From Random Numbers to Random Objects
Abstract
1. Introduction and Basic Concepts
1.1. Basic Concepts
1.1.1. Integer Compositions
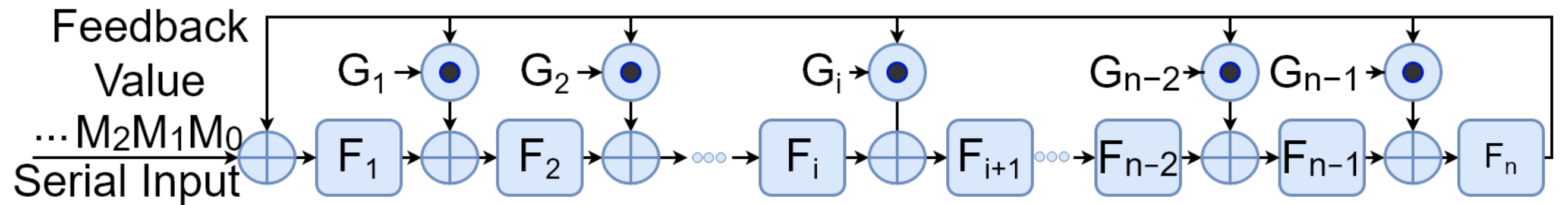
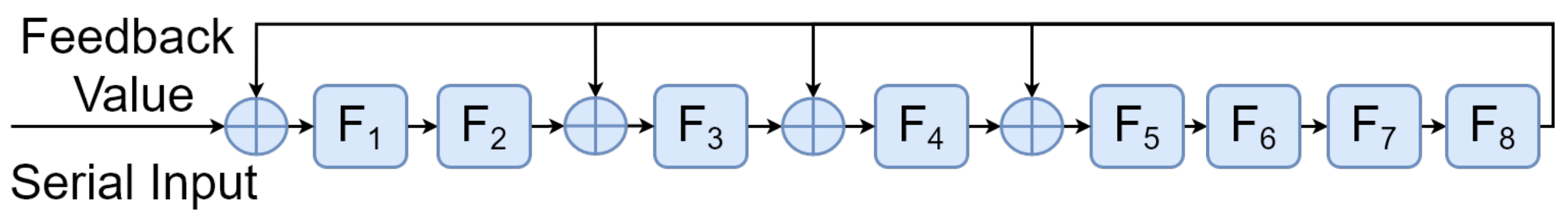
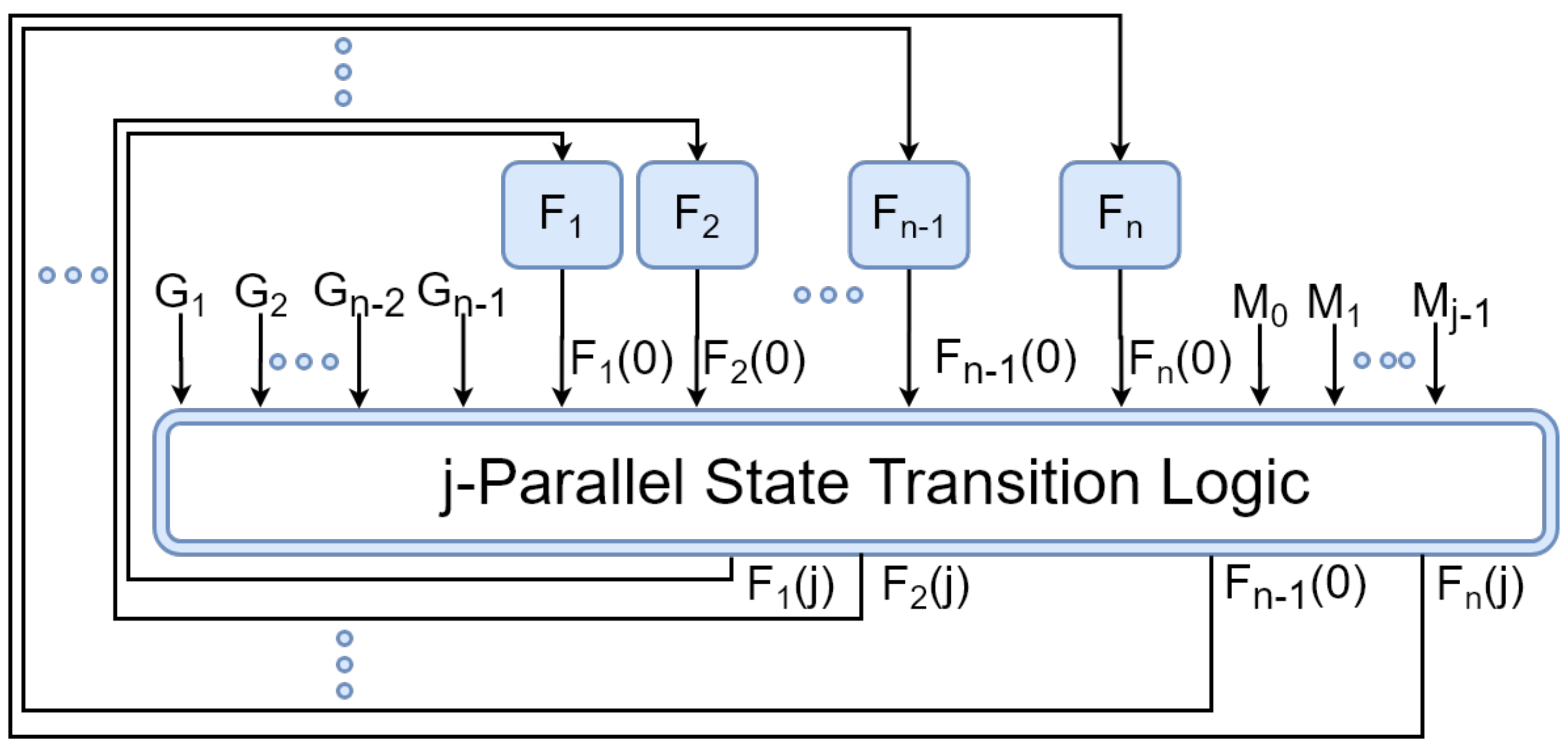
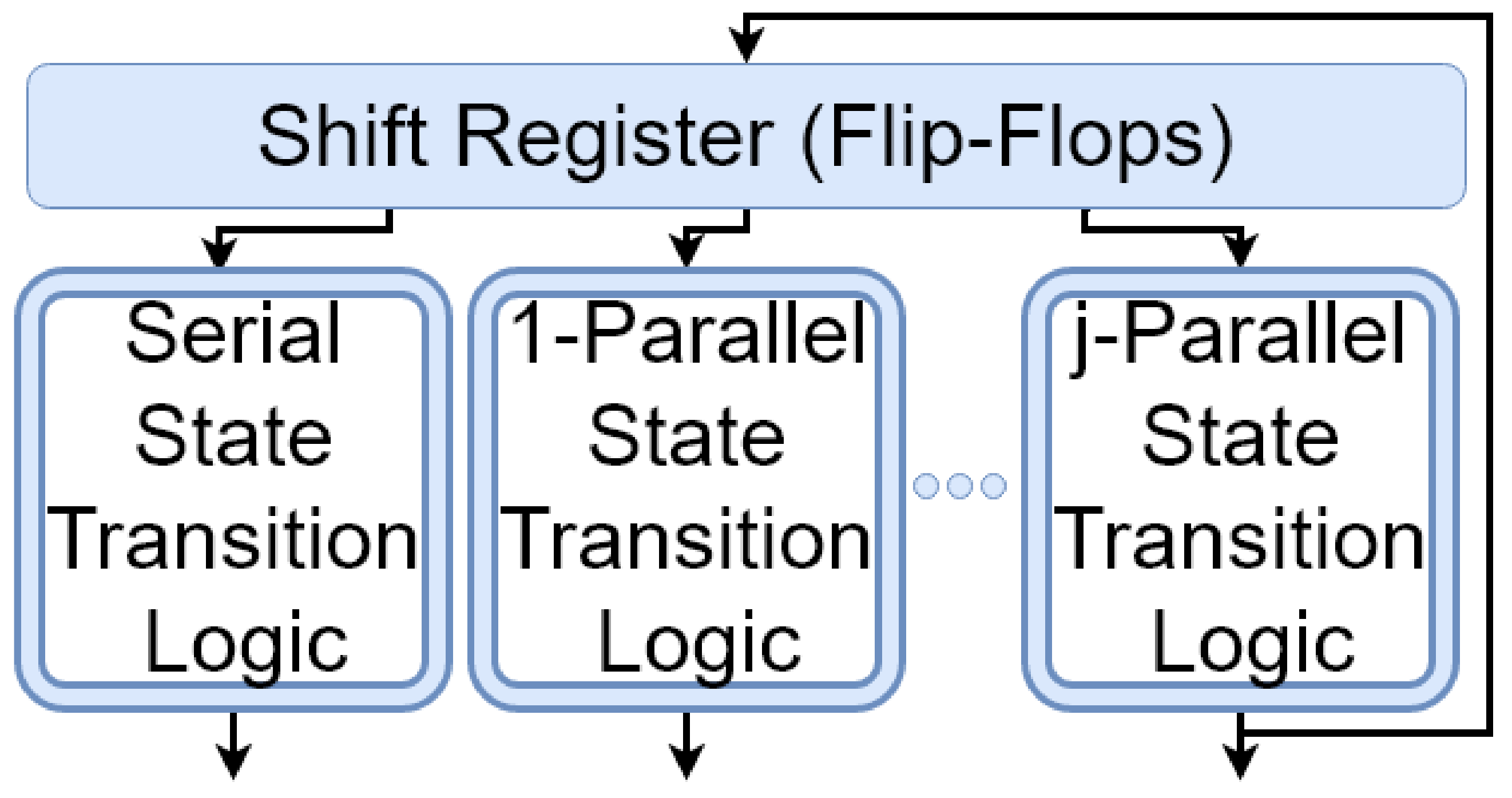
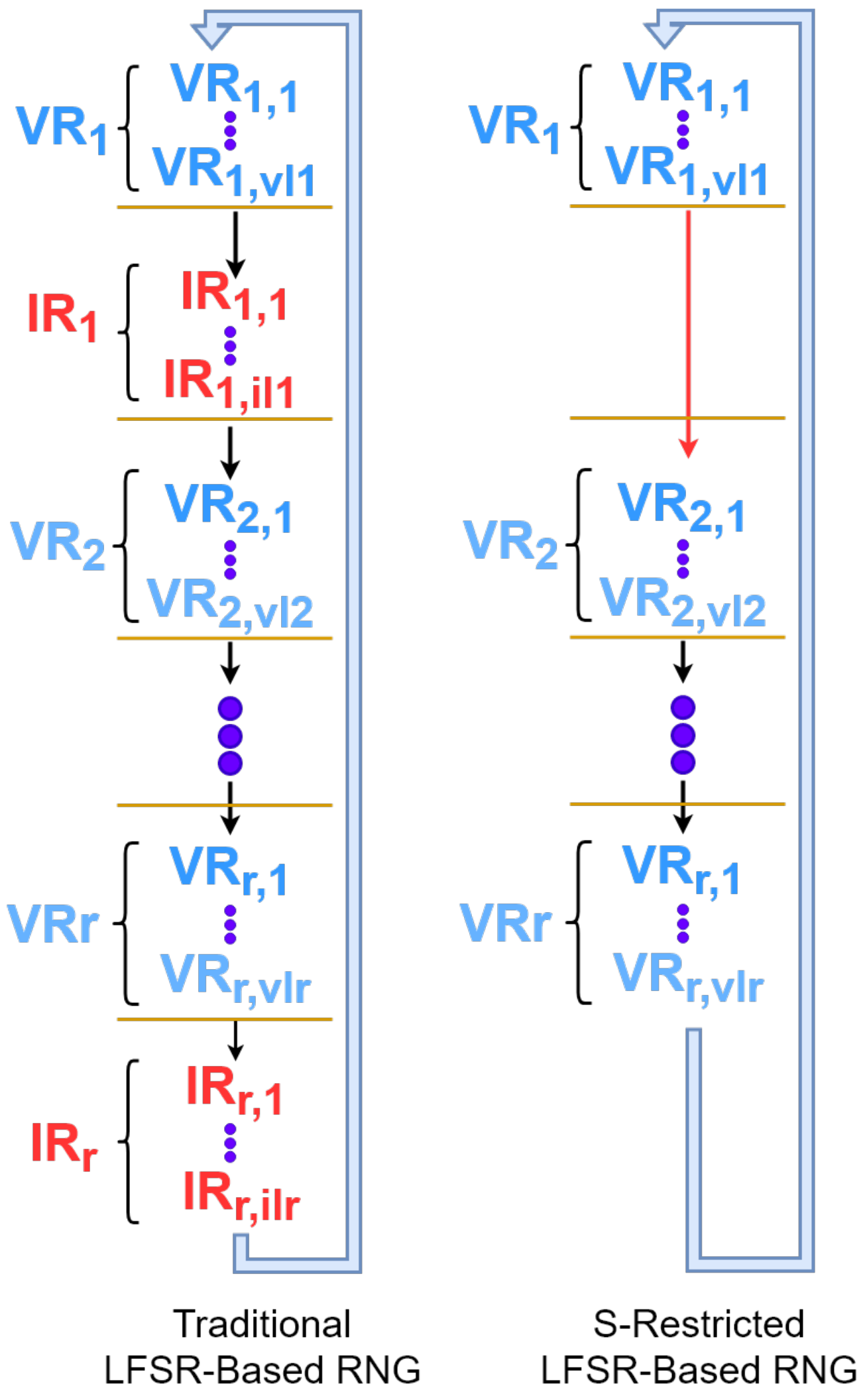
1.1.2. Parallel LFSRs
1.1.3. S-Restricted RNGs
1.1.4. Latin Squares
1.2. Organization
2. Preliminaries
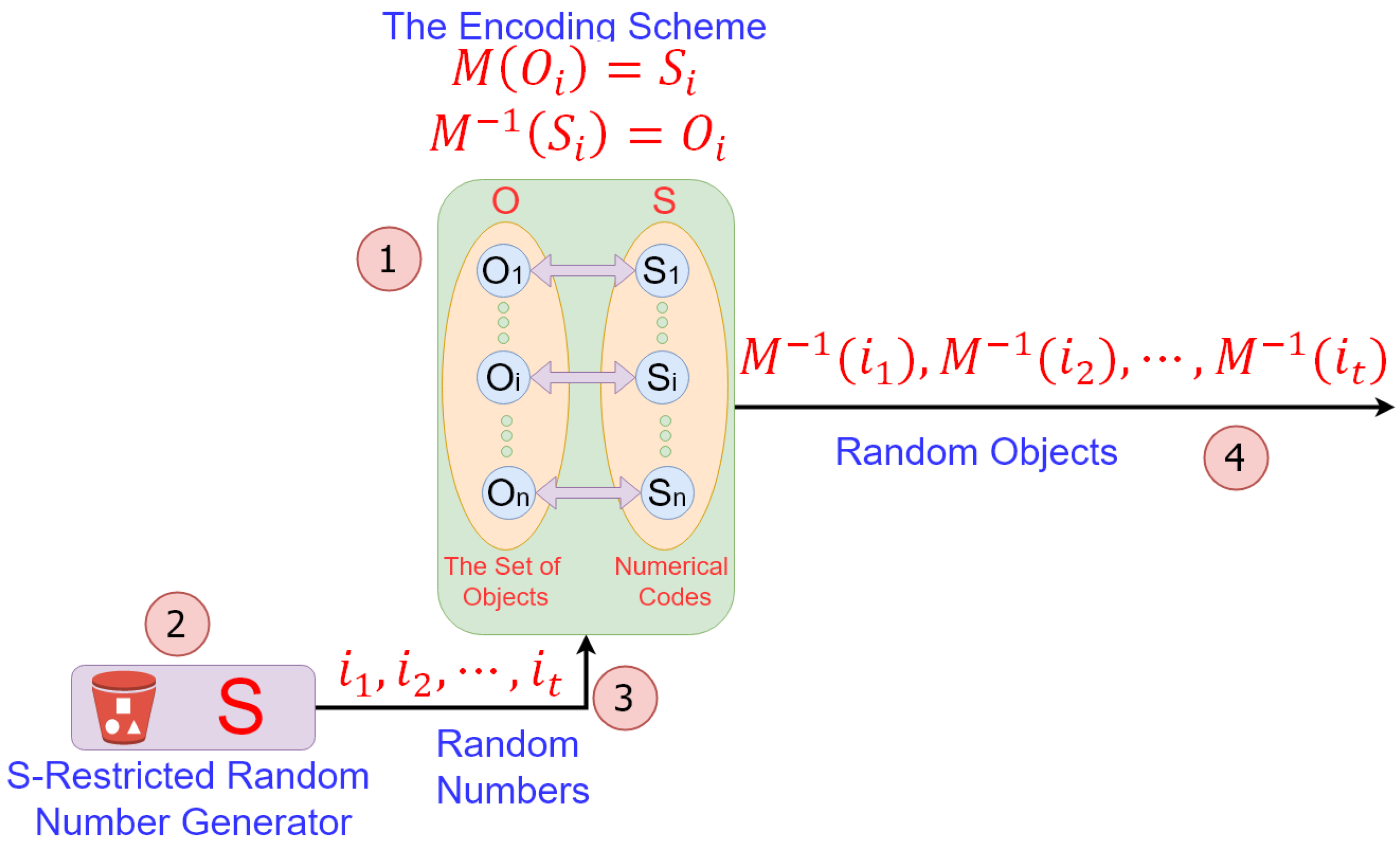
2.1. Problem Statement
2.2. Challenges
- 1.
- The first challenge here is to find or to build an RNG for which the set of possible outputs is exactly equal to the set of codes assigned to the objects. For example, for random permutations, we require encoding schemes that assign codes from to permutations of q objects [19]. Each of the mentioned codes can be represented by binary digits. However, a l-bit RNG usually generates all elements of , while of them are invalid. We address this challenge by introducing S-restricted RNGs, which generate random numbers drawn from a given set S.
- 2.
- The second challenge is that the encoding scheme will most likely be different from one problem to another. For example, an encoding scheme proposed for passwords may not be applicable to CAPTCHAs as the statistical properties of valid passwords are totally different from those of valid CAPTCHAs.
- 3.
- Third, the S-restricted RNG will be dependent on the encoding scheme and consequently on the target set of objects. This component will vary from Latin squares of order n to the same squares of order . We address this challenge as well as the above one via proposing the use of reconfigurable S-restricted RNGs. In our case study, this challenge is resolved in two ways. First, our proposed architecture for designing S-restricted RNG is capable of adopting any kind of parallel RNG. Second, we use programmable parallel LFSRs instead of fixed-polynomial parallel LFSRs to improve the reconfigurability of the design. Existing methods for designing parallel LFSRs work only with a fixed generating polynomial [20,21]. In addition to inadequate reconfigurability, fixed-polynomial LFSRs make the system more vulnerable against some well-known security attacks [22].
2.3. Problem Solving Approach
2.4. Novelties and Contributions
- 1.
- In this paper, we unify all problems related to random generation of non-numerical entities for the first time. We bring all these problems under a single umbrella via posing and formulating the general problem of random object generation (Section 2.1).
- 2.
- This paper is the first to propose a solution suitable for generating random instances of any kind of non-numerical entity. Our solution depends on two core components. The first component is a proper encoding scheme assigning a unique code to every individual object. The second component is an RNG capable of generating random numbers restricted to the set of assigned numeric codes (Section 2.3).
- 3.
- In this paper, we propose a novel approach based on integer compositions for automatic design of programmable parallel LFSRs (Section 4);
- 4.
- In this paper, we introduce the notion of S-restricted, RNGs for the first time. Moreover, we present a novel method for designing S-restricted RNGs using parallel LFSRs (Section 5);
- 5.
- This paper presents the first encoding scheme for Latin squares. This encoding is essentially en extended variant of Lehmer’s code previously proposed for encoding permutations of a set of objects (Section 6.1);
- 6.
- We propose the first circuit for generating random Latin squares of degree 4 (Section 6.2).
3. Background and Related Works
3.1. Random Numbers
3.2. LFSRs and Parallel LFSRs
3.3. Random Non-Numerical Entities
Random Latin Squares
3.4. Most Relevant Works
3.4.1. Restricted RNGs
3.4.2. RNGs and Random Non-Numerical Entities
3.5. Motivations
4. Automatic Design of Parallel LFSRs Using Integer Compositions
4.1. Expression Derivation
| Algorithm 1 create given |
| Requires: . |
| Ensures: . |
| 1: procedure CreateNextComp() |
| 2: |
| 3: for all do |
| 4: |
| 5: |
| 6: end for |
| 7: return |
| 8: end procedure |
4.2. Generation Procedures
| Algorithm 2 Create |
| Requires: n is a positive integer. |
| Ensures: . |
| 1: procedureCreateComp(n) |
| 2: if then |
| 3: |
| 4: else |
| 5: |
| 6: |
| 7: end if |
| 8: return |
| 9:end procedure |
| Algorithm 3 Create |
| Requires: n is a positive integer. |
| Ensures: . |
| 1: procedure CreatePal(n) |
| 2: if then |
| 3: |
| 4: else |
| 5: |
| 6: |
| 7: for all do |
| 8: |
| 9: |
| 10: |
| 11: end for |
| 12: end if |
| 13: return |
| 14: end procedure |
| Algorithm 4 Create S-restricted palindromic compositions |
| Requires: n a positive integer, S a set of positive integers. |
| Ensures: if , if . |
| 1: procedure CreateSRestPal(n,S) |
| 2: |
| 3: |
| 4: if then |
| 5: ▹ A set consisting of an empty composition |
| 6: return |
| 7: end if |
| 8: if then |
| 9: |
| 10: |
| 11: end if |
| 12: |
| 13: for all do |
| 14: for all do |
| 15: ▹ Concatenate s to the left and the right of c |
| 16: |
| 17: |
| 18: end for |
| 19: end for |
| 20: if then |
| 21: |
| 22: end if |
| 23: return |
| 24: end procedure |
- 1.
- if . There are only two statements in Procedure CreateSRestPa that add compositions to : Statement 9 and Statement 16. Statement 9 adds , which is definitely an element of considering . Moreover, Statement 16 adds , which is an element of since , and . Thus, whatever Procedure CreateSRestPa adds to C is an element of .
- 2.
- if . may consist of two kinds of compositions.
- : This composition is added by Statement 9 if .
- : All of these compositions are added by Statement 16.
Thus, every element of is guaranteed to be generated by Procedure CreateSRestPa.converted to . - 3.
- if and only if .The above two statements show that . It is immediate that, if , Procedure CreateSRestPa will generate no composition. Since 1 is assigned to G only after adding compositions to (by Statements 9 and 16), Statement 21 sets if . On the other hand, will not be equal to if because is executed after generating each composition.
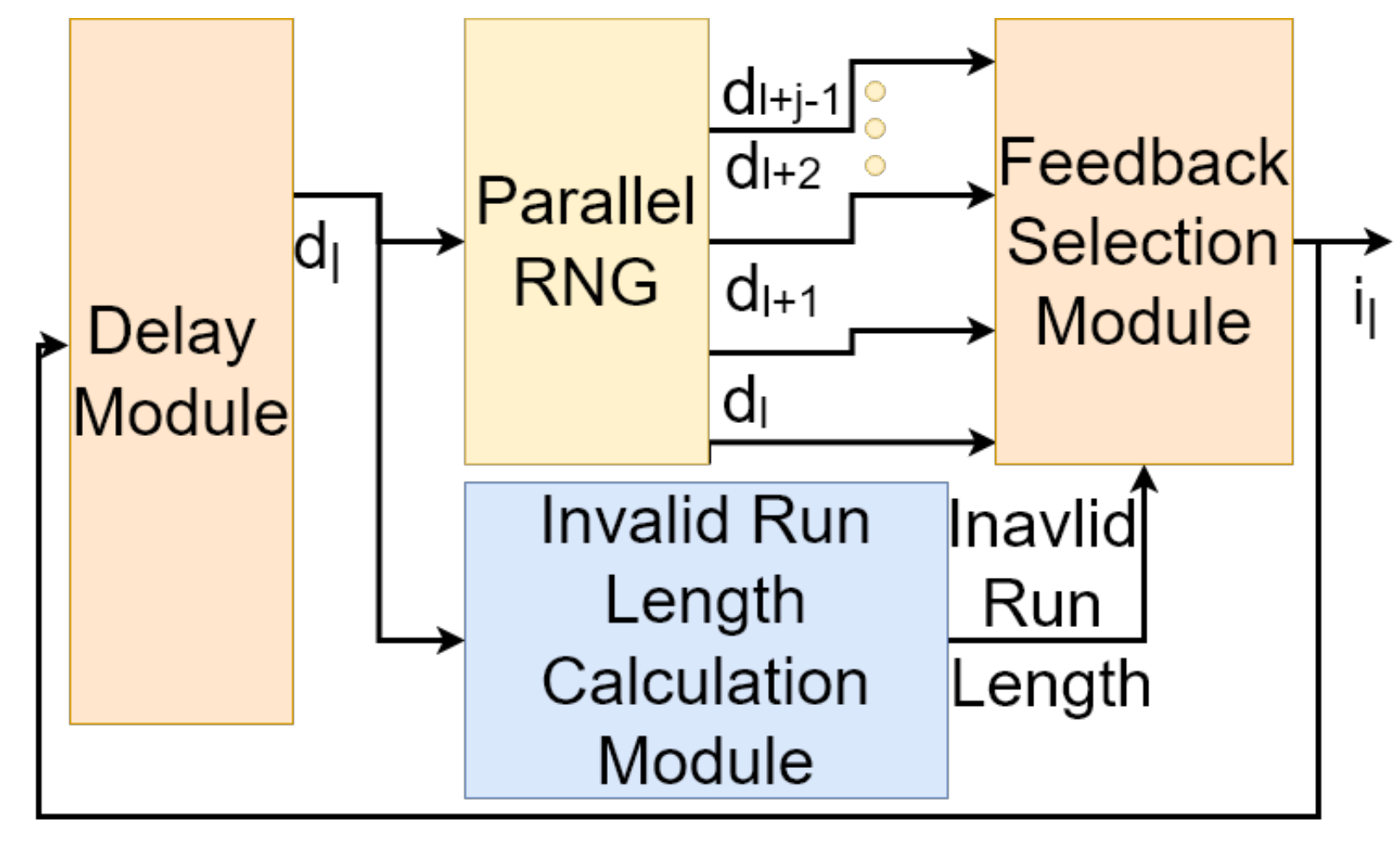
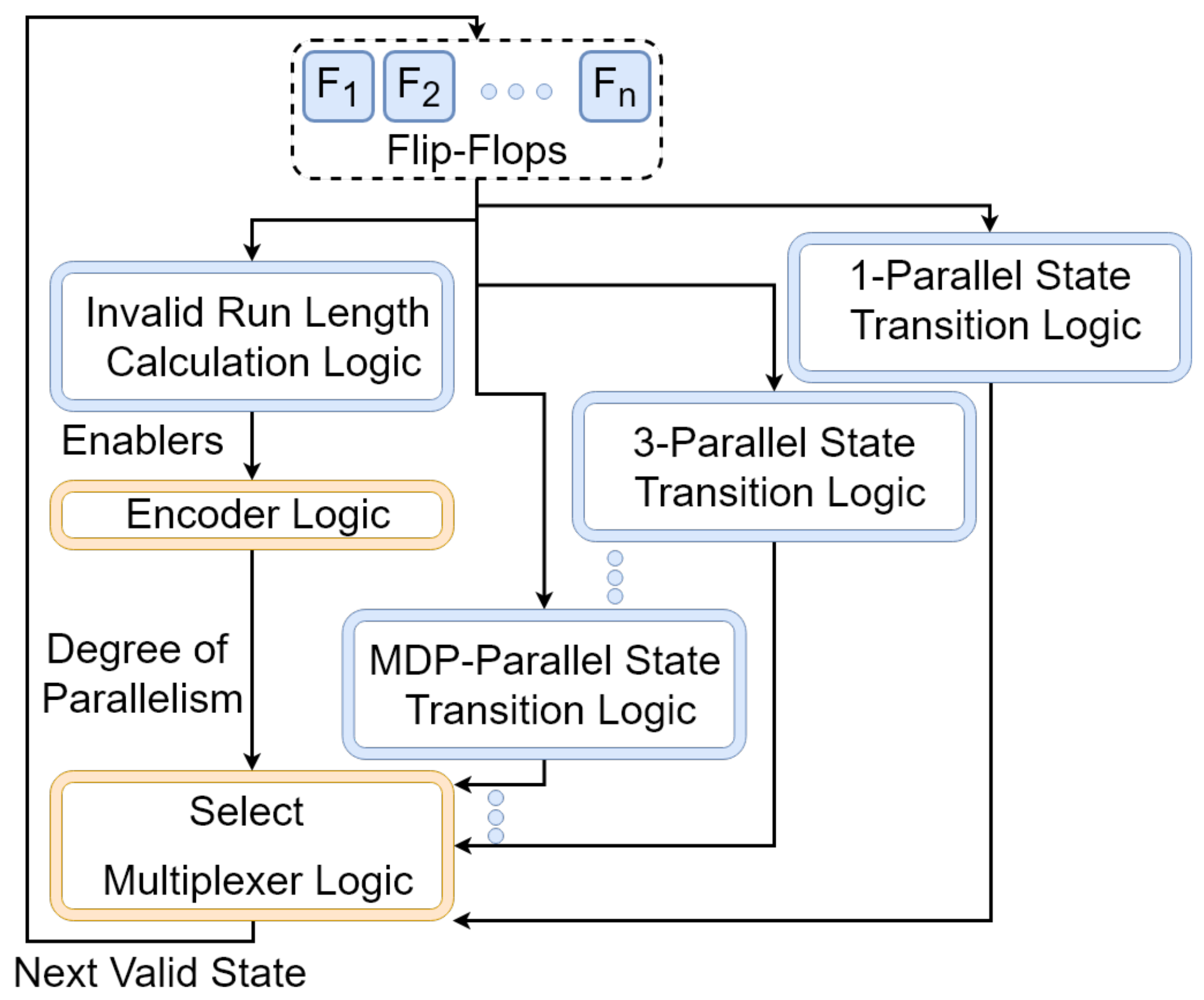
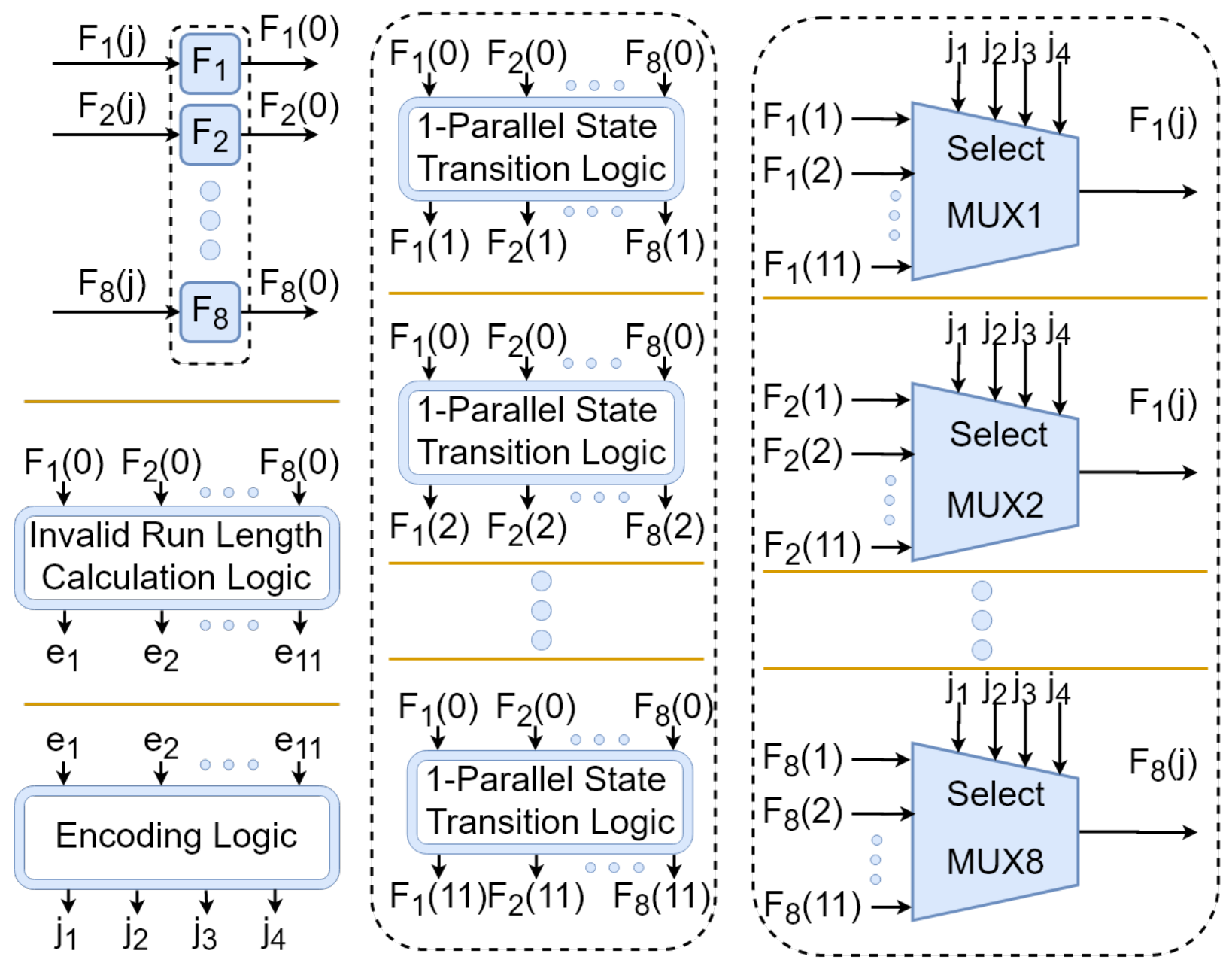
5. Designing the -Restricted Random Number Generator
6. Case Study: Random Latin Squares of Order 4
6.1. Encoding Latin Squares
6.2. S-Restricted RNG for
7. Conclusions and Further Works
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| LFSR | Linear Feedback Shift Register |
| Completely Automated Public | CAPTCHA generation |
| Turing test to tell Computers and Humans Apart | |
| RNG | Random Number Generator |
| VLSI | Very Large Scale Integration |
| CNF | Conjunctive Normal Form |
| DNF | Disjunctive Normal Form |
| ILCL | Invalid Run Length Calculation Logic |
| MDP | Maximum Degree of Parallelism |
| MIRL | Maximum Invalid Run Length |
| NFSR | Nonlinear Feedback Shift Register |
Appendix A. Codes Assigned to Latin Squares of Order 4
| 1: , 2: |
| 3: , 4: |
| 5: , 6: |
| 7: , 8: |
| 9: , 10: |
| 11: , 12: |
| 13: , 14: |
| 15: , 16: |
| 17: , 18: |
| 19: , 20: |
| 21: , 22: |
| 23: , 24: |
| 25: , 26: |
| 27: , 28: |
| 29: , 30: |
| 31: , 32: |
| 33: , 34: |
| 35: , 36: |
| 37: , 38: |
| 39: , 40: |
| 41: , 42: |
| 43: , 44: |
| 45: , 46: |
| 47: , 48: |
| 49: , 50: |
| 51: , 52: |
| 53: , 54: |
| 55: , 56: |
| 57: , 58: |
| 59: , 60: |
| 61: , 62: |
| 63: , 64: |
| 65: , 66: |
| 67: , 68: |
| 69: , 70: |
| 71: , 72: |
| 73: , 74: |
| 75: , 76: |
| 77: , 78: |
| 79: , 80: |
| 81: , 82: |
| 83: , 84: |
| 85: , 86: |
| 87: , 88: |
| 89: , 90: |
| 91: , 92: |
| 93: , 94: |
| 95: , 96: |
| 97: , 98: |
| 99: , 100: |
| 101: , 102: |
| 103: , 104: |
| 105: , 106: |
| 107: , 108: |
| 109: , 110: |
| 111: , 112: |
| 113: , 114: |
| 115: , 116: |
| 117: , 118: |
| 119: , 120: |
| 121: , 122: |
| 123: , 124: |
| 125: , 126: |
| 127: , 128: |
| 129: , 130: |
| 131: , 132: |
| 133: , 134: |
| 135: , 136: |
| 137: , 138: |
| 139: , 140: |
| 141: , 142: |
| 143: , 144: |
| 145: , 146: |
| 147: , 148: |
| 149: , 150: |
| 151: , 152: |
| 153: , 154: |
| 155: , 156: |
| 157: , 158: |
| 159: , 160: |
| 161: , 162: |
| 163: , 164: |
| 165: , 166: |
| 167: , 168: |
| 169: , 170: |
| 171: , 172: |
| 173: , 174: |
| 175: , 176: |
| 177: , 178: |
| 179: , 180: |
| 181: , 182: |
| 183: , 184: |
| 185: , 186: |
| 187: , 188: |
| 189: , 190: |
| 191: , 192: |
| 193: , 194: |
| 195: , 196: |
| 197: , 198: |
| 199: , 200: |
| 201: , 202: |
| 203: , 204: |
| 205: , 206: |
| 207: , 208: |
| 209: , 210: |
| 211: , 212: |
| 213: , 214: |
| 215: , 216: |
| 217: , 218: |
| 219: , 220: |
| 221: , 222: |
| 223: , 224: |
| 225: , 226: |
| 227: , 228: |
| 229: , 230: |
| 231: , 232: |
| 233: , 234: |
| 235: , 236: |
| 237: , 238: |
| 239: , 240: |
| 241: , 242: |
| 243: , 244: |
| 245: , 246: |
| 247: , 248: |
| 249: , 250: |
| 251: , 252: |
| 253: , 254: |
| 255: , 256: |
| 257: , 258: |
| 259: , 260: |
| 261: , 262: |
| 263: , 264: |
| 265: , 266: |
| 267: , 268: |
| 269: , 270: |
| 271: , 272: |
| 273: , 274: |
| 275: , 276: |
| 277: , 278: |
| 279: , 280: |
| 281: , 282: |
| 283: , 284: |
| 285: , 286: |
| 287: , 288: |
| 289: , 290: |
| 291: , 292: |
| 293: , 294: |
| 295: , 296: |
| 297: , 298: |
| 299: , 300: |
| 301: , 302: |
| 303: , 304: |
| 305: , 306: |
| 307: , 308: |
| 309: , 310: |
| 311: , 312: |
| 313: , 314: |
| 315: , 316: |
| 317: , 318: |
| 319: , 320: |
| 321: , 322: |
| 323: , 324: |
| 325: , 326: |
| 327: , 328: |
| 329: , 330: |
| 331: , 332: |
| 333: , 334: |
| 335: , 336: |
| 337: , 338: |
| 339: , 340: |
| 341: , 342: |
| 343: , 344: |
| 345: , 346: |
| 347: , 348: |
| 349: , 350: |
| 351: , 352: |
| 353: , 354: |
| 355: , 356: |
| 357: , 358: |
| 359: , 360: |
| 361: , 362: |
| 363: , 364: |
| 365: , 366: |
| 367: , 368: |
| 369: , 370: |
| 371: , 372: |
| 373: , 374: |
| 375: , 376: |
| 377: , 378: |
| 379: , 380: |
| 381: , 382: |
| 383: , 384: |
| 385: , 386: |
| 387: , 388: |
| 389: , 390: |
| 391: , 392: |
| 393: , 394: |
| 395: , 396: |
| 397: , 398: |
| 399: , 400: |
| 401: , 402: |
| 403: , 404: |
| 405: , 406: |
| 407: , 408: |
| 409: , 410: |
| 411: , 412: |
| 413: , 414: |
| 415: , 416: |
| 417: , 418: |
| 419: , 420: |
| 421: , 422: |
| 423: , 424: |
| 425: , 426: |
| 427: , 428: |
| 429: , 430: |
| 431: , 432: |
| 433: , 434: |
| 435: , 436: |
| 437: , 438: |
| 439: , 440: |
| 441: , 442: |
| 443: , 444: |
| 445: , 446: |
| 447: , 448: |
| 449: , 450: |
| 451: , 452: |
| 453: , 454: |
| 455: , 456: |
| 457: , 458: |
| 459: , 460: |
| 461: , 462: |
| 463: , 464: |
| 465: , 466: |
| 467: , 468: |
| 469: , 470: |
| 471: , 472: |
| 473: , 474: |
| 475: , 476: |
| 477: , 478: |
| 479: , 480: |
| 481: , 482: |
| 483: , 484: |
| 485: , 486: |
| 487: , 488: |
| 489: , 490: |
| 491: , 492: |
| 493: , 494: |
| 495: , 496: |
| 497: , 498: |
| 499: , 500: |
| 501: , 502: |
| 503: , 504: |
| 505: , 506: |
| 507: , 508: |
| 509: , 510: |
| 511: , 512: |
| 513: , 514: |
| 515: , 516: |
| 517: , 518: |
| 519: , 520: |
| 521: , 522: |
| 523: , 524: |
| 525: , 526: |
| 527: , 528: |
| 529: , 530: |
| 531: , 532: |
| 533: , 534: |
| 535: , 536: |
| 537: , 538: |
| 539: , 540: |
| 541: , 542: |
| 543: , 544: |
| 545: , 546: |
| 547: , 548: |
| 549: , 550: |
| 551: , 552: |
| 553: , 554: |
| 555: , 556: |
| 557: , 558: |
| 559: , 560: |
| 561: , 562: |
| 563: , 564: |
| 565: , 566: |
| 567: , 568: |
| 569: , 570: |
| 571: , 572: |
| 573: , 574: |
| 575: , 576: |
Appendix B. Invalid Runs (In Decimal and Binary Forms)
Appendix C. Enablers
References
- Cheng, Y.; Xu, C.; Hai, Z.; Li, Y. Deepmnemonic: Password mnemonic generation via deep attentive encoder-decoder model. IEEE Trans. Dependable Secur. Comput. 2022, 19, 77–90. [Google Scholar] [CrossRef]
- Zi, Y.; Gao, H.; Cheng, Z.; Liu, Y. An end-to-end attack on text captchas. IEEE Trans. Inf. Forensics Secur. 2020, 15, 753–766. [Google Scholar] [CrossRef]
- Gao, S.; Mohamed, M.; Saxena, N.; Zhang, C. Emerging-image motion captchas: Vulnerabilities of existing designs, and countermeasures. IEEE Trans. Dependable Secur. Comput. 2019, 16, 1040–1053. [Google Scholar] [CrossRef]
- Lee, J. Indifferentiability of the sum of random permutations toward optimal security. IEEE Trans. Inf. Theory 2017, 63, 4050–4054. [Google Scholar] [CrossRef]
- Zhou, J.; Liu, X.; Au, O.C.; Tang, Y.Y. Designing an efficient image encryption-then-compression system via prediction error clustering and random permutation. IEEE Trans. Inf. Forensics Secur. 2014, 9, 39–50. [Google Scholar] [CrossRef]
- Selvi, D.; Velammal, T.G.; Arockiadoss, T. Modified method of generating randomized latin squares. IOSR J. Comput. Eng. (IOSR-JCE) 2014, 16, 76–80. [Google Scholar] [CrossRef]
- Kwan, M.; Sudakov, B. Intercalates and discrepancy in random latin squares. arXiv 2017, arXiv:1607.04981. [Google Scholar] [CrossRef]
- Bóna, M.; Knopfmacher, A. On the probability that certain compositions have the same number of parts. Ann. Comb. 2010, 14, 291–306. [Google Scholar] [CrossRef]
- Banderier, C.; Hitczenko, P. Enumeration and asymptotics of restricted compositions having the same number of parts. Discret. Appl. Math. 2012, 160, 2542–2554. [Google Scholar] [CrossRef]
- Sedighi, M.; Fallah, M.S.; Zolfaghari, B. S-restricted compositions revisited. J. Discret. Math. Theor. Comput. Sci. 2017, 19, 1–19. [Google Scholar]
- Goresky, M.; Klapper, A.M. Fibonacci and galois representations of feedback-with-carry shift registers. IEEE Trans. Inf. Theory 2002, 48, 2826–2836. [Google Scholar] [CrossRef]
- Dubrova, E. A transformation from the fibonacci to the galois nlfsrs. IEEE Trans. Inf. Theory 2006, 55, 5263–5271. [Google Scholar] [CrossRef]
- Ayinala, M.; Parhi, K.K. High-speed parallel architectures for linear feedback shift registers. IEEE Trans. Signal Process. 2012, 59, 4459–4469. [Google Scholar] [CrossRef]
- Zolfaghari, B.; Sedighi, M.; Fallah, M.S. Designing programmable parallel lfsr using parallel prefix trees. J. Eng. Res. 2019, 7, 105–122. [Google Scholar]
- Kumar, S.N.; Kumar, H.S.; Panduranga, H.T. Hardware software co-simulation of dual image encryption using latin square image. In Proceedings of the Fourth International Conference on Computing, Communications and Networking Technologies (ICCCNT), Tiruchengode, India, 4–6 July 2013. [Google Scholar]
- Mou, H.; Li, X.; Li, G.; Lu, D.; Zhang, R. A self-adaptive and dynamic image encryption based on latin square and high-dimensional chaotic system. In Proceedings of the IEEE 3rd International Conference on Image, Vision and Computing (ICIVC), Chongqing, China, 27–29 June 2018. [Google Scholar]
- Pal, S.K.; Bhardwaj, D.; Kumar, R.; Bhatia, V. A new cryptographic hash function based on latin squares and non-linear transformations. In Proceedings of the IEEE International Advance Computing Conference, Patiala, India, 6–7 March 2009. [Google Scholar]
- Shen, J.; Zhou, T.; Liu, X.; Chang, Y.C. A novel latin-square-based secret sharing for m2m communications. IEEE Trans. Ind. Inform. 2018, 14, 3659–3668. [Google Scholar] [CrossRef]
- Lehmer, D.H. Teaching combinatorial tricks to a computer. In Proceedings of Symposium on Applied Mathematics; American Mathematical Society: New York City, NY, USA, 1960. [Google Scholar]
- Dubrova, E.; Mansouri, S.S. A bdd-based approach to constructing lfsrs for parallel crc encoding. In Proceedings of the International Symposium on Multiple-Valued Logic, Victoria, BC, Canada, 14–16 May 2012. [Google Scholar]
- Cheng, C.; Parhi, K.K. High-speed parallel crc implementation based on unfolding, pipelining, and retiming. IEEE Trans. Circuits Syst. II Express Briefs 2006, 53, 1017–1021. [Google Scholar] [CrossRef]
- Nandi, S.; Krishnaswamy, S.; Zolfaghari, B.; Mitra, P. Key-dependant feedback configuration matrix of σ-lfsr and resistance to some known plaintext attacks. IEEE Access 2022, 10, 44840–44854. [Google Scholar] [CrossRef]
- Kuehnel, R.; Theiler, J.; Wang, Y. Parallel random number generators for sequences uniformly distributed over any range of integers. IEEE Trans. Circuits Syst. I Regul. Pap. 2006, 53, 1496–1505. [Google Scholar] [CrossRef]
- Pae, S.I. A generalization of peres’s algorithm for generating random bits from loaded dice. IEEE Trans. Inf. Theory 2015, 61, 751–757. [Google Scholar]
- Zhang, G.H.; Poon, C.C.; Zhang, Y.T. Analysis of using interpulse intervals to generate 128-bit biometric random binary sequences for securing wireless body sensor networks. IEEE Trans. Inf. Technol. Biomed. 2012, 16, 176–182. [Google Scholar] [CrossRef]
- Cauwenberghs, G. Delta-sigma cellular automata for analog vlsi random vector generation. IEEE Trans. Circuits Syst. II Analog Digit. Signal Process. 1999, 46, 240–250. [Google Scholar] [CrossRef]
- Morgan, D. Analysis of digital random numbers generated from serial samples of correlated gaussian noise (corresp.). IEEE Trans. Inf. Theory 1981, 27, 235–239. [Google Scholar] [CrossRef]
- Chen, X.; Wang, L.; Li, B.; Wang, Y.; Li, X.; Liu, Y.; Yang, H. Modeling random telegraph noise as a randomness source and its application in true random number generation. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2016, 35, 1435–1448. [Google Scholar] [CrossRef]
- Gao, S.; Zhang, L.; Xu, Y.; Chen, L.; Bao, X. High-speed random bit generation via brillouin random fiber laser with non-uniform fibers. IEEE Photonics Technol. Lett. 2017, 29, 1352–1355. [Google Scholar] [CrossRef]
- Lv, Y.; Zink, B.R.; Wang, J.P. Bipolar random spike and bipolar random number generation by two magnetic tunnel junctions. IEEE Trans. Electron Devices 2022, 69, 1582–1587. [Google Scholar] [CrossRef]
- Ge, Z.; Xiao, Y.; Hao, T.; Li, W.; Li, M. Tb/s fast random bit generation based on a broadband random optoelectronic oscillator. IEEE Photonics Technol. Lett. 2021, 33, 1223–1226. [Google Scholar] [CrossRef]
- Seetharam, D.; Rhee, S. An efficient pseudo random number generator for low-power sensor networks [wireless networks]. In Proceedings of the Annual IEEE International Conference on Local Computer Networks, Tampa, FL, USA, 16–18 November 2004. [Google Scholar]
- Ramesh, A.; Jain, A. Hybrid image encryption using pseudo random number generators, and transposition and substitution techniques. In Proceedings of the International Conference on Trends in Automation, Communications and Computing Technology (I-TACT-15), Bangalore, India, 21–22 December 2015. [Google Scholar]
- Anghelescu, P.; Sofron, E.; Ionita, S.; Ionescu, L. Fpga implementations of cellular automata for pseudo-random number generation. In Proceedings of the International Semiconductor Conference, Sinaia, Romania, 27–29 September 2006. [Google Scholar]
- Tutueva, A.V.; Butusov, D.N.; Pesterev, D.O.; Belkin, D.A.; Ryzhov, N.G. Novel normalization technique for chaotic pseudo-random number generators based on semi-implicit ode solvers. In Proceedings of the International Conference “Quality Management, Transport and Information Security, Information Technologies” (IT&QM&IS), St. Petersburg, Russia, 24–30 September 2017. [Google Scholar]
- Desai, V.V.; Deshmukh, V.B.; Rao, D.H. Pseudo random number generator using elman neural network. In Proceedings of the IEEE Recent Advances in Intelligent Computational Systems, Trivandrum, India, 22–24 September 2011. [Google Scholar]
- Jeong, Y.S.; Oh, K.; Cho, C.K.; Choi, H.J. Pseudo random number generation using lstms and irrational numbers. In Proceedings of the IEEE International Conference on Big Data and Smart Computing (BigComp), Shanghai, China, 15–17 January 2018. [Google Scholar]
- Anikin, I.V.; Alnajjar, K. Pseudo-random number generator based on fuzzy logic. In Proceedings of the International Siberian Conference on Control and Communications (SIBCON), Moscow, Russia, 12–14 May 2016. [Google Scholar]
- Yang, H.T.; Huang, J.R.; Chang, T.Y. A chaos-based fully digital 120 mhz pseudo random number generator. In Proceedings of the 2004 IEEE Asia-Pacific Conference on Circuits and Systems, Tainan, Taiwan, 6–9 December 2004. [Google Scholar]
- Unde, A.S.; Deepthi, P.P. Design and analysis of compressive sensing-based lightweight encryption scheme for multimedia iot. IEEE Trans. Circuits Syst. II Express Briefs 2019, 67, 167–171. [Google Scholar] [CrossRef]
- Wheeldon, A.; Shafik, R.; Rahman, T.; Lei, J.; Yakovlev, A.; Granmo, O.C. Learning automata based energy-efficient ai hardware design for iot applications. Philos. Trans. R. Soc. A 2020, 378, 20190593. [Google Scholar] [CrossRef]
- Hussain, S.; Chaudhary, A.K.; Verma, S. Enhancing security in iot devices by using pseudo random number generator based on two different lfsr and a comparator. In Proceedings of the IEEE Delhi Section Conference (DELCON), New Delhi, India, 11–13 February 2022. [Google Scholar]
- Han, M.; Kim, Y. Unpredictable 16 bits lfsr-based true random number generator. In Proceedings of the International SoC Design Conference (ISOCC), Seoul, Korea, 5–8 November 2017. [Google Scholar]
- Zode, P.; Zode, P.; Deshmukh, R. Fpga based novel true random number generator using lfsr with dynamic seed. In Proceedings of the IEEE 16th India Council International Conference (INDICON), Rajkot, India, 13–15 December 2019. [Google Scholar]
- Gu, X.; Zhang, M. Uniform random number generator using leap ahead lfsr architecture. In Proceedings of the International Conference on Computer and Communications Security, Hong Kong, China, 5–6 December 2009. [Google Scholar]
- Tan, Z.; Guo, W.; Gong, G.; Lu, H. A new pseudo-random number generator based on the leap-ahead lfsr architecture. In Proceedings of the IEEE International Conference on Integrated Circuits, Technologies and Applications (ICTA), Beijing, China, 21–23 November 2018. [Google Scholar]
- Tuncer, T.; Avaroğlu, E. Random number generation with lfsr based stream cipher algorithms. In Proceedings of the 40th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 22–26 May 2017. [Google Scholar]
- Hu, G.; Sha, J.; Wang, Z. High-speed parallel lfsr architectures based on improved state-space transformations. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2017, 25, 1159–1163. [Google Scholar] [CrossRef]
- Moghadam, I.Z.; Rostami, A.S.; Tanhatalab, M.R. Designing a random number generator with novel parallel lfsr substructure for key stream ciphers. In Proceedings of the International Conference On Computer Design and Applications, Qinhuangdao, China, 25–27 June 2010. [Google Scholar]
- Hlawiczka, A. Compression of three-state data serial streams by means of a parallel lfsr signature analyzer. IEEE Trans. Comput. 1986, C-35, 732–741. [Google Scholar] [CrossRef]
- Kongtim, P.; Reungpeerakul, T. Parallel lfsr reseeding with selection register for mixed-mode bist. In Proceedings of the 19th IEEE Asian Test Symposium, Shanghai, China, 1–4 December 2010. [Google Scholar]
- Sokal, N.O. Optimum choice of noise frequency band and sampling rate for generating random binary digits from clipped white noise. IEEE Trans. Comput. 1971, C-21, 614–615. [Google Scholar] [CrossRef]
- Alves, J.C.; Martins, A.C. A strategy to generate random binary errors in a data stream. IEEE Trans. Instrum. Meas. 1986, IM-35, 42–45. [Google Scholar] [CrossRef]
- Waicukauski, J.A.; Lindbloom, E.; Eichelberger, E.B.; Forlenza, O.P. A method for generating weighted random test patterns. IBM J. Res. Dev. 1989, 33, 149–161. [Google Scholar] [CrossRef]
- Xu, M.; Liu, J. Double-layered random coding for secret key generation in gaussian wiretap channels. IEEE Commun. Lett. 2020, 24, 264–267. [Google Scholar] [CrossRef]
- Vaidya, J.; Shafiq, B.; Fan, W.; Mehmood, D.; Lorenzi, D. A random decision tree framework for privacy-preserving data mining. IEEE Trans. Dependable Secur. Comput. 2014, 11, 399–411. [Google Scholar] [CrossRef]
- Tang, F.; Chen, D.G.; Wang, B.; Bermak, A.; Amira, A.; Mohamad, S. Cmos on-chip stable true-random id generation using antenna effect. IEEE Electron Device Lett. 2014, 35, 54–56. [Google Scholar] [CrossRef]
- Li, J.; Zhou, Y.; Chen, H. Age of information for multicast transmission with fixed and random deadlines in iot systems. IEEE Internet Things J. 2020, 7, 8178–8191. [Google Scholar] [CrossRef]
- Chung, S.C.; Yu, C.Y.; Lee, S.S.; Chang, H.C.; Lee, C.Y. An improved dpa countermeasure based on uniform distribution random power generator for iot applications. IEEE Trans. Circuits Syst. I Regul. Pap. 2017, 64, 2522–2531. [Google Scholar] [CrossRef]
- Angelopoulos, G.; Paidimarri, A.; Médard, M.; Chandrakasan, A.P. A random linear network coding accelerator in a 2.4ghz transmitter for iot applications. IEEE Trans. Circuits Syst. I Regul. Pap. 2017, 64, 2582–2590. [Google Scholar] [CrossRef]
- Silverman, J.; Vickers, V.; Sampson, J. Statistical estimates of then-bit gray codes by restricted random generation of permutations of 1 to 2n. IEEE Trans. Inf. Theory 1983, 29, 894–901. [Google Scholar] [CrossRef]
- Gujar, U.; Kavanagh, R. Generation of random signals with specified probability density functions and power density spectra. IEEE Trans. Autom. Control 1968, 13, 716–719. [Google Scholar] [CrossRef]
- Mitchell, R.L.; Stone, C.R. Table-lookup methods for generating arbitrary random numbers. IEEE Trans. Comput. 1977, C-26, 1006–1008. [Google Scholar] [CrossRef]
- Wang, Y.; Li, P.; Zhang, J. Fast random bit generation in optical domain with ultrawide bandwidth chaotic laser. IEEE Photonics Technol. Lett. 2010, 22, 1680–1682. [Google Scholar] [CrossRef]
- Fang, X.; Wetzel, B.; Merolla, J.M.; Dudley, J.M.; Larger, L.; Guyeux, C.; Bahi, J.M. Noise and chaos contributions in fast random bit sequence generated from broadband optoelectronic entropy sources. IEEE Trans. Circuits Syst. I Regul. Pap. 2014, 61, 888–901. [Google Scholar] [CrossRef]
- Almardeny, Y.; Benavoli, A.; Boujnah, N.; Naredo, E. A reinforcement learning system for generating instantaneous quality random sequences. IEEE Trans. Artif. Intell. 2022. [Google Scholar] [CrossRef]
- Boucetta, C.; Nour, B.; Moungla, H.; Lahlou, L. An iot scheduling and interference mitigation scheme in tsch using latin rectangles. In Proceedings of the IEEE Global Communications Conference, Waikoloa, HI, USA, 9–13 December 2019. [Google Scholar]
- Fontana, R. Random latin squares and sudoku designs generation. Electron. J. Stat. 2014, 8, 883–893. [Google Scholar] [CrossRef]
- DeSalvo, S. Random sampling of latin squares via binary contingency tablesand probabilistic divide-and-conquer. arXiv 2017, arXiv:1703.08627. [Google Scholar]
- Muramatsu, J.; Miyake, S. Channel code using constrained-random-number generator revisited. IEEE Trans. Inf. Theory 2019, 65, 500–510. [Google Scholar] [CrossRef]
- Muramatsu, J. Channel coding and lossy source coding using a generator of constrained random numbers. IEEE Trans. Inf. Theory 2014, 60, 2667–2686. [Google Scholar] [CrossRef][Green Version]
- Muramatsu, J. Variable-length lossy source code using a constrained-random-number generator. IEEE Trans. Inf. Theory 2015, 61, 3574–3592. [Google Scholar] [CrossRef]
- Moon, S.; Lee, H.S.; Lee, J.W. Sara: Sparse code multiple access-applied random access for iot devices. IEEE Internet Things J. 2018, 5, 3160–3174. [Google Scholar] [CrossRef]
- Khan, M.H.A. Design of reversible synchronous sequential circuits using pseudo reed-muller expressions. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2014, 22, 2278–2286. [Google Scholar] [CrossRef]
- Zenner, E. On Cryptographic Properties of LFSR-Based Pseudorandom Generators. Ph.D. Thesis, Universitat Mannheim, Mannheim, Germany, 2004. [Google Scholar]

| 1 | 8 | 9 | 10 | 2 | 4 | 6 | 3 | 5 | 7 |
| 7 | 2 | 8 | 9 | 10 | 3 | 5 | 4 | 6 | 1 |
| 6 | 1 | 3 | 8 | 9 | 10 | 4 | 5 | 7 | 2 |
| 5 | 7 | 2 | 4 | 8 | 9 | 10 | 6 | 1 | 3 |
| 10 | 6 | 1 | 3 | 5 | 8 | 9 | 7 | 2 | 4 |
| 9 | 10 | 7 | 2 | 4 | 6 | 8 | 1 | 3 | 5 |
| 8 | 9 | 10 | 1 | 3 | 5 | 7 | 2 | 4 | 6 |
| 2 | 3 | 4 | 5 | 6 | 7 | 1 | 8 | 9 | 10 |
| 3 | 4 | 5 | 6 | 7 | 1 | 2 | 10 | 8 | 9 |
| 4 | 5 | 6 | 7 | 1 | 2 | 3 | 9 | 10 | 8 |
| L | Begin | ||||||||||
| 1 | 580 608 834 656 596 706 752 686 694 848 602 726 654 632 640 578 720 598 650 738 760 588 836 610 728 630 688 666 742 584 612 832 582 626 732 638 674 744 622 646 854 642 736 700 684 842 658 740 862 680 618 730 758 604 696 702 644 592 594 724 710 600 668 676 704 664 692 648 616 614 850 660 708 590 718 860 698 750 712 620 838 624 716 844 852 714 754 764 856 670 858 662 652 840 628 606 682 746 762 766 672 586 722 756 634 734 690 748 846 636 678 | ||||||||||
| 2 | 585 749 653 641 577 589 665 757 637 685 645 725 705 621 669 593 733 597 761 717 649 721 845 697 849 693 737 601 661 833 857 765 837 677 753 673 613 841 605 689 625 581 617 709 729 609 701 861 853 681 657 629 741 633 745 713 | ||||||||||
| 3 | 747 739 859 643 635 651 851 731 587 843 619 627 835 667 715 603 723 755 699 691 763 595 707 683 659 611 579 675 | ||||||||||
| 4 | 599 615 679 583 663 631 647 695 743 727 711 759 839 855 | ||||||||||
| L | Begin | L | Begin | L | Begin | L | Begin | L | Begin | L | Begin |
| 5 | 623 591 655 751 687 719 847 | 6 | 671 735 863 607 | 7 | 703 | 8 | 767 | 9 | - | 10 | 639 |
| j | Equation |
|---|---|
| 2 | |
| 3 | |
| 4 | |
| 5 | |
| 6 | |
| 7 |
| j | Equation |
|---|---|
| 8 | |
| 9 | |
| 10 | |
| 11 |
| j | Simplified Logic Expression |
|---|---|
| 2 | |
| 3 | |
| 4 | |
| 5 | |
| 6 | |
| 7 | |
| 8 | |
| 9 | |
| 11 | |
| 1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zolfaghari, B.; Bibak, K.; Koshiba, T. From Random Numbers to Random Objects. Entropy 2022, 24, 928. https://doi.org/10.3390/e24070928
Zolfaghari B, Bibak K, Koshiba T. From Random Numbers to Random Objects. Entropy. 2022; 24(7):928. https://doi.org/10.3390/e24070928
Chicago/Turabian StyleZolfaghari, Behrouz, Khodakhast Bibak, and Takeshi Koshiba. 2022. "From Random Numbers to Random Objects" Entropy 24, no. 7: 928. https://doi.org/10.3390/e24070928
APA StyleZolfaghari, B., Bibak, K., & Koshiba, T. (2022). From Random Numbers to Random Objects. Entropy, 24(7), 928. https://doi.org/10.3390/e24070928








