Secrecy Enhancing Scheme for Spatial Modulation Using Antenna Selection and Artificial Noise
Abstract
1. Introduction
2. PLS Scheme with SM
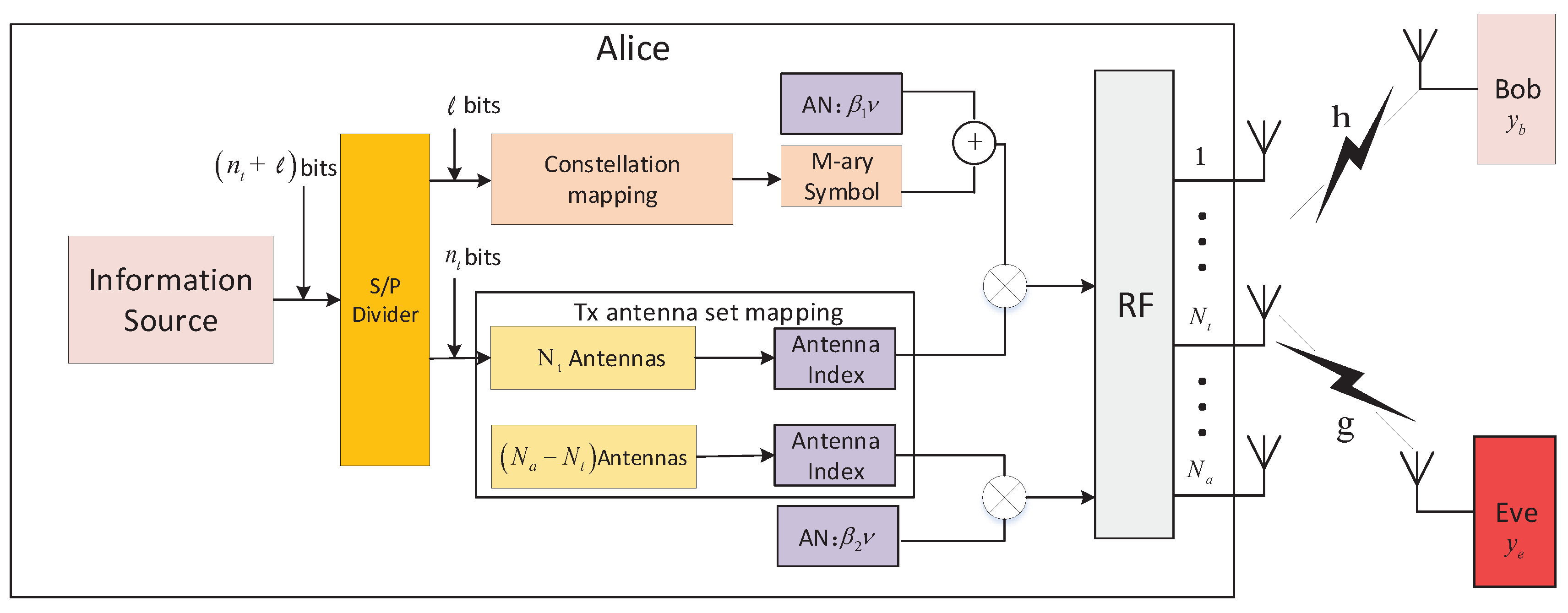
3. Secrecy-Enhancing Spatial Modulation Scheme
3.1. Antenna Selection and Insertion of AN
3.2. Perfect Cancellation of AN
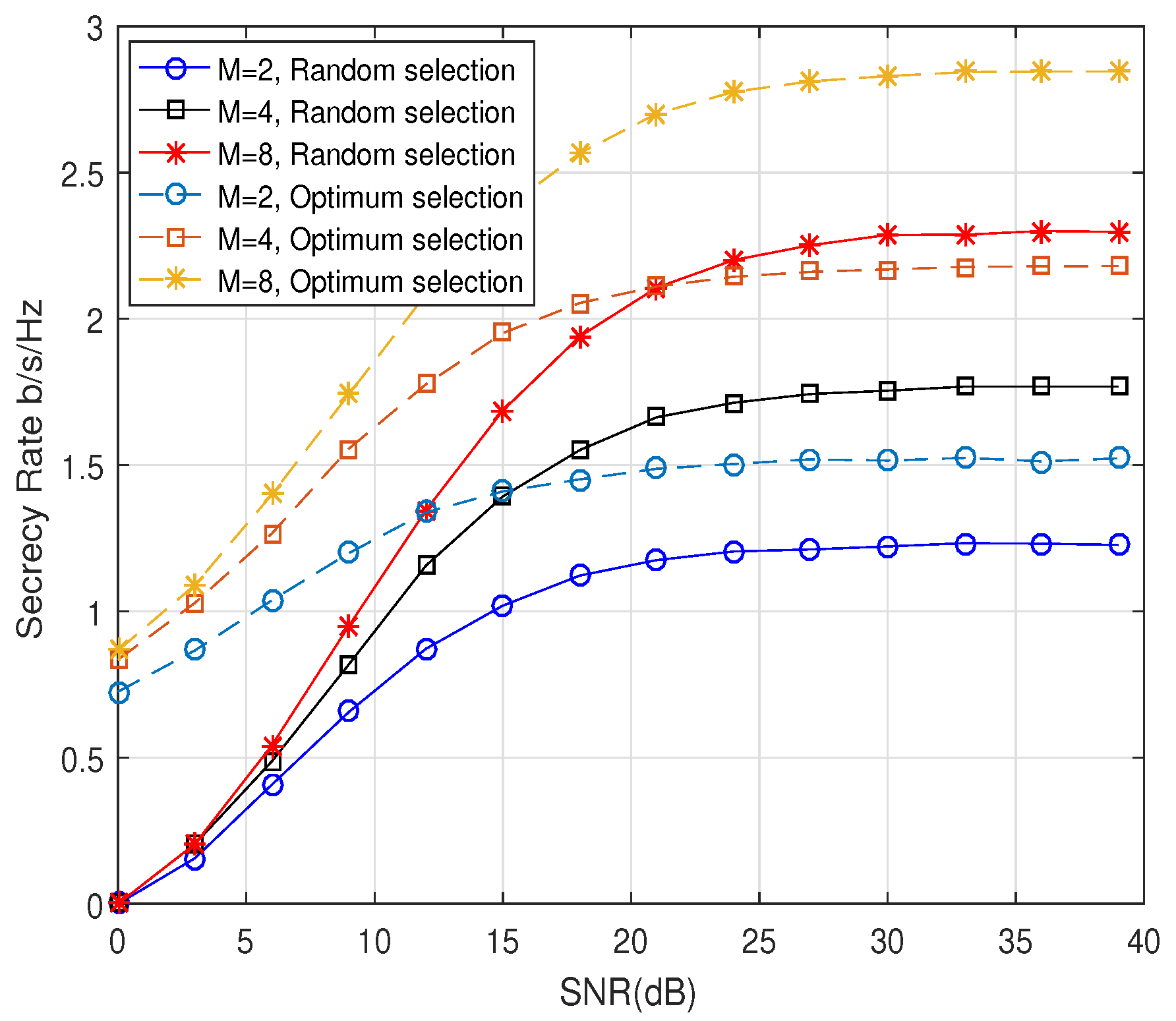
3.3. Optimum Selection of the Transmit Antenna Combination
4. Secrecy Rate Analysis
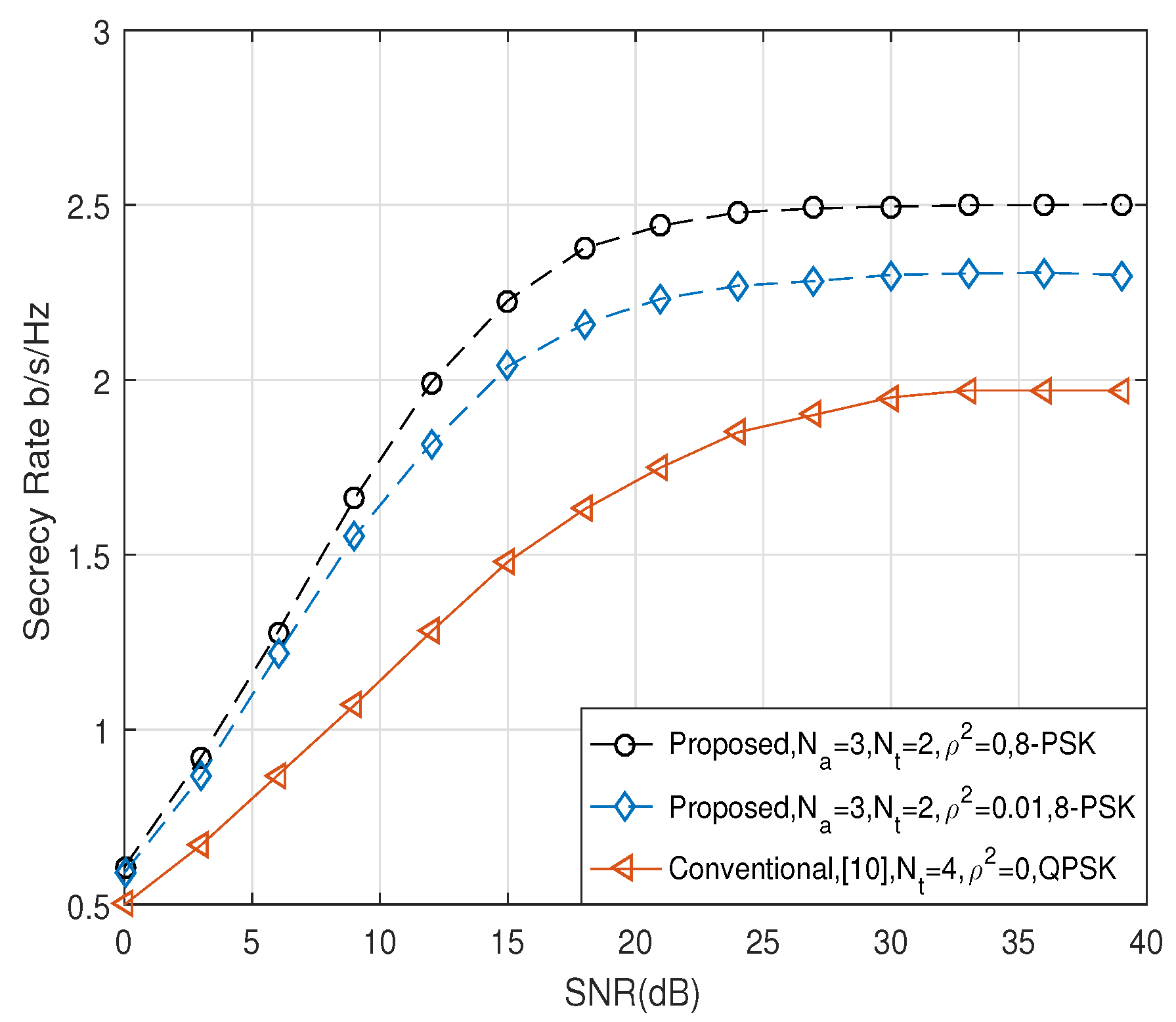
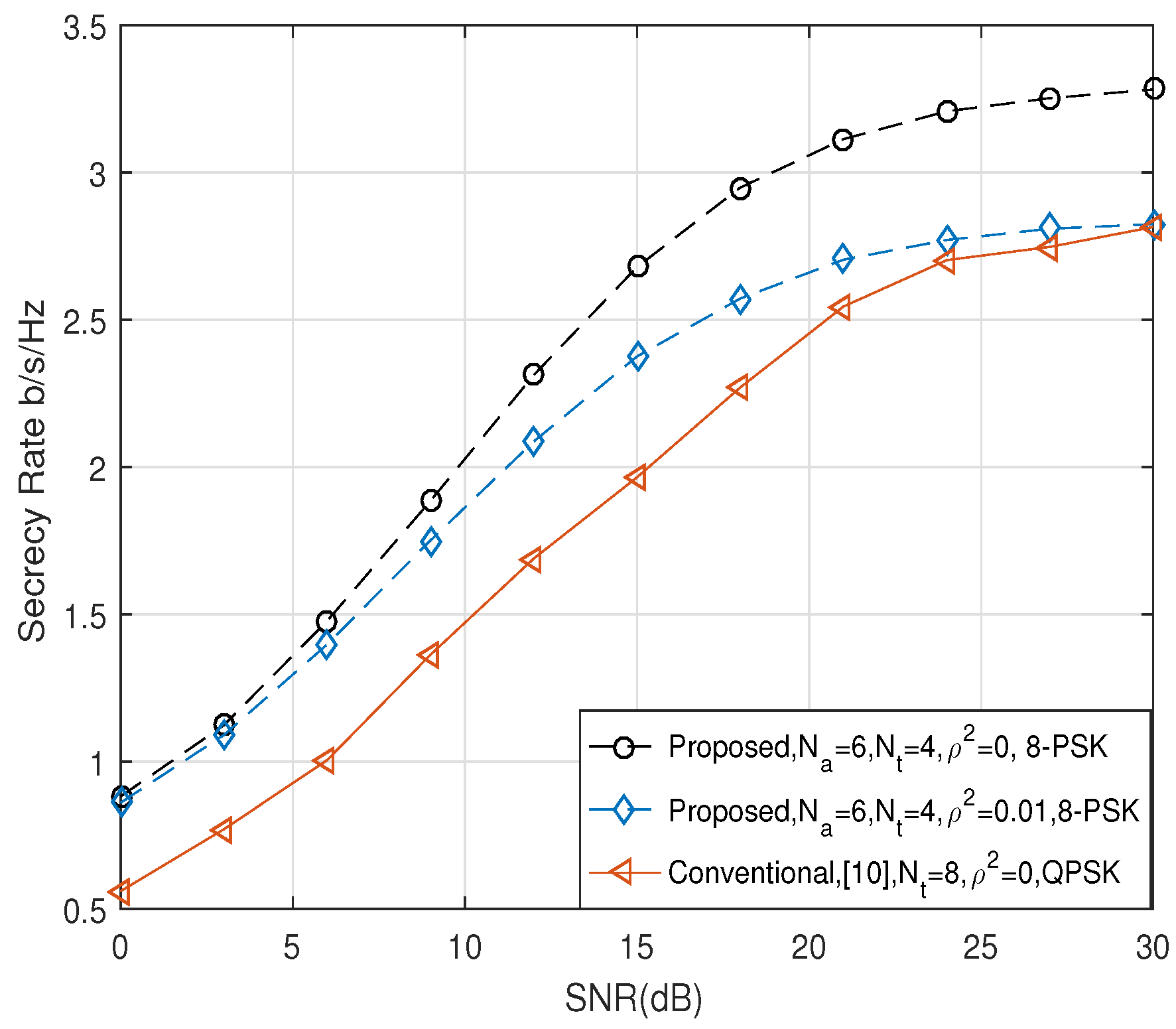
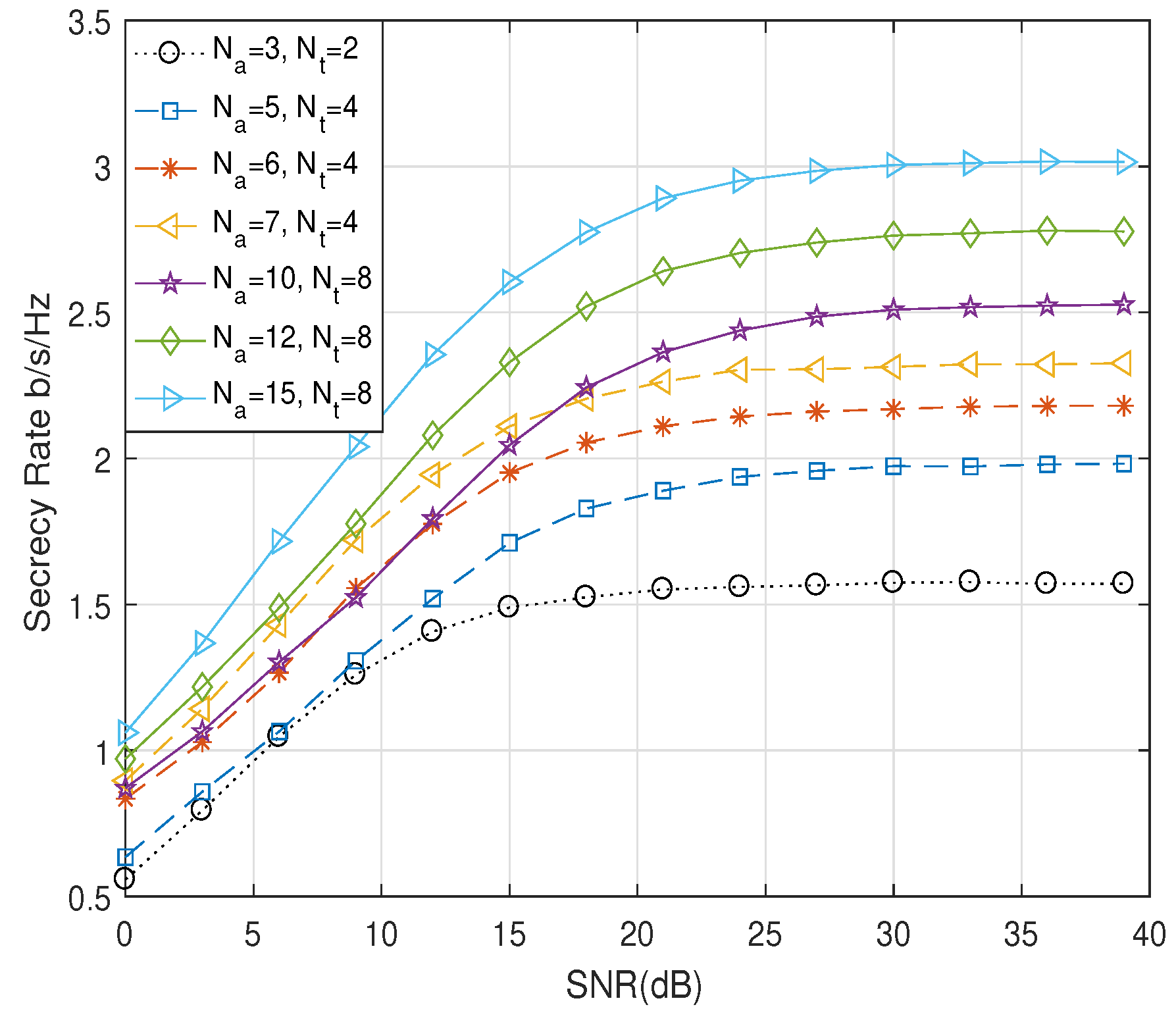
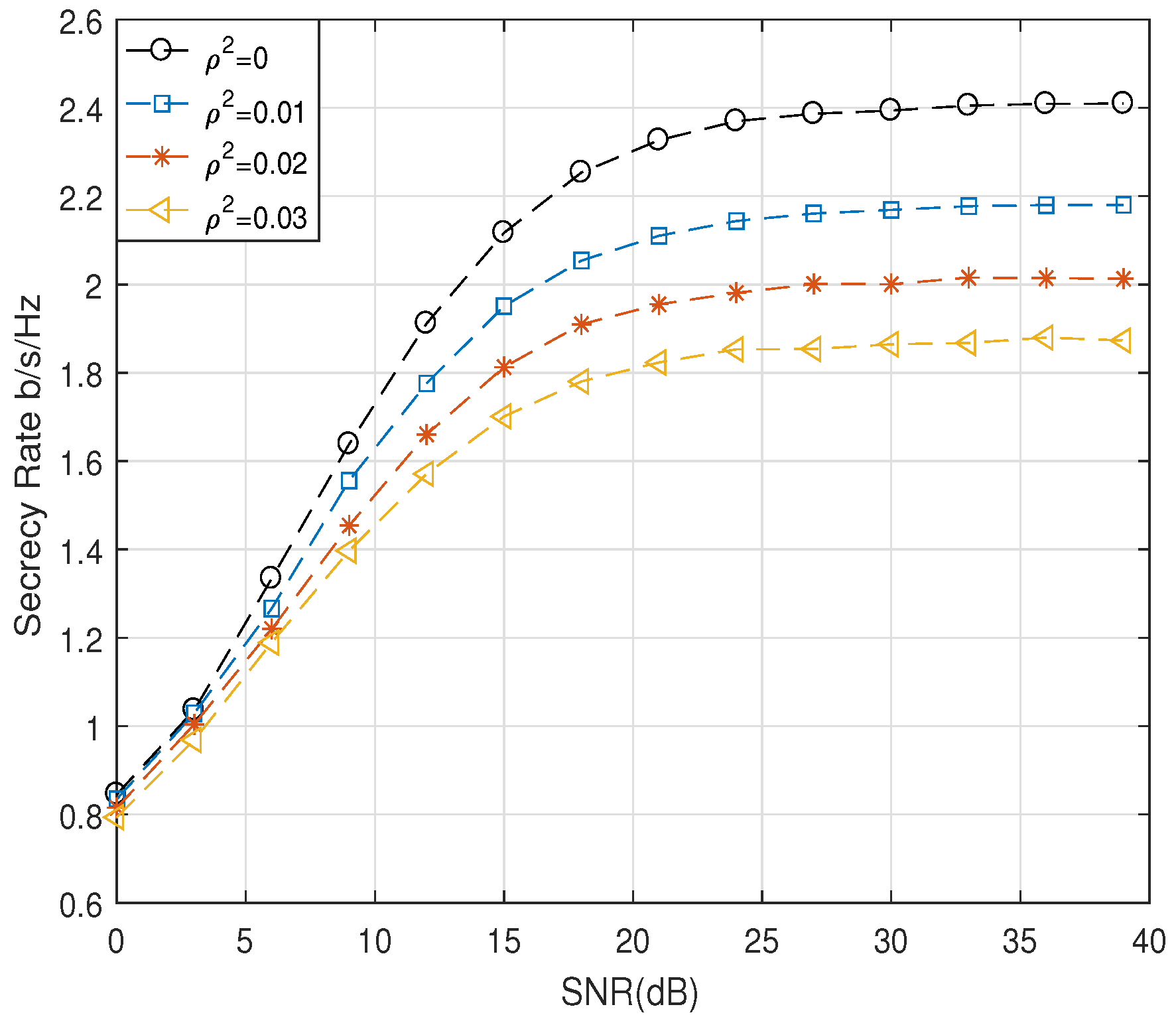
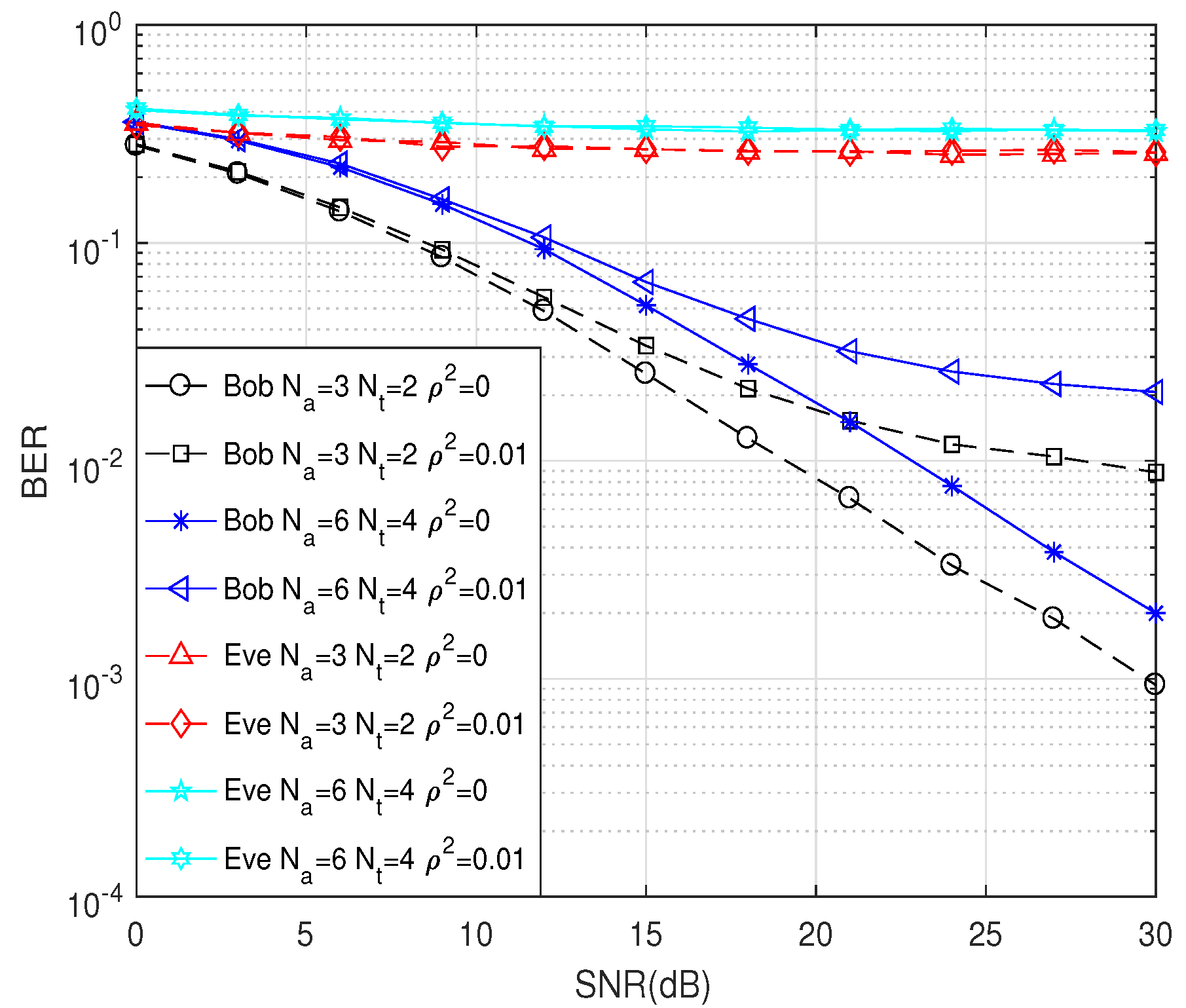
5. Simulation and Numerical Results
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Mesleh, R.Y.; Haas, H.; Sinanovic, S.; Ahn, C.W.; Yun, S.B. Spatial Modulation. IEEE Trans. Veh. Technol. 2008, 57, 2228–2241. [Google Scholar] [CrossRef]
- Renzo, M.D.; Haas, H.; Ghrayeb, A.; Sugiura, S.; Hanzo, L. Spatial Modulation for Generalized MIMO: Challenges, Opportunities, and Implementation. Proc. IEEE 2008, 102, 56–103. [Google Scholar] [CrossRef]
- Basar, E. Index modulation techniques for 5G wireless networks. IEEE Commun. Mag. 2016, 54, 168–175. [Google Scholar] [CrossRef]
- Guo, S.S.; Zhang, H.X.; Zhang, P.; Wu, D.L.; Yuan, D.F. Generalized 3D Constellation Design for Spatial Modulation. IEEE Trans. Commun. 2017, 65, 3316–3327. [Google Scholar]
- Guo, S.S.; Zhang, H.X.; Jin, S.; Zhang, P. Spatial Modulation via 3D Mapping. IEEE Commun. Lett. 2016, 20, 1096–1099. [Google Scholar] [CrossRef]
- Rajashekar, R.; Hari, K.V.S.; Hanzo, L. Antenna Selection in Spatial Modulation Systems. IEEE Commun. Lett. 2013, 17, 521–524. [Google Scholar] [CrossRef]
- Rajashekar, R.; Hari, K.V.S.; Hanzo, L. Quantifying the Transmit Diversity Order of Euclidean Distance Based Antenna Selection in Spatial Modulation. IEEE Signal Process. Lett. 2015, 22, 1434–1437. [Google Scholar] [CrossRef]
- Hamamreh, J.M.; Furqan, H.M.; Arslan, H. Classifications and Applications of Physical Layer Security Techniques for Confidentiality: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2018, 21, 1773–1828. [Google Scholar] [CrossRef]
- Guan, X.R.; Cai, Y.M.; Yang, W.W. On the Secrecy Mutual Information of Spatial Modulation with Finite Alphabet. In Proceedings of the 2012 International Conference on Wireless Communications and Signal Processing (WCSP), Huangshan, China, 25–27 October 2012; pp. 1–4. [Google Scholar]
- Wang, L.; Bashar, S.; Wei, Y.M.; Li, R.G. Secrecy Enhancement Analysis Against Unknown Eavesdropping in Spatial Modulation. IEEE Commun. Lett. 2015, 19, 1351–1354. [Google Scholar] [CrossRef]
- Wang, Y.; Zhang, T.; Yang, W.W.; Guo, J.B.; Liu, Y.X.; Shang, X.H. Secure Transmission for Differential Quadrature Spatial Modulation with Artificial Noise. IEEE Access 2018, 7, 7641–7650. [Google Scholar] [CrossRef]
- Yu, W.C.; Zhang, K.; Shang, P.P.; Jiang, X.Q.; Wen, M.W.; Li, J.; Hai, H. Security Enhancing Spatial Modulation Using Antenna Selection and Artificial Noise Cancellation. In Proceedings of the 2019 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 18–21 February 2019; pp. 105–109. [Google Scholar]
- Jiang, X.Q.; Wen, M.W.; Hai, H.; Li, J.; Kim, S.Y. Secrecy-Enhancing Scheme for Spatial Modulation. IEEE Commun. Lett. 2018, 22, 550–553. [Google Scholar] [CrossRef]
- Wang, X.; Wang, X.; Sun, L. Spatial Modulation aided Physical Layer Security Enhancement for Fading Wiretap Channels. In Proceedings of the 2016 8th International Conference on Wireless Communications & Signal Processing (WCSP), Yangzhou, China, 13–15 October 2016; pp. 1–5. [Google Scholar]
- Shu, F.; Wang, Z.W.; Chen, R.Q.; Wu, Y.P.; Wang, J.Z. Two High-performance Schemes of Transmit Antenna Selection for Secure Spatial Modulation. IEEE Trans. Veh. Technol. 2018, 67, 8969–8973. [Google Scholar] [CrossRef]
- Sadek, M.; Tarighat, A.; Sayed, A.H. Active Antenna Selection in Multiuser MIMO Communications. IEEE Trans. Signal Process. 2007, 55, 1498–1510. [Google Scholar] [CrossRef]
- Lei, H.J.; Ansari, I.S.; Pan, G.F.; Alomair, B.; Alouini, M.S. Secrecy Capacity Analysis Over α-μ Fading Channels. IEEE Commun. Lett. 2017, 21, 1445–1448. [Google Scholar] [CrossRef]

© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shang, P.; Yu, W.; Zhang, K.; Jiang, X.-Q.; Kim, S. Secrecy Enhancing Scheme for Spatial Modulation Using Antenna Selection and Artificial Noise. Entropy 2019, 21, 626. https://doi.org/10.3390/e21070626
Shang P, Yu W, Zhang K, Jiang X-Q, Kim S. Secrecy Enhancing Scheme for Spatial Modulation Using Antenna Selection and Artificial Noise. Entropy. 2019; 21(7):626. https://doi.org/10.3390/e21070626
Chicago/Turabian StyleShang, Pingping, Weicheng Yu, Kai Zhang, Xue-Qin Jiang, and Sooyoung Kim. 2019. "Secrecy Enhancing Scheme for Spatial Modulation Using Antenna Selection and Artificial Noise" Entropy 21, no. 7: 626. https://doi.org/10.3390/e21070626
APA StyleShang, P., Yu, W., Zhang, K., Jiang, X.-Q., & Kim, S. (2019). Secrecy Enhancing Scheme for Spatial Modulation Using Antenna Selection and Artificial Noise. Entropy, 21(7), 626. https://doi.org/10.3390/e21070626






