PHACK: An Efficient Scheme for Selective Forwarding Attack Detection in WSNs
Abstract
:1. Introduction
- (1)
- The PHACK scheme proposed in this paper has better ability for detecting and identifying suspect nodes. In the PHACK scheme, each intermediate node along a forwarding path is responsible for generating acknowledgements (ACK) to the source node for each packet received. The difference from previous research is that each confirmation is routed to the sink along a different path. One benefit is that the probability of the confirmation information reaching the sink successfully can be improved, as this approach can avoid the risk of a single routing failure for the case in which all ACK packets are returned to the source node along the same data forwarding path as in previous work; additionally, because each acknowledgement is independently routed along different paths, this scheme has a higher ability for detecting and identifying suspect nodes [3,4,5]. Though the acknowledgement can be returned by each intermediate node in this scheme, the network lifetime was not affected in comparison to other schemes. This is because, in the process of data collection in a wireless sensor network, the nodes near the sink consume more energy due to the increased amount of data that can be forwarded to the sink from the nodes far from the sink, called hotspots. After the premature death of nodes near the sink area forms an energy hole, the data from nodes in the distance cannot be routed to the sink, which causes the entire network to die in advance [8], with more than 90% of the total energy being unable to be used [12]. This means that if the residual energy can be used effectively, it not only does not affect the network lifetime but also can improve the ability for detecting the selective forwarding attack. Theoretical analysis has proved that although the PHACK scheme increases the energy consumption in the peripheral area, it does not increase the energy consumption in hotspot areas, so the network lifetime in the PHACK scheme is not less than that of other acknowledgement-based schemes, but the performance can be improved significantly with regard to the detection accuracy and effectiveness.
- (2)
- Second, the PHACK scheme can not only effectively detect the selective forwarding attack, but it also has the ability to recover from routing failure, as the attacked data can be rerouted to the sink rapidly along an alternative routing path that excludes the suspect nodes. In the previous research, most of the selective forwarding attack detection schemes only have a detection function. In the PHACK scheme, suspect nodes can be accurately identified, and thus the dropped data can be rerouted from the nodes nearest to the sink to the sink along a routing path that bypasses the suspect nodes; this leads to the quick recovery of the routing data at the lowest cost.
- (3)
- The performance of the PHACK scheme has been proved through theory analysis and extensive simulation results via Omnet++. The validity of this scheme can be confirmed by the experimental results. In the contrast experiment, the detection probability and the veracity of the identification of suspect nodes are better than in previous studies.
2. Related Work
- (1)
- Early schemes did not detect whether there is an SFA, but rather adopted multiple routes to ensure that the data reaches the sink at a higher probability when the network is attacked [3,13]. This is effective for most attacks that prevent data from being transmitted to the sink [3,13]. However, this scheme does not detect whether an SFA exists and also does not have the ability to identify malicious nodes [3,13]. At the same time, the communication overhead and energy consumption are huge, as they are proportional to the number of paths. Karlof et al. [13] firstly discuss the selective forwarding attack and also suggest that multi-path routing can be used to counter these types of attacks.
- (2)
- Subsequent schemes can detect whether there an SFA exists, but cannot identify malicious nodes. The main point of this type of scheme is to detect whether an SFA exists in the process of data transmission; once an SFA is identified in the process, the scheme sends a warning message to the system. However, this type of scheme does not have the ability to identify malicious nodes [3]. Sun et al. [14] proposed a multi-dataflow topology (MDT) method to countermeasure the selective forwarding attacks. In an MDT, if there is a malicious node in a dataflow, the data can be routed to the sink successfully if there is a safely routed path in another dataflow topology. However, the deficiencies in this type of scheme are that: (a) the ability of this scheme to resist attacks is limited [3], and the scheme does not have the ability to identify compromised nodes; and (b) the energy consumption is larger, several times that of a single dataflow topology method [3].
- (3)
- The scheme not only can detect whether there is an SFA but also can identify malicious nodes. The main point is to first detect whether there is an SFA in the network; if there is, the scheme identifies the malicious nodes by adopting an ACK-based mechanism. Then, some action will be adopted to eliminate the malicious nodes. Xiao, Yu et al. [5] have proposed a CHEMAS (checkpoint-based multi-hop acknowledgement scheme) to defend against SFA, and its details can be found in Section 4.1.
3. The System Model
3.1. The Network Model
- (1)
- We consider a wireless sensor network consisting of a large number of sensor nodes that are uniformly and randomly scattered in a circle network; the network radius is R, with the density of nodes equal to ρ, and nodes do not move after being deployed [15,16,17,18]. On detecting an event, a sensor node will generate messages, and those messages must be transmitted to the sink node [12,13]. However, the routing method used for the data packets is determined based on the requirements of the application, such as the shortest routing approach [10,11].
- (2)
- The attacker is considered to have strong intelligence [5]. It obtains legal identification through compromising a sensor node. After that, the attacker can launch various attacks, such as dropping data packets or ACK messages or altering messages with a certain probability. The aim of attackers is to try not to expose themselves and to cause the greatest harm to the network. At the same time, the attackers can also collude to launch attacks.
- (3)
- A message authentication code is adopted in the PHACK scheme, which provides assurance to the recipient that the message came from the expected sender and has not been altered in transit [10]. Therefore, in this paper, if there are no special instructions, all packets or messages adopt the message authentication code technology. To facilitate the discussion, the contents of messages or packets can be given, and specific authentication technology can be found in [10].
3.2. Energy Consumption Model and Related Definitions
| Parameter | Value |
|---|---|
| Threshold distance (d0) (m) | 87 |
| Sensing range rs (m) | 15 |
| Eelec (nJ/bit) | 50 |
| efs (pJ/bit/m2) | 10 |
| eamp (pJ/bit/m4) | 0.0013 |
| Initial energy (J) | 0.5 |
4. The Design of the Protocol
4.1. Research Motivation

4.2. Overview of the Proposed Scheme
- (1)
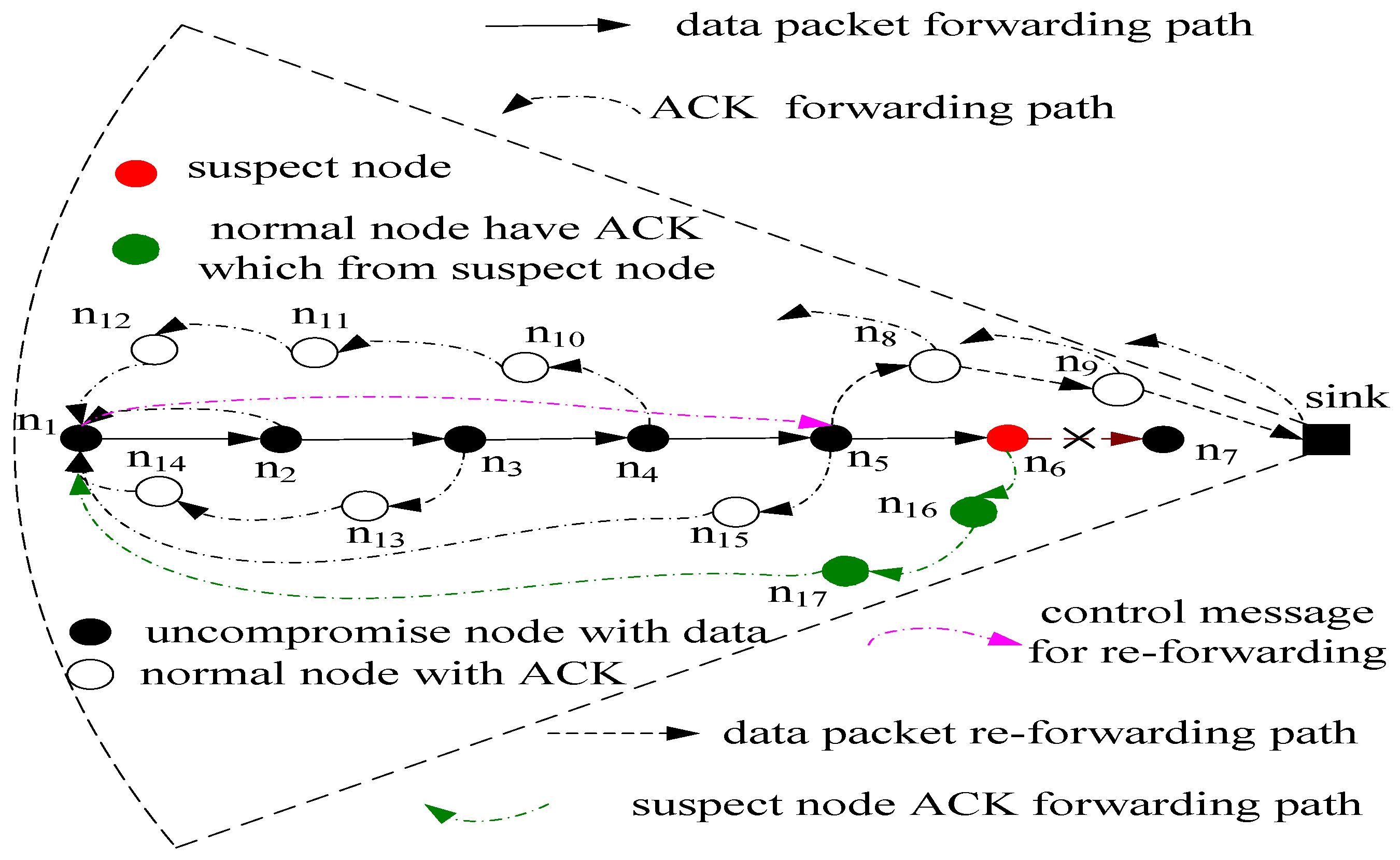
- Every node returns an ACK to the sink when receiving a data packet. The aim is to overcome the shortcoming of too few ACK messages in the previous scheme so the locations of malicious nodes can be located more accurately. This can be observed from Figure 2. The data packets are routed from the source noden1 and then are routed along the routing path of n1→n2→n3→n4→n5→n6→n7→sink; each node in this path can return an ACK to the source node when receiving a data packet.
- (2)
- The most important improvement of PHACK is that each ACK is forwarded along a routing path that is different from the original data routing path. Because each ACK is independently forwarded along a different routing path, it is difficult for malicious nodes to block these ACK packets. In the previous research studies, all the ACK messages are forwarded along the original data routing path. As long as the routing path has a malicious node, this scheme can be disabled. In the PHACK scheme, each produced ACK is forwarded along a different routing path. The ACK originating in noden3 is forwarded to the source node along noden13 and noden14 (see Figure 2). The ACK originating in node n4 is forwarded to the source node along noden10, noden11 and node n12.
- (3)
- A re-routing mechanism is used, i.e., when the data routing is blocked, the data do not need to be rerouted from the source node but instead from a normal node, that retains the data packet and is the nearest to the sink. This can be observed from Figure 2. When the source node receives an ACK from node n6 and does not receive an ACK from a node that is nearer to the sink than node n6, the source node can confirm that the data packet reached node n6. Thus, node n6 may be a malicious node. The reason for this can be explained as follows: (a) node n6 is likely a malicious node. The data packet can be dropped by noden6, but it also sends an ACK to the source node to the confused detector; (b) Node n6 is also likely a normal node. The data packet can be dropped in the following routing. However, in the PHACK scheme, the source node informs node n5 to reroute the data packet by sending control information, namely, the data packet can be rerouted along the routing path of node n5→n8→n9→sink. Compared with previous schemes, the advantage of the PHACK scheme is that the rerouted data packet does not need to be routed from the source node but instead from the node nearest to the sink, which can conserve network energy and cost. To the best of our knowledge, this is the first proposal of such a data rerouting mechanism.
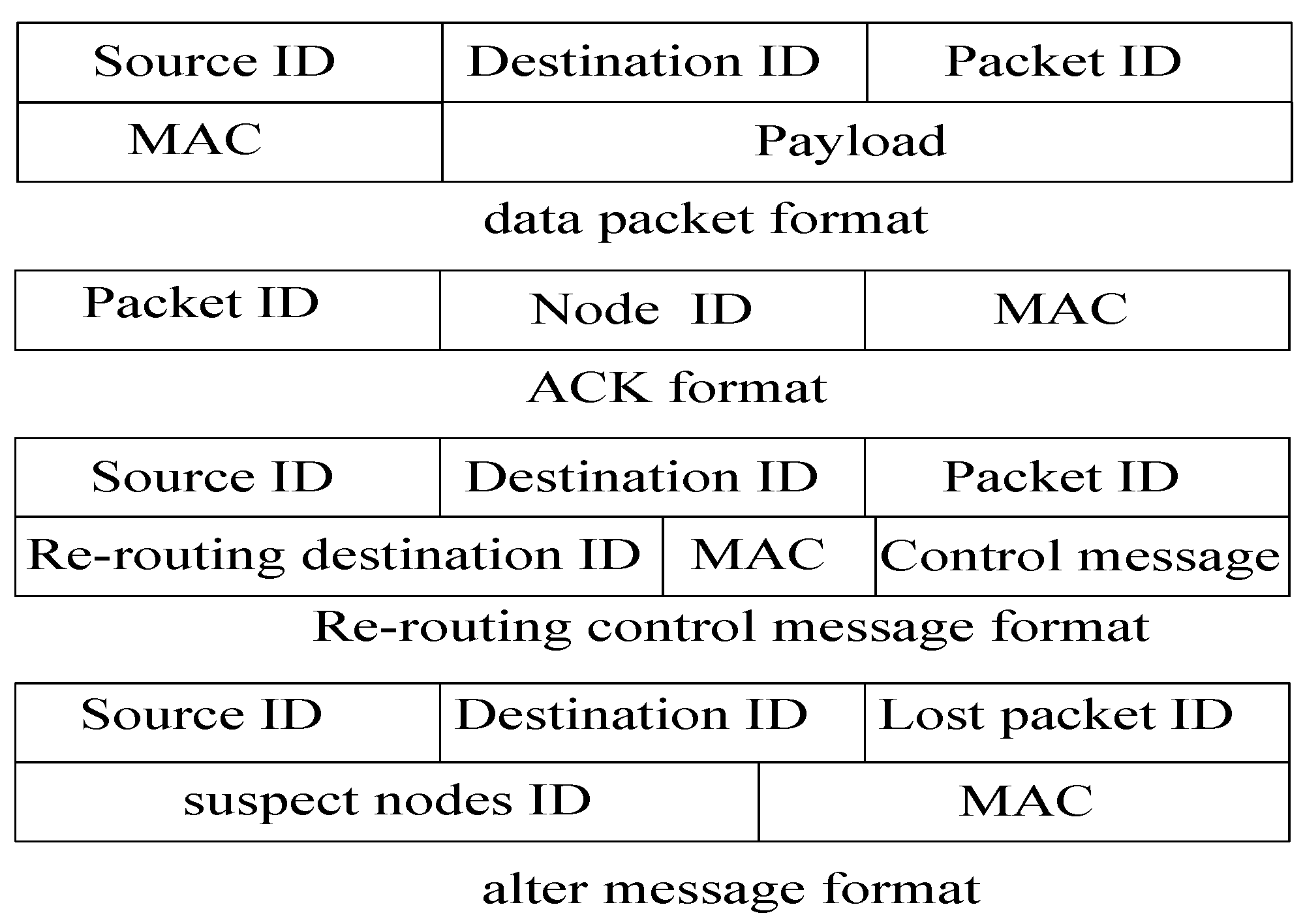
4.3. The Format of Packets and Messages
4.4. Routing in the PHACK Scheme
| Algorithm 1 The ACK Routing Mechanism |
Initialize: If node receives a data packet:
|
4.5. Identification of Suspect Nodes
5. Performance Analysis and Optimization
5.1. Energy Consumption and Network Lifetime
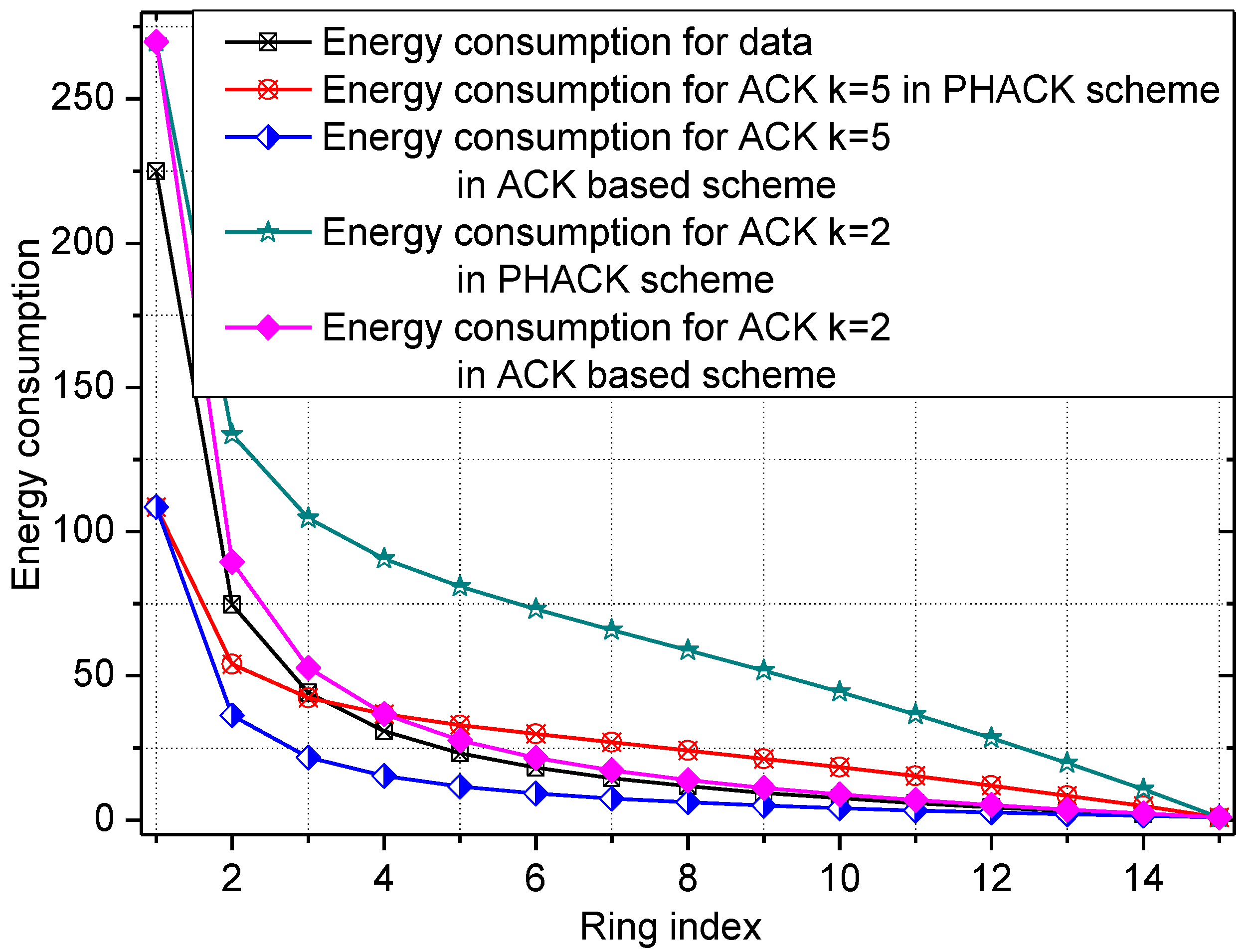

5.2. Attack Analysis
- (1)
- First, the PHACK scheme has a strong ability to resist attacks. The MAC and data ID of each node can be coded by a digital signature to form an ACK message and report whether the node received the data packet to the source node along different routing paths. Therefore, the node that only receives a data packet can send an ACK to the source node, so a malicious node can also produce an ACK packet when it receives a data packet. In the PHACK scheme, for a malicious node, there are four methods to damage the network: (a) the node does not produce an ACK packet and drops the data when receiving a data packet. In this case, the source node does not receive an ACK from this node and the following nodes, and thus this node is a suspect node. Thus, the malicious node is invalidated; (b) the node does not produce an ACK packet when receiving a data packet, but it forwards the ACK produced by other nodes to the source node. In this case, because the downstream nodes return an ACK packet to the source node when receiving a data packet, this node may be marked as a suspect node when the ACK of this node is intercepted; (c) The node returns an ACK and drops the data when receiving a data packet. Because the node is the last node to return an ACK packet to the source node, this node may also be marked as a suspect node; (d) the node returns an ACK and forwards the data packet when receiving a data packet. This type of situation is the same as that of a normal node and does not harm the network, and thus it is consistent with the aim of protecting network security.
- (2)
- In the PHACK scheme, a node cannot fabricate alert packets. In previous schemes, whether a node generates an alert packet is determined by itself. Thus, any node can generate false alert packets or fabricate alert packets. In the PHACK scheme, a node generates an alter packet under the condition that the nodes have received a data packet. Thus, the situation in which a compromised node fabricates alert packets maliciously, resulting in the prosecution of innocent normal nodes, cannot occur [5].
- (3)
- Higher success rate of data transmission. In a network with a higher percentage of malicious nodes, there may be multiple malicious nodes in the routing path. These malicious nodes may drop data and ACK data alone or work together to drop both data and ACK data. Because all the data and the ACKs are routed in the same routing path in previous schemes, this leads to the invalidation of the scheme. Though those schemes have the ability to detect an SFA in theory, they cannot meet the requirements of applications due to data being unable to arrive at the sink in time. In the PHACK scheme, each ACK is independently routed to the sink along different routing paths, even if the malicious node can block most of the ACK messages. As long as one ACK is routed to the source node successfully, it will be able to indicate the reached location of the data packet. That is to say, the probability of malicious nodes blocking the routing is reduced by several times. More importantly, a re-routing mechanism is adopted in the PHACK scheme, so the failed routing can be re-routed in the interception node. The data need not be retransmitted from the source node, therefore ensuring not only a higher success rate but also the shorter routing time.
5.3. Detection Probability Analysis
- (1)
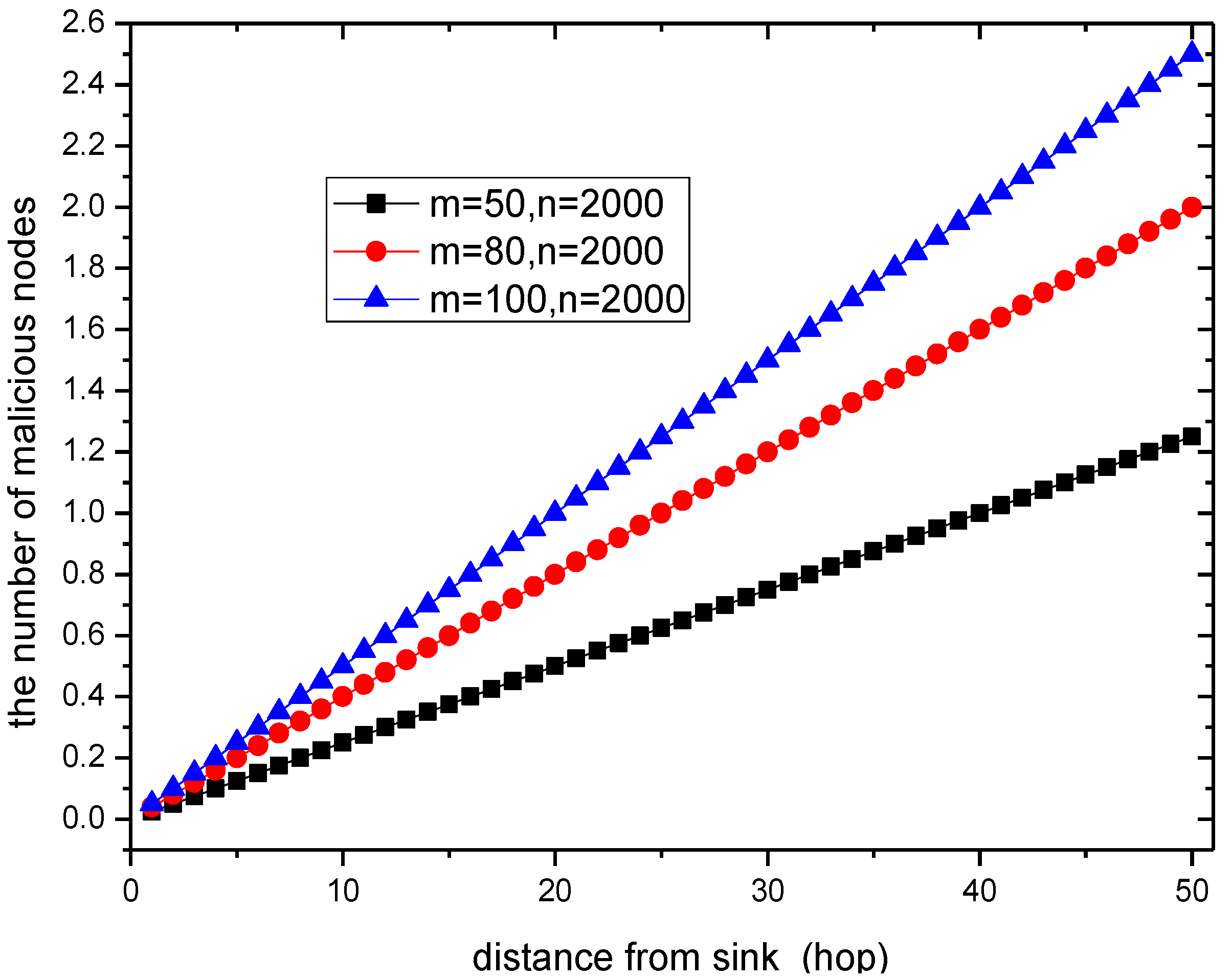
- The probability of malicious nodes dropping data. In the PHACK scheme, as long as the data packet is dropped, the source node will not receive an ACK from the sink. Thus, the dropped packet can be detected as long as it is dropped. That is to say, the probability of detecting the packet loss is 1 in PHACK. In previous schemes, if the data packet is dropped, the alter message is returned by the original path. Thus, as long as there is a malicious node in the return path, the source node will not be able to detect that the data are dropped. Considering the return path length of later messages is hops, statistically there are b = malicious nodes in that path. Considering that malicious nodes drop alter messages with a random probability of , an alter message can reach the source node if all malicious nodes refrain from dropping said alter message. The probability of the detection of dropped datain the ACK-based scheme is:
- (2)
- The probability and the number of times for data packet retransmission. It refers to the situation in which the data packet needs to be retransmitted when the source node does not receive the data packet. In the PHACK scheme, in the process of routing, as long as an ACK reaches the source node, it does not need to be retransmitted. The probability for this situation is: . However, in the ACK-based scheme, the probability is . Thus, the probability in the PHACK scheme is reduced by times.
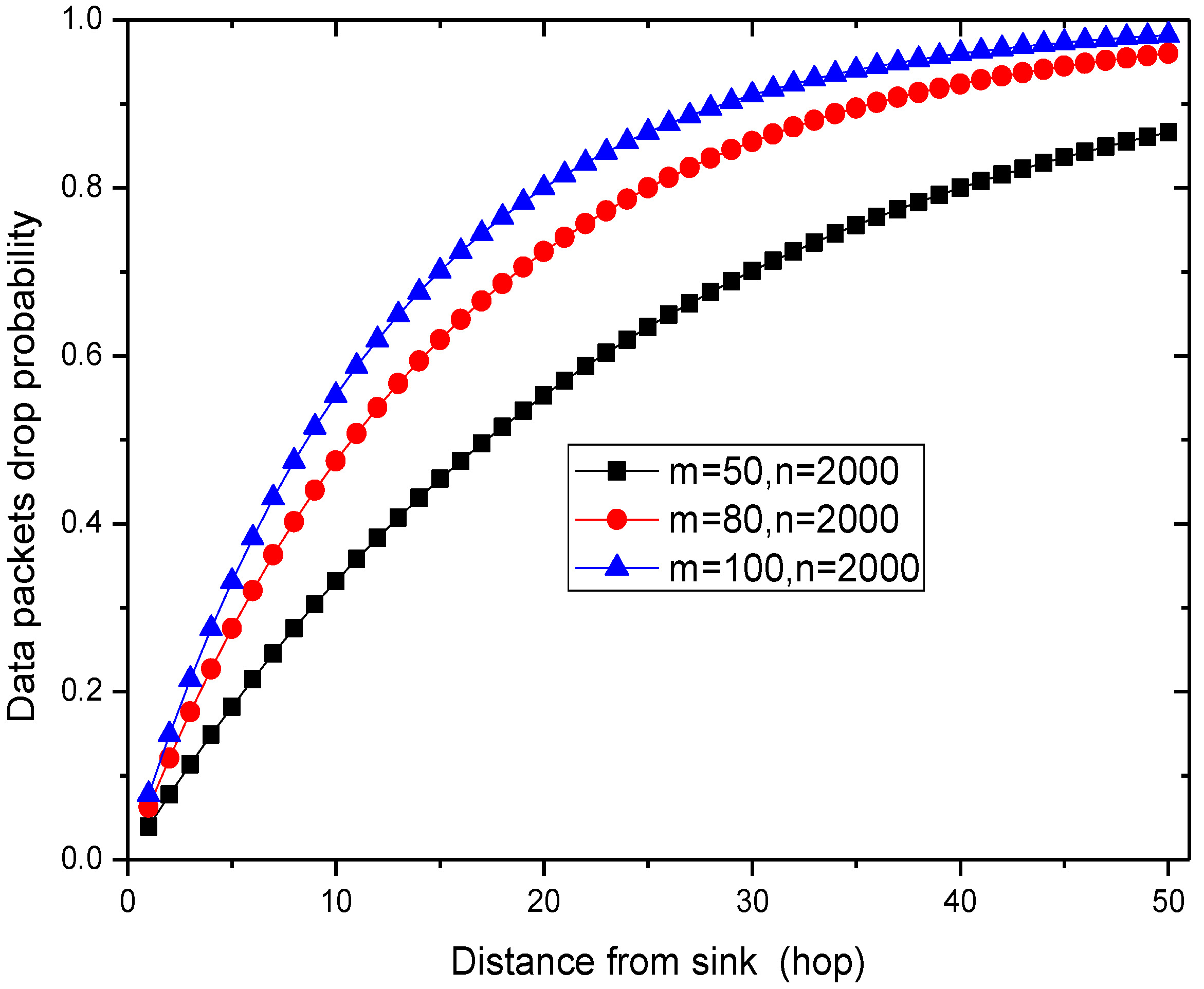
6. Experimental Results
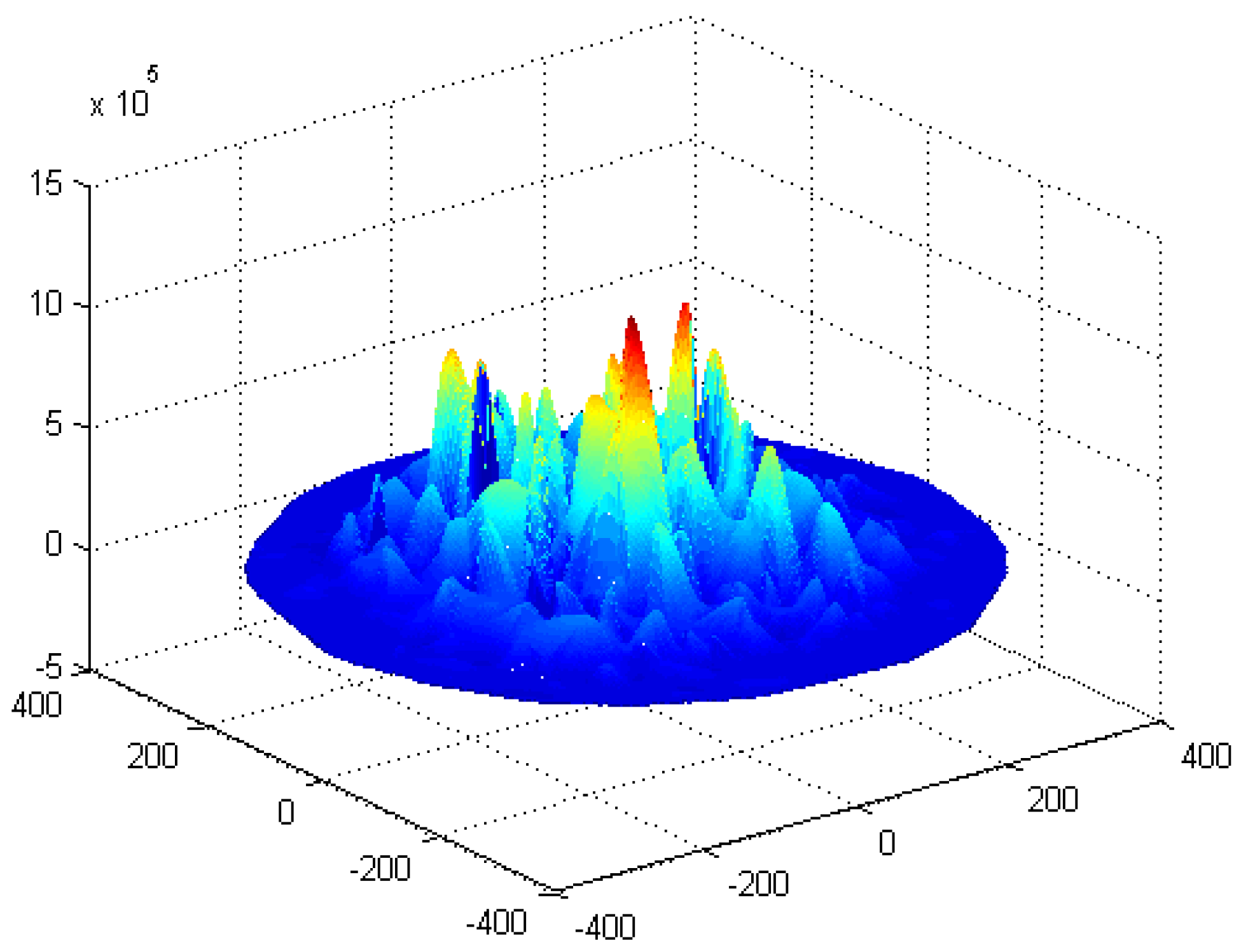
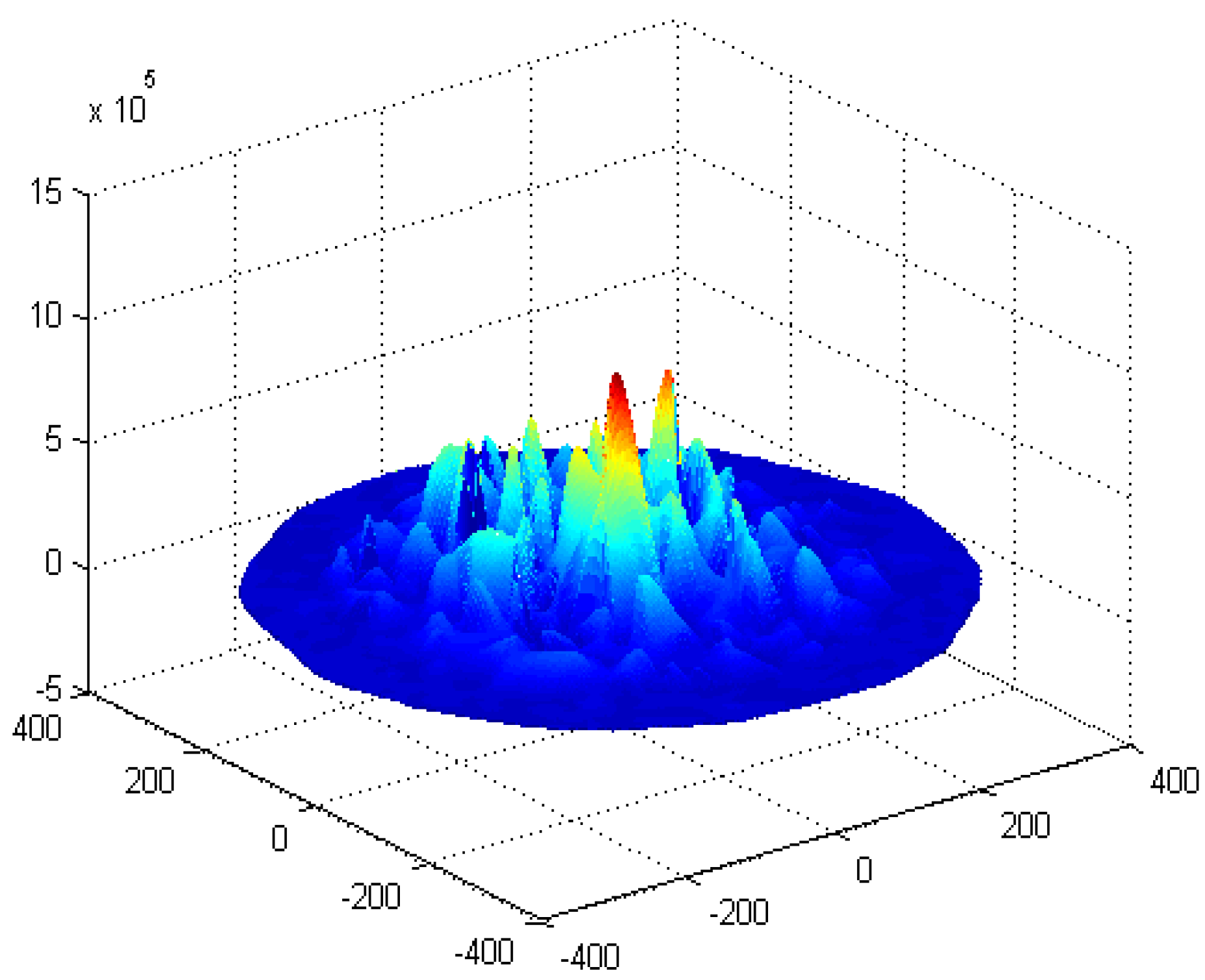

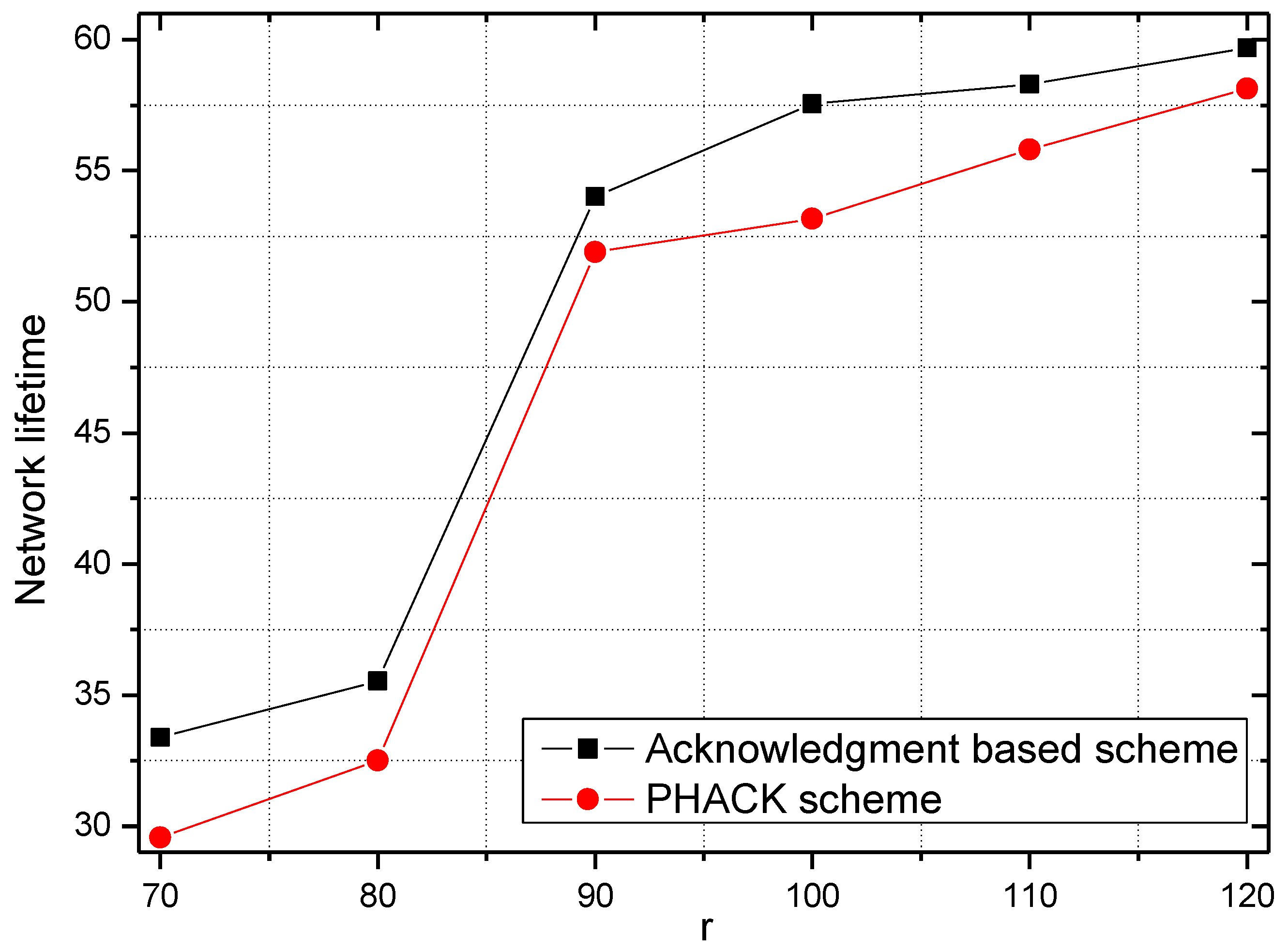
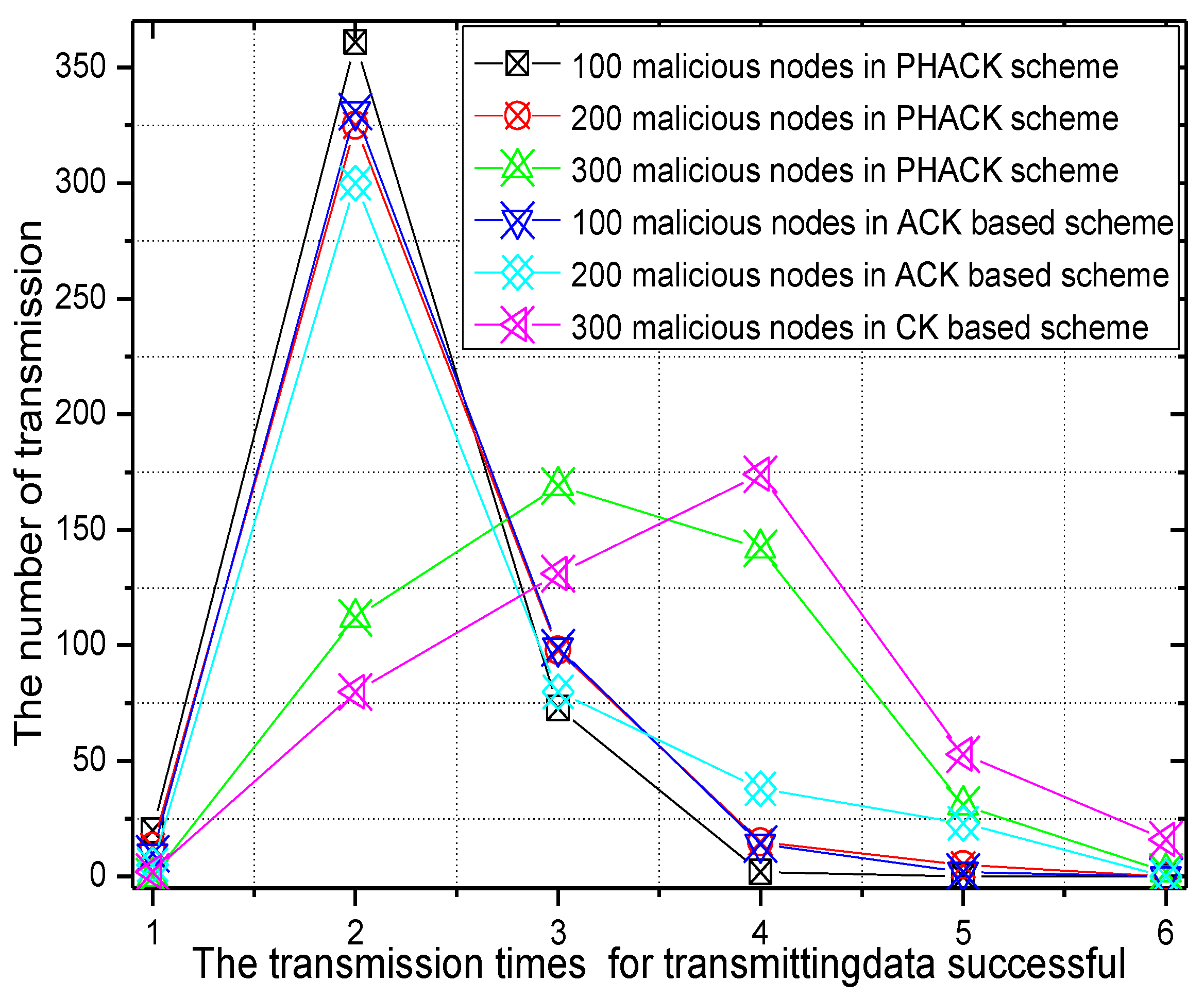

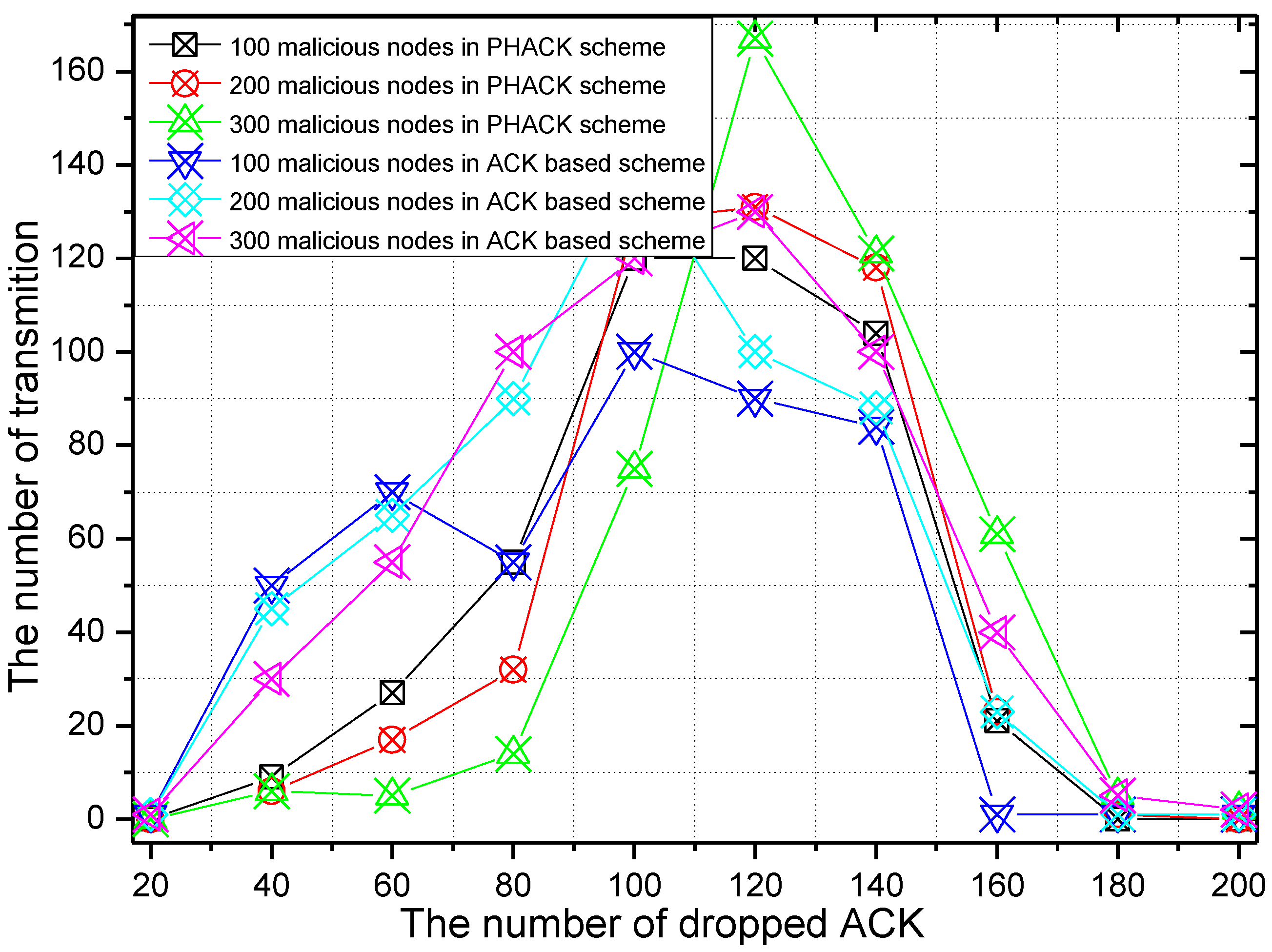
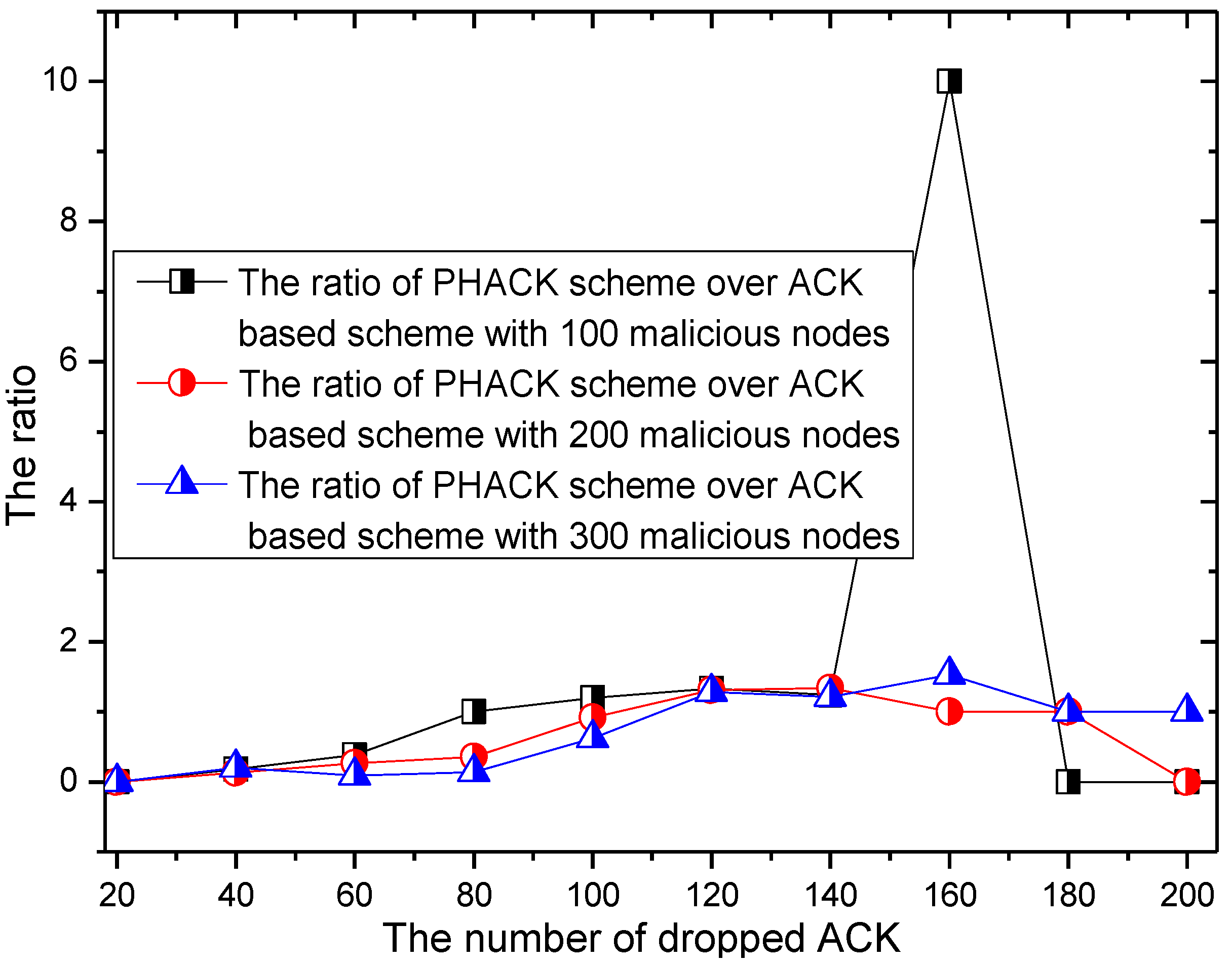
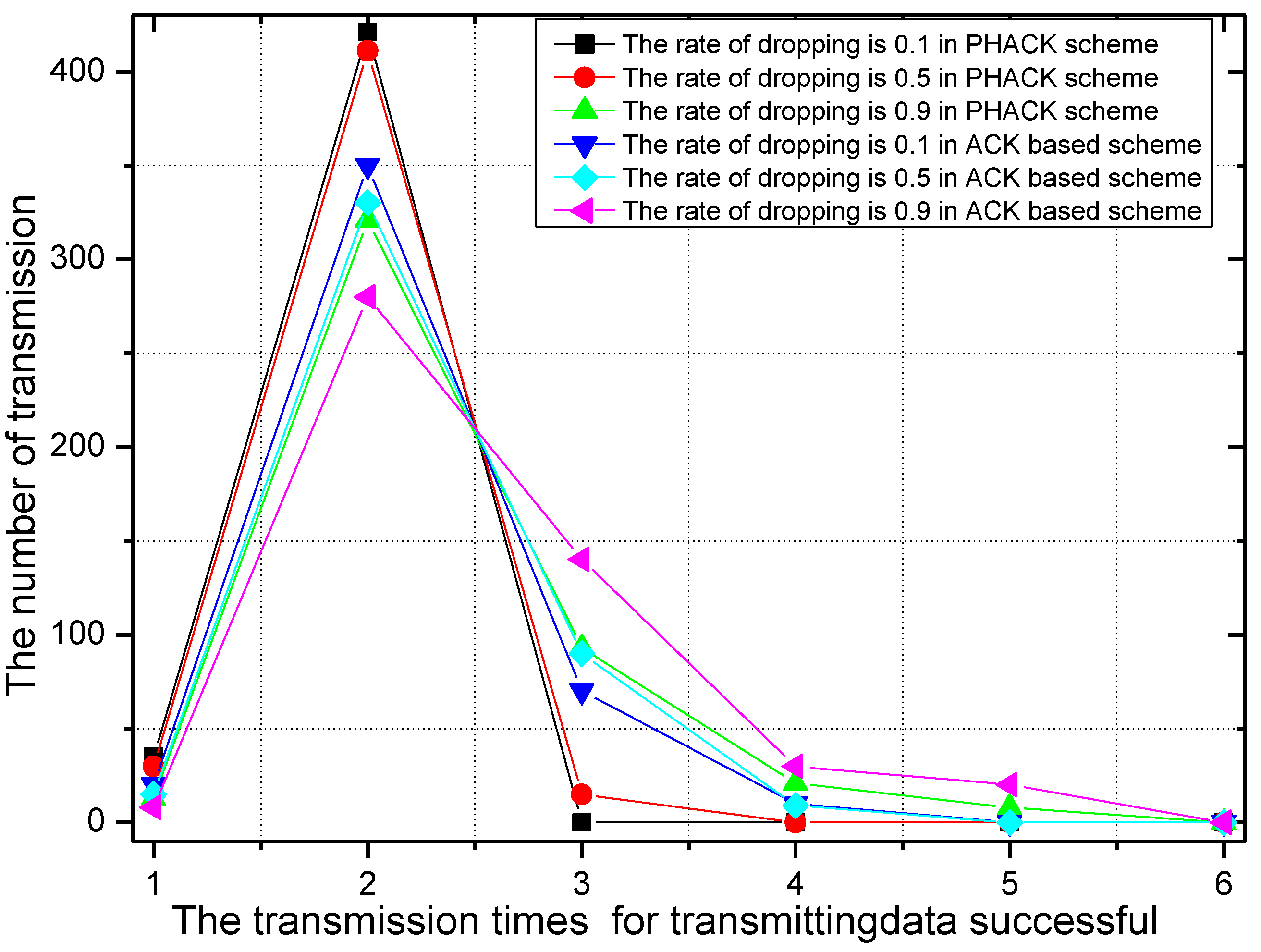
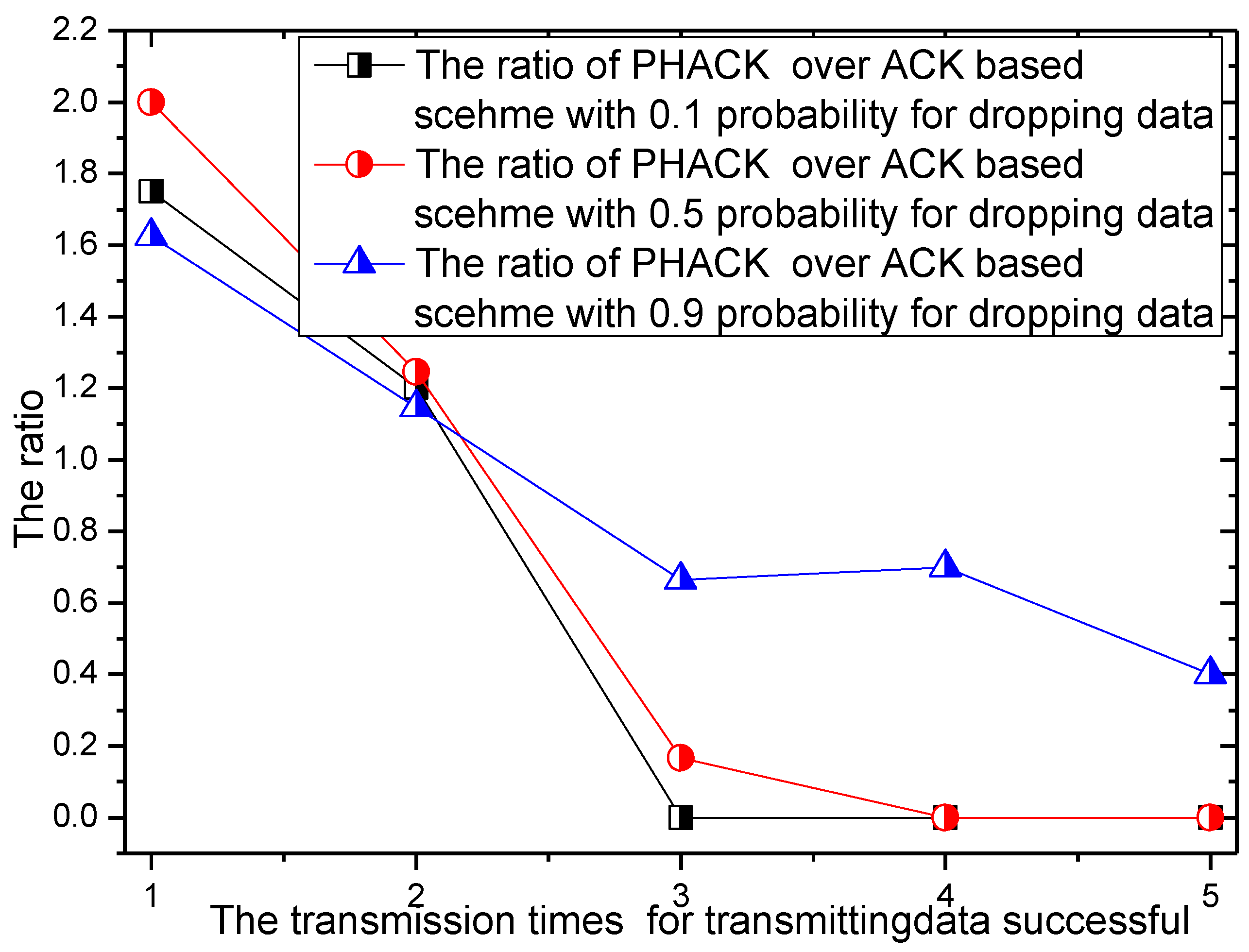
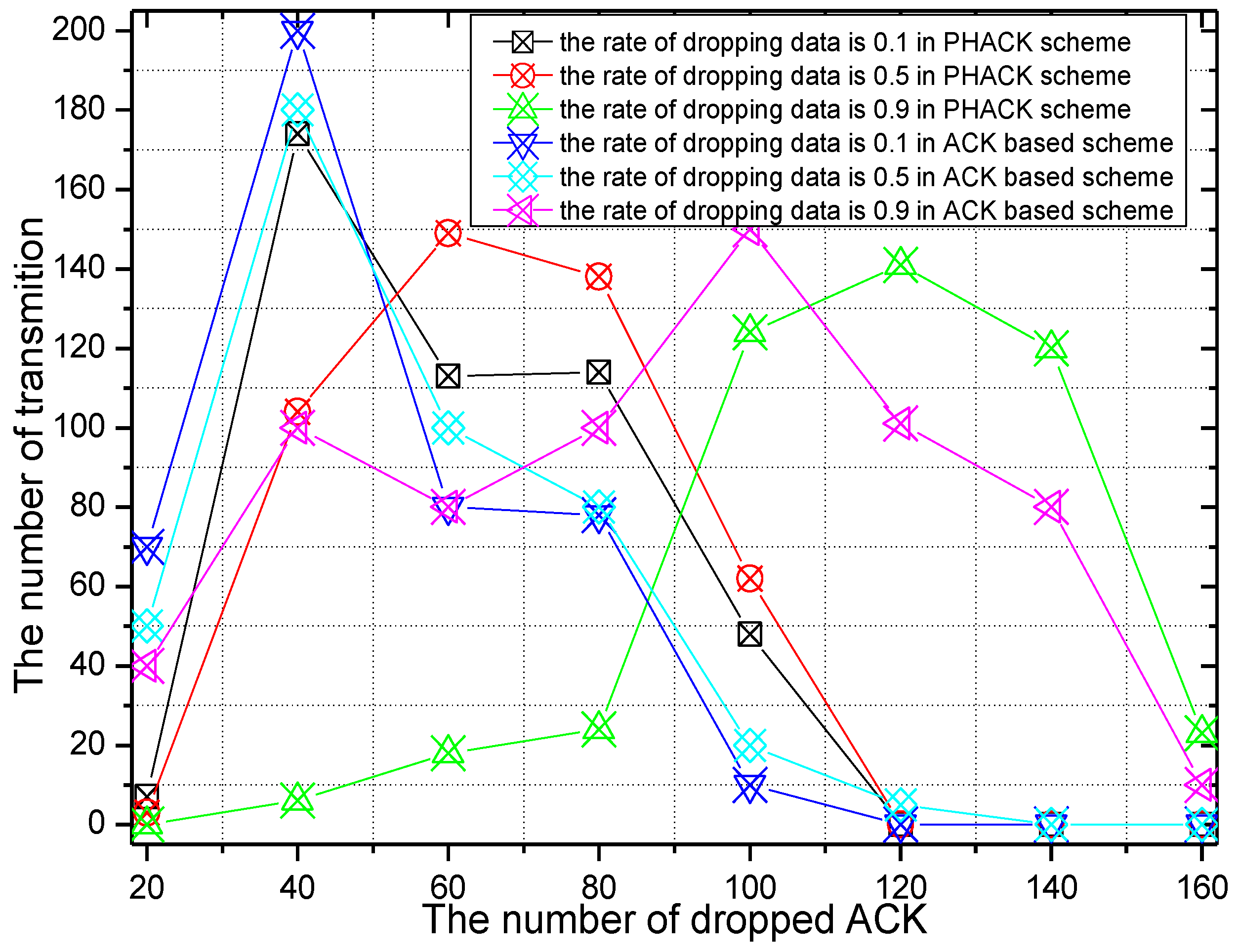
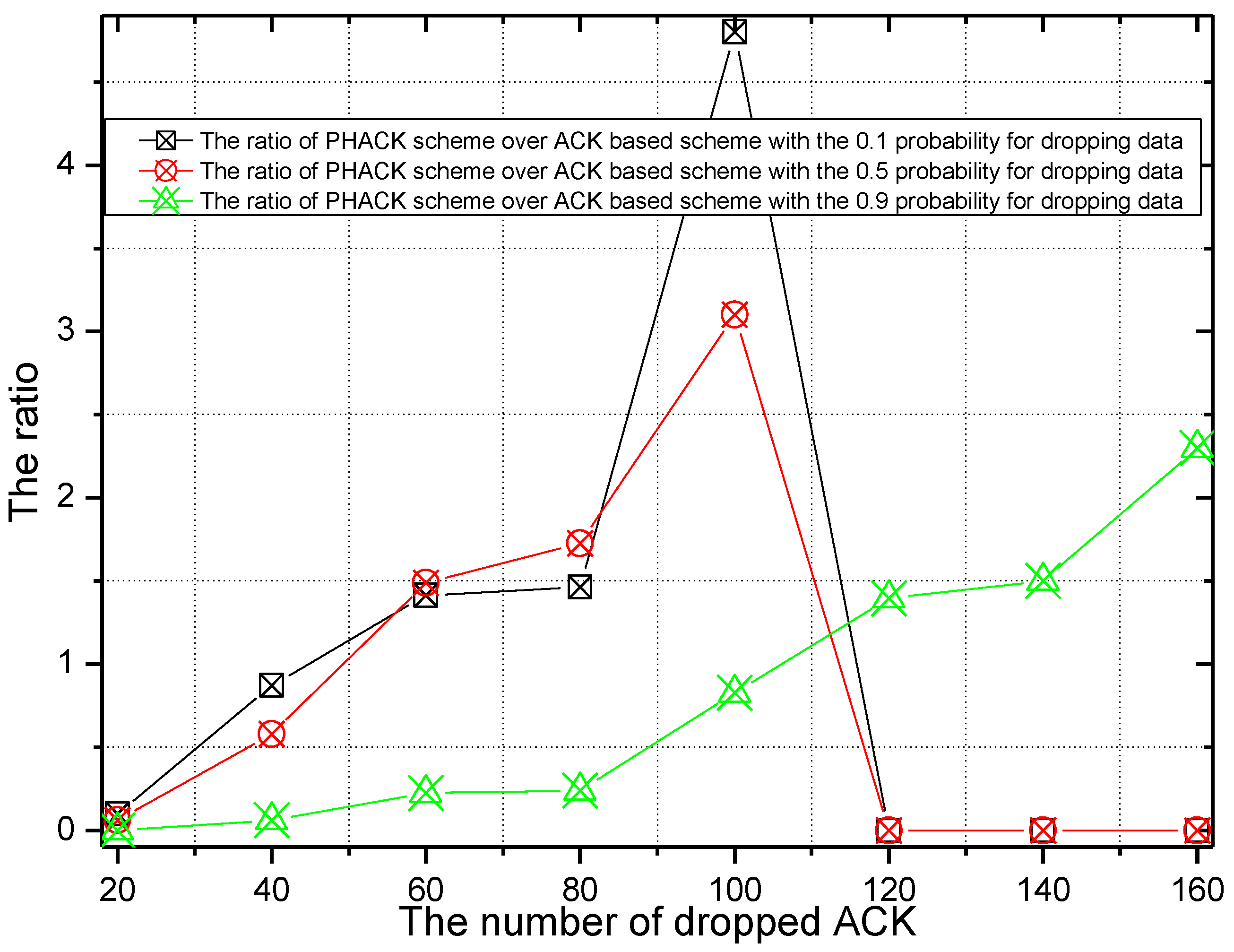
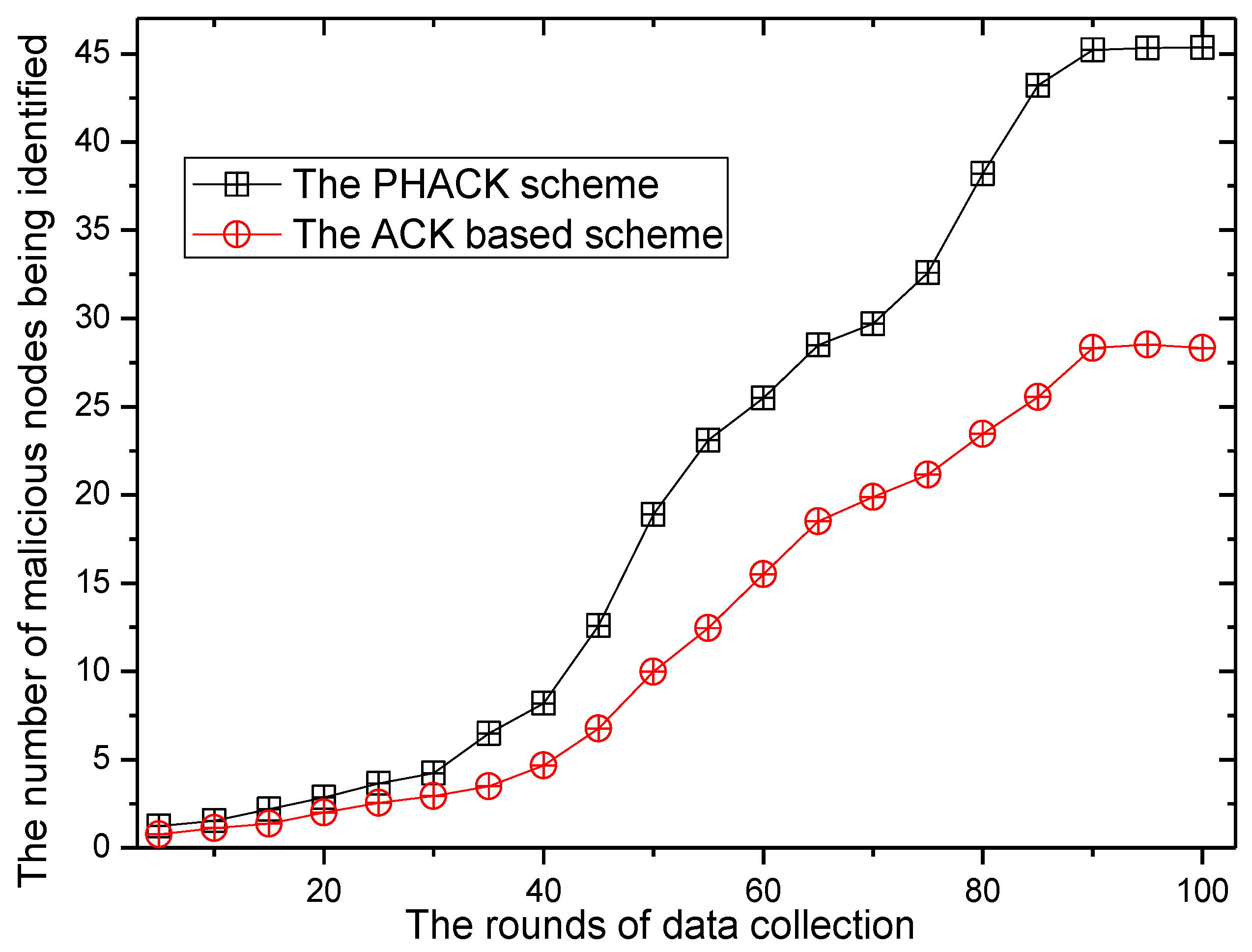
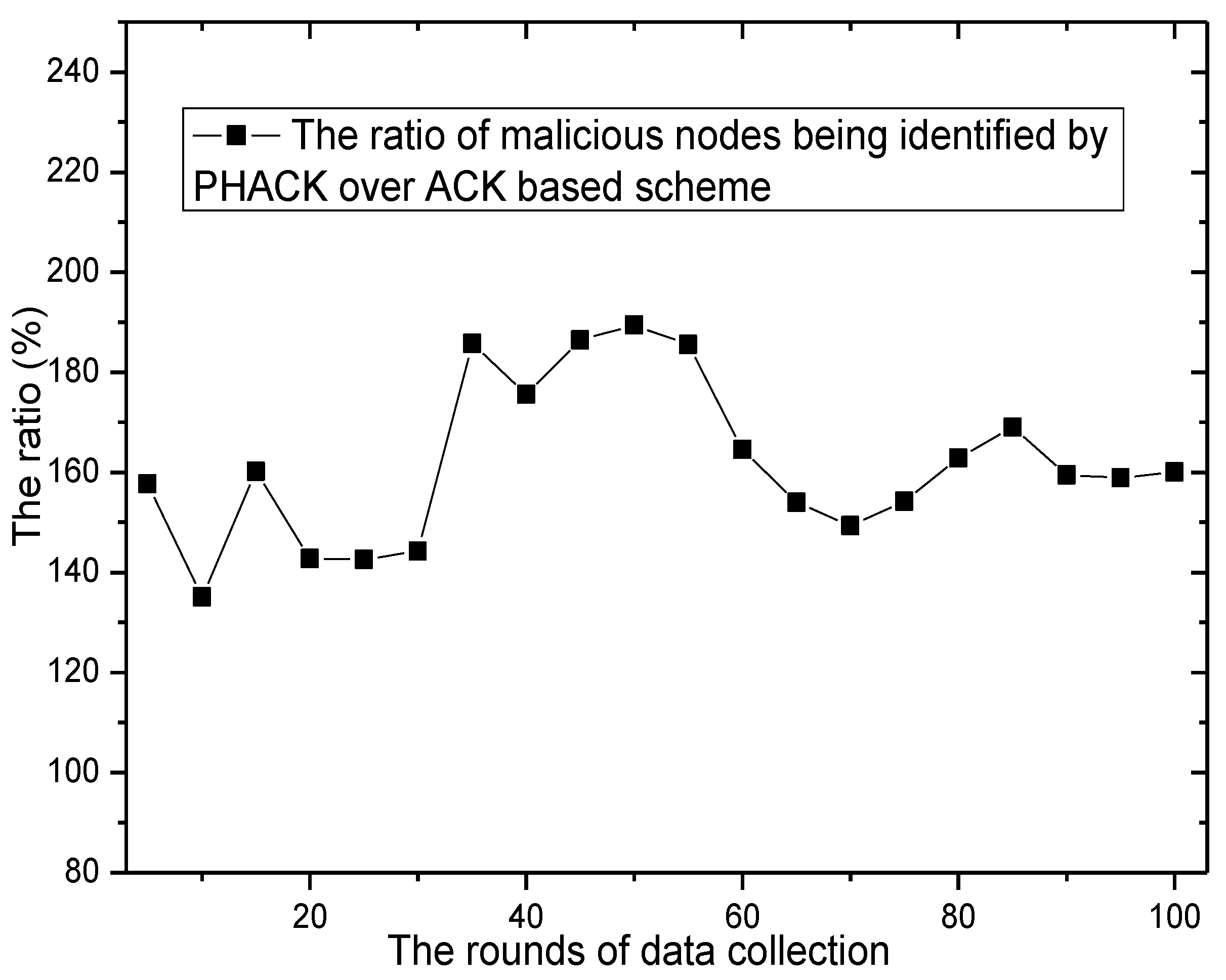
7. Conclusions and Future Work
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Hu, Y.; Liu, A. An efficient heuristic subtraction deployment strategy to guarantee quality of event detection for WSNs. Comput. J. 2015, 58, 1747–1762. [Google Scholar] [CrossRef]
- Jiang, L.; Liu, A.; Hu, Y.; Chen, Z. Lifetime maximization through dynamic ring-based routing scheme for correlated data collecting in WSNs. Comput. Electr. Eng. 2015, 41, 191–215. [Google Scholar] [CrossRef]
- Bysani, L.K.; Turuk, A.K. A Survey on Selective Forwarding Attack in Wireless Sensor. In Proceedings of the International Conference on Networks, Devices and Communications (ICDeCom), Ranchi, India, 24–25 February 2011; pp. 1–5.
- Khan, W.Z.; Xiang, Y.; Aalsalem, M.Y.; Arshad, Q. Comprehensive study of selective forwarding attack in wireless sensor networks. Int. J. Comput. Netw. Inf. Secur. 2011, 3, 1–10. [Google Scholar]
- Xiao, B.; Yu, B.; Gao, C. CHEMAS: Identify suspect nodes in selective forwarding attacks. J. Parallel Distrib. Comput. 2007, 67, 1218–1230. [Google Scholar] [CrossRef]
- Zhang, Y.; He, S.; Chen, J. Data Gathering Optimization by Dynamic Sensing and Routing in Rechargeable Sensor Networks. IEEE/ACM Trans. Netw. 2015. [Google Scholar] [CrossRef]
- He, S.; Chen, J.; Li, X.; Shen, X.; Sun, Y. Mobility and Intruder Prior Information Improving the Barrier Coverage of Sparse Sensor Networks. IEEE Trans. Mob. Comput. 2014, 13, 1268–1282. [Google Scholar]
- Hu, Y.; Dong, M.; Ota, K.; Liu, A. Mobile Target Detection in Wireless Sensor Networks with Adjustable Sensing Frequency. IEEE Syst. J. 2014. [Google Scholar] [CrossRef]
- He, S.; Gong, X.; Zhang, J.; Chen, J. Curve Based Deployment for Barrier Coverage in Wireless Sensor Networks. IEEE Trans. Wirel. Commun. 2014, 13, 724–735. [Google Scholar] [CrossRef]
- Lu, R.; Lin, X.; Zhu, H.; Liang, X.; Shen, X. BECAN: A bandwidth-efficient cooperative authentication scheme for filtering injected false data in wireless sensor networks. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 32–43. [Google Scholar]
- Liu, Y.; Liu, A.; He, S. A novel joint logging and migrating traceback scheme for achieving low storage requirement and long lifetime in WSNs. AEU Int. J. Electron. Commun. 2015, 69, 1464–1482. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, A.; Chen, Z. Analysis and improvement of send-and-wait automatic repeat-request protocols for wireless sensor networks. Wirel. Pers. Commun. 2015, 81, 923–959. [Google Scholar] [CrossRef]
- Karlof, C.; Wagner, D. Secure routing in wireless sensor networks: Attacks and countermeasures. Ad Hoc Netw. 2003, 1, 293–315. [Google Scholar] [CrossRef]
- Sun, H.; Chen, C.; Hsiao, Y. An efficient countermeasure to the selective forwarding attack in wireless sensor networks. In Proceedings of the IEEE TENCON 2007, Taipei, Taiwan, 30 October–2 November 2007; pp. 1–4.
- Dong, M.; Liu, X.; Qian, Z.; Liu, A. QoE-ensured price competition model for emerging mobile networks. IEEE Wirel. Commun. 2015, 22, 50–57. [Google Scholar] [CrossRef]
- Long, J.; Liu, A.; Dong, M.; Li, Z. An energy-efficient and sink-location privacy enhanced scheme for WSNs through ring based routing. J. Parallel Distrib. Comput. 2015, 81, 47–65. [Google Scholar] [CrossRef]
- Dong, M.; Ota, K.; Liu, A.; Guo, M. Joint Optimization of Lifetime and Transport Delay under Reliability Constraint Wireless Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2015. [Google Scholar] [CrossRef]
- Kim, J.W.; Moon, S.Y.; Cho, T.H.; Kim, J.M. Improved message communication scheme in selective forwarding attack detection method. In Proceeding of the 7th International Conference on Digital Content, Multimedia Technology and Its Applications, IDCTA, Busan, Korea, 16–18 August 2011; pp. 169–172.
- Varga, A. The OMNET++ Discrete Event Simulation System, Version 4.1. Available online: http://www.omnetpp.org (accessed on 1 April 2013).
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, A.; Dong, M.; Ota, K.; Long, J. PHACK: An Efficient Scheme for Selective Forwarding Attack Detection in WSNs. Sensors 2015, 15, 30942-30963. https://doi.org/10.3390/s151229835
Liu A, Dong M, Ota K, Long J. PHACK: An Efficient Scheme for Selective Forwarding Attack Detection in WSNs. Sensors. 2015; 15(12):30942-30963. https://doi.org/10.3390/s151229835
Chicago/Turabian StyleLiu, Anfeng, Mianxiong Dong, Kaoru Ota, and Jun Long. 2015. "PHACK: An Efficient Scheme for Selective Forwarding Attack Detection in WSNs" Sensors 15, no. 12: 30942-30963. https://doi.org/10.3390/s151229835
APA StyleLiu, A., Dong, M., Ota, K., & Long, J. (2015). PHACK: An Efficient Scheme for Selective Forwarding Attack Detection in WSNs. Sensors, 15(12), 30942-30963. https://doi.org/10.3390/s151229835







