A New Image Encryption Algorithm Based on Chaos and Secure Hash SHA-256
Abstract
:1. Introduction
2. Preliminaries
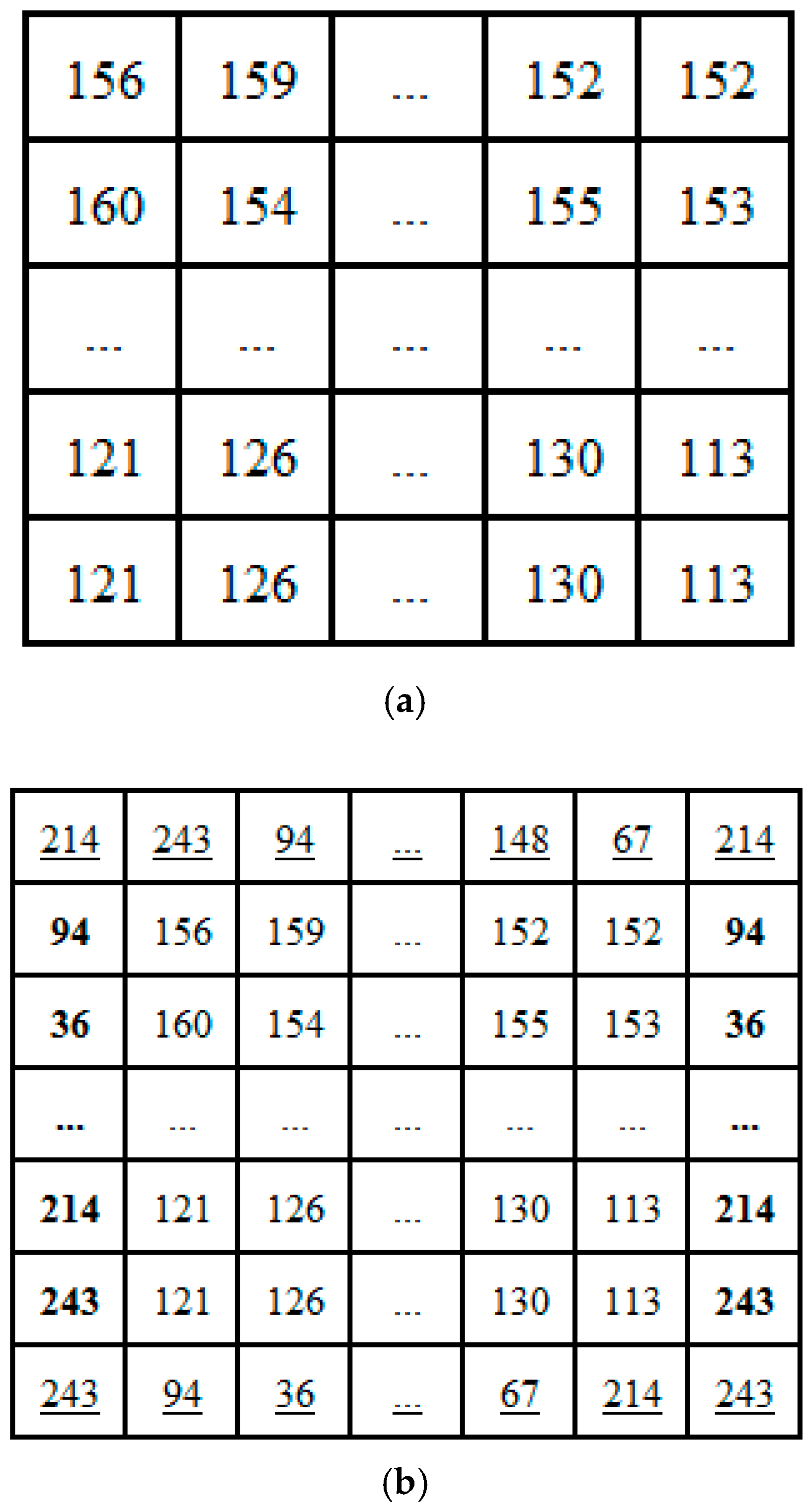
2.1. Adding Surrounding Pixels
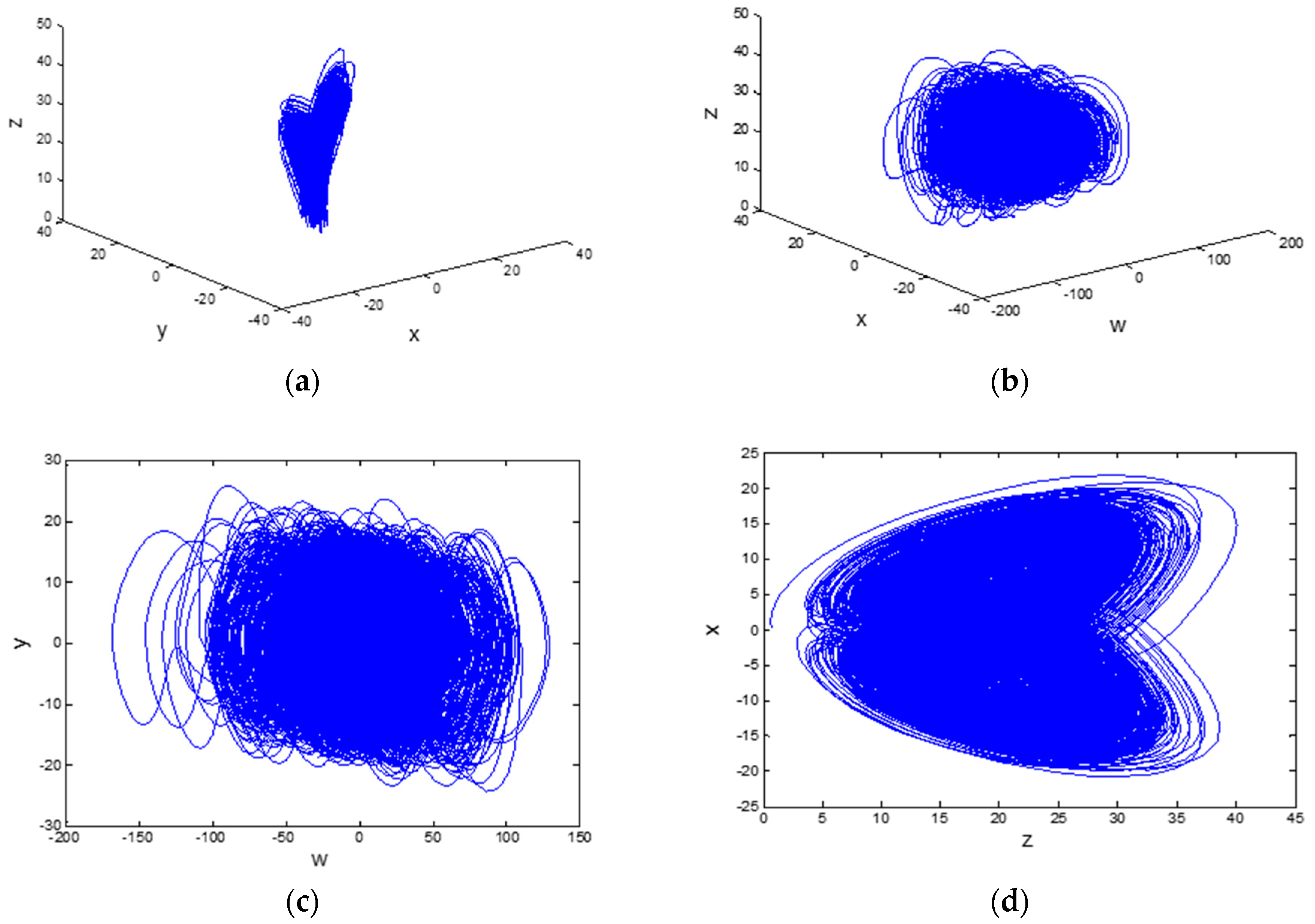
2.2. Hyper-Chaotic System and Chebyshev Map
2.3. The Generation of Random Sequences of the Encryption System
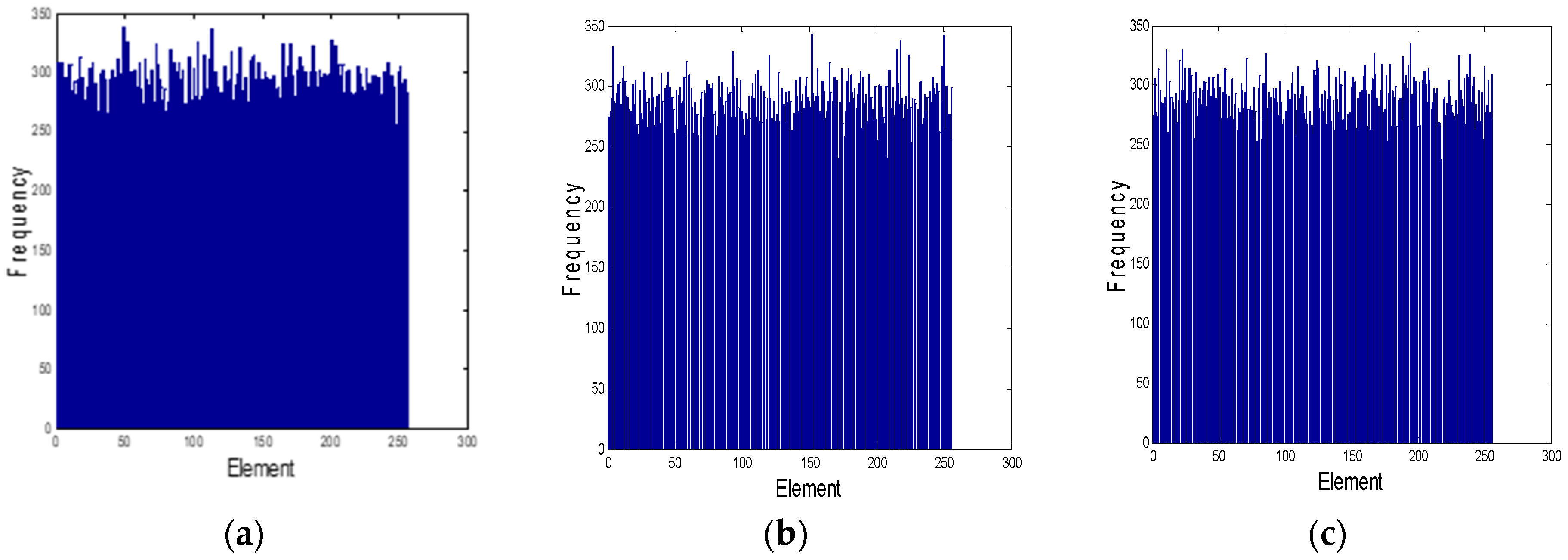
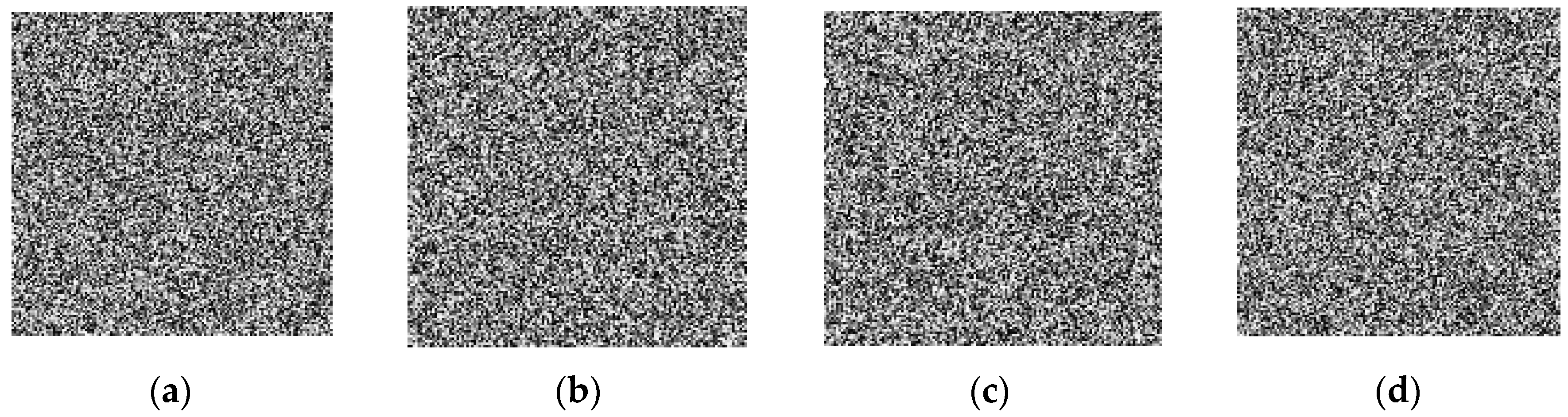
2.4. Statistical Test Analysis of the Three CPRNG Sequences S, V and T
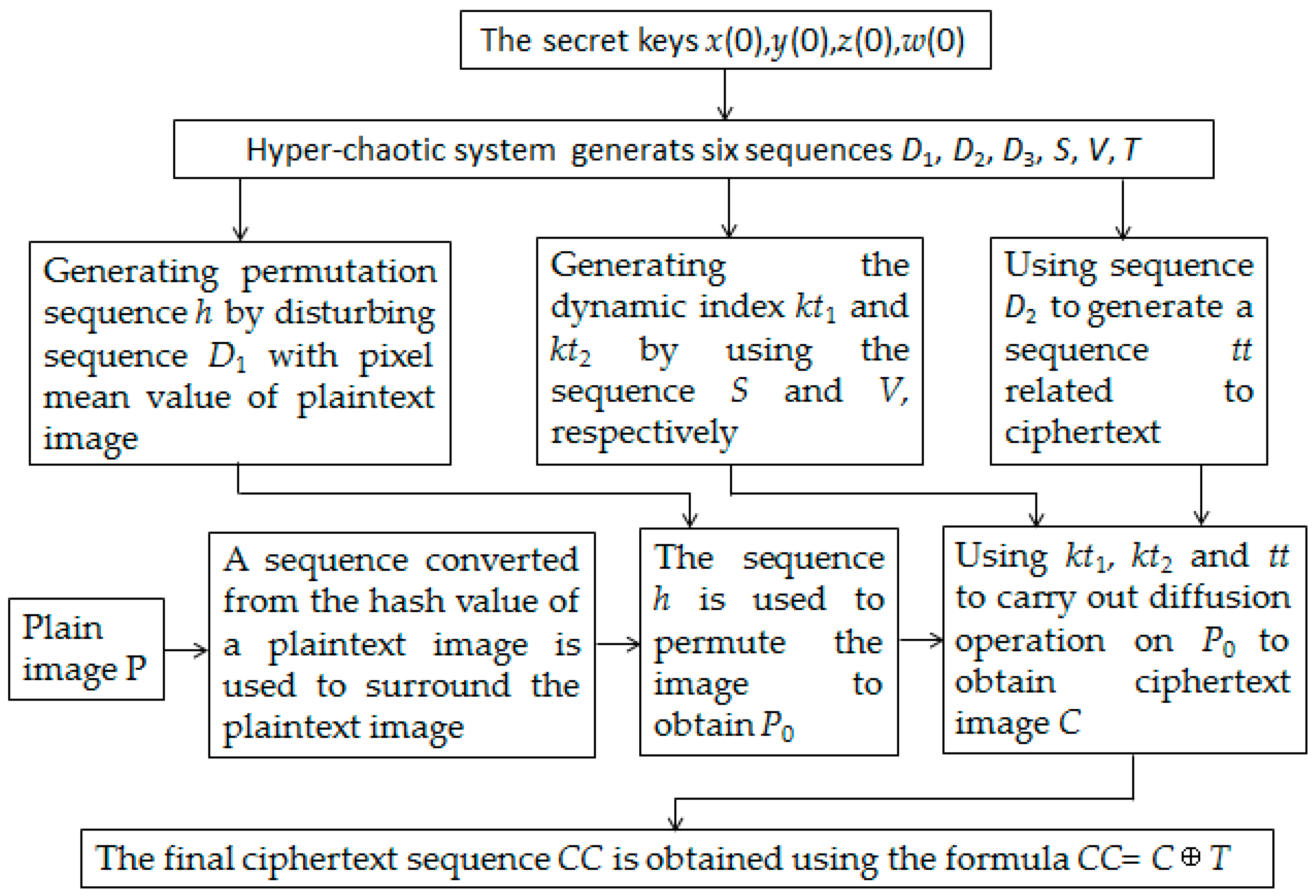
3. Architecture of the Proposed Cryptosystem
3.1. Encryption Algorithm
3.2. Decryption Algorithm
3.3. Application of the Algorithm for Color Images
3.4. The Advantages in the New Encryption Scheme
- (1)
- The method of surrounding pixels generated by the SHA-256 hash value of the plaintext image is adopted, which can enhance the ability of the encryption system to resist chosen plaintext attacks. In general, selecting an image of all the same pixel values to chosen plaintext attack, which can eliminate the global scrambling effect. But in the new encryption algorithms, even encrypt an image of all the same pixel values, because the first step is to add surrounding pixels to the image, then the image is not an image of all the same pixel values. On the other hand, the hash value of the image is not needed in decryption, which reduces the difficulty of key management.
- (2)
- In the permutation process, by adding a perturbation g (g = sum(P0)/(256 × l)) to the chaotic sequence D1, the permutation sequence h is generated by Equation (10). Therefore, h is related to plaintext, which can resist the chosen plaintext attack. At the same time, g is not part of the decryption key, which reduces the difficulty of key management.
- (3)
- From Equation (16), it is known that the sequence tt is related to the transition cyphertext c, so the sequence tt is different when encrypting different images, which further strengthens the ability of the encryption system to resist chosen plaintext attack.
- (4)
- From the cyphertext feedback mechanism of Equation (17), It can be seen that our encryption algorithm is sensitive to plaintext.
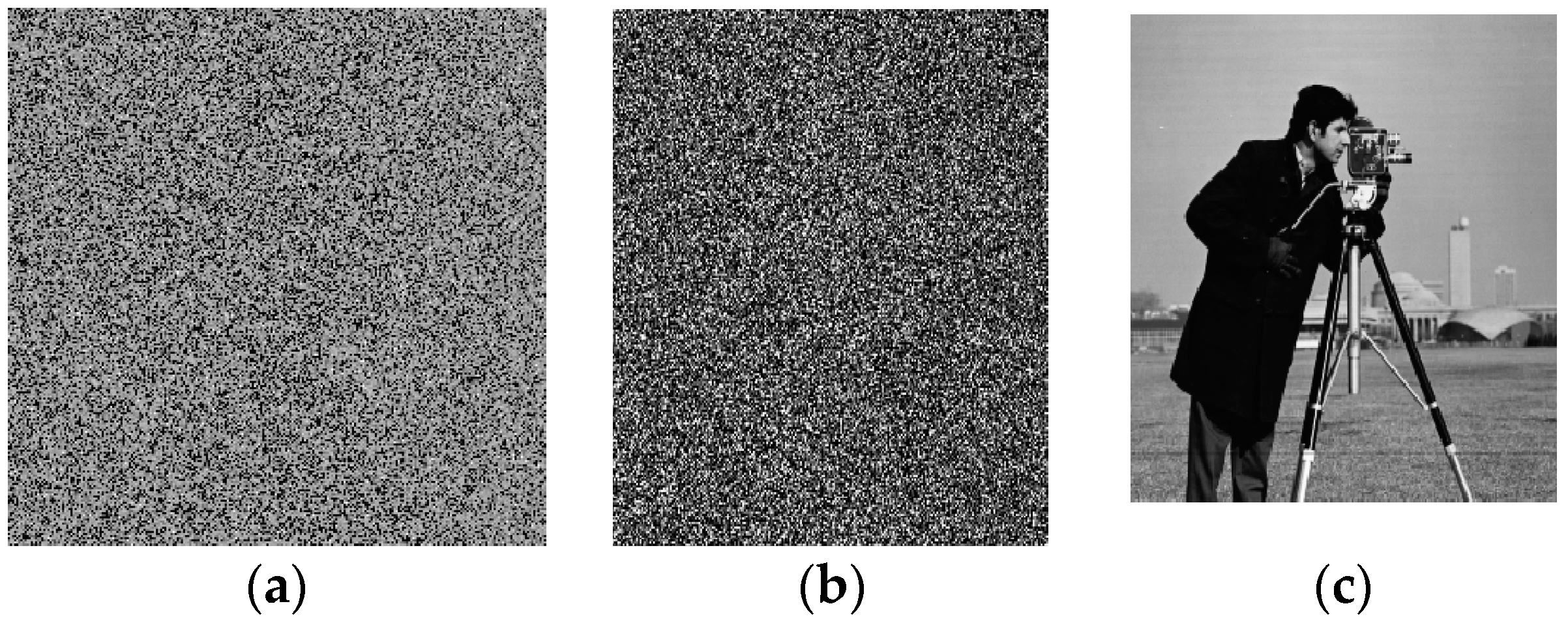
4. Simulation Results
5. Security Analysis
5.1. Key Space
5.2. Key Sensitivity
5.3. Plaintext Sensitivity
5.4. Statistical Analysis
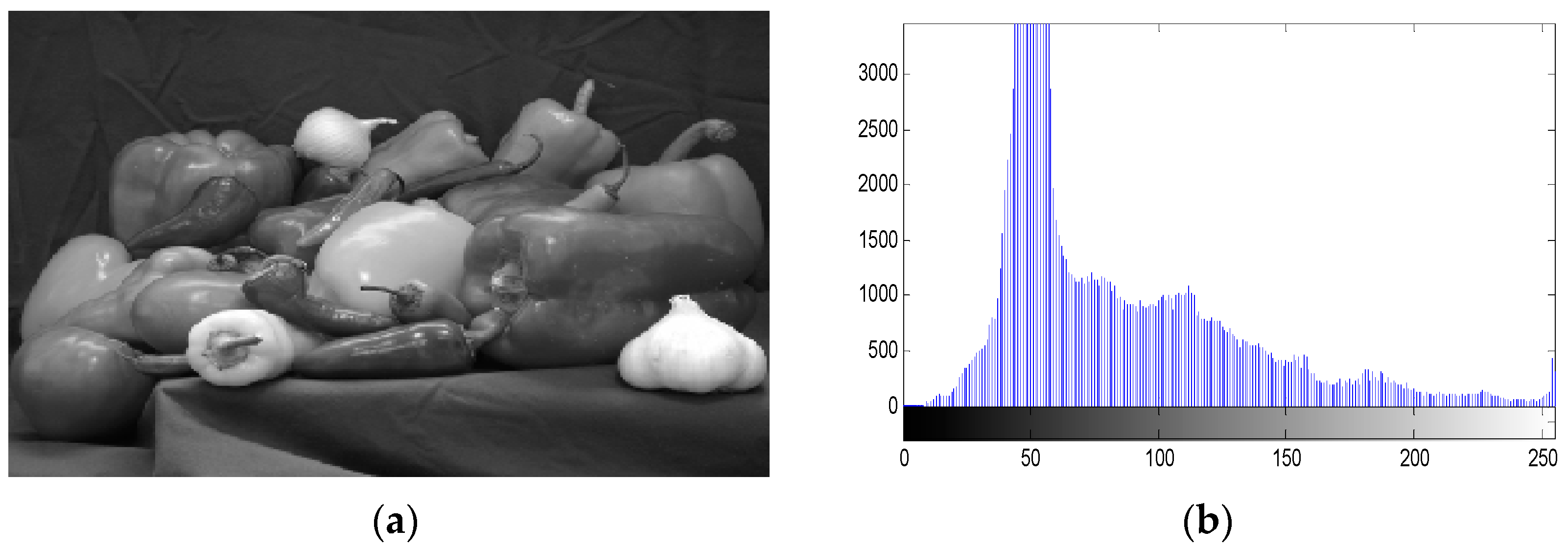
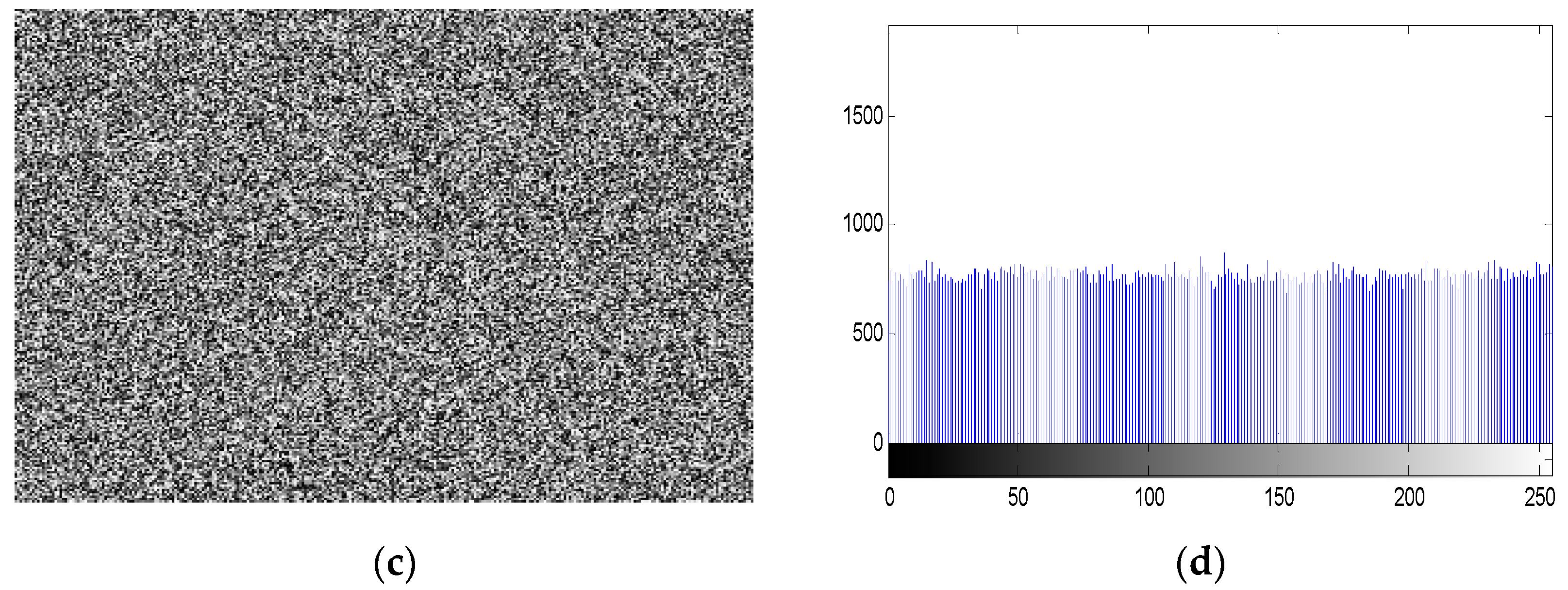
5.4.1. Statistical Histogram Analysis
5.4.2. Chi-Square Test
5.4.3. Information Entropy
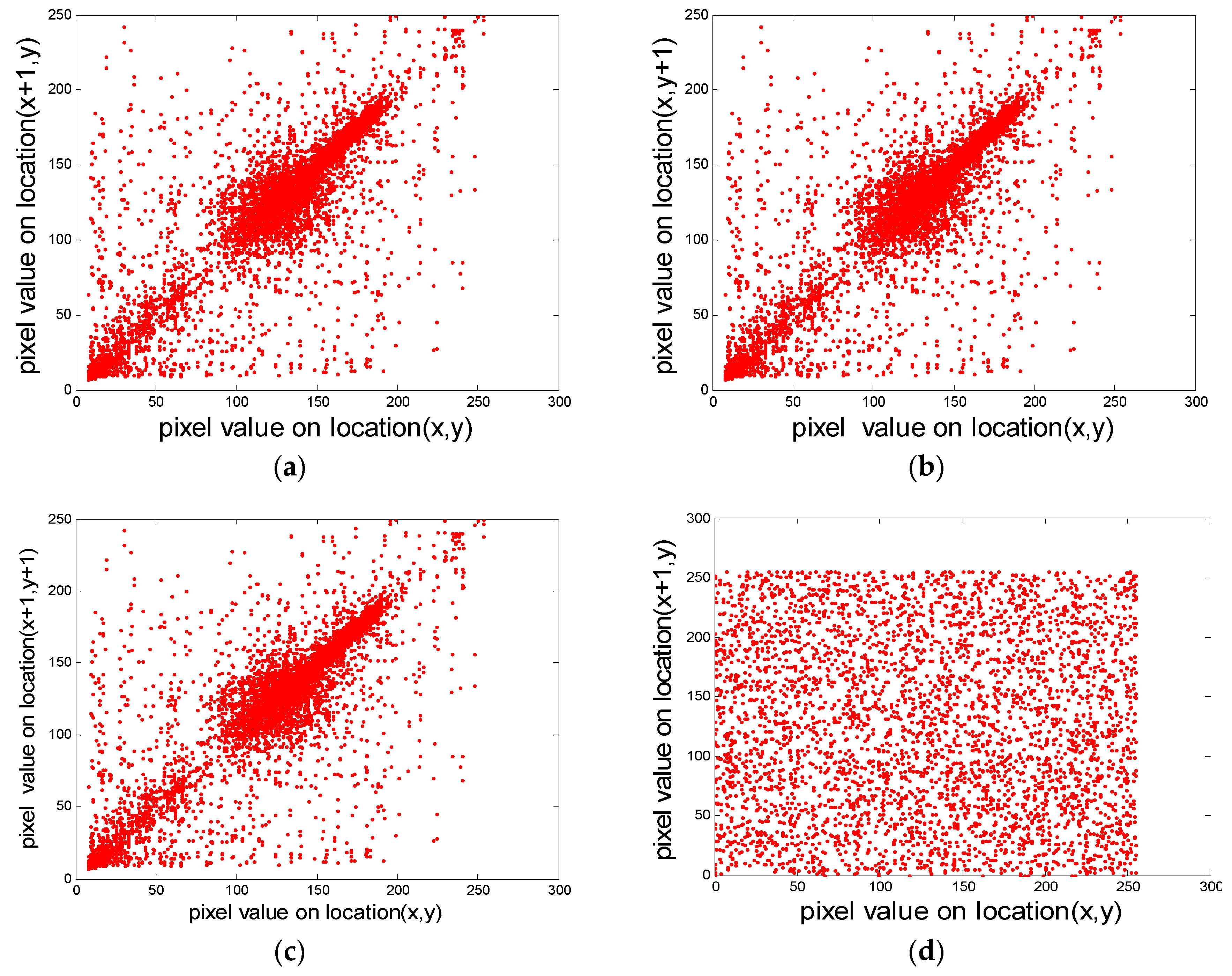
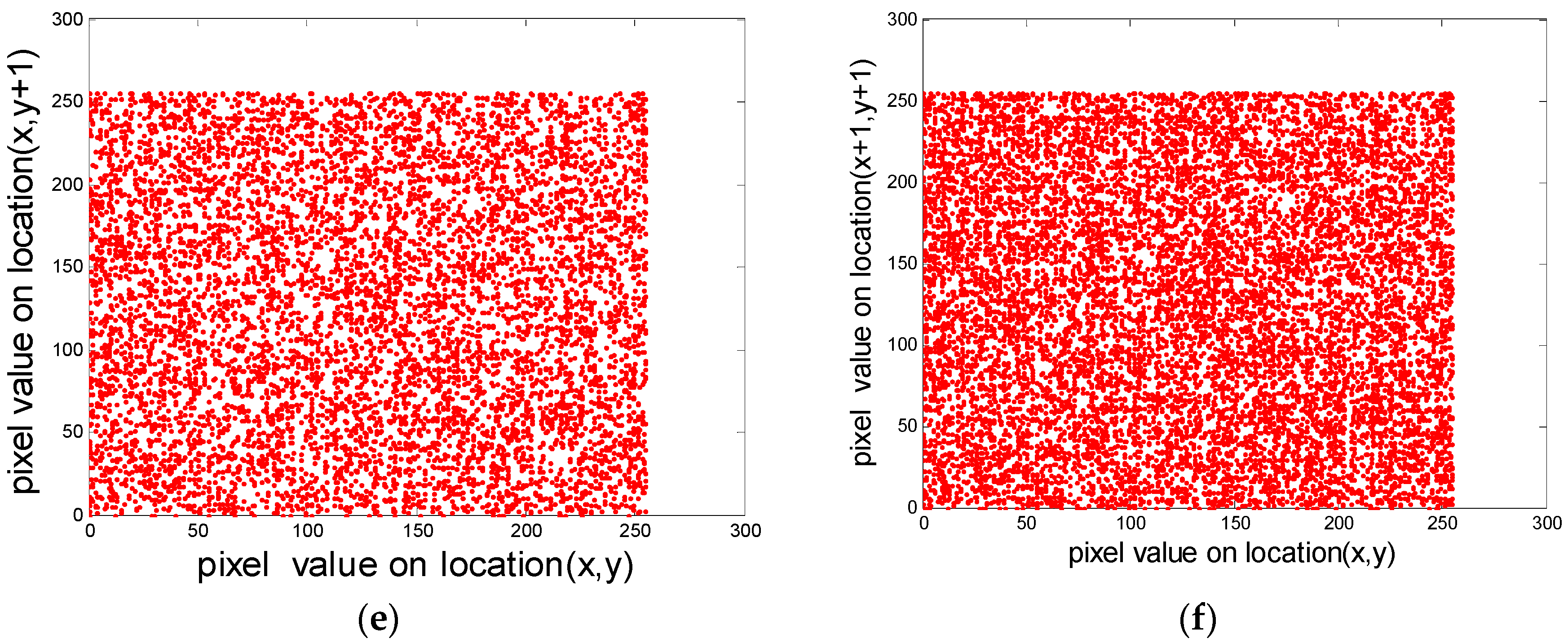
5.4.4. Pixel Correlation Analysis
5.5. Computational Speed Analysis
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Alvarez, G.; Li, S. Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurc. Chaos 2006, 16, 2129–2151. [Google Scholar] [CrossRef]
- Fridrich, J. Symmetric ciphers based on two-dimensional chaotic maps. Int. J. Bifurc. Chaos 1998, 8, 1259–1284. [Google Scholar] [CrossRef]
- Hsiao, H.-I.; Lee, J. Color image encryption using chaotic nonlinear adaptive filter. Signal Process. 2015, 117, 281–309. [Google Scholar] [CrossRef]
- Mirzaei, O.; Yaghoobi, M.; Irani, H. A new image encryption method: Parallel sub-image encryption with hyper chaos. Nonlinear Dyn. 2012, 67, 557–566. [Google Scholar] [CrossRef]
- Wu, Y.; Zhou, Y.; Agaian, S.; Noonan, J.P. A symmetric image cipher using wave perturbations. Signal Process. 2014, 102, 122–131. [Google Scholar] [CrossRef]
- Patidar, V.; Pareek, N.K.; Purohit, G.; Sud, K.K. Modified substitution-diffusion image cipher using chaotic standard and logistic maps. Commun. Nonlinear Sci. Numer. Simul. 2010, 15, 2755–2765. [Google Scholar] [CrossRef]
- Zhu, C. A novel image encryption scheme based on improved hyperchaotic sequences. Opt. Commun. 2012, 285, 29–37. [Google Scholar] [CrossRef]
- Zhang, Y.; Xiao, D.; Shu, Y.; Li, J. A novel image encryption scheme based on a linear hyperbolic chaotic system of partial differential equations. Signal Process. Image Commun. 2013, 28, 292–300. [Google Scholar] [CrossRef]
- Zhang, W.; Wong, K.-W.; Yu, H.; Zhu, Z.-L. A symmetric color image encryption algorithm using the intrinsic features of bit distributions. Commun. Nonlinear Sci. Numer. Simul. 2013, 18, 584–600. [Google Scholar] [CrossRef]
- Zhang, Y.; Xiao, D. An image encryption scheme based on rotation matrix bit-level permutation and block diffusion. Commun. Nonlinear Sci. Numer. Simul. 2014, 19, 74–82. [Google Scholar] [CrossRef]
- Chai, X. An image encryption algorithm based on bit level brownian motion and new chaotic systems. Multimed. Tools Appl. 2017, 76, 1159–1175. [Google Scholar] [CrossRef]
- Zhu, C.-X.; Sun, K.-H. Cryptanalysis and improvement of a class of hyperchaos based image encryption algorithms. Acta Phys. Sin. 2012, 61, 120503. [Google Scholar] [CrossRef]
- Ozkaynak, F.; Yavuz, S. Analysis and improvement of a novel image fusion encryption algorithm based on DNA sequence operation and hyper-chaotic system. Nonlinear Dyn. 2014, 78, 1311–1320. [Google Scholar] [CrossRef]
- Zhu, C.; Xu, S.; Hu, Y.; Sun, K. Breaking a novel image encryption scheme based on brownian motion and pwlcm chaotic system. Nonlinear Dyn. 2015, 79, 1511–1518. [Google Scholar] [CrossRef]
- Yap, W.-S.; Phan, R.C.W.; Yau, W.-C.; Heng, S.-H. Cryptanalysis of a new image alternate encryption algorithm based on chaotic map. Nonlinear Dyn. 2015, 80, 1483–1491. [Google Scholar] [CrossRef]
- Chen, L.; Ma, B.; Zhao, X.; Wang, S. Differential cryptanalysis of a novel image encryption algorithm based on chaos and line map. Nonlinear Dyn. 2016, 87, 1797–1807. [Google Scholar] [CrossRef]
- Li, C.; Lin, D.; Lu, J. Cryptanalyzing an image-scrambling encryption algorithm of pixel bits. IEEE Multimed. 2017, 24, 64–71. [Google Scholar] [CrossRef]
- Zhu, C.; Sun, K. Cryptanalyzing and improving a novel color image encryption algorithm using RT-enhanced chaotic tent maps. IEEE Access 2018, 6, 18759–18770. [Google Scholar] [CrossRef]
- Norouzi, B.; Mirzakuchaki, S.; Seyedzadeh, S.; Mosavi, M.R. A simple, sensitive and secure image encryption algorithm based on hyper-chaotic system with only one round diffusion process. Multimed. Tools Appl. 2014, 71, 1469–1497. [Google Scholar] [CrossRef]
- Diab, H.; El-semary, A.M. Secure image cryptosystem with unique key streams via hyper-chaotic system. Signal Process. 2018, 142, 53–68. [Google Scholar] [CrossRef]
- Akhavan, A.; Samsudin, A.; Akhshani, A. Cryptanalysis of an image encryption algorithm based on DNA encoding. Opt. Laser Technol. 2017, 95, 94–99. [Google Scholar] [CrossRef]
- Zhang, G.; Liu, Q. A novel image encryption method based on total shuffling scheme. Opt. Commun. 2011, 284, 2775–2780. [Google Scholar] [CrossRef]
- Zhu, C.; Liao, C.; Deng, X. Breaking and improving an image encryption scheme based on total shuffling scheme. Nonlinear Dyn. 2013, 71, 25–34. [Google Scholar] [CrossRef]
- Wang, X.; Zhu, X.; Wu, X.; Zhang, Y. Image encryption algorithm based on multiple mixed hash functions and cyclic shift. Opt. Lasers Eng. 2017, 107, 370–379. [Google Scholar] [CrossRef]
- Guesmi, R.; Farah, M.A.B.; Kachouri, A.; Samet, M. A novel chaos-based image encryption using DNA sequence operation and secure hash algorithm sha-2. Nonlinear Dyn. 2016, 83, 1123–1136. [Google Scholar] [CrossRef]
- Liu, H.; Wang, X. Color image encryption based on one-time keys and robust chaotic maps. Comput. Math. Appl. 2010, 59, 3320–3327. [Google Scholar] [CrossRef]
- Huang, L.; Cai, S.; Xiao, M.; Xiong, X. A simple chaotic map-based image encryption system using both plaintext related permutation and diffusion. Entropy 2018, 20, 535. [Google Scholar] [CrossRef]
- Chai, X.; Chen, Y.; Broyde, L. A novel chaos-based image encryption algorithm using DNA sequence operations. Opt. Lasers Eng. 2017, 88, 197–213. [Google Scholar] [CrossRef]
- Li, Y.; Liu, X.; Chen, G.; Liao, X. A new hyperchaotic lorenz-type system: Generation, analysis, and implementation. Int. J. Circuit Theory Appl. 2011, 39, 865–879. [Google Scholar] [CrossRef]
- Stoyanov, B.P. Pseudo-random bit generator based on chebyshev map. In Application of Mathematics in Technical and Natural Sciences; Todorov, M.D., Ed.; American Institute of Physics: College Park, MD, USA, 2013; Volume 1561, pp. 369–372. [Google Scholar]
- Li, S.; Chen, G.; Mou, X. On the dynamical degradation of digital piecewise linear chaotic maps. Int. J. Bifurc. Chaos 2005, 15, 3119–3151. [Google Scholar] [CrossRef]
- Li, S.; Chen, G.; Wong, K.-W.; Mou, X.; Cai, Y. Baptista-type chaotic cryptosystems: Problems and countermeasures. Phys. Lett. A 2004, 332, 368–375. [Google Scholar] [CrossRef]
- Curiac, D.-I.; Volosencu, C. Chaotic trajectory design for monitoring an arbitrary number of specified locations using points of interest. Math. Probl. Eng. 2012, 2012, 1–18. [Google Scholar] [CrossRef]
- Curiac, D.I.; Iercan, D.; Dranga, O.; Dragan, F.; Banias, O. Chaos-Based Cryptography: End of the Road? In Proceedings of the International Conference on Emerging Security Information, System and Technologies, Valencia, Spain, 14–20 October 2007; pp. 71–76. [Google Scholar]
- Wang, X.-Y.; Gu, S.-X.; Zhang, Y.-Q. Novel image encryption algorithm based on cycle shift and chaotic system. Opt. Lasers Eng. 2015, 68, 126–134. [Google Scholar] [CrossRef]
- Khanzadi, H.; Eshghi, M.; Borujeni, S.E. Image encryption using random bit sequence based on chaotic maps. Arab. J. Sci. Eng. 2014, 39, 1039–1047. [Google Scholar] [CrossRef]
- Kulsoom, A.; Xiao, D.; Aqeel Ur, R.; Abbas, S.A. An efficient and noise resistive selective image encryption scheme for gray images based on chaotic maps and DNA complementary rules. Multimed. Tools Appl. 2016, 75, 1–23. [Google Scholar] [CrossRef]
- Wang, X.-Y.; Zhang, Y.-Q.; Bao, X.-M. A novel chaotic image encryption scheme using DNA sequence operations. Opt. Lasers Eng. 2015, 73, 53–61. [Google Scholar] [CrossRef]
- Stoyanov, B.; Kordov, K. Image encryption using chebyshev map and rotation equation. Entropy 2015, 17, 2117–2139. [Google Scholar] [CrossRef]
- Stoyanov, B.; Kordov, K. Novel image encryption scheme based on chebyshev polynomial and duffing map. Sci. World J. 2014, 2014, 283639. [Google Scholar] [CrossRef] [PubMed]
- Seyedzade, S.M.; Mirzakuchaki, S.; Atani, R.E. A novel image encryption algorithm based on hash function. In Proceedings of the Iranian Conference on Machine Vision and Image Processing, Isfahan, Iran, 27–28 October 2011; pp. 1–6. [Google Scholar]
- Chai, X.-L.; Gan, Z.-H.; Yuan, K.; Lu, Y.; Chen, Y.-R. An image encryption scheme based on three-dimensional brownian motion and chaotic system. Chin. Phys. B 2017, 26, 020504. [Google Scholar] [CrossRef]
- Wang, X.; Zhang, J. An image scrambling encryption using chaos-controlled poker shuffle operation. In Proceedings of the International Symposium on Biometrics and Security Technologies, Islamabad, Pakistan, 23–24 April 2008; pp. 41–46. [Google Scholar]
- Rehman, A.U.; Liao, X.; Kulsoom, A.; Abbas, S.A. Selective encryption for gray images based on chaos and DNA complementary rules. Multimed. Tools Appl. 2015, 74, 4655–4677. [Google Scholar] [CrossRef]
- Ramadan, N.; Ahmed, H.H.; El-khamy, S.E.; Abd El-Samie, F.E. Permutation-substitution image encryption scheme based on a modified chaotic map in transform domain. J. Central South Univ. 2017, 24, 2049–2057. [Google Scholar] [CrossRef]
| Statistical Test Name | S′ | V′ | T′ | |||
|---|---|---|---|---|---|---|
| Pass Rate | p-Value | Pass Rate | p-Value | Pass Rate | p-Value | |
| Frequency(monobit) | 99.5% | 0.9346 | 99.3% | 0.4058 | 99.4% | 0.4708 |
| Block Frequency | 99.2% | 0.8068 | 99.1% | 0.6079 | 99.0% | 0.5485 |
| The Run Test | 99.5% | 0.4088 | 99.6% | 0.4317 | 99.5% | 0.5493 |
| Longest Run of Ones | 98.6% | 0.1481 | 98.8% | 0.4555 | 98.6% | 0.4419 |
| Rank | 98.5% | 0.0465 | 98.3% | 0.0467 | 98.1% | 0.0103 |
| DFT Spectral | 99.3% | 0.9537 | 99.1% | 0.5365 | 99.3% | 0.6539 |
| Non-Overlapping Templates | 99.1% | 0.6163 | 99.0% | 0.5348 | 98.8% | 0.4807 |
| Overlapping Templates | 98.8% | 0.7597 | 98.6% | 0.5331 | 98.4% | 0.6420 |
| Universal Statistical Test | 98.5% | 0.5825 | 98.3% | 0.4624 | 98.2% | 0.4171 |
| Linear Complexity | 98.9% | 0.2215 | 98.7% | 0.4642 | 98.5% | 0.4936 |
| Serial Test 1 | 99.1% | 0.3358 | 98.9% | 0.2421 | 98.7% | 0.2602 |
| Serial Test 2 | 99.2% | 0.2046 | 99.4% | 0.4207 | 99.3% | 0.2315 |
| Approximate Entropy | 98.8% | 0.7522 | 98.6% | 0.6033 | 98.8% | 0.4784 |
| Cumulative Sums (forward) | 99.6% | 0.4752 | 99.8% | 0.8023 | 99.7% | 0.8163 |
| Cumulative Sums (Reverse) | 99.4% | 0.8898 | 99.2% | 0.6596 | 99.3% | 0.8101 |
| Random Excursions | 98.7% | 0.1599 | 98.8% | 0.1713 | 98.6% | 0.1314 |
| Random Excursions Variant | 98.9% | 0.3226 | 98.4% | 0.1564 | 98.6% | 0.0942 |
| Encryption Algorithm | Key Space |
|---|---|
| Proposed scheme | 2339 |
| Reference [24] | 2149 |
| Reference [25] | 2256 |
| Reference [31] | 2299 |
| Reference [32] | 2375 |
| Reference [33] | >2128 |
| Reference [34] | 2357 |
| Keys | Change Rate of Cyphertext Image t |
|---|---|
| x(0) | 0.9963 |
| y(0) | 0.9964 |
| z(0) | 0.9976 |
| w(0) | 0.9975 |
| Images | Rice | Autumn | Pepper | Cameraman | |
|---|---|---|---|---|---|
| NPCR% | Max | 99.8943 | 99.7932 | 99.9012 | 99.7821 |
| Min | 99.5426 | 99.4213 | 99.3809 | 99.4608 | |
| Average | 99.6062 | 99.6115 | 99.5956 | 99.5697 | |
| UACI% | Max | 33.5698 | 33.7754 | 33.8712 | 33.6590 |
| Min | 33.3216 | 33.5500 | 33.4919 | 33.1958 | |
| Average | 33.4419 | 33.6319 | 33.5418 | 33.3618 | |
| Images | Rice | Autumn | Pepper | Cameraman | |
|---|---|---|---|---|---|
| NPCR% | Max | 99.8812 | 99.6623 | 99.8719 | 99.8864 |
| Min | 99.4961 | 99.5512 | 99.5698 | 99.5091 | |
| Average | 99.6006 | 99.6098 | 99.5796 | 99.5692 | |
| UACI% | Max | 33.5612 | 33.6067 | 33.8523 | 33.7019 |
| Min | 33.3187 | 33.5602 | 33.4967 | 33.2195 | |
| Average | 33.4297 | 33.5897 | 33.5154 | 33.3478 | |
| Test Images | x2 of Plain Image | x2 of Cypherimage in [33] | x2 of Cypherimage in Our Algorithm |
|---|---|---|---|
| cameraman | 16,711,680 | 288.9823 < 295.25 | 285.3125 < 295.25 |
| pepper | 50,135,040 | 269.3387 < 295.25 | 260.3421 < 295.25 |
| rice | 96,312 | 284.2387 < 295.25 | 278.6172 < 295.25 |
| autumn | 18,122,850 | 289.9832 < 295.25 | 288.5792 < 295.25 |
| Images | This Paper | Ref. [34] | Ref. [39] | Ref. [40] | Ref. [41] | Ref. [42] |
|---|---|---|---|---|---|---|
| Rice (256 × 256) | 7.9973 | 7.9864 | 7.9936 | 7.9643 | 7.9875 | 7.9968 |
| cameraman (256 × 256) | 7.9989 | 7.9763 | 7.9952 | 7.9867 | 7.9946 | 7.9865 |
| autumn (206 × 345) | 7.9968 | 7.9564 | 7.9962 | 7.9698 | 7.9864 | 7.9972 |
| pepper (512 × 512) | 7.9992 | 7.9819 | 7.9983 | 7.9949 | 7.9896 | 7.9993 |
| Images | Horizontal | Vertical | Diagonal |
|---|---|---|---|
| Plaintext “Rice” | 0.9427 | 0.9263 | 0.8994 |
| Cyphertext “Rice” | −0.0046 | 0.0287 | −0.0361 |
| Plaintext “Cameraman” | 0.9588 | 0.9360 | 0.9095 |
| Cypher “Cameraman” | −0.0017 | −0.0279 | 0.0047 |
| Plaintext “autumn” | 0.9675 | 0.9845 | 0.9821 |
| Cyphertext “autumn” | −0.0087 | 0.0142 | 0.0098 |
| Plaintext “pepper” | 0.9894 | 0.9931 | 0.9847 |
| Cyphertext “pepper” | −0.0055 | −0.0194 | −0.0295 |
| Image Size (M × N) | Ref. [39] | Ref. [40] | Ref. [43] | Ref. [44] | Proposed System |
|---|---|---|---|---|---|
| 64 × 64 | 0.07 | 0.03 | 0.19 | 0.61 | 0.02 |
| 128 × 128 | 0.19 | 0.08 | 0.29 | 2.17 | 0.06 |
| 256 × 256 | 0.46 | 0.18 | 6.01 | 7.73 | 0.22 |
| 512× 512 | 1.88 | 0.97 | 35.59 | 31.59 | 0.85 |
| 1024 × 1024 | 3.62 | 2.94 | 253.88 | 169.21 | 3.11 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhu, S.; Zhu, C.; Wang, W. A New Image Encryption Algorithm Based on Chaos and Secure Hash SHA-256. Entropy 2018, 20, 716. https://doi.org/10.3390/e20090716
Zhu S, Zhu C, Wang W. A New Image Encryption Algorithm Based on Chaos and Secure Hash SHA-256. Entropy. 2018; 20(9):716. https://doi.org/10.3390/e20090716
Chicago/Turabian StyleZhu, Shuqin, Congxu Zhu, and Wenhong Wang. 2018. "A New Image Encryption Algorithm Based on Chaos and Secure Hash SHA-256" Entropy 20, no. 9: 716. https://doi.org/10.3390/e20090716
APA StyleZhu, S., Zhu, C., & Wang, W. (2018). A New Image Encryption Algorithm Based on Chaos and Secure Hash SHA-256. Entropy, 20(9), 716. https://doi.org/10.3390/e20090716






