Coded Cooperation for Multiway Relaying in Wireless Sensor Networks †
Abstract
: Wireless sensor networks have been considered as an enabling technology for constructing smart cities. One important feature of wireless sensor networks is that the sensor nodes collaborate in some manner for communications. In this manuscript, we focus on the model of multiway relaying with full data exchange where each user wants to transmit and receive data to and from all other users in the network. We derive the capacity region for this specific model and propose a coding strategy through coset encoding. To obtain good performance with practical codes, we choose spatially-coupled LDPC (SC-LDPC) codes for the coded cooperation. In particular, for the message broadcasting from the relay, we construct multi-edge-type (MET) SC-LDPC codes by repeatedly applying coset encoding. Due to the capacity-achieving property of the SC-LDPC codes, we prove that the capacity region can theoretically be achieved by the proposed MET SC-LDPC codes. Numerical results with finite node degrees are provided, which show that the achievable rates approach the boundary of the capacity region in both binary erasure channels and additive white Gaussian channels.1. Introduction
Wireless sensor networks (WSNs) consist of spatially-distributed autonomous sensors which cooperatively monitor physical or environmental conditions, and they have been identified as one of the most important enabling technologies for constructing smart cities. The rapid development of portable and wearable devices has further fueled the application of sensor networks, which helps to improve the city's sustainable growth and citizens' living quality.
One important feature of WSNs is that the sensor nodes collaborate in some manner for information transmissions. Much of research on the physical-layer techniques has focused on relaying, which is an efficient cooperative strategy to improve throughput and coverage of the sensor network. The three-node relay channel [1], consisting of one source, one relay and one destination, serves as the fundamental unit of large networks. The two-way relaying, also known as bidirectional relaying [2], is another type of cooperative strategy. By exploiting bidirectional communication, the loss in spectral efficiency due to the half-duplex restriction in conventional relaying is reduced. As a generalization of the two-way relay channel, the multiway relay channel (mRC) has been investigated in [3]. In the mRC, multiple users exchange information with the help of a relay terminal. The mRC setup models a large variety of communication scenarios. For example, in a physical sensor network, temperature sensors exchange local temperature measurements among themselves. Similarly, in a social network, different users exchange their personal information through a coordinator.
In this manuscript, we are interested in a typical scenario which is called the multiway relay channel with full data exchange in [3] or the conferencing multiway channel in [4]. A practical example of this model is as follows. Each member of an emergency response team is equipped with a wireless device at a disaster site, and they may obtain valuable information at random times. All of the members, including one leader, need to share their messages with the others. Each member wants to transmit and receive data to and from all other responders, coordinated by the leader who acts as the relay. The above information exchange can be realized in two steps. First, since the members may initiate their transmissions asynchronously, each member is scheduled to transmit his or her message to the leader in a time-division manner. During this procedure, the message in the air may be overheard by other members. After successfully receiving all of the messages, the leader (relay) then encodes all of these messages together with his or her message and broadcasts the resulting codeword to all of the members. At each member's side, different and potentially partly overlapping a priori information is available for decoding the codeword from the relay. Eventually, all of the members in the team are supposed to obtain the messages from all of the others. Since the information delivery in the first phase is essentially a peer-to-peer communication, in this manuscript, we focus on the second phase in which the relay broadcasts the messages to all of the members.
The capacity region for the general multi-user broadcast channel is not known yet. In [5,6], the authors provided the capacity region for the bidirectional broadcast channel with a common and/or private message. The multiway relay channel with full data exchange as we described above can be considered as a generalization of the model in [6]. In this manuscript, we derive the capacity region for the multiway relay case. The capacity region establishes the fundamental limits of the transmission rate and provides guidelines for the code design. On top of this, we propose a coding strategy through coset encoding for broadcasting with receiver side information. The coding strategy is illustrated by using low-density parity-check codes [7]. However, in practice, the regular LDPC codes cannot provide satisfactory performance, while irregular LDPC codes suffer from the complicated optimization of the degree distribution [8]. Therefore, it is of interest to search for code constructions with a good performance and a low optimization overhead. Different designs can be found for various channel models in the literature based on Turbo codes [9,10], LDPC codes [11-13], Polar codes [14], etc.
The spatially-coupled LDPC (SC-LDPC) codes are good candidate for the cooperative code construction. Spatially-coupled LDPC codes were first introduced in [15] as a time-varying convolutional-like LDPC code family. Then, the idea was further developed in, e.g., [16-18], where different constructions and analytical results were provided. It has been proven analytically in [18,19] that the belief-propagation (BP) decoding threshold of a spatially-coupled LDPC code ensemble achieves the maximum a posteriori probability (MAP) threshold of the underlying LDPC block code. This code, in turn, approaches capacity as the node degrees increase. In addition to the capacity-achieving performance for various channels, the regularity of the SC-LDPC code allows us to avoid complicated re-optimization of the degree distributions for varying channel conditions. Meanwhile, this code enables recursive encoding and sliding-window decoding [20], which dispels the concerns about hardware complexity and delay. Motivated by these useful properties, spatially-coupled LDPC codes have been considered for applications in a variety of scenarios.
In this manuscript, we propose to use spatially-coupled LDPC codes for the cooperative channel coding in the mRC. To realize the proposed coding strategy by using SC-LDPC codes, we replace the LDPC codes with their spatially-coupled counterparts. The multi-edge-type (MET) [21] nested spatially-coupled LDPC codes are constructed by repeatedly applying the coset encoding [22]. If setting the node degree the same for all types of check nodes, the MET nested SC-LDPC codes present useful properties. Any combination of the nesting leads to a capacity-achieving SC-LDPC code, regardless of the number of edge types and the order of adding the edges. This property is beneficial for the model under discussion. We then prove that by using the MET nested SC-LDPC code, the capacity region of the channel model is achieved. Numerical results with finite node degrees are provided, which show that the achievable rates approach the boundary of the capacity region in both binary erasure channels (BECs) and binary-input additive white Gaussian channels (BI-AWGNs).
The remainder of the manuscript is organized as follows. The system model is introduced in Section 2. In Section 3, we derive the capacity region of the specific model. The coding strategy is illustrated in Section 4 through multi-edge-type LDPC codes. Based on the multi-edge-type construction, the MET spatially-coupled LDPC codes are proposed in Section 5. In Section 6, we apply the MET SC-LDPC codes to the multiway relay channel and prove that the capacity region can be achieved. The numerical results are provided in Section 7 to verify the theoretical analysis. Finally, Section 8 concludes the manuscript.
2. System Model
2.1. The Two-Way Relay Channel
We first use a special case, the two-way relay channel, to illustrate the system model. We assume that there are three users U0, U1 and U2 in the network, and they have individual messages m0, m1 and m2 to share with the others. Without loss of generality, we choose user U0 to act as the relay. In the first phase, the users U1 and U2 transmit their messages m1 and m2, respectively, in turn to the relay node U0. We assume that both messages are received successfully by U0. In the second phase, i.e., the broadcast phase, the relay U0 transmits a codeword to both U1 and U2. The goal of the transmission from U0 is to convey the messages m0, m1 and m2 efficiently, so that U1 is able to reliably decode the messages m0 and m2 and U2 is able to reliably decode the messages m0 and m1. Eventually, all three users share the three messages in the network. The channel model is illustrated in Figure 1. This model is recognized as the two-way relay channel with a common message in [6].
2.2. The Multiway Relay Channel with Full Data Exchange
In the following, we extend the model to the multiway relay channel with full data exchange. We assume that a number of K users {U0, U1, …,Ul, … Uk– 1 } form a network. Each user Ul has an individual message ml to share with the others, for 0 ≤ l ≤ K ‒ 1. One of the users, for example U0, is assigned as the relay node. In the first phase, all of the users, except the relay U0, send out their messages in a time-division manner. During this procedure, each message ml, 1 ≤ l ≤ K – 1, is successfully received by the relay and may be received by other users. In the second phase, the relay U0 has the task of broadcasting a set of messages



In Figure 2, we give a simple example of the above multiway relay channel. The example system consists of four users, and one of them is selected as the relay. In the first round of transmission, the message m1 from U1 is successfully received by both the relay and the user U2. The message m2 from U2 is successfully received by the relay and the user U3. The message m3 is only correctly received at the relay Each user can use the messages he has overheard together with his own message as the side information for decoding. That is, U1 has only his own message m1 as the side information. U2 has m1 and m2 as the a priori information, and U3 has m2 and m3 as the a priori information for the decoding. In the end of the first phase, each user informs the relay about what side information he has. This can be realized at each user by sending the indexes of his received messages to the relay. The number of bits needed to represent the index of one message is ⌈log2(K − 1)⌉, where K is the number of users. The total number of bits for each user to send the knowledge of available information is at most (K ‒ 2) ⌈log2(K − 1)⌉. For the example in Figure 2, each user only needs four bits. Comparing to the length of the messages, the resulting overhead and latency are negligible. In the broadcast phase, the relay delivers the missing messages to each user, i.e., {m0,m2,m3} to U1, {m0,m3} to U2 and {m0,m1} to U3. The challenge for the relay is then how to realize the information broadcasting efficiently and reliably.
3. Capacity Region
The capacity region for the two-way relay channel with a common message has been proved in [6]. Let R0, R1 and R2 be the encoding rates of the messages m0, m1 and m2, and let the capacities of the links to U1 and U2 be C1 and C2, respectively. The capacity region of the above model is then given by the set of triples (R0, R1, R2) that satisfies [6,14]:
In the multiway broadcast channel that we described in Section 2.2, each user requests all of the messages he has missed from

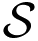
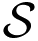

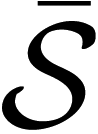
Theorem 1. We assume that Cl is the channel capacity of the link between the relay and the user Ul, for all l ∈ {1, 2,…, K – 1}. We let Rl denote the encoding rate of the message ml and R0 denote the encoding rate of the message m0 from the relay. The capacity region of the multiway relay channel with full data exchange is the set of all achievable rates that satisfies:
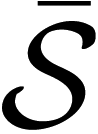 ⊇
⊇
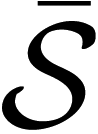 , for any l, k ∈ {1, 2, …,K−1}.
, for any l, k ∈ {1, 2, …,K−1}.Proof. Without loss of generality, we use the link between the relay and the user Ul (1 ≤ l ≤ K ‒ 1) to discuss the converse and the achievability of the capacity region. We assume that the messages are encoded by a length-n codeword X, and the channel observation at Ul is Yl.
First, the entropy can be bounded similarly as has been done in [6], where a two-user case was considered.
Equations (a) and (b) are obtained from the independence of the messages and the definition of mutual information. Inequation (c) has been proven in [6]. Inequations (d) and (e) are based on the properties of mutual information.
Dividing both sides by n and using the memoryless property, we get:
Since εl → 0 when n → ∞, we have the achievable rate on the relay-Ul link:
The above proves the converse of the capacity region. The achievability of the capacity region can be done similarly as for the two-user case. Since we will prove in the remainder of the manuscript that the capacity region can be achieved by using the proposed code structure, we omit the proof of achievability here.
For the example in Figure 2, the capacity region is given as:
4. Multi-Edge-Type LDPC Codes and the Coding Strategy
4.1. Low-Density Parity-Check Codes
As the name suggests, LDPC codes are block codes with parity-check matrices which contain only a small proportion of non-zero entries. An LDPC code can be represented by a parity-check matrix or a Tanner graph.
A parity-check matrix H with elements in GF(2) defines the codeword constraints in a matrix form. For a binary code with k parity-check equations and with codeword length n, the matrix H is of size k × n. A vector X = [X1, X2, …, Xn] is a codeword of the LDPC code defined by H if and only if the following constraint is satisfied:
In the following, we use


Tanner introduced an effective graphical representation for LDPC codes [23]. In a bipartite Tanner graph, the nodes are separated into two distinctive sets: variable nodes for the codeword bits and check nodes for the parity-check equations. An edge connects a variable node to a check node if that codeword bit is included in the parity-check equation.
As originally defined by Gallager, a (dv, dc) regular LDPC code is determined by the condition that every codeword bit participates in exactly dv parity-check equations and that every parity-check equation involves exactly dc codeword bits. The parameter dv is called the variable node degree, and dc is the check node degree.
Since each parity-check equation typically reduces the number of degrees of freedom by one, it follows that the design rate of the (dv, dc) regular LDPC code is:
4.2. Binning and Coset Coding
One of the basic elements of network information theory is the idea of binning [24]. A binning scheme divides a set of codewords into subsets (“bins”), such that the codewords in each subset are as far apart as possible. In [24], random binning was used to prove the Slepian-Wolf source coding theorem. In [25], Cover and El Gamal proposed to use random binning for set partitioning in decode-and-forward relaying.
The random binning approach is convenient for theoretical analysis; however, it is not suitable for practical applications. Therefore, binning schemes with a structure were proposed. Wyner constructed an algebraic binning scheme for noiseless coding problems in [26]. In order to extend the idea to “noisy” coding problems, the structure of nested codes was proposed [27].
We first introduce the concept of coset. Let an LDPC code



A nested code [27] is a pair of linear codes (


That is, each codeword of


The nested parity-check codes can be constructed as follows [27]. Let H1 and H2 be parity-check matrices of dimension k1×n and of dimension k2 × n, respectively, k2 > k1. By bringing in an additional parity-check matrix ΔH of dimension (k2 – k1) × n, the nested codes can be realized by:
We can then partition


4.3. MET Nested LDPC Codes
Multi-edge-type LDPC codes [21] can be considered as a generalization of regular and irregular LDPC codes. For an MET LDPC ensemble, there are multiple equivalence classes of edges, while for a conventional LDPC ensemble, there exists a single type of edge. In the following, we introduce multi-edge-type LDPC codes constructed by coset encoding.
An MET nested LDPC code can be illustrated by the Tanner graph in Figure 3. The bit vector associated with the variable nodes V, i.e., the codeword, is denoted by X. There are K types of check nodes in the graph, C0, C1, …, Cl …, Ck−1. The parity-check matrices, which correspond to the K types of edges connecting the variable nodes and the different types of check nodes, are denoted by H0, H1, …, Hl, …, Hk-1, and have variable and check node degrees (dv0, dc0), (dv1, dc1), …, (dvl, dcl), …, (dvk−1, dck−1), respectively. The MET nested LDPC code can be described by the stacked parity-check matrix H, and we have:
Definition 2. (The multi-edge-type nested LDPC code ensemble) A multi-edge-type nested LDPC ensemble includes all of the bipartite graphs where each variable node is connected to dvl type-l check nodes, and each of the type-l check nodes has dCl edges connecting to the variable nodes, for all l ∈ [0, K − 1].
4.4. Coding Strategy for Multiway Relaying
Based on the nested LDPC codes, in the following, we illustrate the coding strategy for the multiway relay channel with full data exchange. Since the first phase is in fact a peer-to-peer transmission, we focus particularly on the transmission strategy in the broadcast phase. We start with the case of two users and one relay. We assume that the binary messages m0, m1, and m2 are of lengths k0, k1 and k2 bits. To combine the three messages in a single transmission, the relay uses a double binning strategy: a high-rate code of length n is split into 2nR1 × 2nR2 disjoint sub-codes



Once the Tanner graph of an MET nested LDPC code is given or, equivalently, the parity-check matrices H0, H1, and H2 are given, the encoding can be carried out by mapping the message m0 into a codeword which simultaneously satisfies the check constraints (3).
If dC0 = dC1 = dC2 ≡ dc, the rate for encoding m0 is:
The decoding at each user is carried out as follows. Since U1 has perfect knowledge of m1, he interprets X as a codeword of a two-edge-type nested LDPC code and uses:
The above coding strategy can be easily extended to the multi-user case. A multiple binning technique is utilized to combine all of the messages in a single transmission. For the general case, the encoding can be realized by selecting a codeword X that satisfies:
When decoding, each user utilizes the side information available at the receiver. We assume that the indexes of the available messages at Ul form a vector vl of length Pl. Then, the decoding of the codeword X (the message m0) at Ul is carried out by satisfying:
As for the two-user case, the other messages designated to Ul can be recovered by using the decoded X and sub-parity-check equations in Equation (7).
We again have a look at the example in Figure 2. The encoding can be realized by selecting a codeword X that satisfies that:
The decoding is carried out by satisfying:
In the above, we have illustrated the coding strategy using LDPC codes. In general, the regular LDPC codes suffer from poor performance. The performance can be improved by introducing irregularity to the node degrees. However, an irregular degree distribution needs to be derived to match a given channel condition, which complicates the code design. Therefore, we are interested in searching for code constructions with a good performance and a low optimization overhead. The spatially-coupled LDPC codes are then good candidates for this purpose.
5. Multi-Edge-Type Spatially-Coupled LDPC Codes
In this section, we first give a brief introduction of spatially-coupled LDPC codes. Then, we introduce the construction of multi-edge-type nested SC-LDPC codes. The property of the proposed codes is analyzed. We will show that any N-edge-type nested SC-LDPC code embedded in the MET structure is capacity achieving.
5.1. Spatially-Coupled LDPC Codes
A regular {dv,dc} binary spatially-coupled LDPC code can be defined by an infinite parity-check matrix: [17]
There are many variations of spatially-coupled LDPC codes in the literature [15-18]. In this manuscript, we consider a generalized type of SC-LDPC code, which can be denoted by five parameters {dv, dc, M, L, w} [18]. We assume that each of the dv edges of a variable node at position t uniformly and independently connects to the check nodes in the range [t, t + w − 1], where the parameter w is a positive integer. Ignoring the boundary effects, there are in total a number of Mdv/w edges coming from all of the variable nodes at position t − τ, τ ∈ [0, w − 1], to all of the check nodes at position t. Distributing these Mdv/w edges uniformly at random to the Mdv/dc check nodes at position t, for each check node, each edge is connected to the variable nodes at position t − τ with probability 1/w. Therefore, each of the dc connections of a check node at position t is considered to be uniformly and independently chosen from the range [t − w + 1, t].
It has been shown analytically in [18] that, for transmission over the BEC, the BP decoding threshold of an SC-LDPC code ensemble {dv, dc, M, L, w} converges to the MAP threshold of its underlying component ensemble {dv, dc} in the limit of large M, L and w. In the remainder of this manuscript, we will use the following properties, which were derived in [18] for the BEC case: for the design rate of the code, R, we have:
For a given rate R, the Shannon limit is defined as the ultimate channel parameter threshold, below which reliable communication can be achieved by using optimal codes and optimal decoding. For the BEC, the Shannon limit is ϵsh = 1 − R. If we increase the node degrees dv and dc while keeping the ratio λ = dc/dv fixed, i.e., keeping the rate of the code fixed, the MAP threshold in Equation (11) approaches the Shannon limit,
In this sense, the SC-LDPC code ensemble is capacity achieving for the BEC. This result was generalized in [19], where it is concluded that the SC-LDPC code ensemble universally achieves capacity over binary memoryless symmetric (BMS) channels. More details of code construction and theoretical analysis can be found in [18,19] and the references therein.
5.2. MET Nested SC-LDPC Codes
Based on the standard SC-LDPC code ensemble, we construct the MET nested SC-LDPC code as follows. We assume the number of variable nodes at each position to be M; then, for a code with L positions, the codeword length is Nv = ML. The connections between the variable nodes and the K types of check nodes are characterized by {dVl, dCl, M, L, w}, for l ∈ [0, K − 1]. We set the smoothing parameter w to be the same for all of the connections. Note that only edges of the same type are connected to one check node. The connections between the variable nodes and any two types of check nodes construct a two-edge-type SC-LDPC code embedded in the MET nested code. We denote the two-edge-type SC-LDPC code with the m-th and the n-th check nodes by


Definition 3. (The N-edge-type SC-LDPC code ensemble) For a set Φ ⊆ [1, K] of cardinality N, N ∈ [1, K], the MET nested SC-LDPC code ensemble 
5.3. Properties of MET SC-LDPC Codes
In this section, we discuss the performance of the MET nested SC-LDPC codes.
We have shown in [22] that, when choosing the same check degree for both types of connections, the two-edge-type nested SC-LDPC code is equivalent to a standard SC-LDPC code in terms of design rate and BP decoding threshold. Therefore, the two-edge-type nested SC-LDPC code is able to provide capacity-achieving performance in the limit of large parameters.
In the following, we extend the discussion to the N-edge-type case. We can show that an arbitrarily-chosen N-edge-type (N ∈ [1, K]) nested SC-LDPC code ensemble


Based on the above derivation, we obtain the conclusion: if dcl = dc∀l ∈ [0,K − 1], all of the arbitrarily-chosen N-edge-type (N ∈ [1, K]) nested SC-LDPC code ensembles embedded in the MET code are simultaneously capacity achieving in the limit of large parameters.
6. MET Nested SC-LDPC Codes for the Multiway Relay Channel
In this section, we apply the MET nested SC-LDPC codes for the multiway relay channel with full data exchange. We will prove that the capacity region of the model can be achieved by using the proposed code structure.
Again, we start with the case of two users and one relay. When applying the spatially-coupled LDPC codes, the connections between the variable nodes and the three types of check nodes are characterized by {dv0, dc0, M, L, w}, {dv1, dc1, M, L, w} and {dv2, dc2, M, L, w}. We denote the MET nested SC-LDPC code ensemble by



We apply the theoretical results in Section 5.3 for the performance analysis. Following Section 5.3, the two-edge-type codes


Theorem 4. The capacity region of the two-way broadcast channel with a common message can be achieved by using an MET nested SC-LDPC code 
Proof. We assume that the capacities of the two individual links are C1 and C2, which together form the bound of the capacity region. The rate for broadcasting m0 is assumed to be R0, and R0 ≤ min(C1,C2). For constructing an MET nested SC-LDPC code, we first choose a check degree dc which is the same for all types of check nodes. With this dc, we decide the variable degrees by satisfying:
After determining the parameters, we construct an MET nested SC-LDPC code

Assume that the numbers of three types of check nodes are NC0, NC1 and NC2, respectively. The number of variable nodes is Nv. According to the definition of encoding rate in Equations (4)–(6), we have R0 = 1 − (NC0 + NC1 + NC1)/Nv, R1 = NC1/NV, and R2 = NC2/NV. The design rate of the code

Since the code

In a similar manner, for the relay- U2 link, we can prove that:
Therefore, the capacity region can be achieved by using the MET nested SC-LDPC code.
Now, we generalize to the multiway relay case. When constructing the MET nested SC-LDPC code, the connection between the variable nodes and the l-th type of check nodes is realized by the individual code {dvl, dcl, M, L, w}, l ∈ [0, K − 1]. In the following, we briefly discuss the performance of the proposed code construction in the multiway relay channel.
Theorem 5. The capacity region of the multi-user broadcast channel with full data exchange can be achieved by using multi-edge-type SC-LDPC codes.
Proof. For the given channel capacities {Cl : l ∈ [1, K − 1]} and the rate R0, we choose the node degrees by satisfying:
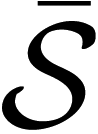 l ⊆
l ⊆
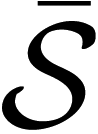 k for l, k, ∈ {1, 2, …, K − 1}.
k for l, k, ∈ {1, 2, …, K − 1}.We have shown in Section 5.3 that all of the N-edge-type nested SC-LDPC codes are simultaneously capacity achieving in the limit of large parameters. Therefore, the rate to be decoded at Ul is asymptotically:
7. Numerical Results
In this section, we present the numerical results in terms of BP decoding thresholds and bit erasure rates (BERs) for the proposed MET nested SC-LDPC codes. The results are based on the density evolution for finite node degrees and based on simulations with finite code lengths. Without loss of generality, we only include the results for the two-way relay channel. The results for the multiway relay channel present the same characteristics, and therefore, they are omitted here.
Since we have shown in Section 5.3 that both the two-edge-type nested SC-LDPC codes



We can see that the two-edge-type code

Similarly, we give the BP thresholds of SC-LDPC codes and regular LDPC block codes for BI-AWGN channels. The parameters are the same as in the BEC case, and the results are summarized in Tables 3 and 4. As for the BECs, the SC-LDPC codes clearly outperform the regular LDPC block codes in terms of the gap to the capacity
In the following, we provide the simulation results for the SC-LDPC codes with finite code lengths over BECs. The bit erasure rates are plotted in Figure 4 together with the BP thresholds of the corresponding ensembles. The node degrees (dV0, dV1, dc) are listed in the legend, and we set M = 1000 and L = 100. It can be seen that the MET SC-LDPC codes generally provide good performance over BECs. Similar observations can be obtained in BI-AWGN channels, and the results are omitted here. We also want to point out that the complexity and latency due to the encoding and decoding of SC-LDPC codes are not an issue for their applications in practice, since SC-LDPC codes allow recursive encoding and sliding-window decoding.
8. Conclusions
In this manuscript, we proposed multi-edge-type spatially-coupled LDPC codes through coset encoding for the multiway relay channel with full data exchange. This model has various applications in wireless sensor networks, and we have provided a practical coding solution for the communication aspects of the model. We have proven that an arbitrarily-chosen N-edge-type SC-LDPC code embedded in the multi-edge-type construction is capacity achieving. By applying the above code construction to the broadcast phase of the multiway relay channel, each user recovers the message from the relay and all of the other users based on the receiver side information. We have proven that the capacity region of the specific model can be achieved by using the proposed construction. Numerical results were provided in both binary erasure channels and AWGN channels, which verified the theoretical analysis.
Acknowledgements
This work was supported in part by the National Natural Science Foundation of China (No. 61401037), the Fundamental Research Funds for the Central Universities (No. 2014RC0102, No. 2014ZD03-01) and the Sweden STINT initiation grant (Dnr. IB2015-5959).
The authors would like to thank the editors and the anonymous reviewers for their valuable comments and suggestions.
Conflicts of Interest
The authors declare no conflict of interest.
Author Contributions
Zhongwei Si and Ragnar Thobaben developed the proposal of the study for the model of bidirectional relaying with a common message. Zhongwei Si and Junyang Ma extended the study to the multiway relay channel with full data exchange. Zhongwei Si carried out the simulations and took care of most of the writing. Junyang Ma and Ragnar Thobaben made corrections of the manuscript. All authors have participated in the discussions and did a general review of the manuscript.
References
- Var der Meulen, E.C. Three-terminal communication channels. Adv. Appl. Probab. 1971, 3, 120–154. [Google Scholar]
- Oechtering, T.J.; Schnurr, C.; Bjelakovic, I.; Boche, H. Broadcast Capacity Region of Two-Phase Bidirectional Relaying. IEEE Trans. Inf. Theory 2008, 54, 454–458. [Google Scholar]
- Gunduz, D.; Yener, A.; Goldsmith, A.; Poor, H.V. The Multiway Relay Channel. IEEE Trans. Inf. Theory 2013, 59, 51–63. [Google Scholar]
- Eswaran, K.; Gastpar, M. Achievable rates for conferencing multiway channels. Proceedings of the IEEE International Symposium on Information Theory, Toronto, ON, Canada, Canada, 6–11 July 2008; pp. 1398–1402.
- Oechtering, T.J.; Boche, H. Piggyback a common message on half-duplex bidirectional relaying. IEEE Trans. Wirel. Commun. 2008, 7, 3397–3406. [Google Scholar]
- Wyrembelski, R.F.; Boche, H. Bidirectional broadcast channels with common and confidential messages. Proceedings of the IEEE Information Theory Workshop, Paraty, Brazil, 16–20 October 2011; pp. 713–717.
- Gallager, R.G. Low Density Parity Check Codes; MIT Press: Cambridge, MA, USA, 1963. [Google Scholar]
- Richardson, T.; Urbanke, R. Model Coding Theory; Cambridge University Press: Cambridge, UK, 2008. [Google Scholar]
- Zhao, B.; Valenti, M.C. Distributed Turbo coded diversity for relay channel. Electron. Lett. 2003, 39, 786–787. [Google Scholar]
- Roy, S.; Duman, T.M. Performance Bounds for Turbo Coded Half Duplex Relay Systems. Proceedings of the IEEE International Conference on Communications, Istanbul, Turkey, 11–15 June 2006; pp. 1586–1591.
- Chakrabarti, A.; de Baynast, A.; Sabharwal, A.; Aazhang, B. Low density parity check codes for the relay channel. IEEE J. Sel. Areas Commun. 2007, 25, 280–291. [Google Scholar]
- Hu, J.; Duman, T.M. Low Density Parity Check Codes over Wireless Relay Channels. IEEE Trans. Wirel. Commun. 2007, 6, 3384–3394. [Google Scholar]
- Azmi, M.H.; Li, J.; Yuan, J.; Malaney, R. Design of Distributed Multi-Edge Type LDPC Codes for Two-Way Relay Channels. In. Proceedings of the IEEE International Conference on Communications, Kyoto, Japan, 5–9 June 2011; pp. 1–5.
- Andersson, M.; Wyrembelski, R.F.; Oechtering, T.J.; Skoglund, M. Polar codes for bidirectional broadcast channels with common and confidential messages. Proceedings of the IEEE International Symposium on Wireless Communication Systems, Paris, France, 28–31 August 2012; pp. 1014–1018.
- Felstrom, A.J.; Zigangirov, K.S. Time-varying periodic convolutional codes with low-density parity-check matrix. IEEE Trans. Inf. Theory 1999, 45, 2181–2191. [Google Scholar]
- Pusane, A.E.; Felström, A.J.; Sridharan, A.; Lentmaier, M.; Zigangirov, K.S.; Costello, D.J. Implementation aspects of LDPC convolutional codes. IEEE Trans. Commun. 2008, 56, 1060–1069. [Google Scholar]
- Lentmaier, M.; Sridharan, A.; Costello, D.J.; Zigangirov, K.S. Iterative decoding threshold analysis for LDPC convolutional codes. IEEE Trans. Inf. Theory 2010, 56, 5274–5289. [Google Scholar]
- Kudekar, S.; Richardson, T.; Urbanke, R. Threshold saturation via spatial coupling: Why convolutional LDPC ensembles perform so well over the BEC. IEEE Trans. Inf. Theory 2011, 57, 803–834. [Google Scholar]
- Kudekar, S.; Richardson, T.; Urbanke, R. Spatially coupled ensembles universally achieve capacity under belief propagation. Proceedings of the IEEE International Symposium on Information Theory, Cambridge, MA, USA, 1–6 July 2012; pp. 453–457.
- Iyengar, A.R.; Papaleo, M.; Siegel, P.H.; Wolf, J.K.; Vanelli-Coralli, A.; Corazza, G.E. Windowed decoding of protograph-based LDPC convolutional codes over erasure channels. IEEE Trans. Inf. Theory 2012, 58, 2303–2320. [Google Scholar]
- Richardson, T.; Urbanke, R. Multi-Edge Type LDPC Codes. Available online: http://www.researchgate.net/publication/37439748_Multi-Edge_Type_LDPC_Codes (accessed on 25 Jun 2015).
- Si, Z.; Thobaben, R.; Skoglund, M.; Oechtering, T.J. Bidirectional broadcasting by using multi-edge type LDPC convolutional codes. Proceedings of the IEEE International Symposium on Turbo Codes and Iterative Information Processing; pp. 91–95.
- Tanner, R.M. A recursive approach to low complexity codes. IEEE Trans. Inf. Theory 1981, 27, 533–547. [Google Scholar]
- Slepian, D.; Wolf, J. Noiseless coding of correlated information sources. IEEE Trans. Inf. Theory 1973, 19, 471–480. [Google Scholar]
- Cover, T.; El Gamal, A. Capacity theorems for the relay channel. IEEE Trans. Inf. Theory 1979, 25, 572–584. [Google Scholar]
- Wyner, A. Recent results in the Shannon theory. IEEE Trans. Inf. Theory 1974, 20, 2–10. [Google Scholar]
- Zamir, R.; Shamai, S.; Erez, U. Nested linear/lattice codes for structured multiterminal binning. IEEE Trans. Inf. Theory 2002, 48, 1250–1276. [Google Scholar]




| (dv0, dv1) | Design Rate | Shannon Limit ϵSh | BP Threshold ϵBP | Gap |
|---|---|---|---|---|
| (3,1) | 0.5921 | 0.4079 | 0.3970 | 0.0109 |
| (3,2) | 0.4902 | 0.5098 | 0.4989 | 0.0109 |
| (3,3) | 0.3882 | 0.6118 | 0.5961 | 0.0157 |
| (3,4) | 0.2862 | 0.7138 | 0.6861 | 0.0277 |
| (3,5) | 0.1883 | 0.8157 | 0.7654 | 0.0503 |
| (3,6) | 0.0823 | 0.9177 | 0.8328 | 0.0849 |
| (dv0, dv1) | Design Rate | Shannon Limit ϵSh | BP Threshold ϵBP | Gap |
|---|---|---|---|---|
| (3,1) | 0.6 | 0.4 | 0.3079 | 0.0921 |
| (3,2) | 0.5 | 0.5 | 0.3415 | 0.1585 |
| (3,3) | 0.4 | 0.6 | 0.3656 | 0.2344 |
| (3,4) | 0.3 | 0.7 | 0.3840 | 0.3160 |
| (3,5) | 0.2 | 0.8 | 0.3990 | 0.4010 |
| (3,6) | 0.1 | 0.9 | 0.4115 | 0.4885 |
| (dv0, dv1) | Design Rate | Shannon Limit ϵSh | BP Threshold ϵBP | Gap |
|---|---|---|---|---|
| (3,1) | 0.5921 | 0.854 | 0.836 | 0.018 |
| (3,2) | 0.4902 | 0.994 | 0.976 | 0.018 |
| (3,3) | 0.3882 | 1.173 | 1.143 | 0.030 |
| (3,4) | 0.2862 | 1.427 | 1.355 | 0.072 |
| (3,5) | 0.1883 | 1.829 | 1.630 | 0.199 |
| (3,6) | 0.0823 | 2.751 | 1.998 | 0.753 |
| (dv0, dv1) | Design Rate | Shannon Limit ∈Sh | BP Threshold ∈BP | Gap |
|---|---|---|---|---|
| (3,1) | 0.6 | 0.844 | 0.748 | 0.096 |
| (3,2) | 0.5 | 0.979 | 0.793 | 0.186 |
| (3,3) | 0.4 | 1.149 | 0.827 | 0.322 |
| (3,4) | 0.3 | 1.386 | 0.853 | 0.533 |
| (3,5) | 0.2 | 1.767 | 0.875 | 0.892 |
| (3,6) | 0.1 | 2.552 | 0.894 | 1.658 |
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Si, Z.; Ma, J.; Thobaben, R. Coded Cooperation for Multiway Relaying in Wireless Sensor Networks. Sensors 2015, 15, 15265-15284. https://doi.org/10.3390/s150715265
Si Z, Ma J, Thobaben R. Coded Cooperation for Multiway Relaying in Wireless Sensor Networks. Sensors. 2015; 15(7):15265-15284. https://doi.org/10.3390/s150715265
Chicago/Turabian StyleSi, Zhongwei, Junyang Ma, and Ragnar Thobaben. 2015. "Coded Cooperation for Multiway Relaying in Wireless Sensor Networks" Sensors 15, no. 7: 15265-15284. https://doi.org/10.3390/s150715265
APA StyleSi, Z., Ma, J., & Thobaben, R. (2015). Coded Cooperation for Multiway Relaying in Wireless Sensor Networks. Sensors, 15(7), 15265-15284. https://doi.org/10.3390/s150715265





