Motivations for the Use of IoT Solutions by Company Managers in the Digital Age: A Romanian Case
Abstract
:1. Introduction
2. Materials and Methods
2.1. Materials
2.1.1. IoT: Definition and Evolution
2.1.2. Unified Theory for Acceptance and Use of Technology (UTAUT): Importance, Advantages and Limitations
2.1.3. Motivation and Relationships between Intrinsic and Extrinsic Motivations of Employees and Managers
2.1.4. Intrinsic and Extrinsic Motivational Factors
2.2. Methods
2.2.1. The Questionnaire
2.2.2. Sample Selection
2.2.3. Methodology and Data Analysis
2.2.4. Questionnaire Validation and Preliminary Results
3. Results and Discussions
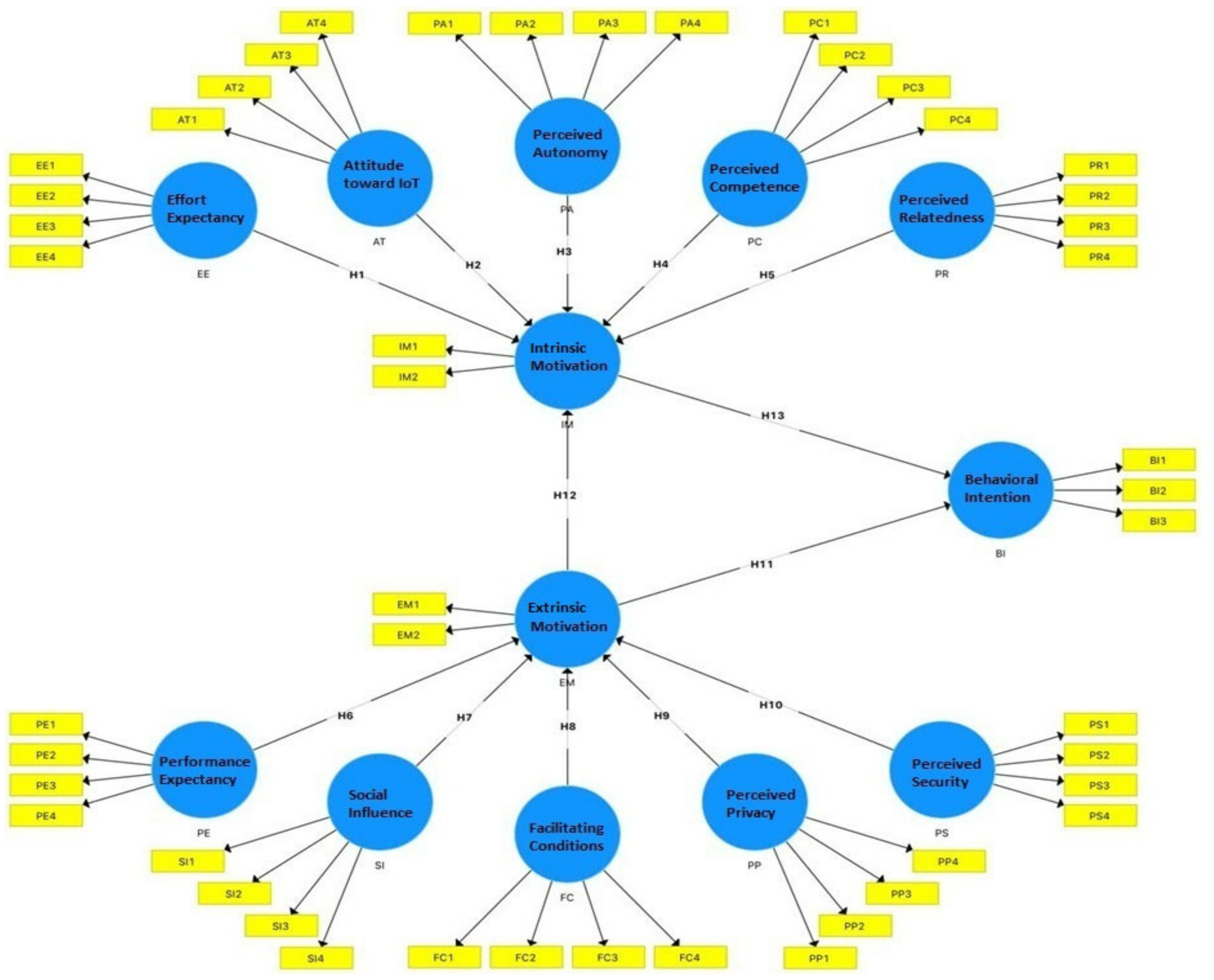
3.1. The Measurement Model
3.2. The Structural Model
4. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Ammirato, S.; Sofo, F.; Felicetti, A.M.; Raso, C. A Methodology to Support the Adoption of IoT Innovation and Its Application to the Italian Bank Branch Security Context. Eur. J. Innov. Manag. 2019, 22, 146–174. [Google Scholar] [CrossRef]
- Li, S.; Da Xu, L.; Zhao, S. The Internet of Things: A Survey. Inf. Syst. Front. 2014, 17, 243–259. [Google Scholar] [CrossRef]
- Liang, X. Internet of Things and Its Applications in Libraries: A Literature Review. Libr. Hi Tech 2018, 38, 67–77. [Google Scholar] [CrossRef]
- CISCO. Internet of Things: At-a-Glance; CISCO: San Jose, CA, USA, 2016. [Google Scholar]
- Ferri, L.; Spano, R.; Tomo, A. Cloud Computing in High Tech Startups: Evidence from a Case Study. Technol. Anal. Strat. Manag. 2019, 32, 146–157. [Google Scholar] [CrossRef]
- Lu, Y.; Papagiannidis, S.; Alamanos, E. Exploring the Emotional Antecedents and Outcomes of Technology Acceptance. Comput. Hum. Behav. 2019, 90, 153–169. [Google Scholar] [CrossRef] [Green Version]
- Caldarelli, A.; Ferri, L.; Maffei, M. Expected Benefits and Perceived Risks of Cloud Computing: An Investigation Within an Italian Setting. Technol. Anal. Strat. Manag. 2016, 29, 167–180. [Google Scholar] [CrossRef]
- Gangwar, H.; Date, H.; Ramaswamy, R. Understanding Determinants of Cloud Computing Adoption Using an Integrated TAM-TOE Model. J. Enterp. Inf. Manag. 2015, 28, 107–130. [Google Scholar] [CrossRef]
- Lee, Y.; Lee, J.; Hwang, Y. Relating Motivation to Information and Communication Technology Acceptance: Self-Determination Theory Perspective. Comput. Hum. Behav. 2015, 51, 418–428. [Google Scholar] [CrossRef]
- Fagan, M.H.; Neill, S.; Wooldridge, B.R. Exploring the Intention to Use Computers: An Empirical Investigation of the Role of Intrinsic Motivation, Extrinsic Motivation, and Perceived Ease of Use. J. Comput. Inf. Syst. 2008, 48, 31–37. [Google Scholar]
- He, G.M. Analysis of the Application of the Internet of Things Technology in Environmental Monitoring. Appl. Mech. Mater. 2015, 733, 796–799. [Google Scholar] [CrossRef]
- Haller, S.; Karnouskos, S.; Schroth, C. The Internet of Things in an Enterprise Context. In Computer Vision; Springer Science and Business Media LLC: Berlin, Germany, 2009; pp. 14–28. [Google Scholar]
- Peoples, C.; Parr, G.; McClean, S.; Scotney, B.; Morrow, P. Performance Evaluation of Green Data Centre Management Supporting Sustainable Growth of the Internet of Things. Simul. Model. Pr. Theory 2013, 34, 221–242. [Google Scholar] [CrossRef]
- Weber, R.H. Internet of Things—New Security and Privacy Challenges. Comput. Law Secur. Rev. 2010, 26, 23–30. [Google Scholar] [CrossRef]
- Zhao, J.; Zheng, X.; Dong, R.; Shao, G. The Planning, Construction, and Management Toward Sustainable Cities in China Needs the Environmental Internet of Things. Int. J. Sustain. Dev. World Ecol. 2013, 20, 195–198. [Google Scholar] [CrossRef]
- Khan, R.; Khan, S.U.; Zaheer, R.; Khan, S. Future Internet: The Internet of Things Architecture, Possible Applications and Key Challenges. In Proceedings of the 10th International Conference on Frontiers of Information Technology, 17–19 December 2012, Islamabad, Pakistan; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2012; pp. 257–260. [Google Scholar]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A Vision, Architectural Elements, and Future Directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef] [Green Version]
- Kim, S.; Kim, S. A Multi-Criteria Approach Toward Discovering Killer IoT Application in Korea. Technol. Forecast. Soc. Chang. 2016, 102, 143–155. [Google Scholar] [CrossRef]
- Almetere, E.S.; Kelana, B.W.Y.; Abu Mansor, N.N. Using UTAUT Model to Determine Factors Affecting Internet of Things Acceptance in Public Universities. Int. J. Acad. Res. Bus. Soc. Sci. 2020, 10, 142–150. [Google Scholar] [CrossRef]
- Ashton, K. That ‘Internet of Things’ thing. RFID J. 1999, 22, 97. [Google Scholar]
- Borgia, E. The Internet of Things vision: Key features, Applications and Open Issues. Comput. Commun. 2014, 54, 1–31. [Google Scholar] [CrossRef]
- UN International Telecommunication Union (ITU). Yearb. United Nations 2005, 59, 1583–1584.
- RFID Global. Casagras-Final Report. An EU framewok on 7 project. Coordination and Support Action for Global RFID-related activities and Standardisation. Cluster of European Research Project Internet of Things. CERP-IoT Research Roadmap, Draft version V1.9, 15 September 2009, Casagras, EU.
- McKinsey & Company. The Internet of Things: Opportunities and Challenges for Semiconductor Companies. Available online: http://www.mckinsey.com/insights/innovation/internet-of-things-opportunities-and-challenges-for-semiconductor-companies, (accessed on 22 March 2017).
- Li, X.; Lu, R.; Liang, X.; Shen, X.; Chen, J.; Lin, X. Smart Community: An Internet of Things Application. IEEE Commun. Mag. 2011, 49, 68–75. [Google Scholar] [CrossRef]
- Solima, L.; Della-Peruta, M.R.; del Giudice, M. Object-Generated Content and Knowledge Sharing: The Forthcoming Impact of the Internet of Things. J. Knowl. Econ. 2015, 7, 738–752. [Google Scholar] [CrossRef]
- Mital, M.; Chang, V.; Choudhary, P.; Papa, A.; Pani, A.K. Adoption of Internet of Things in India: A Test of Competing Models Using a Structured Equation Modeling Approach. Technol. Forecast. Soc. Chang. 2018, 136, 339–346. [Google Scholar] [CrossRef]
- Lee, W.; Shin, S. An Empirical Study of Consumer Adoption of Internet of Things Services. Int. J. Eng. Technol. Innov. 2019, 9, 1–11. [Google Scholar]
- Andersson, P.; Mattsson, L.-G. Service Innovations Enabled by the “Internet of Things”. IMP J. 2015, 9, 85–106. [Google Scholar] [CrossRef]
- Walz, K. Stress Related Issue Due to Too Much Technology: Effects on Working Professionals. MBA Student Scholarship. 2012, 11, 3–2012. [Google Scholar]
- Winner, L. Three Paradoxes of the Information Age. In Culture on the Brink: Ideologies of Technolog; Bender, G., Druckery, T., Eds.; Bay Press Seattle: Seattle, WA, USA, 1994; pp. 191–197. [Google Scholar]
- Mick, D.G.; Fournier, S. Paradoxes of Technology: Consumer Cognizance, Emotions, and Coping Strategies. J. Consum. Res. 1998, 25, 123–143. [Google Scholar] [CrossRef]
- Johnson, D.S.; Bardhi, F.; Dunn, D.T. Understanding How Technology Paradoxes Affect Customer Satisfaction with Self-Service Technology: The Role of Performance Ambiguity and Trust in Technology. Psychol. Mark. 2008, 25, 416–443. [Google Scholar] [CrossRef]
- Malik, A.; Magar, A.T.; Verma, H.; Singh, M.; Sagar, P. A Detailed Study of an Internet of Things (IoT). Int. J. Sci. Technol. Res. 2019, 8, 2989–2994. [Google Scholar]
- Rachisan, P.R.; Berinde, S.-R.; Bota-Avram, C.; Groșanu, A. Bankruptcy Risk Forecasting for the Metallurgical Branch in Romania. METABK 2014, 53, 371–374. [Google Scholar]
- Venkatesh, V.; Morris, M.; Davis, G.; Davis, F. User Acceptance of Information Technology: Toward a Unified View. MIS Q. 2003, 27, 425–478. [Google Scholar] [CrossRef] [Green Version]
- Fishbein, M.; Ajzen, I. Belief, Attitude, Intention, and Behavior: An Introduction to Theory and Research; Addison-Wesley: Reading, MA, USA, 1975. [Google Scholar]
- Davis, F. Perceived Usefulness, Perceived Ease of Use and User Acceptance of Information Technology. MIS Q. 1989, 13, 319–340. [Google Scholar] [CrossRef] [Green Version]
- Venkatesh, V.; Davis, F.D. A Theoretical Extension of the Technology Acceptance Model: Four Longitudinal Field Studies. Manag. Sci. 2000, 46, 186–204. [Google Scholar] [CrossRef] [Green Version]
- Davis, F.D.; Bagozzi, R.P.; Warshaw, P.R. Extrinsic and Intrinsic Motivation to Use Computers in the Workplace. J. Appl. Soc. Psychol. 1992, 22, 1111–1132. [Google Scholar] [CrossRef]
- Ajzen, I.; Anderson, N. Theory of Planned Behavior. Encycl. Health Behav. 2012, 50, 179–211. [Google Scholar] [CrossRef]
- Thompson, R.L.; Higgins, C.A.; Howell, J.M. Personal Computing: Toward a Conceptual Model of Utilization. MIS Q. 1991, 15, 125. [Google Scholar] [CrossRef]
- Compeau, D.; Higgins, C.A.; Huff, S. Social Cognitive Theory and Individual Reactions to Computing Technology: A Longitudinal Study. MIS Q. 1999, 23, 145. [Google Scholar] [CrossRef]
- Moore, G.C.; Benbasat, I. Development of an Instrument to Measure the Perceptions of Adopting an Information Technology Innovation. Inf. Syst. Res. 1991, 2, 192–222. [Google Scholar] [CrossRef]
- Lin, C.-P.; Bhattacherjee, A. Elucidating Individual Intention to Use Interactive Information Technologies: The Role of Network Externalities. Int. J. Electron. Commer. 2008, 13, 85–108. [Google Scholar] [CrossRef]
- Wang, Y.-S.; Wu, M.-C.; Wang, H.-Y. Investigating the Determinants and Age and Gender Differences in the Acceptance of Mobile Learning. Br. J. Educ. Technol. 2009, 40, 92–118. [Google Scholar] [CrossRef]
- van Raaij, E.M.; Schepers, J.J. The Acceptance and Use of a Virtual Learning Environment in China. Comput. Educ. 2008, 50, 838–852. [Google Scholar] [CrossRef]
- Lee, M.K.; Cheung, C.M.; Chen, Z. Acceptance of Internet-Based Learning Medium: The Role of Extrinsic and Intrinsic Motivation. Inf. Manag. 2005, 42, 1095–1104. [Google Scholar] [CrossRef]
- George, J.M.; Jones, G.R. Understanding and Managing Organizational Behaviour, 6th ed.; Prentice Hall: Upper-Saddle River, NJ, USA, 2012. [Google Scholar]
- Legault, L. Intrinsic and Extrinsic Motivation. In Encyclopedia of Personality and Individual Differences; Springer Science and Business Media LLC: Berlin, Germany, 2020; pp. 2416–2419. [Google Scholar]
- Lin, H.-F. Effects of Extrinsic and Intrinsic Motivation on Employee Knowledge Sharing Intentions. J. Inf. Sci. 2007, 33, 135–149. [Google Scholar] [CrossRef]
- Giancola, F.L. Should HR Professionals Devote More Time to Intrinsic Rewards? Compens. Benefits Rev. 2014, 46, 25–31. [Google Scholar] [CrossRef]
- Cerasoli, C.P.; Nicklin, J.M.; Ford, M.T. Intrinsic Motivation and Extrinsic Incentives Jointly Predict Performance: A 40-Year Meta-Analysis. Psychol. Bull. 2014, 140, 980–1008. [Google Scholar] [CrossRef] [PubMed]
- Jurkiewicz, C.L.; Massey, T.K.; Brown, R.G. Motivation in Public and Private Organizations: A Comparative Study. Public Prod. Manag. Rev. 1998, 21, 230. [Google Scholar] [CrossRef]
- Buelens, M.; Broeck, H.V.D. An Analysis of Differences in Work Motivation between Public and Private Sector Organizations. Public Adm. Rev. 2007, 67, 65–74. [Google Scholar] [CrossRef]
- Houston, D.J. Public-Service Motivation: A Multivariate Test. J. Public Adm. Res. Theory 2000, 10, 713–728. [Google Scholar] [CrossRef]
- Chen, K.-Y.; Chang, M.-L. User Acceptance of ‘Near Field Communication’ Mobile Phone Service: An Investigation Based on the ‘Unified Theory of Acceptance and Use of Technology’ Model. Serv. Ind. J. 2013, 33, 609–623. [Google Scholar] [CrossRef]
- Sumak, B.; Heričko, M.; Pusnik, M. A Meta-Analysis of E-Learning Technology Acceptance: The Role of User Types and E-Learning Technology Types. Comput. Hum. Behav. 2011, 27, 2067–2077. [Google Scholar] [CrossRef]
- Hsu, C.-L.; Lin, J.C.-C. Acceptance of Blog Usage: The Roles of Technology Acceptance, Social Influence and Knowledge Sharing Motivation. Inf. Manag. 2008, 45, 65–74. [Google Scholar] [CrossRef]
- Zhang, L.; Zhu, J.; Liu, Q. A Meta-Analysis of Mobile Commerce Adoption and the Moderating Effect of Culture. Comput. Hum. Behav. 2012, 28, 1902–1911. [Google Scholar] [CrossRef]
- Gao, L.; Bai, X. A Unified Perspective on the Factors Influencing Consumer Acceptance of Internet of Things Technology. Asia Pac. J. Mark. Logist. 2014, 26, 211–231. [Google Scholar] [CrossRef]
- Lunney, A.; Cunningham, N.R.; Eastin, M.S. Wearable Fitness Technology: A Structural Investigation into Acceptance and Perceived Fitness Outcomes. Comput. Hum. Behav. 2016, 65, 114–120. [Google Scholar] [CrossRef]
- Al-Momani, A.M.; Mahmoud, M.A.; Ahmad, S. Modeling the Adoption of Internet of Things Services: A Conceptual Framework. Int. J. Appl. Res. 2016, 2, 361–367. [Google Scholar]
- Boonsiritomachai, W.; Pitchayadejanant, K. Determinants Affecting Mobile Banking Adoption by Generation Y Based on the Unified Theory of Acceptance and Use of Technology Model Modified by the Technology Acceptance Model Concept. Kasetsart J. Soc. Sci. 2017, 2452–3151. [Google Scholar] [CrossRef]
- Patel, K.J.; Patel, H.J.; Estelami, H. Adoption of Internet Banking Services in Gujarat. Int. J. Bank Mark. 2018, 36, 147–169. [Google Scholar] [CrossRef]
- Sepasgozar, S.M.; Hawken, S.; Sargolzaei, S.; Foroozanfa, M. Implementing Citizen Centric Technology in Developing Smart Cities: A Model for Predicting the Acceptance of Urban Technologies. Technol. Forecast. Soc. Chang. 2019, 142, 105–116. [Google Scholar] [CrossRef]
- Lee, J.H.; Kim, J.H.; Choi, J.Y. The Adoption of Virtual Reality Devices: The Technology Acceptance Model Integrating Enjoyment, Social Interaction, and Strength of the Social Ties. Telemat. Inform. 2019, 39, 37–48. [Google Scholar] [CrossRef]
- Scherer, R.; Siddiq, F.; Tondeur, J. The Technology Acceptance Model (TAM): A Meta-Analytic Structural Equation Modeling Approach to Explaining Teachers’ Adoption of Digital Technology in Education. Comput. Educ. 2019, 128, 13–35. [Google Scholar] [CrossRef]
- Kim, K.-J. Interacting Socially with the Internet of Things (IoT): Effects of Source Attribution and Specialization in Human-IoT Interaction. J. Comput. Commun. 2016, 21, 420–435. [Google Scholar] [CrossRef] [Green Version]
- Liu, L.; Chen, W.; Solanas, A.; He, A. Knowledge, Attitude, and Practice About Internet of Things for Healthcare. In Proceedings of the 2017 International Smart Cities Conference, Wuxi, China, 14–17 September 2017; 2017; pp. 1–4. [Google Scholar] [CrossRef]
- Economides, A.A. User Perceptions of Internet of Things (IoT) Systems. Commun. Comput. Inf. Sci. 2017, 978, 3–20. [Google Scholar] [CrossRef]
- Wong, E.H.; Wiest, D.J.; Cusick, L.B. Perceptions of Autonomy Support, Parent Attachment, Competence and Self-Worth as Predictors of Motivational Orientation and Academic Achievement: An Examination of Sixth- and Ninth-Grade Regular Education Students. Adolescence 2002, 37, 255–266. [Google Scholar] [PubMed]
- Marchant, G.J.; Paulson, S.E.; Rothlisberg, B.A. Relations of Middle School Students’ Perceptions of Family and School Contexts Within Academic Achievement. Psychol. Sch. 2001, 38, 505–519. [Google Scholar] [CrossRef]
- Guay, F.; Boggiano, A.K.; Vallerand, R.J. Autonomy Support, Intrinsic Motivation, and Perceived Competence: Conceptual and Empirical Linkages. Pers. Soc. Psychol. Bull. 2001, 27, 643–650. [Google Scholar] [CrossRef] [Green Version]
- Ryan, R.M.; Deci, E.L. Intrinsic and Extrinsic Motivations: Classic Definitions and New Directions. Contemp. Educ. Psychol. 2000, 25, 54–67. [Google Scholar] [CrossRef]
- Kreijns, K.; Vermeulen, M.; van Acker, F.; van Buuren, H. Predicting Teachers’ Use of Digital Learning Materials: Combining Self-Determination Theory and the Integrative Model of Behaviour Prediction. Eur. J. Teach. Educ. 2014, 37, 465–478. [Google Scholar] [CrossRef]
- Karahanna, E.; Straub, D.W. The Psychological Origins of Perceived Usefulness and Ease-of-Use. Inf. Manag. 1999, 35, 237–250. [Google Scholar] [CrossRef]
- Lee, M.K.; Cheung, C.M.; Sia, C.L.; Lim, K.H. How Positive Informational Social Influence Affects Consumers’ Decision of Internet Shopping? In Proceedings of the 39th Annual Hawaii International Conference on System Sciences, 4–7 January; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2006; Volume 6, p. 115. [Google Scholar]
- Dong, X.; Chang, Y.; Wang, Y.; Yan, J. Understanding Usage of Internet of Things (IOT) systems in China. Inf. Technol. People 2017, 30, 117–138. [Google Scholar] [CrossRef]
- Venkatesh, V.; Thong, J.Y. Consumer Acceptance and Use of Information Technology: Extending the Unified Theory of Acceptance and Use of Technology. MIS Q. 2012, 36, 157. [Google Scholar] [CrossRef] [Green Version]
- Wang, H.-Y.; Wang, S.-H. User Acceptance of Mobile Internet Based on the Unified Theory of Acceptance and Use of Technology: Investigating the Determinants and Gender Differences. Soc. Behav. Pers. Int. J. 2010, 38, 415–426. [Google Scholar] [CrossRef]
- Weinberg, B.D.; Milne, G.R.; Andonova, Y.G.; Hajjat, F. Internet of Things: Convenience vs. Privacy and Secrecy. Bus. Horiz. 2015, 58, 615–624. [Google Scholar] [CrossRef]
- Roman, R.; Zhou, J.; Lopez, J. On the Features and Challenges of Security and Privacy in Distributed Internet of Things. Comput. Netw. 2013, 57, 2266–2279. [Google Scholar] [CrossRef]
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the Internet of Things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Waber, R.H. Internet of Things: Privacy issues Revisited. Comput. Law Secur. Rev. 2015, 31, 618–627. [Google Scholar] [CrossRef]
- Borgohain, T.; Kumar, U. A Survey on Security and Privacy Issues in Internet-of-Things. Int. J. Adv. Netw. Appl. 2015, 6, 2372–2378. [Google Scholar]
- AlBalawi, U.; Joshi, S. Secure and Trusted Telemedicine in Internet of Things IoT. In 2018 IEEE 4th World Forum on Internet of Things; IEEE: Berlin, Germany, 2018; pp. 30–34. [Google Scholar] [CrossRef]
- Chang, Y.; Dong, X.; Sun, W. Influence of Characteristics of the Internet of Things on Consumer Purchase Intention. Soc. Behav. Pers. Int. J. 2014, 42, 321–330. [Google Scholar] [CrossRef]
- Renko, M.; Kroeck, K.G.; Bullough, A. Expectancy Theory and Nascent Entrepreneurship. Small Bus. Econ. 2011, 39, 667–684. [Google Scholar] [CrossRef]
- Nasri, W.; Charfeddine, L. Motivating Salespeople to Contribute to Marketing Intelligence Activities: An Expectancy Theory Approach. Int. J. Mark. Stud. 2012, 4, 168. [Google Scholar] [CrossRef]
- Urdan, T. Book Review: Intrinsic Motivation, Extrinsic Rewards, and Divergent Views of Reality. Educ. Psychol. Rev. 2003, 15, 311–325. [Google Scholar] [CrossRef]
- Baudier, P.; Ammi, C.; Lecouteux, A. Employees’ Acceptance of the Healthcare Internet of Things: A Source of Innovation in Corporate Human Resource Policies. J. Innov. Econ. 2019, 30, 89–111. [Google Scholar] [CrossRef]
- Tran, T.D. An UTAUT Application-IoT Acceptance in Retail Digital Transformation. Available online: www.42gears.com (accessed on 20 December 2019).
- Evans, J.R.; Mathur, A. The Value of Online Surveys. Internet Res. 2005, 15, 195–219. [Google Scholar] [CrossRef]
- Mota, L.J.; Ramsden, A.E.; Liu, M.; Castle, J.D.; Holden, D.W. SCAMP3 Is a Component of the Salmonella-Induced Tubular Network and Reveals an Interaction Between Bacterial Effectors and Post-Golgi Trafficking. Cell. Microbiol. 2009, 11, 1236–1253. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Bharati, P.; Zhang, W.; Chaudhury, A. Better Knowledge with Social Media? Exploring the Roles of Social Capital and Organizational Knowledge Management. J. Knowl. Manag. 2015, 19, 456–475. [Google Scholar] [CrossRef]
- Chin, W.W. How to Write up and Report PLS Analyses. In Handbook of Partial Least Squares: Concepts, Methods, and Applications; Esposito, V.V., Chin, W.W., Henseler, J., Wang, H., Eds.; Springer Handbook of Computational Studies; Springer: Manhattan, NY, USA, 2010; pp. 655–690. [Google Scholar]
- Sarstedt, M. A Review of Recent Approaches for Capturing Heterogeneity in Partial Least Squares Path Modelling. J. Model. Manag. 2008, 3, 140–161. [Google Scholar] [CrossRef]
- Ringle, C.M.; Wende, S.; Becker, J.-M. SmartPLS Boenningstedt: SmartPLS GmbH. Available online: http://www.smartpls.com (accessed on 22 June 2019).
- Henseler, J.; Ringle, C.M.; Sarstedt, M. Testing Measurement Invariance of Composites Using Partial Least Squares. Int. Mark. Rev. 2016, 33, 405–431. [Google Scholar] [CrossRef]
- Hair, J.F.; Hult, G.T.M.; Ringle, C.M.; Sarstedt, M. A Primer on Partial Least Squares Structural Equation Modeling; Sage Publications: Thousand Oaks, CA, USA, 2014; pp. 3–32. [Google Scholar]
- Bagozzi, R.P.; Yi, Y. Advanced Topics in Structural Equation Models. In Advanced Methods of Marketing Research; Bagozzi R., P., Ed.; Blackwell: Oxford, UK, 1994; p. 151. [Google Scholar]
- Nunally, J.C. Psychometric Theory; McGraw Hill: New York, NY, USA, 1978; p. 640. [Google Scholar]
- Höck, C.; Ringle, C.M.; Sarstedt, M. Management of Multi-Purpose Stadiums: Importance and Performance Measurement of Service Interfaces. Int. J. Serv. Technol. Manag. 2010, 14, 188. [Google Scholar] [CrossRef]
- Henseler, J.; Sarstedt, M. Goodness-of-Fit Indices for Partial Least Squares Path Modeling. Comput. Stat. 2013, 28, 565–580. [Google Scholar] [CrossRef] [Green Version]
- Daskalakis, S.; Mantas, J. Evaluating the Impact of a Service-Oriented Framework for Healthcare Interoperability. In eHealth Beyond the Horizon—Get IT here: Proceedings of MIE 2008; Anderson, S.K., Klein, G.O., Schulz, S., Aarts, J., Mazzoleni, M.C., Eds.; IOS Press: Amsterdam, The Netherlands, 2008; pp. 285–290. [Google Scholar]
- Höck, M.; Ringle, C.M. Local Strategic Networks in the Software Industry: An Empirical Analysis of the Value Continuum. Int. J. Knowl. Manag. Stud. 2010, 4, 132. [Google Scholar] [CrossRef]
- Ringle, C.M.; Sarstedt, M.; Straub, D.W. A Critical Look at the Use of PLS-SEM. MIS Q. 2012, 36, iii. [Google Scholar] [CrossRef] [Green Version]
- Davies, A.M.C. Uncertainty Testing in PLS Regression. Spectrosc. Eur. 2001, 13, 16–19. [Google Scholar]
- Fornell, C.; Larcker, D.F. Evaluating Structural Equation Models with Unobservable Variables and Measurement Error. J. Mark. Res. 1981, 18, 39–50. [Google Scholar] [CrossRef]
- Henseler, J. On the Convergence of the Partial Least Squares Path Modeling Algorithm. Comput. Stat. 2009, 25, 107–120. [Google Scholar] [CrossRef] [Green Version]
- Hu, L.; Bentler, P.M. Cutoff Criteria for Fit Indexes in Covariance Structure Analysis: Conventional Criteria Versus New Alternatives. Struct. Equ. Model. Multidiscip. J. 1999, 6, 1–55. [Google Scholar] [CrossRef]
- Henseler, J.; Dijkstra, T.K.; Sarstedt, M.; Ringle, C.M.; Diamantopoulos, A.; Straub, D.W.; Ketchen, D.J.; Hair, J.F.; Hult, G.T.M.; Calantone, R.J. Common Beliefs and Reality About Partial Least Squares: Comments on Rönkkö & Evermann (2013). Organ. Res. Methods 2014, 17, 182–209. [Google Scholar]
- Cenfetelli, R.T.; Bassellier, G. Interpretation of Formative Measurement in Information Systems Research. MIS Q. 2009, 33, 689. [Google Scholar] [CrossRef]
- Henseler, J.; Ringle, C.M.; Sarstedt, M. A New Criterion for Assessing Discriminant Validity in Variance-Based Structural Equation Modeling. J. Acad. Mark. Sci. 2014, 43, 115–135. [Google Scholar] [CrossRef] [Green Version]
- Gold, A.H.; Malhotra, A.; Segars, A.H. Knowledge Management: An Organizational Capabilities Perspective. J. Manag. Inf. Syst. 2001, 18, 185–214. [Google Scholar] [CrossRef]
- Teo, T.S.H.; Srivastava, S.C.; Jiang, L. Trust and Electronic Government Success: An Empirical Study. J. Manag. Inf. Syst. 2008, 25, 99–132. [Google Scholar] [CrossRef]
- Clark, L.A.; Watson, D. Constructing Validity: Basic Issues in Objective Scale Development. Psychol. Assess. 1995, 7, 309–319. [Google Scholar] [CrossRef]
- Kline, R.B. Principles and Practice of Structural Equation Modeling, 3rd ed.; Guilford Press: New York, NY, USA, 2011. [Google Scholar]
- Tenenhaus, M.; Vinzi, V.E.; Chatelin, Y.-M.; Lauro, C. PLS Path Modeling. Comput. Stat. Data Anal. 2005, 48, 159–205. [Google Scholar] [CrossRef]
- Urbach, N.; Ahlemann, F. Structural Equation Modeling in Information Systems Research Using Partial Least Squares. J. Inf. Technol. Theory 2010, 11, 5–36. [Google Scholar]
- Stone, M. Cross-Validatory Choice and Assessment of Statistical Predictions. J. R. Stat. Soc. 1974, 36, 111–133. [Google Scholar] [CrossRef]
- Geisser, S. A Predictive Approach to the Random Effects Model. Biometrika 1974, 61, 101–107. [Google Scholar] [CrossRef]
- Martín-Ruiz, D.; Gremler, D.D.; Washburn, J.H.; Cepeda-Carrion, G. Reframing Customer Value in a Service-Based Paradigm: An Evaluation of a Formative Measure in a Multi-industry, Cross-cultural Context. In Handbook of Partial Least Squares; Springer Science and Business Media LLC: Berlin, Germany, 2009; pp. 535–566. [Google Scholar]
- Mukhtar, F.; Muis, K.; Elizov, M. Relations between Psychological Needs Satisfaction, Motivation, and Self-Regulated Learning Strategies in Medical Residents: A cross-sectional Study. MedEdPublish 2018, 7. [Google Scholar] [CrossRef] [Green Version]
- Chen, X.; Fang, S.; Li, Y.; Wang, H. Does Identification Influence Continuous E-Commerce Consumption? The Mediating Role of Intrinsic Motivations. Sustainability 2019, 11, 1944. [Google Scholar] [CrossRef] [Green Version]
- Cho, Y.J.; Perry, J. Intrinsic Motivation and Employee Attitudes Role of Managerial Trustworthiness, Goal Directedness, and Extrinsic Reward Expectancy. Rev. Public Pers. Adm. 2012, 32, 382–406. [Google Scholar] [CrossRef]
- Rönkkö, M.; Evermann, J. A Critical Examination of Common Beliefs About Partial Least Squares Path Modeling. Organ. Res. Methods 2013, 16, 425–448. [Google Scholar] [CrossRef]


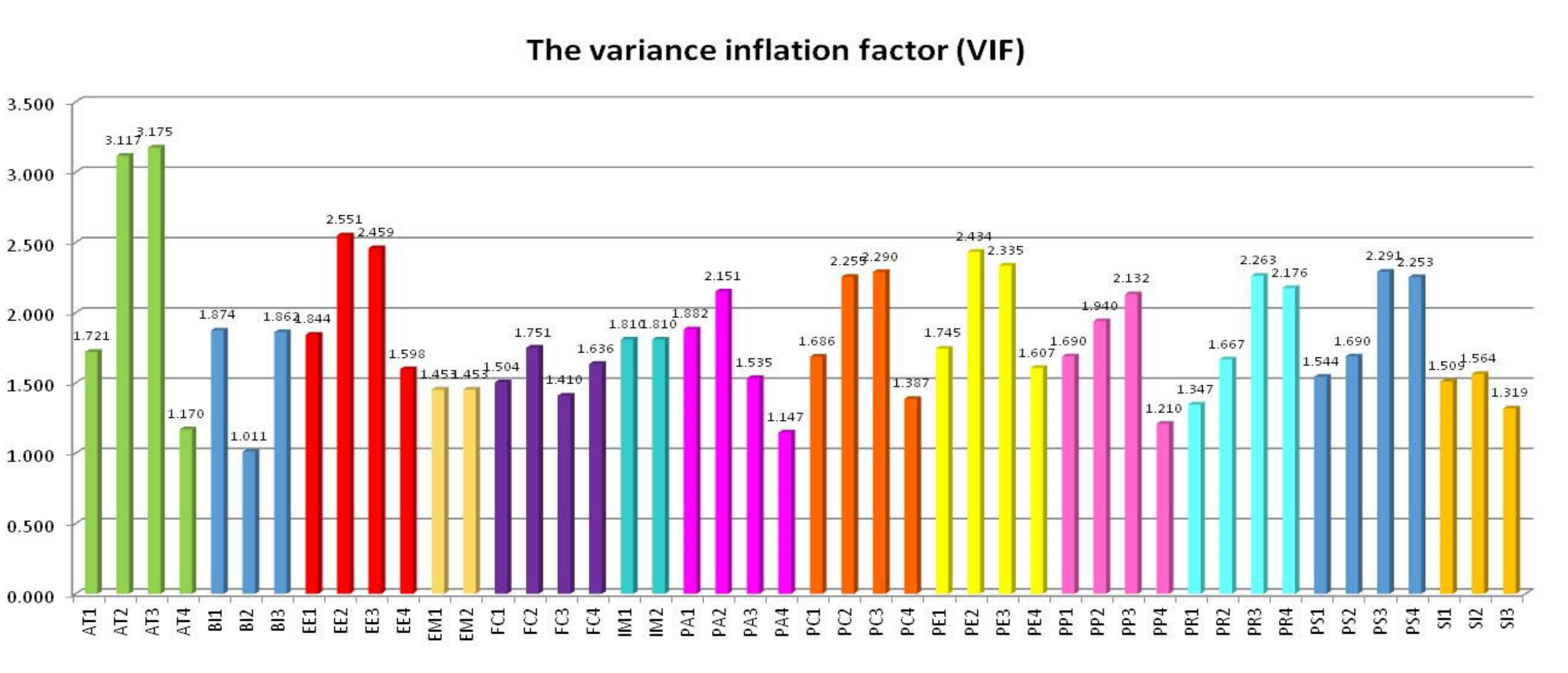
| Dimensions | Frequency | Percentage | |
|---|---|---|---|
| Gender | Male | 261 | 62.74 |
| Female | 155 | 37.26 | |
| Age | Between 20 and 30 years | 53 | 12.74 |
| Between 31 and 40 years | 104 | 25.00 | |
| Between 41 and 50 years | 151 | 36.30 | |
| Between 51 and 60 years | 80 | 19.23 | |
| Upper 60 years | 28 | 6.73 | |
| Education Level | Primary education | 18 | 4.33 |
| High school | 60 | 14.42 | |
| University | 214 | 51.44 | |
| Master/PhD | 119 | 28.61 | |
| Other | 5 | 1.20 | |
| Management Level | Top-Level Management | 60 | 14.42 |
| Middle-Level Management | 203 | 48.80 | |
| Lower-Level Management | 153 | 36.78 | |
| Work Experience | Less than 5 years | 28 | 6.73 |
| Between 5 and 10 years | 187 | 44.95 | |
| Between 11 and 16 years | 129 | 31.01 | |
| More than 16 years | 72 | 17.31 | |
| Industry | Automotive and Consumer Electronics | 23 | 5.53 |
| Healthcare and Hospitality | 12 | 2.88 | |
| Retail | 101 | 24.28 | |
| Discrete and Process Manufacturing | 135 | 32.45 | |
| Finance services | 16 | 3.85 | |
| Energy and Natural Resources | 7 | 1.68 | |
| Communications | 13 | 3.13 | |
| Transportation and Logistics | 59 | 14.18 | |
| Construction and Utilities | 38 | 9.13 | |
| Agriculture/Agrotech/farming | 9 | 2.16 | |
| Other | 3 | 0.72 | |
| Location | AB | 7 | 1.68 |
| AR | 10 | 2.40 | |
| AG | 12 | 2.88 | |
| BC | 9 | 2.16 | |
| BH | 6 | 1.44 | |
| BN | 7 | 1.68 | |
| BT | 4 | 0.96 | |
| BV | 3 | 0.72 | |
| BR | 11 | 2.64 | |
| B | 114 | 27.40 | |
| BZ | 5 | 1.20 | |
| CS | 6 | 1.44 | |
| CL | 2 | 0.48 | |
| CJ | 17 | 4.09 | |
| CT | 11 | 2.64 | |
| CV | 6 | 1.44 | |
| DB | 5 | 1.20 | |
| DJ | 9 | 2.16 | |
| GL | 13 | 3.13 | |
| GR | 5 | 1.20 | |
| GJ | 1 | 0.24 | |
| HR | 3 | 0.72 | |
| HD | 4 | 0.96 | |
| IL | 9 | 2.16 | |
| IS | 5 | 1.20 | |
| IF | 27 | 6.49 | |
| MM | 9 | 2.16 | |
| MH | 3 | 0.72 | |
| MS | 8 | 1.92 | |
| NT | 5 | 1.20 | |
| OT | 7 | 1.68 | |
| PH | 16 | 3.85 | |
| SJ | 1 | 0.24 | |
| SM | 3 | 0.72 | |
| SB | 13 | 3.13 | |
| SV | 5 | 1.20 | |
| TR | 2 | 0.48 | |
| TM | 15 | 3.61 | |
| TL | 3 | 0.72 | |
| VS | 7 | 1.68 | |
| VL | 2 | 0.48 | |
| VN | 6 | 1.44 | |
| Total | 416 | 100 |
| Items | Questions |
|---|---|
| Effort Expectancy (EE) | (EE1) Learning how to use IoT solutions would be easy for me |
| (EE2) I think I could easily use IoT solutions | |
| (EE3) My interaction with IoT solutions would be clear and easy to understand | |
| (EE4) I think it would be easy for me to become proficient in monitoring, controlling and using IoT solutions | |
| Attitude Towards IoT (AT) | (AT1) Using robust IoT solutions will make my job a lot easier |
| (AT2) I am interested in understanding and using IoT solutions | |
| (AT3) I like to use IoT solutions because they involve many challenges | |
| (AT4) I am happy when I use IoT solutions because it allows me to monitor and control the ecosystem | |
| Perceived Autonomy (PA) | (PA1) Using IoT solutions, I will have new options and opportunities for developing the desired activities |
| (PA2) I feel that using IoT solutions will allow me to better coordinate activities at work | |
| (PA3) Using IoT solutions can reduce the number of decisions I have to make to get optimal results | |
| (PA4) By using IoT solutions, I have the freedom to monitor and control a wide range of devices remotely | |
| Perceived Competence (PC) | I think I’m pretty good at connecting devices and using IoT solutions |
| I think I have the skills to build IoT solutions if I attend specific courses; | |
| I think I am quite good at getting involved in a programming project on the development of IoT solutions in the future | |
| I think I’m good at managing IoT solutions | |
| Perceived Relatedness (PR) | (PR1) When I use IoT solutions, I feel closer to my colleagues and business partners |
| PR2 When I use IoT solutions, I feel better understood by colleagues and business partners | |
| PR4 When I use IoT solutions, I am better listened to by colleagues and business partners | |
| PR4 When I use IoT solutions, I feel more connected to colleagues and business partners | |
| Intrinsic Motivation (IM) | (IM1) When I use IoT solutions, I feel involvement, pleasure and satisfaction |
| (IM2) When I use IoT solutions, I can easily master any task | |
| Performance Expectancy (PE) | (PE1) IoT solutions are useful both for my daily life and for my job |
| (PE2) IoT solutions help me quickly accomplish work tasks | |
| (PE3) IoT solutions would increase the productivity of my work | |
| (PE4) IoT solutions allow me to acquire new interpersonal skills in programming with a direct impact on increasing my morale | |
| Facilitating Conditions (FC) | (FC1) To use IoT solutions, they have all the necessary resources: skills and knowledge |
| (FC2) I have the necessary knowledge to use IoT solutions (IoT Developer Guide and/or exploring classical/online learning modules) | |
| (FC3) Using IoT solutions are useful for exchanging ideas in the IoT partner community | |
| (FC4) I benefit of IoT consulting and technical support | |
| Social Influence (SI) | (SI1) People who are important to me have given me useful tips and information about using IoT solutions |
| (SI2) People who are important to me have helped me find the best IoT solutions | |
| (SI3) People who are important to me have given me the support I need to use IoT solutions | |
| (SI4) People who are important to me believe that I have the skills to become a partner in providing IoT solutions | |
| Perceived Privacy (PP) | (PP1) When I use IoT solutions, I feel that other systems would have control over my work |
| (PP2) When I use IoT solutions, I feel that there are certain risks when it comes to manipulating information | |
| (PP3) When I use IoT solutions, from reputable manufacturers I feel that my information is safe/secure | |
| (PP4) When I use strong password-protected IoT solutions, I have the security of my information | |
| Perceived Security (PS) | (PS1) When I use IoT solutions, I feel protected by unauthorized access to other systems |
| (PS2) When I use IoT solutions, additional methods of verifying my access are used | |
| (PS3) When I use IoT solutions, I feel protected by the use of encryption technologies | |
| (PS4) When I use IoT solutions, the website has a data security policy through which it assumes responsibility | |
| Extrinsic Motivation (EM) | (EM1) When I use IoT solutions, I feel that I contribute to my success |
| (EM2) When I use IoT solutions, I feel the recognition of personal achievements | |
| Behavioral Intention (BI) | (B1) I intend to use IoT solutions in the future |
| (B2) I plan to use IoT solutions in the future/year | |
| B3) I foresee the use of IoT solutions in the future |
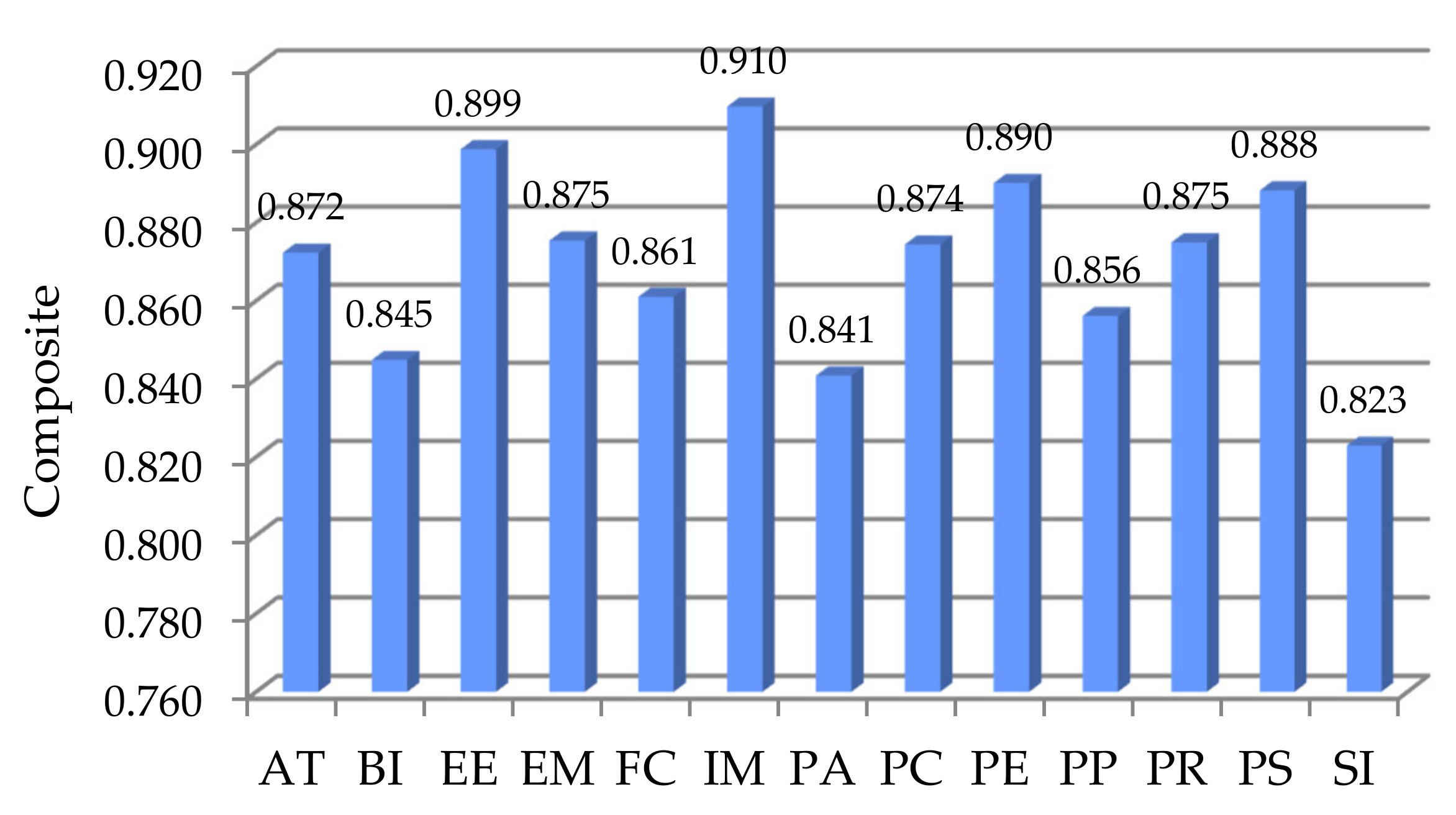
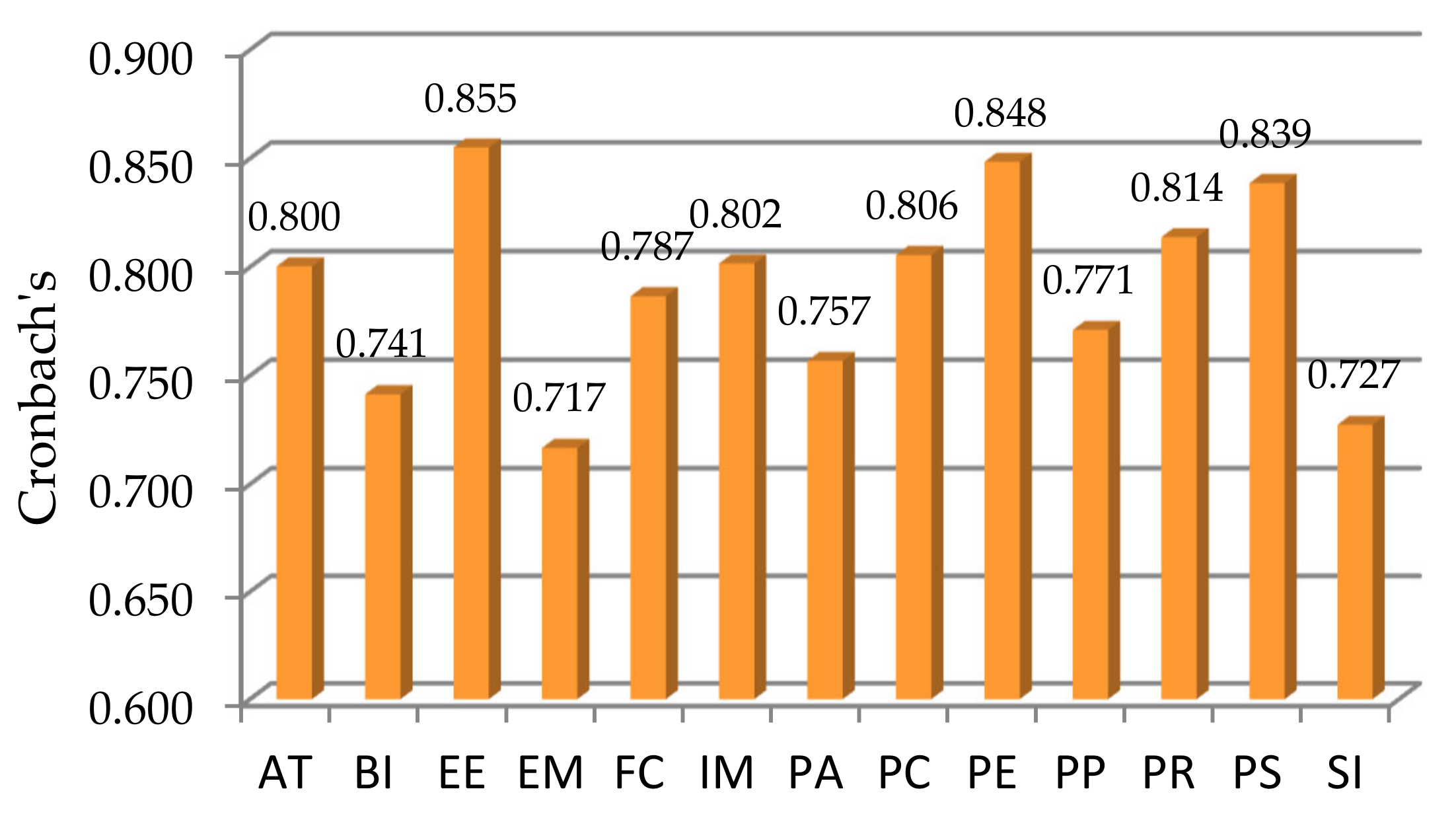
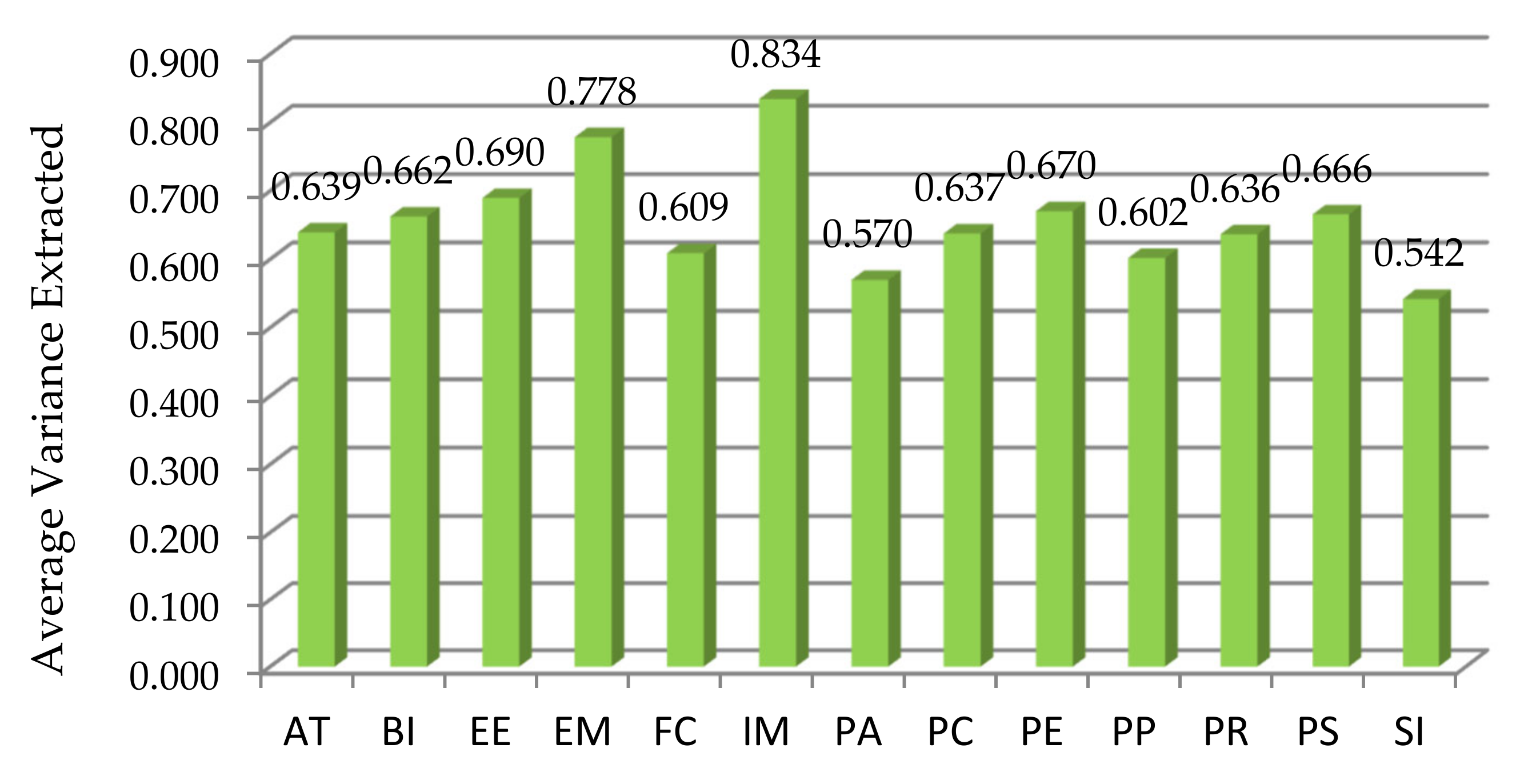
| Latent Variables | Cronbach’s Alpha (CA) | Composite Reliability | Average Variance Extracted (AVE) |
|---|---|---|---|
| AT | 0.800 | 0.872 | 0.639 |
| BI | 0.741 | 0.845 | 0.662 |
| EE | 0.855 | 0.899 | 0.690 |
| EM | 0.717 | 0.875 | 0.778 |
| FC | 0.787 | 0.861 | 0.609 |
| IM | 0.802 | 0.910 | 0.834 |
| PA | 0.757 | 0.841 | 0.570 |
| PC | 0.806 | 0.874 | 0.637 |
| PE | 0.848 | 0.890 | 0.670 |
| PP | 0.771 | 0.856 | 0.602 |
| PR | 0.814 | 0.875 | 0.636 |
| PS | 0.839 | 0.888 | 0.666 |
| SI | 0.727 | 0.823 | 0.542 |
| AT | BI | EE | EM | FC | IM | PA | PC | PE | PP | PR | PS | SI | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| AT | 0.800 | ||||||||||||
| BI | 0.354 | 0.750 | |||||||||||
| EE | 0.408 | 0.442 | 0.830 | ||||||||||
| EM | 0.394 | 0.529 | 0.503 | 0.882 | |||||||||
| FC | 0.238 | 0.362 | 0.271 | 0.383 | 0.780 | ||||||||
| IM | 0.421 | 0.558 | 0.555 | 0.543 | 0.282 | 0.913 | |||||||
| PA | 0.261 | 0.365 | 0.244 | 0.320 | 0.351 | 0.372 | 0.755 | ||||||
| PC | 0.417 | 0.534 | 0.552 | 0.512 | 0.349 | 0.542 | 0.387 | 0.798 | |||||
| PE | 0.472 | 0.506 | 0.583 | 0.563 | 0.342 | 0.574 | 0.258 | 0.539 | 0.819 | ||||
| PP | 0.239 | 0.419 | 0.374 | 0.491 | 0.262 | 0.358 | 0.252 | 0.596 | 0.515 | 0.776 | |||
| PR | 0.463 | 0.559 | 0.557 | 0.530 | 0.346 | 0.533 | 0.342 | 0.588 | 0.525 | 0.593 | 0.798 | ||
| PS | 0.372 | 0.564 | 0.594 | 0.577 | 0.427 | 0.475 | 0.289 | 0.515 | 0.582 | 0.508 | 0.563 | 0.816 | |
| SI | 0.236 | 0.382 | 0.406 | 0.473 | 0.296 | 0.330 | 0.257 | 0.354 | 0.380 | 0.288 | 0.358 | 0.458 | 0.736 |
| AT | BI | EE | EM | FC | IM | PA | PC | PE | PP | PR | PS | SI | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| AT1 | 0.764 | 0.288 | 0.258 | 0.201 | 0.238 | 0.257 | 0.134 | 0.342 | 0.315 | 0.185 | 0.313 | 0.265 | 0.216 |
| AT2 | 0.904 | 0.280 | 0.326 | 0.339 | 0.179 | 0.343 | 0.167 | 0.336 | 0.382 | 0.171 | 0.358 | 0.269 | 0.236 |
| AT3 | 0.928 | 0.333 | 0.440 | 0.481 | 0.200 | 0.458 | 0.195 | 0.414 | 0.419 | 0.250 | 0.418 | 0.438 | 0.173 |
| AT4 | 0.843 | 0.226 | 0.221 | 0.115 | 0.167 | 0.219 | 0.427 | 0.204 | 0.213 | 0.139 | 0.209 | 0.137 | 0.146 |
| BI1 | 0.294 | 0.885 | 0.360 | 0.444 | 0.380 | 0.405 | 0.311 | 0.499 | 0.418 | 0.468 | 0.412 | 0.462 | 0.426 |
| BI2 | 0.244 | 0.831 | 0.341 | 0.280 | 0.053 | 0.334 | 0.190 | 0.021 | 0.391 | 0.083 | 0.046 | 0.141 | 0.091 |
| BI3 | 0.348 | 0.942 | 0.440 | 0.372 | 0.299 | 0.449 | 0.349 | 0.488 | 0.426 | 0.323 | 0.515 | 0.410 | 0.295 |
| EE1 | 0.220 | 0.265 | 0.785 | 0.255 | 0.163 | 0.377 | 0.169 | 0.501 | 0.445 | 0.285 | 0.493 | 0.434 | 0.211 |
| EE2 | 0.282 | 0.346 | 0.854 | 0.287 | 0.169 | 0.376 | 0.186 | 0.548 | 0.464 | 0.323 | 0.537 | 0.474 | 0.285 |
| EE3 | 0.289 | 0.393 | 0.840 | 0.244 | 0.213 | 0.369 | 0.174 | 0.549 | 0.417 | 0.280 | 0.494 | 0.425 | 0.333 |
| EE4 | 0.476 | 0.428 | 0.841 | 0.201 | 0.304 | 0.320 | 0.251 | 0.560 | 0.562 | 0.338 | 0.515 | 0.583 | 0.449 |
| EM1 | 0.452 | 0.455 | 0.432 | 0.900 | 0.378 | 0.563 | 0.287 | 0.480 | 0.383 | 0.465 | 0.546 | 0.588 | 0.494 |
| EM2 | 0.227 | 0.480 | 0.344 | 0.864 | 0.293 | 0.572 | 0.278 | 0.421 | 0.473 | 0.397 | 0.454 | 0.569 | 0.331 |
| FC1 | 0.192 | 0.238 | 0.189 | 0.263 | 0.749 | 0.168 | 0.217 | 0.256 | 0.213 | 0.226 | 0.225 | 0.294 | 0.238 |
| FC2 | 0.198 | 0.329 | 0.193 | 0.313 | 0.826 | 0.240 | 0.254 | 0.258 | 0.266 | 0.153 | 0.264 | 0.336 | 0.216 |
| FC3 | 0.184 | 0.243 | 0.177 | 0.232 | 0.704 | 0.166 | 0.287 | 0.198 | 0.235 | 0.160 | 0.234 | 0.265 | 0.211 |
| FC4 | 0.177 | 0.308 | 0.270 | 0.364 | 0.833 | 0.280 | 0.331 | 0.351 | 0.335 | 0.268 | 0.338 | 0.411 | 0.259 |
| IM1 | 0.468 | 0.581 | 0.573 | 0.580 | 0.274 | 0.918 | 0.334 | 0.550 | 0.532 | 0.363 | 0.571 | 0.496 | 0.366 |
| IM2 | 0.296 | 0.622 | 0.430 | 0.595 | 0.241 | 0.908 | 0.345 | 0.438 | 0.410 | 0.289 | 0.480 | 0.368 | 0.232 |
| PA1 | 0.187 | 0.201 | 0.148 | 0.179 | 0.212 | 0.212 | 0.755 | 0.196 | 0.128 | 0.168 | 0.144 | 0.140 | 0.207 |
| PA2 | 0.206 | 0.261 | 0.166 | 0.203 | 0.227 | 0.260 | 0.814 | 0.206 | 0.161 | 0.097 | 0.168 | 0.157 | 0.198 |
| PA3 | 0.174 | 0.202 | 0.111 | 0.192 | 0.260 | 0.228 | 0.725 | 0.217 | 0.184 | 0.098 | 0.249 | 0.167 | 0.137 |
| PA4 | 0.209 | 0.371 | 0.261 | 0.334 | 0.322 | 0.365 | 0.721 | 0.452 | 0.261 | 0.326 | 0.391 | 0.335 | 0.218 |
| PC1 | 0.323 | 0.368 | 0.573 | 0.399 | 0.304 | 0.424 | 0.319 | 0.768 | 0.565 | 0.493 | 0.510 | 0.530 | 0.252 |
| PC2 | 0.387 | 0.474 | 0.507 | 0.439 | 0.325 | 0.451 | 0.363 | 0.861 | 0.596 | 0.555 | 0.513 | 0.580 | 0.328 |
| PC3 | 0.352 | 0.527 | 0.535 | 0.380 | 0.312 | 0.468 | 0.329 | 0.875 | 0.503 | 0.461 | 0.499 | 0.494 | 0.328 |
| PC4 | 0.260 | 0.317 | 0.351 | 0.425 | 0.160 | 0.384 | 0.212 | 0.873 | 0.362 | 0.388 | 0.471 | 0.345 | 0.213 |
| PE1 | 0.249 | 0.290 | 0.445 | 0.350 | 0.196 | 0.327 | 0.169 | 0.483 | 0.740 | 0.466 | 0.516 | 0.568 | 0.183 |
| PE2 | 0.345 | 0.397 | 0.482 | 0.396 | 0.239 | 0.391 | 0.214 | 0.539 | 0.835 | 0.546 | 0.494 | 0.625 | 0.257 |
| PE3 | 0.342 | 0.446 | 0.444 | 0.375 | 0.298 | 0.398 | 0.223 | 0.538 | 0.820 | 0.513 | 0.561 | 0.586 | 0.285 |
| PE4 | 0.403 | 0.478 | 0.522 | 0.398 | 0.339 | 0.523 | 0.230 | 0.544 | 0.874 | 0.512 | 0.523 | 0.527 | 0.419 |
| PP1 | 0.151 | 0.293 | 0.355 | 0.358 | 0.208 | 0.317 | 0.202 | 0.478 | 0.518 | 0.758 | 0.503 | 0.491 | 0.170 |
| PP2 | 0.173 | 0.360 | 0.317 | 0.421 | 0.236 | 0.269 | 0.246 | 0.483 | 0.504 | 0.850 | 0.504 | 0.567 | 0.262 |
| PP3 | 0.215 | 0.442 | 0.325 | 0.383 | 0.270 | 0.308 | 0.214 | 0.520 | 0.517 | 0.857 | 0.517 | 0.509 | 0.296 |
| PP4 | 0.203 | 0.186 | 0.153 | 0.351 | 0.086 | 0.213 | 0.108 | 0.359 | 0.357 | 0.714 | 0.299 | 0.297 | 0.154 |
| PR1 | 0.450 | 0.479 | 0.560 | 0.355 | 0.294 | 0.544 | 0.296 | 0.506 | 0.414 | 0.387 | 0.779 | 0.539 | 0.387 |
| PR2 | 0.268 | 0.329 | 0.493 | 0.345 | 0.224 | 0.408 | 0.221 | 0.401 | 0.537 | 0.464 | 0.767 | 0.551 | 0.161 |
| PR3 | 0.349 | 0.444 | 0.527 | 0.408 | 0.259 | 0.448 | 0.281 | 0.549 | 0.412 | 0.551 | 0.833 | 0.430 | 0.243 |
| PR4 | 0.363 | 0.502 | 0.493 | 0.374 | 0.312 | 0.446 | 0.275 | 0.459 | 0.581 | 0.523 | 0.810 | 0.590 | 0.293 |
| PS1 | 0.416 | 0.492 | 0.513 | 0.462 | 0.336 | 0.536 | 0.250 | 0.491 | 0.591 | 0.476 | 0.531 | 0.839 | 0.465 |
| PS2 | 0.164 | 0.325 | 0.451 | 0.455 | 0.284 | 0.262 | 0.152 | 0.467 | 0.562 | 0.469 | 0.573 | 0.747 | 0.245 |
| PS3 | 0.277 | 0.463 | 0.491 | 0.537 | 0.359 | 0.322 | 0.248 | 0.532 | 0.543 | 0.543 | 0.451 | 0.840 | 0.350 |
| PS4 | 0.275 | 0.531 | 0.473 | 0.534 | 0.420 | 0.328 | 0.276 | 0.531 | 0.628 | 0.518 | 0.537 | 0.834 | 0.368 |
| SI1 | 0.184 | 0.296 | 0.284 | 0.326 | 0.267 | 0.223 | 0.162 | 0.288 | 0.282 | 0.220 | 0.263 | 0.373 | 0.767 |
| SI2 | 0.279 | 0.307 | 0.370 | 0.498 | 0.233 | 0.339 | 0.220 | 0.303 | 0.370 | 0.205 | 0.339 | 0.400 | 0.872 |
| SI3 | -0.041 | 0.224 | 0.164 | 0.186 | 0.103 | 0.148 | 0.101 | 0.135 | 0.127 | 0.178 | 0.119 | 0.217 | 0.717 |
| SI4 | 0.145 | 0.304 | 0.330 | 0.274 | 0.249 | 0.198 | 0.260 | 0.283 | 0.267 | 0.277 | 0.272 | 0.321 | 0.862 |
| Hypothesis | Correlation | β | T-Statistics | p-Values | Decision |
|---|---|---|---|---|---|
| H1 | EE - > IM | 0.175 | 2.407 | 0.016 | Supported |
| H2 | AT - > IM | 0.079 | 1.186 | 0.236 | No Supported |
| H3 | PA - > IM | 0.123 | 2.484 | 0.013 | Supported |
| H4 | PC - > IM | −0.010 | 0.110 | 0.912 | No Supported |
| H5 | PR - > IM | 0.231 | 2.031 | 0.043 | Supported |
| H6 | PE - > EM | 0.136 | 2.793 | 0.024 | Supported |
| H7 | SI - > EM | 0.139 | 3.426 | 0.001 | Supported |
| H8 | FC - > EM | 0.044 | 0.968 | 0.333 | No Supported |
| H9 | PP - > EM | −0.004 | 0.057 | 0.954 | No Supported |
| H10 | PS - > EM | 0.590 | 6.759 | 0.000 | Supported |
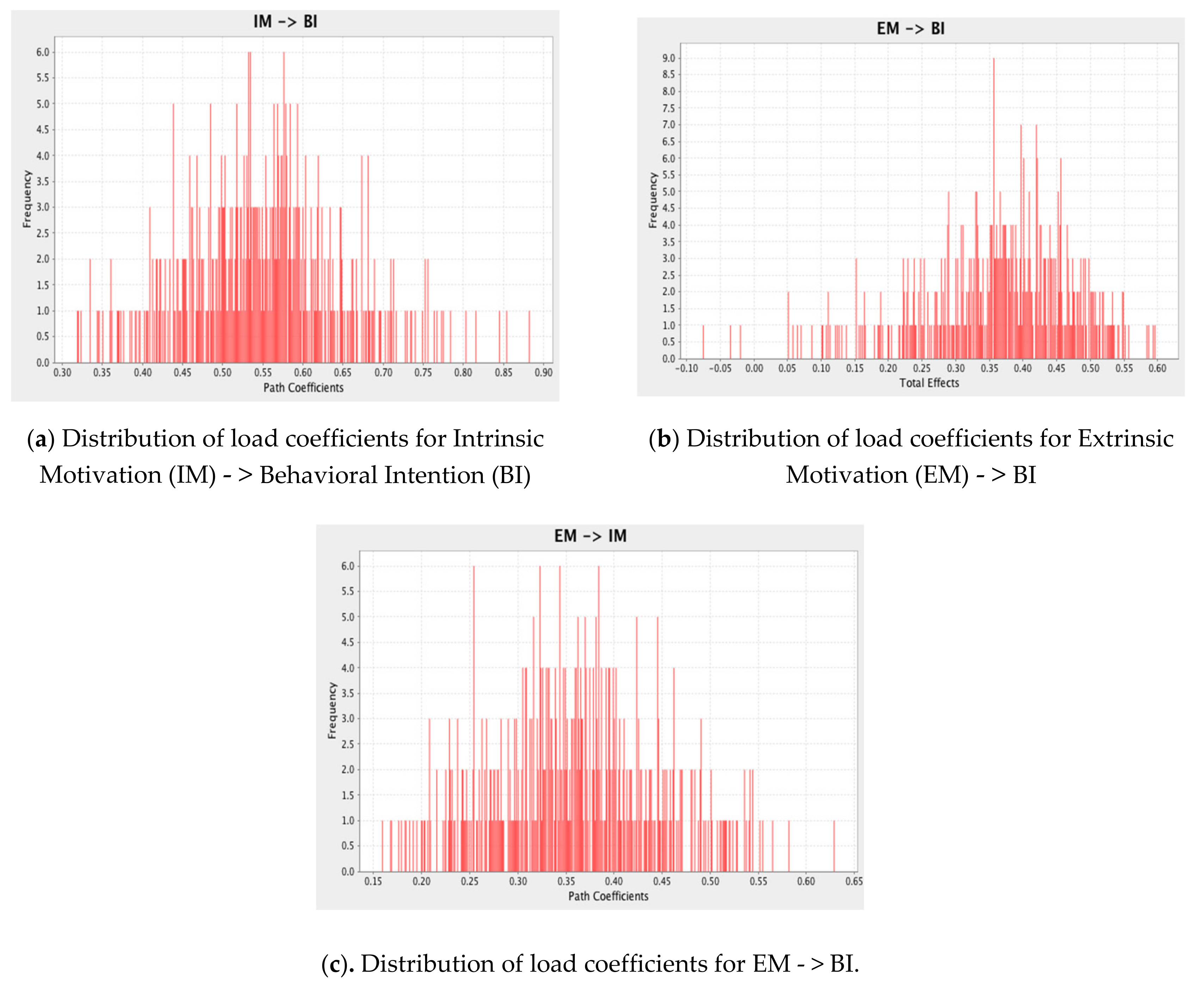
| H11 | EM - > BI | 0.180 | 1.511 | 0.131 | No Supported |
| H12 | EM - > IM | 0.344 | 4.149 | 0.000 | Supported |
| H13 | IM - > BI | 0.542 | 5.879 | 0.000 | Supported |
| R2 | R2 Adjusted | Q² | |
|---|---|---|---|
| BI | 0.452 | 0.449 | 0.230 |
| EM | 0.630 | 0.625 | 0.462 |
| IM | 0.538 | 0.531 | 0.422 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tűrkeș, M.C.; Căpușneanu, S.; Topor, D.I.; Staraș, A.I.; Hint, M.Ș.; Stoenica, L.F. Motivations for the Use of IoT Solutions by Company Managers in the Digital Age: A Romanian Case. Appl. Sci. 2020, 10, 6905. https://doi.org/10.3390/app10196905
Tűrkeș MC, Căpușneanu S, Topor DI, Staraș AI, Hint MȘ, Stoenica LF. Motivations for the Use of IoT Solutions by Company Managers in the Digital Age: A Romanian Case. Applied Sciences. 2020; 10(19):6905. https://doi.org/10.3390/app10196905
Chicago/Turabian StyleTűrkeș, Mirela Cătălina, Sorinel Căpușneanu, Dan Ioan Topor, Adela Ioana Staraș, Mihaela Ștefan Hint, and Laurentiu Florentin Stoenica. 2020. "Motivations for the Use of IoT Solutions by Company Managers in the Digital Age: A Romanian Case" Applied Sciences 10, no. 19: 6905. https://doi.org/10.3390/app10196905
APA StyleTűrkeș, M. C., Căpușneanu, S., Topor, D. I., Staraș, A. I., Hint, M. Ș., & Stoenica, L. F. (2020). Motivations for the Use of IoT Solutions by Company Managers in the Digital Age: A Romanian Case. Applied Sciences, 10(19), 6905. https://doi.org/10.3390/app10196905









