1. Introduction
Presently, due to increasingly fierce market competition, product reliability is generally improved with the advance of production technology. It often takes quite a long period of time to observe the failure time for all units in life-testing experiments, which results in a significant increase in test time and cost. Therefore, it is natural that censoring appears in reliability studies as a result of the limitation of duration and cost of the experiments. In the literature, numerous authors have investigated the traditional type-I censoring under which case the life-testing experiment terminates when the experimental time reaches the preset time, as well as type-II censoring under which case the life-testing experiment terminates when the number of the observed failure units reaches the preset target. Neither of them allows the removal of the test unit during the experiment, which is one of their drawbacks. Furthermore, the concept of progressive censoring is proposed as units may exit the experiment before their failure. In some special situations, the loss of units is beyond the control of the experimenters and may be caused by sudden damage to experimental equipment. It could also be intentional to remove units from the experiment for the sake of freeing up experimental facilities and materials for other experiments as well as saving time and cost. One may refer to [
1], which provides an elaborate discussion on progressive censoring. Sometimes it still cannot meet the restriction of test time and cost. Thus, various censoring patterns are proposed successively to improve efficiency.
When experimental materials are relatively cheap, we can use
units for experiments instead of only
n units and randomly divide them into
n sets with
k independent test units in each set. It is known as the first-failure censoring that only the first failure time is recorded in every set during the experiment, the test will terminate until the first failure occurs for all sets. Moreover, a novel censoring pattern, called the progressive first-failure censoring scheme (PFFCS), was proposed by [
2]. The maximum likelihood estimates (MLEs), accurate intervals together with approximate intervals for Weibull parameters, and the expected termination time were derived under PFFCS.
Recently, this new life-testing plan has aroused the interest of a great number of researchers. The MLEs and interval estimation of the lifetime index
for progressive first-failure censored Weibull distribution, as well as a sensitivity analysis, were studied by [
3]. Based on the methods mentioned before, Refs. [
4,
5] further implemented Bayes estimation methods to compute the parameters of Lindley and exponentiated exponential distributions, respectively. Ref. [
6] dedicated to discussing the Bayes inference in two cases and two-sample prediction issues for a progressive first-failure censored Gompertz distribution. Ref. [
7] also mainly focused on Bayes methods for Chen distribution, whereas they also introduced the least square estimator and illustrated its good performance against MLEs. Furthermore, Ref. [
8] introduced the competing risks model into the progressive censoring scheme for the Gompertz distribution and [
9] introduced the step-stress partially accelerated life test and derived the MLEs for the acceleration factor in this life test for the progressive first-failure censored Weibull distribution.
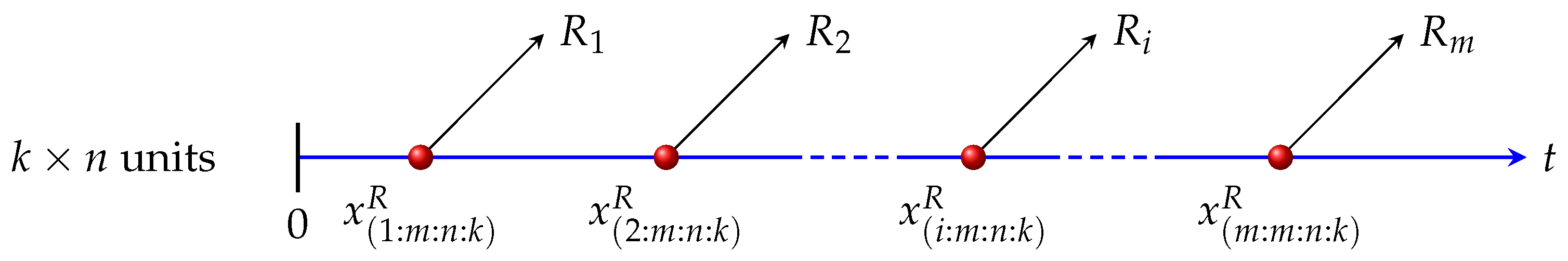
Now, we illustrate the progressive first-failure censoring as follows: Suppose that
n groups are being tested simultaneously in a life-testing experiment, every group has
k test units and they are totally independent of each other. During the experiment, in time of the occurrence of the first failed component, the group it belongs to and any
groups in the rest of
groups are promptly eliminated from the test. In the same way, in time of the occurrence of the second failed component, the group it belongs to and any
groups in the rest of
groups are promptly eliminated from the test. This procedure keeps going on until the
mth failed component occurs and all the remaining
groups are immediately eliminated from the test. Here
m and
are set in advance and
. To further illustrate,
Figure 1 shows the process of the generation of progressive first-failure censored sample. In particular, pay attention that this censoring scheme has several special cases, one may refer to [
10]. All the conclusions mentioned afterward are available to extend to those kinds of data, which is one of the advantages of progressive first-failure censoring.
The truncated normal distribution is used in many fields, including education, insurance, engineering, biology and medicine, etc. When a threshold is set on a normally distributed dataset, the remaining data naturally have a truncated normal distribution. For instance, when all college admission candidates whose SAT scores are below the screening value are eliminated, people may be interested in the scores of the remaining candidates. However, if the original score population is normally distributed, the problem they concern turns to investigate the truncated normal distribution. Generally speaking, the truncated normal distribution consists of one-sided truncated and two-sided truncated in terms of the number of truncated points. Simultaneously, with respect to the truncation range, the one-sided truncated normal distribution can be subdivided into left-truncated and right-truncated, and they are also known as lower-truncated and upper-truncated.
The truncated normal distribution has recently attracted a lot of research interest. The existence of MLEs for the parameters was discussed in [
11] when the two truncated points were known, and the modified MLEs were further explored to improve the efficiency of the estimation. Ref. [
12] developed a handy algorithm to compute the expectation and variance of a truncated normally distributed variable and they compared its behavior under both full and censored data. As for the left-truncated normal distribution, Ref. [
13] employed three available approaches to investigate the problem of sample size. In addition to the MLEs and Bayes estimators, Ref. [
14] also proposed midpoint approximation to derive the estimates of parameters based on progressive type-I interval-censored sample, and meanwhile, the optimal censoring plans were considered. For the purpose of advancing the research on the standardized truncated normal distribution, Ref. [
15] developed a standard truncated normal distribution that wherever the truncated points are, it remains the mean value zero and the variance one. Ref. [
16] proposed a mixed truncated normal distribution to describe the wind speed distribution and verified its validity.
When it comes to the properties of the truncated normal distribution, it is worth noting that its shape and scale parameters are not equal to its expectation and variance but correspond to the parameters of the parent normal distribution before truncation. After the truncation range is determined, the value of the probability density function outside it becomes zero, while the value within it is adjusted uniformly to make the total integral one. Therefore, expectation and variance are adjusted for the truncation.
Assuming
X is a truncated normally distributed random variable and its truncation range is
, the shape and scale parameters are
and
, then its expectation and variance correspond to
and
here
and
denote the probability density function (PDF) and cumulative distribution function (CDF) of the standard normal distribution.
Some mechanical and electrical products such as their material strength, wear life, gear bending, and fatigue strength can be considered to have a truncated normal life distribution. As a lifetime distribution, the domain of the random variable should be non-negative and consequently, it is reasonable to assume that
. Thus, we consider the left-truncated normal distribution with the truncation range
, denoted as
, then the corresponding PDF that is
and CDF that is
of the distribution
are
and
here
is the shape parameter and
is the scale parameter. And the survival function is
For comparison,
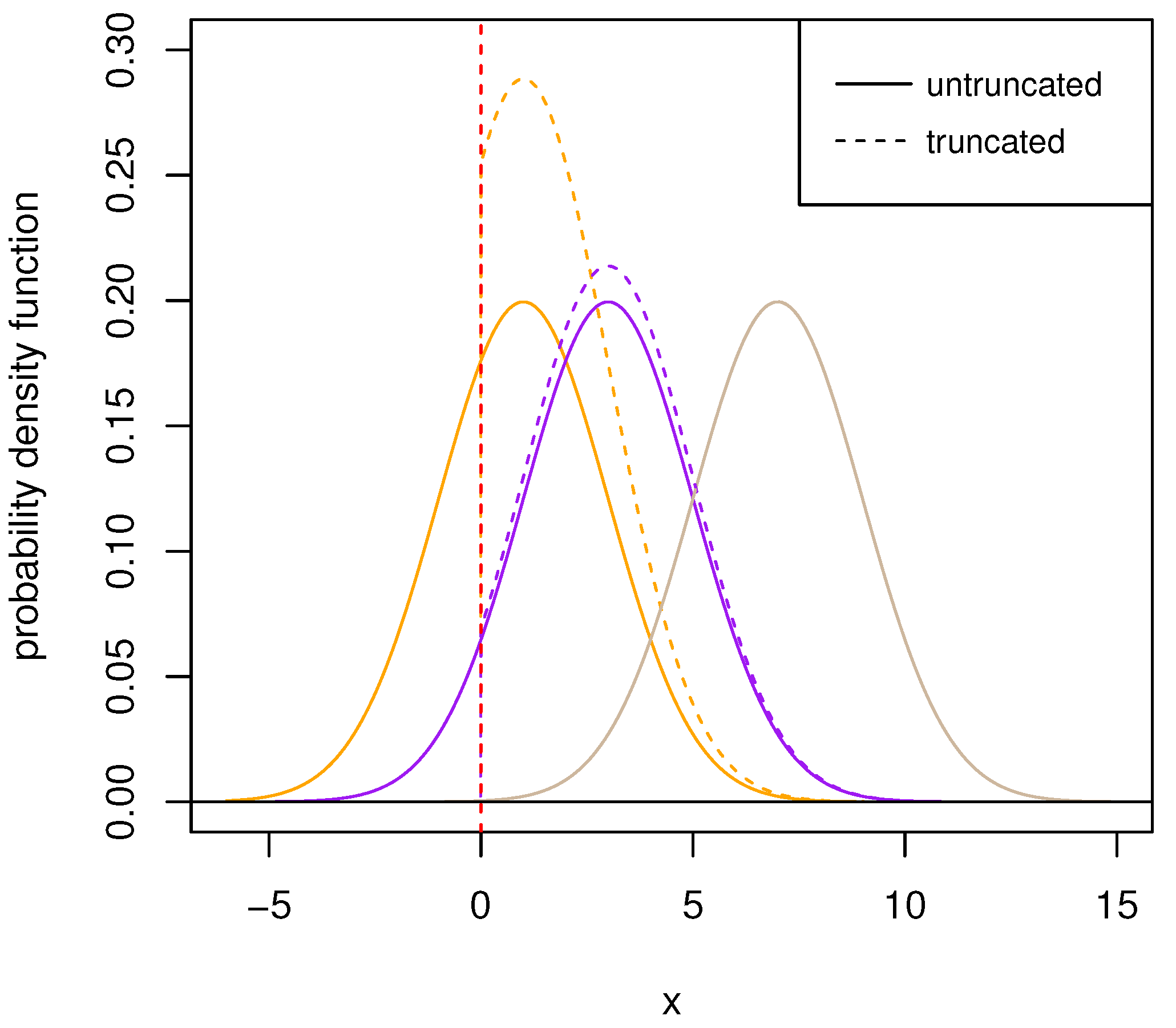
Figure 2 visually shows the distinction of PDFs between three groups of parent normal distributions
and the corresponding truncated normal distribution
. The parent normal distributions possess the same
but different
. Obviously, the parent normal distribution whose shape parameter is closest to the truncated point changes drastically after truncation, while the one with the shape parameter farthest to the truncated point barely changes and even retains the same pattern as normal. In particular, it is worth mentioning that when the truncated point
satisfies
, the truncation basically loses its effect. In
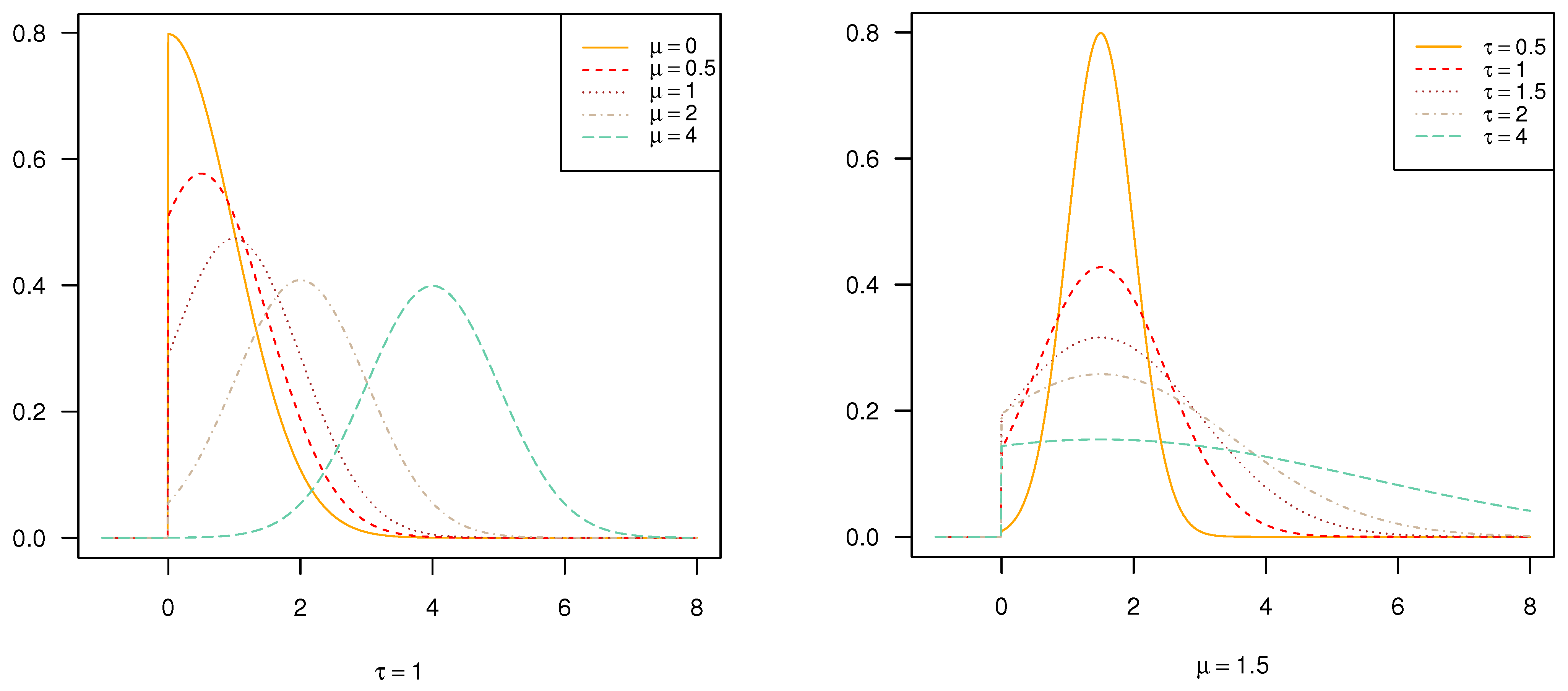
Figure 3, we can observe that the position where the peak of the truncated normal distribution occurs is in accordance with the value of
. As this value gets closer to the truncated point, the peak value of PDF of the distribution
and the same scale parameter will be larger as a result of the integral of one. However, under the same shape parameters, the image of PDF becomes flat with the increase of scale parameter and it is consistent with the property of normal distribution.
This article begins with the following sections. In the first place, the MLEs for two unknown parameters of the distribution
are derived in
Section 2 and we establish the corresponding asymptotic confidence intervals (ACIs) associated with the approximate asymptotic variance-covariance matrix. In
Section 3, the bootstrap resampling method is applied to develop both bootstrap-p and bootstrap-t intervals. In
Section 4, we propose the Bayes approaches to estimate two parameters under squared error, Linex, and general entropy loss functions using Lindley approximation. As this approximation method is failed to provide us the credible intervals, the importance sampling procedure is employed to gain both parameter estimates and the highest posterior density (HPD) credible intervals. The behaviors of diverse estimators proposed in the above sections are evaluated and compared by amounts of simulations in
Section 5. In
Section 6, an authentic dataset is introduced and applied to clarify how to make statistical inferences using the methods presented before and the effectiveness of these approaches. Finally, a summary of the whole article is made in
Section 7.
3. Bootstrap Confidence Intervals
Bootstrap methods can make great sense in the case with little effective sample size
m, so here we propose two widely used bootstrap methods to establish the intervals, see [
19]. One is the percentile bootstrap method, also regarded as bootstrap-p (boot-p). The other is known as the bootstrap-t (boot-t) method. The specific steps of the two methods are as follows.
3.1. Percentile Bootstrap Confidence Intervals
Step 1 For a given PFF censored sample from with and , figure the MLEs of parameters and under the primitive sample , denoted as and .
Step 2 In accordance with the identical censoring pattern as , generate a PFF censored bootstrap sample from . Similarly to step 1, compute the bootstrap MLEs and based on .
Step 3 Do step 2 repeatedly for K times to collect a series of bootstrap MLEs and .
Step 4 Arrange and in an ascending order respectively then obtain and .
Step 5 The approximate boot-p CIs for and are presented by and , where and are respectively the integer parts of and .
3.2. Bootstrap-t Confidence Intervals
Step 1 For a given PFF censored sample from with and , figure the MLEs and and their variances and under the primitive sample .
Step 2 In accordance with the identical censoring pattern as , generate a PFF censored bootstrap sample from . Similarly to step 1, compute the bootstrap MLEs and based on .
Step 3 Compute the variances of and , say and , then compute the statistics for and for .
Step 4 Do steps 2-3 repeatedly for K times to collect a series of bootstrap statistics and
Step 5 Arrange and in an ascending order respectively then obtain and .
Step 6 The approximate
boot-t CIs for
and
are presented by
where
and
are respectively the integer parts of
and
.
4. Bayesian Estimation
The selection of prior distribution is a primary problem of Bayesian estimation for the fact that the prior distribution could have a significant impact on the posterior distribution in small sample cases. So, a proper prior distribution is worth discussing at the beginning.
In general cases, the conjugate prior distribution is a preferred choice in Bayesian estimation because of its algebraic convenience. However, such prior does not exist when both parameters
and
are unknown. For the sake of simplicity, we need to find a prior distribution with the same form as (7). Furthermore, according to the form of the denominator part of the exponential term in the likelihood function (7),
should appear as a parameter of the prior distribution of
. Therefore, assuming that they are not independent is feasible and we can presume that
follows an Inverse Gamma prior
and
follows a truncated normal prior associated with
, namely
, where all hyper-parameters are bound to be positive. The PDFs of their prior distributions can be written as
The corresponding joint prior distribution is
Given
, the joint posterior distribution
can be obtained by
4.1. Symmetric and Asymmetric Loss Functions
The loss function is used to evaluate the degree to which the predicted value or the estimated value of the parameter is different from the real value. In practice, the squared error loss function has been used extensively in the literature and it is preferred in the case where the loss caused by overestimation and underestimation is of equal importance. But sometimes, it is not appropriate to use a symmetric loss function when an overestimate plays a crucial role compared with an underestimate, or vice versa. Thus, in this subsection, we discuss the Bayesian estimations theoretically under one symmetric loss function, namely squared error loss function (SE), and two non-symmetric loss functions, namely Linex loss function (LX) and general entropy loss function (GE).
4.1.1. Squared Error Loss Function
This loss function is defined as
here,
denotes any estimate of
.
The Bayesian estimator of
under SE is
Given a function
, the expression of its Bayesian posterior expectation is
Thus, the Bayesian estimate
under SE can be given theoretically as
4.1.2. Linex Loss Function
The Linex loss function is suggested in the case that underestimation is more costly compared with overestimation, and this loss function is defined as
In fact, it is recognized as a family
where
could be either the usual estimation error
or a relative error
, namely
. In this paper, we take advantage that
and let
, then LX becomes
The sign of the
s indicates the orientation of asymmetry, while its size represents the degree of asymmetry. Under the same difference
, the larger the magnitude of
s is, the larger the cost is. Given small values of
, LX is almost symmetric and very close to SE. One may refer to [
20] for details.
The Bayesian estimator of
under LX is
Thus, the Bayesian estimate
under LX can be given theoretically as
4.1.3. General Entropy Loss Function
This loss function is defined as
The Bayesian estimator of
under GE is
When , the positive error value is more costly compared with the negative error value, and vice versa. In particular, when , the Bayesian estimate under SE is the same as that under GE.
The Bayesian estimate
under GE can be given theoretically as
It is noticeable that the Bayesian estimates are expressed in terms of the ratio of two integrals and the specific forms cannot be presented theoretically. So, we implement the Lindley approximation method to determine such estimates.
4.2. Lindley Approximation Method
In this subsection, we take advantage of Lindley approximation to acquire the Bayesian parameter estimates. Consider the posterior expectation of
expressed in terms of the ratio of two integrals
here,
l denotes the log-likelihood function,
denotes the logarithmic form of the joint prior distribution.
According to [
21], expression (34) can be approximated as
with
and
Here , denotes the -th element of the inverse FIM. All terms in (35) are computed at MLEs and . Then the approximate solution expressions of Bayesian parameter estimates under loss functions SE, LX, and GE are as follows.
4.2.1. Squared Error Loss Function
For parameter
, we take
, hence
The Bayesian estimate of
under SE is derived by combining (24), (35) and (36)
Similarly, for parameter
, we take
, hence
The Bayesian estimate of
under SE is derived by combining (24), (35) and (38)
4.2.2. Linex Loss Function
For parameter
, it is clear that
The Bayesian estimate of
under LX is derived by combining (29), (35) and (40)
For parameter
, it is clear that
The Bayesian estimate of
under LX is derived by combining (29), (35) and (42)
4.2.3. General Entropy Loss Function
For parameter
, the corresponding items become
The Bayesian estimate of
under GE is derived by combining (32), (35) and (44)
For parameter
, the corresponding items become
The Bayesian estimate of
under GE is derived by combining (32), (35), and (46)
When it comes to estimating the ratio of two integrals in the form given in (34), the Lindley approximation method is very effective. Nevertheless, one of its drawbacks is that this method only provides point estimates but not the credible intervals. Therefore, in the upcoming subsection, we propose the importance sampling procedure to gain both estimations of points and intervals.
4.3. Importance Sampling Procedure
Here, we propose a useful approach called importance sampling procedure to acquire the Bayesian parameter estimates. Meanwhile, the HPD credible intervals for both parameters are constructed in this procedure.
From (22), the joint posterior distribution can be rewritten as
where
According to the Lemma 1, the parameters of the inverse gamma distribution and the truncated normal distribution in (48) are positive. Thus, it makes sense to sample from the and sample from .
Lemma 1. If and , then for all , for .
Proof. According to the sum of squares inequality, we can get .
Because
then we must prove the non-negativeness of the following quadratic function when we regard
as the independent variable of it.
Notably, the quadratic function above minimizes at , and the corresponding result is , which is strictly non-negative. Thus, the lemma is proved.
□
Then, the following steps are used to derive the Bayesian estimate of any function of the parameters and .
- (1)
Generate from .
- (2)
Generate from with the generated in (1).
- (3)
Repeat (1) and (2) M times and get the sample .
- (4)
Then the Bayesian estimate of
is computed by
Considering the unknown parameters
and
, their Bayesian estimates could be derived by
Next the HPD credible interval for parameter
is illustrated, while the corresponding HPD credible interval for
can be computed by the same method. Let
Then we sort
by the first component
in ascending order and we can get
. Here
is associated with
, which means that
is not ordered. The construction of HPD credible interval is based on an estimate
and
, where
is an integer that satisfies
Now, a
credible interval for the unknown parameter
can be acquired as
. Therefore, the corresponding HPD credible interval for
is given by
where
for all
.
5. Simulation Study
For evaluating the effectiveness of the proposed methods, plenty of simulations are carried out in this part. The maximum likelihood and Bayes estimators proposed above are assessed based on the mean absolute bias (MAB) and mean squared error (MSE), whereas interval estimations are considered according to the mean length (ML) and coverage rate (CR). Looking back to the progressive first-failure censoring presented in the first part, it can be found that when an experimental group is regarded as one unit, the life of this experimental unit turns into the life distribution of the minimum value of the group. In this way, it is intelligible to generate PFF censored sample through a simple modification of the algorithm introduced in [
22] and Algorithm 1 given subsequently provides the specific generation method.
| Algorithm 1 Generating progressive first-failure censored sample from |
- 1.
Set the initial values of both group size k and censoring scheme . - 2.
Generate independent random variables that obey the uniform distribution . - 3.
Let for all . - 4.
Let for all . - 5.
For given and , let , here represents the CDF of . - 6.
Finally, we set for all , here represents the inverse function of . Hence, is the PFF censored sample from .
|
Here, we take the true values of parameters as
and
For comparison purposes, we consider
,
and
. Meanwhile, different censoring schemes (CS) designed for the later simulations are presented in
Table 1. As a matter of convenience, we abbreviate the censoring scheme to make it clear, for instance,
is the abbreviation of the censoring scheme
. In each case, we repeat the simulation at least 2000 times. Thus, the associated MABs and MSEs with the point estimation and the associated MLs and CRs with the interval estimation can be obtained.
First, it should be noted that all our simulations are performed in R software. For maximum likelihood estimation, we use
optim command with method L-BFGS-B to derive the MLEs of parameters, and then we tabulate the corresponding results in
Table 2. For Bayesian estimation, we naturally consider the true value as the mean of the prior distribution. But such hyper-parameters are intractable because of the complexity of prior distribution. Therefore, we use genetic algorithm and
mcga package in R software to search for the optimal hyper-parameters and the result turns out to be
. Then two Bayes approaches with informative prior are implemented to derive the estimates under loss functions SE, LX and GE. We set the parameter
s of LX to
and 1, while the parameter
h of GE is
and
. These simulation results are listed in
Table 3,
Table 4,
Table 5 and
Table 6.
At the same time, the proposed intervals are established at 95% confidence/credible level and
Table 7 and
Table 8 summarize the results. Here, ACI denotes asymptotic confidence interval based on MLEs, Log-ACI denotes the asymptotic confidence interval based on log-transformed MLEs. In the following simulations, the bootstrap confidence intervals are obtained after
resamples while HPD credible intervals are obtained after
samples.
From
Table 2, we can observe some properties about maximum likelihood estimates:
- (1)
The maximum likelihood estimate of performs much better than that of the maximum likelihood estimate of with respect to MABs and MSEs.
- (2)
When the effective sample size m or the total number of groups n or the value of increases, MABs and MSEs decrease significantly for all estimators, which is exactly as we expected. With the increasing group size k, MABs and MSEs generally decrease for the shape parameter , while the corresponding indicators generally increase for the scale parameter .
- (3)
Different censoring schemes show a certain pattern as for MABs and MSEs. For , both are generally smaller under the middle censoring schemes, on the contrary, both are generally smaller under the left censoring schemes for .
- (1)
Under three loss functions, the Bayesian estimates with proper prior are more accurate than MLEs as for MABs and MSEs in all cases. Both Bayesian methods are better than MLEs undoubtedly and it is clear that the Lindley approximation outperforms the importance sampling.
- (2)
Few censoring schemes such as and do not compete well for the Bayesian estimation of . The commonality of these two schemes is that they own the small effective sample size m and both are middle censorings.
- (3)
The Bayesian estimates of under SE is superior compared with GE, while the Bayesian estimates of under SE is similar to GE. For GE, choosing is better than . For LX, both and are satisfactory and they compete quite well. Overall, the Bayes estimates under Linex loss function using Lindley approximation are highly recommended as it possesses the minimum of MABs and MSEs.
- (1)
In general, the ML of HPD credible interval is the most satisfying compared with the other intervals, while the boot-t confidence interval possesses the widest ML. With the increase of , the ML shows a tendency to narrow, and this pattern holds for both parameters.
- (2)
Boot-p confidence interval is unstable as its CR decreases significantly when the group size k increases, whereas boot-t interval is basically not affected by k and possesses the robustness to some extent considering .
- (3)
ACI competes well with Log-ACI for and they are similar in terms of ML and CR. However, the CR of Log-ACI is much improved and more precise than ACI for . Therefore, Log-ACI seems to be a better choice.
6. Authentic Data Analysis
Now, we introduce an authentic dataset and we analyze it by using the methods developed above. This dataset was obtained from [
23], which was analyzed in [
5,
24] respectively. This dataset, presented in
Table 9, describes the tensile strength of 100 tested 50mm carbon fibers and it is measured in giga-Pascals (GPa).
First, we test whether the distribution
fits this real dataset well. In particular, Ref. [
24] compared the fitting results with many famous reliability distributions, such as Rayleigh distribution, and Log-Logistic distribution, etc. They concluded that Log-Logistic distribution has the best fitting effect. Therefore, we compare the fitting effect of truncated normal distribution and Log-Logistic distribution with the PDF that is
.
Various criteria are applied for testing the goodness of fit of the model, such as the negative log-likelihood function
, Akaike Information Criterion (AIC), Bayesian Information Criterion (BIC), and Kolmogorov–Smirnov (K-S) statistics with its
p-value. The corresponding definitions of the above criteria are given as
here,
is a parameter vector,
d is the number of parameters in the fitted model,
is evaluated at the MLEs, and
n is the number of observed values.
Table 10 shows the MLEs of the parameters for each distribution, along with
, AIC, BIC, K-S, and
p-value corresponding to two distributions. Conspicuously, since the truncated normal distribution has the lower statistics and higher
p-value, it does fit the complete sample well. Now, we can use this dataset for analysis.
Therefore, we randomly divide the given data into 50 groups, and each group has two independent units. Thus, the first-failure censored data are obtained, as shown in
Table 11. In order to gain the PFF censored samples, we set
and give three different kinds of censoring schemes, namely
.
Table 12 presents the PFF censored samples under left censoring, middle censoring and right censoring.
In
Table 13 and
Table 14, the point estimates of parameters
and
are shown, respectively. No informative prior is available for Bayesian estimation, so we apply non-informative prior, and the four hyper-parameters are all around zero tightly and three loss functions discussed before are taken into account. As for the two asymmetric loss functions, we continue to use the parameters in the previous simulations, namely
and
,
and
. It can be seen from the table that there are some differences between the estimated values obtained by different censoring schemes and different methods. The parameter estimates based on censoring scheme
are closest to the MLEs under the full sample, while the estimates using the importance sampling are pervasively inclined to be smaller compared with those gained by Lindley approximation. At the same time, we construct
ACIs, Log-ACIs, bootstrap, and HPD intervals, while
Table 15 and
Table 16 display the corresponding results.
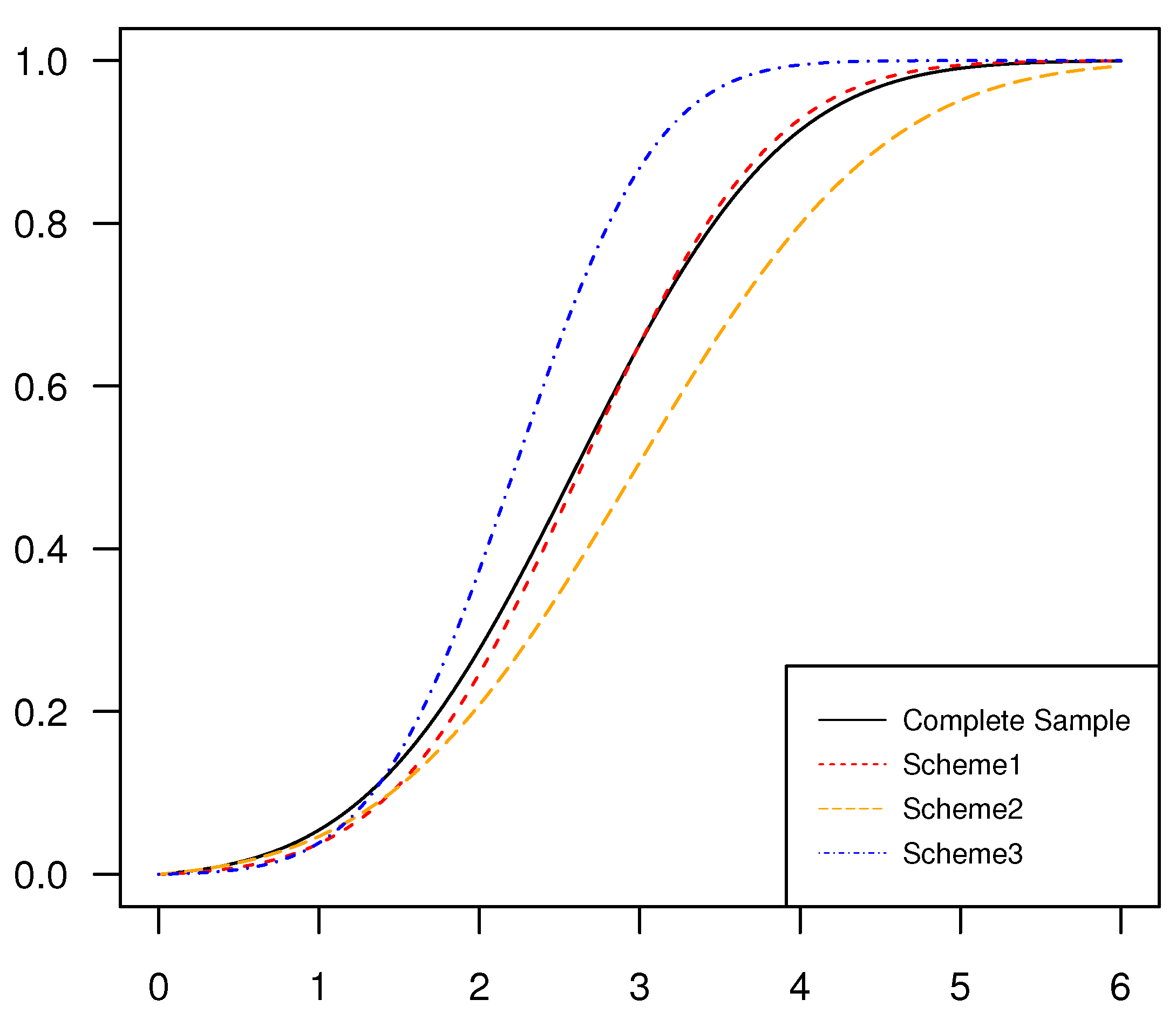
In
Figure 4, we have drawn four different estimated distribution function images, and their corresponding parameters are MLEs under complete samples and censored samples with schemes
and
. It is of considerable interest to see that the estimated curve based on the censoring scheme
is the closest to the estimated curve based on full data, which indicates that the left censored data is the superior one. In the middle part of the graphics, we can tell that the value of the estimated curve is underestimated based on the censoring scheme
, and on the contrary, the value based on the censoring scheme
is overestimated.