A Colour Image Encryption Scheme Using Permutation-Substitution Based on Chaos
Abstract
:1. Introduction
2. Related Works
2.1. The CML System
2.2. Zigzag Path Scrambling
3. Colour Image Encryption Algorithm Based on Chaos
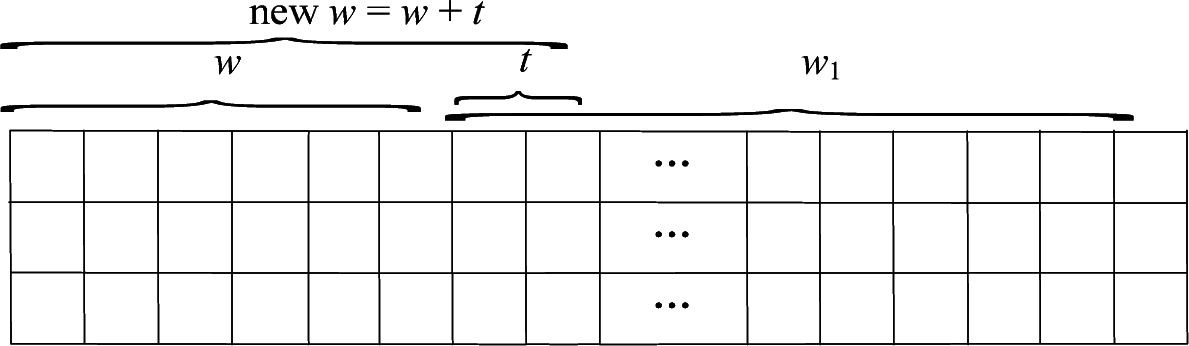
- Permute the selected block of width t for r times using the zigzag path scrambling.
- Confuse the permutated block: implement exclusive OR operation bit-by-bit on the first row of the permutated block using ; implement exclusive OR operation bit-by-bit on the second row of the permutated block using ; implement exclusive OR operation bit-by-bit on the third row of the permutated block using . Then set:
- Permute the selected block of width w1 for r times using the zigzag path scrambling.
- Confuse the permutated block: implement exclusive OR operation bit-by-bit on the first row of the permutated block using ; implement exclusive OR operation bit-by-bit on the second row of the permutated block using ; implement exclusive OR operation bit-by-bit on the third row of the permutated block using .
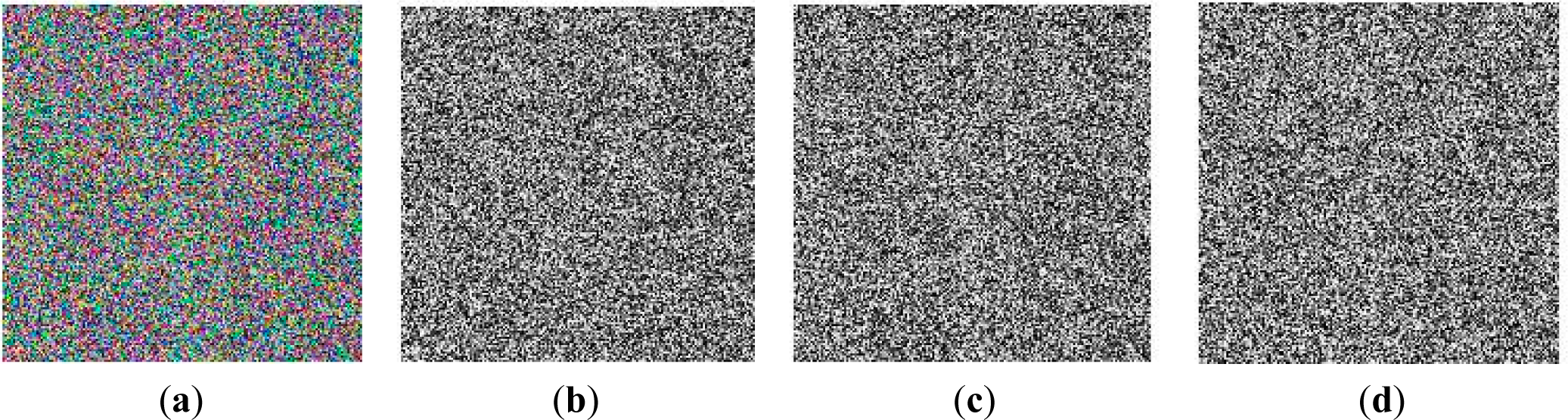
4. Experimental Simulations
5. Performance Analysis
5.1. Key Space
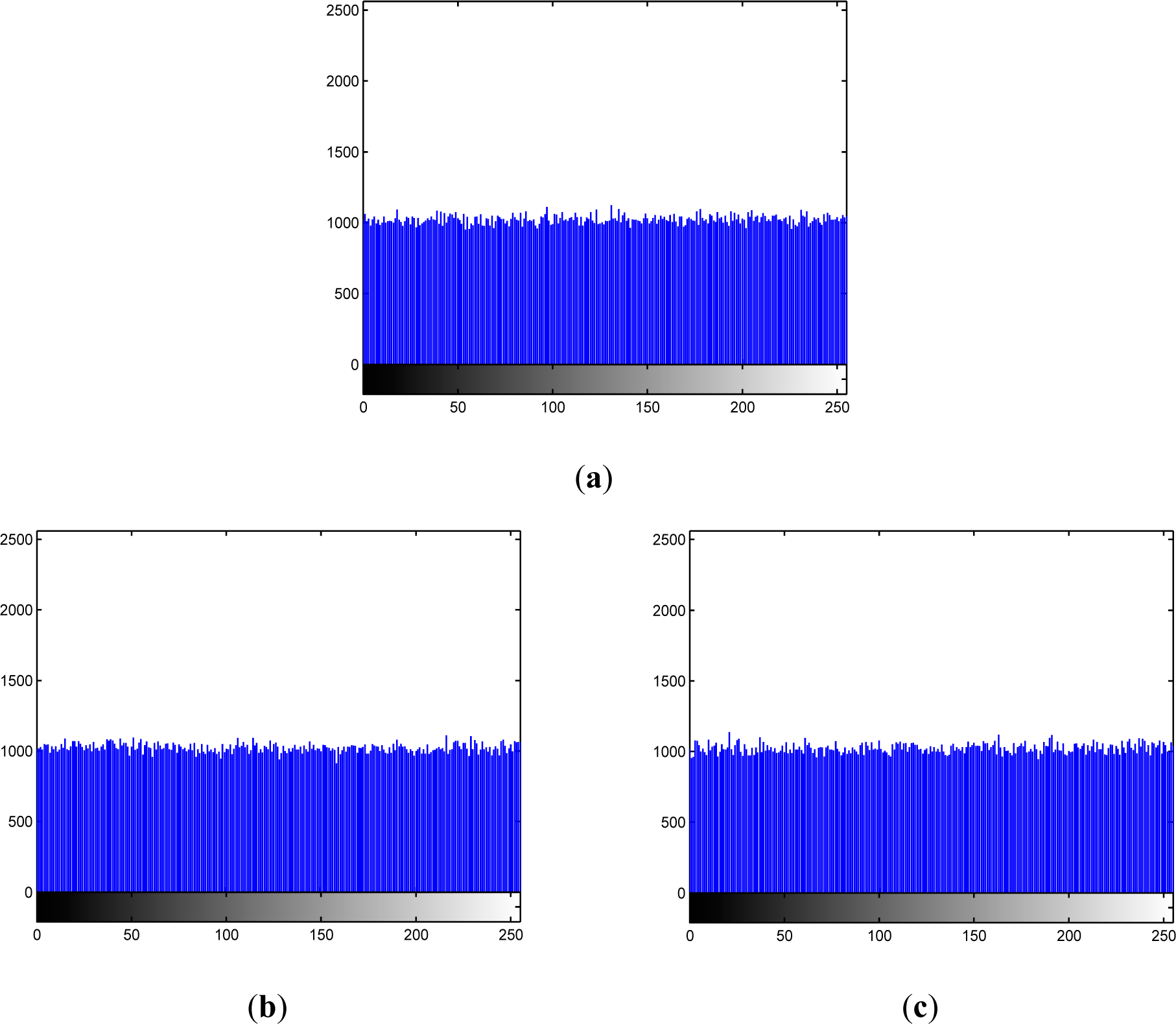
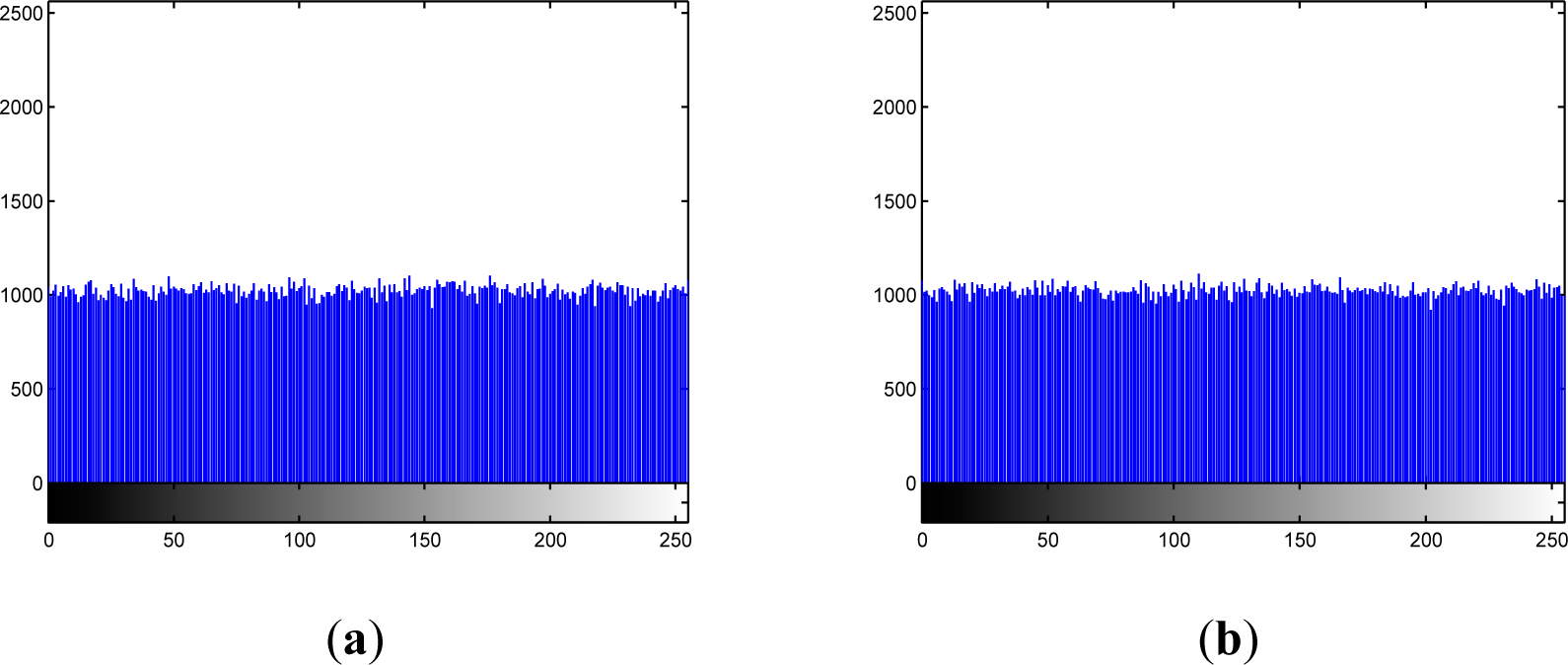
5.2. Histogram Analysis
5.3. Information Entropy Analysis
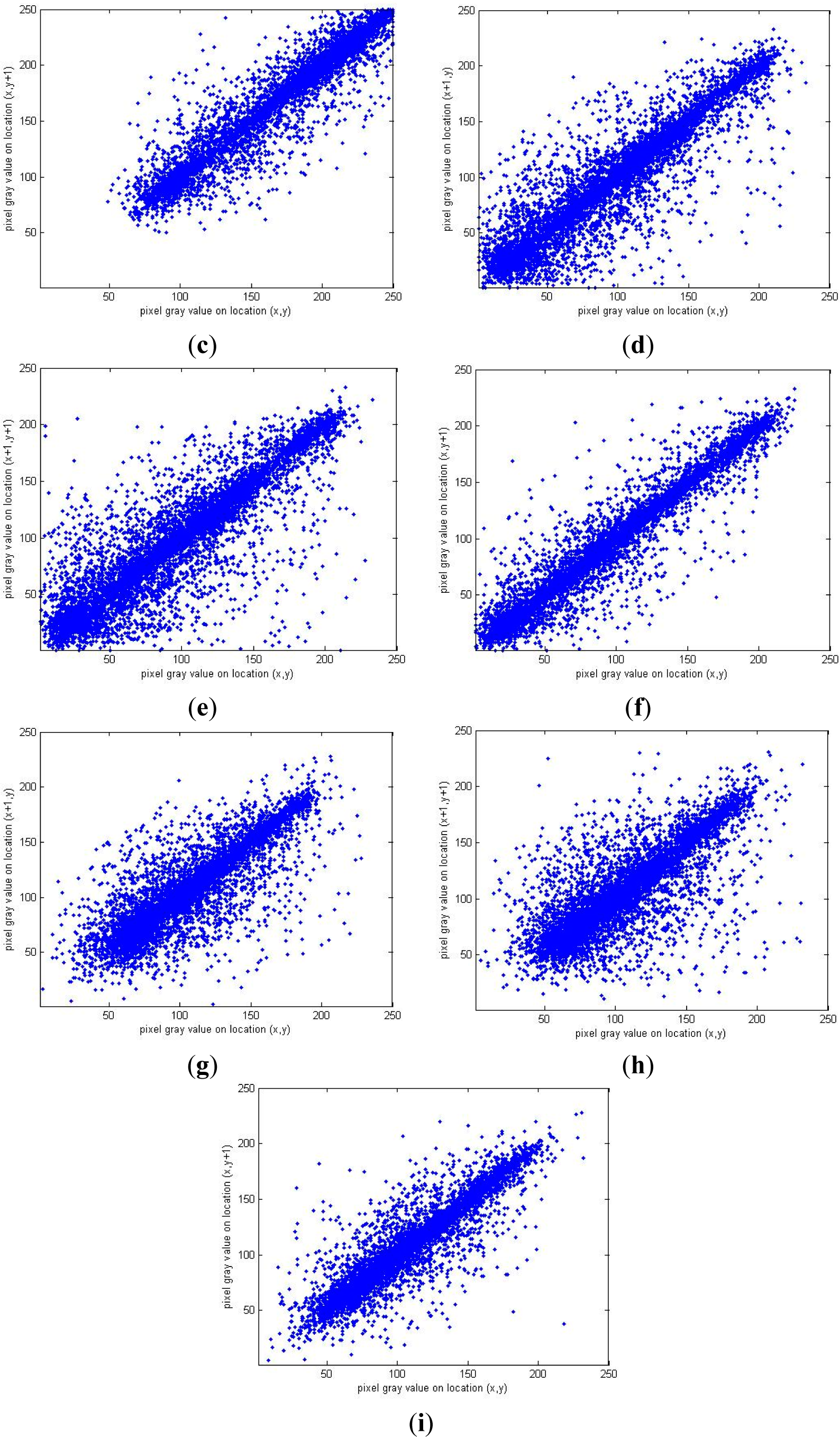
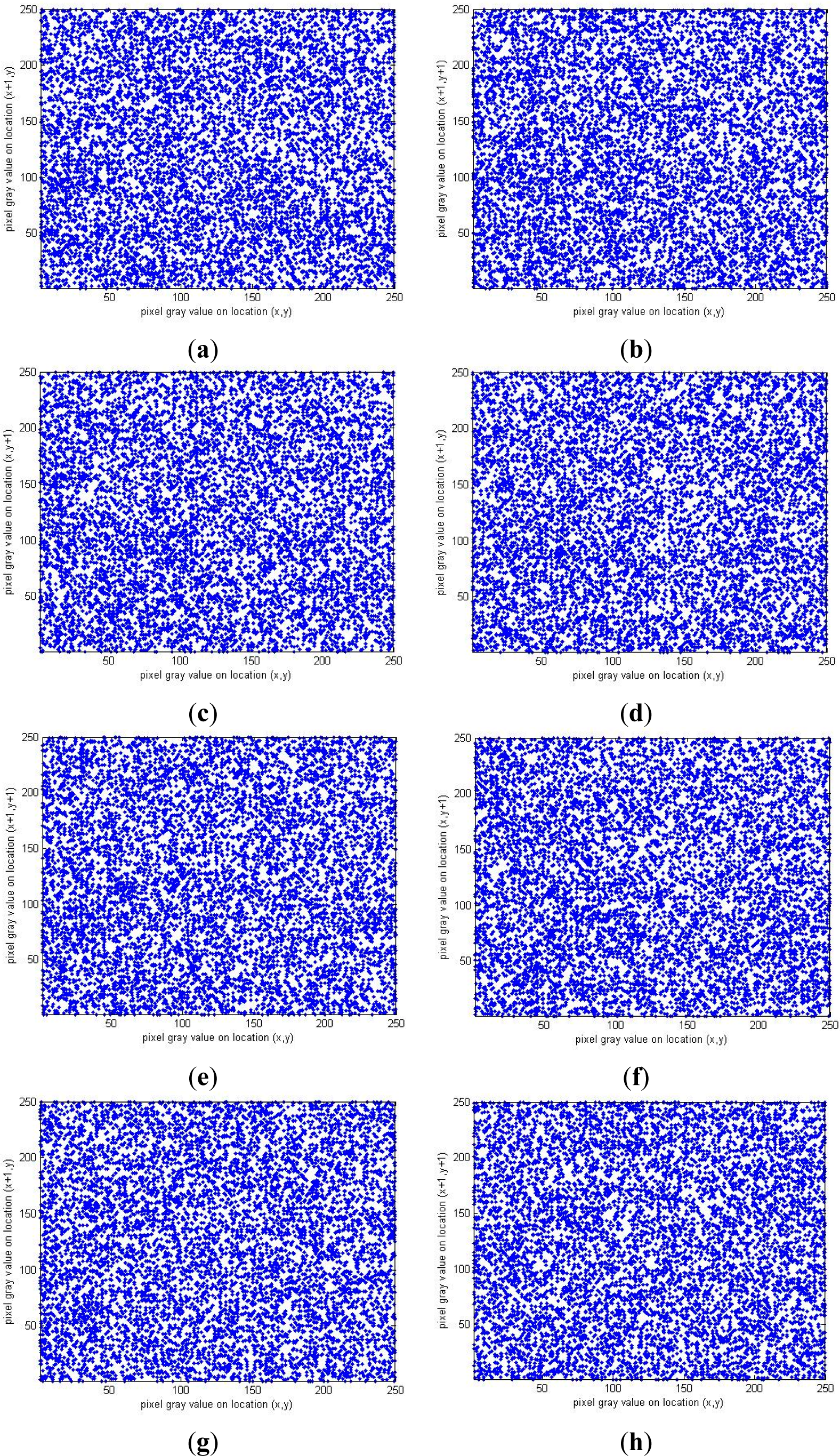
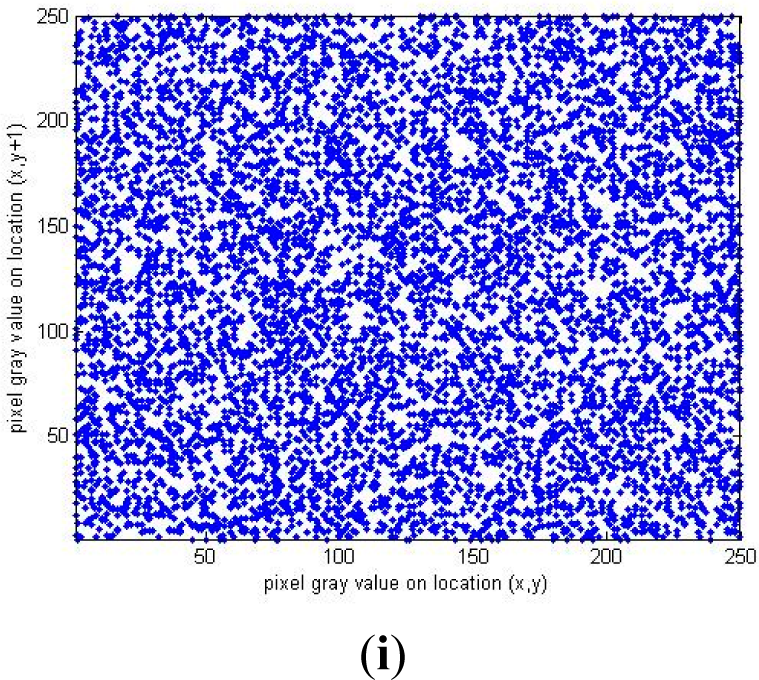
5.4. Correlation Analysis
5.5. Differential Attacks
5.6. Key Sensitivity
5.7. Speed Performance
5.8. Performance Comparison with Other Colour Image Encryption Schemes
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Uhl, A.; Pommer, A. Image and Video Encryption: From Digital Rights Management to Secured Personal Communication; Springer: New York, NY, USA; 2004. [Google Scholar]
- Liu, B.; Peng, J. Nonlinear Dynamics; High Education Press: Beijing, China; 2004; in Chinese. [Google Scholar]
- Wang, X.Y.; Teng, L. An image blocks encryption algorithm based on spatiotemporal chaos. Nonlinear Dyn 2012, 67, 365–371. [Google Scholar]
- Bigdeli, N.; Farid, Y.; Afshar, K. A novel image encryption/decryption scheme based on chaotic neural networks. Eng. Appl. Artif. Intell 2012, 25, 753–765. [Google Scholar]
- Liao, X.F.; Lai, S.Y.; Zhou, Q. A novel image encryption algorithm based on self-adaptive wave transmission. Signal Proc 2010, 90, 2714–2722. [Google Scholar]
- Ren, X.; Liao, X.; Xiong, Y.; Jisuanji, Y. New image encryption algorithm based on cellular neural network. J. Comput. Appl 2011, 31, 1528–1530. [Google Scholar]
- Wang, X.Y.; Yang, L.; Liu, R.; Kadir, A. A chaotic image encryption algorithm based on perceptron model. Nonlinear Dyn 2010, 62, 615–621. [Google Scholar]
- Rhouma, R.; Soumaya, M.; Safya, B. CML-based colour image encryption. Chaos Solitons Fractals 2009, 40, 309–318. [Google Scholar]
- Sahar, M.; Amir, M.E. Colour image encryption based on coupled nonlinear chaotic map. Chaos Solitons Fractals 2009, 42, 1745–1754. [Google Scholar]
- Liu, H.J.; Wang, X.Y. Colour image encryption based on one-time keys and robust chaotic maps. Comput. Math. Appl 2010, 59, 3320–3327. [Google Scholar]
- Peng, Z.N.; Liu, W.B. Colour image authentication based on spatiotemporal chaos and SVD. Chaos Solitons Fractals 2008, 36, 946–952. [Google Scholar]
- Madhusudan, J.; Shakher, C.; Kehar, S. Colour image encryption and decryption for twin images in fractional Fourier domain. Opt. Commun 2008, 8, 5713–5720. [Google Scholar]
- Guo, Q.; Liu, Z.G.; Liu, S.T. Colour image encryption by using Arnold and discrete fractional random transforms in IHS space. Opt. Lasers Eng 2010, 48, 1174–1181. [Google Scholar]
- Tay, C.J.; Quan, C.; Chen, W.; Fu, Y. Colour image encryption based on interference and virtual optics. Opt. Laser Technol 2010, 42, 409–415. [Google Scholar]
- Wheeler, D.D. Problems with chaotic cryptosystems. Cryptologia 1991, 7, 243–250. [Google Scholar]
- Li, P.; Li, Z.; Halang, W.A.; Chen, G. A stream cipher based on a spatiotemporal chaotic system. Chaos Solitons Fractals 2007, 32, 1867–1876. [Google Scholar]
- Ziba, E.; Atieh, B. An improvement over an image encryption method based on total shuffling. Opt. Commun 2013, 286, 51–55. [Google Scholar]
- Fatih, O.; Bedri, O.A.; Sirma, Y. Cryptanalysis of a novel image encryption scheme based on improved hyperchaotic sequences. Opt. Commun 2012, 285, 4946–4948. [Google Scholar]
- Teng, L.; Wang, X. A bit-level image encryption algorithm based on spatiotemporal chaotic system and self-adaptive. Opt. Commun 2012, 285, 4048–4054. [Google Scholar]
- Liu, G.; Li, J.; Liu, H. Chaos-based color pathological image encryption scheme using one-time keys. Comput. Biol. Med 2014, 45, 111–117. [Google Scholar]
- Gonzalo, A.; Shujun, L.; Luis, H. Analysis of security problems in a medical image encryption system. Comput. Biol. Med 2007, 27, 424–427. [Google Scholar]
- Almasalha, F.; Hasimoto-Beltran, R.; Khokhar, A.A. Partial Encryption of Entropy-Coded Video Compression Using Coupled Chaotic Maps. Entropy 2014, 16, 5575–5600. [Google Scholar]
- Tong, X.; Liu, Y.; Zhang, M.; Xu, H.; Wang, Z. An Image Encryption Scheme Based on Hyperchaotic Rabinovich and Exponential Chaos Maps. Entropy 2015, 17, 181–196. [Google Scholar]
- Boriga, R.; Dăscălescu, A.C.; Diaconu, A.V. A New One-Dimensional Chaotic Map and its Use in a Novel Real Time Image Encryption Scheme. Adv. Multimed 2014, 2014. [Google Scholar] [CrossRef]
- Boriga, R.; Dăscălescu, A.C.; Diaconu, A.V. A New Fast Image Encryption Scheme Based on 2D Chaotic Maps. IAENG Int. J. Comput. Sci 2014, 41, 249–258. [Google Scholar]
- Huang, X.; Sun, T.; Li, Y.; Liang, J. A Color Image Encryption Algorithm Based on a Fractional-Order Hyperchaotic System. Entropy 2015, 17, 28–38. [Google Scholar]
- Huang, C.K.; Liao, C.W.; Hsu, S.L.; Jeng, Y.C. Implementation of gray image encryption with pixel shuffling and gray-level encryption by single chaotic system. Telecommun. Syst 2013, 52, 563–571. [Google Scholar]
- Diaconu, A.V.; Loukhaoukha, K. An Improved Secure Image Encryption Algorithm Based on Rubik’s Cube Principle and Digital Chaotic Cipher. Math. Probl. Eng 2013, 2013, 848392. [Google Scholar]
- Ghebleh, M.; Kanso, A.; Noura, H. An image encryption scheme based on irregularly decimated chaotic maps. Signal Proc. Image Commun 2014, 29, 618–627. [Google Scholar]
- El-Latif, A.A.; Li, L.; Wang, N.; Han, Q.; Niu, X. A new approach to chaotic image encryption based on quantum chaotic system, exploiting color spaces. Signal Proc. Image Commun 2013, 93, 2986–3000. [Google Scholar]
- Dăscălescu, A.C.; Boriga, R.; Mihăilescu, M.I. A Novel Chaos-Based Image Encryption Scheme. Ann. Univ. Craiova Math. Comput. Sci. Ser 2014, 41, 47–58. [Google Scholar]
- Ye, G.; Wong, K.W. An image encryption scheme based on time-delay and hyperchaotic system. Nonlinear Dyn 2013, 71, 259–267. [Google Scholar]
- Kwok, H.S.; Tang, W.K.S. A fast image encryption system based on chaotic maps with finite precision representation. Chaos Solitons Fractals 2007, 32, 1518–1529. [Google Scholar]
- Diaconu, A.V.; Costea, A.; Costea, M.A. Color image scrambling technique based on transposition of pixels between RBG channels using Knight’s moving rules and digital chaotic map. Math. Probl. Eng 2014, 2014. [Google Scholar] [CrossRef]
- Saraswathi, P.V.; Venkatesulu, M. A block cipher algorithm for multimedia content protection with random substitution using binary tree traversal. J. Comput. Sci 2012, 8, 1541–1546. [Google Scholar]
- Sivakumar, T.; Venkatesan, R. A novel approach for image encryption using dynamic SCAN pattern. IAENG Int. J. Comput. Sci 2014, 41, 91–101. [Google Scholar]
- Kaneko, K. Spatiotemporal intermittency in Coupled Map Lattices. Prog. Theor. Phys 1985, 74, 1033–1044. [Google Scholar]
- USC-SIPI Image Database. Available online: http://sipi.usc.edu/database/database.php accessed on 10 April 2015.
- Wu, Y.; Zhou, Y.; Saveriades, G.; Agaian, S.; Noonan, J.P.; Natarajan, P. Local Shannon entropy measure with statistical tests for image randomness. Inf. Sci 2013, 222, 323–342. [Google Scholar]
- Wu, Y.; Noonan, J.P.; Agaian, S. NPCR and UACI randomness tests for image encryption. J. Sel. Areas Telecommun 2011, 2, 31–38. [Google Scholar]








| Images | χ2 Tests
| |
|---|---|---|
| Plaintext Image
| Ciphered Image
| |
| Lena | 712,602.34 | 812.34 |
| Grill | 15,699,323.29 | 825.45 |
| House | 772,576.61 | 815.73 |
| Mandrill | 305,590.38 | 795.75 |
| Peppers | 1,022,998.32 | 816.85 |
| Ciphered Images | Entropy |
|---|---|
| Lena | 7.9931 |
| Grill | 7.9947 |
| House | 7.9954 |
| Mandrill | 7.9958 |
| Peppers | 7.9962 |
| Ciphered Images | Entropy | Results |
|---|---|---|
| Lena | 7.9021 | Success |
| Grill | 7.9026 | Success |
| House | 7.9027 | Success |
| Mandrill | 7.9023 | Success |
| Peppers | 7.9024 | Success |
| Component | Horizontal | Vertical | Diagonal |
|---|---|---|---|
| R component in ciphered Lena | −0.0032 | −0.0006 | 0.0005 |
| G component in ciphered Lena | −0.0041 | 0.0056 | 0.0074 |
| B component in ciphered Lena | 0.0021 | −0.0065 | −0.0022 |
| R component in ciphered Girl | −0.0012 | −0.0014 | 0.0004 |
| G component in ciphered Girl | 0.0054 | −0.0037 | −0.0042 |
| B component in ciphered Girl | −0.0003 | 0.0032 | 0.0017 |
| R component in ciphered House | 0.0053 | −0.0024 | −0.0049 |
| G component in ciphered House | −0.0023 | 0.0008 | −0.0017 |
| B component in ciphered House | 0.0046 | 0.0021 | 0.0037 |
| R component in ciphered Mandrill | 0.0029 | 0.0023 | −0.0021 |
| G component in ciphered Mandrill | −0.0007 | −0.0038 | 0.0019 |
| B component in ciphered Mandrill | 0.0011 | 0.0020 | 0.0015 |
| R component in ciphered Peppers | −0.0020 | 0.0024 | −0.0026 |
| G component in ciphered Peppers | −0.0025 | 0.0030 | −0.0025 |
| B component in ciphered Peppers | 0.0008 | 0.0011 | −0.0016 |
| Component | NPCR | UACI |
|---|---|---|
| R component in ciphered Lena | 99.59% | 33.28% |
| G component in ciphered Lena | 99.55% | 33.33% |
| B component in ciphered Lena | 99.58% | 33.33% |
| R component in ciphered Girl | 99.45% | 33.31% |
| G component in ciphered Girl | 99.47% | 33.34% |
| B component in ciphered Girl | 99.51% | 33.35% |
| R component in ciphered House | 99.55% | 33.38% |
| G component in ciphered House | 99.53% | 33.43% |
| B component in ciphered House | 99.57% | 33.41% |
| R component in ciphered Mandrill | 99.59% | 33.40% |
| G component in ciphered Mandrill | 99.59% | 33.43% |
| B component in ciphered Mandrill | 99.58% | 33.42% |
| R component in ciphered Peppers | 99.57% | 33.33% |
| G component in ciphered Peppers | 99.57% | 33.43% |
| B component in ciphered Peppers | 99.58% | 33.42% |
| Indicator | Reference [25] | Reference [29] | Reference [35] | Reference [36] | Proposed Scheme |
|---|---|---|---|---|---|
| NPCR | 99.24 | 99.61 | 99.85 | 99.48 | 99.55 |
| UACI | 33.13 | 33.72 | 33.58 | 30.87 | 33.37 |
| Horizontal | 0.0039 | −0.0043 | 0.01776 | 0.342 | 0.0026 |
| Vertical | 0.0059 | 0.0049 | 0.04912 | 0.352 | 0.0027 |
| Diagonal | 0.0004 | 0.0057 | 0.00348 | 0.298 | 0.0026 |
| Speed (MB/s) | 3 | 2.4 | 0.45 | 1.65 | 2.87 |
© 2015 by the authors; licensee MDPI, Basel, Switzerland This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, X.-Y.; Zhang, Y.-Q.; Bao, X.-M. A Colour Image Encryption Scheme Using Permutation-Substitution Based on Chaos. Entropy 2015, 17, 3877-3897. https://doi.org/10.3390/e17063877
Wang X-Y, Zhang Y-Q, Bao X-M. A Colour Image Encryption Scheme Using Permutation-Substitution Based on Chaos. Entropy. 2015; 17(6):3877-3897. https://doi.org/10.3390/e17063877
Chicago/Turabian StyleWang, Xing-Yuan, Ying-Qian Zhang, and Xue-Mei Bao. 2015. "A Colour Image Encryption Scheme Using Permutation-Substitution Based on Chaos" Entropy 17, no. 6: 3877-3897. https://doi.org/10.3390/e17063877
APA StyleWang, X.-Y., Zhang, Y.-Q., & Bao, X.-M. (2015). A Colour Image Encryption Scheme Using Permutation-Substitution Based on Chaos. Entropy, 17(6), 3877-3897. https://doi.org/10.3390/e17063877





