GNSS Spoofing Network Monitoring Based on Differential Pseudorange
Abstract
:1. Introduction
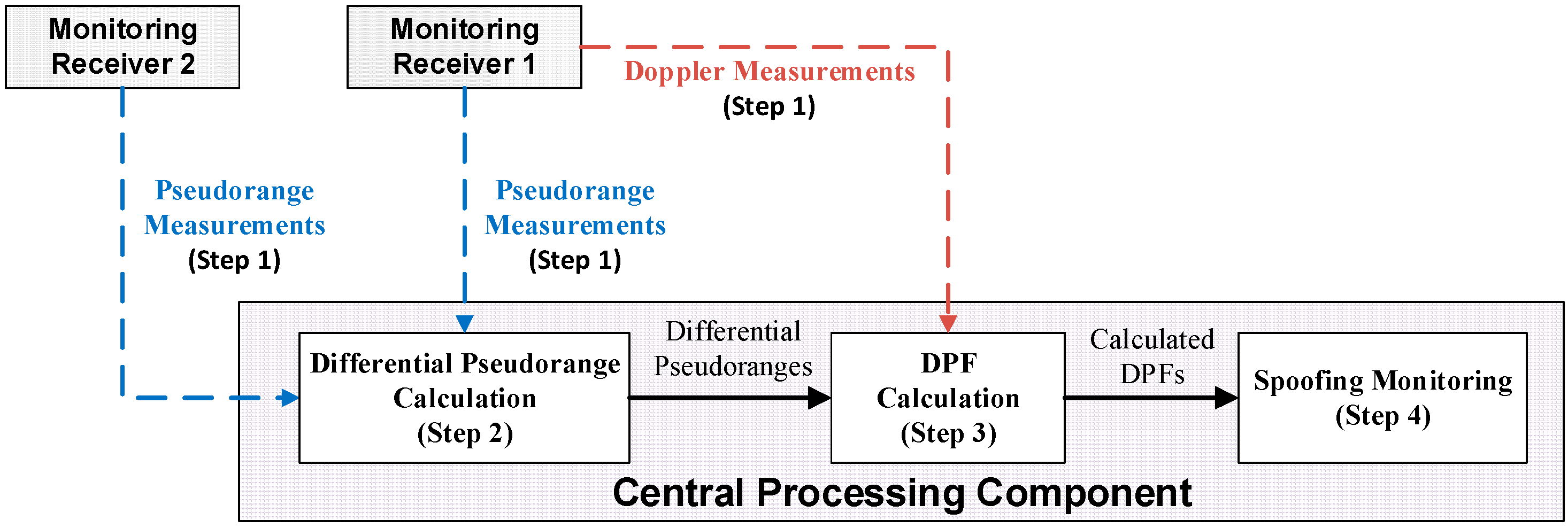
2. Spoofing Network Monitoring Architecture
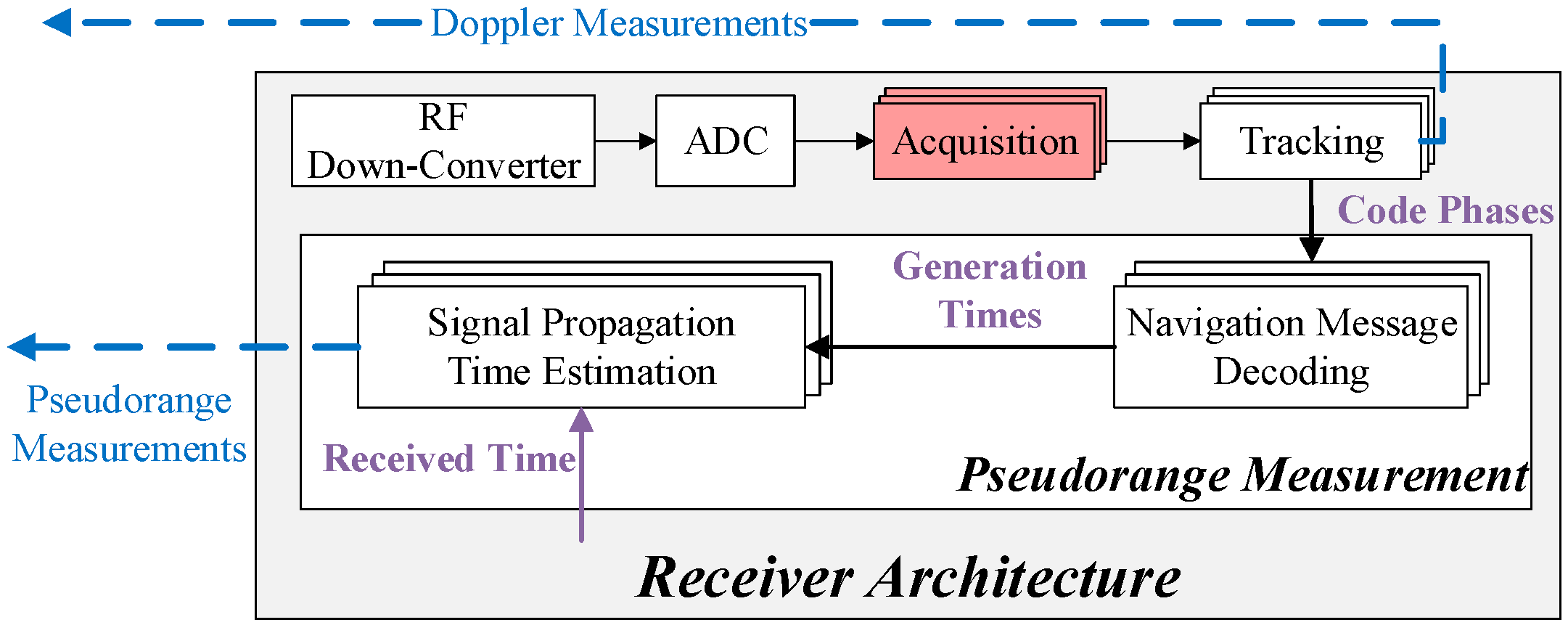
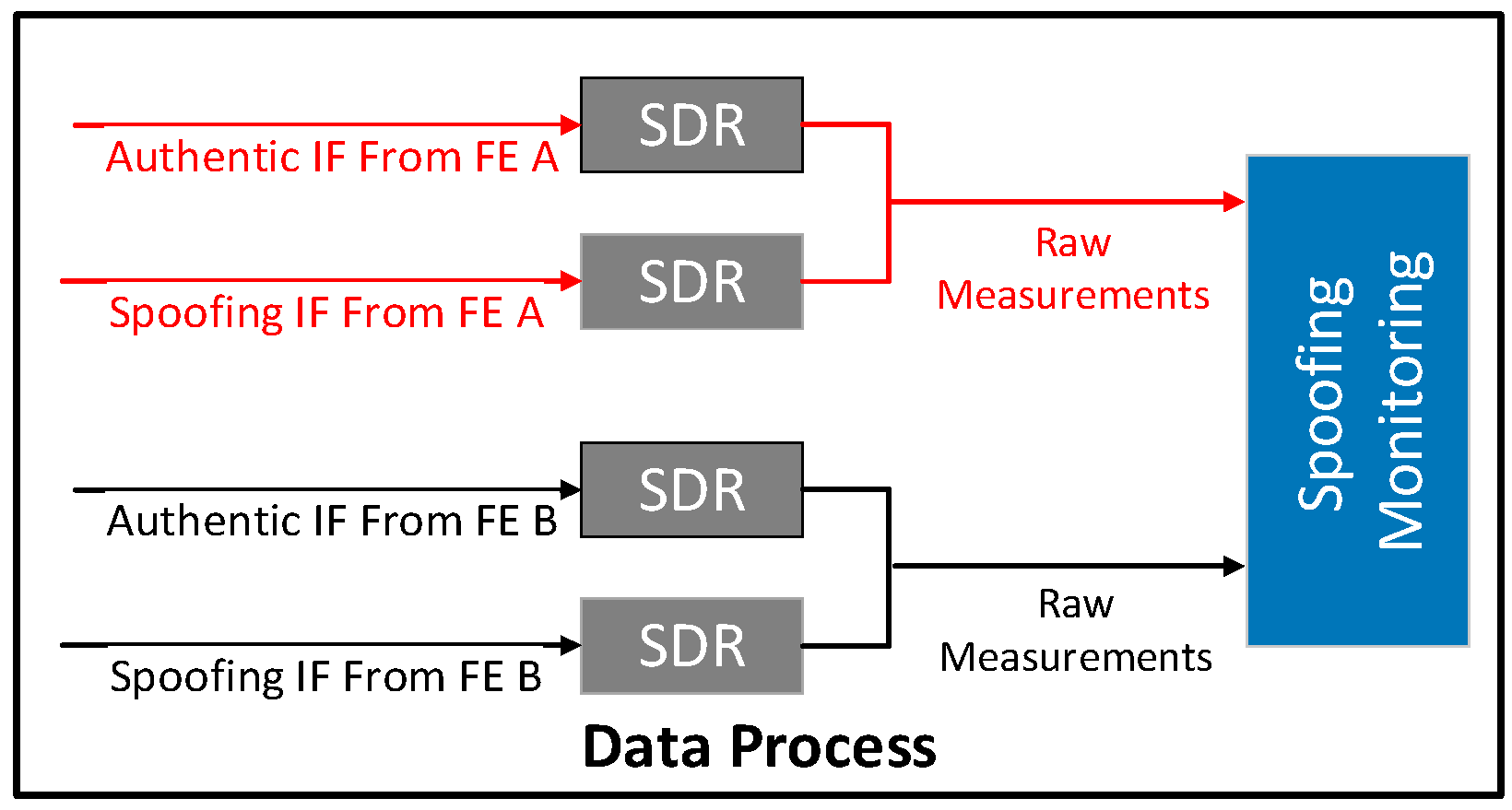
2.1. Raw Measurements
- In a spoofing case, although both authentic and spoofing signals are processed by the receiver, the receiver itself does not know the types of the signals (spoofing or authentic), and it does not even know whether there are spoofing signals or not.
- The monitoring receiver does not need to perform the PVT process because its only function is to provide raw measurements. Hence, the PVT block is not given in the monitoring receiver architecture.
2.2. Differential Pseudorange Calculation
2.3. DPF Calculation
2.4. Spoofing Monitoring
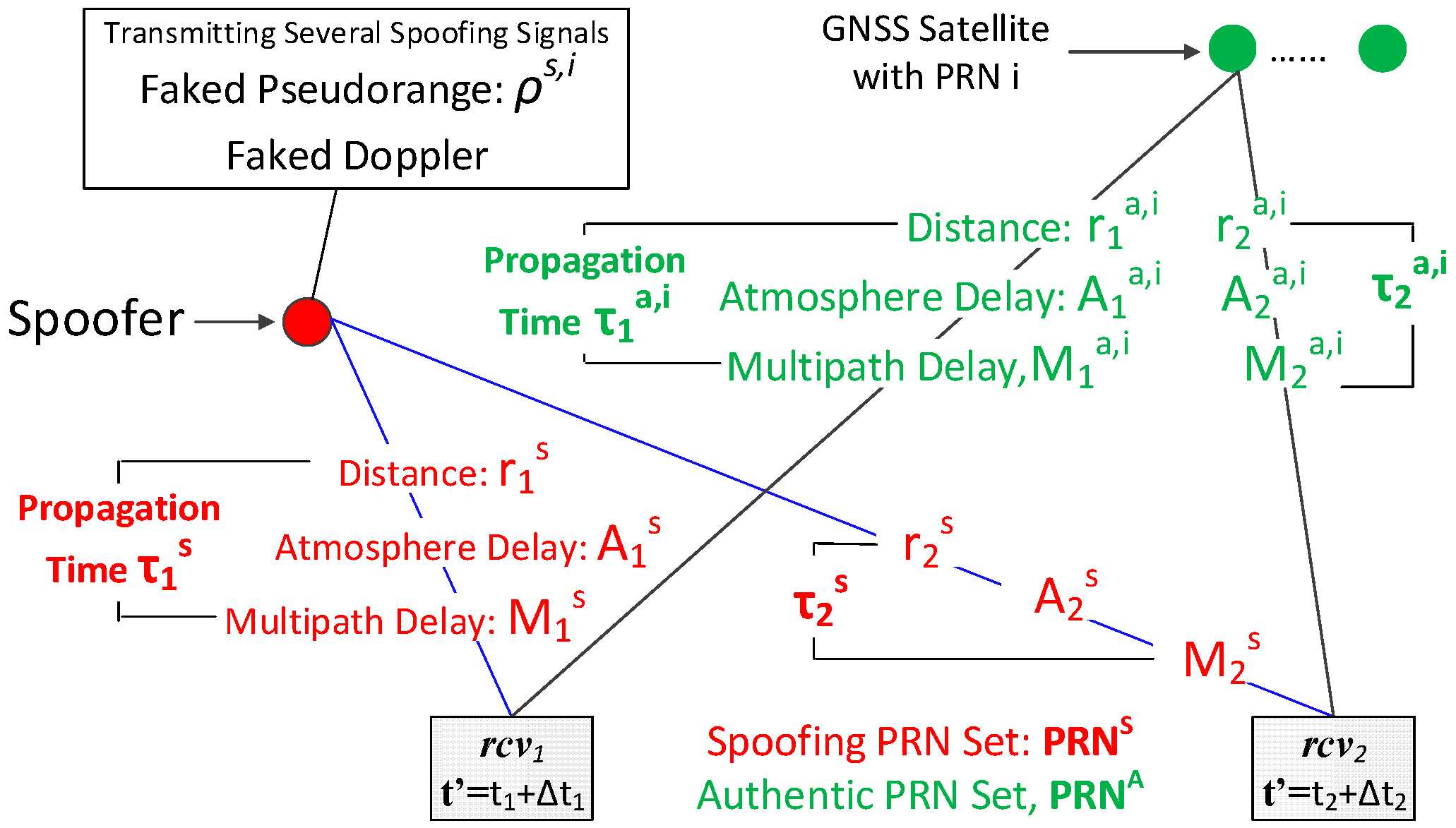
3. Differential Pseudorange Models
3.1. Spoofing Scenario
3.2. Pseudorange Measurement
3.3. Differential Pseudorange
4. Differential Pseudorange to Carrier Frequency Ratio
5. Monitoring Methodology
5.1. Hypothesis Test
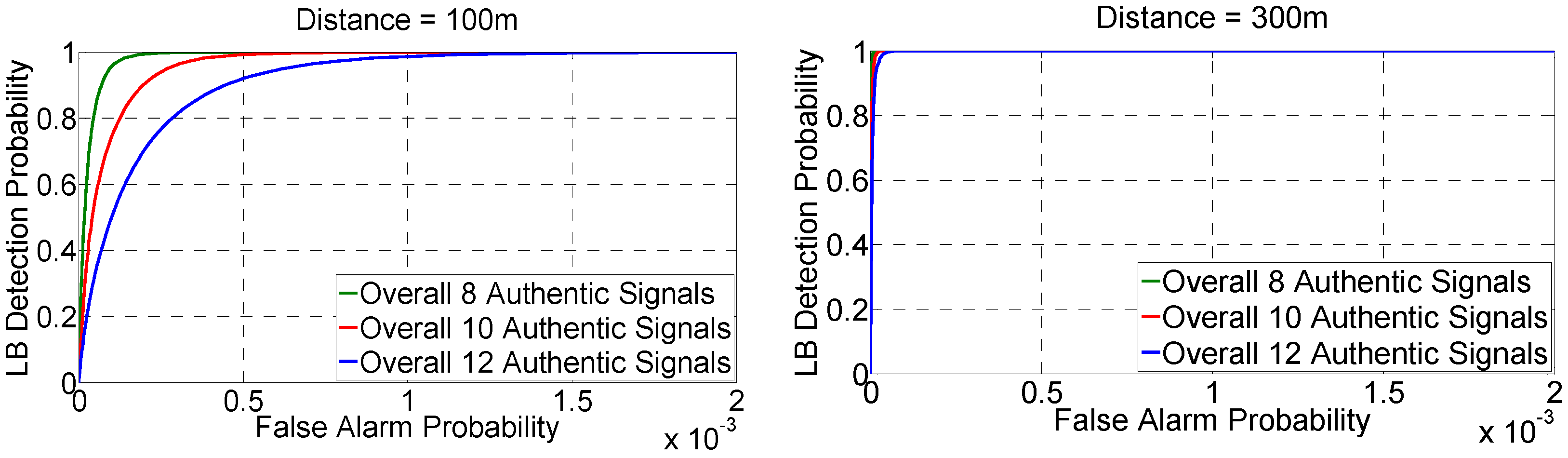
5.2. The Lower Bound (LB) on the Detection Probability
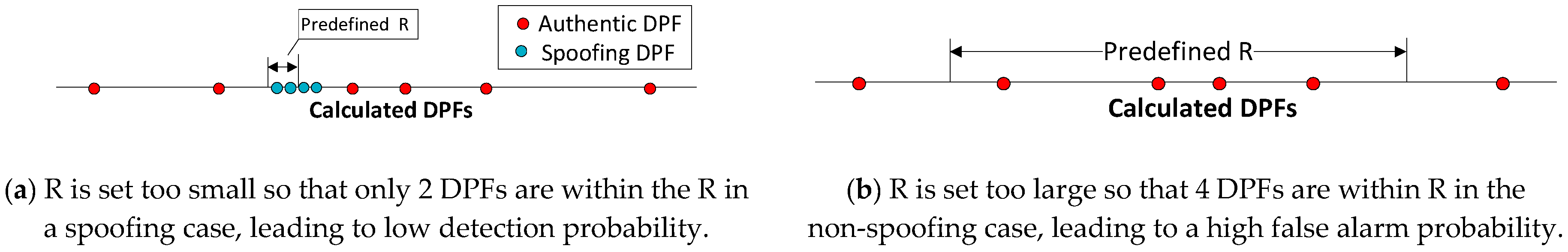
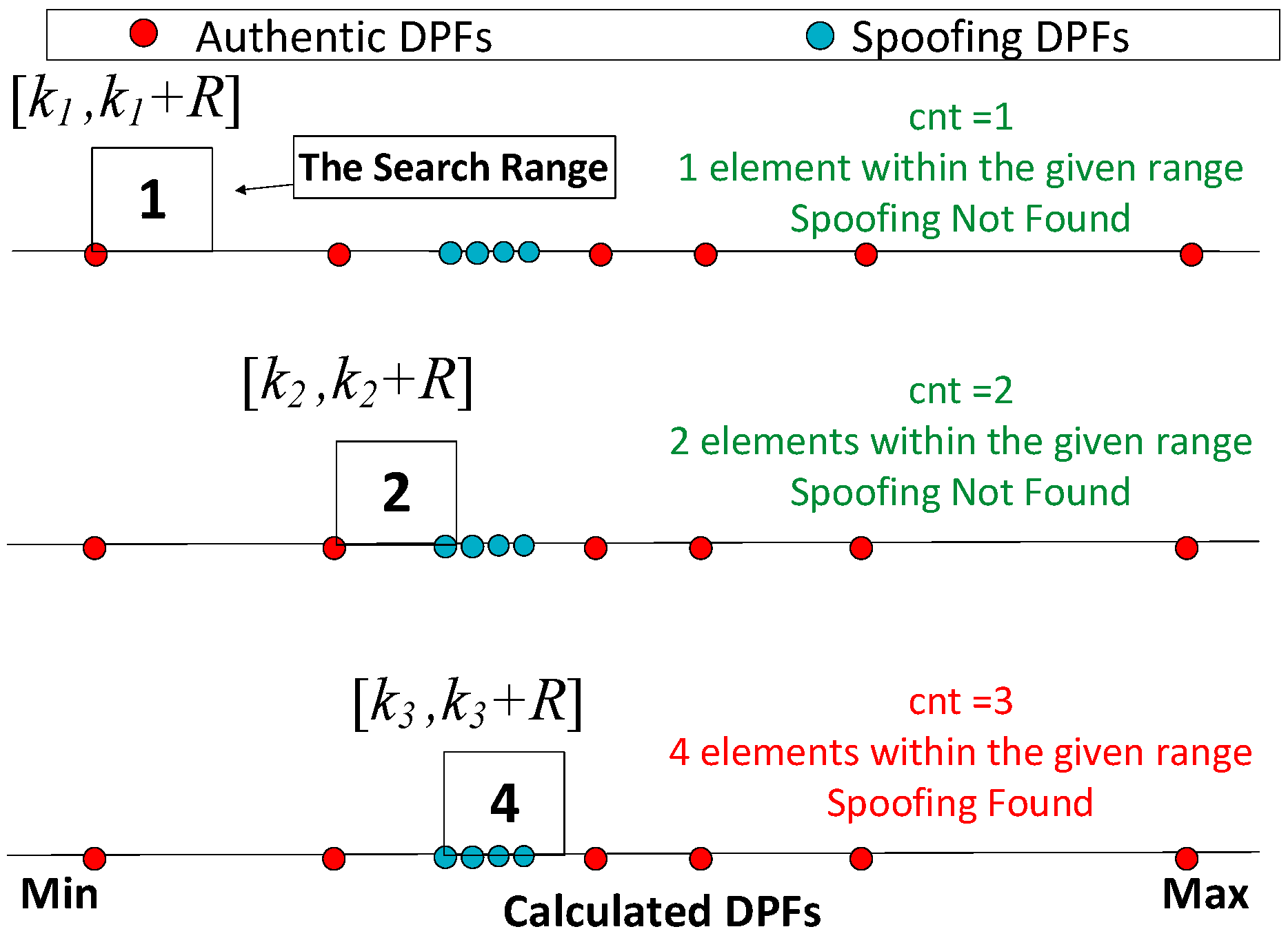
5.3. Algorithm
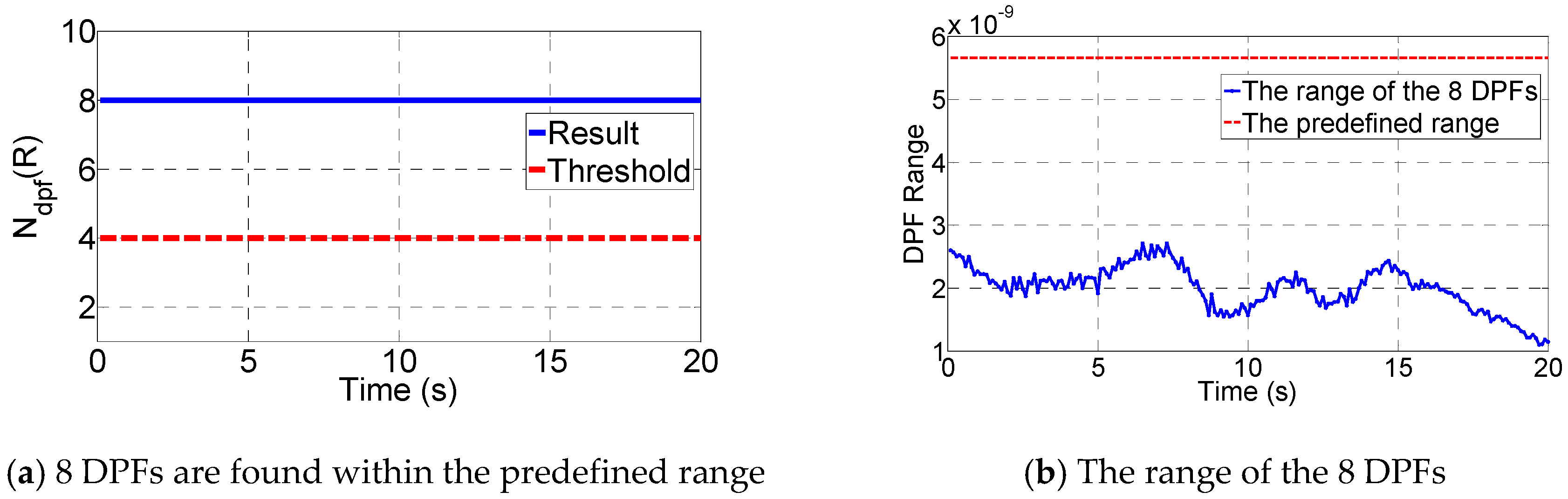
- Define the range R based on Equation (23).
- Sort the calculated DPFs from minimum to maximum: [k1 ≤ k2 ≤ … ≤ kn].
- Generate a counter cnt and initialize it as 1.
- Define a search range [kcnt,kcnt + R] and calculate the number of elements within the range.
- If the number equals or is over 4, the presence of spoofing is determined. Otherwise, goes to step 6.
- Update cnt as: cnt = cnt + 1, and goes to step 4 to test the next range.
6. Performance Analysis
6.1. Simulation Setup
6.2. Result
7. Experiments and Results
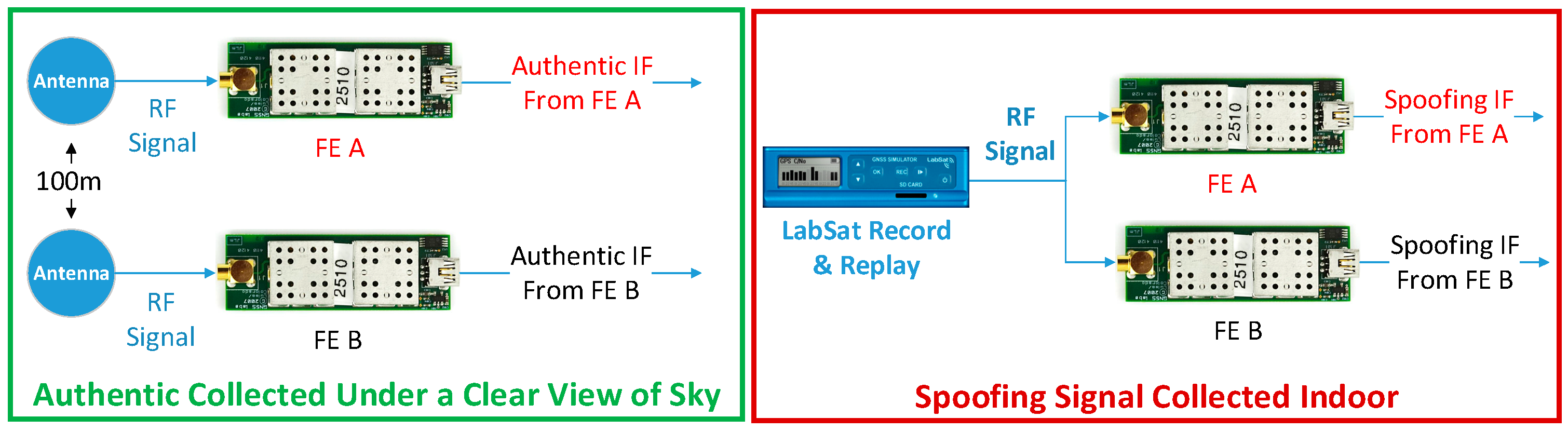
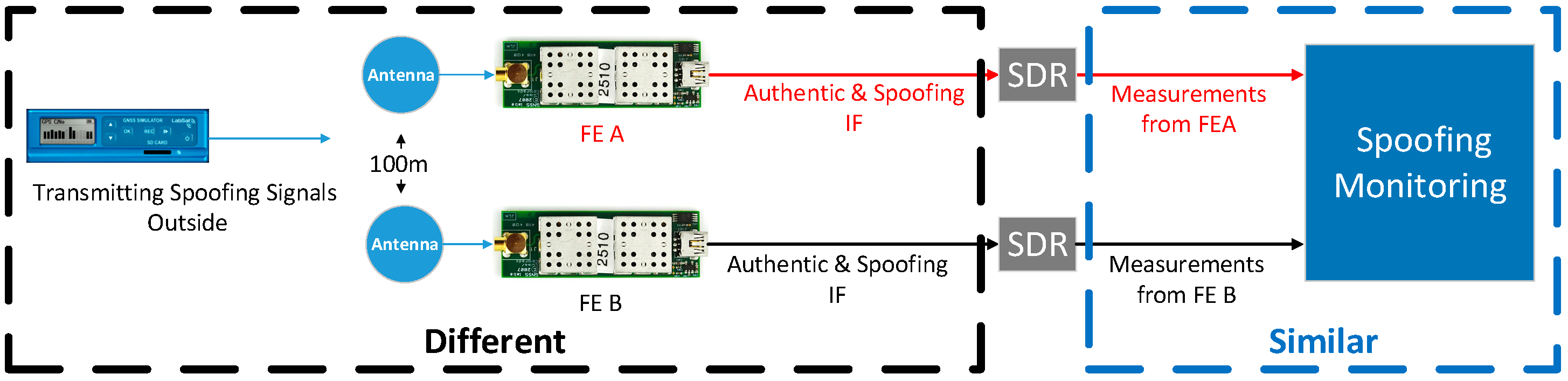
7.1. Setup
7.1.1. Signal Collection
7.1.2. Signal Process
7.1.3. The Limitations of the Adopted Experiment
7.2. Result
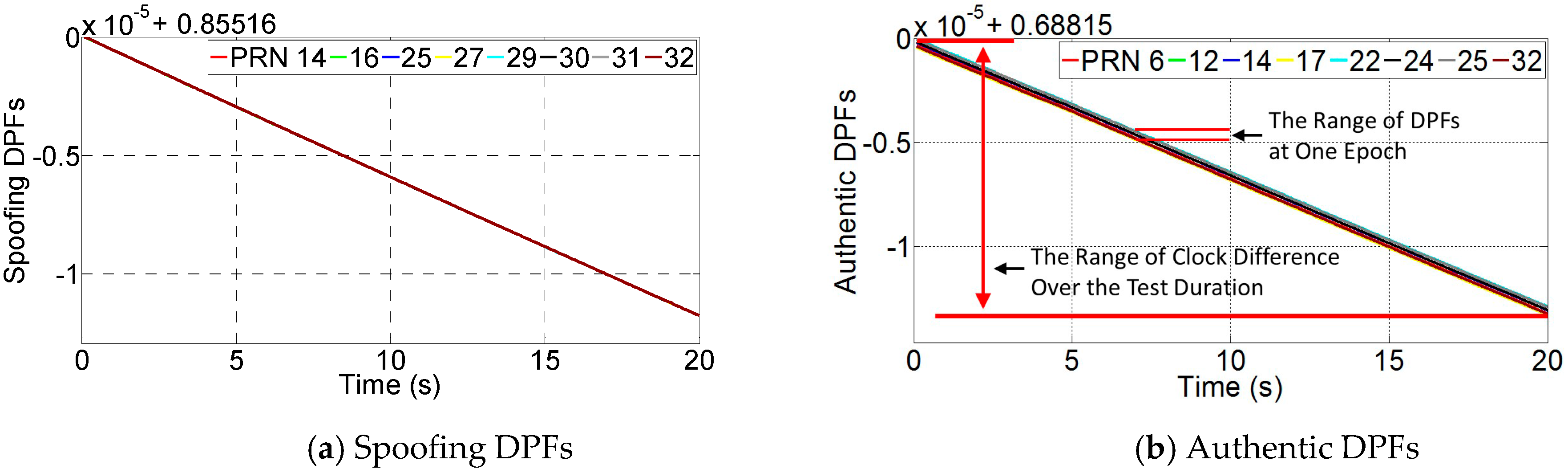
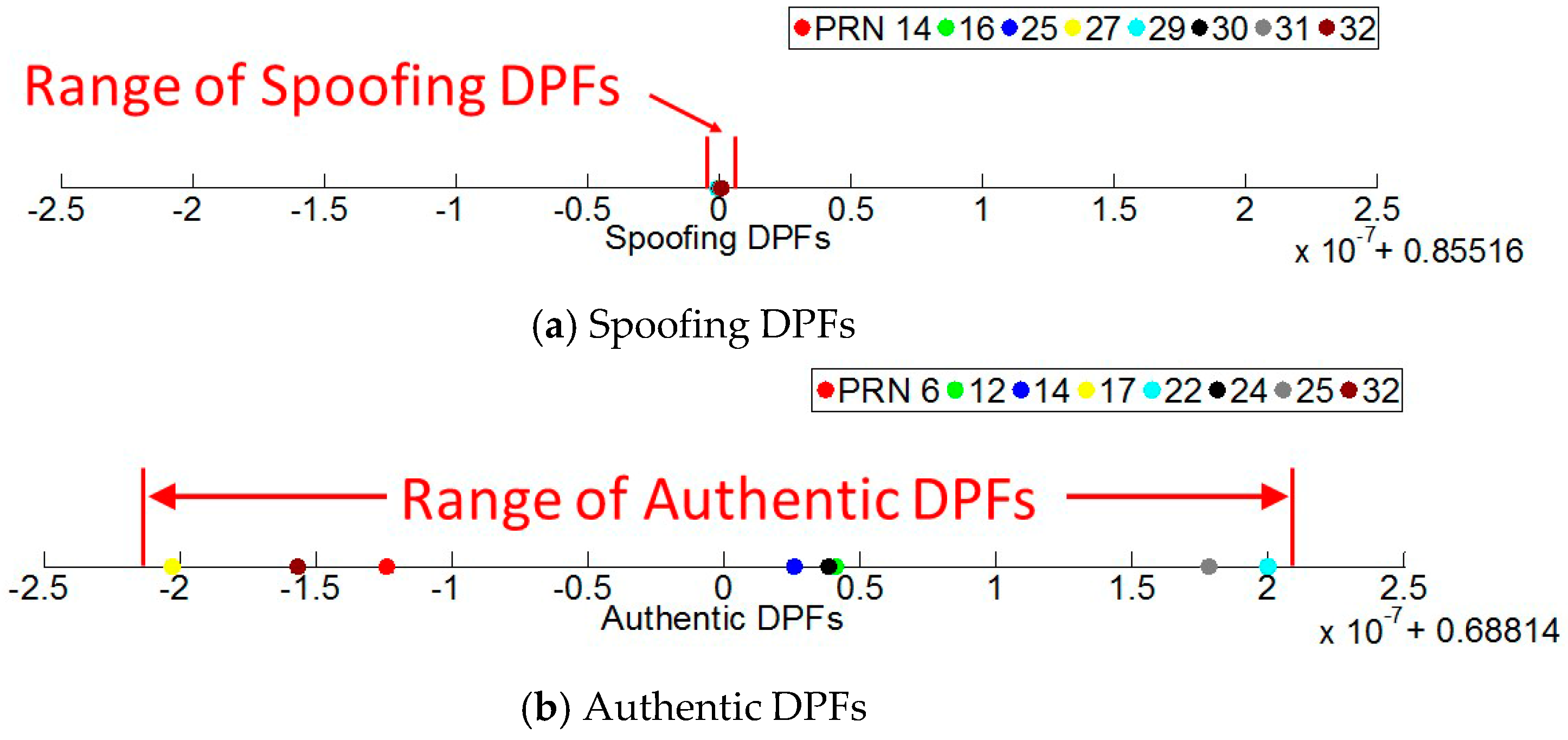
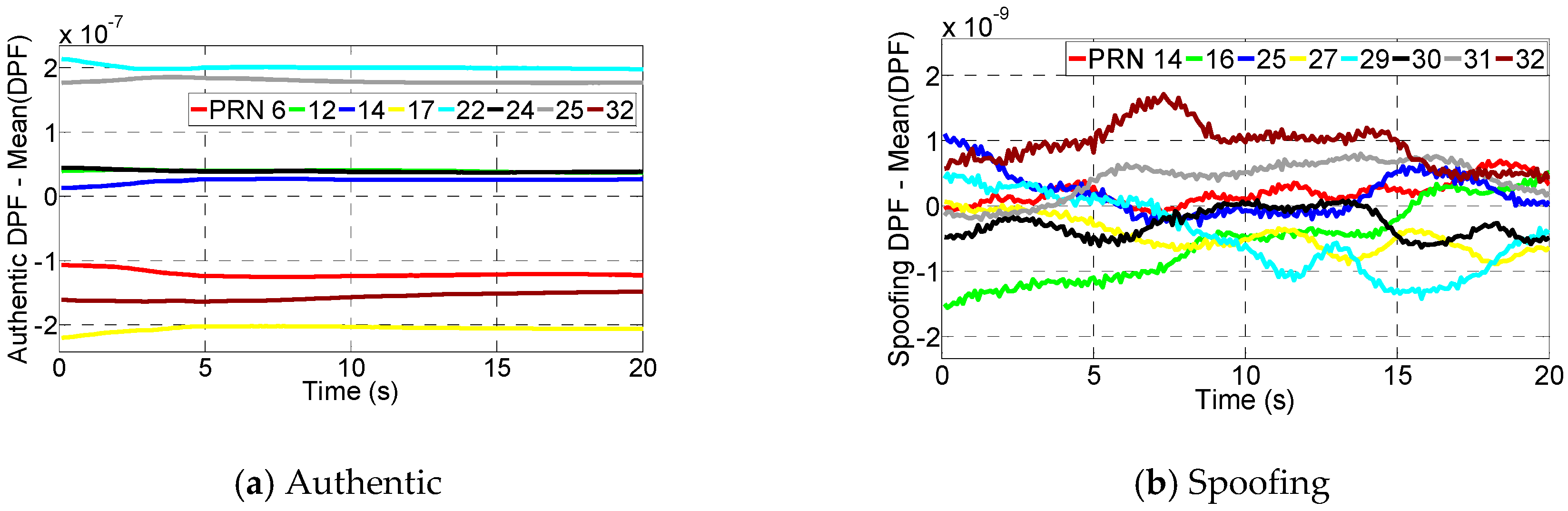
7.2.1. DPF
7.2.2. Spoofing Monitoring
8. Discussions and Future Work
8.1. The Rationality of the Two Assumptions
8.1.1. Assumption 1: Multiple Fake Signals are Transmitted from a Common Antenna
8.1.2. Assumption 2: There are 4 or More Spoofing Signals Present in the Spoofing Case
8.2. Future Work
9. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Appendix A
A.1. Spoofing Pseudorange
A.2. Authentic Pseudorange
Appendix B
Appendix C
References
- John, A. Vulnerability Assessment of the Transportation Infrastructure Relying on the Global Positioning System; Volpe National Transportation Systems Center: Cambridge, MA, USA, 2001. [Google Scholar]
- Shepard, D.P.; Bhatti, J.A.; Humphreys, T.E. Drone hack: Spoofing attack demonstration on a civilian unmanned aerial vehicle. GPS World 2012, 23, 30–33. [Google Scholar]
- Proctor, A.G.; Curry, C.W.T.; Tong, J.; Watson, R.; Greaves, M.; Cruddace, P. Protecting the UK infrastructure: A system to detect GNSS jamming and interference. Inside GNSS 2011, September/October, 49–57. [Google Scholar]
- Humphreys, T.E.; Ledvina, B.M.; Psiaki, M.L.; O’Hanlon, B.; Kintner, P.M., Jr. Assessing the spoofing threat: Development of a portable GPS civilian spoofer. In Proceedings of the ION GNSS International Technical Meeting of the Satellite Division, Savannah, GA, USA, 16–19 September 2008.
- Psiaki, M.L.; Humphreys, T.E. GNSS spoofing and detection. Proc. IEEE 2016, 104, 1258–1270. [Google Scholar] [CrossRef]
- Lo, S.; De Lorenzo, D.; Enge, P.; Akos, D.; Bradley, P. Signal authentication: A secure civil GNSS for today. Inside GNSS 2009, 4, 30–39. [Google Scholar]
- Wesson, K.; Rothlisberger, M.; Humphreys, T.E. Practical cryptographic civil GPS signal authentication. Navig. J. Inst. Navig. 2012, 59, 177–193. [Google Scholar] [CrossRef]
- Humphreys, T.E. Detection strategy for cryptographic GNSS anti-spoofing. IEEE Trans. Aerosp. Electron. Syst. 2013, 49, 1073–1090. [Google Scholar] [CrossRef]
- Nielsen, J.; Broumandan, A.; Lachapelle, G. Method and System for Detecting GNSS Spoofing Signals. U.S. Patent 7,952,519 B1, 31 May 2011. [Google Scholar]
- Nielsen, J.; Broumandan, A.; Lachapelle, G. GNSS spoofing detection for single antenna handheld receivers. Navig. J. Inst. Navig. 2011, 58, 335–344. [Google Scholar] [CrossRef]
- Broumandan, A.; Jafarnia, A.; Dehghanian, V.; Nielsen, J.; Lachapelle, G. GNSS spoofing detection in handheld receivers based on signal spatial correlation. In Proceedings of the 2012 IEEE/ION Position Location and Navigation Symposium (PLANS), Myrtle Beach, SC, USA, 23–26 April 2012; pp. 479–487.
- Broumandan, A.; Jafarnia-Jahromi, A.; Lachapelle, G. Spoofing detection, classification and cancelation (SDCC) receiver architecture for a moving GNSS receiver. GPS Solut. 2014, 19, 475–487. [Google Scholar] [CrossRef]
- Ledvina, B.M.; Bencze, W.J.; Galusha, B.; Miller, I. An in-line anti-spoofing device for legacy civil GPS receivers. In Proceedings of the 2010 International Technical Meeting of The Institute of Navigation, San Diego, CA, USA, 25–27 January 2010; pp. 698–712.
- Wesson, K.D.; Shepard, D.P.; Bhatti, J.A.; Humphreys, T.E. An evaluation of the vestigial signal defense for civil GPS anti-spoofing. In Proceedings of the 2011 ION GNSS, Portland, OR, USA, 20–23 September 2011; pp. 2646–2656.
- Akos, D.M. Who’s Afraid of the Spoofer? GPS/GNSS spoofing detection via automatic gain control (AGC). Navigation 2012, 59, 281–290. [Google Scholar]
- Jafarnia, J.A.; Broumandan, A.; Nielsen, J.; Lachapelle, G. Pre-despreading authenticity verification for GPS L1 C/A signals. Navigation 2014, 61, 1–11. [Google Scholar] [CrossRef]
- Psiaki, M.L.; O’Hanlon, B.W.; Powell, S.P.; Bhatti, J.A.; Wesson, K.D.; Humphreys, T.E.; Schofield, A. GNSS spoofing detection using two-antenna differential carrier phase. In Proceedings of the 27th International Technical Meeting of The Satellite Division of the Institute of Navigation (ION GNSS+ 2014), Tampa, FL, USA, 8–12 September 2014.
- Swaszek, P.F.; Hartne, R.J. Spoof detection using multiple COTS receivers in safety critical applications. In Proceedings of the 2013 ION GNSS+, Nashville, TN, USA, 16–20 September 2013.
- Swaszek, P.F.; Richard, J.H. A multiple COTS receiver GNSS spoof detector—Extensions. In Proceedings of the 2014 International Technical Meeting of the Institute of Navigation, San Diego, CA, USA, 27–29 January 2014.
- Axell, E.; Larsson, E.G.; Persson, D. GNSS spoofing detection using multiple mobile COTS receivers. In Proceedings of the IEEE International Conference on Acoustics, Speech, and Signal Process (ICASSP), Brisbane, Australia, 19–24 April 2015.
- Tippenhauer, N.O.; Pöpper, C.; Rasmussen, K.B.; Capkun, S. On the requirements for successful GPS spoofing attacks. In Proceedings of the ACM Conference on Computer and Communications Security, Chicago, IL, USA, 17–21 October 2011; pp. 75–86.
- Radin, S.D.; Swaszek, P.F.; Seals, K.C.; Hartnett, R.J. GNSS spoof detection based on pseudoranges from multiple receivers. In Proceedings of the 2015 International Technical Meeting of The Institute of Navigation, Dana Point, CA, USA, 26–28 January 2015; pp. 657–671.
- Montgomery, P.Y.; Humphreys, T.E.; Ledvina, B.M. A multi-antenna defense receiver autonomous GPS spoofing detection. Inside GNSS 2009, 4, 40–46. [Google Scholar]
- Kaplan, E.D. Understanding GPS: Principles and Applications; Artech House: Norwood, MA, USA, 1996. [Google Scholar]
- Neagoe, T.; Cristea, V.; Banica, L. NTP versus PTP in computer networks clock synchronization. In Proceedings of IEEE International Symposium on Industrial Electronics, Montreal, QC, Canada, 9–13 July 2006; pp. 317–362.
- Parkinson, B.W.; Spilker, J.J.; Axelrad, P.; Enge, P. Global Positioning System: Theory and Applications; American Institute of Aeronautics and Astronautics Inc.: New York, NY, USA, 1996. [Google Scholar]
- Enge, P.K. The global positioning system: Signals, measurements, and performance. Int. J. Wirel. Inf. Netw. 1994, 1, 83–105. [Google Scholar] [CrossRef]
- Psiaki, M.L.; Powell, S.P.; O’Hanlon, B.W. GNSS spoofing detection using high-frequency antenna motion and carrier-phase data. In Proceedings of the 26th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS+ 2013), Nashville, TN, USA, 16–20 September 2013; pp. 2949–2991.
- Tsimashenka, I.; Knottenbelt, W.; Harrison, P. Controlling variability in split-merge systems. In Proceedings of the International Conference on Analytical and Stochastic Modeling Techniques and Applications, Grenoble, France, 4–6 June 2012.
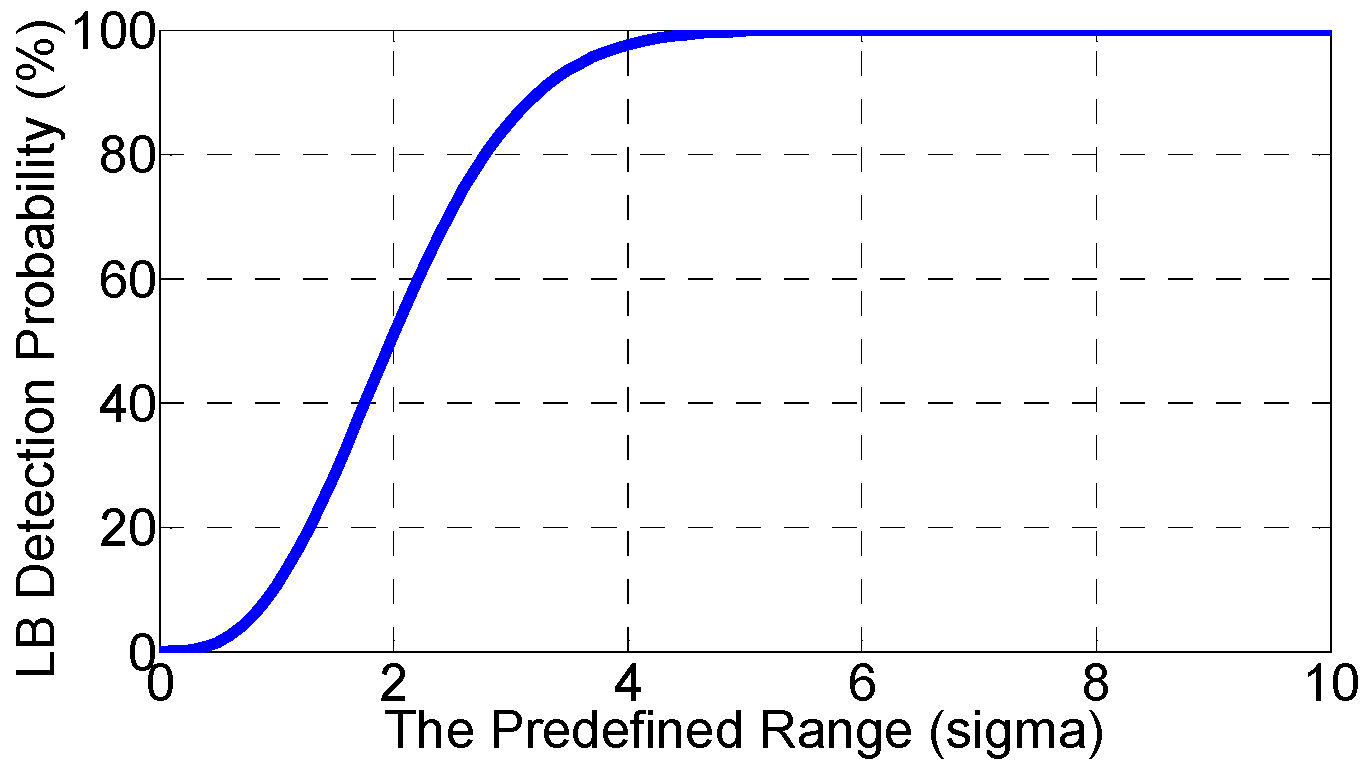
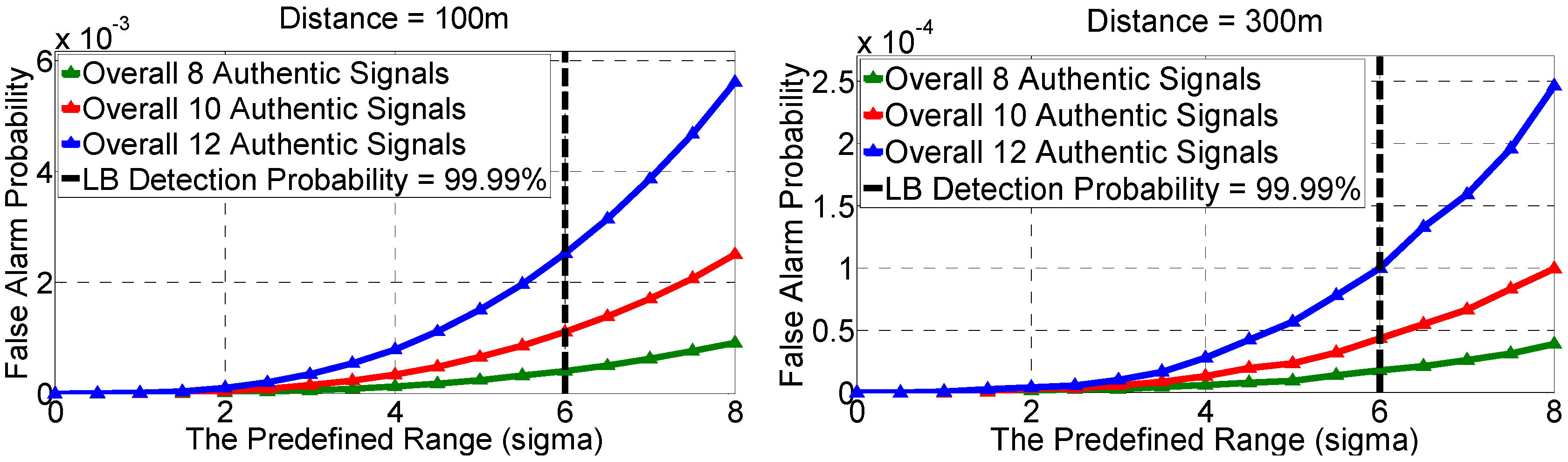
| LB Detection Probability | 99.00% | 99.90% | 99.99% |
|---|---|---|---|
| Minimum R |
| Number of Authentic Signals = 8 | 10 | 12 | |
|---|---|---|---|
| Distance = 100 m | 4.0 × 10−4 | 1.1 × 10−3 | 2.5 × 10−3 |
| Distance = 300 m | 1.8 × 10−5 | 4.3 × 10−5 | 1.0 × 10−4 |
| Spoofing: | 14,16,25,27,29,30,31,32 |
| Authentic: | 06,12,14,17,22,24,25,32 |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, Z.; Zhan, X. GNSS Spoofing Network Monitoring Based on Differential Pseudorange. Sensors 2016, 16, 1771. https://doi.org/10.3390/s16101771
Zhang Z, Zhan X. GNSS Spoofing Network Monitoring Based on Differential Pseudorange. Sensors. 2016; 16(10):1771. https://doi.org/10.3390/s16101771
Chicago/Turabian StyleZhang, Zhenjun, and Xingqun Zhan. 2016. "GNSS Spoofing Network Monitoring Based on Differential Pseudorange" Sensors 16, no. 10: 1771. https://doi.org/10.3390/s16101771
APA StyleZhang, Z., & Zhan, X. (2016). GNSS Spoofing Network Monitoring Based on Differential Pseudorange. Sensors, 16(10), 1771. https://doi.org/10.3390/s16101771






