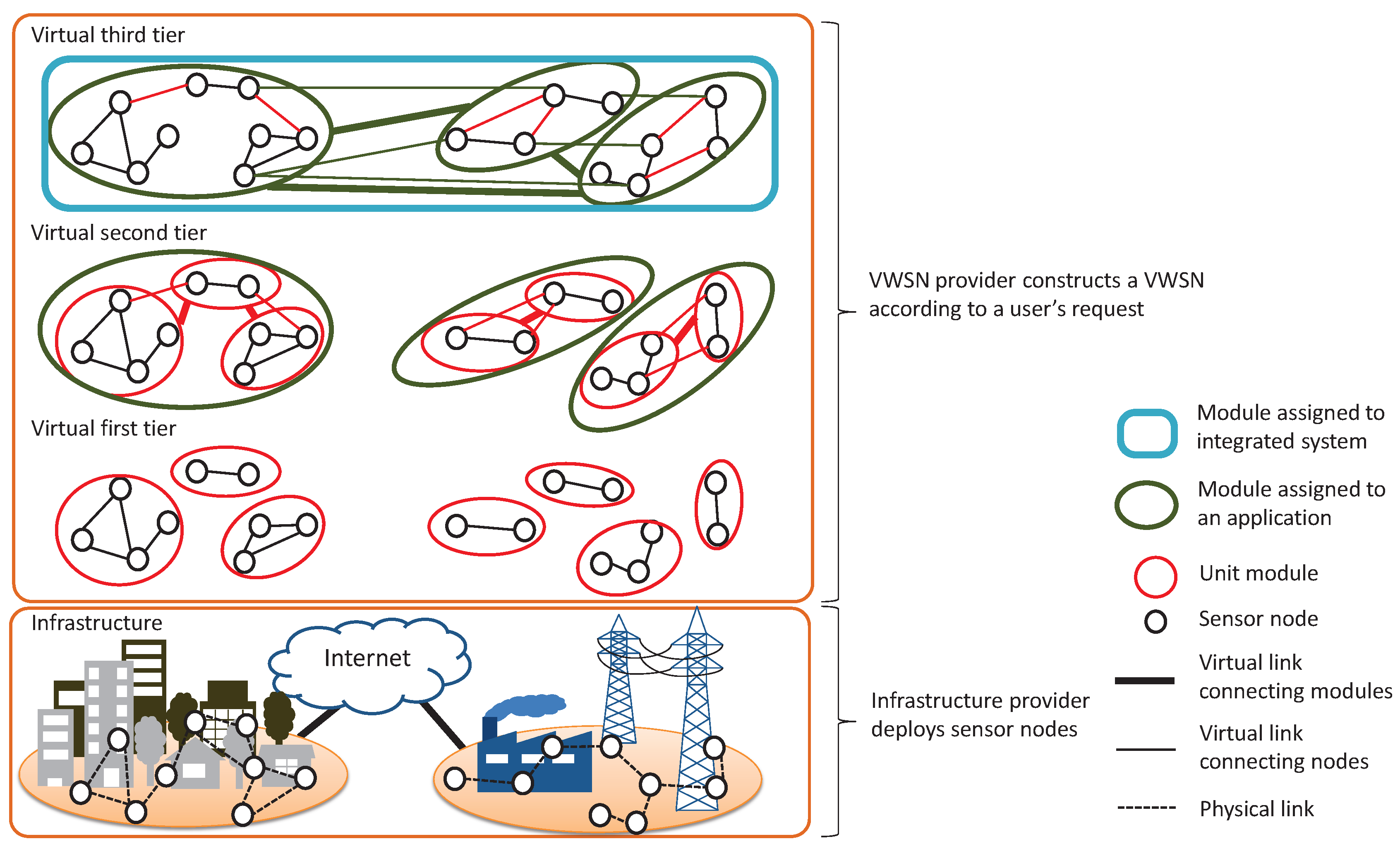
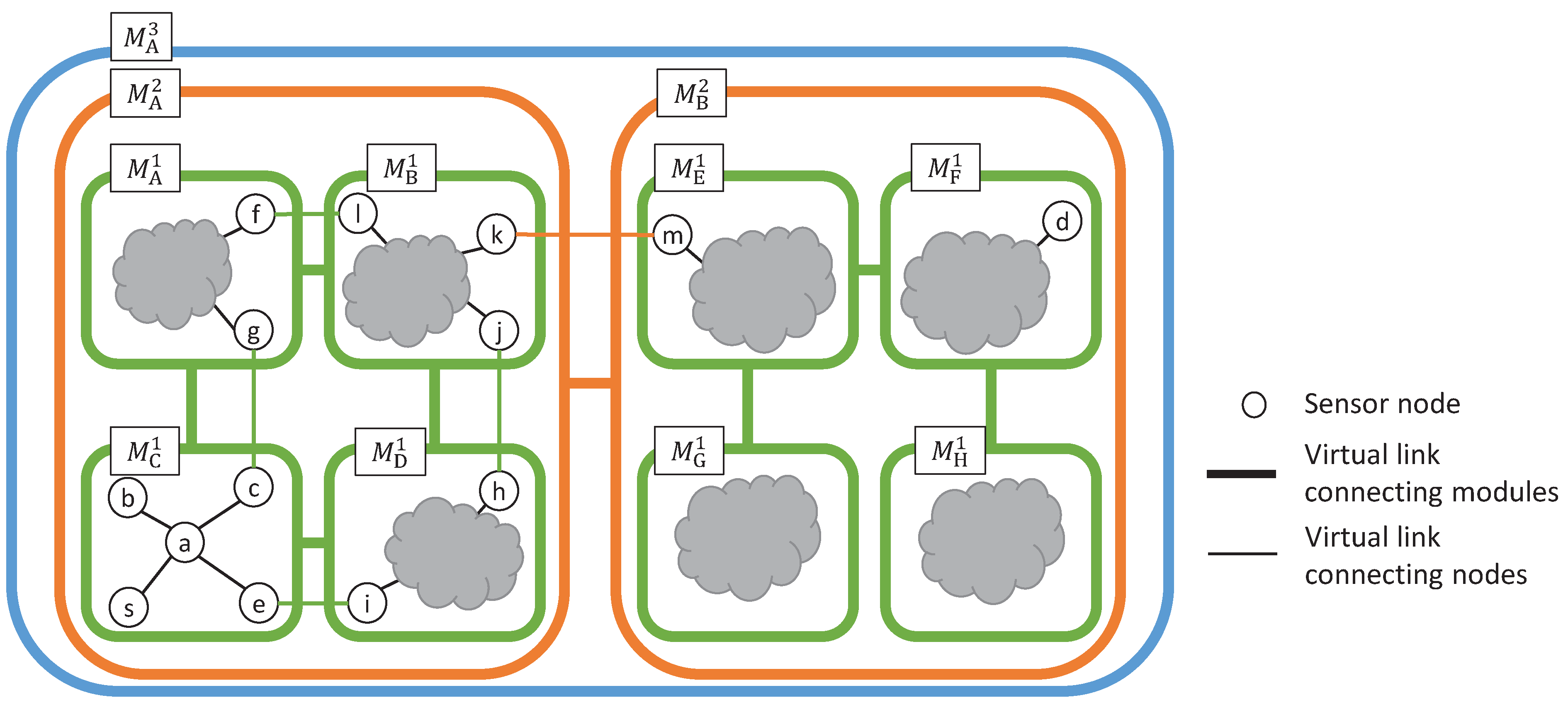
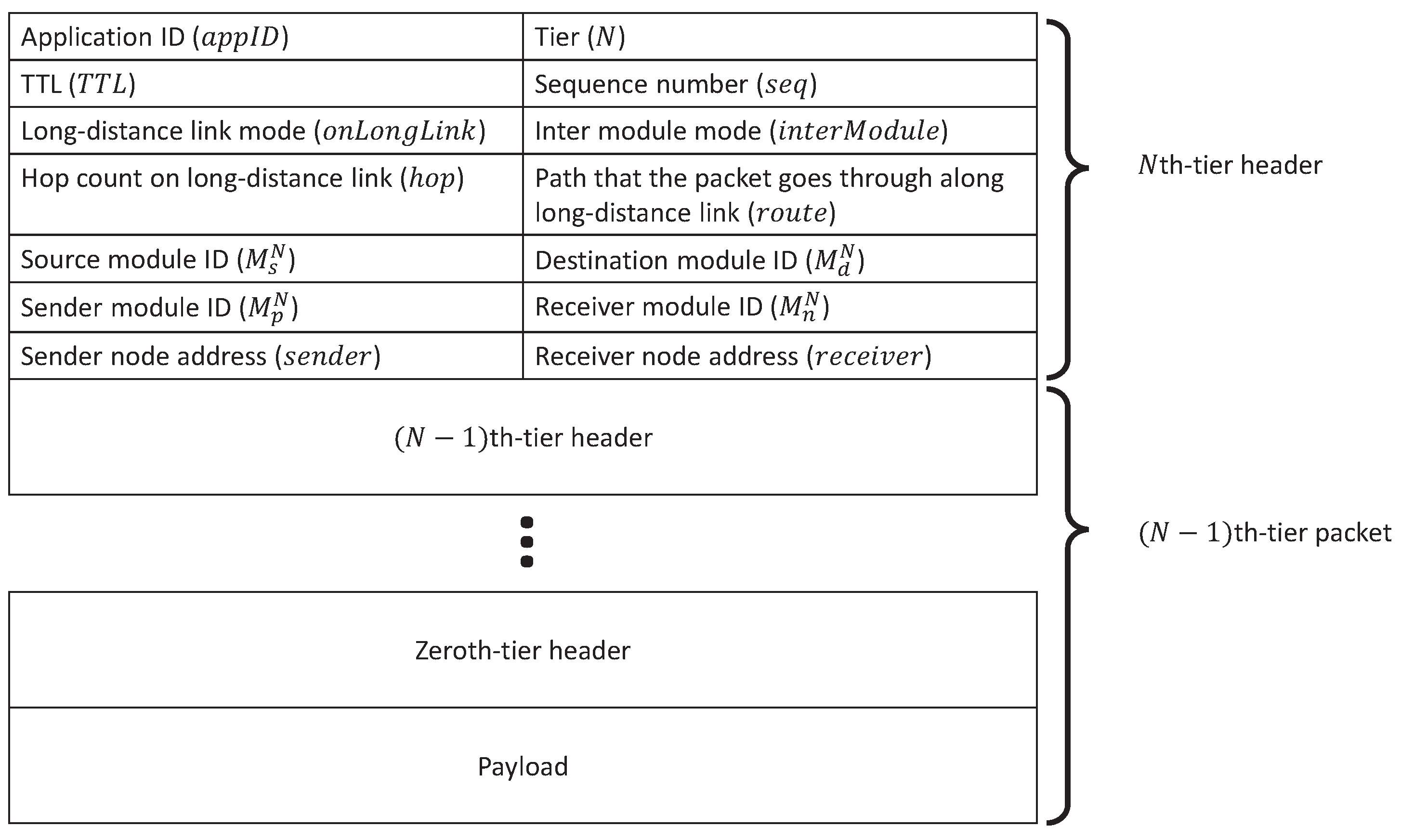
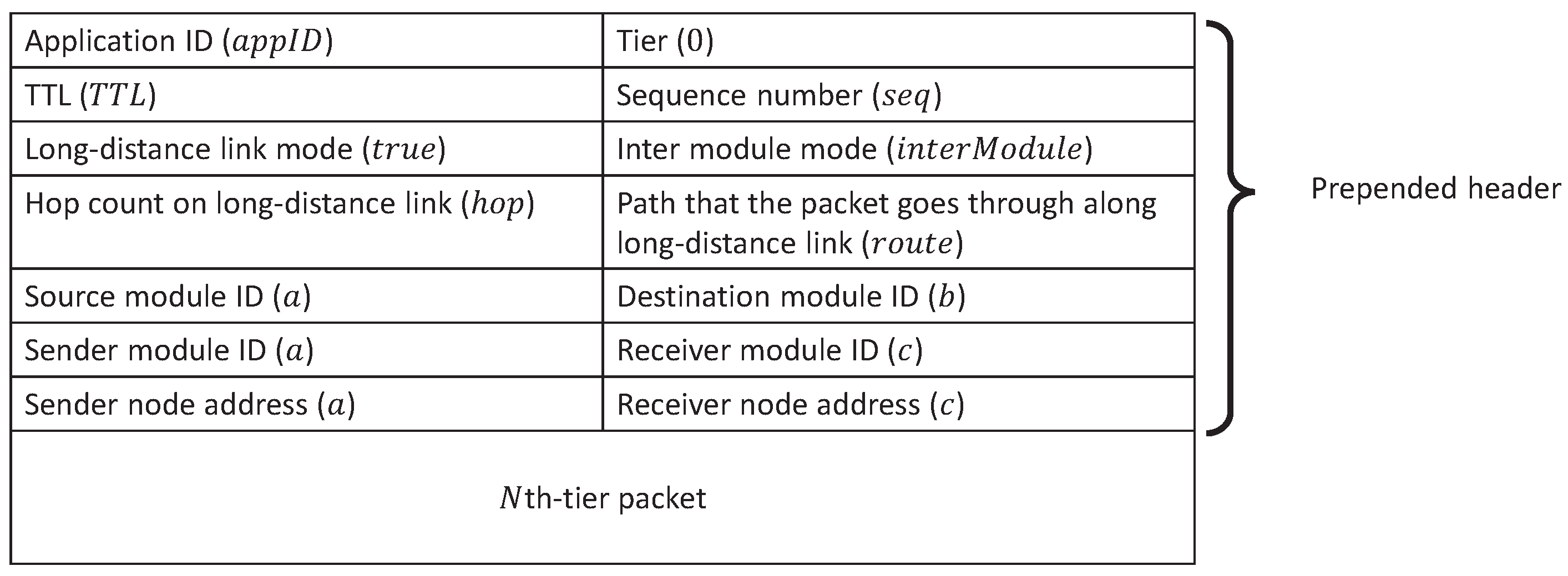
6.3. Evaluation Environments
We evaluate the adaptivity of a VWSN topology constructed from the network, which is composed of two sensor networks and one wired link. Each of the sensor networks consists of 150 sensor nodes deployed in a domain of size . For one of the sensor networks, we deploy 150 sensor nodes at randomly-selected positions in the rectangular area with corners, denoted in meters along the coordinate axes of the domain, at and ; we deploy the other 150 sensor nodes at randomly-selected positions in the rectangular area given by and . Additionally, one wired link connects the two sensor networks, and its endpoint nodes are static once they are chosen. We assume the wireless communication range is 100 m.
In this simulation, we construct a three-tiered VWSN topology. We use OMNeT++ [
30] to perform the simulation experiments, and the parameter settings are shown in
Table 1. When the physical topology described above is used, the value of
is comparatively high, which means that many virtual links are added between first-tier modules; this results in low modularity. To correct for this, we set
to a value lower than
in the higher tier.
The flow of simulation is described below.
The VWSN provider receives, from a user, a request to construct a new VWSN topology and data on traffic patterns.
The VWSN provider constructs a VWSN topology and calculates the routing tables, connection tables and long-link tables for each node.
The VWSN provider informs the gateway about the tables of each node and the traffic pattern.
The gateway sends the information to each node.
Each node sends a data packet periodically according to the received traffic pattern.
The traffic pattern consists of some traffic flow information: a source node, a destination node and a flow rate. In this paper, flow rates are randomly selected from among , , , , , , , , and . The number of flows is 0.2% of the number of all of the possible combinations of two nodes included in the VWSN topology. The pairs of source node and destination node are also selected randomly. The TTL of each data packet is set to 50.
From the simulations, we identified the reasons for failure to recover the data delivery ratio. These are listed in
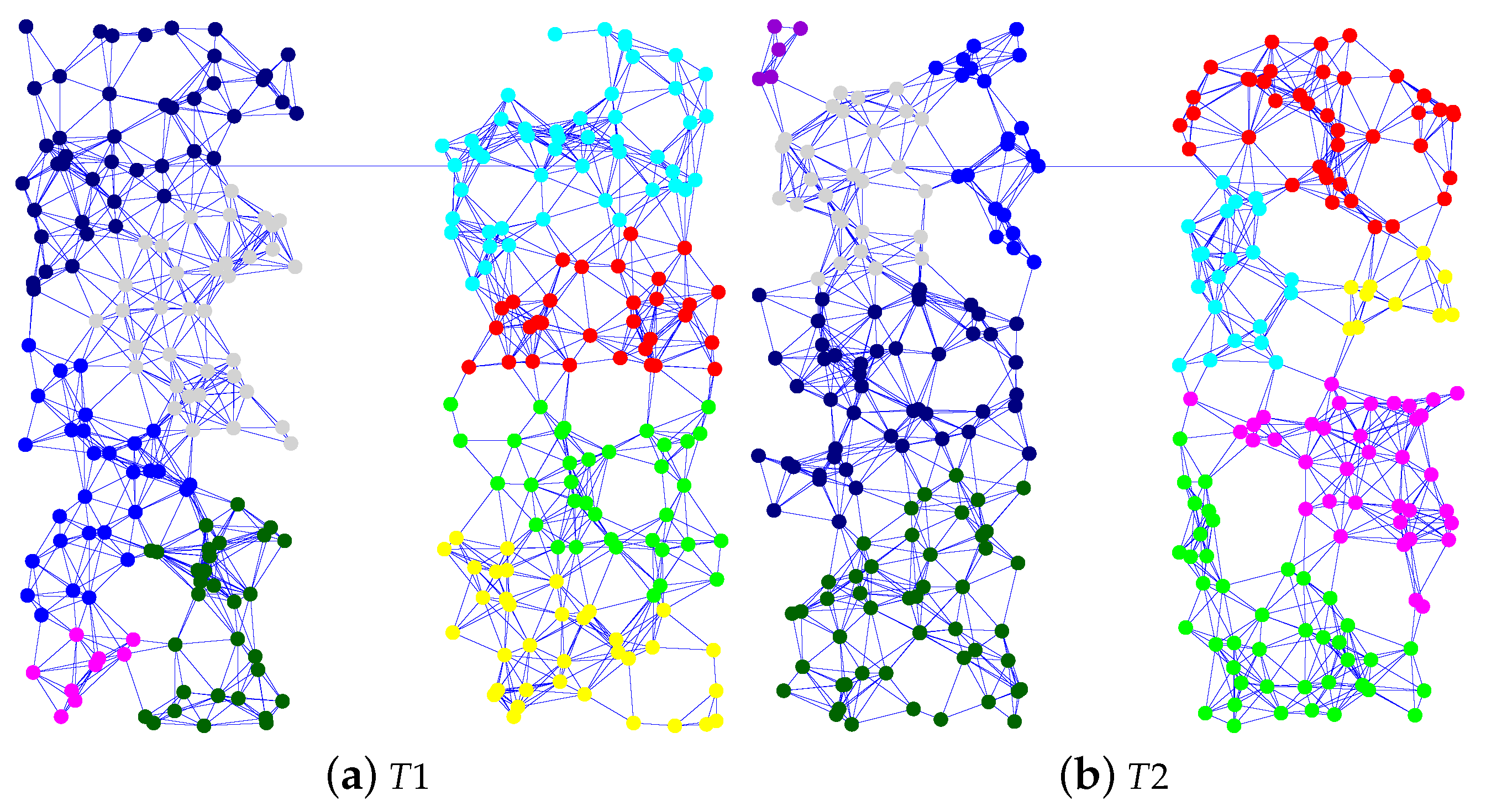
Table 2. Physical topology and the result of modular division have a strong influence on adaptivity within our proposed method and can lead to different reasons for failure to recover the data delivery ratio. Therefore, we use five physical topologies and perform 100 trials with each topology. In this paper, we show the results of only two physical topologies; the results for the omitted topologies show the same characteristics. We call these physical topologies
and
. Each physical topology with the result of modular division by the Newman algorithm is shown in
Figure 4. Each color shows the group of each module.
6.4. Adaptivity of the VWSN Topology against Random Failure
In this section, we evaluate the adaptivity of the VWSN topology against random failure. The simulation time is 10,000 s; after 5000 s have elapsed, one node fails every 10 s until 30 nodes have failed. We use one hundred patterns of node failure, each corresponding to a trial. In each pattern, 30 nodes are randomly selected to fail, and the order of failure is random.
To compare the adaptivity of a physical topology with that of a VWSN topology, we try to evaluate the adaptivity of a physical topology in which we apply shortest-path routing to the topology. However, the simulation cannot be finished. Because all nodes have routing table entries to all other nodes, several nodes generate more than one hundred route request packets after failure of a single node. This leads to frequent packet collision and high packet loss. When a Hello packet is lost, neighboring nodes erroneously detect the failure of the sending node and generate many unnecessary route request packets. From this result, the division of a physical topology into small sub-topologies is an effective method for avoiding this type of problem.
Table 3 shows the rate of recovering the data delivery ratio in each combination of a physical topology and a method of constructing a VWSN topology. The recovery rate is the ratio between the number of trials in which all of the flows can reach the destination node and the total number of trials. In the simulation,
indicates the physical topology. We use
to denote the rate of recovering the data delivery ratio.
Table 3 shows that
for the bio-inspired topology is zero. There are some connected centroid nodes with a high degree in the virtual topology constructed by the bio-inspired method. The failure of a few of these is fatal because they are essential for connectivity. Note that the routing algorithm mentioned in
Section 5 restricts the communication between modules because we keep nodes’ overheads low by reducing their managing information on tables. A data packet must pass through the connected node of the module if the destination node of the data packet belongs to the different module. This means that, in the bio-inspired method, the virtual link connecting different modules is ignored when an endpoint node is neither a centroid node nor a peripheral node. Therefore, a VWSN topology constructed by the bio-inspired method seems to fragment easily into subnetworks because of the routing algorithm, even though it is highly robust on connectivity against random failure, as discussed in our previous work [
13]. Moreover, these topologies generate many control packets as part of the route recovery mechanism in upper tiers. This results in congestion and the loss of control packets.
In the topologies created according to our proposal, the physical topology determines whether is high or low. As an example, when there are some sparse areas in the physical topology, it is difficult to find an alternative path by flooding because of collisions among control packets or isolation in the physical or virtual topology. When we compare values of among different physical topologies, the differences are small between methods.
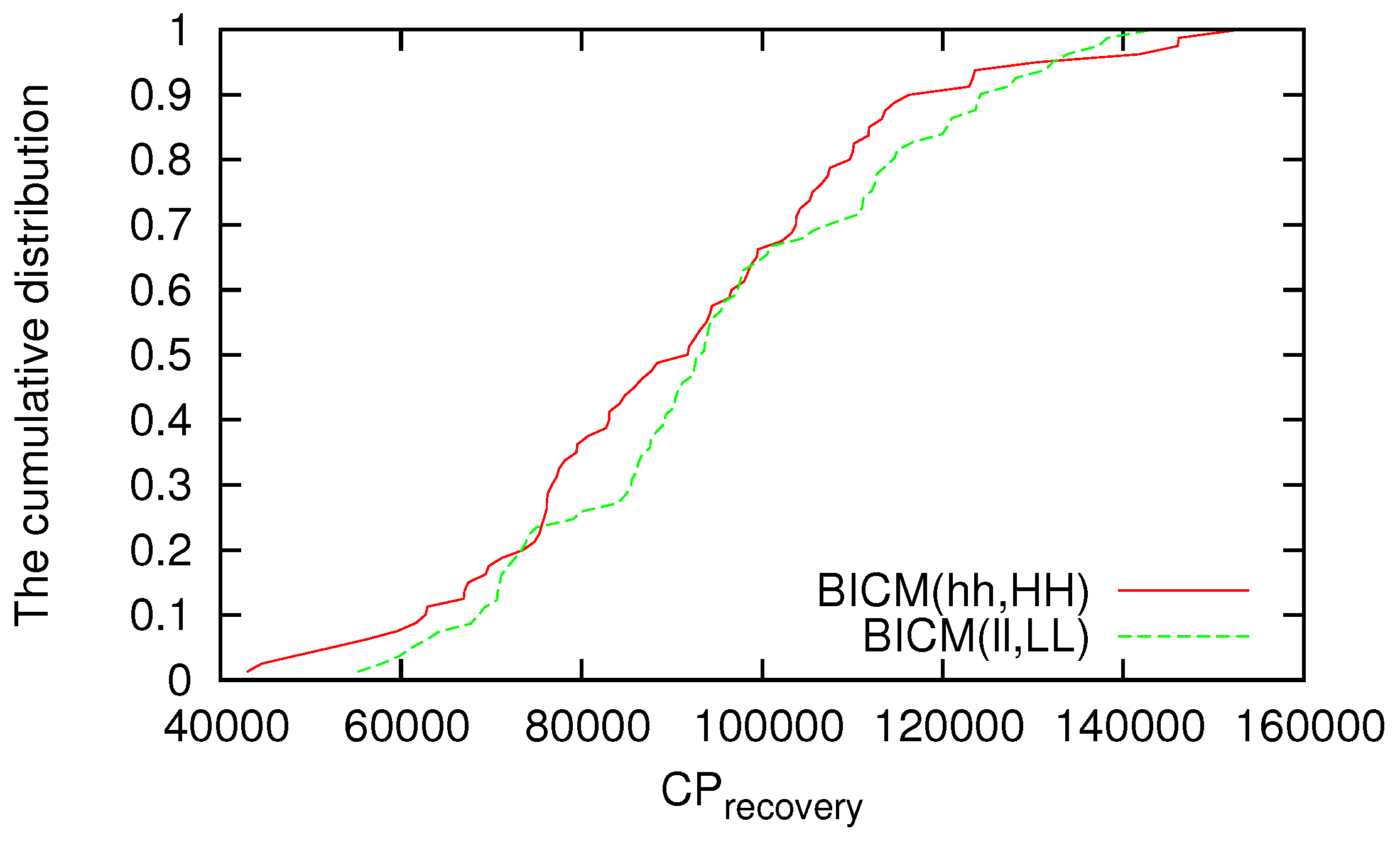
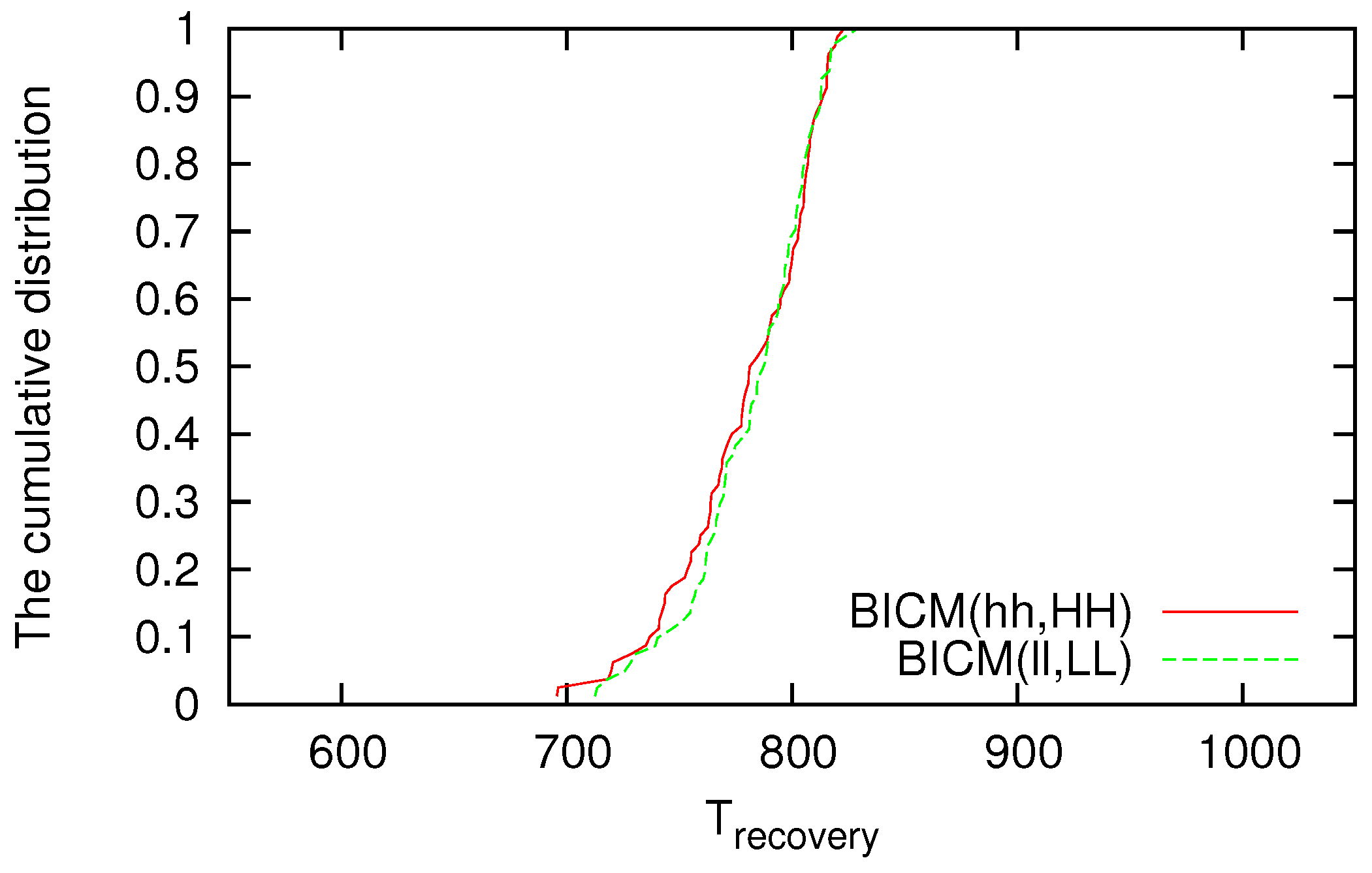
We investigate the cumulative distributions of
and
against random failure; however, few differences can be seen among the strategies for
in each topology. Examples of the cumulative distributions of
and
are shown in
Figure 5 and
Figure 6, respectively. In
Figure 5,
is mapped on the horizontal axis, and the cumulative number of trials in which the data delivery ratio recovers before
has elapsed is mapped on the vertical axis. Similarly, in
Figure 6, the horizontal axis reflects
, and the vertical axis reflects the cumulative distribution of the number of trials in which the data delivery ratio recovers before
has elapsed. Although the difference according to the method is small for the cumulative distribution of
or
against random failure, when a VWSN is constructed by BICM(hh,HH), there are some trials whose
and
are smaller (i.e., better) than those for topologies constructed by other methods. This is because when a node with a high degree is selected as a connected node in BICM(hh,HH), the endpoints of virtual links between modules tend to be concentrated to a small number of nodes. Therefore, the probability that a connected node fails in random failure is low, allowing the recovery of the zeroth-tier routing table unless a connected node fails.
The number of trials in which either the virtual or physical topology fragments is shown in
Table 4, and the number of trials in which the data delivery ratio does not recover because of the inconsistency in tables is shown in
Table 5. In this,
identifies the physical topology. Blank entries in
Table 4 reflect that the VWSN topology constructed by the bio-inspired method does not have tiers higher than the first tier.
The values of are the same in each physical topology, because we use the same node failure patterns. The value of for BICM(hh,HH) and BICM(ll,LL) is the same because the results of modular division by the Newman algorithm are almost identical between the cases. Whether the value of is high or low depends on the physical topology. For topologies constructed according to our proposed method, it is easy to fragment the first-tier virtual topology into physical topology . There are two main reasons for this. One is that there is a first-tier module with a small number of nodes, and the other is that there is a first-tier module whose degree in the first tier is one. The point in common between these is that some first-tier modules contain few connected nodes. Therefore, the failure of a few connected nodes in a first-tier module that either has few nodes or has degree one in the first tier results in the fragmentation of the module. When we use the bio-inspired method, few connected nodes exist in their respective first-tier modules, and each module is small. Therefore, fragmentation of the topology is more likely than with our proposed method.
In
Table 5,
has the highest value for each method. This is because it is comparatively difficult to find an alternative route in the upper tier. Particularly when using the bio-inspired method,
is nearly the same as the number of trials. This near parity results from the congestion and loss of control packets around the connected nodes, which attract a large number of links.
From the above, the adaptivity of VWSN topologies constructed by our proposal is not markedly different. However, in a few trials, is notably smaller in the topology constructed by BICM(hh,HH). This suggests that the adaptivity to random failure of a VWSN topology constructed by BICM(hh,HH) is comparatively high.
6.5. Adaptivity of the VWSN Topology against Targeted Attacks
In this section, we evaluate the adaptivity of the VWSN topology against targeted attacks. The simulation time is 10,000 s; after 5000 s have elapsed, one node fails for every 10 s until 30 nodes have failed. Nodes fail in descending order of initial degree in the VWSN topology, without adjusting degrees after each failure and choosing arbitrarily among nodes of equal degree.
The values of
, average
and average
for each method are summarized in
Table 6. The number of trials in which the virtual or physical topology becomes fragmented is shown in
Table 7, and the number of trials in which the data delivery ratio fails to recover due to the inconsistency in the tables is shown in
Table 8. As elsewhere,
indicates the physical topology. The blanks in
Table 6 indicate that the value could not be calculated because the data delivery ratio did not recover.
In physical topology
,
is quite low when using BICM(hh,HH), but
remains high when using BICM(ll,LL). When using BICM(hh,HH), it is easy to divide a module, and so, the route discovery process must be carried out frequently because high-degree nodes are selected to be connected nodes. This means that many connected nodes fail when nodes are removed by targeted attack. However, the value of
is zero in BICM(ll,LL) for
. This is because a zeroth-tier topology in a first-tier module becomes fragmented in all trials, as shown in
Table 7. In
, there is a first-tier module whose central area is densely connected. Because the degree of a node in this area is high, this first-tier module becomes fragmented when all of the nodes in the area fail.
From the above, although adaptivity against targeted attack is strongly dependent on physical topology and the method of modular division, the adaptivity of the VWSN constructed by BICM(ll,LL) is the highest in many cases.
Considering all of the results, the physical deployment of sensor nodes and the modular division algorithm is quite important for keeping services running on a VWSN topology. Because sparse areas where link density is low could fragment easily, infrastructure providers should deploy redundant nodes in order to provide stable services. Nodes in dense areas where link density is high can consume more energy than nodes in other areas because they will forward or receive more packets. When a first-tier module has both dense and sparse areas, the energy depletion of nodes in the dense area can result in the fragmentation of the module. To prevent this, infrastructure providers should supply energy to nodes or deploy nodes with high-capacity batteries in areas where many nodes are to be deployed. Alternatively, VWSN providers should construct a first-tier module in which the link density is homogeneous.
6.6. Discussion of Memory Utilization
In this section, we estimate the amount of memory needed to store the tables used for the routing algorithm shown in this paper. For the
N-th-tier routing table, the number of entries that each node needs to hold is the sum of the number of
N-th-tier modules that belong to the
-th-tier module of that node (excluding the
N-th-tier module of the node) and the number of neighboring
N-th-tier modules that belong to a different
-th-tier module. Therefore, the number of entries
of the
N-th-tier routing table when node
n belongs to an
N-th-tier module
and an
-th-tier module
is defined as follows:
Here,
and
.
is the set of
N-th-tier modules that belong to the
-th-tier module
, and
is the cardinality of
. The second term means that
is not included as the destination module in the
N-th-tier routing table.
is the set of
N-th-tier modules that neighbor
, and
is the relative complement of
in
. Then,
is the number of
N-th-tier modules that are connected to
and belong to an
-th-tier module other than
. From the above, the total number of entries
of the routing tables held by node
n is
where
i is the identity of each tier composing the VWSN topology.
Because the number of zeroth-tier modules, which are nodes belonging to the same first-tier module, is the largest of all of the tiers, the size of the zeroth-tier routing table is dominant in many cases.
For the
N-th-tier connection table, the number of entries that each node needs to hold is the number of
-th-tier virtual links that connect an
-th-tier module belonging to the
N-th-tier module of the node with another
-th-tier module belonging to a neighboring
N-th-tier module. In our proposal, the number of
-th-tier virtual links added by mapping the
N-th-tier virtual link depends on the number of
-th-tier virtual links embedded in the
N-th-tier VWSN topology. Therefore, the number of entries
of an
N-th-tier connection table for node
n that belongs to
is as follows:
Here,
. Therefore, the total number of entries
of the connection tables held by
n is
where
i is the identity of each tier composing the VWSN topology.
Although the number of zeroth-tier virtual links is the largest among all of the tiers, we can tune the parameter separately for each tier. In this paper, because we set to a small value, the size of the connection tables is smaller than that of the routing tables.
For the long-link table, the number of entries that each node needs to hold, denoted by , is the number of virtual links to which it is assigned as a relay node or an end node. Because the number of entries of a long-link table depends entirely on the specific node, we cannot easily estimate the size of the long-link table. Some nodes will have an empty long-link table; others will have a large number of entries in the long-link table. In our evaluation environment, the two nodes connected by the wired link and the nodes around those end nodes have a large number of entries in their long-link tables, because all traffic between the two sensor networks must go through the wired link. However, the number of entries of the long-link tables is much less than that of the routing tables because of the large number of zeroth-tier modules. Because the sizes of the long-link tables depend on the method of modular division, further investigation into the effect of the choice of method of modular division will be needed.
Then, we derive the expectation of the total number of entries of each N-th-tier table, denoted by , and , respectively. Let us define the expectation of each variable as follows. , and denote the expectation of the number of N-th-tier modules belonging to an -th-tier module, the expectation of the number of -th-tier virtual links in an N-th-tier module and the expectation of the degree of an N-th-tier module, respectively.
We calculates the expectation of the number of
N-th-tier modules that are connected to an
N-th-tier module and belong to an
-th-tier module other than the
-th-tier module that the
N-th-tier module belongs to, denoted by
. The expectation of the total number of
N-th-tier virtual links that connected
N-th-tier modules belonging to an
-th-tier module and
N-th-tier modules belonging to other
-th-tier modules equals
. Then, the probability that the number of
N-th-tier virtual links connecting an
N-th-tier module and other
N-th-tier modules belonging to other
-th-tier modules is
x, denoted by
p, is as follows:
Because of the binomial distribution, the following satisfies:
Then,
is calculated as follows:
From Equation (
6),
is calculated as follows:
As mentioned above, we cannot easily estimate the size of the long-link table. Therefore, we use as a parameter in the following discussion.
Then, we discuss how much memory size is required for the tables. Let us denote
,
and
as the required size of memory of an entry of
N-th-tier routing table,
N-th-tier connection table and long-link table in bytes, respectively. Then, the required total memory size for tables of node
n, denoted by
, is
The entries in the routing table in the zeroth tier consist of a destination node, a forwarding node for the destination node and path weight. The entries in the routing table for the higher tier consist of an identifier of a destination module, a forwarding module for the destination module and path weight. Because of the difference of the scale of the number of nodes/modules in each tier, the memory size for the identifier of modules can be smaller in a higher tier. Therefore, we assume that the memory size of the identifier for nodes and modules are two bytes and one byte, respectively, here. We treat the path weight as the float type variable (four bytes). Then, and where .
When node n belongs to the N-th-tier virtual module , it holds an N-th-tier connection table whose entries consist of N-th-tier neighboring module identifiers (), the module identifier of -th-tier connected modules () belonging to and the module identifiers of -th-tier connected modules () belonging to . Because a zeroth-tier module denotes a node, and where .
The entries of a long-link table consist of the end nodes of a virtual long-distance link, the next and previous forwarding nodes and a hop count from the source node of the virtual long-distance link. Because we set TTL to 50 in our evaluation, one byte is enough for a hop count from the source node of the virtual long-distance link. Then, .
From the above assumptions, Equation (
12) can be rewritten as
Now, we assume a two-tiered structure for one application and a situation in which
,
,
,
and
. Because the expected number of nodes in a first tier module is 100 and the expected number of total first-tier modules is 10, the total number of nodes in the VWSN network is 1000. From Equations (
10) and (
11), the expectation of the required total memory size for tables of a node is 2152 bytes.
Next, we assume a three-tiered structure for one application and a situation in which , , , , , , and . In this case, the total number of nodes in the VWSN network is 3000. Then, the expectation of the required total memory size for tables of a node is bytes.
Then, we assume a four-tiered structure for one application and a situation in which , , , , , , , , , and . In this case, the total number of nodes in the VWSN network is 9000. Then, the expectation of the required total memory size for the tables of a node is byte. Therefore, there is a case that 3 KB of memory on average per node is enough for the routing algorithm shown in this paper even when the four-tiered VWSN is provided.
Note that tables for the routing can be reused by multiple applications. When a user wants to run an application over the integrated VWSN, which comprises multiple VWSNs that may have been deployed for other applications, the same tables for routing in the lower tiers can be used in the integrated VWSN. Additional entries in the tables for routing are needed for the highest tier only. Therefore, the modular structure contributes to memory efficiency in such situations.
6.7. Discussion of Approaching Our Considered World from the Current Real World
In this paper, we show an overall architecture that is suitable for constructing and running VWSN services within a VWSN topology for the IoT environment. However, it is often considered that nodes in the WSNs are involved in severe restriction on their processing, energy, memory and storage. In the virtualization scenario, this restriction is more critical because multiple applications, such as in-network processing defined by users or the manager of concurrency, run on the same entity.
The things to process are concurrency management, protocol translation, sensing, actuation, packet processing, signal processing, timer management, routing, route recovery, neighbor nodes’ management and table management. Because they can add a big overhead to nodes, how to manage device resources is a crucial viewpoint of network design. In completely centralized management systems, an overhead for collecting information of nodes explosively grows as the number of nodes in the system increases. However, on the contrary, in decentralized systems, more powerful resources are required for any node in the network.
Khan et al. mentioned that research of the virtualization of WSNs is getting more pertinent because WSNs’ nodes are becoming more powerful [
16]. It is expected that this trend will continue, and WSNs’ nodes will get more powerful resources in the future. In our architecture, therefore, sensor nodes process their tasks in a decentralized manner after the VWSN provider deploys the constructed VWSN.
Moreover, some techniques with small overheads can be applied to our architecture. For example, only high-spec connected nodes hold the entire
N-tier routing tables and are responsible for routing between higher tier modules, while a low-spec node holds only zeroth-tier table and sends its sensing data to only the nearest connected node. Any routing algorithm will do in the zeroth-tier, not only any-to-any routing, but also converge routing to a high-spec node. Many efficient converge routing algorithms for WSNs have been proposed [
31]. Here, a method of resource management or an energy-efficient solution is out of the scope of this paper and relies on other research.
Another important aspect is Internet compatibility. It is natural to consider that the VWSN providers or users access the virtualized resources through the Internet. Therefore, we need to address compatibility or connectivity between WSNs and the Internet. As mentioned by many researchers [
32], the gateway-based strategy can be one solution to this problem. Our architecture can also gain the compatibility to the Internet by using gateway-based solutions. In our architecture, connected nodes can be seen as gateways between modules or networks. As mentioned in
Section 1, we consider that users can select or configure protocols that they use in their applications. Standardized protocols, such as 6LoWPAN, can be also included. Moreover, this idea can be applied to each tier in a VWSN network deployed for an application. As mentioned above, because there are some low-spec nodes in WSNs, an energy-efficient and low overhead routing algorithm can be the first choice in zeroth-tier networks. Then, each connected node, behaving as a gateway, aggregates data packets whose destination is out of the module, encapsulates them for routing in higher tier networks and translates protocols as necessary. In this scenario, although the amount of energy consumption is heterogeneous, the heterogeneity of the nodes’ spec is more general in the future IoT environment because of the existence of multiple vendors and providers. How to manage such heterogeneity is out of our scope, but should be future work.