A Reliable TTP-Based Infrastructure with Low Sensor Resource Consumption for the Smart Home Multi-Platform
Abstract
:1. Introduction
2. Related Works
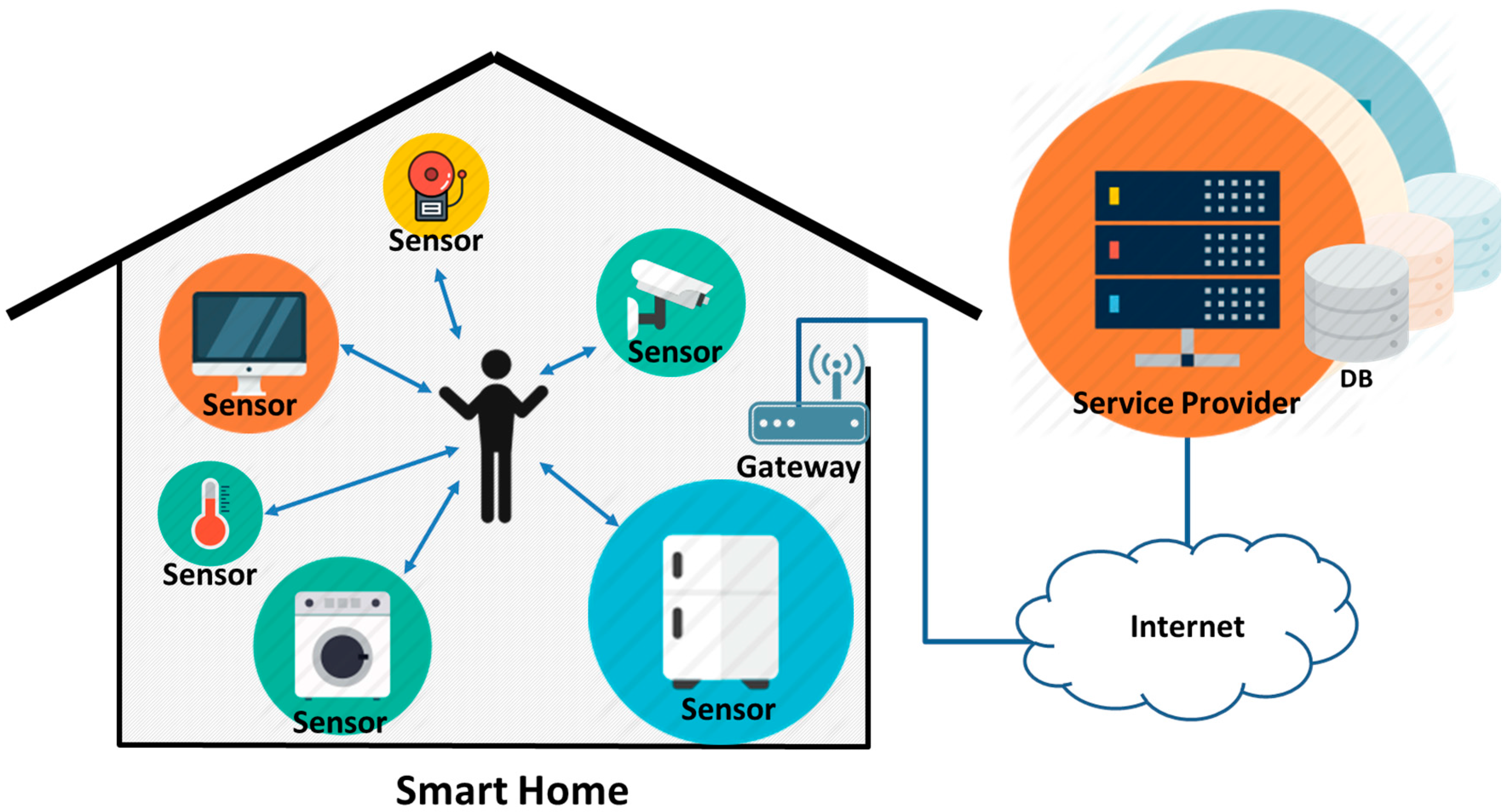
2.1. Smart Home Infrastructure
2.2. Security Requirements for Smart Home
2.3. Previous Research on Smart Home
3. Proposed Infrastructure
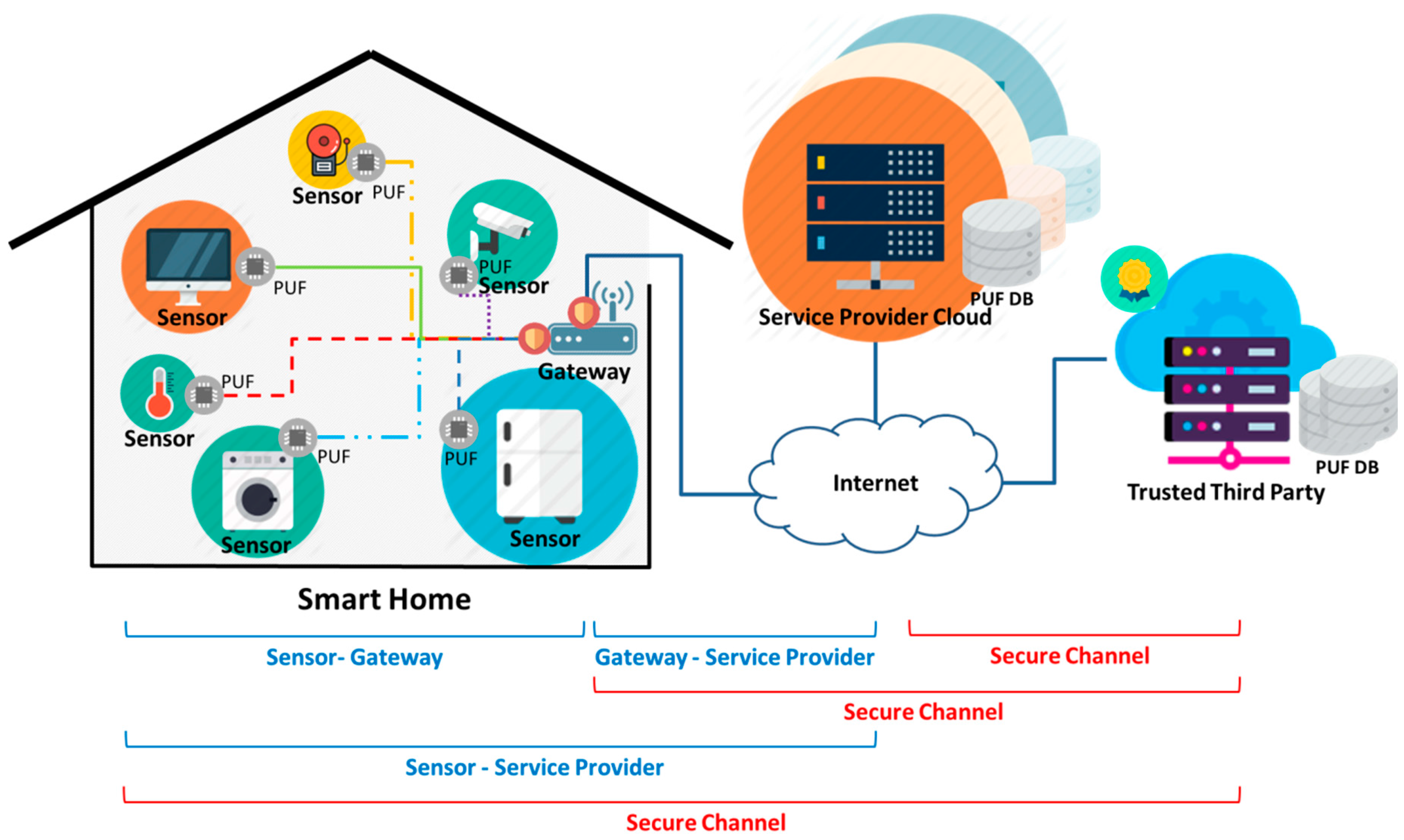
3.1. Proposed Smarthome Multiplatform Infrastructure
3.2. Proposed Protocols
3.2.1. Provisioning Phase
3.2.2. Authentication Phase
4. Security and Performance Analysis
4.1. Security Analysis
4.2. Computing Resource Analysis
4.3. Storage Resource Analysis
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Abbreviations
| IoT | Internet of Things |
| ZiSAS | ZigBee-based intelligent self-adjusting sensor |
| WSNs | Wireless Sensor Networks |
| RHS | Remote Home Server |
| SDN | Software Defined Networking |
| SMP | Security Management Provider |
| PUFs | Physical Unclonable Functions |
| TTP | Trusted Third Party |
| SP | Service Provider |
References
- Whitmore, A.; Agarwal, A.; Xu, L.D. The Internet of Things? A survey of topics and trends. Inf. Syst. Front. 2015, 17, 261–274. [Google Scholar] [CrossRef]
- Mainetti, L.; Patrono, L.; Vilei, A. Evolution of wireless sensor networks towards the internet of things: A survey. In Proceedings of the 19th International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 15–17 September 2011; pp. 1–6.
- Ahn, H.; Kim, H.; Park, J.R. Smart monitoring of indoor asbestos based on the distinct optical properties of asbestos from particulate matters. J. Converg. 2014, 5, 22–25. [Google Scholar]
- Xu, L.D.; He, W.; Li, S. Internet of things in industries: A survey. IEEE Trans. Ind. Inf. 2014, 10, 2233–2243. [Google Scholar] [CrossRef]
- Hwang, K.; Nam, S. Near real-time M2M communication for bidirectional AMR systems. J. Converg. 2014, 5, 1–7. [Google Scholar]
- Mennicken, S.; Vermeulen, J.; Huang, E.M. From today’s augmented houses to tomorrow’s smart homes: New directions for home automation research. In Proceedings of the 2014 ACM International Joint Conference on Pervasive and Ubiquitous Computing, Seattle, WA, USA, 13–17 September 2014; pp. 105–115.
- Ablondi, W. 2014 Smart Home Systems and Services Forecast Global Total; Strategy Analytics: Boston, MA, USA, 2014; Available online: https://www.strategyanalytics.com/access-services/devices/connected-home/smart-home/reports/report-detail/2014-smart-home-systems-and-services-forecast-global-total#.V3YPmPmLRFE (accessed on 28 June 2016).
- Levy, D.; Saadoun, O.; Taga, K.; Riegel, L. Catching the smart home opportunity. Arthur D. Little Time. 2012. Available online: http://www.adlittle.es/uploads/tx_extthoughtleadership/ADL_TIME_2012_Smart_Home_Opportunity.pdf (accessed on 28 June 2016).
- Hewlett Packard Enterprise. How Safe Are Home Security Systems? An HPE on IoT Security. 2015. Available online: http://www8.hp.com/h20195/V2/GetPDF.aspx/4AA5-7342ENW.pdf (accessed on 28 June 2016).
- Barcena, M.B.; Wueest, C. Insecurity in the Internet of Things. Symantec White Paper. 2015. Available online: https://www.symantec.com/content/dam/symantec/docs/white-papers/insecurity-in-the-internet-of-things-en.pdf (accessed on 28 June 2016).
- Yoshigoe, K.; Dai, W.; Abramson, M.; Jacobs, A. Overcoming invasion of privacy in smart home environment with synthetic packet injection. In Proceedings of the TRON Symposium (TRONSHOW), Tokyo, Japan, 9–10 December 2015; pp. 1–7.
- Suryadevara, N.K.; Mukhopadhyay, S.C.; Kelly, S.D.T.; Gill, S.P.S. WSN-based smart sensors and actuator for power management in intelligent buildings. Mechatronics. IEEE/ASME Trans. Mechatron. 2015, 20, 564–571. [Google Scholar] [CrossRef]
- Lee, C.; Zappaterra, L.; Choi, K.; Choi, H.A. Securing smart home: Technologies, security challenges, and security requirements. In Proceedings of the 2014 IEEE Conference on Communications and Network Security (CNS), San Francisco, CA, USA, 29–31 October 2014; pp. 67–72.
- Pughat, A.; Sharma, V. A review on stochastic approach for dynamic power management in wireless sensor networks. Hum.-Centric Comput. Inf. Sci. 2015, 5, 1–14. [Google Scholar] [CrossRef]
- Vanus, J.; Kucera, P.; Martinek, R.; Koziorek, J. Development and testing of a visualization application software, implemented with wireless control system in smart home care. Hum.-Centric Comput. Inf. Sci. 2014, 4, 1–19. [Google Scholar] [CrossRef]
- Soliman, M.; Abiodun, T.; Hamouda, T.; Zhou, J.; Lung, C.H. Smart home: Integrating internet of things with web services and cloud computing. In Proceedings of the 2013 IEEE 5th International Conference on Cloud Computing Technology and Science (CloudCom), Bristol, UK, 2–5 December 2013; pp. 317–320.
- Lai, Y.X.; Lai, C.F.; Huang, Y.M.; Chao, H.C. Multi-appliance recognition system with hybrid SVM/GMM classifier in ubiquitous smart home. Inf. Sci. 2013, 230, 39–55. [Google Scholar] [CrossRef]
- Sun, Q.; Yu, W.; Kochurov, N.; Hao, Q.; Hu, F. A multi-agent-based intelligent sensor and actuator network design for smart house and home automation. J. Sens. Actuator Netw. 2013, 2, 557–588. [Google Scholar] [CrossRef]
- Asare-Bediako, B.; Kling, W.L.; Ribeiro, P.F. Multi-agent system architecture for smart home energy management and optimization. In Proceedings of the Innovative Smart Grid Technologies Europe (ISGT EUROPE), Lyngby, Danmark, 6–9 October 2013; pp. 1–5.
- Gaur, M.S.; Pant, B. Trusted and secure clustering in mobile pervasive environment. Hum.-Centric Comput. Inf. Sci. 2015, 5, 1–17. [Google Scholar] [CrossRef]
- Kang, J.; Park, J.H.; Suk, S. Design of a Distributed Personal Information Access Control Scheme for Secure Integrated Payment in NFC. Symmetry 2015, 7, 935–948. [Google Scholar] [CrossRef]
- Penrig, A.; Song, D.; Tygar, D. Elk, a new protocol for efficient large-group key distribution. In Proceedings of the Security and Privacy, Oakland, CA, USA, 14–16 May 2001; pp. 247–262.
- Wong, C.K.; Mohamed, W.; Simon, G.; Lam, S. Secure group communications using key graphs. Tech. Rep. 1998, 8, 16–30. [Google Scholar]
- Nguyen, T.-D.; Huh, E.-N. An efficient Key management for secure multicast in Sensor-Cloud. In Proceedings of the 2011 First ACIS/JNU International Conference, Suwon, Korea, 23–25 May 2011; pp. 3–9.
- Hassan, M.M.; Song, B.; Huh, E.-N. A framework of sensor-cloud integration opportunities and challenges. In Proceedings of the 3rd International Conference on Ubiquitous Information Management and Communication, Suwon, Korea, 15–16 January 2009; pp. 618–626.
- Kang, J.; Han, J.; Park, J.H. Design of IP Camera Access Control Protocol by Utilizing Hierarchical Group Key. Symmetry 2015, 7, 1567–1586. [Google Scholar] [CrossRef]
- Gupta, G.P.; Misra, M.; Garg, K. An Energy Efficient Distributed Approach-Based Agent Migration Scheme for Data Aggregation in Wireless Sensor Networks. JIPS 2015, 11, 148–164. [Google Scholar]
- Hwang, K.; Jang, I. Ultra Low Power Data Aggregation for Request Oriented Sensor Networks. JIPS 2014, 10, 412–428. [Google Scholar] [CrossRef]
- Dahane, A.; Berrached, N.-E.; Loukil, A. A virtual laboratory to practice mobile wireless sensor networks: A case study on energy efficient and safe weighted clustering algorithm. J. Inf. Process. Syst. 2015, 11, 205–228. [Google Scholar]
- Byun, J.; Jeon, B.; Noh, J.; Kim, Y.; Park, S. An intelligent self-adjusting sensor for smart home services based on ZigBee communications. IEEE Trans. Consum. Electron. 2012, 58, 794–802. [Google Scholar] [CrossRef]
- Viani, F.; Robol, F.; Polo, A.; Rocca, P.; Oliveri, G.; Massa, A. Wireless architectures for heterogeneous sensing in smart home applications: Concepts and real implementation. IEEE Proc. 2013, 101, 2381–2396. [Google Scholar] [CrossRef]
- Gill, K.; Yang, S.H.; Wang, W.L. Secure remote access to home automation networks. IET Inf. Secur. 2013, 7, 118–125. [Google Scholar] [CrossRef]
- Sivaraman, V.; Gharakheili, H.H.; Vishwanath, A.; Boreli, R.; Mehani, O. Network-level security and privacy control for smart-home IoT devices. In Proceedings of the 2015 IEEE 11th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Abu Dhabi, Saudi Arabia, 19–21 October 2015; pp. 163–167.
- Gassend, B.; Clarke, D.; van Dijk, M.; Devadas, S. Silicon physical random functions. In Proceedings of the 9th ACM Conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002; pp. 148–160.
- Gassend, B.L.P. Physical Random Functions. Master’s Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 2003. [Google Scholar]
- Bielefeldt, J.; Chellappan, S. Sensor authentication in collaborating sensor networks. In Proceedings of the 2014 13th Annual Mediterranean, Ad Hoc Networking Workshop (MED-HOC-NET), Piran, Slovenia, 2–4 June 2014; pp. 55–62.
- Delvaux, J.; Peeters, R.; Gu, D. A survey on lightweight entity authentication with strong PUFs. ACM Comput. Surv. (CSUR) 2015, 48, 26. [Google Scholar] [CrossRef]
- Feige, U.; Fiat, A.; Shamir, A. Zero-knowledge proofs of identity. J. Cryptol. 1988, 1, 77–94. [Google Scholar] [CrossRef]
- Mohr, A. A Survey of Zero-Knowledge Proofs with Applications to Cryptography; Southern Illinois University: Carbondale, IL, USA, 2007; pp. 1–12. [Google Scholar]
- Bengio, S.; Brassard, G.; Desmedt, Y.G.; Goutier, C.; Quisquater, J.J. Secure implementation of identification systems. J. Cryptol. 1991, 4, 175–183. [Google Scholar] [CrossRef]


| Notation | Meaning |
|---|---|
| Sensor | Smart home Sensor Device |
| Gateway | Smart home Gateway |
| TTP | Trusted Third Party |
| SP | Service Provider |
| IDS, IDG, IDT, IDP | Sensor, Gateway, TTP and SP ID |
| PUF | Physical unclonable function |
| C[c1, c2, … , cm] | Challenge vector value for PUF |
| R[r1, r2, … , rm] | Response vector value for PUF |
| S[s1, s2, … , sk] | Gateway private key vector for Zero-knowledge Proofs |
| V[v1, v2, … , vk] | Gateway public key vector for Zero-knowledge Proofs |
| PC[pc1, pc2, … , pcj] | Challenge vector for zero-knowledge Proofs |
| n | Public key for Zero-knowledge Proofs |
| r | Random value for Zero-knowledge Proofs |
| x | Witness value for zero-knowledge Proofs |
| y | Response value for zero-knowledge Proofs |
| T | Timestamp |
| N | Nonce |
| SK | Session key between Sensor and SP |
| H() | Hash function |
| f() | SK generator |
| D() | Decryption |
| E() | Encryption |
| Jinsung et al. [30] | Alessandro et al. [31] | Khusvinder et al. [32] | Vijay et al. [33] | Proposed Scheme | |
|---|---|---|---|---|---|
| Multiplatform | X | O | X | X | O |
| Low Resource | O | O | Δ | X | O |
| Security | X | X | O | O | O |
| Privacy | X | X | Δ | O | O |
| ELK [22] | LKH [23] | CoGKTK [24] | sGIM [25] | Proposed Scheme | |
|---|---|---|---|---|---|
| Distributed KS | Not-support | Not-support | Support | Support | Support |
| Forward Security | X | X | O | X | O |
| Mutual Authentication | X | X | O | X | O |
| Relay Attack | X | X | X | X | O |
| Replay Attack | X | X | O | O | O |
| Sensor | Gateway | SP | TTP | |
|---|---|---|---|---|
| PUF | m+1 | - | - | (m + 1) * X |
| Hash | 1 | 1 | - | 2X |
| Encryption | 1 | - | x | - |
| Decryption | 1 | - | x | - |
| f() | 1 | - | x | - |
| Nonce generation | 1 | k | - | (m + 2) * X |
| Zero-knowledge Proofs computations | - | O(ni) | O(nj) | - |
| Sensor | Gateway | SP | TTP | |
|---|---|---|---|---|
| ID | 4 | 2 + Y + X | 3 + x | 2 + Y + X |
| Challenge C | 1 | 1 | mx | mX |
| Response R | 1 | - | - | mX |
| SK | 1 | - | x | - |
| Timestamp | 1 | - | - | X |
| Nonce | 1 | 1 | - | - |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kang, J.; Kim, M.; Park, J.H. A Reliable TTP-Based Infrastructure with Low Sensor Resource Consumption for the Smart Home Multi-Platform. Sensors 2016, 16, 1036. https://doi.org/10.3390/s16071036
Kang J, Kim M, Park JH. A Reliable TTP-Based Infrastructure with Low Sensor Resource Consumption for the Smart Home Multi-Platform. Sensors. 2016; 16(7):1036. https://doi.org/10.3390/s16071036
Chicago/Turabian StyleKang, Jungho, Mansik Kim, and Jong Hyuk Park. 2016. "A Reliable TTP-Based Infrastructure with Low Sensor Resource Consumption for the Smart Home Multi-Platform" Sensors 16, no. 7: 1036. https://doi.org/10.3390/s16071036
APA StyleKang, J., Kim, M., & Park, J. H. (2016). A Reliable TTP-Based Infrastructure with Low Sensor Resource Consumption for the Smart Home Multi-Platform. Sensors, 16(7), 1036. https://doi.org/10.3390/s16071036





_Park.png)

