From Key Encapsulation to Authenticated Group Key Establishment—A Compiler for Post-Quantum Primitives †
Abstract
:1. Introduction
- The compiler made by Bresson et al., C-AMA [3] requires a signature for each message in the original protocol, plus one more for each protocol participant (and according signature verifications).
- Bohli’s framework for robust group key agreement [4] targets two-round protocols, and in each round each participant sends a signed message (and verifies signatures by all other participants).
Our Contribution
2. Preliminaries
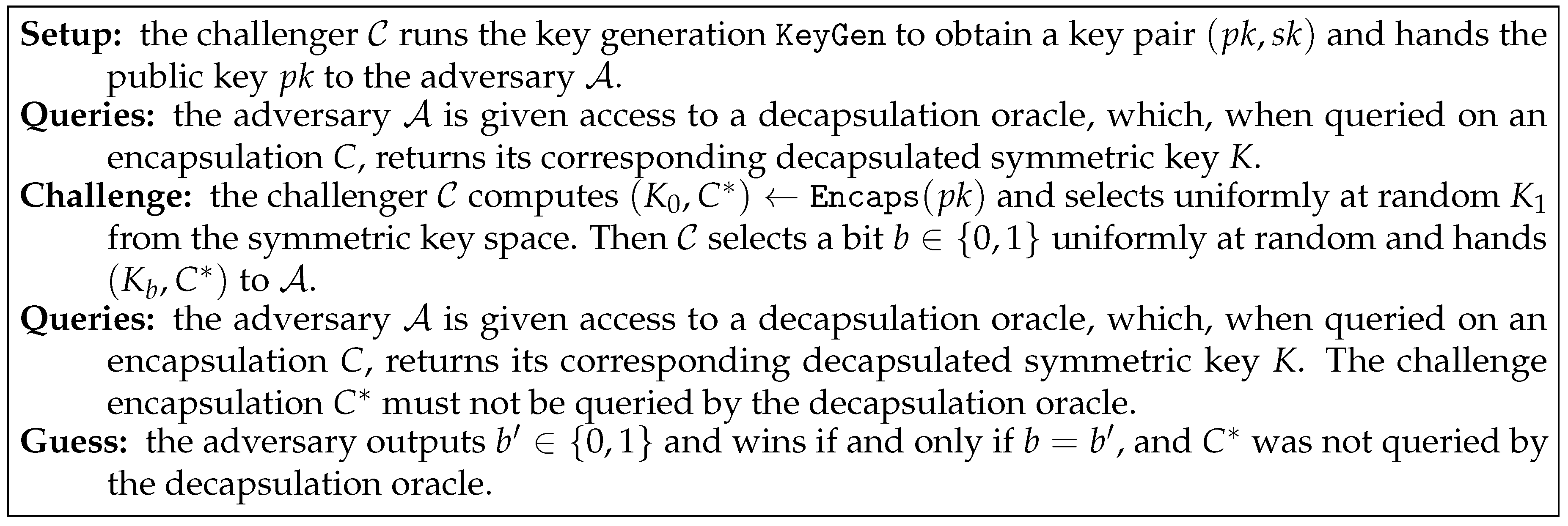
2.1. Key Encapsulation Mechanism
- KeyGen
- is probabilistic. Given the security parameter ℓ, it generates a pair of public and secret keys .
- Encaps
- is probabilistic. Given a public key , it generates a pair where is a symmetric key and C is an encapsulation of this key under the public key .
- Decaps
- is deterministic. Given a secret key and an encapsulation C, this algorithm outputs the symmetric key K or a special error symbol ⊥.
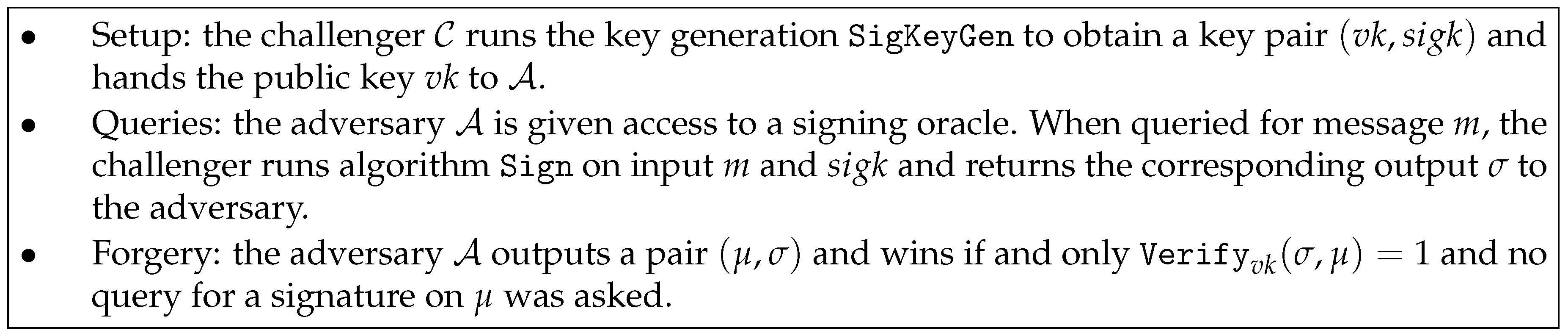
2.2. Signature Scheme
- SigKeyGenis probabilistic. Given the security parameter ℓ, it generates a pair of public and secret keys .
- Signis probabilistic. Given a secret key and a message M it generates a signature σ.
- Verifyis deterministic. Given a public key , a signature σ, and a message M, this algorithm outputs 1 if the signature is valid and 0 otherwise.
3. Security Model and Security Goals
3.1. Protocol Participants
- :
- stores the identities of those users in with which a key is to be established a particular instance aims at establishing a key with, including U (this ensures being partnered is thus a reflexive relation);
- :
- stores a session identifier, i.e., a non-secret public identifier for the session key ;
- :
- stores a distinguished null value and after a successful protocol run holds the session key;
- :
- is set to true if the session key stored in has been accepted;
- :
- keeps state information needed while executing the protocol (e.g., the secret scalars used as ephemeral Diffie–Hellman keys);
- :
- is set to true if this protocol execution has terminated;
- :
- indicates if this instance is used, i.e., currently involved in a protocol execution.
3.2. Initialization
3.3. Adversarial Capabilities and Communication Network
- This oracle can be used in two ways.
- The adversary can initialize a protocol execution; sending the special message to an unused instance with initializes a protocol run among . After such a query, sets , true, and processes the first step of the protocol.
- The message M is sent to instance . The oracle returns the protocol message output by after receiving M.
- returns the stored session key if true and a null value otherwise.
- for a user this query returns U’s long-term secret key .
- all users accept, i.e., ;
- all users obtain the same session identifier, i.e., ;
- all users accept the same session key, i.e., associated with the same session identifier ;
- all communication partners are specified as desired communication partner, i.e., .
- For some a query was executed before a query of the form has taken place where .
- A query with and being partnered occurred.
4. Proposed Construction
- Whenever a query is made by , generates the keys for the signature and returns as answer to .
- To answer a query for Round 2 involving , uses the challenge encapsulation . The rest of the answers are generated as in a real execution of the protocol.
- To answer an query by , our adversary modifies the messages as described for the simulation of the oracle.
- A query by is answered in a similar way as a or query. Notice that a query cannot be made on t or any partnered instance. To answer any other query uses the decapsulation oracle of its IND-CCA game.
- Finally, to answer a query, a bit is chosen by when starting the simulation. will return the key received from the KEM challenger to .
4.1. Remark
4.2. Instantiation
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Katz, J.; Yung, M. Scalable Protocols for Authenticated Group Key Exchange. J. Cryptol. 2007, 20, 85–113. [Google Scholar] [CrossRef]
- Apon, D.; Dachman-Soled, D.; Gong, H.; Katz, J. Constant-Round Group Key Exchange from the Ring-LWE Assumption. In Proceedings of the 10th International Conference on Post-Quantum Cryptography (PQCrypto 2019), Chongqing, China, 8–10 May 2019; pp. 189–205. [Google Scholar]
- Bresson, E.; Manulis, M.; Schwenk, J. On Security Models and Compilers for Group Key Exchange Protocols. In Proceedings of the Second International Workshop on Security (IWSEC), Nara, Japan, 29–31 October 2007; pp. 292–307. [Google Scholar] [CrossRef]
- Bohli, J. A Framework for Robust Group Key Agreement. In Proceedings of the International Conference on Computational Science and Its Applications—ICCSA 2006, Glasgow, UK, 8–11 May 2006; pp. 355–364. [Google Scholar] [CrossRef]
- Burmester, M.; Desmedt, Y. A Secure and Efficient Conference Key Distribution System (Extended Abstract). In Proceedings of the Workshop on the Theory and Application of Cryptographic Techniques (UROCRYPT ’94), Perugia, Italy, 9–12 May 1994; pp. 275–286. [Google Scholar] [CrossRef]
- Shor, P.W. Algorithms for Quantum Computation: Discrete Logarithms and Factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar] [CrossRef]
- Bundesamt für Sicherheit in der Informationstechnik. Studie: Entwicklungsstand Quantencomputer V.1.1. 2019. Available online: https://www.bsi.bund.de/DE/Publikationen/Studien/Quantencomputer/quantencomputer.html (accessed on 28 November 2019).
- National Academies of Sciences, Engineering, and Medicine. Quantum Computing: Progress and Prospects; The National Academies Press: Washington, DC, USA, 2019. [Google Scholar] [CrossRef]
- Bernstein, D.J.; Dobraunig, C.; Eichlseder, M.; Fluhrer, S.; Gazdag, S.L.; Hülsing, A.; Kampanakis, P.; Kölbl, S.; Lange, T.; Lauridsen, M.M.; et al. SPHINCS+. Submission to the NIST Post-Quantum Project. 2017. Available online: https://sphincs.org/data/sphincs+-submission-nist.zip (accessed on 28 November 2019).
- Tang, Q.; Mitchell, C.J. Efficient Compilers for Authenticated Group Key Exchange. In Proceedings of the International Conference on Computational Intelligence and Security (CIS), Xi’an, China, 15–19 December 2005; pp. 192–197. [Google Scholar] [CrossRef]
- Post-Quantum Cryptography Standardization. 2019. Available online: https://csrc.nist.gov/Projects/Post-Quantum-Cryptography/Post-Quantum-Cryptography-Standardization (accessed on 28 November 2009).
- Shoup, V. Using hash functions as a hedge against chosen ciphertext attack. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Bruges, Belgium, 14–18 May 2000; pp. 275–288. [Google Scholar]
- Bresson, E.; Chevassut, O.; Pointcheval, D.; Quisquater, J. Provably authenticated group Diffie-Hellman key exchange. In Proceedings of the 8th ACM Conference on Computer and Communications Security (CCS 2001), Philadelphia, PA, USA, 6–8 November 2001; pp. 255–264. [Google Scholar] [CrossRef]
- Barreto, P.S.L.M.; Gueron, S.; Güneysu, T.; Misoczki, R.; Persichetti, E.; Sendrier, N.; Tillich, J. CAKE: Code-Based Algorithm for Key Encapsulation. In Proceedings of the 16th IMA International Conference on Cryptography and Coding (IMACC), Oxford, UK, 12–14 December 2017; pp. 207–226. [Google Scholar] [CrossRef]
- Banegas, G.; Barreto, P.; Boidje, B.O.; Cayrel, P.; Dione, G.N.; Gaj, K.; Gueye, C.T.; Haeussler, R.; Klamti, J.B.; Ndiaye, O.; et al. DAGS: Key encapsulation using dyadic GS codes. J. Math. Cryptol. 2018, 12, 221–239. [Google Scholar] [CrossRef]
- Bos, J.W.; Costello, C.; Ducas, L.; Mironov, I.; Naehrig, M.; Nikolaenko, V.; Raghunathan, A.; Stebila, D. Frodo: Take off the Ring! Practical, Quantum-Secure Key Exchange from LWE. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–29 October 2016; pp. 1006–1018. [Google Scholar] [CrossRef]
- Bos, J.W.; Ducas, L.; Kiltz, E.; Lepoint, T.; Lyubashevsky, V.; Schanck, J.M.; Schwabe, P.; Seiler, G.; Stehlé, D. CRYSTALS—Kyber: A CCA-Secure Module-Lattice-Based KEM. In Proceedings of the 2018 IEEE European Symposium on Security and Privacy (EuroS&P 2018), London, UK, 24–26 April 2018; pp. 353–367. [Google Scholar] [CrossRef]
- Ducas, L.; Kiltz, E.; Lepoint, T.; Lyubashevsky, V.; Schwabe, P.; Seiler, G.; Stehlé, D. CRYSTALS-Dilithium: A Lattice-Based Digital Signature Scheme. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2018, 2018, 238–268. [Google Scholar] [CrossRef]

© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Persichetti, E.; Steinwandt, R.; Suárez Corona, A. From Key Encapsulation to Authenticated Group Key Establishment—A Compiler for Post-Quantum Primitives †. Entropy 2019, 21, 1183. https://doi.org/10.3390/e21121183
Persichetti E, Steinwandt R, Suárez Corona A. From Key Encapsulation to Authenticated Group Key Establishment—A Compiler for Post-Quantum Primitives †. Entropy. 2019; 21(12):1183. https://doi.org/10.3390/e21121183
Chicago/Turabian StylePersichetti, Edoardo, Rainer Steinwandt, and Adriana Suárez Corona. 2019. "From Key Encapsulation to Authenticated Group Key Establishment—A Compiler for Post-Quantum Primitives †" Entropy 21, no. 12: 1183. https://doi.org/10.3390/e21121183
APA StylePersichetti, E., Steinwandt, R., & Suárez Corona, A. (2019). From Key Encapsulation to Authenticated Group Key Establishment—A Compiler for Post-Quantum Primitives †. Entropy, 21(12), 1183. https://doi.org/10.3390/e21121183





