Cuproof: Range Proof with Constant Size
Abstract
:1. Introduction
1.1. Related Work
1.2. Contributions
1.3. Structure of the Paper
2. Preliminaries
2.1. Notation
2.2. Assumptions
2.3. Commitments
2.4. Zero-Knowledge Arguments of Knowledge
3. Efficient Range Proof Protocol
3.1. Four Integer Zero-Knowledge Proof
3.2. Aggregating Logarithmic Proofs
3.3. Our Protocol: Cuproof
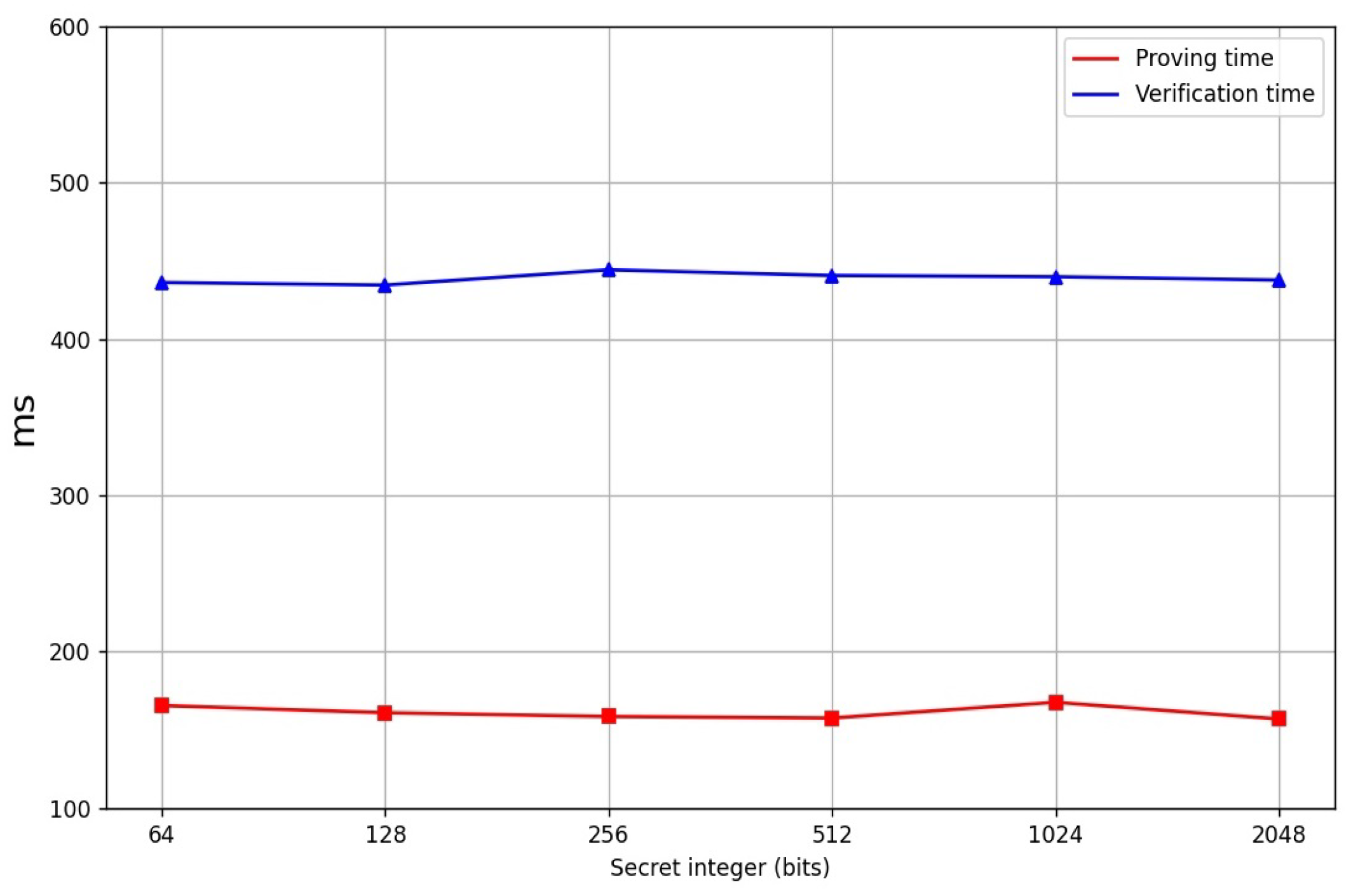
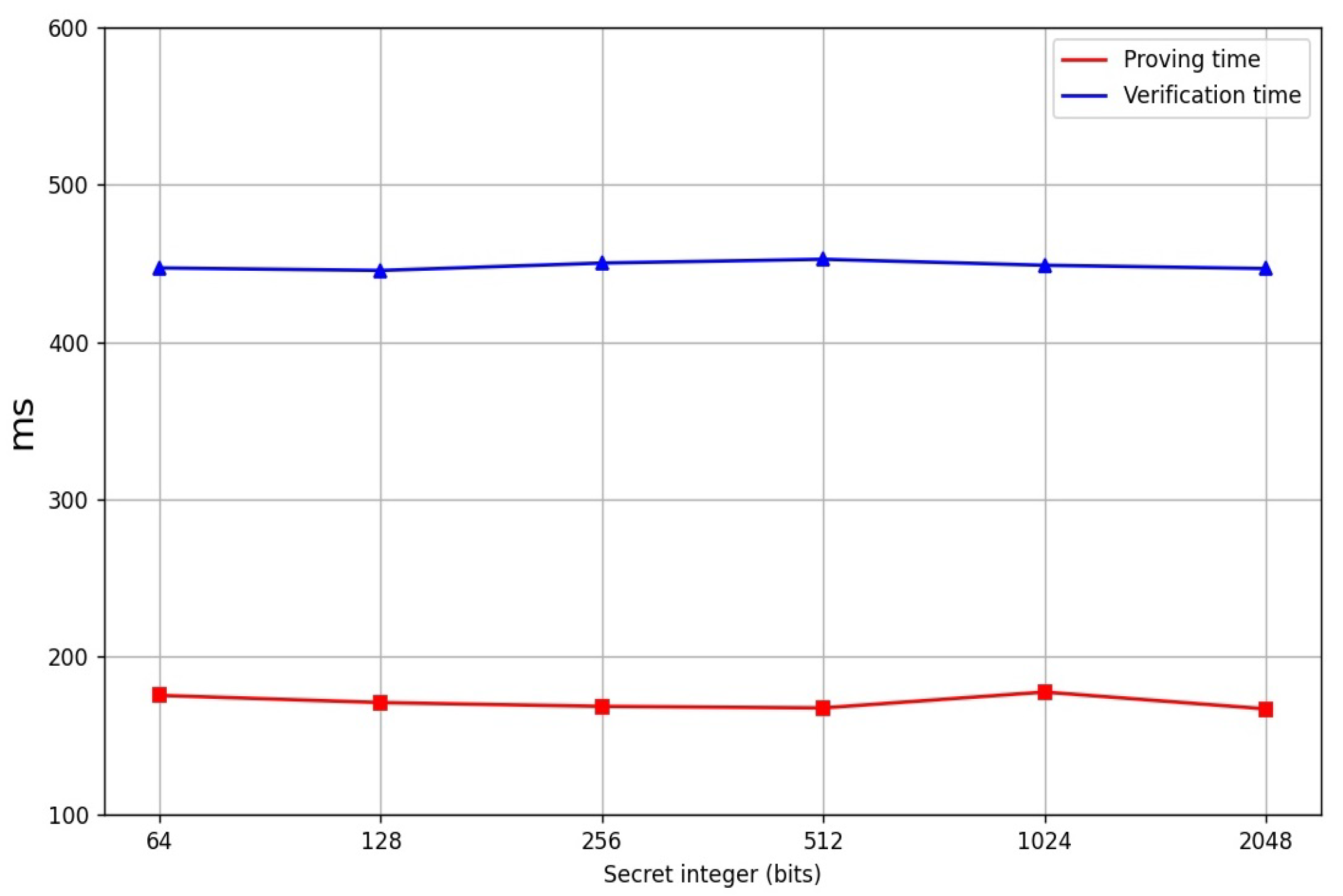
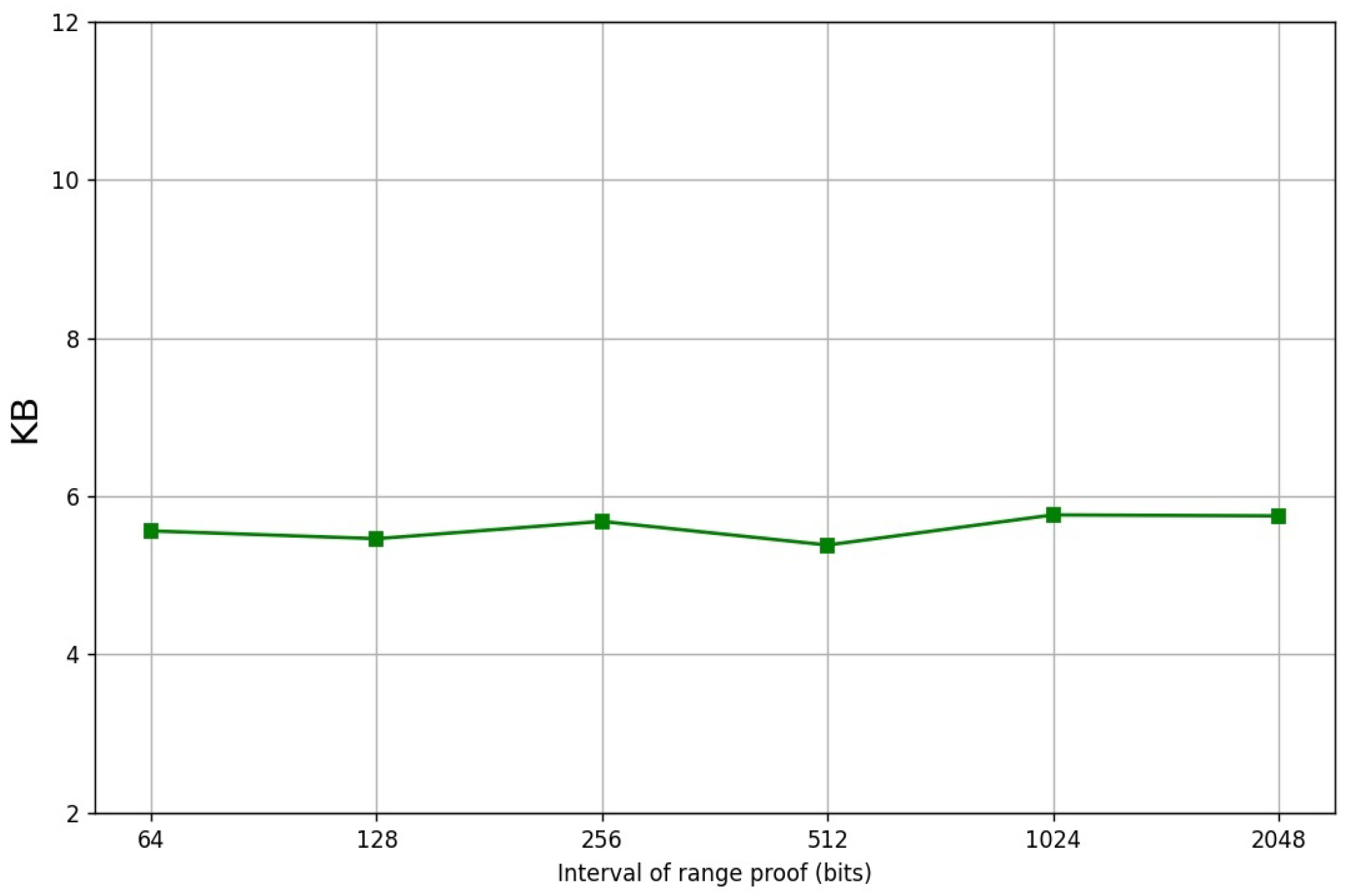
4. Performance
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A. Proof of Theorem 3
References
- Tsang, Y.; Wu, C.; Ip, W.; Shiau, W.L. Exploring the intellectual cores of the blockchain–Internet of Things (BIoT). J. Enterp. Inf. Manag. 2021, 34, 1287–1317. [Google Scholar] [CrossRef]
- Fedorov, I.R.; Pimenov, A.V.; Panin, G.A.; Bezzateev, S.V. Blockchain in 5G Networks: Perfomance Evaluation of Private Blockchain. In Proceedings of the 2021 Wave Electronics and its Application in Information and Telecommunication Systems (WECONF), St. Petersburg, Russia, 31 May–4 June 2021; pp. 1–4. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: http://www.bitcoin.org/bitcoin.pdf (accessed on 21 February 2022).
- Sun, X.; Yu, F.R.; Zhang, P.; Sun, Z.; Xie, W.; Peng, X. A survey on zero-knowledge proof in blockchain. IEEE Netw. 2021, 35, 198–205. [Google Scholar] [CrossRef]
- Bünz, B.; Bootle, J.; Boneh, D.; Poelstra, A.; Wuille, P.; Maxwell, G. Bulletproofs: Short Proofs for Confidential Transactions and More. In Proceedings of the 2018 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 20–24 May 2018; pp. 315–334. [Google Scholar] [CrossRef]
- Brickell, E.F.; Chaum, D.; Damgård, I.B.; van de Graaf, J. Gradual and Verifiable Release of a Secret (Extended Abstract). In Advances in Cryptology—CRYPTO ’87; Pomerance, C., Ed.; Springer: Santa Barbara, CA, USA, 1987; pp. 156–166. [Google Scholar]
- Gabizon, A.; Williamson, Z.J.; Ciobotaru, O. PLONK: Permutations over Lagrange-Bases for Oecumenical Noninteractive Arguments of Knowledge. Cryptology ePrint Archive, Report 2019/953. 2019. Available online: https://eprint.iacr.org/2019/953 (accessed on 8 December 2021).
- Maller, M.; Bowe, S.; Kohlweiss, M.; Meiklejohn, S. Sonic: Zero-Knowledge SNARKs from Linear-Size Universal and Updateable Structured Reference Strings. Cryptology ePrint Archive, Report 2019/099. 2019. Available online: https://eprint.iacr.org/2019/099 (accessed on 8 December 2021).
- Setty, S.; Angel, S.; Lee, J. Verifiable state machines: Proofs that untrusted services operate correctly. ACM SIGOPS Oper. Syst. Rev. 2020, 54, 40–46. [Google Scholar] [CrossRef]
- Ben-Sasson, E.; Bentov, I.; Horesh, Y.; Riabzev, M. Scalable, Transparent, and Post-Quantum Secure Computational Integrity. 2018. Available online: https://eprint.iacr.org/2018/046 (accessed on 15 August 2021).
- Ben Sasson, E.; Chiesa, A.; Garman, C.; Green, M.; Miers, I.; Tromer, E.; Virza, M. Zerocash: Decentralized Anonymous Payments from Bitcoin. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 18–21 May 2014; pp. 459–474. [Google Scholar] [CrossRef] [Green Version]
- Dong, K.; Lin, R.; Yin, X.; Xie, Z. How does overconfidence affect information security investment and information security performance? J. Enterp. Inf. Syst. 2021, 15, 474–491. [Google Scholar] [CrossRef]
- Chan, A.; Frankel, Y.; Tsiounis, Y. Easy come—Easy go divisible cash. In Advances in Cryptology—EUROCRYPT’98; Nyberg, K., Ed.; Springer: Berlin/Heidelberg, Germany, 1998; pp. 561–575. [Google Scholar] [CrossRef] [Green Version]
- Boudot, F. Efficient Proofs that a Committed Number Lies in an Interval. In Advances in Cryptology—EUROCRYPT 2000; Preneel, B., Ed.; Springer: Berlin/Heidelberg, Germany, 2000; pp. 431–444. [Google Scholar] [CrossRef] [Green Version]
- Rabin, M.O.; Shallit, J.O. Randomized algorithms in number theory. Commun. Pure Appl. Math. 1986, 39, 239–256. [Google Scholar] [CrossRef]
- Lipmaa, H. On Diophantine Complexity and Statistical Zero-Knowledge Arguments. In Advances in Cryptology—ASIACRYPT 2003; Laih, C.S., Ed.; Springer: Berlin/Heidelberg, Germany, 2003; pp. 398–415. [Google Scholar] [CrossRef] [Green Version]
- Groth, J. Non-interactive Zero-Knowledge Arguments for Voting. In Applied Cryptography and Network Security; Ioannidis, J., Keromytis, A., Yung, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 467–482. [Google Scholar] [CrossRef]
- Boneh, D.; Boyen, X. Short Signatures Without Random Oracles. In Advances in Cryptology—EUROCRYPT 2004; Cachin, C., Camenisch, J.L., Eds.; Springer: Berlin/Heidelberg, Germany, 2004; pp. 56–73. [Google Scholar] [CrossRef] [Green Version]
- Teranishi, I.; Sako, K. k-Times Anonymous Authentication with a Constant Proving Cost. In Public Key Cryptography—PKC 2006; Yung, M., Dodis, Y., Kiayias, A., Malkin, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2006; pp. 525–542. [Google Scholar] [CrossRef] [Green Version]
- Camenisch, J.; Chaabouni, R.; Shelat, A. Efficient Protocols for Set Membership and Range Proofs. In Advances in Cryptology—ASIACRYPT 2008; Pieprzyk, J., Ed.; Springer: Berlin/Heidelberg, Germany, 2008; pp. 234–252. [Google Scholar] [CrossRef] [Green Version]
- Belenkiy, M. U-Prove Range Proof Extension. 2014. Available online: https://www.microsoft.com/en-us/research/publication/u-prove-range-proof-extension/ (accessed on 5 September 2021).
- Paquin, C.; Zaverucha, G. U-Prove Cryptographic Specification V1.1 (Revision 3). 2013. Available online: https://www.microsoft.com/en-us/research/publication/u-prove-cryptographic-specification-v1-1-revision-3/ (accessed on 8 December 2021).
- Bootle, J.; Cerulli, A.; Chaidos, P.; Groth, J.; Petit, C. Efficient Zero-Knowledge Arguments for Arithmetic Circuits in the Discrete Log Setting. In Advances in Cryptology—EUROCRYPT 2016; Fischlin, M., Coron, J.S., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; pp. 327–357. [Google Scholar] [CrossRef]
- Groth, J. On the Size of Pairing-Based Non-interactive Arguments. In Advances in Cryptology—EUROCRYPT 2016; Fischlin, M., Coron, J.S., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; pp. 305–326. [Google Scholar] [CrossRef] [Green Version]
- Li, K.; Yang, R.; Au, M.H.; Xu, Q. Practical range proof for cryptocurrency monero with provable security. In Proceedings of the International Conference on Information and Communications Security, Beijing, China, 6–8 December 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 255–262. [Google Scholar] [CrossRef]
| Scheme | Universal SRS | Circle SRS | Size | Computation | Computation |
|---|---|---|---|---|---|
| Bulletproofs [5] | − | ||||
| Boudot [14] | − | ||||
| Lipmaa [16] | − | ||||
| Groth et al. [24] | − | ||||
| This work | − |
| Scheme | PQ? | Universal | Untrusted Setup | Assumption | Runtime | |
|---|---|---|---|---|---|---|
| Prover | Verifier | |||||
| Bulletproofs [5] | ◊ | ⧫ | ⧫ | |||
| Boudot [14] | ◊ | ⧫ | ◊ | |||
| Lipmaa [16] | ◊ | ⧫ | ◊ | |||
| This work | ◊ | ⧫ | ◊ | |||
| Range Size | Gates | Proof Size | Timing (ms) | |
|---|---|---|---|---|
| (Bytes) | Prove | Verify | ||
| 6 | 5561 | |||
| 6 | 5462 | |||
| 6 | 5681 | |||
| 6 | 5382 | |||
| 6 | 5763 | |||
| 6 | 5751 | |||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Deng, C.; You, L.; Tang, X.; Hu, G.; Gao, S. Cuproof: Range Proof with Constant Size. Entropy 2022, 24, 334. https://doi.org/10.3390/e24030334
Deng C, You L, Tang X, Hu G, Gao S. Cuproof: Range Proof with Constant Size. Entropy. 2022; 24(3):334. https://doi.org/10.3390/e24030334
Chicago/Turabian StyleDeng, Cong, Lin You, Xianghong Tang, Gengran Hu, and Shuhong Gao. 2022. "Cuproof: Range Proof with Constant Size" Entropy 24, no. 3: 334. https://doi.org/10.3390/e24030334
APA StyleDeng, C., You, L., Tang, X., Hu, G., & Gao, S. (2022). Cuproof: Range Proof with Constant Size. Entropy, 24(3), 334. https://doi.org/10.3390/e24030334






