Theory and Application of Zero Trust Security: A Brief Survey
Abstract
:1. Introduction
- Innovatively understand zero trust from the perspective of trust in network security, and discover the existence of trust in zero trust through representative literature on zero trust theory and application.
- Proposes the concept and characteristics of trust in zero trust, and provides the basic principles it should have. On top of this, the research trends of zero trust in different scenarios in the future are discussed.
2. Conceptual Background
2.1. Trust in Cybersecurity
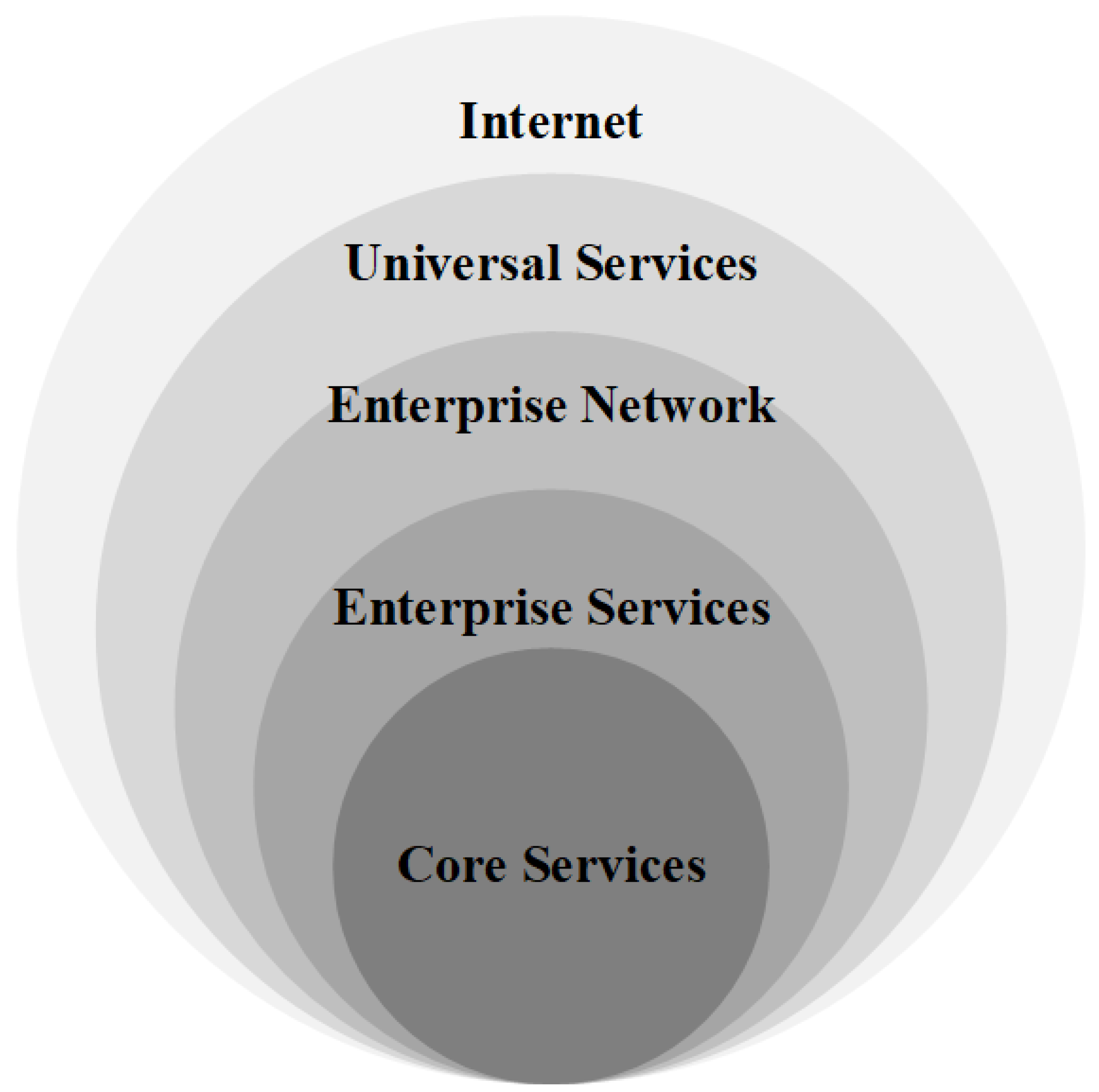
2.2. What Is Zero Trust
- Separation of trust from location. This principle is one of the basic premises for achieving zero trust. The biggest difference between zero trust and traditional security perimeters is whether the location determines the trust in the access behaviour. Zero trust dispels the credibility of the internal trusted network set by the traditional security perimeter based on the resource location, and is premised on the belief that location can no longer fully guarantee trust in the current network environment. Furthermore, the network security situation, such as the long-term hostility of the network and existence of internal and external threats, makes the trust gained by the location unable to guarantee the security of critical resources in the network. The separation of trust from the location that is the core of zero trust can invalidate the trust determined by location, thereby reducing the scope of the influence of implicit trust in internal trusted networks, and ultimately achieving the goal of resisting threats from internal and external networks simultaneously. However, it should be noted that that trust is not solely determined by location, as zero trust does not completely negate the influence of the location on trust judgment; rather, it is simply one of other collectible elements as an equal condition for judging trust.
- The principle of least privilege. The formulation of least-privilege policies is essential to achieve frequent and fine-grained authentication and authorisation. All requested permissions must be restricted to a specific entity under access and only given the minimum permissions for the current operation. This is similar to the principle of the least privilege in the access control. It is necessary to enumerate all possible access conditions and avoid conflicts among policies by comparing a series of elements related to access such as subjects, resources, and context. At the same time, the principle of the least privilege can also reduce the scale of risks caused by the abuse of power and minimize the scope of threats. Additionally, dynamic security policies must be used to maintain the necessary flexibility in dynamic contexts. Therefore, the scale of zero trust security policies is often determined based on the complexity of the deployment scenario.
- All data and services as resources. Zero trust expands resource coverage and protects critical resources from damage. Logically, the access can be regarded as the operation of the subject in a specific environment, aiming to protect against existing attacks. However, once services involving data flow and computation are damaged, access security will also be affected, and protection against attacks cannot resist unknown attacks. Therefore, all data and services included in the zero trust access process are regarded as resources that are as important as the object or device being accessed, and critical resources are specifically protected.
- Continuous monitoring and evaluation. No entity is inherently trustworthy; thus, all entities should be monitored. The monitoring proposed here does not monitor only specific threat behaviors or characteristics as before, it monitors all states of all entities (data flow, devices, services, files) related to the access. A robust continuous monitoring system can collect environmental information as much as possible and provides reliable data for safety assessment. As the observable information increases, the credibility of the security analysis results obtained by the assessment system would increase, thereby reducing the probability of threats caused by the trust.
2.3. Zero Trust Achievement
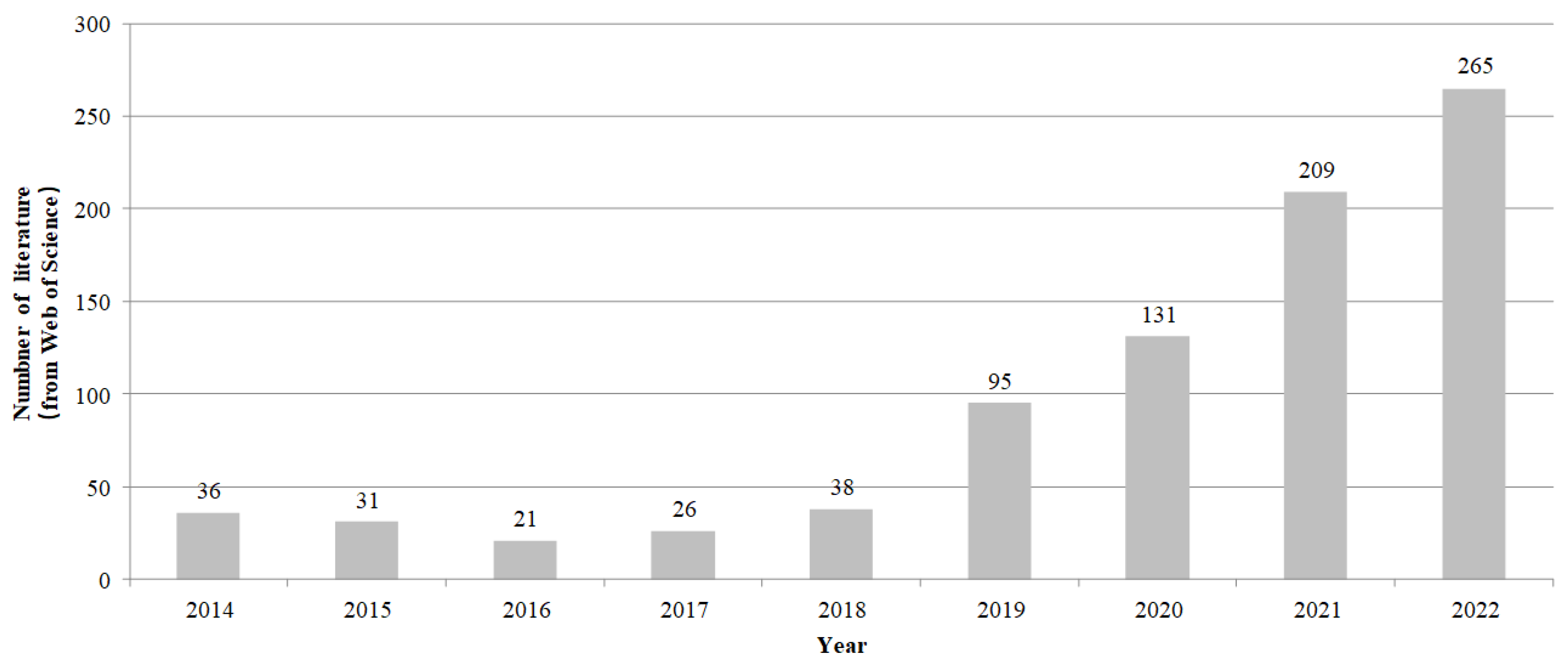
2.4. Overview of the Literature
3. Application
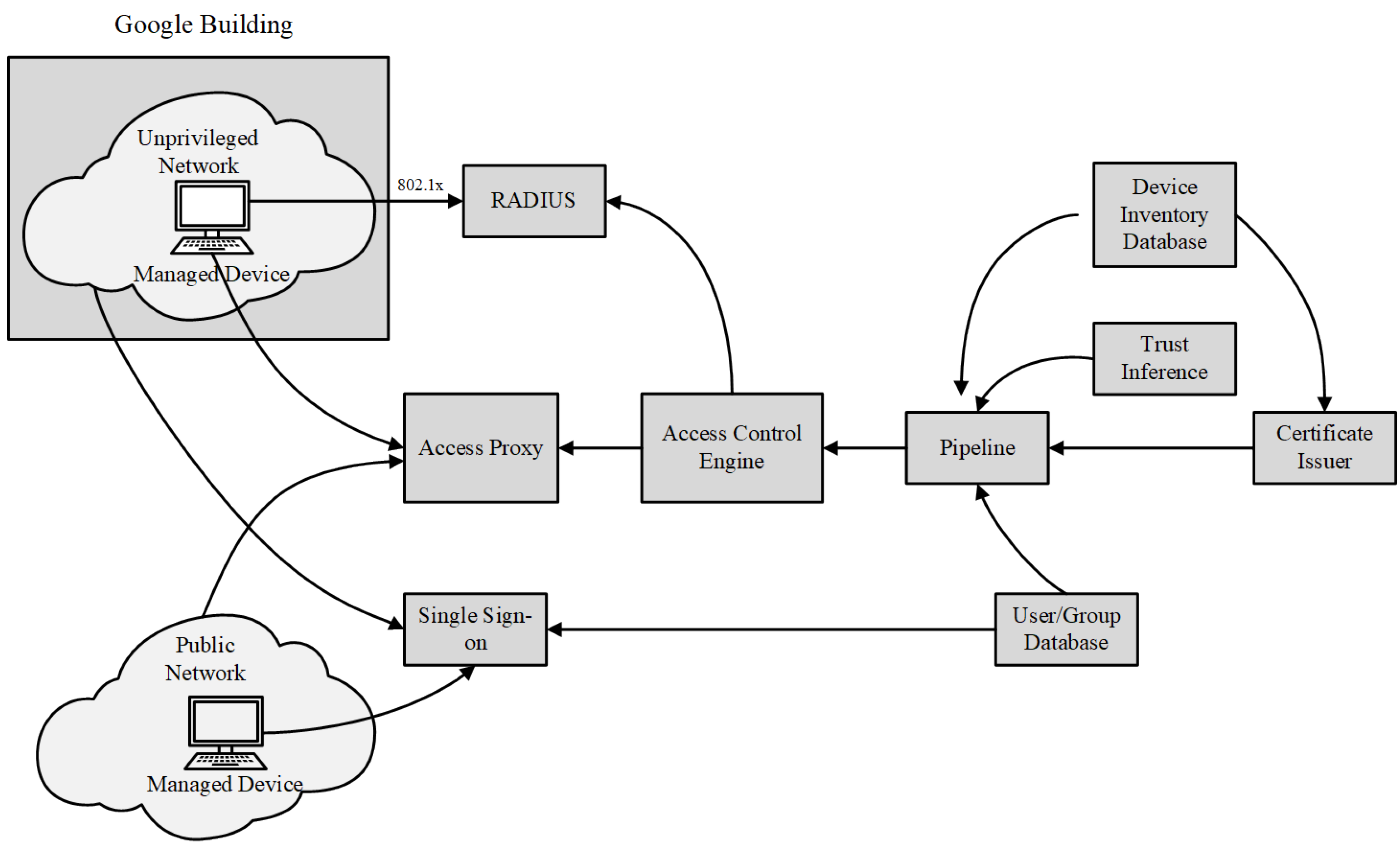
3.1. Application of Zero Trust in the Cloud Environment
3.2. Application of Zero Trust in the IoT Environment
3.3. Overview of the Literature
4. Analysis
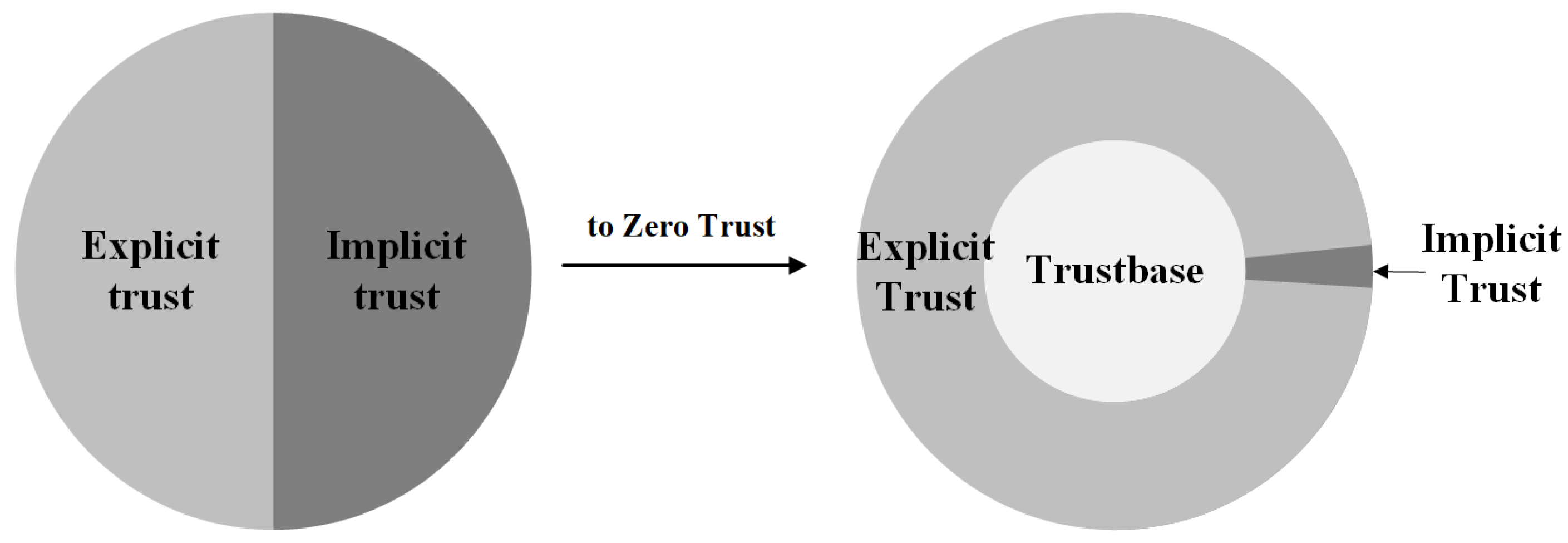
4.1. Trust in Zero Trust
4.2. The Principles of Trust in Zero Trust
- Trust should be context-based. This principle is derived from the requirements for dynamic access control and continuous evaluation. In the existing deployment of zero trust, security professionals can realize authentication and authorization through fine-grained dynamic access control policies. These policies must address the security requirements of the system for access in different contexts and grant trust to the access that is met. This means that trust in zero trust is not persistent but dynamic, and should be context-based.
- Trust should be based on the minimum security requirements of resource owners. Unlike the traditional perimeter, zero trust defaults on all transactions, and data are untrusted until verified. Additionally, the principle of the least privilege allows trust to be granted to the finest-grained information carrier in the interaction such as a single transaction or packet. However, once the critical resource is leaked and destroyed, the resource owner will be exposed to great security risks. That makes the risk of leakage often borne by the resource owners. Thus, in zero trust, the minimum security requirements of resource owners must be satisfied before trust can be granted.
- Trust should be hierarchical. In realistic scenarios, different trust evaluation criteria may produce opposite results for the same matter, thus creating conflict. A hierarchy of trust should be established to ensure consistent results in the case of conflict. In zero trust, the hierarchy of trust is that trust has different priorities in different contexts. Owing to the complexity of the context of cybersecurity, there could be multiple trusts in zero trust. If there is no hierarchical division, the credibility assessment of current transactions based on different forms of trust will lead to inconsistencies in the assessment results, which will render the transaction unsuitable for normal processing. Therefore, to solve the problem of the difference among the trust evaluation results of different forms of trusts caused by the continuous change in context, there should be a clear classification of trusts according to context-based criteria.
5. Feature Research Trends
5.1. Zero Trust Theory
5.1.1. Establish Initial Trust
5.1.2. Dynamic Trust Mechanism
5.1.3. Insider Threat of Zero Trust
5.1.4. Entropy of Zero Trust
5.2. Zero Trust Application
5.2.1. Zero Trust in Cloud
5.2.2. Zero Trust in IoT
6. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- FireEye Mandiant M-Trends. 2022. Available online: https://mandiant.widen.net/s/kxbbdppzzk/m-trends-2022-executive-summary (accessed on 18 November 2023).
- Northcutt, S.; Zeltser, L.; Winters, S.; Kent, K.; Ritchey, R.W. Inside Network Perimeter Security (Inside), 2nd ed.; Sams: Indianapolis, IN, USA, 2005. [Google Scholar]
- Kindervag, J. No More Chewy Centers: Introducing the Zero Trust Model of Information Security; Forrester Research: Cambridge, MA, USA, 2010; Volume 3. [Google Scholar]
- Jericho Forum Commandments, Version 1.2. Available online: https://static.spiceworks.com/attachments/post/0016/4842/commandments_v1.2.pdf (accessed on 18 November 2023).
- Ward, R.; Beyer, B. Beyondcorp: A new approach to enterprise security. Login Usenix Mag. 2014, 39, 6–11. [Google Scholar]
- Osborn, B.; McWilliams, J.; Beyer, B.; Saltonstall, M. Beyondcorp: Design to deployment at google. Login 2016, 41, 28–34. [Google Scholar]
- Escobedo, V.; Beyer, B.; Saltonstall, M.; Zyzniewski, F. BeyondCorp: The user experience. Login 2017, 42, 38–43. [Google Scholar]
- Software Defined Perimeter. Available online: https://cloudsecurityalliance.org/download/artifacts/software-defined-perimeter/ (accessed on 18 November 2023).
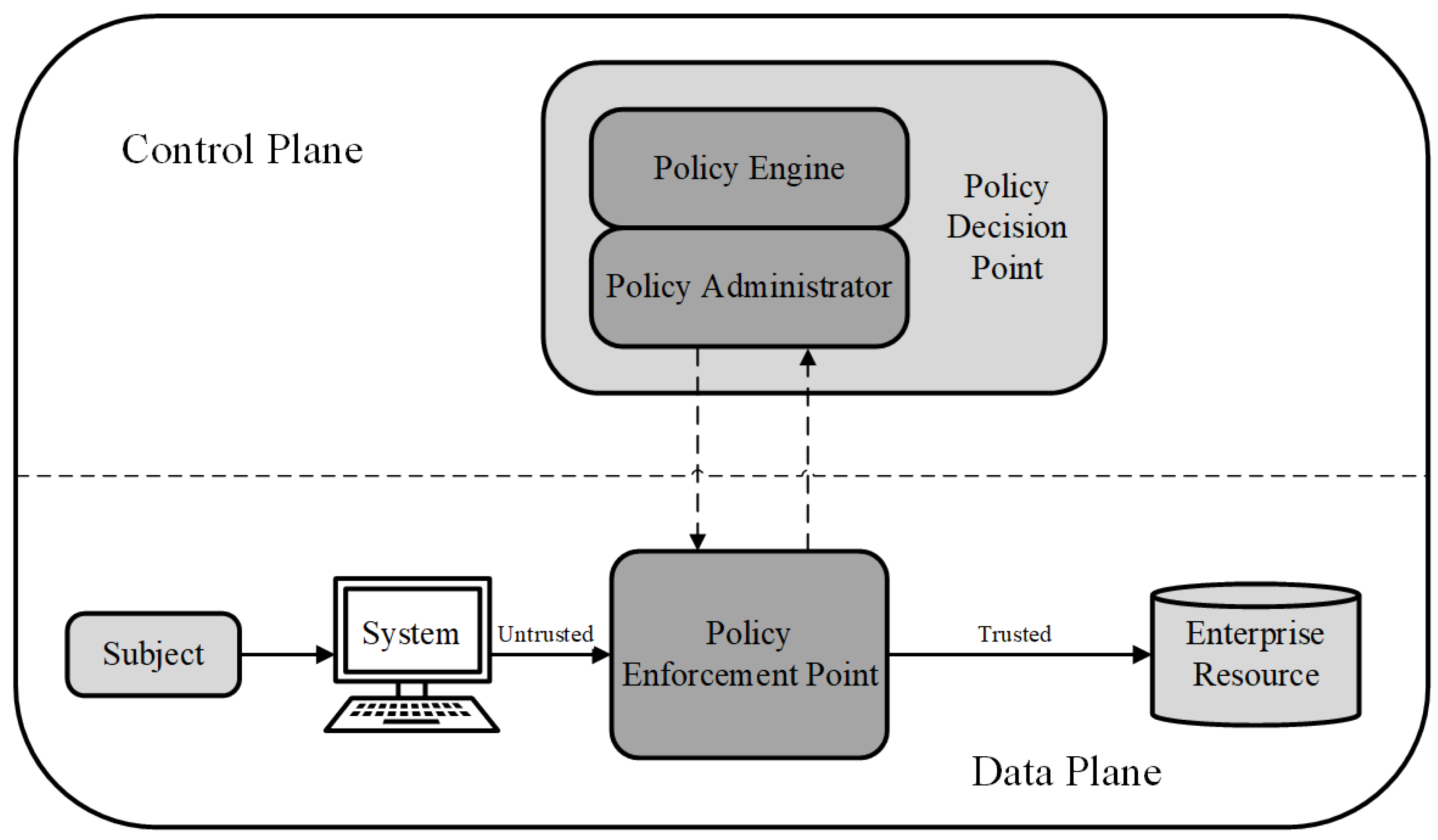
- Rose, S.; Borchert, O.; Mitchell, S.; Connelly, S. Zero Trust Architecture; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2020.
- He, Y.; Huang, D.; Chen, L.; Ni, Y.; Ma, X. A survey on zero trust architecture: Challenges and future trends. Wirel. Commun. Mob. Comput. 2022, 2022, 6476274. [Google Scholar] [CrossRef]
- Buck, C.; Olenberger, C.; Schweizer, A.; Völter, F.; Eymann, T. Never trust, always verify: A multivocal literature review on current knowledge and research gaps of zero-trust. Comput. Secur. 2021, 110, 102436. [Google Scholar] [CrossRef]
- Rousseau, D.M.; Sitkin, S.B.; Burt, R.S.; Camerer, C. Not so different after all: A cross-discipline view of trust. Acad. Manag. Rev. 1998, 23, 393–404. [Google Scholar] [CrossRef]
- Govindan, K.; Mohapatra, P. Trust computations and trust dynamics in mobile adhoc networks: A survey. IEEE Commun. Surv. Tutorials 2011, 14, 279–298. [Google Scholar] [CrossRef]
- Nitti, M.; Girau, R.; Atzori, L.; Iera, A.; Morabito, G. A subjective model for trustworthiness evaluation in the social internet of things. In Proceedings of the 2012 IEEE 23rd International Symposium on Personal, Indoor and Mobile Radio Communications-(PIMRC), Sydney, NSW, Australia, 9–12 September 2012. [Google Scholar]
- Theodorakopoulos, G.; Baras, J.S. On trust models and trust evaluation metrics for ad hoc networks. IEEE J. Sel. Areas Commun. 2006, 24, 318–328. [Google Scholar] [CrossRef]
- Burns, C.; Mearns, K.; McGeorge, P. Explicit and implicit trust within safety culture. Risk Anal. 2006, 26, 1139–1150. [Google Scholar] [CrossRef]
- Dunning, D.; Anderson, J.E.; Schlösser, T.; Ehlebracht, D.; Fetchenhauer, D. Trust at zero acquaintance: More a matter of respect than expectation of reward. J. Personal. Soc. Psychol. 2014, 107, 122. [Google Scholar] [CrossRef]
- Pearson, S.; Mont, M.C.; Crane, S. Persistent and dynamic trust: Analysis and the related impact of trusted platforms. In Proceedings of the Trust Management: Third International Conference, iTrust 2005, Paris, France, 23–26 May 2005. [Google Scholar]
- ACT-IAC Zero-trust Project Team. Zero-Trust Cybersecurity Current Trends. Available online: https://www.actiac.org/system/files/ACT-IACZeroTrustProjectReport04182019.pdf (accessed on 18 November 2023).
- Tidjon, L.N.; Khomh, F. Never trust, always verify: A roadmap for Trustworthy AI? arXiv 2022, arXiv:2206.11981. [Google Scholar]
- Kindervag, J.; Balaouras, S.; Mak, K.; Blackborow, J. No More Chewy Centers: The Zero Trust Model of Information Security; Forrester Research: Cambridge, MA, USA, 2016; Volume 23. [Google Scholar]
- Embracing a Zero-Trust Security Model. Available online: https://media.defense.gov/2021/Feb/25/2002588479/-1/-1/0/CSI_EMBRACING_ZT_SECURITY_MODEL_UOO115131-21.PDF (accessed on 18 November 2023).
- Garbis, J.; Chapman, J.W. What Is Zero Trust? In Zero Trust Security; Garbis, J., Chapman, J.W., Eds.; Apress: Berkeley, CA, USA, 2021; pp. 7–18. [Google Scholar]
- Campbell, M. Beyond zero trust: Trust is a vulnerability. Computer 2020, 53, 110–113. [Google Scholar] [CrossRef]
- Eidle, D.; Ni, S.Y.; De Cusatis, C.; Sager, A. Autonomic security for zero trust networks. In Proceedings of the 2017 IEEE 8th Annual Ubiquitous Computing, Electronics and Mobile Communication Conference (UEMCON), New York, NY, USA, 19–21 October 2017. [Google Scholar]
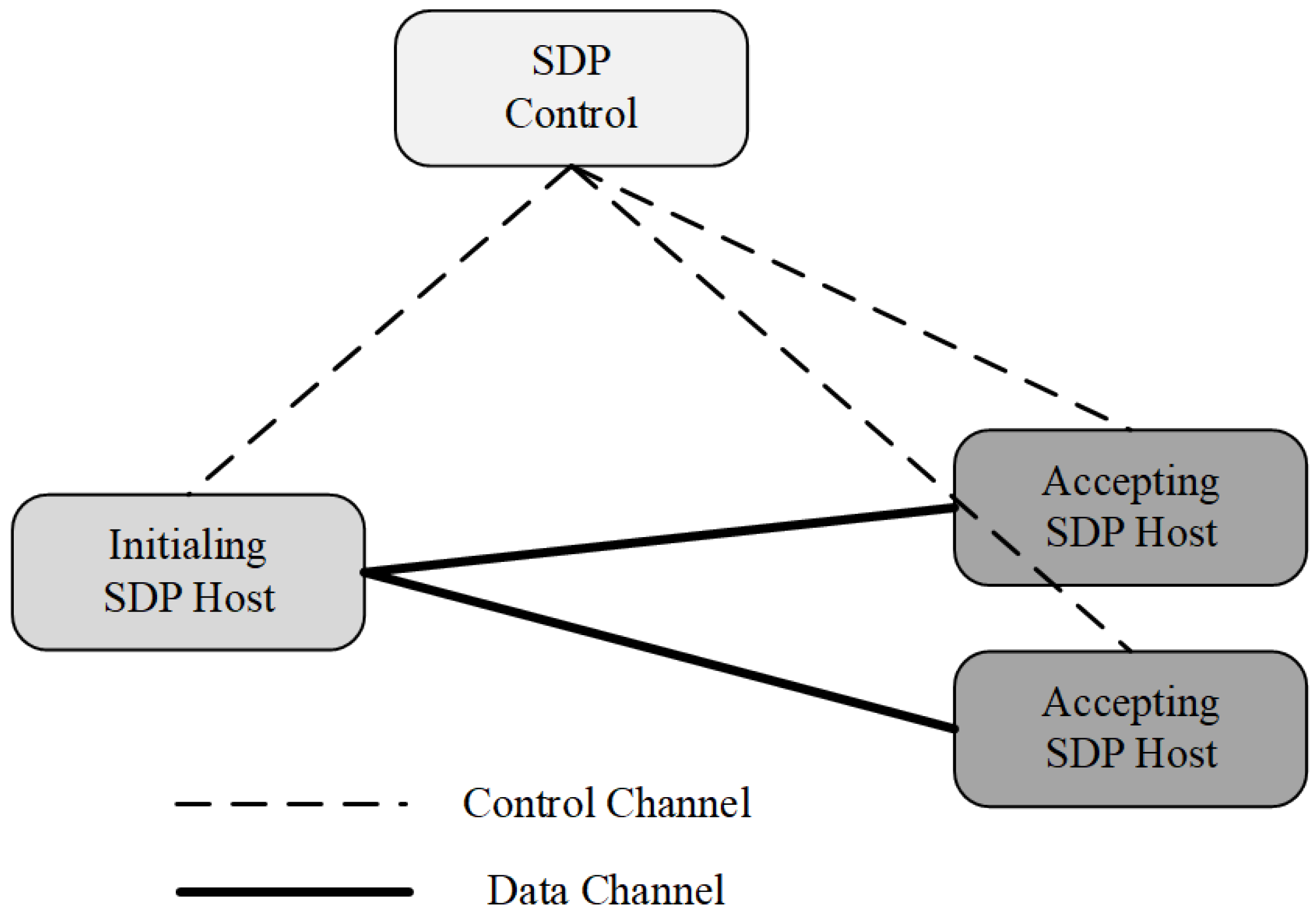
- Moubayed, A.; Refaey, A.; Shami, A. Software-Defined Perimeter (SDP): State of the Art Secure Solution for Modern Networks. Netwrk. Mag. Glob. Internetwkg. 2019, 33, 226–233. [Google Scholar] [CrossRef]
- Kumar, P.; Moubayed, A.; Refaey, A.; Shami, A.; Koilpillai, J. Performance analysis of sdp for secure internal enterprises. In Proceedings of the 2019 IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–18 April 2019. [Google Scholar]
- Singh, J.; Refaey, A.; Shami, A. Multilevel security framework for nfv based on software defined perimeter. IEEE Netw. 2020, 34, 114–119. [Google Scholar] [CrossRef]
- Syed, N.F.; Shah, S.W.; Shaghaghi, A.; Anwar, A.; Baig, Z.; Doss, R. Zero trust architecture (zta): A comprehensive survey. IEEE Access 2022, 10, 57143–57179. [Google Scholar] [CrossRef]
- AWS Identity & Access Management. Available online: https://aws.amazon.com/cn/iam/ (accessed on 18 November 2023).
- Sailpoint IDM. Available online: https://www.sailpoint.com/identity-management-solutions/ (accessed on 18 November 2023).
- IBM Cloud Services. Available online: https://www.ibm.com/cloud-computing/in-en/services/cloud-managed-services/ (accessed on 18 November 2023).
- Oracle Cloud Services. Available online: https://www.oracle.com/cloud/index.html (accessed on 18 November 2023).
- Coresecurity IAM. Available online: https://www.rsa.com/en-us/products/rsa-securid-suite.html (accessed on 18 November 2023).
- Sailpoint IDM. Available online: https://www.coresecurity.com/iam-products (accessed on 18 November 2023).
- SDP, ZTNA, and CARTA: Making Sense of the Zero Trust Security Buzz. Available online: https://www.zscaler.com/ (accessed on 18 November 2023).
- Leahy, D.; Thorpe, C. Zero Trust Container Architecture (ZTCA): A Framework for Applying Zero Trust Principals to Docker Containers. In Proceedings of the International Conference on Cyber Warfare and Security, New York, NY, USA, 17–18 March 2022. [Google Scholar]
- Huang, J.; Nicol, D.M. Trust mechanisms for cloud computing. J. Cloud Comput. Adv. Syst. Appl. 2013, 2, 9. [Google Scholar] [CrossRef]
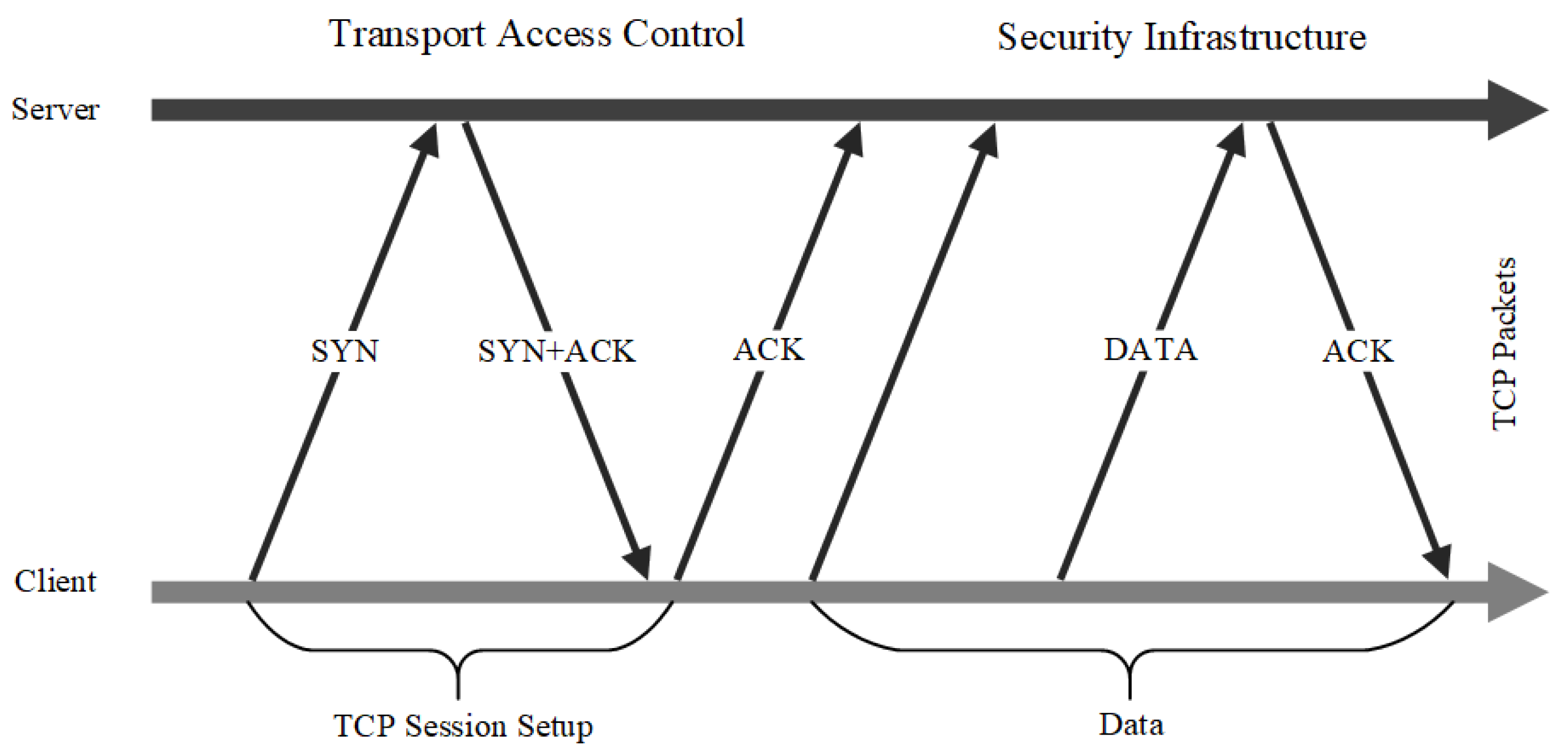
- DeCusatis, C.; Liengtiraphan, P.; Sager, A.; Pinelli, M. Implementing zero trust cloud networks with transport access control and first packet authentication. In Proceedings of the 2016 IEEE International Conference on Smart Cloud (SmartCloud), New York, NY, USA, 18–20 November 2016. [Google Scholar]
- Zaheer, Z.; Chang, H.; Mukherjee, S.; Van der Merwe, J. eZTrust: Network-independent zero-trust perimeterization for microservices. In Proceedings of the 2019 ACM Symposium on SDN Research, San Jose, CA, USA, 3–4 April 2019. [Google Scholar]
- Liu, S.; Zhuang, Y.; Huang, L.; Zhou, X. Exploiting lsb self-quantization for plaintext-related image encryption in the zero-trust cloud. J. Inf. Secur. Appl. 2022, 66, 103138. [Google Scholar] [CrossRef]
- Zolotukhin, M.; Hämäläinen, T.; Kotilainen, P. Intelligent Solutions for Attack Mitigation in Zero-Trust Environments. In Cyber Security; Lehto, M., Neittaanmäki, P., Eds.; Springer: Cham, Switzerland, 2022; pp. 403–417. [Google Scholar]
- Sarkar, S.; Choudhary, G.; Shandilya, S.K.; Hussain, A.; Kim, H. Security of zero trust networks in cloud computing: A comparative review. Sustainability 2022, 14, 11213. [Google Scholar] [CrossRef]
- Alaba, F.A.; Othman, M.; Hashem, I.A.T.; Alotaibi, F. Internet of Things security: A survey. J. Netw. Comput. Appl. 2017, 88, 10–28. [Google Scholar] [CrossRef]
- Siegel, J.E.; Kumar, S.; Sarma, S.E. The future internet of things: Secure, efficient, and model-based. IEEE Internet Things J. 2017, 5, 2386–2398. [Google Scholar] [CrossRef]
- Samaniego, M.; Deters, R. Zero-trust hierarchical management in IoT. In Proceedings of the 2018 IEEE International Congress on Internet of Things (ICIOT), San Francisco, CA, USA, 2–7 July 2018. [Google Scholar]
- Dhar, S.; Bose, I. Securing IoT devices using zero trust and blockchain. J. Organ. Comput. Electron. Commer. 2021, 31, 18–34. [Google Scholar] [CrossRef]
- Zhao, S.; Li, S.; Li, F.; Zhang, W.; Iqbal, M. Blockchain-enabled user authentication in zero trust internet of things. In Proceedings of the Security and Privacy in New Computing Environments: Third EAI International Conference, SPNCE 2020, Lyngby, Denmark, 6–7 August 2020. [Google Scholar]
- Alevizos, L.; Ta, V.T.; Hashem Eiza, M. Augmenting zero trust architecture to endpoints using blockchain: A state-of-the-art review. Secur. Priv. 2022, 5, 191. [Google Scholar] [CrossRef]
- Palmo, Y.; Tanimoto, S.; Sato, H.; Kanai, A. Optimal Federation Method for Embedding Internet of Things in Software-Defined Perimeter. IEEE Consum. Electron. Mag. 2022, 12, 68–75. [Google Scholar] [CrossRef]
- Valero, J.M.J.; Sánchez, P.M.S.; Lekidis, A.; Hidalgo, J.F.; Pérez, M.G.; Siddiqui, M.S.; Celdrán, A.H.; Pérez, G.M. Design of a Security and Trust Framework for 5G Multi-domain Scenarios. J. Netw. Syst. Manag. 2022, 30, 7. [Google Scholar] [CrossRef]
- Li, S.; Iqbal, M.; Saxena, N. Future industry internet of things with zero-trust security. Inf. Syst. Front. 2022, 1–14. [Google Scholar] [CrossRef]
- Chen, Z.; Yan, L.; Lü, Z.; Zhang, Y.; Guo, Y.; Liu, W.; Xuan, J. Research on zero-trust security protection technology of power IoT based on blockchain. In Proceedings of the 5th International Conference on Computer Science and Information Engineering (ICCSIE 2020), Dalian, China, 23–25 October 2020. [Google Scholar]
- Zhang, X.; Chen, L.; Fan, J.; Wang, X.; Wang, Q. Power IoT security protection architecture based on zero trust framework. In Proceedings of the 2021 IEEE 5th International Conference on Cryptography, Security and Privacy (CSP), Zhuhai, China, 8–10 January 2021. [Google Scholar]
- Rapuzzi, R.; Repetto, M. Building situational awareness for network threats in fog/edge computing: Emerging paradigms beyond the security perimeter model. Future Gener. Comput. Syst. 2018, 85, 235–249. [Google Scholar] [CrossRef]
- Mehraj, S.; Banday, M.T. Establishing a zero trust strategy in cloud computing environment. In Proceedings of the 2020 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 22–24 January 2020. [Google Scholar]
- Hunker, J.; Probst, C.W. Insiders and Insider Threats-An Overview of Definitions and Mitigation Techniques. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2011, 2, 4–27. [Google Scholar]

| Author(s) | Year | Title | Publication Type | View |
|---|---|---|---|---|
| Kindervag, J. [3] | 2010 | No more chewy centers: Introducing the zero trust model of information security | Institution Research Report | Trust is a vulnerability and, like all vulnerabilities, should be eliminated; zero trust should consider the flaws of security perimeters facing internal threats and the risks arising from implicit trust. |
| Cloud Security Alliance [8] | 2013 | Software Defined Perimeter | Institution Publication | A new approach is needed that enables application owners to protect infrastructure in a public or private cloud, a server in a data center, or even inside an application server. |
| Ward, R.; Beyer, B. [5] | 2014 | Beyondcorp: A new approach to enterprise security | Institution Research Report | The perimeter is no longer just the physical location of the enterprise, and what lies inside the perimeter is no longer a blessed and safe place to host personal computing devices and enterprise applications; fat-client applications that use proprietary protocols to talk to servers will be a challenge for moving to BeyondCorp. |
| Osborn, B.; McWilliams, J.; Beyer, B.; Saltonstall, M. [6] | 2016 | Beyondcorp: Design to deployment at Google | Institution Research Report | Correct trust assessment requires ensuring data quality and relevance; the sparsity of data sets will hinder the use of high-productivity applications, and it is necessary to monitor and verify whether these data can produce expected results when used for trust assessment; the unique implementation of obtaining information from multiple data sources requires simplifying the data dissemination method to control latency; fundamental changes to the security infrastructure can potentially adversely affect the productivity of the entire company’s workforce; various fail-safes need to be deployed to reduce the impact of catastrophic failures. |
| Kindervag, J. [21] | 2016 | No more chewy centers: The zero trust model of information security | Institution Research Report | Perimeter-based network security models fail to protect against today’s threats; eliminate chewy centers with the zero trust model; zero trust is not a one-time project. |
| Escobedo, V.; Beyer, B.; Saltonstall, M.; Zyzniewski, F. [7] | 2017 | BeyondCorp: the user experience | Institution Research Report | The deployment of BeyondCorp needs to take into account the user’s learning cost, user experience and workflow, which is also what other zero trust solutions need to focus on. |
| Eidle, D.; Ni, S.Y.; DeCusatis, C.; Sager, A. [25] | 2017 | Autonomic security for zero trust networks | Conference Paper | Automated systems could improve both efficiency and response time to immediate threats; increased automation of cyber-defense leveraging OODA, and autonomic principles holds potential for defending cloud and enterprise data center networks. |
| ACT-IAC Zero trust Project Team [19] | 2019 | Zero trust Cybersecurity Current Trends | Institution Research Report | Zero trust is not a technology in and of itself but a shift in the design approach for cybersecurity; zero trust can augment and compliment other cybersecurity tools and practices rather than replacing them. |
| Moubayed, A.; Refaey, A.; Shami, A. [26] | 2019 | Software-Defined Perimeter (SDP): State of the Art Secure Solution for Modern Networks | Journal Paper | SDP faces the challenges of security, privacy and availability; exploring how to integrate SDP with other paradigms such as SDN and NFV is essential. |
| Kumar, P.; Moubayed, A.; Refaey, A.; Shami, A.; Koilpillai, J. [27] | 2019 | Performance analysis of sdp for secure internal enterprises | Conference Paper | SDP suffers from long connection setup time but it can provide robustness to the network under threats; SDP provides protection against a wide range of attack, it cannot guarantee complete protection. |
| Rose, S.; Borchert, O.; Mitchell, S.; Connelly, S. [9] | 2020 | Zero trust architecture | Institution Publication | Zero is not a single architecture but a set of guiding principles for workflow, system design and operations; Organizations should seek to incrementally implement zero trust principles, process changes, and technology solutions; Organizations need to implement comprehensive information security and resiliency practices for zero trust to be effective. |
| Campbell, M. [24] | 2020 | Beyond zero trust: Trust is a vulnerability | Journal Editorial | The attack surface is never static, never localized, and never impregnable; zero trust solutions will mature and become the security strategy standard as they grow more automated, smart, and extended. |
| Singh, J.; Refaey, A.; Shami, A. [28] | 2020 | Multilevel security framework for nfv based on software defined perimeter | Journal Paper | There is a need for an additional security framework to improve the NFV security solutions; the install deployment of SDP has problems such as difficulty in certificate distribution and complicated installation process; the potential for attacks originating from inside a secured network is an open challenge which NFV-SDP could mitigate, in theory. |
| NSA Cybersecurity Requirements Center [22] | 2021 | Embracing a Zero trust Security Model | Institution Research Report | The scalability of the capabilities is essential for applying zero trust; implementing Zero Trust should not be undertaken lightly and will require significant resources and persistence to achieve. |
| Garbis, J.; Chapman, J.W. [23] | 2021 | What Is Zero Trust? | Book Chapter | A Zero Trust system is an integrated security platform that uses contextual information from identity, security, and IT Infrastructure; and risk and analytics tools to inform and enable the dynamic enforcement of security policies uniformly across the enterprise. |
| Syed, N.F.; Shah, S.W.; Shaghaghi, A.; Anwar, A.; Baig, Z.; Doss, R. [29] | 2022 | Zero trust architecture (zta): A comprehensive survey | Journal Paper | A lightweight and scalable continuous authentication mechanism is essential to achieve trust for resources; a fine-grained contextual access control scheme is needed to adapt to different network environments; the goal of ZTA is to protect data, and encryption is an important requirement to achieve zero trust; ZTA requires micro-segmentation to prevent attackers from lateral movement, and the single point of failure issues need to be addressed; an effective feedback system is needed to provide ZTA with threat intelligence and security situational awareness; ZTA requires reliable trust assessment capabilities to implement dynamic access control and could use ML to provide automatic learning capabilities; the fuzziness and heterogeneity of data require a more variable trust mechanism. |
| Leahy, D.; Thorpe, C. [37] | 2022 | Zero Trust Container Architecture (ZTCA): A Framework for Applying Zero Trust Principals to Docker Containers | Conference Paper | The security issues of Docker deployment can be solved based on whether the components deployed by Docker belong to trust zones rather than focusing on specific attacks; the implicit trust that Docker users place on the Docker engine is a recipe for security issues, and this is exactly what ZTA can alleviate. |
| Author(s) | Year | Title | Publication Type | View |
|---|---|---|---|---|
| DeCusatis, C.; Liengtiraphan, P.; Sager, A.; Pinelli, M. [39] | 2016 | Implementing zero trust cloud networks with transport access control and first packet authentication | Conference Paper | Traditional VLANs and similar network segmentation technologies do not provide sufficient network security; penetration testing is required to identify and mitigate any additional vulnerabilities of the scheme. |
| Samaniego, M.; Deters, R. [46] | 2018 | Zero trust hierarchical management in IoT | Conference Paper | Neither the infrastructure in IoT nor the transactions performed by the infrastructure can be trusted; the resource-constrained environment of IoT makes zero trust solutions using a central trust verification authority difficult to implement. |
| Zaheer, Z.; Chang, H.; Mukherjee, S.; Van der Merwe, J. [40] | 2019 | eZTrust: Network-independent zero trust perimeterization for microservices | Conference Paper | Traditional perimeterization approaches do not fare well in highly dynamic microservices environments; eZTrust could expand in tag granularity, tag anonymization, smart NIC offload and platform compatibility. |
| Dhar, S.; Bose, I. [47] | 2021 | Securing IoT devices using zero trust and blockchain | Journal Paper | The implementation of standard security mechanisms, such as access control, session management, and cryptography mechanism, is difficult for IoT networks; ways need to be found to measure the reliability of the proposed framework in real-world IoT networks. |
| Zhao, S.; Li, S.; Li, F.; Zhang, W.; Iqbal, M. [48] | 2021 | Blockchain-enabled user authentication in zero trust internet of things | Conference Paper | The heterogeneity and security of IoT require each device to authenticate before being granted access, ensuring serverless, passwordless, self-sovereign security. |
| Chen, Z.; Yan, L.; Lü, Z.; Zhang, Y.; Guo, Y.; Liu, W.; Xuan, J. [53] | 2021 | Research on zero trust security protection technology of power IoT based on blockchain | Conference Paper | Traditional network security technology that relies on the central organization cannot meet the high security requirements of the development of the new energy Internet business; the power terminal has a wide deployment range, uncontrolled on-site environment, and complex vulnerability risk handling that will provide attackers with opportunities to threat energy network. |
| Zhang, X.; Chen, L.; Fan, J.; Wang, X.; Wang, Q. [54] | 2021 | Power IoT security protection architecture based on zero trust framework | Conference Paper | The gradual implementation of the power IoT will bring new demands such as massive access, heterogeneous authentication, and frequent interactions, and existing security protection methods are not enough to cope with them; in the construction of the power IoT, in addition to considering the identity management of people, it is also necessary to authenticate the identity of devices, applications, and services. |
| Liu, S.; Zhuang, Y.; Huang, L.; Zhou, X. [41] | 2022 | Exploiting lsb self-quantization for plaintext-related image encryption in the zero trust cloud | Journal Paper | Existing plaintext-related image encryption schemes cannot meet the requirements of ZT in both reducing implementation overhead and resisting multiple attacks. |
| Zolotukhin, M.; Hämäläinen, T.; Kotilainen, P. [42] | 2022 | Intelligent Solutions for Attack Mitigation in Zero Trust Environments | Journal Paper | The requirement for dynamic updates of access policies in IoT requires that deployed zero trust models dynamically adjust security policies to reduce the ongoing attack surface and minimize the risk of subsequent attacks; traffic from real devices and applications is needed to validate the effectiveness and scalability of the framework. |
| Sarkar, S.; Choudhary, G.; Shandilya, S.K.; Hussain, A.; Kim, H. [43] | 2022 | Security of zero trust networks in cloud computing: A comparative review | Journal Paper | Zero Trust can also be combined and used with other novel technologies such as blockchain and the IoT; zero trust under 5G/6G networks can use AI to quickly prevent malicious requests and network performance degradation to serve mission-critical areas such as healthcare, military, and autonomous driving; zero trust can serve national security needs as a technology to prevent adversaries from entering military networks; using zero trust in containerized software, microservices, and sustainable cloud systems requires greater focus on performance, security, reliability, and sustainability. |
| Alevizos, L.; Ta, V.T.; Hashem Eiza, M. [49] | 2022 | Augmenting zero trust architecture to endpoints using blockchain: A state-of-the-art review | Journal Paper | A compromised endpoint’s authenticated and authorized session can perform limited activities, becoming ZTA’s Achilles’ heel; using blockchain-based intrusion detection and authentication in ZTA requires full consideration of issues such as performance, computational overhead, and appropriate blockchain implementation. |
| Palmo, Y.; Tanimoto, S.; Sato, H.; Kanai, A. [50] | 2022 | Optimal Federation Method for Embedding Internet of Things in Software-Defined Perimeter | Journal Paper | When embedding IoT devices into SDP, it is imperative to ensure the reliability of the IoT device. |
| Valero, J.M.J.; Sánchez, P.M.S.; Lekidis, A.; Hidalgo, J.F.; Pérez, M.G.; Siddiqui, M.S.; Celdrán, A.H.; Pérez, G.M. [51] | 2022 | Design of a Security and Trust Framework for 5G Multi-domain Scenarios | Journal Paper | 5G networks require security and trust mechanisms covering multi-domain scenarios to achieve complete isolation of network slices, thereby preventing unauthorized and malicious entities from accessing 5G infrastructure; for 5G networks, the zero trust approach can not only guarantee data and services intra-and inter-domain protection, but also all enterprise resources and subjects, thereby enclosing the security and trust threat landscape. |
| Li, S.; Iqbal, M.; Saxena, N. [52] | 2022 | Future industry internet of things with zero trust security | Journal Paper | Developing security policies and hybrid policy definitions to be followed on 5G networks is very important for the application of zero trust model on 5G; The zero trust model’s continuous monitoring and analysis of each device hinders latency, which in turn affects its use in IoT. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kang, H.; Liu, G.; Wang, Q.; Meng, L.; Liu, J. Theory and Application of Zero Trust Security: A Brief Survey. Entropy 2023, 25, 1595. https://doi.org/10.3390/e25121595
Kang H, Liu G, Wang Q, Meng L, Liu J. Theory and Application of Zero Trust Security: A Brief Survey. Entropy. 2023; 25(12):1595. https://doi.org/10.3390/e25121595
Chicago/Turabian StyleKang, Hongzhaoning, Gang Liu, Quan Wang, Lei Meng, and Jing Liu. 2023. "Theory and Application of Zero Trust Security: A Brief Survey" Entropy 25, no. 12: 1595. https://doi.org/10.3390/e25121595
APA StyleKang, H., Liu, G., Wang, Q., Meng, L., & Liu, J. (2023). Theory and Application of Zero Trust Security: A Brief Survey. Entropy, 25(12), 1595. https://doi.org/10.3390/e25121595







