A Zero-Touch Dynamic Configuration Management Framework for Time-Sensitive Networking (TSN)
Abstract
1. Introduction
- (1)
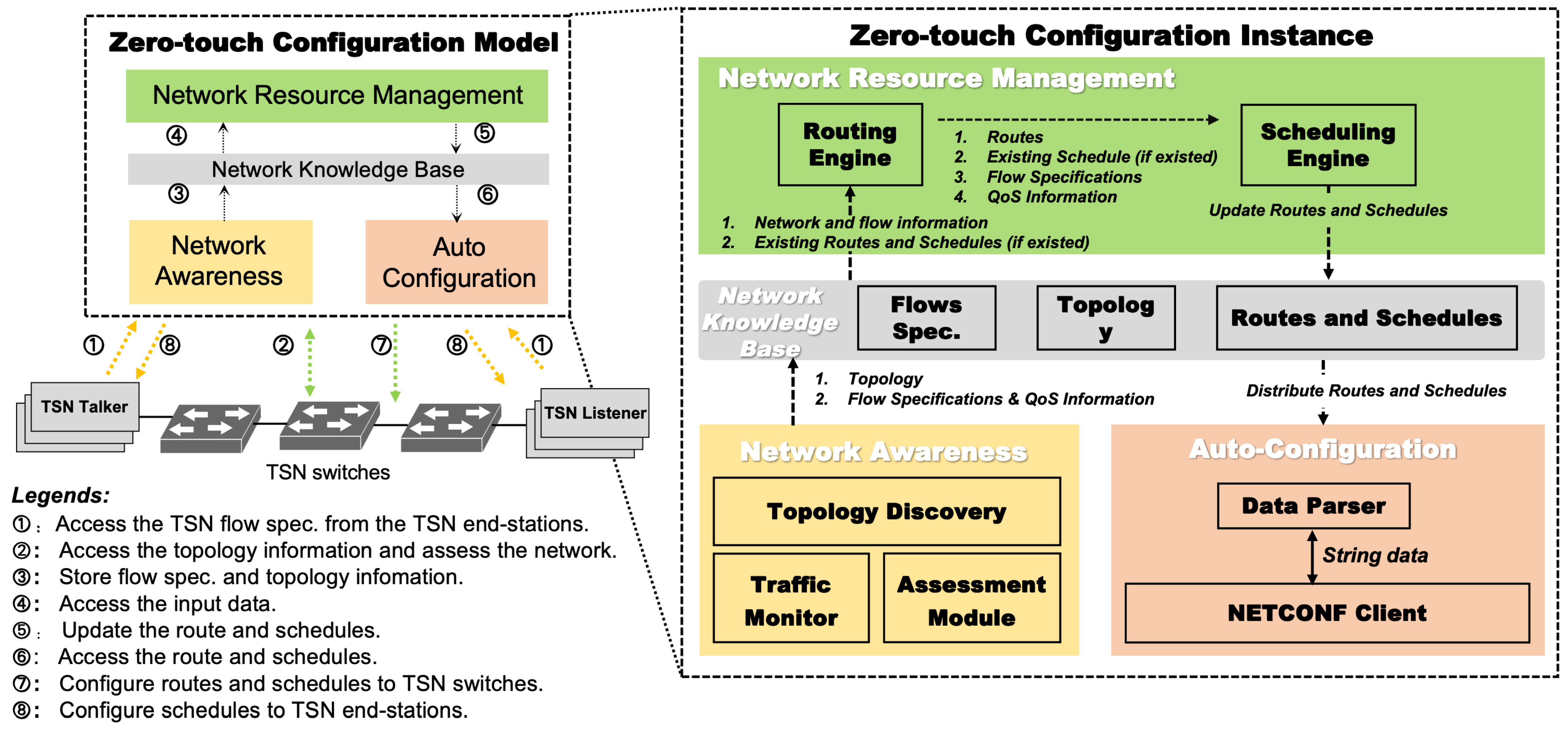
- A zero-touch configuration model is proposed to automatically detect network state changes, recalculate traffic paths and schedules, and configure these updates to network nodes in real-time.
- (2)
- The proposed DASPS algorithm formulates the delay constraint as a maximum hop count constraint and assigns the flow to the path with the most remaining bandwidth.
- (3)
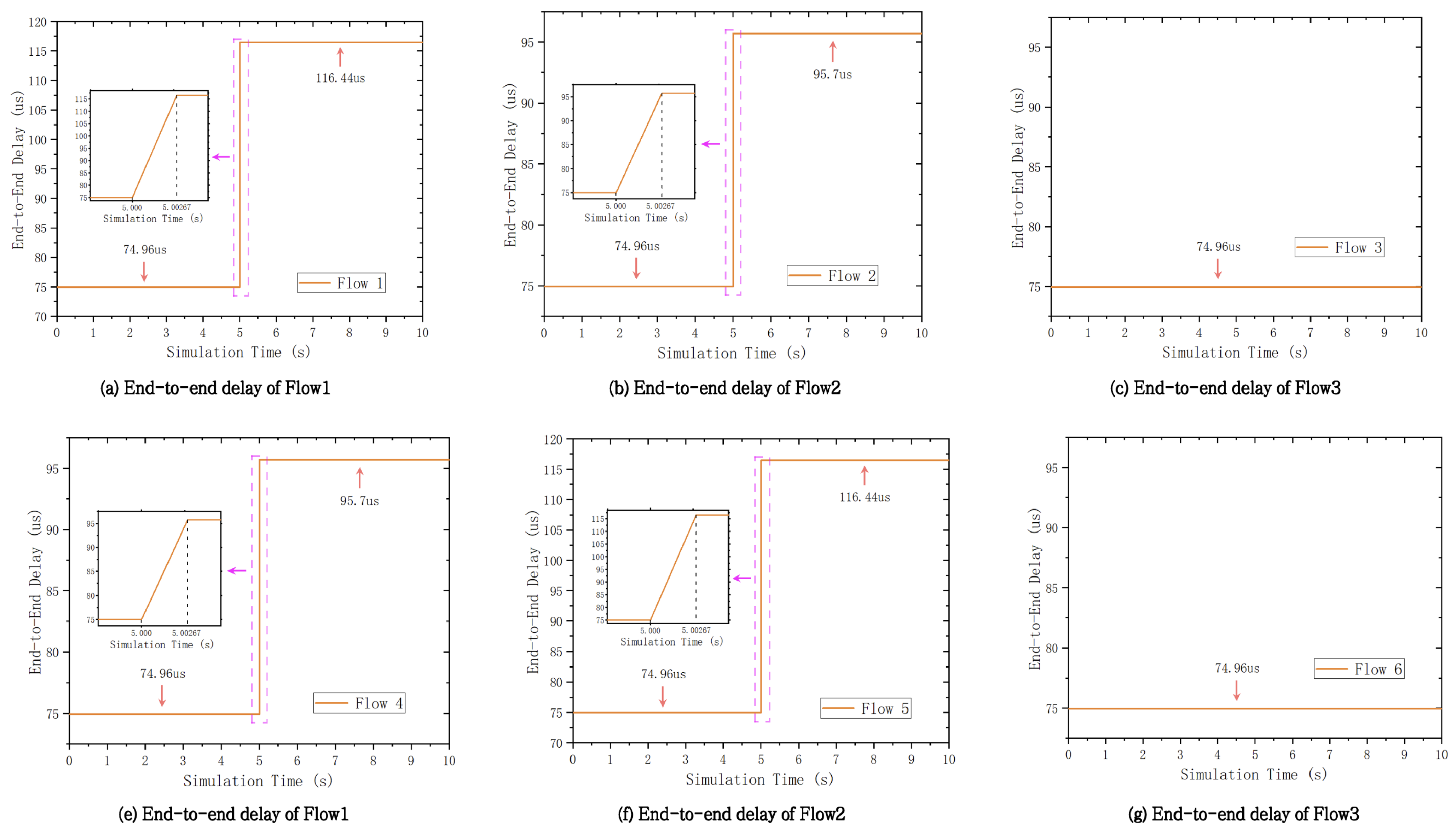
- Simulation experiments demonstrate that the proposed framework can reconfigure the network in 2.67 milliseconds. The DASPS algorithm significantly improves scheduling success rates compared to the SPS algorithm. Specifically, DASPS achieves a 70.22% scheduling success rate for 1000 TSN flows, while SPS only achieves 22.23%.
2. Dynamic Configuration Management Framework
2.1. Zero-Touch Configuration Model
2.2. DASPS Algorithm
| Algorithm 1: DASPS algorithm. |
 |
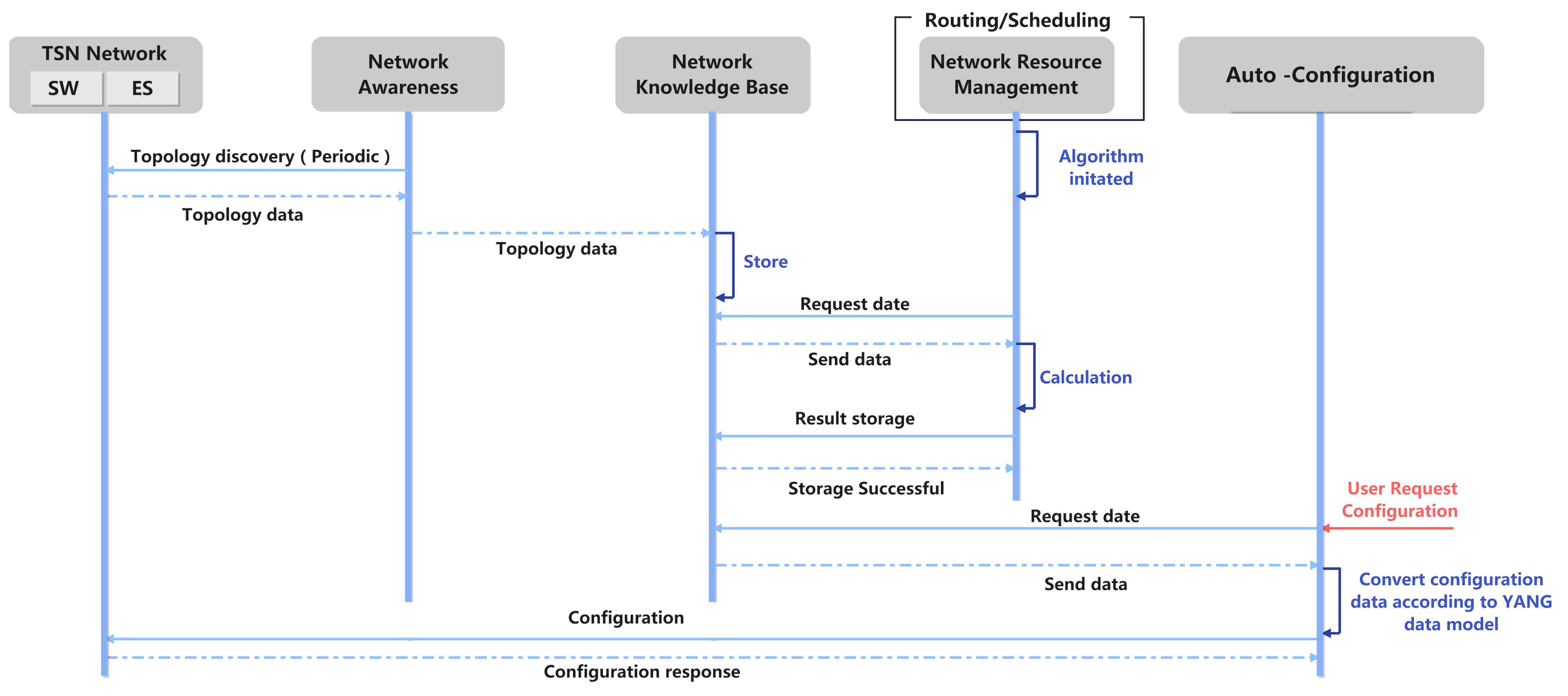
2.3. Configuration Procedure
3. Implementation and Evaluation
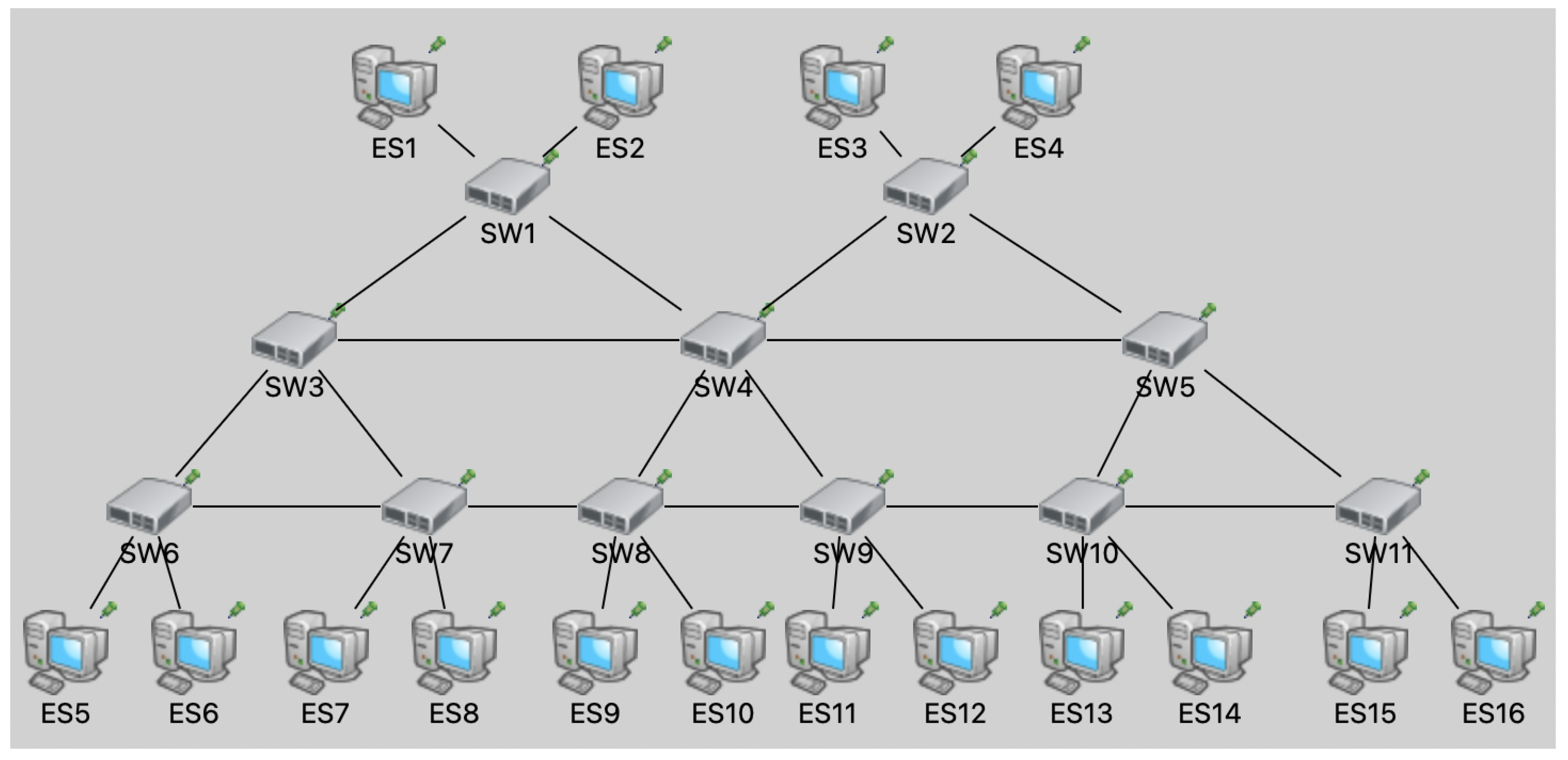
3.1. System Implementation
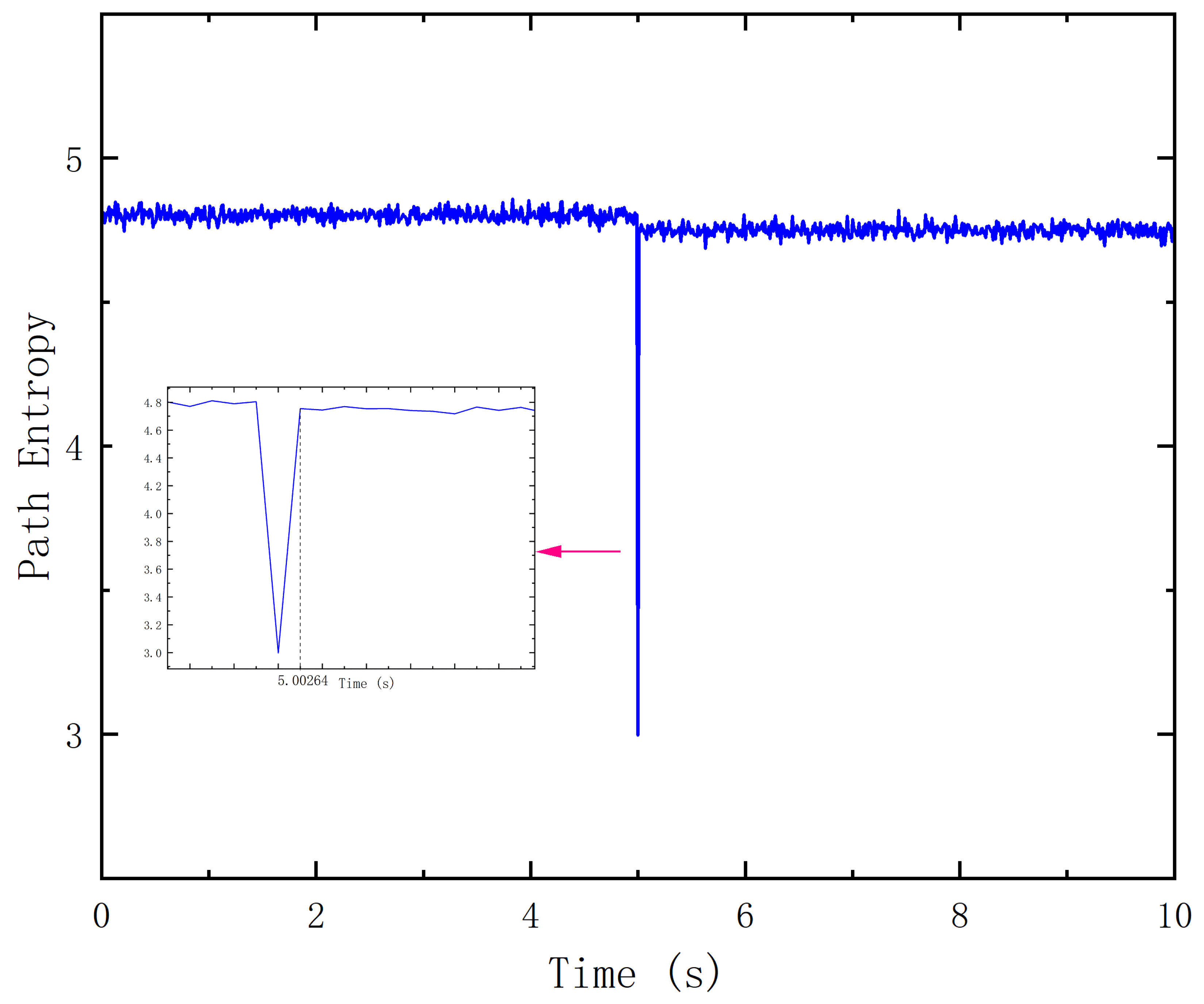
3.2. Numerical Results
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
References
- Leng, J.; Sha, W.; Wang, B.; Zheng, P.; Zhuang, C.; Liu, Q.; Wuest, T.; Mourtzis, D.; Wang, L. Industry 5.0: Prospect and retrospect. J. Manuf. Syst. 2022, 65, 279–295. [Google Scholar] [CrossRef]
- Shi, B.; Tu, X.; Wu, B.; Peng, Y. Recent advances in time-sensitive network configuration management: A literature review. J. Sens. Actuator Netw. 2023, 12, 52. [Google Scholar] [CrossRef]
- IEEE 802 Time-Sensitive Networking Task Group. IEEE 802 Time-Sensitive Networking. Available online: https://1.ieee802.org/tsn/ (accessed on 20 July 2024).
- Std 802.1AS-2020; Timing and Synchronization for Time-Sensitive Applications. IEEE: New York, NY, USA, 2020. Available online: https://standards.ieee.org/ieee/802.1AS/7121/ (accessed on 20 July 2024).
- Std 802.1Qbv-2015; Enhancements for Scheduled Traffic. IEEE: New York, NY, USA, 2015. Available online: https://standards.ieee.org/ieee/802.1Qbv/6068/ (accessed on 20 July 2024).
- Std 802.1CB-2017; Frame Replication and Elimination for Reliability. IEEE: New York, NY, USA, 2017; pp. 1–102. [CrossRef]
- Std 802.1Qcc-2018; Stream Reservation Protocol (SRP) Enhancements and Performance Improvements. IEEE: New York, NY, USA, 2018. Available online: https://standards.ieee.org/ieee/802.1Qcc/5784/ (accessed on 20 July 2024).
- Zezulka, F.; Marcon, P.; Bradac, Z.; Arm, J.; Benesl, T. Time-Sensitive Networking as the Communication Future of Industry 4.0. IFAC Pap. 2019, 52, 133–138. [Google Scholar] [CrossRef]
- Zhao, L.; Pop, P.; Steinhorst, S. Quantitative performance comparison of various traffic shapers in time-sensitive networking. IEEE Trans. Netw. Serv. Manag. 2022, 19, 2899–2928. [Google Scholar] [CrossRef]
- Xue, C.; Zhang, T.; Zhou, Y.; Nixon, M.; Loveless, A.; Han, S. Real-time scheduling for 802.1 Qbv time-sensitive networking (TSN): A systematic review and experimental study. In Proceedings of the 2024 IEEE 30th Real-Time and Embedded Technology and Applications Symposium (RTAS), Hong Kong, China, 13–16 May 2024; pp. 108–121. [Google Scholar]
- Chaine, P.J.; Boyer, M.; Pagetti, C.; Wartel, F. Egress-TT configurations for TSN networks. In Proceedings of the 30th International Conference on Real-Time Networks and Systems, Paris, France, 7–8 June 2022; pp. 58–69. [Google Scholar]
- Pang, Z.; Huang, X.; Li, Z.; Zhang, S.; Xu, Y.; Wan, H. Flow scheduling for conflict-free network updates in time-sensitive software-defined networks. IEEE Trans. Ind. Inform. 2020, 17, 1668–1678. [Google Scholar] [CrossRef]
- Craciunas, S.S.; Oliver, R.S. Out-of-sync schedule robustness for time-sensitive networks. In Proceedings of the 2021 17th IEEE International Conference on Factory Communication Systems (WFCS), Linz, Austria, 9–11 June 2021; pp. 75–82. [Google Scholar]
- Feng, Z.; Cai, M.; Deng, Q. An efficient pro-active fault-tolerance scheduling of IEEE 802.1 Qbv time-sensitive network. IEEE Internet Things J. 2021, 9, 14501–14510. [Google Scholar] [CrossRef]
- Huang, Z.; Zhu, H.; Zhang, H.; Huang, T. A scalable heuristic time-sensitive traffic scheduling algorithm for in-vehicle network. In Proceedings of the 2022 5th International Conference on Hot Information-Centric Networking (HotICN), Guangzhou, China, 24–26 November 2022; pp. 111–118. [Google Scholar]
- Zhang, Y.; Xu, Q.; Wang, S.; Chen, Y.; Xu, L.; Chen, C. Scalable no-wait scheduling with flow-aware model conversion in time-sensitive networking. In Proceedings of the GLOBECOM 2022–2022 IEEE Global Communications Conference, Rio de Janeiro, Brazil, 4–8 December 2022; pp. 413–418. [Google Scholar]
- Jiang, J.; Li, Y.; Zhang, X.; Yu, M.; Lee, C.D.; Hong, S.H. Assessing the traffic scheduling method for time-sensitive networking (TSN) by practical implementation. J. Ind. Inf. Integr. 2023, 33, 100464. [Google Scholar] [CrossRef]

| Parameter | Value |
|---|---|
| Link Speed | 1 Gbps |
| Link Length | 100 m |
| Python Version | 3.12 |
| CPU | Intel Core i9-12900 |
| RAM | 32 GB |
| Flow Name | Max. Hop Count | Actual Hop Count |
|---|---|---|
| Flow1 | 4 | 3 |
| Flow2 | 3 | 2 |
| Flow3 | 6 | 3 |
| Flow4 | 7 | 5 |
| Flow5 | 6 | 4 |
| Flow6 | 3 | 2 |
| Flow7 | 9 | 6 |
| Flow8 | 8 | 5 |
| Flow9 | 7 | 5 |
| Flow10 | 8 | 3 |
| Flow Name | Fault Status | Path |
|---|---|---|
| Flow1 | Pre | ES1, SW1, SW3, SW6, ES5 |
| Post | ES1, SW1, SW4, SW8, SW7, SW6, ES5 | |
| Flow2 | Pre | ES2, SW1, SW3, SW7, ES7 |
| Post | ES2, SW1, SW4, SW8, SW7, ES7 | |
| Flow3 | Pre | ES1, SW1, SW4, SW9, ES11 |
| Post | ES1, SW1, SW4, SW9, ES11 | |
| Flow4 | Pre | ES3, SW2, SW5, SW10, ES13 |
| Post | ES3, SW2, SW4, SW9, SW10, ES13 | |
| Flow5 | Pre | ES4, SW2, SW5, SW11, ES15 |
| Post | ES4, SW2, SW4, SW9, SW10, SW11, ES15 | |
| Flow6 | Pre | ES4, SW2, SW4, SW8, ES9 |
| Post | ES4, SW2, SW4, SW8, ES9 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jiang, J.; Jin, S.; Li, X.; Zhang, K.; Sun, B. A Zero-Touch Dynamic Configuration Management Framework for Time-Sensitive Networking (TSN). Entropy 2025, 27, 584. https://doi.org/10.3390/e27060584
Jiang J, Jin S, Li X, Zhang K, Sun B. A Zero-Touch Dynamic Configuration Management Framework for Time-Sensitive Networking (TSN). Entropy. 2025; 27(6):584. https://doi.org/10.3390/e27060584
Chicago/Turabian StyleJiang, Junhui, Shanyu Jin, Xinghan Li, Kaisong Zhang, and Baodan Sun. 2025. "A Zero-Touch Dynamic Configuration Management Framework for Time-Sensitive Networking (TSN)" Entropy 27, no. 6: 584. https://doi.org/10.3390/e27060584
APA StyleJiang, J., Jin, S., Li, X., Zhang, K., & Sun, B. (2025). A Zero-Touch Dynamic Configuration Management Framework for Time-Sensitive Networking (TSN). Entropy, 27(6), 584. https://doi.org/10.3390/e27060584






