Forensic Support for Abraham et al.’s BB Protocol
Abstract
1. Introduction
- Designing a forensic protocol for Abraham et al.’s BB. This protocol can label Byzantine nodes that violate the flow of Abraham et al.’s BB when the number of Byzantine nodes controlled by the adversary does not exceed , and provide verifiable evidence of specific malicious operations executed by the labeled nodes at each step.
- Analyzing two key performance indicators of the forensic protocol: the number of Byzantine nodes that can be labeled and the number of additional messages that need to be requested. A higher number of labeled Byzantine nodes indicates stronger forensic support, while fewer additional messages indicate greater efficiency. The forensic protocol designed in this paper can label Byzantine nodes, requiring only one additional message to be transmitted.
- Proposing and proving an impossibility result, demonstrating that Abraham et al.’s BB cannot provide any effective forensic support when the number of Byzantine nodes exceeds . This impossibility result shows that the forensic protocol designed in this paper is optimal in terms of the number of allowable Byzantine nodes.
2. Preliminaries and Related Work
2.1. Byzantine Broadcast
- Agreement. It holds that , when two honest parties commit value v and , respectively.
- Validity. For any honest broadcaster, all honest parties will commit the value sent by the designated broadcaster and terminate.
- Termination. Every honest party commits and terminates.
- Agreement. Same as above.
- Validity. For any honest broadcaster, all replicas will commit the value broadcasted by the designated broadcaster, if .
- Termination. After GST is reached, all honest replicas commit and terminate.
2.2. Related Work of State Machine Replication Protocol
2.3. Related Work of Forensic Support
3. Model Assumptions and Problem Description
3.1. System Model
3.2. Forensic Support
4. Review of Abraham et al.’s BB Protocol
4.1. Overview of the Protocol
- Proposal Phase: The leader of the current view sends a proposal message to all nodes containing the broadcast value v and a status certificate M. The specific definition of the status certificate is provided later in this section.
- Voting Phase: Upon receiving a proposal message from the leader, a node verifies that the broadcast value v in the proposal message complies with the protocol rules, i.e., whether it aligns with the state certificate M. If it passes the verification, the node broadcasts a voting message for v.
- Confirmation Phase: Upon receiving votes for v from different nodes in the current view, the node generates a valid Confirmation certificate, output v, and returns a reply message to the client. The reply message contains the broadcast value and the corresponding Confirmation certificate.
4.1.1. Timeout Certificates and Locked Broadcast Values
- The timeout certificate contains at least timeout messages that include the broadcast value v, and there are no timeout messages that contains a value that conflicts with v.
- The timeout certificate contains at least timeout messages that include the broadcast value v, with no timeout messages from the leader of the current view.
4.1.2. Status Certificate
4.2. Agreement Guarantee
4.2.1. Agreement Within a Single View
4.2.2. Agreement Across Views
5. Forensic Protocols for Abraham et al.’s BB
5.1. High Level Overview
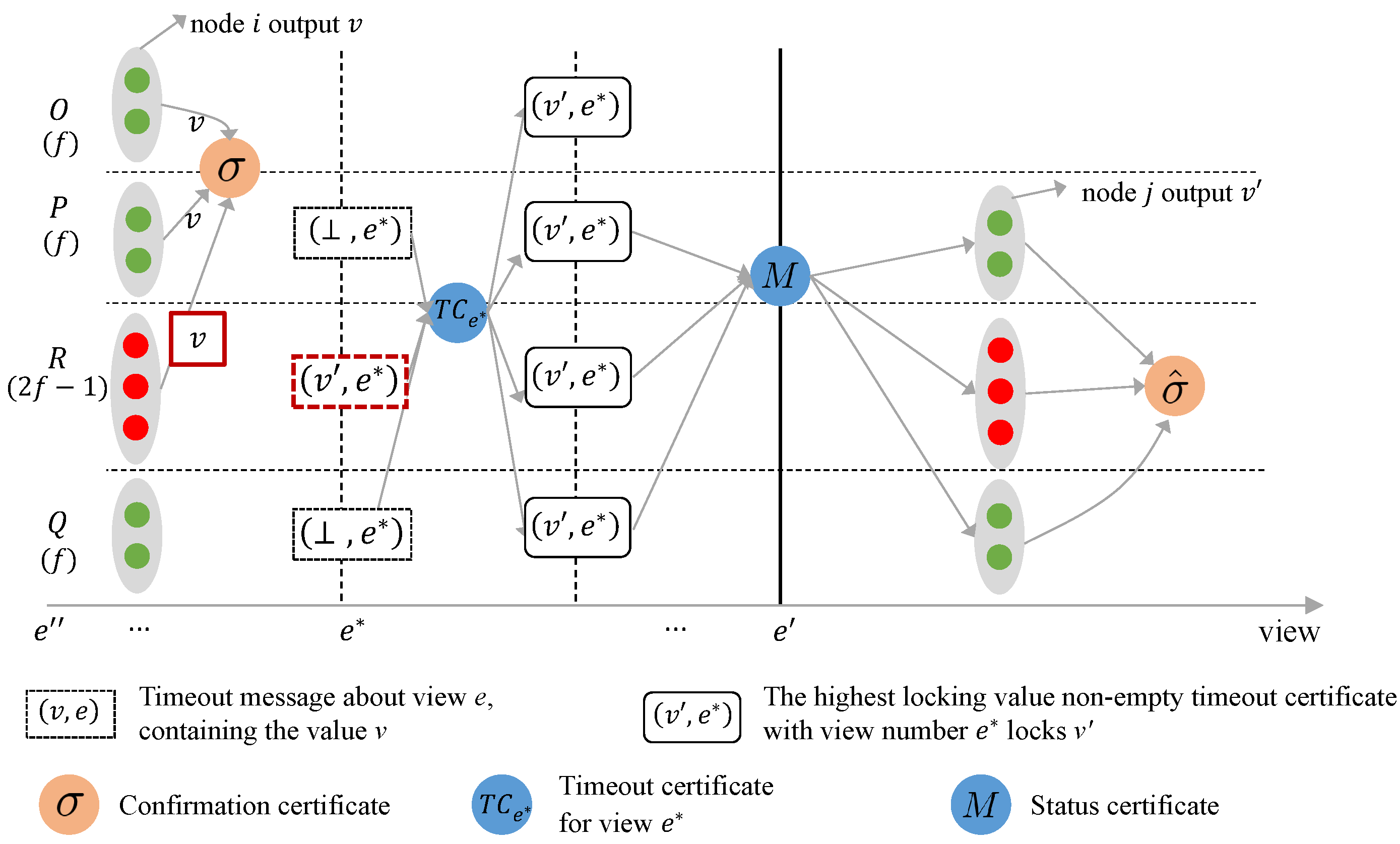
- In view e, the nodes in , , and vote for v. A node i in receives these votes, generates an confirmation certificate, and outputs v. Meanwhile, the node in does not receive a proposal message from the leader and does not vote for any value in view e.
- At the end of view e, all nodes receive timeout messages from , , and . The timeout message for the node in contains its vote value v, while the timeout messages for the nodes in and contain ⊥. As a result, all honest nodes fail to meet the protocol’s locking rules for the timeout certificates they generate in view e, and thus do not lock any values. The honest node’s most recent timeout certificate with a non-empty locking value has view number and locks .
- In the subsequent view , the timeout certificates received by the leader lock . Therefore, the leader sets its proposal value to and includes the status certificate consisting of these timeout certificates in the proposal message. According to the protocol’s voting rules, the proposal value set by the leader passes the node check. All nodes then vote on after receiving the proposal and output .
5.2. Forensic Protocol
| Algorithm 1: Abraham et al.’s BB forensics protocol |
|
5.3. Forensic Support Analysis on Abraham et al.’s BB Protocol
- Case 1:
- the view number of is less than e
- There is no timeout message in that contains a value conflicting with the broadcast value v. At most timeout messages in contain the broadcast value v; otherwise, would lock the broadcast value v. Therefore, there are at least timeout messages in containing ⊥. Sincethere are at least intersecting nodes between the nodes sending these timeout messages and the corresponding nodes in the confirmation certificate . These nodes can be labeled as Byzantine nodes because they both vote on the broadcast value v in view e and simultaneously contain ⊥ in the timeout message, violating the protocol flow.
- If there are timeout messages in containing a value conflicting with the value v, at most timeout messages in can contain the broadcast value v; otherwise, would lock the broadcast value. Therefore, there are at least timeout messages in that do not contain the broadcast value v. Sincethere are at least t intersecting nodes between the nodes sending these timeout messages and the corresponding nodes in the confirmation certificate . These t nodes can be labeled as Byzantine because they both vote for the broadcast value v in view e and simultaneously fail to include v in the timeout message, violating the protocol flow. Furthermore, since there are timeout messages in that contain values conflicting with the broadcast value v, this indicates that the leader of view e has proposed conflicting broadcast values and can also be labeled as a Byzantine node. Thus, the forensic protocol can identify a total of Byzantine nodes.
- Case 2:
- the view number of is equal to e
- There is no timeout message in that contains a value conflicting with the broadcast value . In this case, the timeout messages in can only contain the broadcast value or ⊥, but not the broadcast value v. Sincethere exist at least intersecting nodes between the node that sent these timeout messages and the node corresponding to the confirmation certificate . These nodes can be labeled as Byzantine nodes because they both vote for the broadcast value v in view e and simultaneously do not include the broadcast value v in the timeout message, violating the protocol flow.
- There are timeout messages in that contain values conflicting with the broadcast value . In this case, there are at least timeout messages in that contain the broadcast value . Sincethere exist at least t intersecting nodes between the set of nodes sending these timeout messages and the set of nodes corresponding to the confirmation certificate . These t nodes can be labeled as Byzantine nodes because they both vote for the broadcast value v in view e and simultaneously include the broadcast value in the timeout message, violating the protocol flow of Abraham et al.’s BB. In addition, the leader of view e can also be labeled as a Byzantine node due to issuing conflicting broadcast values. Therefore, the forensic protocol described in Algorithm 1 can label at least Byzantine nodes.
6. Impossible Conclusion Regarding Forensic Support for Abraham et al.’s BB Protocols
6.1. Overview of the Proof
6.2. Proof of Conclusions
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
References
- Lamport, L.; Shostak, R.; Pease, M. The Byzantine generals problem. In Concurrency: The Works of Leslie Lamport; Association for Computing Machinery: New York, NY, USA, 2019; pp. 203–226. [Google Scholar]
- Yao, A.C. Protocols for secure computations. In Proceedings of the 23rd Annual Symposium on Foundations of Computer Science (SFCS 1982), Chicago, IL, USA, 3–5 November 1982; pp. 160–164. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An overview of blockchain technology: Architecture, consensus, and future trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; pp. 557–564. [Google Scholar]
- Abraham, I.; Nayak, K.; Ren, L.; Xiang, Z. Good-case latency of byzantine broadcast: A complete categorization. In Proceedings of the 2021 ACM Symposium on Principles of Distributed Computing, Virtual, 26–30 July 2021; pp. 331–341. [Google Scholar]
- Castro, M.; Liskov, B. Practical byzantine fault tolerance. In Proceedings of the OSDI, New Orleans, LA, USA, 22–25 February 1999; Volume 99, pp. 173–186. [Google Scholar]
- Martin, J.P.; Alvisi, L. Fast byzantine consensus. IEEE Trans. Dependable Secur. Comput. 2006, 3, 202–215. [Google Scholar] [CrossRef]
- Abraham, I.; Nayak, K.; Ren, L.; Xiang, Z. Brief announcement: Byzantine agreement, broadcast and state machine replication with optimal good-case latency. In Proceedings of the 34th International Symposium on Distributed Computing (DISC 2020), Virtual, 12–16 October 2020; pp. 47:1–47:3. [Google Scholar]
- Dolev, D.; Strong, H.R. Authenticated algorithms for Byzantine agreement. SIAM J. Comput. 1983, 12, 656–666. [Google Scholar] [CrossRef]
- Sheng, P.; Wang, G.; Nayak, K.; Kannan, S.; Viswanath, P. BFT protocol forensics. In Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security, Virtual, 15–19 November 2021; pp. 1722–1743. [Google Scholar]
- Buterin, V.; Griffith, V. Casper the friendly finality gadget. arXiv 2017, arXiv:1710.09437. [Google Scholar]
- Buchman, E. Tendermint: Byzantine Fault Tolerance in the Age of Blockchains. Ph.D. Thesis, University of Guelph, Guelph, ON, Canada, 2016. [Google Scholar]
- Lamport, L. The part-time parliament. In Concurrency: The Works of Leslie Lamport; Association for Computing Machinery: New York, NY, USA, 2019; pp. 277–317. [Google Scholar]
- Corbett, J.C.; Dean, J.; Epstein, M.; Fikes, A.; Frost, C.; Furman, J.J.; Ghemawat, S.; Gubarev, A.; Heiser, C.; Hochschild, P.; et al. Spanner: Google’s globally distributed database. ACM Trans. Comput. Syst. (TOCS) 2013, 31, 8. [Google Scholar] [CrossRef]
- Apache ZooKeeper. Welcome to Apache Zookeeper. 2013. Available online: https://zookeeper.apache.org/ (accessed on 24 April 2025).
- Van Renesse, R.; Altinbuken, D. Paxos made moderately complex. ACM Comput. Surv. (CSUR) 2015, 47, 42. [Google Scholar] [CrossRef]
- Ongaro, D.; Ousterhout, J. In search of an understandable consensus algorithm. In Proceedings of the 2014 USENIX Annual Technical Conference (USENIX ATC 14), Philadelphia, PA, USA, 19–20 June 2014; pp. 305–319. [Google Scholar]
- Roohitavaf, M.; Ahn, J.S.; Kang, W.H.; Ren, K.; Zhang, G.; Ben-Romdhane, S.; Kulkarni, S.S. Session guarantees with raft and hybrid logical clocks. In Proceedings of the 20th International Conference on Distributed Computing and Networking, Bangalore, India, 4–7 January 2019; pp. 100–109. [Google Scholar]
- Taft, R.; Sharif, I.; Matei, A.; VanBenschoten, N.; Lewis, J.; Grieger, T.; Niemi, K.; Woods, A.; Birzin, A.; Poss, R.; et al. Cockroachdb: The resilient geo-distributed sql database. In Proceedings of the 2020 ACM SIGMOD International Conference on Management of Data, Portland, OR, USA, 14–19 June 2020; pp. 1493–1509. [Google Scholar]
- Giridharan, N.; Suri-Payer, F.; Ding, M.; Howard, H.; Abraham, I.; Crooks, N. Beegees: Stayin’alive in chained bft. In Proceedings of the 2023 ACM Symposium on Principles of Distributed Computing, Orlando, FL, USA, 19–23 June 2023; pp. 233–243. [Google Scholar]
- Giridharan, N.; Suri-Payer, F.; Abraham, I.; Alvisi, L.; Crooks, N. Autobahn: Seamless high speed BFT. In Proceedings of the ACM SIGOPS 30th Symposium on Operating Systems Principles, Austin, TX, USA, 4–6 November 2024; pp. 1–23. [Google Scholar]
- Haeberlen, A.; Kouznetsov, P.; Druschel, P. PeerReview: Practical accountability for distributed systems. ACM SIGOPS Oper. Syst. Rev. 2007, 41, 175–188. [Google Scholar] [CrossRef]
- Tang, W.; Sheng, P.; Roy, P.; Wang, X.; Fanti, G.; Viswanath, P. Raft-Forensics: High Performance CFT Consensus with Accountability for Byzantine Faults. arXiv 2023, arXiv:2305.09123. [Google Scholar]
- Civit, P.; Gilbert, S.; Gramoli, V. Polygraph: Accountable byzantine agreement. In Proceedings of the 2021 IEEE 41st International Conference on Distributed Computing Systems (ICDCS), Washington, DC, USA, 7–10 July 2021; pp. 403–413. [Google Scholar]
- Yin, M.; Malkhi, D.; Reiter, M.K.; Gueta, G.G.; Abraham, I. HotStuff: BFT consensus with linearity and responsiveness. In Proceedings of the 2019 ACM Symposium on Principles of Distributed Computing, Toronto, ON, Canada, 29 July–2 August 2019; pp. 347–356. [Google Scholar]
- Gilad, Y.; Hemo, R.; Micali, S.; Vlachos, G.; Zeldovich, N. Algorand: Scaling byzantine agreements for cryptocurrencies. In Proceedings of the 26th Symposium on Operating Systems Principles, Shanghai, China, 28–31 October 2017; pp. 51–68. [Google Scholar]
- Baudet, M.; Ching, A.; Chursin, A.; Danezis, G.; Garillot, F.; Li, Z.; Malkhi, D.; Naor, O.; Perelman, D.; Sonnino, A. State Machine Replication in the Libra Blockchain; The Libra Assosiation Technical Report; The Diem Association: Geneva, Switzerland, 2019. [Google Scholar]
- Ranchal-Pedrosa, A.; Gramoli, V. Blockchain is dead, long live blockchain! accountable state machine replication for longlasting blockchain. arXiv 2020, arXiv:2007.10541. [Google Scholar]
- Tas, E.N.; Adler, J.; Al-Bassam, M.; Khoffi, I.; Tse, D.; Vaziri, N. Accountable safety for rollups. arXiv 2022, arXiv:2210.15017. [Google Scholar]
- Adler, J.; Quintyne-Collins, M. Building scalable decentralized payment systems. arXiv 2019, arXiv:1904.06441. [Google Scholar]
- Sheng, P.; Wang, G.; Nayak, K.; Kannan, S.; Viswanath, P. Player-replaceability and forensic support are two sides of the same (crypto) coin. In Proceedings of the International Conference on Financial Cryptography and Data Security, Bol, Brač, Croatia, 1–5 May 2023; pp. 56–74. [Google Scholar]
- Dwork, C.; Lynch, N.; Stockmeyer, L. Consensus in the presence of partial synchrony. J. ACM (JACM) 1988, 35, 288–323. [Google Scholar] [CrossRef]


| Protocol | m | k | d |
|---|---|---|---|
| HotStuff-view [9] | 1 | ||
| HotStuff-hash [9] | |||
| Ours | 1 |
| Symbol | Description |
|---|---|
| n | total number of nodes in the system |
| t | maximum number of Byzantine nodes the system can tolerate |
| f | the number of nodes actually controlled by the adversary |
| public and private key for each node | |
| m 1 | message sent by the node |
| message signed by the i-th node |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
You, Q.; Yang, H.; Zhang, X.; Jiang, X.; Guo, K.; Hu, K. Forensic Support for Abraham et al.’s BB Protocol. Entropy 2025, 27, 504. https://doi.org/10.3390/e27050504
You Q, Yang H, Zhang X, Jiang X, Guo K, Hu K. Forensic Support for Abraham et al.’s BB Protocol. Entropy. 2025; 27(5):504. https://doi.org/10.3390/e27050504
Chicago/Turabian StyleYou, Qidi, Hongjian Yang, Xiyong Zhang, Xiaotong Jiang, Kaiwen Guo, and Kexin Hu. 2025. "Forensic Support for Abraham et al.’s BB Protocol" Entropy 27, no. 5: 504. https://doi.org/10.3390/e27050504
APA StyleYou, Q., Yang, H., Zhang, X., Jiang, X., Guo, K., & Hu, K. (2025). Forensic Support for Abraham et al.’s BB Protocol. Entropy, 27(5), 504. https://doi.org/10.3390/e27050504





