Entropy and Network Centralities as Intelligent Tools for the Investigation of Terrorist Organizations
Abstract
:1. Introduction
2. Methodology
2.1. Centrality Measures
2.1.1. Degree Centrality
2.1.2. Betweenness Centrality
2.1.3. Clustering Coefficient
2.2. Identification of Roles
2.3. Entropy of Centralities
3. Data Sets
3.1. Terrorist Organization “Jamaah Islamiah Section of Indonesia”
3.2. Terrorist Organization “Hamburg Cell”
3.3. Terrorist Organization “Al-Qaeda Section of Madrid”
3.4. Terrorist Organization “Jamaah Islamiah Section of Philippines”
4. Results
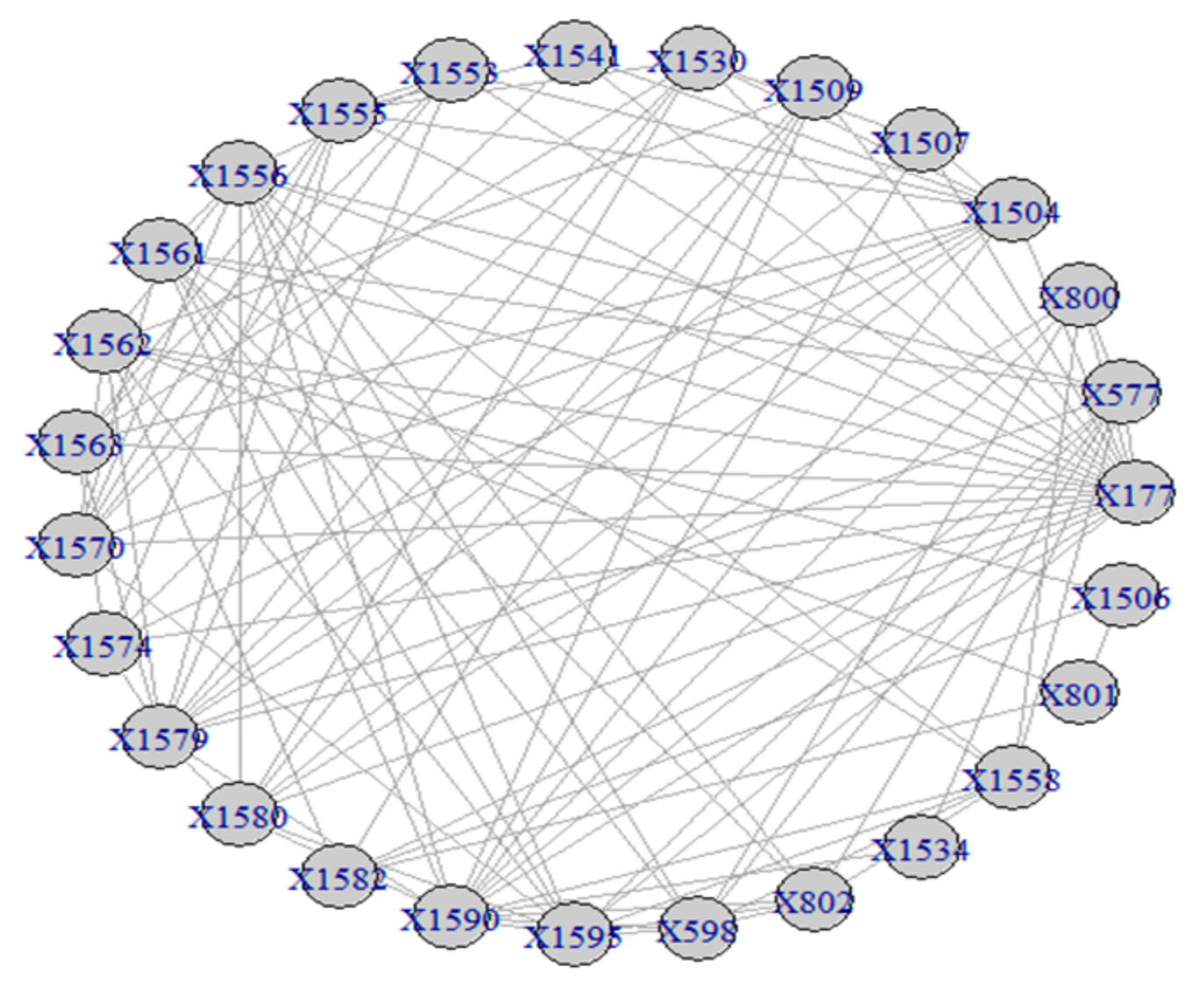
4.1. Terrorist Organization “Jamaah Islamiah Section of Indonesia”
4.2. Terrorist Organization “Hamburg Cell”
4.3. Terrorist Organization “Al-Qaeda Section of Madrid”
4.4. Terrorist Organization “Jamaah Islamiah Section of Philippines”
5. Discussion
5.1. Different Roles of the Members of Terrorist Organizations
5.2. Early Signs of Impending Terrorist Acts
6. Conclusions
Supplementary Materials
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Council of the European, European Union. Criminal Offence to Participate in a Criminal Organisation. Off. J. Eur. Union 1998, 31998F0733, 1–3. [Google Scholar]
- Council Of The European Union. Fight Against Organised Crime. Off. J. Eur. Union. Available online: https://www.consilium.europa.eu/en/policies/eu-fight-against-crime/ (accessed on 1 August 2021).
- Terrorism: Facts and Statistics; Statisra: Hamburg, Germany, 10 September 2021. Available online: https://www.statista.com/topics/2267/terrorism/ (accessed on 1 August 2021).
- Chaisson, E.J.; Chaisson, E. Cosmic Evolution: The Rise of Complexity in Nature; Harvard University Press: Cambridge, MA, USA, 2001; ISBN 978-0-674-00987-5. [Google Scholar]
- Barrat, A.; Barthélemy, M.; Vespignani, A. Dynamical Processes on Complex Networks; Cambridge University Press: Cambridge, UK, 2008; ISBN 978-1-107-37742-4. [Google Scholar]
- Vespignani, A.; Caldarelli, G. Large Scale Structure and Dynamics of Complex Networks: From Information Technology to Finance and Natural Science; World Scientific: Singapore, 2007; ISBN 978-981-4475-41-9. [Google Scholar]
- Estrada, E. The Structure of Complex Networks: Theory and Applications; OUP Oxford: Oxford, UK, 2012; ISBN 978-0-19-959175-6. [Google Scholar]
- Kolaczyk, E.D.; Csárdi, G. Network Topology Inference. In Statistical Analysis of Network Data with R; Springer International Publishing: Cham, Switzerland, 2020; pp. 115–140. ISBN 978-3-030-44129-6. [Google Scholar]
- Kolaczyk, E.D.; Csárdi, G. Dynamic Networks. In Statistical Analysis of Network Data with R; Springer International Publishing: Cham, Switzerland, 2020; pp. 207–223. ISBN 978-3-030-44129-6. [Google Scholar]
- Freeman, L.C. Centrality in Social Networks Conceptual Clarification. Soc. Netw. 1978, 1, 215–239. [Google Scholar] [CrossRef] [Green Version]
- Newman, M. Networks; Oxford University Press: Oxford, UK, 2018; ISBN 978-0-19-252749-3. [Google Scholar]
- Thurner, S.; Hanel, R.; Klimek, P. Introduction to the Theory of Complex Systems; Oxford University Press: Oxford, UK, 2018; ISBN 978-0-19-255507-6. [Google Scholar]
- Airoldi, E.M. Getting Started in Probabilistic Graphical Models. PLoS Comput. Biol. 2007, 3, e252. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Kolaczyk, E.D.; Csárdi, G. Networked Experiments. In Statistical Analysis of Network Data with R; Springer International Publishing: Cham, Switzerland, 2020; pp. 187–205. ISBN 978-3-030-44129-6. [Google Scholar]
- Kolaczyk, E.D.; Csárdi, G. Mathematical Models for Network Graphs. In Statistical Analysis of Network Data with R; Springer International Publishing: Cham, Switzerland, 2020; pp. 69–85. ISBN 978-3-030-44129-6. [Google Scholar]
- Li, H. Centrality Analysis of Online Social Network Big Data. In Proceedings of the 2018 IEEE 3rd International Conference on Big Data Analysis (ICBDA), Shanghai, China, 9–12 March 2018. [Google Scholar]
- Boldi, P.; Vigna, S. Axioms for Centrality. Internet Math. 2014, 10, 222–262. [Google Scholar] [CrossRef] [Green Version]
- Agreste, S.; Catanese, S.; De Meo, P.; Ferrara, E.; Fiumara, G. Network Structure and Resilience of Mafia Syndicates. Inf. Sci. 2016, 351, 30–47. [Google Scholar] [CrossRef] [Green Version]
- Yang, C.C.; Ng, T.D. New Brunswick, NJ Terrorism and Crime Related Weblog Social Network: Link, Content Analysis and Information Visualization. In Proceedings of the 2007 IEEE Intelligence and Security Informatics, New Brunswick, NJ, USA, 23–24 May 2007; pp. 55–58. [Google Scholar]
- Saramäki, J.; Kivelä, M.; Onnela, J.-P.; Kaski, K.; Kertész, J. Generalizations of the Clustering Coefficient to Weighted Complex Networks. Phys. Rev. E 2007, 75, 027105. [Google Scholar] [CrossRef] [Green Version]
- Memon, B.R. Identifying Important Nodes in Weighted Covert Networks Using Generalized Centrality Measures. In Proceedings of the 2012 European Intelligence and Security Informatics Conference, Odense, Denmark, 22–24 August 2012; pp. 131–140. [Google Scholar]
- Pacheco, J.M. Crime as a Complex System: Comment on “Statistical Physics of Crime: A Review” by M.R. D’Orsogna and M. Perc. Phys. Life Rev. 2015, 12, 32–33. [Google Scholar] [CrossRef]
- Primicerio, M. The Role of Mathematical Modelling in Modern Criminology: Comment on “Statistical Physics of Crime: A Review” by M.R. D’Orsogna and M. Perc. Phys. Life Rev. 2015, 12, 34–35. [Google Scholar] [CrossRef] [Green Version]
- Ribeiro, H.V. We Need More Empirical Investigations and Model Validation for a Better Understanding of Crime: Comment on “Statistical Physics of Crime: A Review” by M.R. D’Orsogna and M. Perc. Phys. Life Rev. 2015, 12, 36–37. [Google Scholar] [CrossRef]
- Rodríguez, N. Recent Advances in Mathematical Criminology: Comment on “Statistical Physics of Crime: A Review” by M.R. D’Orsogna and M. Perc. Phys. Life Rev. 2015, 12, 38–39. [Google Scholar] [CrossRef]
- D’Orsogna, M.R.; Perc, M. Physics for Better Human Societies: Reply to Comments on “Statistical Physics of Crime: A Review.”. Phys. Life Rev. 2015, 12, 40–43. [Google Scholar] [CrossRef]
- D’Orsogna, M.R.; Perc, M. Statistical Physics of Crime: A Review. Phys. Life Rev. 2015, 12, 1–21. [Google Scholar] [CrossRef]
- de Bie, J.L.; de Poot, C.J.; Freilich, J.D.; Chermak, S.M. Changing Organizational Structures of Jihadist Networks in the Netherlands. Soc. Netw. 2017, 48, 270–283. [Google Scholar] [CrossRef]
- Morselli, C. Assessing Vulnerable and Strategic Positions in a Criminal Network. J. Contemp. Crim. Justice 2010, 26, 382–392. [Google Scholar] [CrossRef]
- Sparrow, M.K. The Application of Network Analysis to Criminal Intelligence: An Assessment of the Prospects. Soc. Netw. 1991, 13, 251–274. [Google Scholar] [CrossRef]
- Da Cunha, B.R.; Gonçalves, S. Topology, Robustness, and Structural Controllability of the Brazilian Federal Police Criminal Intelligence Network. Appl. Netw. Sci. 2018, 3, 36. [Google Scholar] [CrossRef] [Green Version]
- Collins, B.; Hoang, D.T.; Hwang, D. A Model for Predicting Terrorist Network Lethality and Cohesiveness. In Trends in Artificial Intelligence Theory and Applications. Artificial Intelligence Practices, Proceedings of the International Conference on Industrial, Engineering and Other Applications of Applied Intelligent Systems, Kitakyushu, Japan, 22–25 September 2020; Fujita, H., Fournier-Viger, P., Ali, M., Sasaki, J., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 174–185. [Google Scholar]
- Malang, K.; Wang, S.; Phaphuangwittayakul, A.; Lv, Y.; Yuan, H.; Zhang, X. Identifying Influential Nodes of Global Terrorism Network: A Comparison for Skeleton Network Extraction. Phys. Stat. Mech. Its Appl. 2020, 545, 123769. [Google Scholar] [CrossRef]
- Ferrara, E.; De Meo, P.; Catanese, S.; Fiumara, G. Detecting Criminal Organizations in Mobile Phone Networks. Expert Syst. Appl. 2014, 41, 5733–5750. [Google Scholar] [CrossRef] [Green Version]
- Shaikh, M.A.; Jiaxin, W. Investigative Data Mining: Identifying Key Nodes in Terrorist Networks. In Proceedings of the 2006 IEEE International Multitopic Conference, Islamabad, Pakistan, 23–24 December 2006; pp. 201–206. [Google Scholar]
- Ezeh, C.; Tao, R.; Zhe, L.; Yiqun, W.; Ying, Q. Multi-Type Node Detection in Network Communities. Entropy 2019, 21, 1237. [Google Scholar] [CrossRef] [Green Version]
- Helbing, D.; Brockmann, D.; Chadefaux, T.; Donnay, K.; Blanke, U.; Woolley-Meza, O.; Moussaid, M.; Johansson, A.; Krause, J.; Schutte, S.; et al. Saving Human Lives: What Complexity Science and Information Systems Can Contribute. J. Stat. Phys. 2015, 158, 735–781. [Google Scholar] [CrossRef]
- Wasserman, S.; Faust, K. Social Network Analysis: Methods and Applications; Cambridge University Press: Cambridge, UK, 1994; ISBN 978-0-521-38707-1. [Google Scholar]
- Restrepo, J.G.; Ott, E.; Hunt, B.R. Characterizing the Dynamical Importance of Network Nodes and Links. Phys. Rev. Lett. 2006, 97, 094102. [Google Scholar] [CrossRef] [Green Version]
- Rodríguez, J.A.; Estrada, E.; Gutiérrez, A. Functional Centrality in Graphs. Linear Multilinear Algebra 2007, 55, 293–302. [Google Scholar] [CrossRef] [Green Version]
- Klein, D.J. Centrality Measure in Graphs. J. Math. Chem. 2010, 47, 1209–1223. [Google Scholar] [CrossRef]
- Hughes, C.E.; Bright, D.A.; Chalmers, J. Social Network Analysis of Australian Poly-Drug Trafficking Networks: How Do Drug Traffickers Manage Multiple Illicit Drugs? Soc. Netw. 2017, 51, 135–147. [Google Scholar] [CrossRef]
- Baika, L.; Campana, P. Centrality, Mobility, and Specialization: A Study of Drug Markets in a Non-Metropolitan Area in the United Kingdom. J. Drug Issues 2020, 50, 107–126. [Google Scholar] [CrossRef]
- Gutfraind, A.; Genkin, M. A Graph Database Framework for Covert Network Analysis: An Application to the Islamic State Network in Europe. Soc. Netw. 2017, 51, 178–188. [Google Scholar] [CrossRef]
- Li, Y.; Cai, W.; Li, Y.; Du, X. Key Node Ranking in Complex Networks: A Novel Entropy and Mutual Information-Based Approach. Entropy 2020, 22, 52. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Ziviani, A.; Gomes, A.; Rodrigues, P.S.; Monsores, M.L. Network Anomaly Detection Using Nonextensive Entropy. IEEE Commun. Lett. 2007, 11, 1034–1036. [Google Scholar] [CrossRef]
- Campedelli, G.M.; Cruickshank, I.; Carley, K.M. A Complex Networks Approach to Find Latent Clusters of Terrorist Groups. Appl. Netw. Sci. 2019, 4, 1–22. [Google Scholar] [CrossRef] [Green Version]
- Kalantari, M.; Rahmaty, A.; Toomanian, A.; Dero, Q. A New Methodological Framework for Crime Spatial Analysis Using Local Entropy Map. Mod. Appl. Sci. 2016, 10, 179. [Google Scholar] [CrossRef] [Green Version]
- Lopes, A.M.; Machado, J.A.T.; Mata, M.E. Analysis of Global Terrorism Dynamics by Means of Entropy and State Space Portrait. Nonlinear Dyn. 2016, 85, 1547–1560. [Google Scholar] [CrossRef] [Green Version]
- Wen, T.; Jiang, W. Measuring the Complexity of Complex Network by Tsallis Entropy. Phys. Stat. Mech. Its Appl. 2019, 526, 121054. [Google Scholar] [CrossRef]
- Petter, H.; Jari, S. Temporal Network Theory; Springer: Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- Holme, P.; Saramäki, J. Temporal Networks. Phys. Rep. 2012, 519, 97–125. [Google Scholar] [CrossRef] [Green Version]
- Gilbert, F.; Simonetto, P.; Zaidi, F.; Jourdan, F.; Bourqui, R. Communities and Hierarchical Structures in Dynamic Social Networks: Analysis and Visualization. Soc. Netw. Anal. Min. 2011, 1, 83–95. [Google Scholar] [CrossRef]
- Kolaczyk, E.D.; Csárdi, G. Modeling and Prediction for Processes on Network Graphs. In Statistical Analysis of Network Data with R; Springer International Publishing: Cham, Switzerland, 2020; pp. 141–167. ISBN 978-3-030-44129-6. [Google Scholar]
- Kolaczyk, E.D.; Csárdi, G. Descriptive Analysis of Network Graph Characteristics. In Statistical Analysis of Network Data with R; Springer International Publishing: Cham, Switzerland, 2020; pp. 43–68. ISBN 978-3-030-44129-6. [Google Scholar]
- Khinchin, A. Mathematical Foundations of Information Theory; Dover: New York, NY, USA, 1957. [Google Scholar]
- Yanglom, A.; Yanglom, I. Probability and Information; Reidel: Dordecht, The Netherlands, 1983. [Google Scholar]
- Shannon, C.; Weaver, W. The Mathematical Theory of Communication; University of Illinois Press: Urbana, IL, USA, 1949. [Google Scholar]
- Cover, T.M. Elements of Information Theory; John Wiley & Sons: Hoboken, NJ, USA, 1999. [Google Scholar]
- Farquhar, I.E.; Seeger, R.J. Ergodic Theory in Statistical Mechanics. Am. J. Phys. 1965, 33, 973. [Google Scholar] [CrossRef]
- Cornfeld, I.P.; Fomin, S.V.; Sinai, Y.G. Ergodic Theory; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Gell-Mann, M.; Tsallis, C. Nonextensive Entropy: Interdisciplinary Applications; Oxford University Press: Oxford, UK, 2004. [Google Scholar]
- John Jay & ARTIS Transnational Terrorism Database Austrailian Embassy Bombing Data Set [Data Set]. 2016. Available online: http://doitapps.jjay.cuny.edu/jjatt/index.php (accessed on 1 August 2021).
- Jemaah Islamiyah—Wikipedia. Available online: https://en.wikipedia.org/w/index.php?title=Jemaah_Islamiyah&oldid=1025043319 (accessed on 26 June 2021).
- John Jay & ARTIS Transnational Terrorism Database Hamburg Cell 9/11 [Data Set]. 2001. Available online: http://doitapps.jjay.cuny.edu/jjatt/data.php (accessed on 1 August 2021).
- Hamburg Cell—Wikipedia. Available online: https://en.wikipedia.org/w/index.php?title=Hamburg_cell&oldid=977822420 (accessed on 10 August 2021).
- John Jay & ARTIS Transnational Terrorism Database Madrid Train Bombing 2004 [Data Set]. 2004. Available online: http://doitapps.jjay.cuny.edu/jjatt/data.php (accessed on 1 August 2021).
- Madrid Train Bombings—Wikipedia. 2004. Available online: https://en.wikipedia.org/w/index.php?title=2004_Madrid_train_bombings&oldid=1037095728 (accessed on 10 August 2021).
- John Jay & ARTIS Transnational Terrorism Database Phillippines Bombing [Data Set]. 2000. Available online: http://doitapps.jjay.cuny.edu/jjatt/data.php (accessed on 1 August 2021).
- Rizal Day Bombings—Wikipedia. Available online: https://en.wikipedia.org/w/index.php?title=Rizal_Day_bombings&oldid=1033689495 (accessed on 10 August 2021).
- Marriott Hotel Bombing—Wikipedia. 2003. Available online: https://en.wikipedia.org/w/index.php?title=2003_Marriott_Hotel_bombing&oldid=1037387377 (accessed on 10 August 2021).
- Australian Embassy Bombing in Jakarta—Wikipedia. Available online: https://en.wikipedia.org/wiki/Australian_Embassy_bombing_in_Jakarta (accessed on 10 August 2021).
- Bali Bombings—Wikipedia. 2002. Available online: https://en.wikipedia.org/w/index.php?title=2002_Bali_bombings&oldid=1025707408 (accessed on 26 June 2021).
- Schurger, A.; Sitt, J.D.; Dehaene, S. An Accumulator Model for Spontaneous Neural Activity Prior to Self-Initiated Movement. Proc. Natl. Acad. Sci. USA 2012, 109, E2904–E2913. [Google Scholar] [CrossRef] [Green Version]










| Central Nodes | ||||
|---|---|---|---|---|
| High Degree | Mediators | Teamworking Nodes | ||
| Periods | 1985–1989 | - | - | - |
| 1990–1994 | 1580 (0.1) | - | - | |
| 1595 (0.1) | ||||
| 1995–1999 | 1556 (0.1) | - | - | |
| 1580 (0.1) | ||||
| 1595 (0.1) | ||||
| 2000 | 1556 (0.1) | - | - | |
| 1561 (0.1) | ||||
| 1562 (0.1) | ||||
| 1570 (0.1) | ||||
| 1580 (0.1) | ||||
| 1595 (0.1) | ||||
| 2001 | 1556 (0.1) | - | - | |
| 1561 (0.1) | ||||
| 1562 (0.1) | ||||
| 1570 (0.1) | ||||
| 1580 (0.1) | ||||
| 1582 (0.1) | ||||
| 1590 (0.1) | ||||
| 1595 (0.1) | ||||
| 2002 | 1556 (0.7) | 1509 (0.2) | - | |
| 1561 (0.5) | ||||
| 1562 (0.7) | 1556 (0.2) | |||
| 1580 (0.7) | 1580 (0.3) | |||
| 1582 (0.7) | 1582 (0.2) | |||
| 1590 (0.7) | ||||
| 1595 (1.0) | ||||
| 2003 | 1579 (0.2) | 1553 (0.2) | 0177 (0.6) | |
| 1556 (0.3) | 1574 (0.6) | |||
| 1561 (0.3) | 1579 (0.6) | |||
| 1590 (0.3) | ||||
| 2004 | 177 (0.7) | 0177 (0.3) | 0801 (0.6) | |
| 1579 (0.5) | 0802 (0.6) | |||
| 1507 (0.6) | ||||
| 1590 (0.5) | 1534 (0.6) | |||
| 1563 (0.6) | ||||
| 1574 (0.6) | ||||
| 2005 | 177 (0.2) | - | 801 (1.0) | |
| 1506 (0.8) | ||||
| 1562 (0.2) | 1574 (1.0) | |||
| 2006 | 800 (0.1) | - | 177 (0.3) | |
| 0800 (0.3) | ||||
| 177 (0.1) | 1580 (1.0) | |||
| 2007 | - | - | ||
| Central Nodes | ||||
|---|---|---|---|---|
| High Degree | Mediators | Teamworking Nodes | ||
| Periods | 1985–1989 | - | - | 57 (0.6) |
| 58 (0.7) | ||||
| 1012 (0.6) | ||||
| 1032 (0.7) | ||||
| 1990–1994 | 57 (0.1) | - | 58 (0.7) | |
| 1012 (0.6) | ||||
| 1032 (0.7) | ||||
| 1995 | 57 (0.1) | - | 58 (0.7) | |
| 60 (0.1) | 1012 (0.6) | |||
| 61 (0.1) | 1030 (0.6) | |||
| 63 (0.1) | 1032 (0.7) | |||
| 1035 (0.6) | ||||
| 1996 | 1026 (0.2) | 1026 (0.1) 57 (0.1) 61 (0.1) | 58 (0.7) | |
| 1035 (0.2) | 1012 (0.6) | |||
| 1037 (0.2) | 1030 (0.6) | |||
| 60 (0.2) | 1032 (0.7) | |||
| 63 (0.2) | 1033 (0.6) | |||
| 1997 | 57 (0.1) | - | 58 (0.7) | |
| 60 (0.1) | 1012 (0.6) | |||
| 61 (0.1) | 1030 (0.6) | |||
| 63 (0.1) | 1032 (0.7) | |||
| 1035 (0.6) | ||||
| 1998 | 61 (0.4) | 60 (0.1) | 1014 (0.7) | |
| 1016 (0.1) | ||||
| 64 (0.4) | 64 (0.1) | 1017 (0.7) | ||
| 65 (0.2) | ||||
| 1999 | 64 (0.5) | 64 (0.1) | 60 (0.6) | |
| 65 (0.1) | 1017 (0.7) | |||
| 2000 | 60 (0.3) | 65 (0.1) | 60 (0.6) | |
| 61 (0.3) | ||||
| 62 (0.3) | 66 (0.6) | |||
| 64 (0.3) | ||||
| 65 (0.3) | 1017 (0.6) | |||
| 1005 (0.3) | ||||
| 2001 | 60 (0.3) | 61 (0.1) | 63 (0.6) | |
| 61 (0.3) | 1017 (0.6) | |||
| 62 (0.3) | 1039 (0.7) | |||
| 64 (0.3) | ||||
| 2002 | - | - | 64 (0.7) | |
| 1005 (0.7) | ||||
| 2003 | - | - | 58 (0.5) | |
| 1012 (0.5) | ||||
| 1032 (0.5) | ||||
| 2004 | - | - | 58 (0.5) | |
| 1012 (0.5) | ||||
| 1032 (0.5) | ||||
| 2005 | - | - | - | |
| 2006 | - | - | 58 (0.5) | |
| 1012 (0.5) | ||||
| 1032 (0.5) | ||||
| Central Nodes | ||||
|---|---|---|---|---|
| High Degree | Mediators | Teamworking Nodes | ||
| Periods | 1985–1989 | - | - | - |
| 1990–1994 | - | - | - | |
| 1995 | - | - | - | |
| 1996 | - | - | 3100 (0.1) | |
| 1997 | - | - | 3100 (0.1) | |
| 1998 | - | - | 3100 (0.1) | |
| 1999 | - | - | 3100 (0.1) | |
| 2000 | - | - | 318 (0.8) | |
| 3100 (0.1) | ||||
| 3104 (1.0) | ||||
| 2001 | - | - | 3100 (0.1) | |
| 2002 | 3132 (0.2) | - | 3135 (1.0) | |
| 3138 (0.6) | ||||
| 3140 (0.6) | ||||
| 3148 (0.5) | ||||
| 3136 (0.2) | 3149 (0.5) | |||
| 3156 (0.8) | ||||
| 3157 (0.5) | ||||
| 3167 (1.0) | ||||
| 2003 | 3132 (0.2) | 3157 (0.1) | 3134 (0.5) | |
| 3134 (0.2) | 3146 (1.0) | |||
| 3144 (0.3) | 3147 (1.0) | |||
| 3145 (0.2) | 3148 (0.6) | |||
| 3147 (0.2) | 3149 (0.5) | |||
| 3148 (0.2) | 3151 (0.6) | |||
| 3149 (0.2) | 3156 (0.6) | |||
| 3150 (0.2) | 3157 (0.5) | |||
| 3157 (0.2) | 3165 (0.8) | |||
| 3167 (1.0) | ||||
| 2004 | - | - | 3155 (0.6) | |
| 3161 (0.6) | ||||
| 3179 (0.6) | ||||
| 2005 | - | - | - | |
| 2006 | - | - | ||
| Central Nodes | ||||
|---|---|---|---|---|
| High Degree | Mediators | Teamworking Nodes | ||
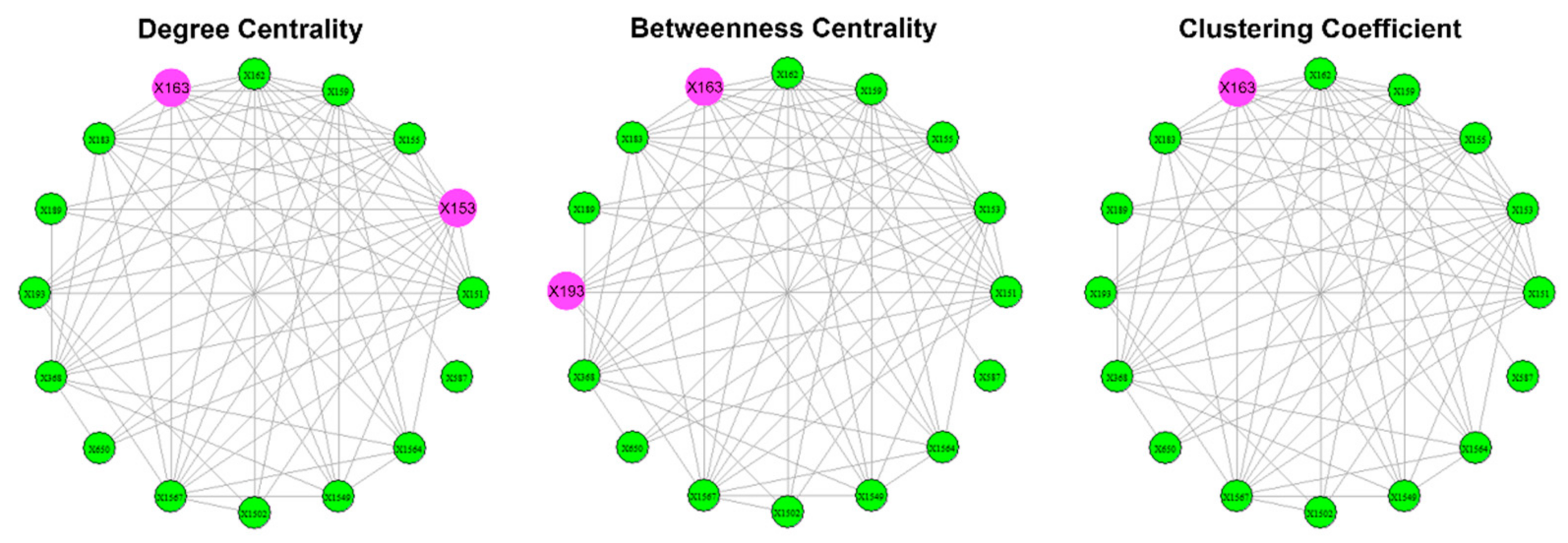
| Periods | 1985–1989 | 151 (0.4) | 151 (0.1) | 155 (1.0) |
| 155 (0.4) | 155 (0.2) | 162 (1.0) | ||
| 1990–1994 | 151 (0.4) | 368 (0.2) | 162 (1.0) | |
| 153 (0.4) | ||||
| 155 (0.4) | ||||
| 159 (0.4) | ||||
| 163 (0.4) | ||||
| 368 (0.5) | ||||
| 1564 (0.4) | ||||
| 1995–1999 | 151 (0.6) | 151 (0.1) | 155 (0.6) | |
| 153 (0.6) | 155 (0.1) | 162 (0.7) | ||
| 155 (0.6) | 159 (0.1) | |||
| 163 (0.6) | 163 (0.1) | 183 (0.7)650 (0.6) | ||
| 368 (0.6) | 193 (0.1) | |||
| 183 (0.6) | 368 (0.1) | |||
| 2000 | 153 (0.9) | 155 (0.1) | 162 (0.6) | |
| 189 (0.6) | ||||
| 163 (0.8) | 163 (0.1) | 650 (0.6) | ||
| 193 (0.1) | 1502 (0.6) | |||
| 1567 (0.6) | ||||
| 2001 | 153 (0.9) | 155 (0.1) | 162 (0.6) | |
| 189 (0.6) | ||||
| 163 (0.8) | 163 (0.1) | 650 (0.6) | ||
| 193 (0.1) | 1502 (0.6) | |||
| 1567 (0.6) | ||||
| 2002 | 153 (0.9) | 151 (0.1) | 155 (0.7) | |
| 162 (0.6) | ||||
| 155 (0.2) | 189 (0.6) | |||
| 163 (0.8) | 650 (0.6) | |||
| 163 (0.1) | 1502 (0.6) | |||
| 1567 (0.6) | ||||
| 2003 | 153 (0.4) | 153 (0.1) | 155 (0.7) | |
| 162 (0.6) | ||||
| 189 (0.6) | ||||
| 650 (0.6) | ||||
| 1502 (0.6) | ||||
| 1567 (0.6) | ||||
| 2004 | - | - | - | |
| 2005 | - | - | - | |
| 2006 | 151 (0.2) | - | 151 (0.3) | |
| 159 (0.1) | 159 (0.5) | |||
| 1549 (0.1) | 1549 (1.0) | |||
| 2007 | 151 (0.2) | - | - | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Spyropoulos, A.Z.; Bratsas, C.; Makris, G.C.; Ioannidis, E.; Tsiantos, V.; Antoniou, I. Entropy and Network Centralities as Intelligent Tools for the Investigation of Terrorist Organizations. Entropy 2021, 23, 1334. https://doi.org/10.3390/e23101334
Spyropoulos AZ, Bratsas C, Makris GC, Ioannidis E, Tsiantos V, Antoniou I. Entropy and Network Centralities as Intelligent Tools for the Investigation of Terrorist Organizations. Entropy. 2021; 23(10):1334. https://doi.org/10.3390/e23101334
Chicago/Turabian StyleSpyropoulos, Alexandros Z., Charalampos Bratsas, Georgios C. Makris, Evangelos Ioannidis, Vassilis Tsiantos, and Ioannis Antoniou. 2021. "Entropy and Network Centralities as Intelligent Tools for the Investigation of Terrorist Organizations" Entropy 23, no. 10: 1334. https://doi.org/10.3390/e23101334
APA StyleSpyropoulos, A. Z., Bratsas, C., Makris, G. C., Ioannidis, E., Tsiantos, V., & Antoniou, I. (2021). Entropy and Network Centralities as Intelligent Tools for the Investigation of Terrorist Organizations. Entropy, 23(10), 1334. https://doi.org/10.3390/e23101334











