Commitment Schemes from OWFs with Applications to Quantum Oblivious Transfer
Abstract
1. Introduction
1.1. Related Work
1.2. Contribution and Structure
1.3. Quantum Oblivious Transfer Protocol
| Algorithm 1 quantum oblivious transfer protocol. |
| Parameters: n (security parameter), (two-universal family of hash functions) Inputs:
|
Security
| Algorithm 2 : BBCS QOT protocol with commitment functionality. |
| Parameters: Same as in protocol Inputs: Same as in protocol // BB84 Phase
|
2. Preliminaries
2.1. Definitions
- -
- takes as input , for a security parameter, n, and outputs some public parameter, , as a public commitment key, i.e., ;
- -
- takes as input a public key, , and a message, m. It outputs a commitment, c, and a reveal value, d, i.e., ;
- -
- takes as input a public key, , a message, m, a commitment, c, and a reveal value, d. It returns 1 or 0 to accept or reject, respectively, i.e., , where .
- -
- Perfect completeness: The verification algorithm outputs 1 whenever the inputs are computed honestly, i.e., for all messages, m,
Security
- The scheme is perfectly hiding if and are equally distributed.
2.2. Commitment Scheme for qOT
2.3. Naor’s Bit Commitment Scheme
- -
- : The setup algorithm chooses any pseudorandom number generator, G, that stretches a random seed with the length n to bits, i.e., ;
- -
- : This algorithm has two phases:
- -
- Commit phase:
- 1.
- selects a random bit string, r, of the length and sends it to ;
- 2.
- After receiving r, selects a random seed, , and returns the commitment string c to , where
- -
- Reveal phase: To open the commitment, sends b and x to .
- -
- : verifies that the values , and r match the previously given commitment.
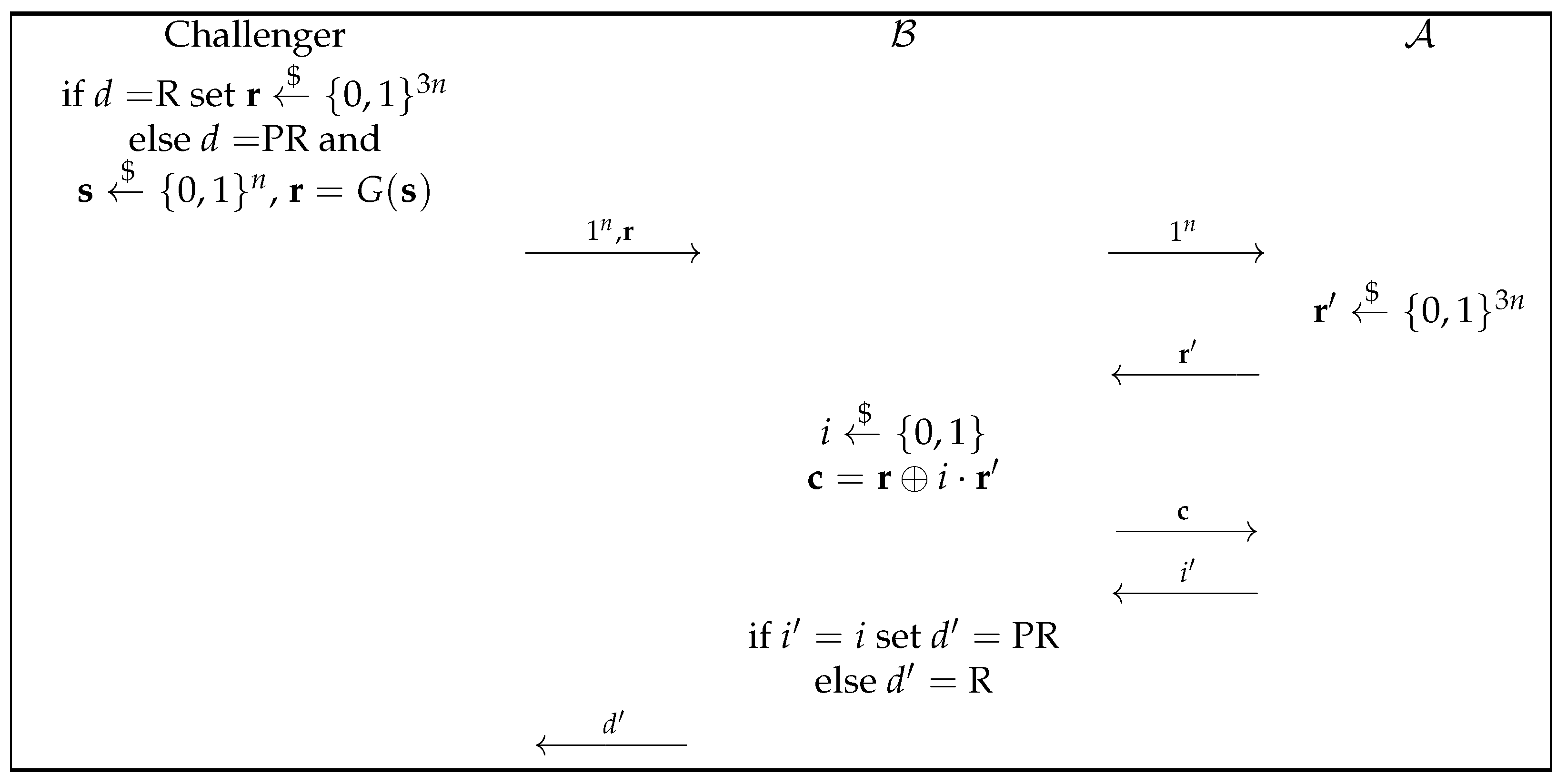
- Computational Hiding: We have to prove that no PPT distinguisher is capable of distinguishing between and for two distinct bits, b and , with a non-negligible advantage. Specifically, we will demonstrate that if G is a secure PRNG, then the scheme possesses the hiding property. To argue by contradiction, suppose that the scheme is not hiding. This implies the existence of an adversary, , who can distinguish between and for two different bits, b and , with a non-negligible probability. Given this situation, we can construct another adversary, , that can distinguish between a truly random string, , and a pseudorandom string, , for a seed, .To model this attack, we refer to Figure 1. Notably, we recognize that the adversary can break the hiding property. In other words, is able to distinguish between and with a non-negligible probability in n, where is a random string chosen from and is chosen by .Now, let us assume that the challenger selects to be a truly random string, i.e., . Under this assumption, it becomes crucial to analyze the behavior of and understand how it exploits the properties of G to distinguish between the given instances.Then, remains random for , so cannot distinguish it with non-negligible probability.Specifically, in this case, we haveNow, consider the scenario where the challenger instead chooses as a pseudorandom string (i.e., , where ). In this situation, . Under this assumption, when , , which is a pseudorandom string generated by G using a random seed, . Instead, when , is the XOR of a pseudorandom string, , and a random string (). This is precisely the case where can distinguish, with a non-negligible advantage, the two cases.Thus, with a non-negligible advantage, will correctly identify i, that is,Recall that the ultimate goal is to prove that can distinguish a pseudorandom string from a random string with non-negligible probability, i.e.,In this case, the previous difference isThis result confirms that can indeed distinguish between a pseudorandom string and a random string with a non-negligible probability, confirming the computational hiding property of the scheme.
- Statistical Binding: We must establish that for every potential forger, , and for any two distinct messages, m and , from the message space, there exists a negligible function, , such thatwhere , , , , and .Considering the commitment notation, this requirement translates toIt is important to note that the set contains at most elements. Consequently, the set can have at most elements. Given this, the probability that a randomly chosen string, , falls within this set is at mostTherefore, this is the maximum probability with which a forger can identify two values that generate two different valid openings for the commitment. This extremely low probability, decreasing exponentially with n, ensures that the statistical binding property is verified, effectively preventing the forger from finding such values and thus maintaining the integrity and security of the commitment scheme.
2.4. On Naor’s String Commitment Scheme
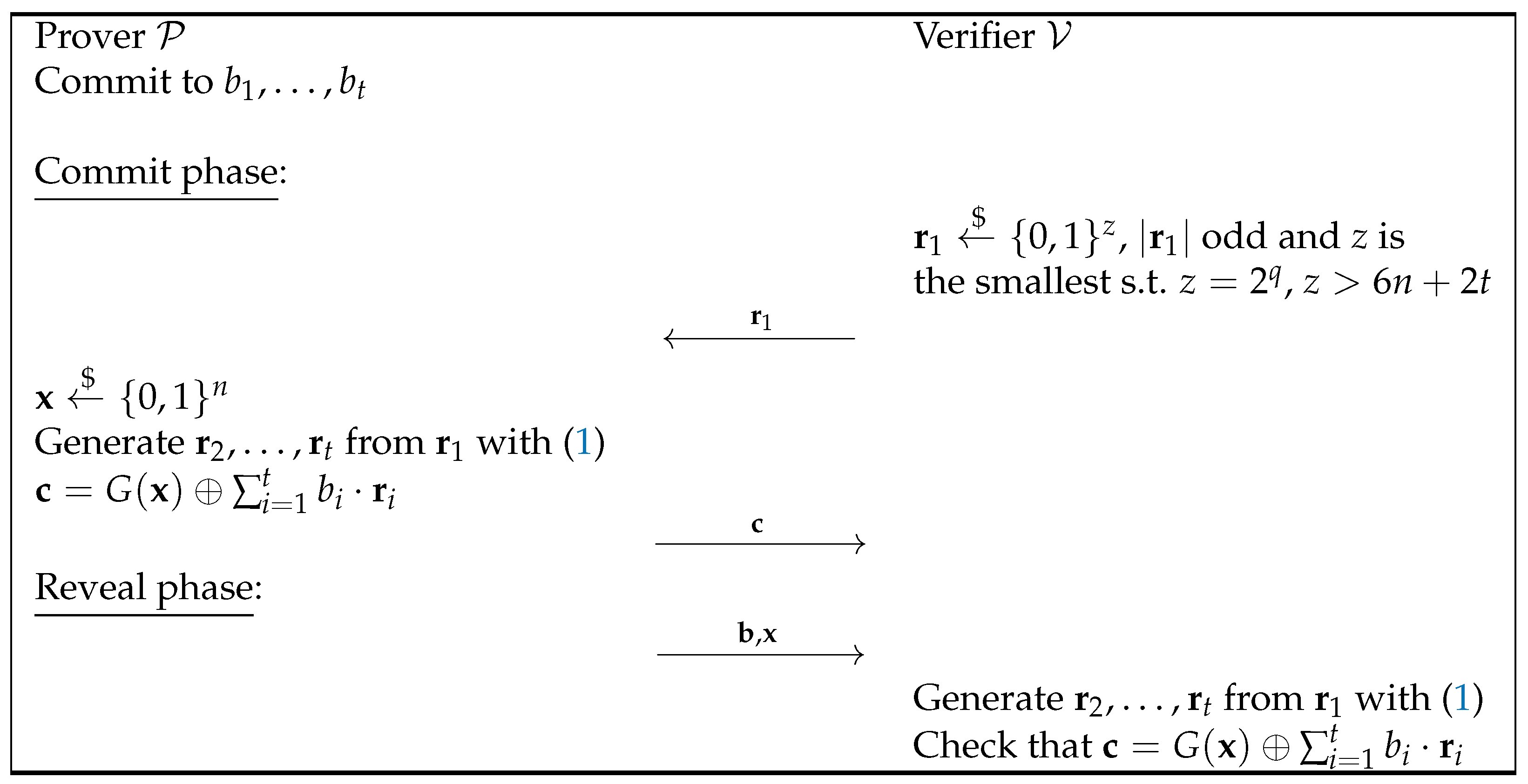
3. New String Commitment Based on Naor
- Computational Hiding: The proof of the computational hiding property can be obtained naturally by modifying that of Naor’s bit commitment scheme. In particular, the attack is the same as the one described in Figure 1, just changing the fact that instead of committing to a bit, a bit string is committed to and the adversary can guess the right values for with a probability of - when is given and with the probability when .
- Statistical Binding: Suppose that wants to open the commitment to a different value, , after already committing to . To carry this out, needs to find a new such that . We know that for any fixed value of , the chance of successfully finding such an is very low, specifically bounded by . This can be shown by following the proof of the binding property in Naor’s bit commitment scheme and adjusting the length of the pseudorandom string generated by G.Thus, the probability that can find one such value to cheat is bounded by since all possible values that allow to cheat are (that is, all the possible values ) and the probability for all is bounded by .
3.1. On the Algorithm for Generating Some Linearly Independent Vectors from a Random One
- The rank of C is n;
- The degree of the greatest common divisor of and the associated polynomial of C is 0.
- ⇒:Suppose, for the sake of contradiction, that . This implies the existence of a non-zero linear combination of the matrix vectors that results in the zero vector. Each vector can be identified with a polynomial in . Specifically, the polynomial corresponding to the first vector is the polynomial f; the second vector corresponds to , and so on. Finding a non-zero linear combination that generates translates into finding a subset, , such that . In polynomial terms, this means that , which implies that divides . Since , two possibilities arise: either divides f, which implies that divides both f and , leading to , contradicting our initial assumption; or divides . Given that , this is only possible if , which contradicts our assumption of a non-zero linear combination.
- ⇒:Suppose, for the sake of contradiction, that . According to the earlier discussion, this implies that divides g. Since g divides f by definition, f must have a root in 1. This means that f has an even number of terms. If this is the case, it is easy to check that the sum of all vectors in the matrix is , implying that the rank of the matrix is strictly less than n. Therefore, , and thus its degree is 0.
3.2. Extending Kilian with Our Approach
3.3. The Commitment Scheme Used in qOT
- If then we have the same as before with in place of , but is obtained by rotating , so it is random as well, and the same as before can be said;
- If, instead, , then the equation the prover must be able to satisfy isNow, for every value of , has even weight. However, there are no more constraints on it. So, it is a random value in a subspace of the dimension , and the probability of finding an satisfying Equation (3) is(it is not possible that because it would imply that and, in our case, this implies that either or ).
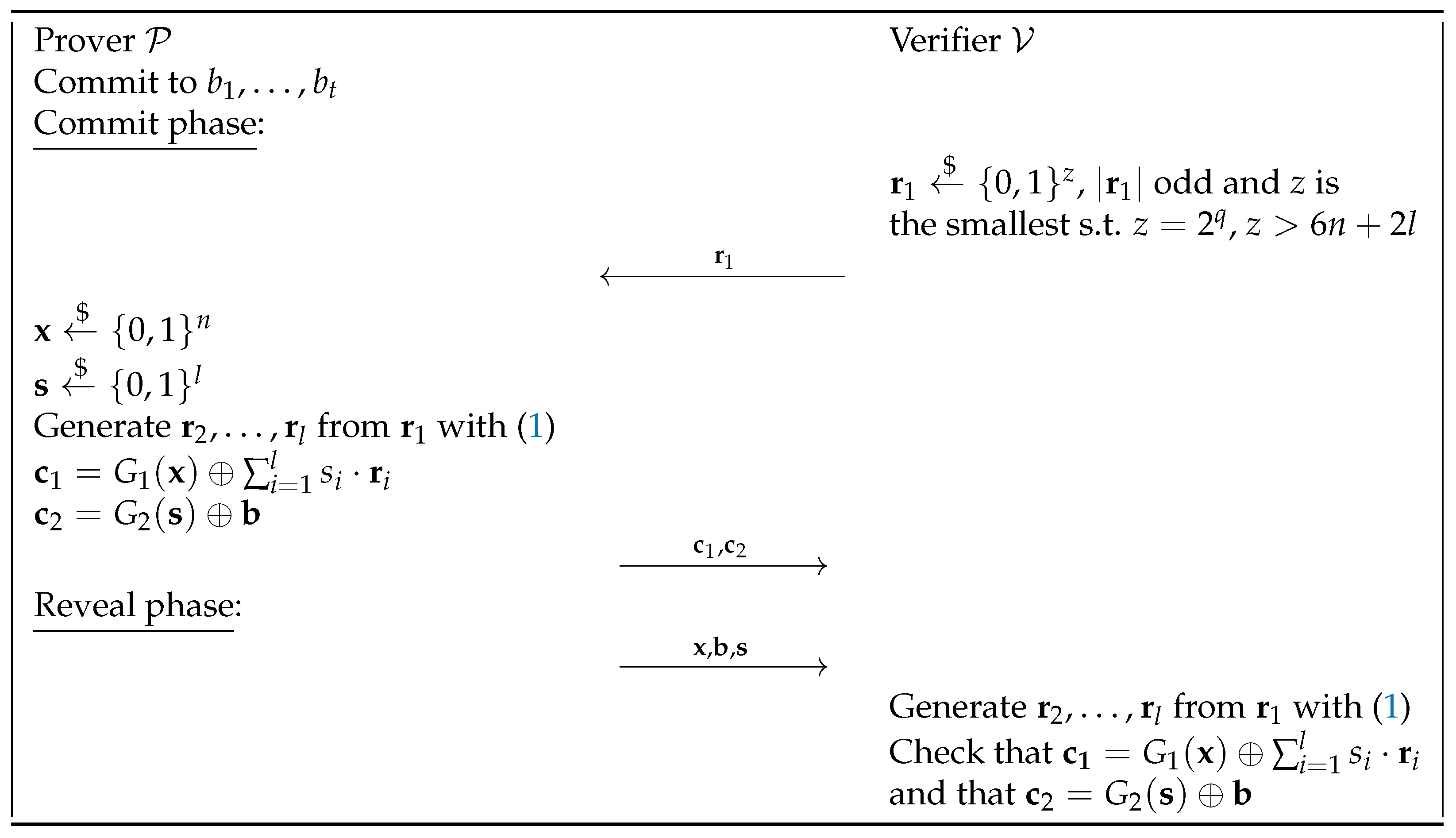
4. A New Preprocessing Model for Commitments
- Binding: Suppose that the prover commits to b by publishing for a committed m in the preprocessing phase, with the commitment c. To open to , the prover must be able to open c to , so that . However, if the prover cannot open c to , this is impossible. Therefore, to break the binding property here, the prover would need to break the binding property of the commitment scheme used in the preprocessing phase.
- Hiding: Again, suppose that the prover commits to b by publishing for a committed m in the preprocessing phase, with the commitment c. For the verifier, learning b from is equivalent to learning m from . To learn m, the verifier would need to break the hiding property of the commitment scheme used in the preprocessing phase.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
References
- Naor, M.; Pinkas, B. Oblivious Transfer and Polynomial Evaluation. In Proceedings of the Thirty-First Annual ACM Symposium on Theory of Computing, Atlanta, GA, USA, 1–4 May 1999; pp. 245–254. [Google Scholar] [CrossRef]
- Abdalla, M.; Benhamouda, F.; Blazy, O.; Chevalier, C.; Pointcheval, D. SPHF-Friendly Non-interactive Commitments. In Proceedings of the 19th International Conference on the Theory and Application of Cryptology and Information, Bengaluru, India, 1–5 December 2013; Part, I; LNCS. Sako, K., Sarkar, P., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; Volume 8269, pp. 214–234. [Google Scholar] [CrossRef]
- Lindell, Y. Secure multiparty computation. Commun. ACM 2021, 64, 86–96. [Google Scholar] [CrossRef]
- Líšková, L.; Stanek, M. Efficient Simultaneous Contract Signing. In Security and Protection in Information Processing Systems, Proceedings of the IFIP 18th World Computer Congress TC11 19th International Information Security Conference, Toulouse, France, 22–27 August 2004; Deswarte, Y., Cuppens, F., Jajodia, S., Wang, L., Eds.; Springer: Boston, MA, USA, 2004; pp. 441–455. [Google Scholar][Green Version]
- Kolesnikov, V.; Kumaresan, R.; Rosulek, M.; Trieu, N. Efficient Batched Oblivious PRF with Applications to Private Set Intersection. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; Weippl, E.R., Katzenbeisser, S., Kruegel, C., Myers, A.C., Halevi, S., Eds.; ACM Press: New York, NY, USA, 2016; pp. 818–829. [Google Scholar] [CrossRef]
- Gertner, Y.; Kannan, S.; Malkin, T.; Reingold, O.; Viswanathan, M. The Relationship between Public Key Encryption and Oblivious Transfer. In Proceedings of the 41st Annual Symposium on Foundations of Computer Science, Redondo Beach, CA, USA, 2–14 November 2000; pp. 325–335. [Google Scholar] [CrossRef]
- Santos, M.B.; Mateus, P.; Pinto, A.N. Quantum oblivious transfer: A short review. Entropy 2022, 24, 945. [Google Scholar] [CrossRef] [PubMed]
- Lemus, M.; Schiansky, P.; Goulão, M.; Bozzio, M.; Elkouss, D.; Paunković, N.; Mateus, P.; Walther, P. Performance of Practical Quantum Oblivious Key Distribution. arXiv 2025, arXiv:2501.03973. [Google Scholar]
- Bennett, C.H.; Brassard, G.; Crépeau, C.; Skubiszewska, M.H. Practical Quantum Oblivious Transfer. In Advances in Cryptology—CRYPTO ’91; Feigenbaum, J., Ed.; Springer: Berlin/Heidelberg, Germany, 1992; pp. 351–366. [Google Scholar]
- Aaronson, S. Quantum lower bound for the collision problem. In Proceedings of the Thiry-Fourth Annual ACM Symposium on Theory of Computing, Montreal, QC, Canada, 19–21 May 2002; pp. 635–642. [Google Scholar] [CrossRef]
- Santos, M.B.; Gomes, A.C.; Pinto, A.N.; Mateus, P. Private Computation of Phylogenetic Trees Based on Quantum Technologies. IEEE Access 2022, 10, 38065–38088. [Google Scholar] [CrossRef]
- Jain, A.; Krenn, S.; Pietrzak, K.; Tentes, A. Commitments and Efficient Zero-Knowledge Proofs from Learning Parity with Noise. In Proceedings of the 18th International Conference on the Theory and Application of Cryptology and Information Security, Beijing, China, 2–6 December 2012; LNCS. Wang, X., Sako, K., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7658, pp. 663–680. [Google Scholar] [CrossRef]
- Halevi, S.; Micali, S. Practical and Provably-Secure Commitment Schemes from Collision-Free Hashing. In Advances in Cryptology—CRYPTO ’96, Proceedings of the 16th Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 1996; Koblitz, N., Ed.; Springer: Berlin/Heidelberg, Germany, 1996; pp. 201–215. [Google Scholar] [CrossRef]
- Naor, M. Bit Commitment Using Pseudorandomness. J. Cryptol. 1991, 4, 151–158. [Google Scholar] [CrossRef]
- Faz-Hernandez, A.; López, J.; de Oliveira, A.K.D.S. SoK: A Performance Evaluation of Cryptographic Instruction Sets on Modern Architectures. In Proceedings of the ASIA CCS ’18: ACM Asia Conference on Computer and Communications Security, Incheon, Republic of Korea, 4 June 2018; pp. 9–18. [Google Scholar] [CrossRef]



Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lorünser, T.; Ramacher, S.; Valbusa, F. Commitment Schemes from OWFs with Applications to Quantum Oblivious Transfer. Entropy 2025, 27, 751. https://doi.org/10.3390/e27070751
Lorünser T, Ramacher S, Valbusa F. Commitment Schemes from OWFs with Applications to Quantum Oblivious Transfer. Entropy. 2025; 27(7):751. https://doi.org/10.3390/e27070751
Chicago/Turabian StyleLorünser, Thomas, Sebastian Ramacher, and Federico Valbusa. 2025. "Commitment Schemes from OWFs with Applications to Quantum Oblivious Transfer" Entropy 27, no. 7: 751. https://doi.org/10.3390/e27070751
APA StyleLorünser, T., Ramacher, S., & Valbusa, F. (2025). Commitment Schemes from OWFs with Applications to Quantum Oblivious Transfer. Entropy, 27(7), 751. https://doi.org/10.3390/e27070751






