Resilient Topology Reconfiguration for Industrial Internet of Things: A Feature-Driven Approach Against Heterogeneous Attacks
Abstract
1. Introduction
- Distributed Subnetwork Segmentation: We classify IIoT nodes into subnetworks based on localized attack features (degree, betweenness, or random), enabling targeted structural adaptations.
- Differentiated Topology Design: Small-world and scale-free configurations are tailored to subnetworks under intentional and random attacks, respectively, balancing robustness and efficiency.
- Real-World Validation: Experiments on a real-world datasets of radio frequency sensor networks (2113 nodes, 21 subnetworks) demonstrate significant improvements in connectivity and communication efficiency under four attack scenarios.
2. Problem Statement and Related Work
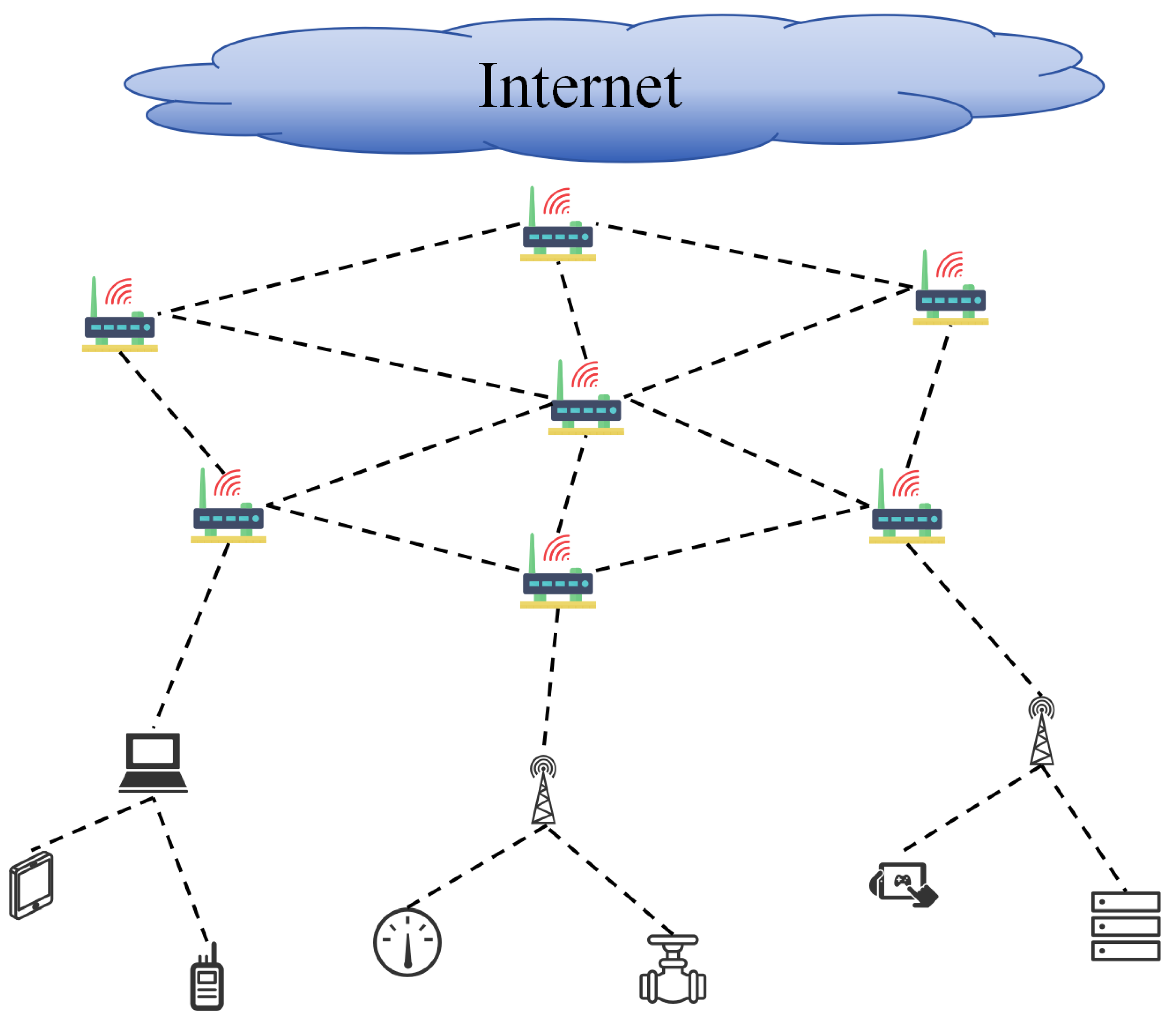
2.1. Topology Reconfiguration Problem Description
- Connectivity Integrity: Measured by the giant component size (), defined as the largest connected subgraph post-attack. A larger ensures sustained data interoperability among functional nodes.
- Communication Efficiency: Quantified via network average efficiency , which inversely correlates with path lengths between node pairs.
2.2. Related Work
- Topology Optimization:Chen et al. [14] pioneered scale-free network designs for IoT systems, demonstrating enhanced resilience against random attacks through hub node redundancy. However, their static approach fails to adapt to targeted attacks on critical nodes.Buesser et al. [15] employed simulated annealing to rewire edges in Barabási–Albert networks, preserving degree distributions while marginally improving intentional attack resistance. This method, however, restricts structural adaptability to predefined configurations.
- Node Deployment Strategies:Basu et al. [16] optimized mobile multirobot IoT systems via linear programming, dynamically relocating nodes to mitigate localized failures. While effective for physical disruptions, their method neglects cyber-attack vectors like betweenness exploitation.Tan et al. [17] introduced multihop neighbor-aware algorithms for mobile sensor networks, balancing coverage and robustness. Their energy-centric design lacks mechanisms to counter evolving attack patterns.
- Efficiency-Driven Architectures:Peng et al. [18] developed self-organizing wireless IoT schemes using neighbor overlap metrics, achieving energy efficiency gains of 18% over traditional models. Nevertheless, their topology prioritizes low latency over security considerations.Sohn [19] hybridized small-world and scale-free principles for IoT optimization but retained fixed network partitions, limiting responsiveness to heterogeneous threats.
- Security-Centric Enhancements:Musleh et al. [20] proposed multisensor time-prediction models for smart grids, reducing attack success rates by 22% in wide-area control systems. Their cryptographic focus, however, overlooks structural vulnerabilities.
3. Methodology
3.1. Attack Feature Taxonomy and Reconfiguration Framework
- Degree-based attacks: These attacks leverage the degree centrality principle in network theory, targeting nodes with the highest number of connections (degree). By compromising these hub nodes (e.g., core routers, authentication servers), attackers maximize network fragmentation through minimum effort. Behavior mechanism: Attackers first perform network reconnaissance to identify high-degree nodes, then deploy targeted exploits. For instance, DNS spoofing redirects traffic by compromising highly connected DNS servers, while SQL injection attacks frequently accessed database nodes to breach entire web ecosystems.
- Betweenness-based attacks: Focusing on nodes with maximum betweenness centrality—the bridges controlling shortest paths between node pairs—these attacks strategically disrupt critical communication channels. Behavior pattern: Attackers use flow analysis algorithms to identify bottleneck nodes, then launch precision strikes. For example, DDoS attacks flood border gateways (high-betweenness nodes) to collapse inter-subnet traffic, while ransomware encryption specifically targets file servers mediating departmental data exchange.
- Random attacks: Employing stochastic strategies independent of network topology, these attacks exploit systemic vulnerabilities through non-selective penetration attempts. Behavior characteristics: Attackers use automated scanning tools for blind probing without target profiling. The zero-day exploits randomly test unpatched vulnerabilities across all nodes, while phishing campaigns blast generic deceptive messages network-wide.
3.2. General Model of IIoT Topology Reconfiguration
3.3. Proposed Feature-Driven Reconfiguration Method
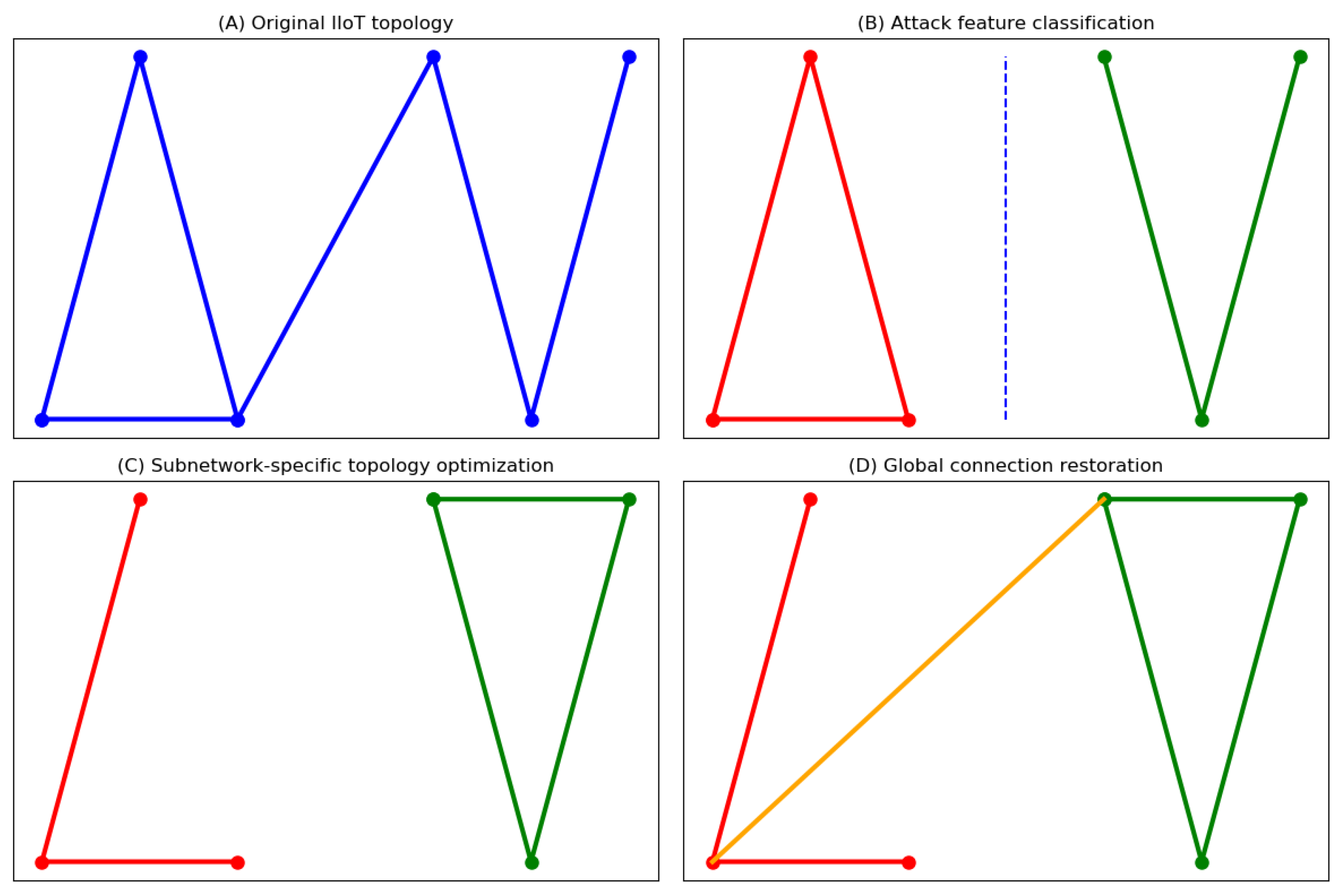
3.3.1. Phase 1: Attack-Aware Subnetwork Classification
- Degree-attack subnets:where denotes 2-hop neighbors.
- Betweenness-attack subnets:
- Random-attack subnets:
3.3.2. Phase 2: Subnetwork-Specific Topology Optimization
- Generate initial regular network with nodes, edges.
- Validate edges: Remove invalid connections () and reconnect to lowest-degree valid nodes. (If the shortest path between nodes and in the original network G exceeds 3 steps, the edge is invalid and is reconnected to the node with the lowest degree in subnet A within the valid range.)
- Rewire edges with probability p (in this study, we set , empirically selected to preserve local clustering) within the valid connection range to create shortcuts.
- Initialize with nodes () and edges ().
- Add nodes incrementally with preferential attachment:
- Prune invalid edges and regenerate via same mechanism
3.3.3. Phase 3: Inter-Subnetwork Connection Optimization
- Intentional-attack subnets: Random selection from perimeter nodes.
- Random-attack subnets: Preferential attachment based on .
| Algorithm 1 Feature-Driven IIoT Reconfiguration |
Require: IIoT network , attack signatures Ensure: Reconfigured network Classify V into via Section 3.3 for each subnet do if is intentional-attacked then Apply small-world construction (Strategy 1) else Apply scale-free construction (Strategy 2) end if end for Compute using Equations (3) and (4) Connect subnets via load-balanced node selection |
3.4. Computational Complexity Analysis
- Phase 1: This stage utilizes the Louvain community detection algorithm to partition the IIoT network into sub-networks. The time complexity of the Louvain algorithm primarily depends on the number of nodes () and edges () in the network, yielding an asymptotic bound of .
- Phase 2–3: These stages involve greedy optimization-based topology refinement within and between subnetworks, including edge rewiring and node selection. The greedy strategy iteratively selects locally optimal solutions, resulting in a time complexity dominated by .
4. Evaluations
4.1. Datasets
- Physical proximity constraint: Nodes within the same community predominantly reside in contiguous spatial regions (e.g., under identical base station coverage), where spatial coupling increases vulnerability to homogeneous external attacks (e.g., directed electromagnetic interference or physical intrusions).
- Functional correlation intensity: A high average modularity score () reveals significantly denser intra-community connections than inter-community links, confirming functional consistency in subnet partitioning.
- Attack surface homogenization: Topologically clustered device groups frequently share identical communication protocol stacks and security vulnerabilities, forming coordinated domains for attack propagation.
- Processor: 11th Gen Intel Core i7-11700F @ 2.50 GHz.
- System Memory: 32.0 GB RAM.
- Operating System: Windows 10 Pro (64-bit) version 22H2 (build 19045.5737).
4.2. Experimental Results
4.2.1. Attack Simulation Protocol
- Attack resistance enhancement through diversified path creation (manifested in extended shortest paths).
- Information efficiency preservation via controlled structural modifications (reflected in entropy consistency).
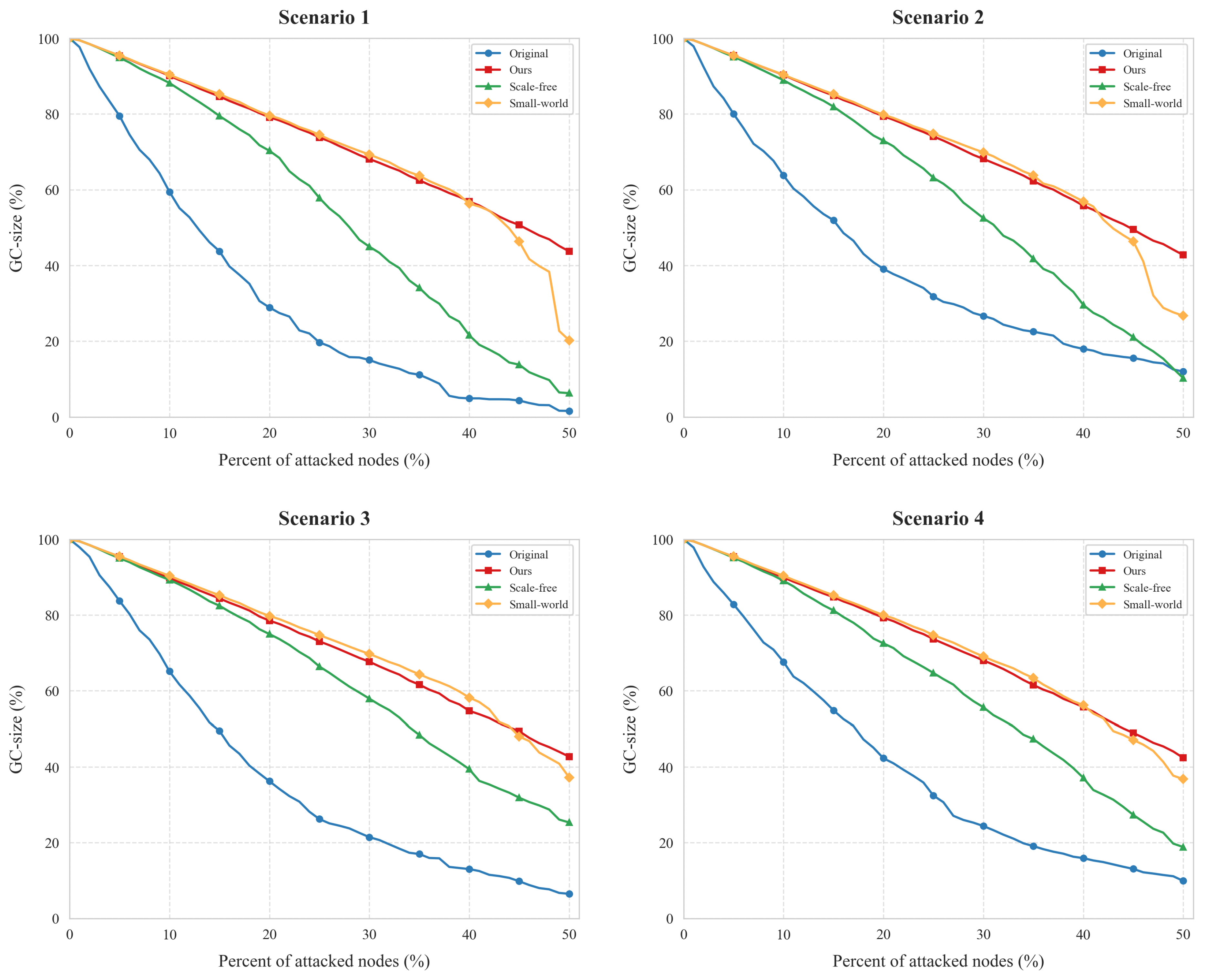
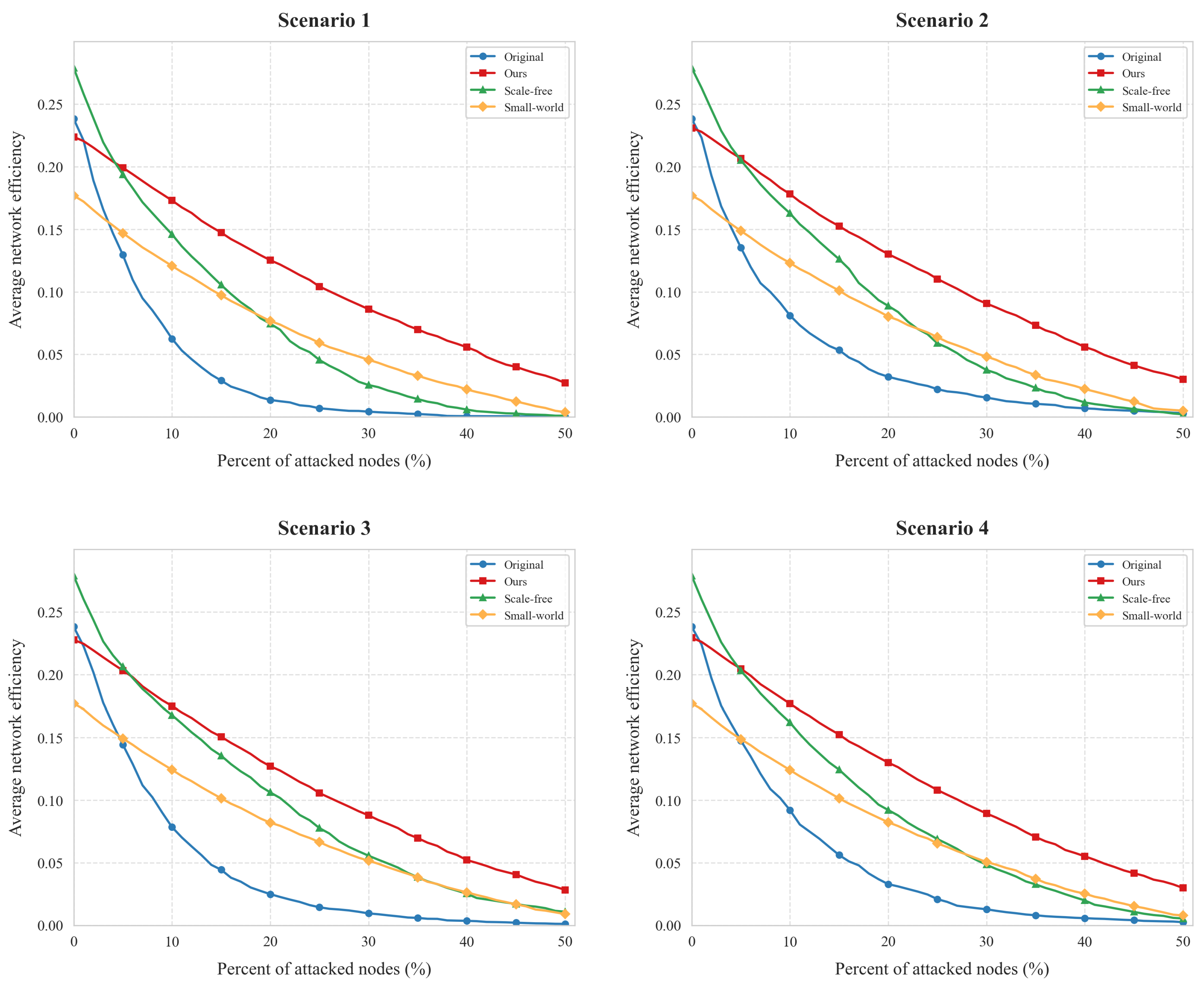
- Connectivity plots: y-axis = giant component ratio; x-axis = failed node ratio.
- Efficiency plots: y-axis = network efficiency; x-axis = failed node ratio.
4.2.2. Connectivity
4.2.3. Communication Effeciency
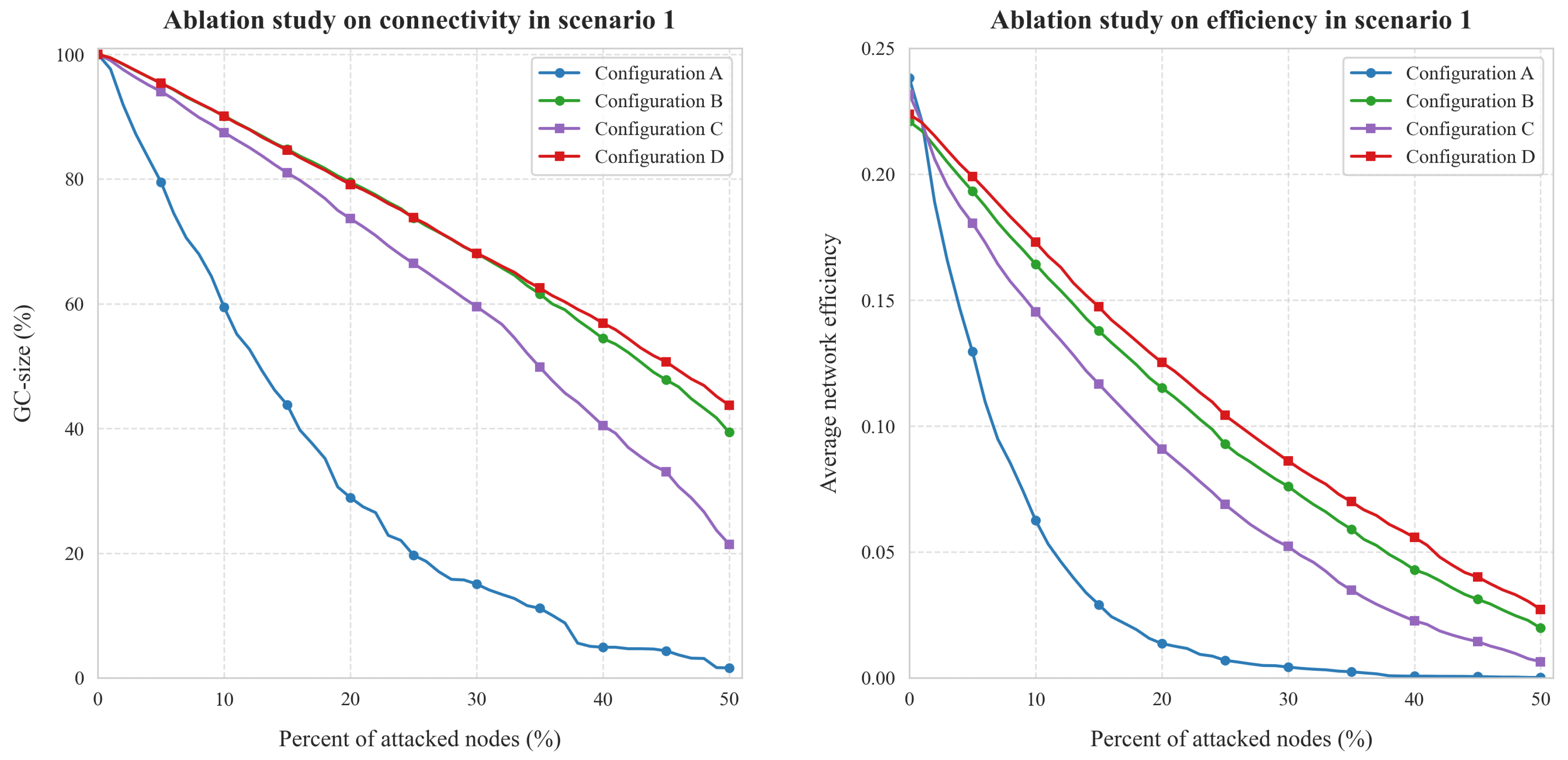
4.2.4. Ablation Study
- Configuration A: Original Topology. This configuration represents the baseline, with no topology reconfiguration applied.
- Configuration B: Phase 1 + Phase 2 (Subnet Optimization) + Random Inter-Subnet Connections. In this configuration, we apply attack-aware subnetwork classification (Phase 1) and subnetwork-specific topology optimization (Phase 2). However, inter-subnetwork connections are established randomly without following the load-balanced node selection strategy described in Phase 3.
- Configuration C: Phase 1 + Construction of Scale-Free Network Subnets + Phase 3 (Inter-Subnet Connections). Here, we apply attack-aware subnetwork classification (Phase 1) and construct all subnetworks using the scale-free topology model, regardless of the attack type. Subsequently, we apply the inter-subnetwork connection optimization (Phase 3).
- Configuration D: Complete Framework (Phase 1–3). This is the full implementation of our proposed framework, including attack-aware subnetwork classification (Phase 1), subnetwork-specific topology optimization (Phase 2), and inter-subnetwork connection optimization (Phase 3).
5. Conclusions
- Real-time attack classification: Enhancing segmentation accuracy by incorporating dynamic communication patterns and node-specific vulnerabilities and integrate Graph Neural Networks (GNNs) for real-time detection of attack characteristics, superseding the current Louvain-based offline segmentation approach.
- Node capability-aware design: Integrating heterogeneous node properties (e.g., computational power, energy constraints) into topology optimization and proposing a multi-objective optimization model to jointly optimize robustness, energy consumption, and computational load during topology reconfiguration (as exemplified by ).
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Choo, K.K.R.; Gritzalis, S.; Park, J.H. Cryptographic Solutions for Industrial Internet-of-Things: Research Challenges and Opportunities. IEEE Trans. Ind. Inform. 2018, 14, 3567–3569. [Google Scholar] [CrossRef]
- Jeong, Y.S. Secure IIoT Information Reinforcement Model Based on IIoT Information Platform Using Blockchain. Sensors 2022, 22, 4645. [Google Scholar] [CrossRef] [PubMed]
- Gulati, N.; Kaur, P.D. Towards socially enabled internet of industrial things: Architecture, semantic model and relationship management. Hoc Netw. 2019, 91, 101869. [Google Scholar] [CrossRef]
- Chai, H.; Jin, X.; Xu, C.; Xia, C. Review of Machine Learning-based 5G for Industrial Internet of Things. Inf. Control 2023, 52, 257–276. [Google Scholar] [CrossRef]
- Alrumaih, T.N.; Alenazi, M.J. GENIND: An industrial network topology generator. Alex. Eng. J. 2023, 79, 56–71. [Google Scholar] [CrossRef]
- Cheng, C.F.; Dong, Y.C.; Hsu, M.H.; Chang, H.Y. The Carrier-Based Sensor Deployment Problem in Industrial Internet of Things With Mesh Topologies. IEEE Internet Things J. 2024, 11, 41137–41150. [Google Scholar] [CrossRef]
- An, H.; Wang, L. Robust Topology Generation of Internet of Things Based on PPO Algorithm Using Discrete Action Space. IEEE Trans. Ind. Inform. 2024, 20, 5406–5414. [Google Scholar] [CrossRef]
- Ge, M.; Hong, J.B.; Yusuf, S.E.; Kim, D.S. Proactive defense mechanisms for the software-defined Internet of Things with non-patchable vulnerabilities. Future Gener. Comput. Syst. 2018, 78, 568–582. [Google Scholar] [CrossRef]
- Li, Z.; Wan, H.; Pang, Z.; Chen, Q.; Deng, Y.; Zhao, X.; Gao, Y.; Song, X.; Gu, M. An Enhanced Reconfiguration for Deterministic Transmission in Time-Triggered Networks. IEEE/ACM Trans. Netw. 2019, 27, 1124–1137. [Google Scholar] [CrossRef]
- Sekiyama, K.; Tkada, I.; Araki, H. Robustness Enhancement with Network Topology Reconfiguration Against Targeted and Random Attack. In Proceedings of the 2006 SICE-ICASE International Joint Conference, Busan, Republic of Korea, 18–21 October 2006; pp. 2746–2751. [Google Scholar] [CrossRef]
- Shannon, C.E. A mathematical theory of communication. Bell Syst. Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Schneider, C.M.; Moreira, A.A.; Andrade, J.S.; Havlin, S.; Herrmann, H.J. Mitigation of malicious attacks on networks. Proc. Natl. Acad. Sci. USA 2011, 108, 3838–3841. [Google Scholar] [CrossRef]
- Latora, V.; Marchiori, M. A measure of centrality based on network efficiency. New J. Phys. 2007, 9, 188. [Google Scholar] [CrossRef]
- Chen, N.; Qiu, T.; Mu, C.; Han, M.; Zhou, P. Deep Actor-Critic Learning-Based Robustness Enhancement of Internet of Things. IEEE Internet Things J. 2020, 7, 6191–6200. [Google Scholar] [CrossRef]
- Buesser, P.; Daolio, F.; Tomassini, M. Optimizing the Robustness of Scale-Free Networks with Simulated Annealing. In Proceedings of the Adaptive and Natural Computing Algorithms, Ljubljana, Slovenia, 14–16 April 2011; Dobnikar, A., Lotrič, U., Šter, B., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 167–176. [Google Scholar]
- Basu, P.; Redi, J. Movement control algorithms for realization of fault-tolerant ad hoc robot networks. IEEE Netw. 2004, 18, 36–44. [Google Scholar] [CrossRef]
- Tan, G.; Jarvis, S.A.; Kermarrec, A.M. Connectivity-Guaranteed and Obstacle-Adaptive Deployment Schemes for Mobile Sensor Networks. In Proceedings of the 2008 The 28th International Conference on Distributed Computing Systems, Beijing, China, 17–20 June 2008; pp. 429–437. [Google Scholar] [CrossRef]
- Peng, H.; Si, S.; Awad, M.K.; Zhang, N.; Zhao, H.; Shen, X.S. Toward Energy-Efficient and Robust Large-Scale WSNs: A Scale-Free Network Approach. IEEE J. Sel. Areas Commun. 2016, 34, 4035–4047. [Google Scholar] [CrossRef]
- Sohn, I. Small-World and Scale-Free Network Models for IoT Systems. Mob. Inf. Syst. 2017, 2017, 6752048. [Google Scholar] [CrossRef]
- Musleh, A.S.; Khalid, H.M.; Muyeen, S.M.; Al-Durra, A. A Prediction Algorithm to Enhance Grid Resilience Toward Cyber Attacks in WAMCS Applications. IEEE Syst. J. 2019, 13, 710–719. [Google Scholar] [CrossRef]
- Fu, X.; Li, W.; Fortino, G. Empowering the Invulnerability of Wireless Sensor Networks through Super Wires and Super Nodes. In Proceedings of the 2013 13th IEEE/ACM International Symposium on Cluster, Cloud, and Grid Computing, Delft, The Netherlands, 13–16 May 2013; pp. 561–568. [Google Scholar] [CrossRef]
- Sitanayah, L.; Brown, K.N.; Sreenan, C.J. A fault-tolerant relay placement algorithm for ensuring k vertex-disjoint shortest paths in wireless sensor networks. Hoc Netw. 2014, 23, 145–162. [Google Scholar] [CrossRef]
- Ou, Z.; Wang, S. Finding robust and influential nodes on directed networks using a memetic algorithm. Swarm Evol. Comput. 2024, 87, 101542. [Google Scholar] [CrossRef]
- Wang, S.; Tan, X. Finding robust influential seeds from networked systems against structural failures using a niching memetic algorithm. Appl. Soft Comput. 2023, 136, 110134. [Google Scholar] [CrossRef]
- Wang, T.; Zeng, P.; Zhao, J.; Liu, X.; Zhang, B. Identification of Influential Nodes in Industrial Networks Based on Structure Analysis. Symmetry 2022, 14, 211. [Google Scholar] [CrossRef]
- Andria, J.; di Tollo, G.; Kalda, J. Propagation of Bankruptcy Risk over Scale-Free Economic Networks. Entropy 2022, 24, 1713. [Google Scholar] [CrossRef] [PubMed]
- Roveri, N.; Carcaterra, A.; Molinari, L.; Pepe, G. Safe and Secure Control of Swarms of Vehicles by Small-World Theory. Energies 2020, 13, 1043. [Google Scholar] [CrossRef]
- Zhu, Y.; Li, W.; Cai, X. Opinion evolution on a BA scaling network. Phys. A Stat. Mech. Its Appl. 2013, 392, 6596–6602. [Google Scholar] [CrossRef]
- Latora, V.; Marchiori, M. Efficient Behavior of Small-World Networks. Phys. Rev. Lett. 2001, 87, 198701. [Google Scholar] [CrossRef]
- Blondel, V.D.; Guillaume, J.L.; Lambiotte, R.; Lefebvre, E. Fast unfolding of communities in large networks. J. Stat. Mech. Theory Exp. 2008, 2008, P10008. [Google Scholar] [CrossRef]
- Rossi, R.A.; Ahmed, N.K. The Network Data Repository with Interactive Graph Analytics and Visualization. In Proceedings of the AAAI Conference on Artificial Intelligence, Austin, TX, USA, 25–30 January 2015. [Google Scholar]


| Networks | Node Num. | Link Num. | Ave. Deg | Ave. Betw | Ave. SPL | CC | Q |
|---|---|---|---|---|---|---|---|
| Total network | 2113 | 6632 | 6.28 | 0.002 | 4.61 | 0.25 | 0.69 |
| Networks | Node Num. | Link Num. | Ave. Deg | Ave. Bet | Ave. SPL | CC |
|---|---|---|---|---|---|---|
| Subnet 1 | 213 | 505 | 4.74 | 0.013 | 3.74 | 0.24 |
| Subnet 2 | 200 | 444 | 4.44 | 0.014 | 3.68 | 0.25 |
| Subnet 3 | 173 | 341 | 3.94 | 0.016 | 3.73 | 0.20 |
| Subnet 4 | 147 | 205 | 2.79 | 0.026 | 4.74 | 0.19 |
| Subnet 5 | 143 | 269 | 3.76 | 0.017 | 3.38 | 0.20 |
| Subnet 6 | 137 | 301 | 4.39 | 0.023 | 4.05 | 0.26 |
| Subnet 7 | 131 | 229 | 3.50 | 0.022 | 3.78 | 0.22 |
| Subnet 8 | 110 | 636 | 11.56 | 0.013 | 2.43 | 0.47 |
| Subnet 9 | 107 | 182 | 3.40 | 0.029 | 4.04 | 0.23 |
| Subnet 10 | 101 | 332 | 6.57 | 0.020 | 2.99 | 0.38 |
| Subnet 11 | 97 | 376 | 7.75 | 0.016 | 2.52 | 0.58 |
| Subnet 12 | 93 | 176 | 3.78 | 0.031 | 3.81 | 0.29 |
| Subnet 13 | 73 | 488 | 13.37 | 0.020 | 2.43 | 0.55 |
| Subnet 14 | 68 | 92 | 2.71 | 0.052 | 4.47 | 0.17 |
| Subnet 15 | 64 | 177 | 5.53 | 0.036 | 3.25 | 0.38 |
| Subnet 16 | 62 | 86 | 2.77 | 0.033 | 3.01 | 0.14 |
| Subnet 17 | 59 | 65 | 2.20 | 0.046 | 3.62 | 0.07 |
| Subnet 18 | 57 | 78 | 2.74 | 0.058 | 4.20 | 0.28 |
| Subnet 19 | 37 | 43 | 2.32 | 0.059 | 3.08 | 0.27 |
| Subnet 20 | 35 | 36 | 2.06 | 0.081 | 3.66 | 0.04 |
| Subnet 21 | 6 | 8 | 2.67 | 0.133 | 1.53 | 0.58 |
| Attack Scenarios | Scenario 1 | Scenario 2 | Scenario 3 | Scenario 4 |
|---|---|---|---|---|
| Subnet 1 | Deg | Rand | Deg | Deg |
| Subnet 2 | Betw | Deg | Deg | Betw |
| Subnet 3 | Deg | Deg | Deg | Rand |
| Subnet 4 | Betw | Betw | Betw | Deg |
| Subnet 5 | Deg | Betw | Betw | Betw |
| Subnet 6 | Betw | Betw | Betw | Rand |
| Subnet 7 | Rand | Rand | Rand | Deg |
| Subnet 8 | Deg | Rand | Rand | Betw |
| Subnet 9 | Betw | Deg | Rand | Rand |
| Subnet 10 | Deg | Deg | Deg | Deg |
| Subnet 11 | Betw | Betw | Deg | Betw |
| Subnet 12 | Deg | Betw | Deg | Rand |
| Subnet 13 | Betw | Betw | Betw | Deg |
| Subnet 14 | Rand | Rand | Betw | Betw |
| Subnet 15 | Deg | Rand | Betw | Rand |
| Subnet 16 | Betw | Deg | Rand | Deg |
| Subnet 17 | Deg | Deg | Rand | Betw |
| Subnet 18 | Betw | Betw | Rand | Rand |
| Subnet 19 | Deg | Betw | Deg | Deg |
| Subnet 20 | Betw | Betw | Deg | Betw |
| Subnet 21 | Rand | Rand | Deg | Rand |
| Scenarios | Metrics | Before Reconfiguration | After Reconfiguration |
|---|---|---|---|
| Scenario 1 | Ave. Deg | 6.28 | 6.28 |
| Ave. Betw | 0.0017 | 0.0018 | |
| Ave. SPL | 4.61 | 4.75 | |
| CC | 0.25 | 0.029 | |
| Information Entropy | 3.68 | 3.63 | |
| Scenario 2 | Ave. Deg | 6.28 | 6.28 |
| Ave. Betw | 0.0017 | 0.0017 | |
| Ave. SPL | 4.61 | 4.61 | |
| CC | 0.25 | 0.037 | |
| Information Entropy | 3.68 | 3.65 | |
| Scenario 3 | Ave. Deg | 6.28 | 6.28 |
| Ave. Betw | 0.0017 | 0.0017 | |
| Ave. SPL | 4.61 | 4.67 | |
| CC | 0.25 | 0.0372 | |
| Information Entropy | 3.68 | 3.70 | |
| Scenario 4 | Ave. Deg | 6.28 | 6.28 |
| Ave. Betw | 0.0017 | 0.0017 | |
| Ave. SPL | 4.61 | 4.63 | |
| CC | 0.25 | 0.038 | |
| Information Entropy | 3.68 | 3.71 |
| Scenario | Original | Ours | Scale-Free | Small-World | Improvement |
|---|---|---|---|---|---|
| Scenario 1 | 16.30 | 37.39 | 28.45 | 36.83 | +129.4% |
| Scenario 2 | 20.77 | 37.29 | 30.74 | 36.75 | +79.5% |
| Scenario 3 | 19.27 | 37.02 | 33.06 | 37.48 | +92.1% |
| Scenario 4 | 20.88 | 37.15 | 32.06 | 37.17 | +78.0% |
| Scenario | Original | Ours | Scale-Free | Small-World | Improvement |
|---|---|---|---|---|---|
| Scenario 1 | 0.019 | 0.058 | 0.039 | 0.036 | +67.2% |
| Scenario 2 | 0.025 | 0.060 | 0.044 | 0.037 | +58.3% |
| Scenario 3 | 0.023 | 0.058 | 0.049 | 0.038 | +60.3% |
| Scenario 4 | 0.026 | 0.059 | 0.046 | 0.038 | +55.9% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, T.; Li, D.; Zhang, B.; Liu, X.; Shang, W. Resilient Topology Reconfiguration for Industrial Internet of Things: A Feature-Driven Approach Against Heterogeneous Attacks. Entropy 2025, 27, 503. https://doi.org/10.3390/e27050503
Wang T, Li D, Zhang B, Liu X, Shang W. Resilient Topology Reconfiguration for Industrial Internet of Things: A Feature-Driven Approach Against Heterogeneous Attacks. Entropy. 2025; 27(5):503. https://doi.org/10.3390/e27050503
Chicago/Turabian StyleWang, Tianyu, Dong Li, Bowen Zhang, Xianda Liu, and Wenli Shang. 2025. "Resilient Topology Reconfiguration for Industrial Internet of Things: A Feature-Driven Approach Against Heterogeneous Attacks" Entropy 27, no. 5: 503. https://doi.org/10.3390/e27050503
APA StyleWang, T., Li, D., Zhang, B., Liu, X., & Shang, W. (2025). Resilient Topology Reconfiguration for Industrial Internet of Things: A Feature-Driven Approach Against Heterogeneous Attacks. Entropy, 27(5), 503. https://doi.org/10.3390/e27050503







