1. Introduction
Classical encryption methods rely on computational complexity, which exposes them to the risk of being compromised by future advances in computability. In contrast, quantum key distribution (QKD) guarantees the absolute security of information transmission by leveraging the fundamental principles of quantum mechanics [
1,
2,
3]. Since the inception of the first QKD protocol, namely the BB84 protocol [
4], it has ignited a surge of research interest in the field of QKD. In QKD systems, single photons serve as the carriers of quantum keys, which cannot be amplified and are easily scattered or absorbed by the transmission channel. For the transmittance channel
, the secure key rate (SKR) cannot exceed the PLOB (Pirandola, Laurenza, Ottaviani, and Banchi) bound
[
5], which represents the exact SKR limit for point-to-point QKD systems without quantum repeaters.
Twin-field (TF) QKD [
6] utilizes single-photon interference for key generation, surpassing the PLOB bound, while also retaining immunity to detector-side attacks. Nevertheless, in order to maintain the coherence between distant quantum states, TF-QKD requires the deployment of global phase locking technology [
7,
8], leading to increased complexity and additional resource consumption within QKD systems. Fortunately, the recently proposed mode pairing (MP) QKD protocol [
9,
10] eliminates the requirement for global phase locking while also surpassing the repeaterless bound. Given its exceptional performance in laboratory [
11,
12] and field environments [
13,
14], the MP-QKD protocol has established itself as a robust candidate for the future deployment of quantum communication networks.
In scenarios involving geographical disparities (e.g., in star-shaped quantum communication networks [
15]), or when the communicating parties (Alice and Bob) are situated in moving free spaces (e.g., drones, ships, satellites, etc.), challenges are posed in achieving symmetric communication with the central node, Charlie. Introducing additional losses to compensate for channel asymmetry is a solution, but it results in suboptimal SKR [
16]. Previous analyses of the asymmetric MP-QKD protocol [
17,
18] required ideal decoy state assumptions and infinite-key, which are overly idealized and impractical. Thus, it is crucial to account for the finite-key size effects in the asymmetric MP-QKD protocol while considering practical decoy state deployment.
In this paper, we evaluate the performance of the MP-QKD protocol with asymmetric channels. Through employing the practical decoy state method and the universally composable framework, we analyzed the security of the asymmetric MP-QKD protocol with finite-key size. By employing our modified particle swarm optimization (PSO) algorithm, we globally optimized the 10 independent parameters of the decoy state MP-QKD protocol. Our modified PSO algorithm is more suitable for asymmetric MP-QKD, as it does not rely on the specific form or gradient information of the SKR function, demonstrating robust global search capabilities. Numerical simulation results show that when the distance difference between Alice–Charlie and Bob–Charlie is 50 km and 100 km, the SKRs with the asymmetric intensity strategy show a significant improvement compared to those obtained using the extra attenuation method, though they remain lower than that of the symmetric channel. We further present the relationship curves between signal and decoy state intensities (probabilities) and channel loss, and provide an analysis to explain the observed differences. Finally, we examine the effect of the maximum pairing interval on the performance of the asymmetric MP-QKD protocol.
2. Finite-Key Analysis for MP-QKD with Asymmetric Channels
Since the key size in practical implementations is not infinite, it is crucial to develop a framework that addresses the finite-key size effect. In previous studies on asymmetric MP-QKD [
17,
18], the key size was often assumed to be infinite, leading to overly idealized parameter estimation. In the following analysis, we extend the consideration from the infinite-key regime to the realistic finite-key scenario. At the end of the asymmetric MP-QKD protocol, Alice and Bob each share a key string, denoted as
and
, respectively. According to the universally composable framework [
19], if these key strings satisfy both
-correct and
-secret, they are considered secure keys.
-correct refers to
. And
-secret requires satisfaction of the condition
where
denotes the trace norm,
is the density operator of the system of Alice and Eve,
is the uniform mixture of all possible values of the bit string
, and
is density operator of Eve’s system. In this way, the protocol with finite-key can be regarded as
-secure, where
. In addition, we fix the security bound to
.
In the following finite-key analysis of the asymmetric MP-QKD protocol, we assume the distances from Alice and Bob to Charlie are denoted as and , where and . In the i-th round, Alice prepares the coherent state , where intensity is randomly selected from with probabilities . And modulated phase is randomly chosen from , where is typically set to 16. In parallel, Bob randomly selects and to prepare the coherent state with probabilities . It is important to note that in asymmetric channels, except for the case where , the intensity and probability settings of Alice and Bob are unequal. Therefore, full parameter optimization is required to achieve the maximum SKR. After interference measurement, Charlie announces the measurement outcomes (0 represents “no click”, while 1 represents “click”). is considered as an effective detection. After N rounds, Alice and Bob pair each click with its immediate next neighbor within a maximum pairing interval l to form a successful pairing.
According to the intensities of the paired
i-th and
j-th rounds (
), Alice (Bob) labels the “basis” as illustrated in
Table 1.
Subsequently, Alice and Bob announce the basis, and the sum of the intensity pairs
for each pairing. Subsequently, they perform the pair assignment based on
Table 2. Notably, the 0-pair data are retained specifically for decoy-state parameter estimation.
For each Z-pair on location i, j, Alice (Bob) extracts a bit 0 when (), and a bit 1 when (). For each X-pair on location i, j, Alice (Bob) extracts a bit from the relative phase and announces the alignment angle . Alice and Bob only retain the results with or . In particular, when , Bob flips the bit. Thus, Alice (Bob) can then obtain the sifted key strings () and (), derived, respectively, from the Z-pair and the X-pair. According to the decoy state method, () is employed for generating secure keys, while () is used to estimate the phase-error rate.
In finite-key scenarios, sifted keys may contain some errors. Here, error correction and privacy amplification are required to ensure both
-correct and
-secret of the keys. Alice sends
bits to Bob for performing key reconciliation, through which Bob computes an estimate
of
. Alice computes a hash of
of length
with a random
hash function [
20], which she sends to Bob together with the hash. If hash(
) = hash(
), this guarantees the
-correct of the keys; otherwise, the protocol aborts.
To ensure the security of final secure keys, Alice and Bob employ the privacy amplification based on the Quantum Leftover Hash Lemma [
21,
22], which offers a clear operational interpretation of smooth min-entropy. According to a random
hash function is used to extract an
-secret key of length
from
, where
Here,
summarizes all information Eve learned about
during the protocol. Based on a chain rule inequality [
23], the smooth min-entropy
can be represented as
where
is the information before error correction,
,
f is the error correction efficiency,
represents the number of pairs
for
Z-basis, and
denotes the corresponding bit error rate. Furthermore, the strings
can be partitioned into two subsets:
, which contains bits where both Alice and Bob each send a single photon, and
, which comprises all remaining bits. Considering the smooth entropies from the uncertainty relation [
22,
24], we find that
where
and
. It is evident that the single-photon components prepared in the
Z- and
X-bases are mutually unbiased. We denote
(and
) as the bit string that Alice (and Bob) would have obtained had they performed measurements in the
X basis instead of the
Z basis. The quantity
can be reformulated using the entropic uncertainty relation:
where
denotes a lower bound on the length of
,
represents the number of bits required for Bob to use the bit string
to reconstruct
,
is the phase-error rate associated with the single-photon pair events in the
Z-basis,
.
We can set
without compromising security. The total secrecy parameter is given by
where
, with
and
representing the failure probabilities in estimating
and
, respectively. The term
denotes the failure probability associated with privacy amplification. By combining Equations (
2)–(
5), the final secure key length is
As long as the final key length satisfies Equation (
6), the asymmetric MP-QKD protocol is
-secure. The finite-key security analysis based on the entropy uncertainty relation method only requires consideration of the statistical fluctuations in observed quantities, without the need to account for additional information leakage. Here, the Chernoff bound [
25] is employed to calculate the statistical fluctuations. Given an observed quantity
, the upper
and lower
bounds of the expected value are given by,
where
, and
is the failure probability of the Chernoff bound.
3. Simulation and Discussion
Since the number of single-photon pair events
in the
Z-basis and the phase-error rate associated with the single-photon pair events
in the
Z-basis cannot be directly observed, through the decoy state method [
12,
26,
27,
28,
29], we can discover the yield of
Z-pair single photon pulse pairs
where
Here,
,
and
are the number of the effective detection for the intensity pairs
after the statistical fluctuations in the
Z-pairs,
is the expected number of pairs with
. For simplicity, here we only use the
Z-basis pairs with intensities
for key generation. Thus,
.
The single-photon bit error rate of
X-pair can be expressed as
where
and
and
are the error effective detection for the
after the statistical fluctuations in the
X-pairs. Through a random-sampling theory without replacement [
30,
31,
32],
can be written as
where
is the failure probability of random sampling without replacement.
represent the number of single-photon pair events in the
X-basis. After calculating
and
, the secure key length for the asymmetric MP-QKD protocol under finite key analysis can be obtained by applying Equation (
6). The SKR is defined as
, where
N is the number of total pluses.
It should be clearly stated that although some studies have analyzed asymmetric MP-QKD, there remain certain limitations. For instance, Ref. [
10] focuses solely on the advantage of asymmetric MP-QKD over TF-QKD, without examining the impact of channel asymmetry on the intensities and probabilities of decoy states. Additionally, Refs. [
17,
18] assumes that the decoy-state parameter estimation either meets idealized conditions or is performed with perfect accuracy, which is not representative of practical scenarios. For the gaps in their work, we have performed a thorough analysis addressing the effects of asymmetric channels on decoy-state parameters under practical conditions.
Here, we can consider the SKR as a function of the source parameters
Given the uncertainty of the convex form of function
R, we employ the modified PSO algorithm (detailed in
Appendix A) for global optimization of the 10 parameters rather than the local search algorithm (LSA) [
33,
34,
35]. The LSA is highly sensitive to the selection of the initial point, as a randomly chosen initial point can often result in an invalid or infeasible outcome. The modified PSO algorithm can optimize non-smooth and non-convex functions to search for the optimal
that maximizes
R. It is especially effective for asymmetric MP-QKD because it does not depend on the specific form or gradient information of the SKR function, and it does not require an initial starting point, showing robust global search abilities. In comparison with the original PSO algorithm [
36], the modified version demonstrates an improved balance between global exploration and local exploitation, strengthened particle coordination, and enhanced optimization efficiency and convergence speed. We note that Ref. [
10] employs a genetic algorithm for parameter optimization, whereas our use of a modified PSO algorithm offers a simpler implementation with faster convergence and lower computational complexity, making it more suitable for practical deployment scenarios.
In the simulation, we employed an asymmetric intensity strategy to address the asymmetric channel: by deploying the PSO algorithm to optimize
for compensating the channel asymmetry and achieving the optimal SKR. The simulation formulas for the observed values in asymmetric MP-QKD are provided in
Appendix B. Furthermore, we also compare this approach with the strategy of adding extra attenuation. It is important to note that in the simulation, we consider Alice’s and Bob’s source configurations as independent, satisfying
without imposing constraints such as
(or
), where
and
are the channel transmittance of Alice and Bob. The formula
(or
) is a rule of thumb on the ratio of intensities between Alice’s and Bob’s light [
37]. Equation (
15) imposes three constraints: the first line ensures that the intensity of the signal state is greater than that of the decoy state, which in turn is greater than that of the vacuum state; the second line enforces that the sum of the probabilities for the three states equals 1; and the third line guarantees that the individual probabilities for the signal, decoy, and vacuum states are all strictly between 0 and 1. The parameters employed for the numerical simulations are detailed in
Table 3. Additionally, we set
, where
,
.
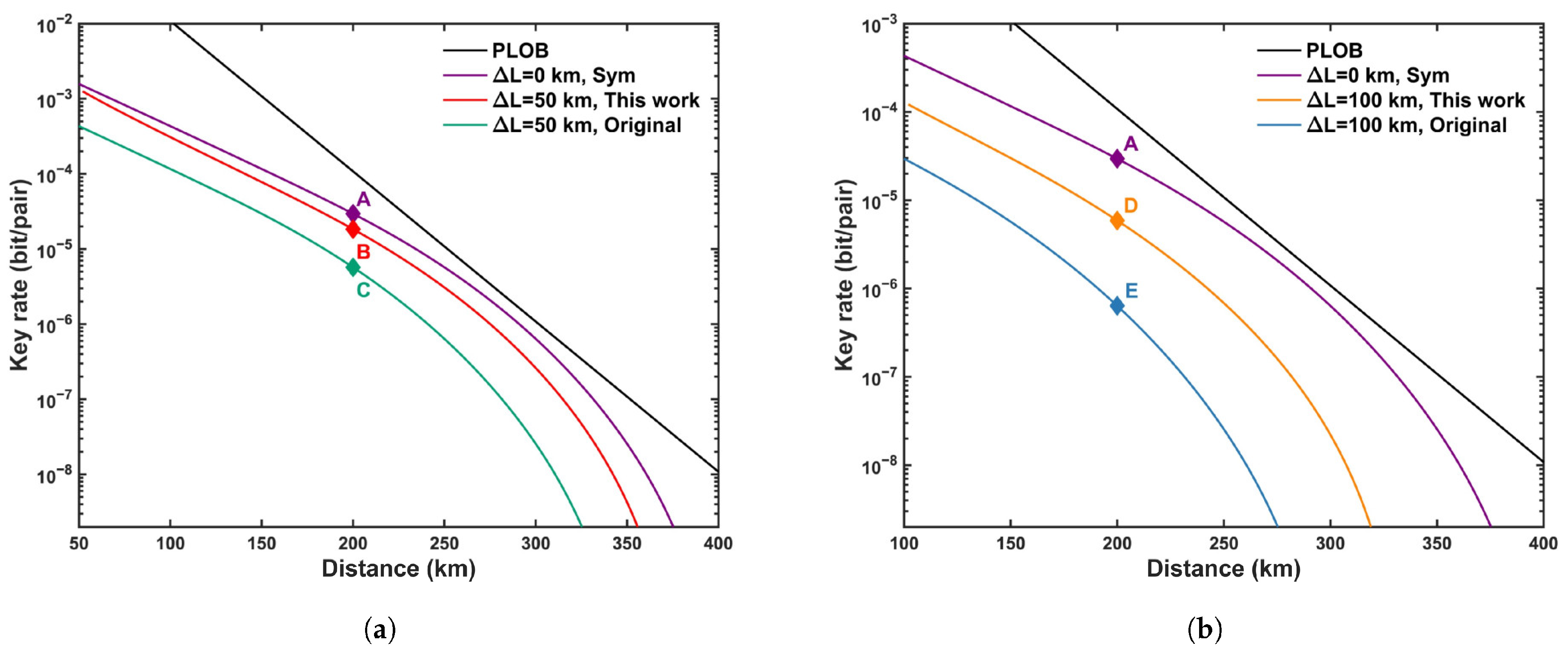
We plot the optimized SKR for the asymmetric scenario in
Figure 1 and the detailed optimization results at a distance of 200 km in
Table 4. From
Figure 1, it is evident that the SKR of the asymmetric intensities strategy consistently outperforms that of the adding extra attenuation, for both
and
. However, regardless of the strategy employed, the SKR does not achieve a level comparable to that of the symmetric channel case. The SKR for
experiences a significant decrease compared to
, indicating that an increase in channel asymmetry leads to a reduction in the SKR. As evident from
Table 4, the asymmetric intensities strategy exhibits a substantial increase of approximately an order of magnitude compared to the adding extra attenuation strategy when
km. All data in
Table 4 are optimized using the modified PSO algorithm. Furthermore, from points A, B, and D, it can be observed that Alice and Bob adjusted their intensities (probabilities) to compensate for the channel asymmetry. As
increases, to achieve the optimal Hong–Ou–Mandel (HOM) interference effect,
and
continuously decrease, while
and
increase.
In the asymmetric intensity strategy for MP-QKD, a primary concern is the optimal selection of weak coherent pulse intensities by Alice and Bob. While
(or
) may seem natural, we do not impose this constraint in the modified PSO algorithm.
Figure 2 depicts the variation of
and
for
km. It is evident that the magnitude of
remains predominantly near 1, although some deviations occur as the distance increases. The decoy state
(
) are primarily employed for estimating the phase error rate. The relationship
helps maintain a balance in the photon intensities reaching Charlie, ensuring good HOM visibility and low error rates. However, this relationship is derived under the assumptions of the infinite-key size, an infinite number of decoy states, and the neglect of dark counts. Therefore, discarding the ideal assumption mentioned above, slight deviations in
and
are reasonable for the scenario depicted in
Figure 2. Additionally, from
Figure 2, it can be observed that the value of
is significantly distant from 1, largely deviating from the condition
. The reason for this phenomenon is that the signal state is primarily used for key generation, where the intensity
(
) not only impacts the quantum bit error rate but also influences the probability of sending single photons and error correction. The optimal selection of signal states
(
) is a balance among quantum bit error rate, the probability of single-photon transmission, and error correction.
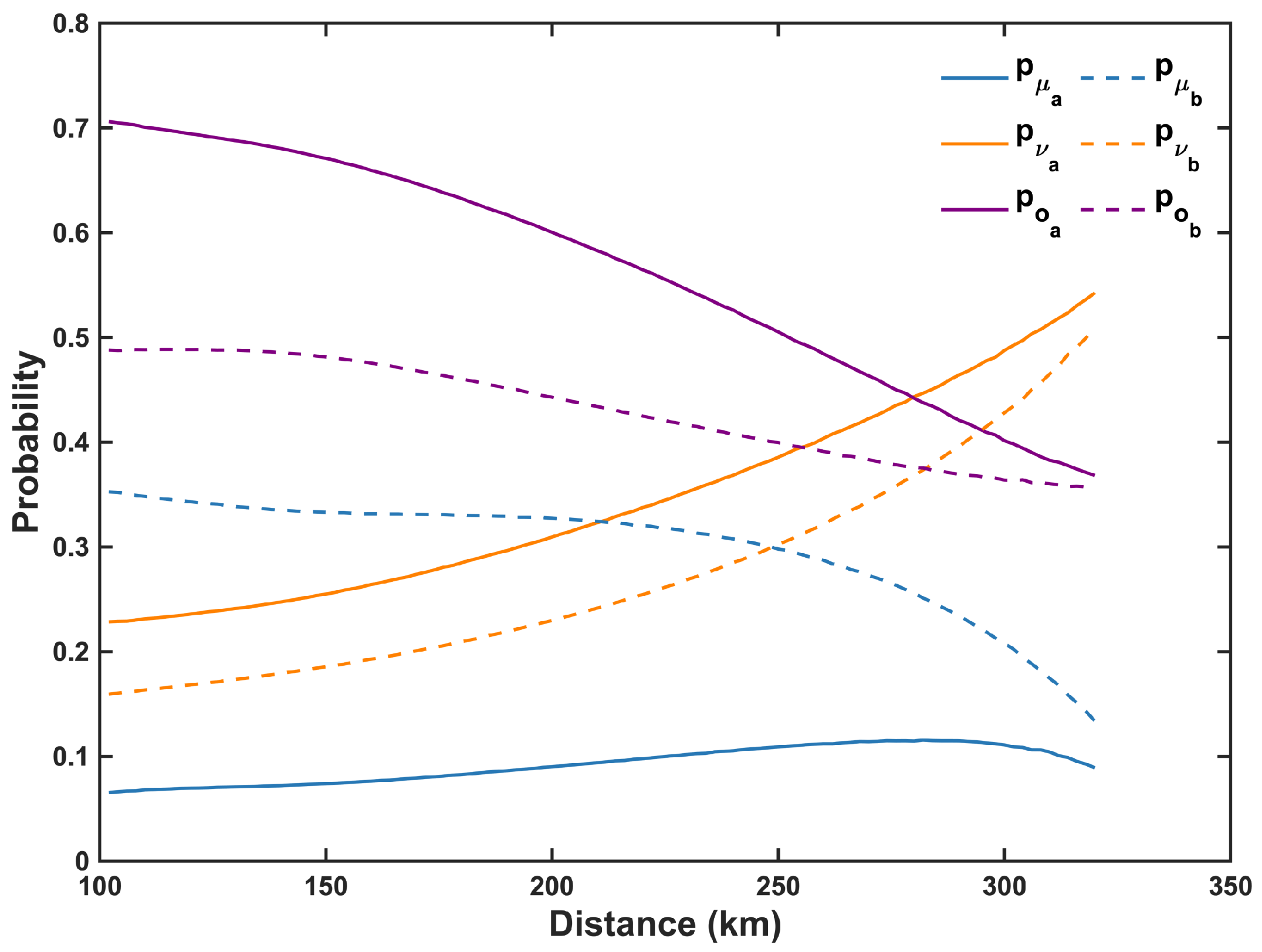
Figure 3 illustrates the variations in the probabilities of the signal, decoy, and vacuum states with asymmetric intensity strategy as the distance increases, when
km. It can be observed that as the distance increases, the probability of the signal states remains relatively stable in most cases, while the probability of the decoy states notably increases. As the distance increases and losses grow, an inevitable increase in the probability of the decoy states is necessary to achieve better HOM interference effects and lower error rates. We also notice a relatively high proportion of vacuum states, attributable to their contribution in the pairing of the
Z-basis, estimation of single-photon counts, and calculation of phase error rates. It is important to emphasize that for each optimization point in
Figure 2 and
Figure 3, the intensities and probabilities of the signal, decoy, and vacuum states strictly adhere to the constraints specified in Equation (
15), while the counts and count rates are required to satisfy the physical validity conditions outlined in Equation (
A1).
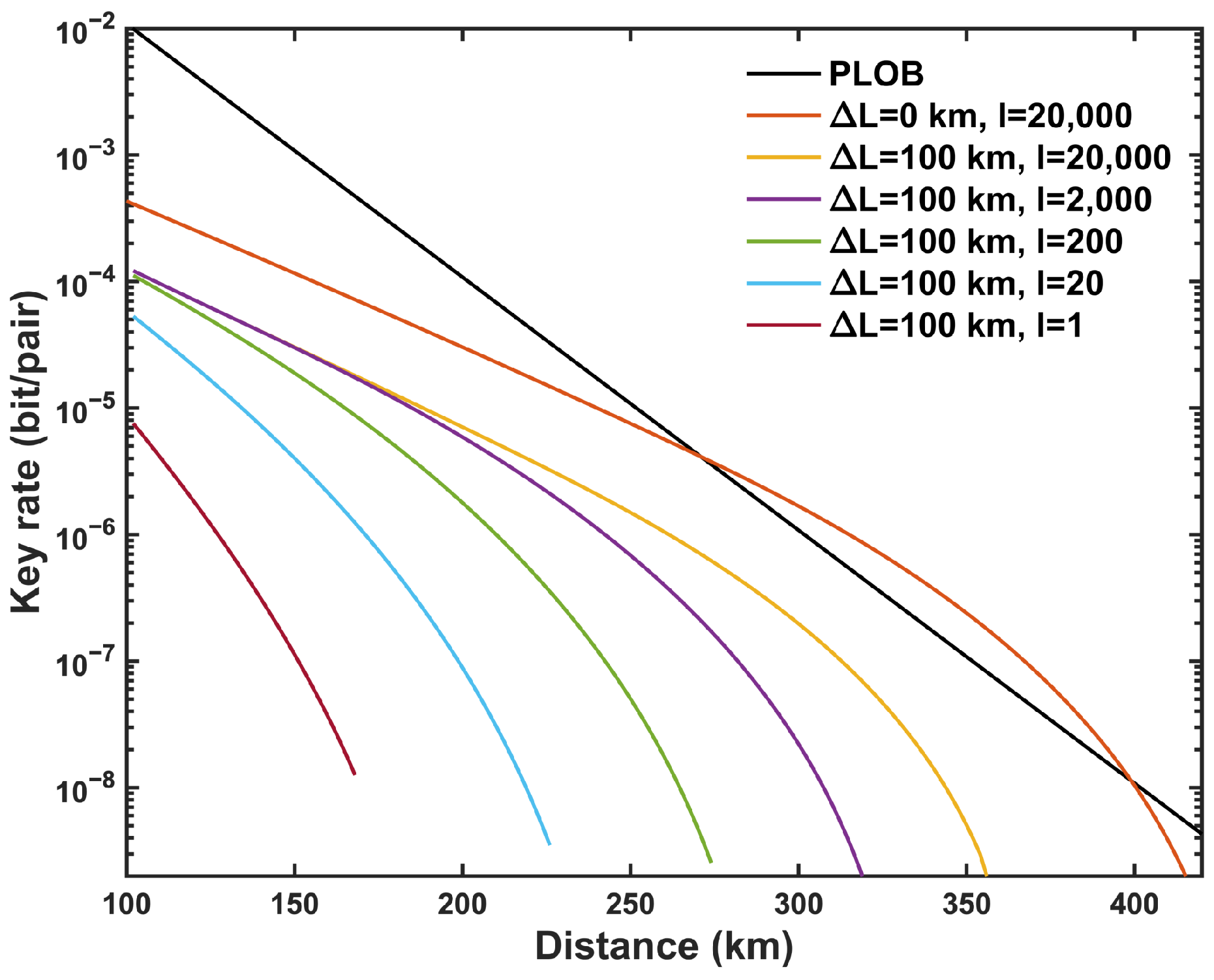
Figure 4 demonstrates the influence of different maximum pairing intervals
l on the SKR with asymmetric intensity strategy. With the increase in
l, the SKR in the asymmetric scenario shows a significant improvement but remains below that of the symmetric case, unable to surpass the PLOB bound. Additionally, as shown in
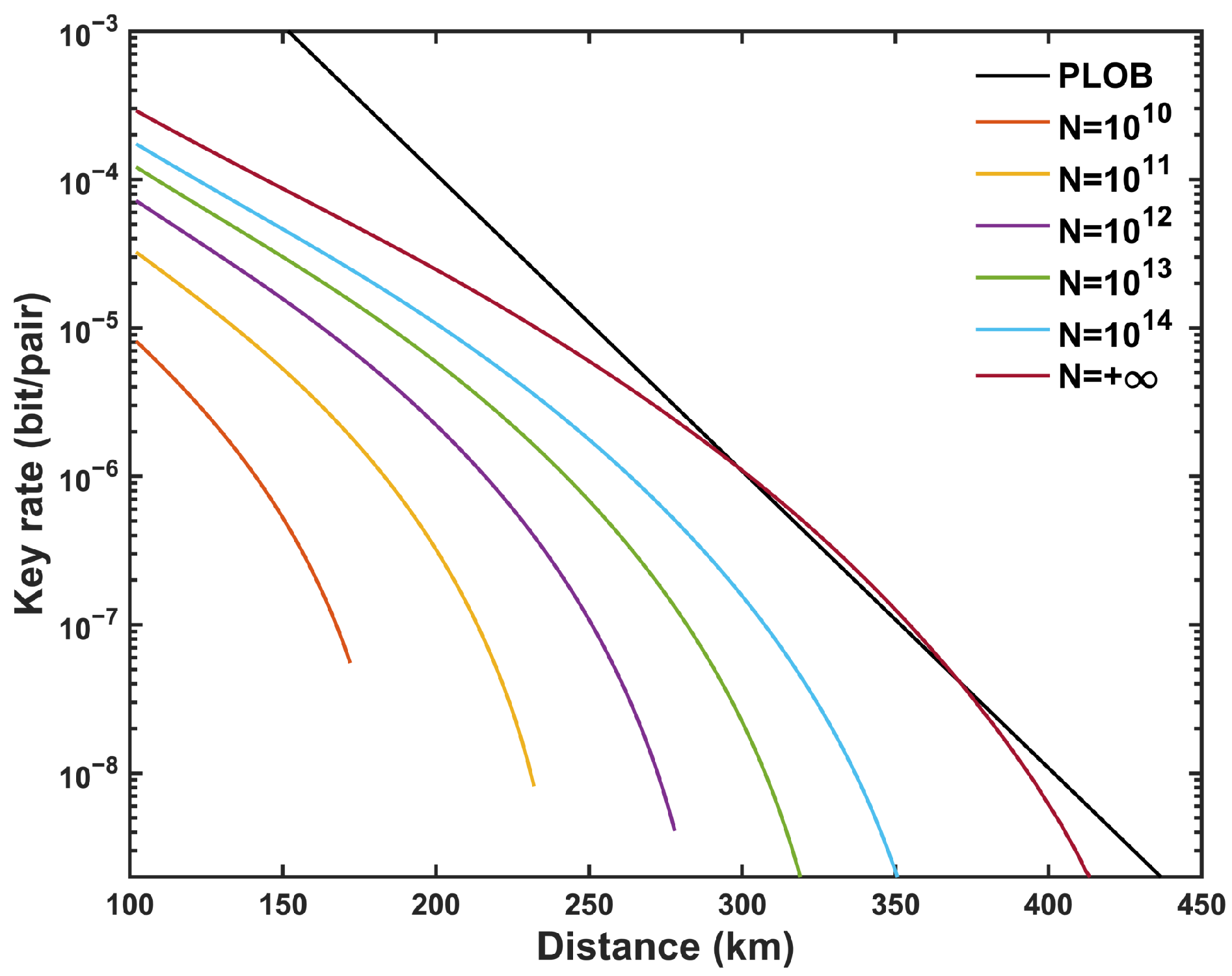
Figure 5, at long distances, the infinite-key scenario slightly surpasses the PLOB bound, representing the theoretical performance limit of MP-QKD in this regime. In contrast, under the finite-key condition, increasing the total number of pulses
N makes it challenging to surpass the PLOB bound due to statistical fluctuations and finite-size constraints.