Physical Layer Security: Channel Sounding Results for the Multi-Antenna Wiretap Channel
Abstract
1. Introduction
2. Notation
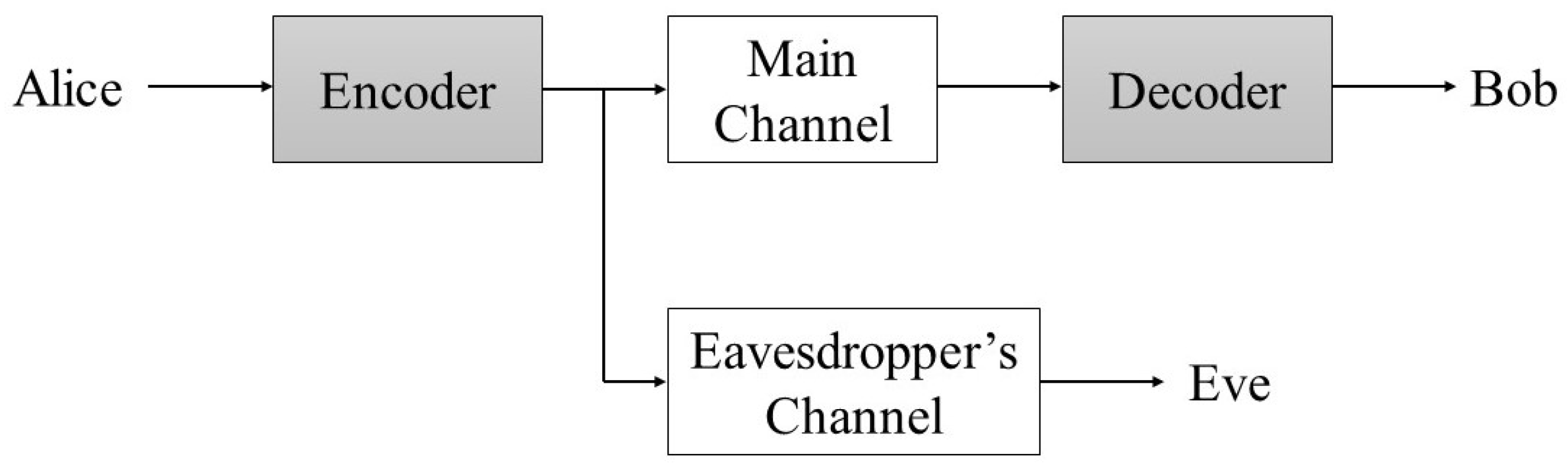
3. Channel Model and System Setup
3.1. MIMOME Secrecy Capacity
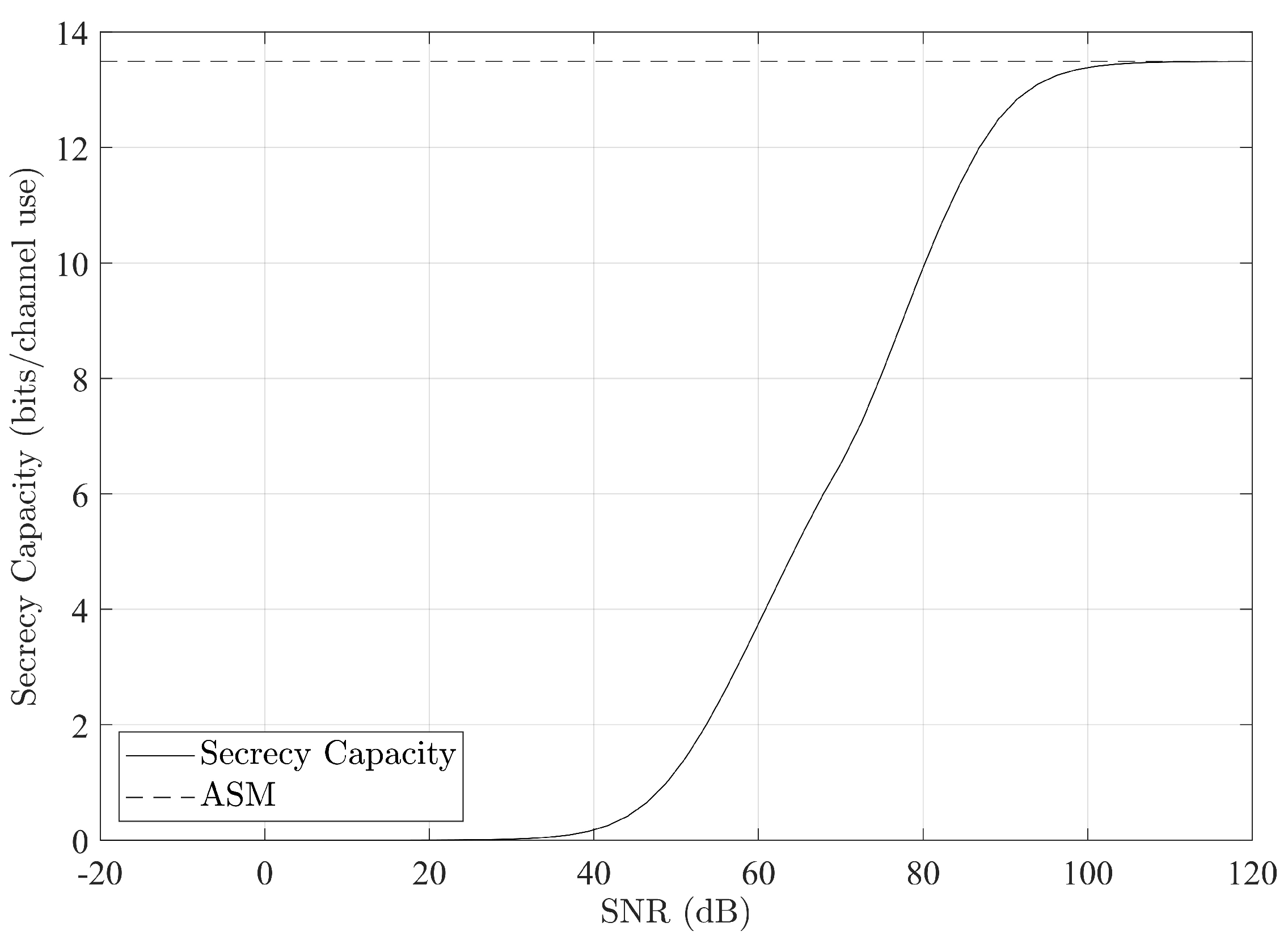
3.2. High-SNR Asymptotic Results
3.3. Note on Multi-Carrier Waveforms
3.4. Brute-Force Optimization
4. Channel Sounding
4.1. Environments
4.2. Materials and Methods
4.3. Channel Sounding Results and Discussion
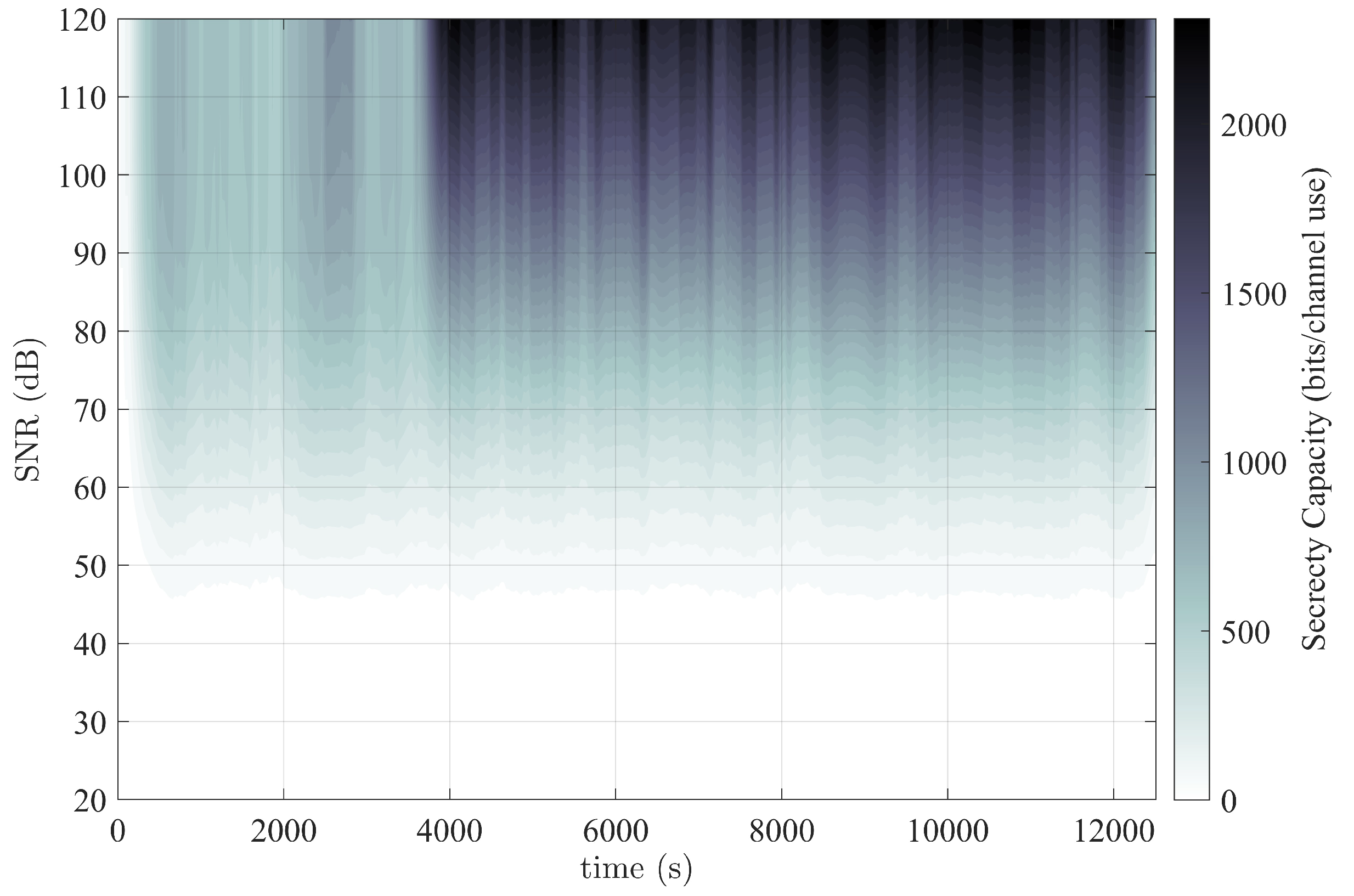
4.3.1. Temporal Experiment
4.3.2. Spatial Experiment
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| MDPI | Multidisciplinary Digital Publishing Institute |
| SISO | Single-Input, Single-Output |
| MIMO | Multi-Input, Multi-Output |
| MIMOME | Multi-Input, Multi-Output, Multi-Eavesdropper |
| CSI | Channel State Information |
| OFDM | Orthogonal Frequency Division Multiplexing |
| IOT | Internet of Things |
| V2V | Vehicle to Vehicle |
| SNR | Signal to Noise Ratio |
| IEEE | Institute of Electrical and Electronics Engineers |
| GSVD | Generalized Singular Value Decomposition |
| KKT | Karush Kuhn Tucker |
References
- Shor, P. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar] [CrossRef]
- Shannon, C.E. A mathematical theory of communication. Bell Syst. Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Bloch, M.; Barros, J. Physical-Layer Security: From Information Theory to Security Engineering; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
- Zhou, X.; Song, L.; Zhang, Y. Physical Layer Security in Wireless Communications; CRC Press: Boca Raton, FL, USA, 2016. [Google Scholar]
- Mucchi, L.; Nizzi, F.; Pecorella, T.; Fantacci, R.; Esposito, F. Benefits of Physical Layer Security to Cryptography: Tradeoff and Applications. In Proceedings of the IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom), Sochi, Russia, 3–6 June 2019; pp. 1–3. [Google Scholar] [CrossRef]
- Mukherjee, A.; Fakoorian, S.A.A.; Huang, J.; Swindlehurst, A.L. Principles of Physical Layer Security in Multiuser Wireless Networks: A Survey. IEEE Commun. Surv. Tutor. 2014, 16, 1550–1573. [Google Scholar] [CrossRef]
- Harrison, W.K.; Almeida, J.; Bloch, M.R.; McLaughlin, S.W.; Barros, J. Coding for Secrecy: An Overview of Error-Control Coding Techniques for Physical-Layer Security. IEEE Sign Process. Mag. 2013, 30, 41–50. [Google Scholar] [CrossRef]
- Shannon, C.E. Communication theory of secrecy systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Khisti, A.; Wornell, G.W. Secure Transmission With Multiple Antennas—Part II: The MIMOME Wiretap Channel. IEEE Trans. Inf. Theory 2010, 56, 5515–5532. [Google Scholar] [CrossRef]
- Oggier, F.; Hassibi, B. The Secrecy Capacity of the MIMO Wiretap Channel. IEEE Trans. Inf. Theory 2011, 57, 4961–4972. [Google Scholar] [CrossRef]
- Liu, T.; Shamai, S. A Note on the Secrecy Capacity of the Multiple-Antenna Wiretap Channel. IEEE Trans. Inf. Theory 2009, 55, 2547–2553. [Google Scholar] [CrossRef]
- Duong, T.Q.; Zhou, X.S.; Poor, H.V. Trusted Communications with Physical Layer Security for 5G and Beyond; The Institution of Engineering and Technology: London, UK, 2017; p. 439. [Google Scholar]
- Jensen, B.; Clark, B.; Flanary, D.; Norman, K.; Rice, M.; Harrison, W.K. Physical-Layer Security: Does it Work in a Real Environment? In Proceedings of the IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Rice, M.; Clark, B.; Flanary, D.; Jensen, B.; Nelson, N.; Norman, K.; Perrins, E.; Harrison, W.K. Physical-Layer Security for Vehicle-to-Everything Networks: Increasing Security While Maintaining Reliable Communications. IEEE Veh. Technol. Mag. 2020, 15, 68–76. [Google Scholar] [CrossRef]
- Li, Z.; Yates, R.; Trappe, W. Secrecy Capacity of Independent Parallel Channels. In Securing Wireless Communications at the Physical Layer; Springer: Boston, MA, USA, 2010; pp. 1–18. [Google Scholar]
- Renna, F.; Laurenti, N.; Poor, H.V. Physical-Layer Secrecy for OFDM Transmissions Over Fading Channels. IEEE Trans. Inf. Forensics Secur. 2012, 7, 1354–1367. [Google Scholar] [CrossRef]
- Tse, D.; Viswanath, P. Fundamentals of Wireless Communication; Cambridge University Press: Cambridge, UK, 2013. [Google Scholar]
- Brown, T.; DeCarvalho, E.; Kyritsi, P. Practical Guide to the MIMO Radio Channel: With MATLAB Examples; Wiley: Hoboken, NJ, USA, 2012. [Google Scholar]
- Yang, T.; Taghizadeh, O.; Mathar, R. SEE of Full-Duplex Multi-carrier Bidirectional Wiretap Channels with Multiple Eavesdroppers. In Proceedings of the 2019 IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–18 April 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Goldsmith, A.; Jafar, S.; Jindal, N.; Vishwanath, S. Capacity limits of MIMO channels. IEEE J. Sel. Areas Commun. 2003, 21, 684–702. [Google Scholar] [CrossRef]
- Cuan-Cortes, J.V.; Vargas-Rosales, C.; Munoz-Rodriguez, D. MIMO channel capacity using antenna selection and water pouring. EURASIP J. Wirel. Commun. Netw. 2014, 2014, 288. [Google Scholar] [CrossRef][Green Version]
- Mukherjee, A.; Ottersten, B.; Tran, L.N. On the Secrecy Capacity of MIMO Wiretap Channels: Convex Reformulation and Efficient Numerical Methods. IEEE Trans. Commun. 2021, 69, 6865–6878. [Google Scholar] [CrossRef]
- Mukherjee, A.; Kumar, V.; Jorswieck, E.; Ottersten, B.; Tran, L.N. On the Optimality of the Stationary Solution of Secrecy Rate Maximization for MIMO Wiretap Channel. IEEE Wirel. Commun. Lett. 2022, 11, 357–361. [Google Scholar] [CrossRef]
- Gursoy, M.C. Secure Communication in the Low-SNR Regime. IEEE Trans. Commun. 2012, 60, 1114–1123. [Google Scholar] [CrossRef]
- Xie, Y.; Li, Z.; Li, M. Precise Power Delay Profiling with Commodity Wi-Fi. IEEE Trans. Mob. Comput. 2019, 18, 1342–1355. [Google Scholar] [CrossRef]



Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Harman, D.; Knapp, K.; Sweat, T.; Lundrigan, P.; Rice, M.; Harrison, W. Physical Layer Security: Channel Sounding Results for the Multi-Antenna Wiretap Channel. Entropy 2023, 25, 1397. https://doi.org/10.3390/e25101397
Harman D, Knapp K, Sweat T, Lundrigan P, Rice M, Harrison W. Physical Layer Security: Channel Sounding Results for the Multi-Antenna Wiretap Channel. Entropy. 2023; 25(10):1397. https://doi.org/10.3390/e25101397
Chicago/Turabian StyleHarman, Daniel, Karl Knapp, Tyler Sweat, Philip Lundrigan, Michael Rice, and Willie Harrison. 2023. "Physical Layer Security: Channel Sounding Results for the Multi-Antenna Wiretap Channel" Entropy 25, no. 10: 1397. https://doi.org/10.3390/e25101397
APA StyleHarman, D., Knapp, K., Sweat, T., Lundrigan, P., Rice, M., & Harrison, W. (2023). Physical Layer Security: Channel Sounding Results for the Multi-Antenna Wiretap Channel. Entropy, 25(10), 1397. https://doi.org/10.3390/e25101397









