1. Introduction
Quantum key distribution (QKD) [
1,
2,
3] is well known to have its goal in developing methods (protocols) for sharing a secret key between legitimate users, who can lately use the key for the confidential information transfers. First started with the discrete-variable protocols based on direct detection of single-photon states (and their emulation using weak coherent pulses or entangled photon pairs [
4]), QKD was later extended to the realm of continuous variables (CV) [
5] based on efficient and low-noise homodyne detection of multiphoton coherent or squeezed states of light.
One of the important applications of QKD is in the extra-terrestrial channels, which potentially allow extremely long-distance secure communication enabled by QKD over a satellite. While discrete-variable protocols were recently successfully tested over the satellite links [
6,
7,
8,
9], the applicability of satellite-based CV QKD remains less studied. Indeed, it was considered in the asymptotic regime of the infinitely many quantum states [
10,
11], which however is never the case in practice. Moreover, CV QKD may have an important practical advantage in free-space applications and particularly in the satellite-based channels because a homodyne detector, in which the signal is coupled to a narrow-band local oscillator (bright coherent beam used as a phase reference), intrinsically filters out the background radiation at unmatched wavelengths [
12]. Thus CV QKD can operate in conditions of strong stray light and potentially at daytime, which, in the case of discrete-variable protocols, would require additional filtering, increasing attenuation and complexity of the set-up. Recently, the feasibility of coherent-state CV QKD over satellite links was discussed in [
13]. In the current work we analyze applicability of CV QKD over satellite-based channels considering also squeezed signal states. As the feasible squeezing up 10 dB, achievable with current technology [
14], is known to improve robustness of CV QKD to noise [
15,
16,
17], we confirm its usefulness in the satellite-based links as well. We build the channel model on the assumption of normal fluctuation of deflected signal beam center around the receiving aperture center and study applicability of CV QKD, taking into account the finite data ensemble size. We show that in this regime the protocols appear to be extremely sensitive to strong channel attenuation and large amounts of data are required for successful realization of CV QKD over satellites, which contradicts relatively short passage times. Possible solutions to circumvent the problem can be (i) use of squeezed states, that reduce requirements on the data ensemble size and can tolerate stronger attenuation and channel noise; (ii) relaxation of security assumptions considering individual attacks or passive eavesdropping, introducing no excess noise; (iii) increase of the link transmittance using larger telescopes in the downlink regime; (iv) increase of the repetition rate of the system in order to accumulate larger statistics. Our results reveal substantial challenges for implementing CV QKD over satellites but shows no fundamental limits for such realizations. Already under the strict assumption of collective eavesdropping attacks and untrusted channel noise, CV QKD protocols using feasible squeezing should be applicable with low-orbit satellites, while in the assumption of passive eavesdropping squeezed-state CV QKD can tolerate up to 43 dB of channel attenuation, which paves the way towards realization over geostationary satellites.
2. Security of CV QKD
We address satellite-based implementation of Gaussian CV QKD protocols [
18] using coherent or squeezed states of light as shown in
Figure 1a. We describe the quantum states of light in a given mode of electromagnetic radiation using two complementary observables, namely quadratures, being analogues of position and momentum operators of a single particle, and expressed through mode’s quantum operators as
and
. The sender Alice prepares coherent or squeezed states using respectively a laser source or an optical parametric oscillator [
19] and modulates the states by applying quadrature displacements, governed by independent zero-centered Gaussian distributions, by using quadrature modulators. This way Alice prepares the states described by the quadratures
and
, where
and
with variances
and
(we define variance of an operator
with zero mean value as
) are the quadrature values of the signal (so that either
for coherent states or with no loss of generality we assume
quadrature squeezed states with
).
and
with
are the displacements known to Alice, which constitute her classical data contributing to the final secret key. The signal then travels through a generally noisy and lossy quantum channel, which can be optimally [
20,
21] represented as a Gaussian channel resulting in the output state described by the quadratures
, where
is the channel transmittance,
with
is the variance of the vacuum noise concerned with the channel attenuation, and
is the contribution from the excess noise on the channel output with
, similarly for
quadrature with the same
and
, as the free-space channel is typically phase-insensitive. Trusted parties use a beacon laser for signal acquiring, tracing and pointing, as well as for timing synchronization [
22]. The receiving side Bob is performing homodyne detection on the incoming mode by measuring
or
(bases have to be randomly switched between in order to fully characterize channel loss and excess noise). Preferably such measurement is made using locally generated local oscillator [
23,
24], that despite additional noise contribution from signal wavefront aberration [
25] and phase noise due to relative phase drift [
26,
27,
28], allows for one to avoid phase reference pulse attenuation in a strongly lossy satellite link and provides enhanced security of the protocol by ruling out the attacks on the local oscillator. After accumulating a certain amount of data points
N from state preparation and measurement, parties use
of these to estimate the channel parameters
and
, from which the security of the protocol can be assessed as described below. The remaining
n points are processed using error correction and privacy amplification algorithms [
4] in order to obtain the resulting provably secure key which can then be used for classical encryption. The ratio
can be optimized [
29], here for simplicity we assume it to be
(which is close to optimal except for the low repetition rates) and resulting estimates to be perfectly accurate i.e., with infinitesimal confidence intervals (or already being pessimistic lower bounds complying with a given probability of failure of the channel estimation procedure). We assume that the remote trusted side (Bob) is the reference side for the error correction algorithms, thus using so-called reverse reconciliation, which was shown robust against any level of pure channel loss [
30] and is applicable in the strongly attenuating links with
.
Security of CV QKD was established against two main types of attacks, namely individual, when an eavesdropper is able to interact optimal probe states with the signal states and then individually measure the probes, and collective, when the probes are assumed to be stored in a quantum memory after the interaction and then optimally collectively measured, which increases the amount of information that can be potentially obtained by an eavesdropper [
31]. Security of the coherent-state protocol with heterodyne detection against collective can be extended to security against general attacks using de Finetti reduction [
32], similar extensions for the squeezed-state protocol and homodyne detection being more demanding [
33,
34].
We study security of the above described protocol by evaluating the lower bound on secure key rate per channel use, which in the finite-size regime, reverse reconciliation scenario and firstly assuming collective attacks, performed by an eavesdropper, reads
where
is postprocessing efficiency representing how close the trusted parties are able to reach the Shannon mutual information
using realistic error correction codes,
is the Holevo bound [
35], giving the upper bound on an eavesdropper’s information on the measurement results at the remote receiving side, Bob, and
is the correction parameter related to the finite-size effects [
36], where
is the smoothing parameter that contributes to the overall failure probability of the protocol and is set further to
.
The mutual information between the trusted parties
for the Gaussian-distributed data can be expressed through variances and correlations between the measurement outcomes, i.e., through the variance of Bob’s measurement
, where
, and conditional variance
,
is the variance of Alice’s data and
is the correlation between modulation data and measurements on
, for the zero-mean-distributed observables obtained as
. The resulting expression for the mutual information then reads
and is essentially determined by the signal modulation variance
, signal state variance
, channel transmittance
, and channel noise
related to the channel output.
Evaluation of the Holevo bound on the other hand is more involved. It is based on the assumption that Eve holds purification of the noise added in the channel (due to losses and excess noise) and relies on the evaluation of von Neumann entropies of the state shared between Alice and Bob [
37]. This is performed in the equivalent entanglement-based representation, when state preparation is purified using two-mode entangled state. In the case of coherent-state protocol a symmetrical two-mode squeezed vacuum (TMSV) [
38] state with variance
is used for purification, such that Alice is measuring one of the modes using a heterodyne (balanced homodyne) detector [
37]. For a general state preparation in the squeezed-state protocol, assuming independent levels of signal squeezing and modulation variance (contrary to the standard symmetrically modulated protocol, where squeezing and modulation are essentially related as
[
39]), we use the generalized entanglement-based scheme using an asymmetrical entangled state instead of TMSV and a homodyne detection on the local mode [
17], as shown in
Figure 1b. The preparation in this case is equivalent to the prepare-and-measure scheme provided the asymmetrical state is constructed of the oppositely squeezed states with variances in
x-quadratures being
while having the opposite variances (
and
respectively) in the
p-quadratures.
In the purification-based scenario, the Holevo bound is evaluated as
, where
denotes the von Neumann (quantum) entropy of a state,
is the quantum entropy of a (generally noisy) state shared between the trusted parties and
is the von Neumann entropy of the state of the trusted parties, conditioned by Bob’s measurement results in
x-quadrature. We obtain the relevant von Neumann entropies from bosonic entropic functions of symplectic eigenvalues of respective covariance matrices of the states, shared between Alice and Bob (see [
37] for details of security analysis techniques in CV QKD).
In the case of individual attacks and reverse reconciliation scenario, the upper bound on the information leakage is reduced to the classical (Shannon) information between Bob and Eve, which, similarly to
(
2) described above, reads
. The evaluation of
is done in the assumption that Eve is able to purify the channel noise. The optimal individual attack in this case is the entangling cloner attack [
40], which is a TMSV state of variance
set so to emulate the channel loss
and noise
. One of the modes of the cloner interacts with the signal with a linear coupling
, corresponding to the channel loss and resulting in
(which gives exactly
as described above and as expected by the trusted parties), while the other mode is measured by Eve in order to reduce her uncertainty on the quantum noise added in the channel. The mutual information between Bob and Eve then reads [
40,
41]
which gives the bounds on the secure key rate in the case of individual eavesdropping attacks, similarly to (
1).
3. CV QKD over Satellite Channels
The main challenge in the satellite-based communication, and particularly the quantum one, is the extremely strong attenuation levels, which are much higher than the typical loss in the terrestrial fiber and free-space links in which QKD was mostly tested.
The total level of signal loss in a satellite link can widely vary and depends on the type of satellite and technical specifications of the channel realization. Indeed, in the recent experiment with measurement of the quantum-limited signal from a geostationary satellite using the homodyne detection, the total loss of 69 dB was observed [
42] with an aperture of 27 cm. The loss can be reduced to 55 dB once a bigger aperture of 1.5 m is used. Alternatively, the channel loss from a low Earth orbit (LEO) satellite can be substantially smaller and as low as 31 dB for an Alphasat-like satellite at a distance of 500 km. The loss can be reduced to about 20 dB by using larger receiving apertures [
42]. Therefore, it is important to assess applicability of CV QKD in various scenarios, mainly resulting in different optical link attenuation levels.
3.1. Quantum Channel and Protocol Parameters
The protocols are essentially influenced by the excess noise on the channel
output,
, further fixed to
shot-noise units (SNU), which are the vacuum quadrature fluctuations. This complies with the experiment in the 100-km optical fiber with the total attenuation of −20 dB, where the noise on the channel
input was estimated as
SNU [
43] and with the recent experiment in the 300 km long low-loss fiber with the total attenuation of −32 dB, where the noise at the channel
input was estimated in the worst case as
SNU [
44]. Note that the excess noise is mainly concerned with imperfect parameter estimation from the homodyne data on the receiving side of the protocol (even if the channel noise is physically absent, the pessimistic assumption on the level of noise, related to noise estimation error, results in effectively nonzero level of channel noise in order to comply with the required probability of failure of channel estimation procedures [
29]), which substantially depends on the stability of the set-up. It is essential that we fix the noise at the channel output contrary to the standard approach in CV QKD, when noise was fixed as relates to the channel input and then scaled by the channel attenuation, making the assessment of the channel noise in long-distance channels too optimistic. Alternatively and taking into account the fact that the excess noise atop of the calibrated electronic noise of the detector appears most likely due to the imperfect estimation of a noiseless quantum channel, one may assume passive eavesdropping such that no untrusted channel excess noise is present. In the case of satellite-based links, where line of sight between the sender and the receiver suggests the absence of equipment capable of active eavesdropping, this is a particularly sensible assumption and it was applied recently for feasibility study of DV QKD over satellite links [
45]. We also take this assumption into account in CV QKD by assuming the excess noise to be trusted (i.e., being out of control by an eavesdropper) and including it in the state purification using the scheme similar to the entangling cloner with a strongly unbalanced coupling to the signal prior to detection [
37].
For the data ensemble size, we rely on the typical passage time of 300 s observed for the Micius quantum satellite [
7]. Assuming repetition rate of a CV QKD system to be of order of GHz, which is challenging but feasible with the current technology [
46], we may expect
data points acquired during a satellite passage, half of which will then contribute to the key. Lastly, postprocessing efficiency is taken
, complying with the currently available algorithms [
47].
The maximum tolerable channel attenuation gives the idea of the protocols applicability independently of the aperture setting and random atmospheric disturbances, i.e., based only on the link optical budget. The results are summarized in
Table 1 for given security assumptions and protocol parameters (signal states and clock rates).
Evidently, in the assumption of passive eavesdropping there is no substantial difference between collective and individual attacks. On the other hand, when the channel excess noise is assumed to be untrusted, relaxing the assumptions on the possible attacks from collective to individual ones can substantially extend the tolerable loss. Note that the use of squeezed states typically increases the tolerable channel attenuation by 4–6 dB depending on the attack assumption (the better improvement being observed upon more strict collective attacks). Furthermore, with the high repetition rate the squeezed-state protocol can tolerate from 30 to 44 dB of channel attenuation depending on the attack assumption, making it potentially feasible in the geostationary scenario.
Performance of CV QKD over short-range (terrestrial) free-space links can be essentially limited by quantum channel transmittance fluctuations [
48,
49], also referred to as fading, which are mainly caused by the atmospheric turbulence effects of beam wander [
50], when a beam spot travels around the receiving aperture. The channel fading then results in increase of the channel noise, detected on the receiver [
48]. Even though this effect will be partially compensated for in the long-distance realization of CV QKD, where beam spot drastically expands during the propagation, which results in channel stabilization at the cost of increasing the overall loss [
51] as well as by active beam tracking and stabilization systems, it must be taken into account in the realistic CV QKD security analysis. However, as the residual transmittance fluctuations due to atmospheric effects are slow (of the order of KHz [
52]) compared to high achievable repetition rates of CV QKD systems (enabled by GHz rates of homodyne detectors [
46]), the fading can be further compensated for by properly grouping the data according to estimated relatively stable transmittance values [
53], which we also apply in our study.
3.2. Satellite-to-Ground Channel Model
In our study we consider that downlink satellite channels, as the turbulence effects, being destructive for CV QKD [
48], are less pronounced in this regime compared to the uplink scenario, where the signal is strongly affected by the atmosphere already in the beginning of the channel [
54]. Optical Gaussian beam in the satellite-to-ground link is influenced by analytically predictable systematic and statistical effects occurring during the communication window. Aside from losses within the receiver optical system
, due to coupling and detection inefficiencies, systematic effects also include diffraction and refraction induced losses. The main source of loss is beam-spot broadening caused by diffraction. The broadening limits the maximal transmission efficiency
as finite receiving aperture of size
a truncates and measures only a part of the incoming collimated beam with spot-size
W. The latter is largely determined as
by divergence of the beam
and the channel length
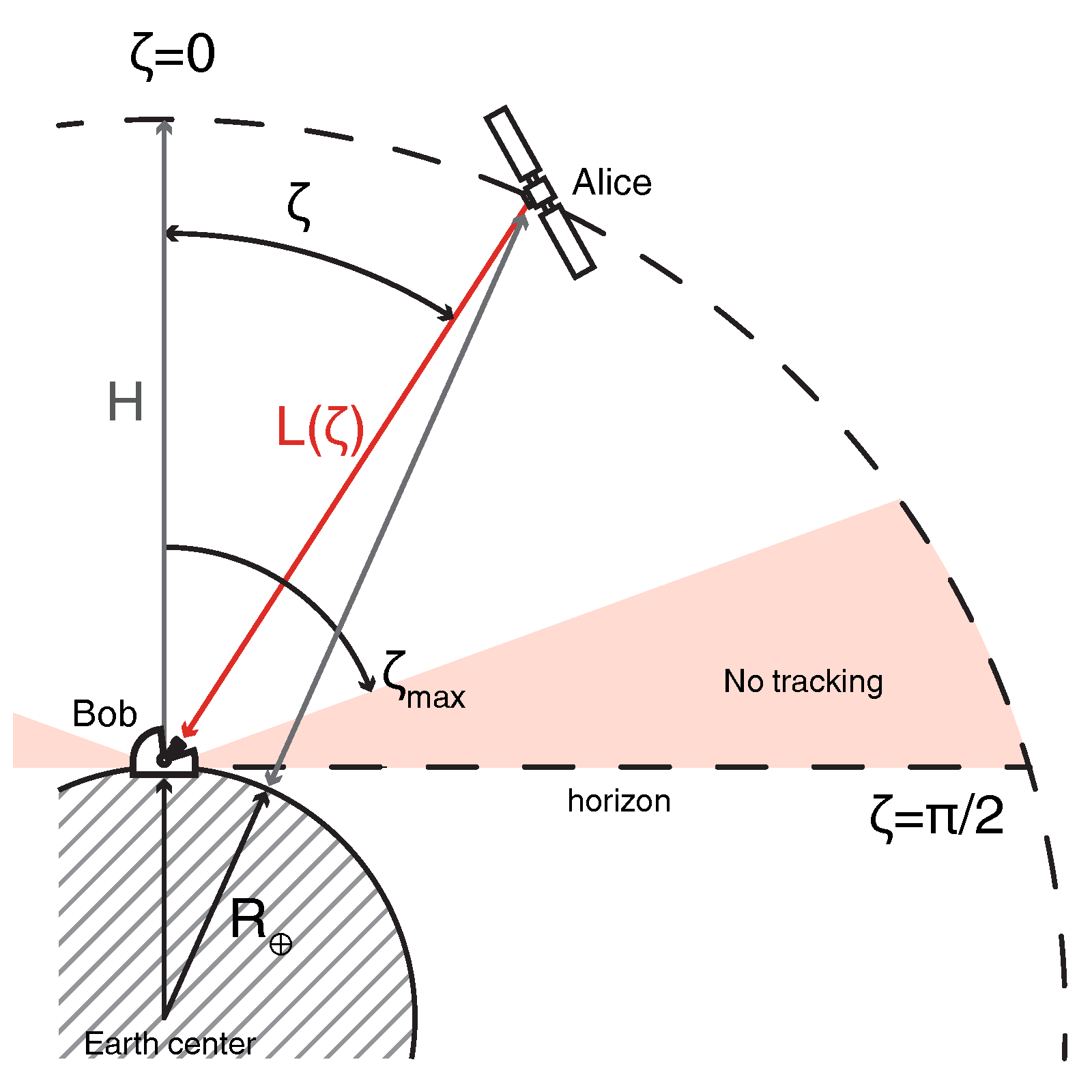
. Line-of-sight distance, also referred to as slant range, between the observer and the satellite depends on the exact position of the latter. In following we assume a perfectly circular Low-Earth orbit within observers meridian plane, characterized by the altitude above the ground
H, ranging from 200 km to 2000 km. The slant range is obtained as
where
is Earth radius and
is zenith angle i.e., between the line pointing in opposite direction to the gravity from the observer and the slant range, see also
Figure 2. Additionally, air density and optical refractive index change with the altitude causing the bending of the beam and making the overall traveling distance longer than the straight geometrical slant range. The refraction induced elongation also depends on the signal wavelength, geographical position and altitude of the receiver as well as atmospheric conditions (relative humidity, temperature, wind, pressure). We assume the communication window is established up to the zenith angle
, when the difference between actual and perceived slant ranges is small [
55]. While such limitation reduces the communication window and the size of data block, it also avoids contributions from the longest propagation distance overall and through the thickest air mass [
56,
57]. Duration of communication window, i.e., total time in view of the satellite
t, determines the amount of accumulated data points
N for given source repetition rate. The time in view is calculated from geometrical considerations and satellite orbital velocity, which for circular orbit in the observers meridian plane can be simplified as [
58,
59]:
where
G is the gravitational constant, and
is Earth mass.
The volume of air mass is related to the atmospheric extinction ratio
, which is a measure of Rayleigh scattering, scattering due to aerosols and molecular absorption experienced by the signal beam in terrestrial atmosphere [
60]. The value of extinction ratio
depends on the the signal wavelength, air constituents, temperature and weather conditions, and its change with increase of the path length through the atmosphere (in terms of zenith angle) can be approximated (for angles up to
where refraction effects are small) as [
61,
62]:
The ratio at zenith can be obtained based on MODTRAN atmospheric transmittance and radiance model [
63], which for rural or urban sea-level Mid-latitude location with clear sky visibility yields
.
Aside from aforementioned effects, refraction and diffraction are also caused by wind shear and temperature fluctuations and consequently by spatial and temporal variations of refractive index in the channel. Such perturbations result in scintillation, deviation of beam-spot from the center of the receiving aperture and deformation of the beam-spot. For satellite links, the beam-spot radius is always significantly larger than the aperture, i.e., , which allows us to ignore the deformation of the Gaussian beam profile, hence making beam wandering the dominant effect governing the fluctuation statistic of the channel transmittance.
The maximal transmission efficiency is reached when incoming signal is perfectly aligned with the receiving aperture (
) and is defined by the ratio
of the aperture and beam spot sizes as follows
Efficiency
decreases with the increase of deflection distance
r, with approximate analytical solution [
50] being
where
and
R are shape and scale parameters respectively:
where
is
n-th order Bessel function. The position of deflected beam center is assumed to be normally fluctuating around the aperture center [
64] and described by random transverse vector
:
where beam-wandering variance is limited by tracking accuracy and beam stabilization
, and
. The analytical form of the probability distribution of atmospheric transmittance is the log-negative Weibull distribution [
64]:
We simulate the values of
for each zenith angle
within the communication window with respect to the clock rate of the CV QKD protocol and combine it with systematic receiver loss
and respective extinction ratio
to obtain an overall mean transmittance
(as well as
) of the satellite pass. Hence the transmittance statistics during an overall communication window consists of contributions from individual simulated free-space channels at every permitted zenith angle
. Both
and
govern the evolution of a covariance matrix of the state shared between Alice and Bob over the fluctuating channel [
65]. Note that we evaluate the mutual information between the trusted parties,
, from the overall covariance matrix, averaged over the whole transmittance distribution (similarly to evaluating the Holevo bound), which we observe to be lower than the average mutual information, hence being the pessimistic estimate. Following is the list of parameters used in the simulation: the receiver aperture radius
(m) (respective plots shown in green color)
(m) (shown in blue), and 1 (m) (red), wavelength
(nm), detection efficiency
dB [
56], tracking and pointing accuracy
(μrad) [
22], and beam divergence
(μrad) [
7]. The resulting mean transmittance for a single pass at altitude
H is shown in
Figure 3.
3.3. Security Evaluation
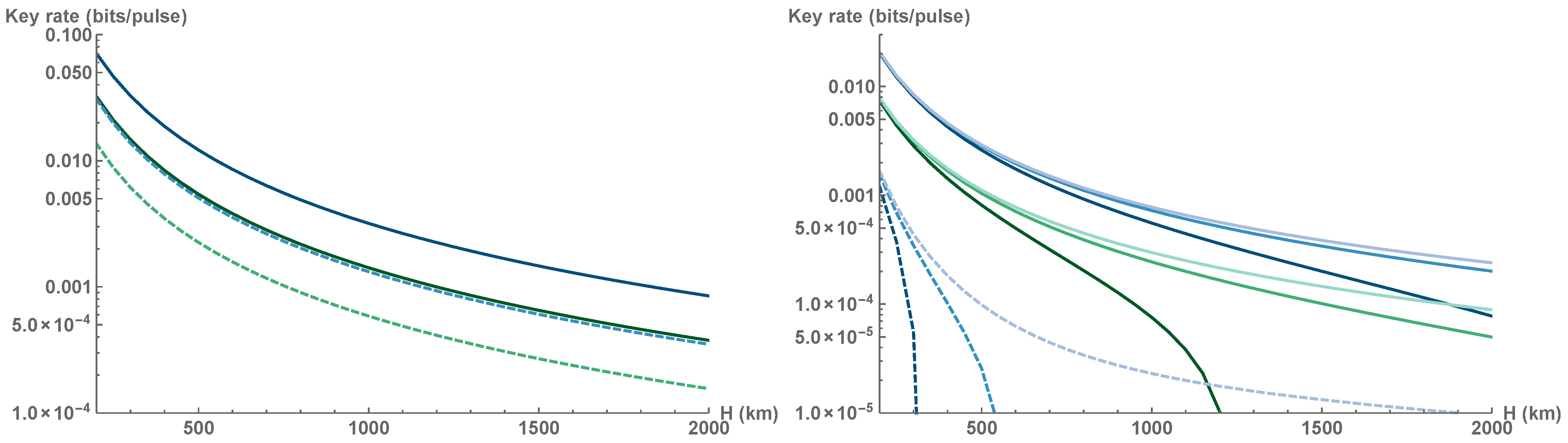
We first assess the security by looking at the impact of individual attacks in asymptotic regime (see
Figure 4 left). In this regime, security can be established for every LEO satellite altitude and feasible squeezing
(SNU) provides a noticeable rate gain. Note that under the individual attacks, the higher levels of squeezing always translate into a higher secure key rate, which is not the case for collective attacks where the transmittance fluctuations limit the applicable values of squeezing [
66] and require active squeezing optimization based on the estimated atmospheric transmittance distribution. The optimization of the latter is a crucial step required for the establishing of secure key rate based on the data generated from a single pass of the satellite.
The performance of the optimized CV QKD protocol under passive collective attacks with trusted noise
is depicted in
Figure 4 (right). The impact of finite-size effects reduces with an increase of the altitude
H as the communication window gets longer and consequently the overall block size
N gets larger. Low altitude satellite downlinks exhibit less mean attenuation but such advantage is partially offset by larger confidence intervals of estimated channel parameters and shorter raw key. While optimization of estimation block-size
can lengthen the key to some extent, increasing the repetition rate of the system is necessary to greatly extend the raw key. Higher repetition rate is especially crucial for the coherent-state protocol that can be implemented at the altitudes above 500 km only with 10 GHz clock rates. Increasing the size of receiving aperture also leads to significant improvement of the secure key rate.
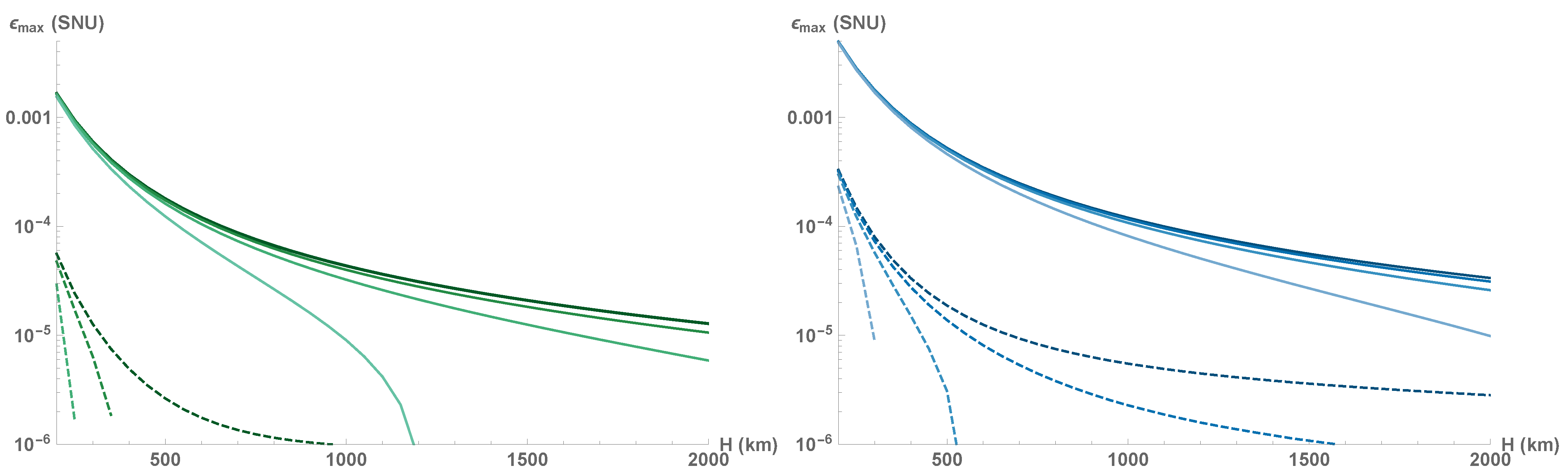
Mean channel attenuation and fading noise, originating from transmittance fluctuations, diminish the tolerance to the channel excess noise, as shown in
Figure 5. Evidently, both protocols are extremely sensitive to excess noise and no secure key can be generated at any orbit altitude if the noise at the output of the squeezed-state protocol is
SNU for
, or if the noise
for
, with orders of magnitude lower values needed for security of the coherent-state protocol (
at
, or
at
). Note that with an increase of satellite orbit altitude, the rate at which the protocol loses noise tolerance decreases. As the optical channel becomes longer it also becomes more stable [
48,
51], i.e., both mean attenuation and fading (viewed as the variance of transmittance fluctuations
) are simultaneously reduced.
While the effect at LEO altitudes is more apparent for the coherent-state protocol, the same dependency can be expected for the squeezed-state protocol at higher altitudes (MEO or GEO). Furthermore, channel stabilization will be more pronounced with less accurate beam-tracking which directly limits the beam-wandering and consequently channel fading.
Clearly, in order to operate under collective attacks with untrusted channel noise, the noise has to be limited to very low values. This can be achieved by proper control of the set-up or precise parameter estimation; however, one can as well reduce the amount of fading noise by dividing the overall single-pass data block into a subset of smaller blocks [
48]. Data clusterization with respect to channel attenuation allows to compensate the effect of channel transmittance fluctuations [
53]; however, such postprocessing can be demanding for satellite-based QKD and is not needed for slow systematic changes of transmittance during the satellite pass. In the current work we therefore adopt simpler albeit similar method by splitting the satellite tracked pass into a set of segments and generating the key for each one. This allows for the achievement of the following lower bound on the overall secure key rate as a weighed sum of the key rates from individual segments:
where
is the raw key length for a given segment
i with number of data points
, so that
,
of data points is used for segment channel estimation, and the weight is determined by the relative size of the segment
, with
N being the overall block size for a given satellite pass. The segments are chosen in accordance with the zenith angle
, so that for
we obtain three segments each containing measurement results at respectively
,
, and
. The finite-size effects are stronger within each segment and transmittance fluctuations are substantial, yet reduced. Three segments are already sufficient to attain an enhanced positive secure key rate and extend the range of secure altitudes, as shown in
Figure 6. For systems with smaller apertures this implies an effective increase of no tracking zone
, as the segment characterized by the longer slant ranges
might not contribute to the overall key.