Abstract
Smart grids incorporating internet-of-things are emerging solutions to provide a reliable, sustainable and efficient electricity supply, and electric vehicle drivers can access efficient charging services in the smart grid. However, traditional electric vehicle charging systems are vulnerable to distributed denial of service and privileged insider attacks when the central charging server is attacked. The blockchain-based charging systems have been proposed to resolve these problems. In 2018, Huang et al. proposed the electric vehicle charging system using lightning network and smart contract. However, their system has an inefficient charging mechanism and does not guarantee security of key. We propose a secure charging system for electric vehicles based on blockchain to resolve these security flaws. Our charging system ensures the security of key, secure mutual authentication, anonymity, and perfect forward secrecy, and also provides efficient charging. We demonstrate that our proposed system provides secure mutual authentication using Burrows–Abadi–Needham logic and prevents replay and man-in-the-middle attacks using automated validation of internet security protocols and applications simulation tool. Furthermore, we compare computation and communication costs with previous schemes. Therefore, the proposed charging system efficiently applies to practical charging systems for electric vehicles.
1. Introduction
With widespread adoption of electric vehicles (EVs) and internet-of-things (IoT), smart grids with IoT have become promising solutions to control distributed energy and electricity generation [1]. Internet-of-things is applicable to various forms for vehicular systems, such as vehicular ad hoc networks, vehicle to grid (V2G), vehicle to vehicle (V2V), and internet of vehicle (IoV). Vehicles generally have various communication and measuring sensors, including speed, position, Bluetooth, Wi-Fi and On-board units (OBU). The sensors in vehicle collect and share data such as speed, location, identity and movements. However, an adversary can intercept, modify and reuse the sensitive data of user, and then try to obatin user’s sensitive data because it is transmitted via public network. Therefore, secure mutual authentication and key agreement must be guaranteed to provide secure communication and protect user’s privacy.
In the past decades, the numerous authentication and key agreement schemes for vehicular systems in IoT have been studied to achieve essential security requirements [2,3,4,5,6,7,8,9,10]. Although these schemes try to ensure privacy and enhance efficiency, their scheme is vulnerable to various potential attacks such as distributed denial of service and privileged insider attacks because it is based on trusted third party to provide high security level. If the trusted third party is compromised, their schemes cannot provide services. For these reasons, authenticaion and key agreement schemes without a trusted third party must be proposed to achieve integrity, confidentiality, availability and reliability, considering resource-constrained devices
The smart grid provides reliable, sustainable, stable, and efficient electricity supply. EV charging management is a particularly important issue for smart grids, and related studies have been proposed [11,12,13,14,15,16], providing EV charging for users when they want to use it. However, traditional smart grid systems provide charging services based on a third party and are vulnerable to various attacks, including distributed denial of service and privileged insider attacks. If the third party is compromised, users cannot use EV charging, and smart grid systems with IoT must also consider efficiency, because EV sensors as OBU in EV also have low power and small memory.
Several studies have proposed blockchain approaches to overcome these security weaknesses and enhance efficiency [17,18,19,20,21,22]. Blockchain [17] technology guarantees decentralization, verification, and integrity, and is applicable to various fields, including smart grids, healthcare, finance, markets, and voting. Generally, blockchains consists of data blocks, called transactions, where each transaction includes data regarding previous transactions using a hash algorithm [18]. However, early blockchain studies focused on cryptocurrency, e.g., Bitcoin and Ethereum, which have significant scalability problems. Hyperledgers [19], which do not generate cryptocurrency, have been proposed to overcome these problems and solve scalability. Huang et al. [20] proposed blockchain based EV charging management security model using smart contracts and the lightning network.
This paper demonstrates that Huang et al.’s charging system [20] has inefficient charging mechanisms such as the deposit problem, generating transaction and cost of transaction fee. Huang et al.’s system also does not guarantee security of keys. Consequently, we propose a secure charging system for electric vehicles using a hyperledger to improve security and efficiency. Our main contributions are as follows.
- (1)
- We demonstrate security weaknesses of Huang et al.’s model, and highlight its inefficiencies.
- (2)
- We propose a secure charging system for EV based on blockchain to solve these security weaknesses and improve efficiency.
- (3)
- We perform informal analysis to demonstrate the proposed system is secure against various attacks, and prove that it provides secure mutual authentication using Burrows–Abadi–Needham (BAN) logic. We also perform formal security verification using the AVISPA tool and compare performances with previous schemes.
- (4)
- We analyze the computational and communication costs compared with other related existing schemes.
1.1. Organization
The remainder of this paper is organized as follows. Section 2 introduces the proposed blockchain-based EV charging model. Section 3 and Section 4 review Huang et al.’s scheme and analyze its security flaws. Section 5 proposes a secure charging system for EV based on blockchain. Section 6 provides informal analysis to verify the proposed system’s security and proves that the system mutual authentication using BAN logic. We also demonstrate that the proposed system is secure against replay and man-in-the-middle attacks using the AVISPA simulation tool. Section 7 compares the proposed system’s performance with related previous schemes. Finally, Section 8 summarizes and concludes the paper.
1.2. Related Works
There are several authentication and key agreement schemes for wireless sensor networks to resolve privacy and security issues [23,24,25,26]. In 2011, Roman et al. [23] analyzed existing authentication and key management schemes for WSN in IoT to enhance security and performance. In 2014, Turkanovic et al. [24] first proposed an authentication and key agreement scheme based on IoT considering resource-constrained devices. However, in 2016, Amin et al. [25] showed that Turkanovic et al.’s scheme was vulnerable to smart card theft, offline identity-password guessing and user impersonation attacks, and proposed an enhanced authentication scheme to overcome these security problems. However, Lu [26] et al. pointed out that Amin et al.’s scheme did not prevent known session-specific temporary information attack and proposed improved authentication and key agreement scheme using symmetric key.
Numerous privacy protection schemes for a vehicular system in IoT ensure security and improve efficiency [2,3,4,5,6,7,8,9,10]. In 2016, Lo and Tasi [2] proposed an efficient authentication scheme for vehicular sensor networks to improve performance. Kumari et al. [3] also proposed a secure trust-extended authentication scheme for vehicular ad-hoc networks to ensure authenticity of messages. In 2017, Chin et al. [4] discussed the security vulnerabilities in the internet-of-things-based smart grid and Liu et al. [5] proposed efficient dual authentication and key agreement scheme in IoV. Mohit et al. [6] also proposed authentication protocol for smart vehicular system in IoT considering energy efficiency of sensor and Guo et al. [7] proposed secure information collection scheme for big data in large scale IoV. Zhou et al. [8] proposed an enhanced privacy-preserving authentication scheme for vehicle sensor network to overcome security weaknesses of the Kumari et al.’s scheme [3]. In 2018, Shen et al. [9] proposed privacy-preserving and lightweight key agreement scheme for V2G in social IoT to guarantee security of smart grid. In 2019, Wu et al. [10] proposed mutual authentication scheme for V2V in vehicular ad hoc network to achieve better performance and security.
Several previous studies have considered EV charging systems [11,12,13,14,15,16]. In 2013, Gan et al. [11] proposed a decentralized protocol for EV charging to improve charging efficiency. In 2016, Xu et al. [12] proposed dynamic EV scheduling using less laxity and longer remaining processing time principle. In 2010 and 2012, Lu et al. [13] and Kim et al. [14] proposed scheduling mechanisms to reduce waiting times at charging stations. In 2016, Tian et al. [15] proposed recommendation system in real-time to provide charging station information. Tang and Zhang [16] proposed a low complexity EV charging scheduling algorithm using near optimal solutions.
Many studies have guaranteed decentralization, verification, and integrity [17,19,21,22,27]. However, initial blockchain models have scalability problems. Lightning network [21] and hyperledger [19] networks have been proposed to overcome this problem and improve efficiency. Lightning networks establish trading channels outside the main blockchain to enhance network performance. Hyperledger solves scalability problem and removes the requirement for cryptocurrency transactions to enhance the performances. These systems incorporate smart contracts, a set of commitments, that improve performance and privacy without requiring a trusted third party [22,27].
Several blockchain-based EV charging management systems have been proposed to improve performance [20,28,29,30]. In 2017, Dubois et al. [28] proposed an app-based blockchain system using smart contracts to provide a charging service between EVs and charging stations without requiring a trusted third party. Knirsch et al. [29] proposed an EV charging system where the EV finds the best charging station by bidding on the blockchain. Li et al. [30] proposed a consortium blockchain for energy trading in the industrial IoT to guarantee fast and reliable energy trading using the Stackelberg game. In 2018, Huang et al. [20] proposed a blockchain-based EV charging management security model, incorporating authentication mechanisms using smart contracts and the lightning network. However, the lightning network has an inefficient charging mechanism and Huang et al.’s system does not guarantee security of keys.
2. System Model
This section presents a secure charging system model for EV based on blockchain and basic concept of hyperledger.
2.1. Hyperledger
Hyperledger [19] is an open source project proposed by the Linux Foundation in 2015. The purpose is to promote cross-industry cooperation with blockchain technology. Hyperledger focuses on enhancing blockchain performance and reliability without requiring cryptocurrency.
Hyperledger architecture comprises nine blockchain components.
- Consensus layer: ensures agreement between transaction order and checks their validation.
- Smart contract layer: processes transaction requests and verifies smart contracts are valid.
- Communication layer: guarantees security for messages transmitted between nodes.
- Data store abstraction: manages data.
- Crypto abstraction: includes cryptographic algorithms or modules.
- Identity service: sets up the blockchain network, manages user and system node registration, and provides authentication and authorization.
- Policy services: provide various policies for blockchain systems.
- APIs: provide various blockchain interfaces.
- Interoperation: allows interoperation among blockchain instances.
Hyperledger provides scalability, confidentiality, complexity, essential security requirements, and compliance; and can also provide distributed ledgers, smart contracts, and friendly interfaces. Therefore, hyperledgers can be applied to various fields and disseminate blockchain technologies for cross-industry applications.
2.2. System Model
Figure 1 presents the proposed charging system for EV based on blockchain and our charging system comprises three entities: operator, energy aggregator (EAG), and user/EV; and incorporates four phases: initialization, registration, authentication, and charging, as follows.
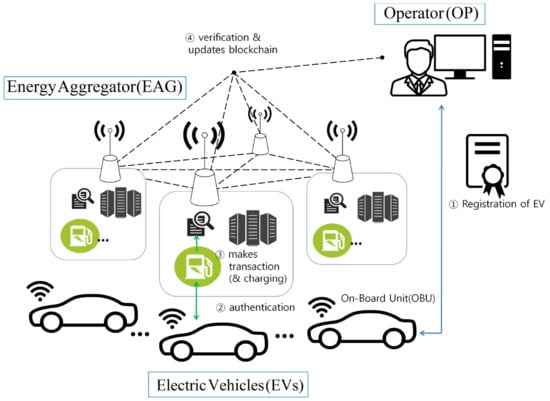
Figure 1.
Proposed blockchain based charging system model for electric vehicle.
- EV registers their identity with the operator to access charging services.
- EV and EAG authenticate each other.
- EAG generates transactions.
- EAG verifies the transaction is valid and records transactions on blockchain networks.
3. Review of Huang et al.’s Scheme
This section reviews Huang et al.’s blockchain based EV charging system [20], comprising four phases: registration, scheduling, authentication, and charging.
3.1. Registration Phase
Figure 2 shows how Huang scheme charging management includes EVs, charging piles (CPs) and operators (OP). Each participant is required to register in the open blockchain system. In Huang et al.’s scheme, lightning network transaction management system adopts an internet based cloud platform. The detailed steps are as follows.
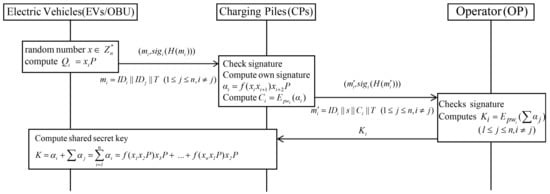
Figure 2.
Registration phase of Huang et al.’s scheme.
- Step 1:
- EVs choose a random number and calculate . The EVs request a registration in a blockchain and broadcast ,, and .
- Step 2:
- CPs check whether the received signature is valid, and then compute signature and . Then, CPs send and to the OP in the blockchain.
- Step 3:
- OP verifies the received the signature is valid and reuses , where is shared with each participant to decrypt . Subsequently OP computes and broadcasts it in the blockchain.
- Step 4:
- After receiving key from the OP, each participant decrypts and computes session key . When a request is recorded in the blockchain, it is checked by all CPs.
3.2. Scheduling Phase
Figure 3 shows the Huang scheme includes four scheduling strategies to provide charging services and improve charging efficiency: minimum time, minimum waiting time, minimum total cost, and shortest path.
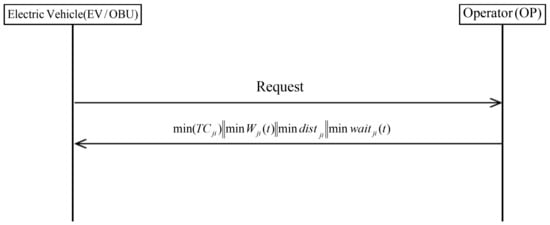
Figure 3.
Scheduling phase of Huang et al.’s scheme.
3.3. Authentication Phase
Figure 4 shows that EV and CP perform point-to-point (P2P) transactions under the Huang scheme, followed with mutual authentication to improve trading flexibility. Depending on scheduling strategies, the EV receives the recommendation from the OP, then EV and the selected CP authenticate each other, with mutual authentication performed between EV and CP when the EV arrives at the CP. The detailed authentication steps are as follows.
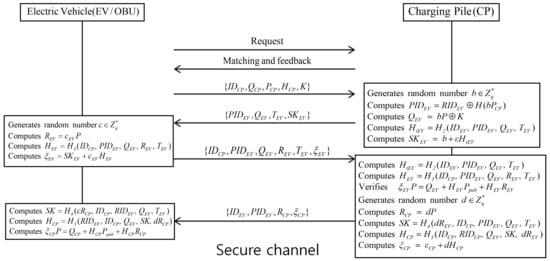
Figure 4.
Authentication phase of Huang et al.’s scheme.
- Step 1:
- EV sends identity to the CP, and then the CP checks whether it is valid through the blockchain networks. If it is valid, the CP returns charging request to the EV.
- Step 2:
- After receiving the charging request from the CP, the EV sends to the CP.
- Step 3:
- CP selects a random number , current timestamp , and calculates , , , and . Then, the CP sends , to the EV.
- Step 4:
- EV selects a random number , calculates =, , and , and sends , to the CP via the secure channel.
- Step 5:
- After receiving the message from the EV, the CP computes = and , and checks the received signature. If it is not valid, the CP aborts the authentication phase. Otherwise, the CP selects a random number and computes , , , and . Finally, the CP sends to the EV.
- Step 6:
- After receiving the message from the CP, the EV computes , ,, and . The CP checks the received signature. If valid, the EV and CP achieve mutual authentication. Otherwise, the EV aborts mutual authentication. After mutual authentication, the session key is used to encrypt messages to ensure secure communications.
3.4. Charging Phase
Figure 5 shows the Huang scheme charging phase. After completing authentication, the EV performs charging and updates the transactions. The commitment is recorded in the blockchain. The detailed steps are as follows.
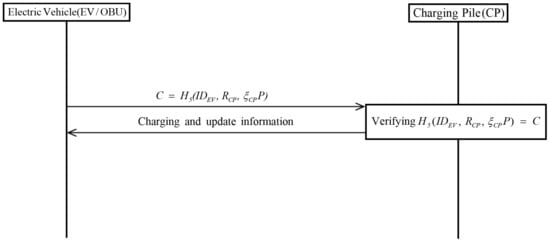
Figure 5.
Charging phase of Huang et al.’s scheme.
- Step 1:
- EV calculates commitment including EV’s identity, random parameter, and signature.
- Step 2:
- CP verifies whether commitment and current time stamps are valid. If valid, the CP starts charging for EV. Otherwise, this phase is aborted.
4. Problems of Huang et al.’s Scheme
This section discusses problems of Huang et al.’s scheme, such as deposit problem, inefficient transaction generation mechanism, and transaction cost.
4.1. Deposit Problem
In the scheduling phase of Huang et al.’s scheme, the OP recommends an efficient charging station using four strategies. However, the system has a deposit problem where EV needs to establish many payment channels for charging. In lightning networks, a deposit is used to establish a payment channel between two participants. However, an EV is mobile and cannot efficiently choose optimal charging stations because a payment channel must be established with each new charging station. Therefore, an EV unnecessarily spends many deposits, i.e., the mechanism is inefficient.
4.2. Inefficient Mechanism for Generating Transaction
The lightning network records a transaction in the blockchain when opening and closing a payment channel. When charging is completed at a charging station, the commitment transaction is generated and recorded in the blockchain. However, an EV already makes a transaction in the registration phase to allows access to the service, hence, two transactions are generated for one trade, i.e., an inefficient charging mechanism.
4.3. Cost of Transaction Fee
The Huang et al.’s scheme charges a transaction fee when a payment channel is opened or closed. However, after completing charging, an EV needs to re-register with the OP to use the service, hence re-opening the payment channel and incurring a transaction fee. Therefore, the Huang et al.’s scheme results in high transaction fees.
4.4. Security of Key
Huang et al. claimed their scheme provided known key security because the shared secret key K included unique random numbers for each participant. However, an adversary can steal the EV on-board unit (OBU) [31] and extract sensitive data stored in its memory using the power analysis attack [32,33]. Consequently, an adversary can obtain shared secret keys stored in the OBU, avoiding known key security.
5. Proposed Charging System for EV Based on Blockchain
This section proposes a blockchain based EV charging system that addresses the identified problems. Table 1 details the notation used for the proposed phases: initialization, registration, authentication, and charging.

Table 1.
Notations.
5.1. Initialization Phase
The operator conducts system initialization to set up the networks and EAG is registered in network. The details initialization process is as follows.
- Step 1:
- OP selects a base point G on the elliptic curve with order n, where n is a large prime number.
- Step 2:
- EAG generates public key, private key, and random number .
- Step 3:
- OP defines network configuration including channel members and policies, records it in a blockchain, and shares it with system participants.
5.2. Registration Phase
When it wants to access the charging system, EV generates its identity, password, public/private key pair, and then receives a random number from OP. Figure 6 shows the registration phase, with detailed steps as follows.
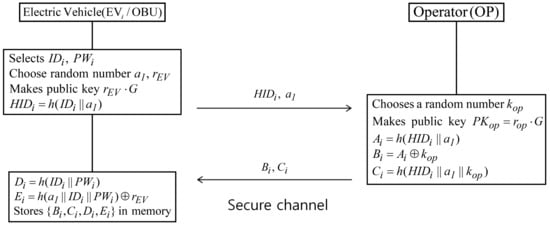
Figure 6.
Registration phase of proposed scheme
- Step 1:
- EV selects their identity , password , generates random numbers and , calculates a public key and , and then sends and to OP through a secure channel.
- Step 2:
- OP chooses a random number and calculates public key , , , and . Finally, OP sends , to EV, modifies network configurations, and stores details in the blockchain.
- Step 3:
- EV computes , ; and stores , , , and in memory.
5.3. Authentication Phase
When EV wants to use the charging service, EV and EAG must authenticate each other, and then generate a common session key. Figure 7 shows the authentication phase with detailed steps as follows
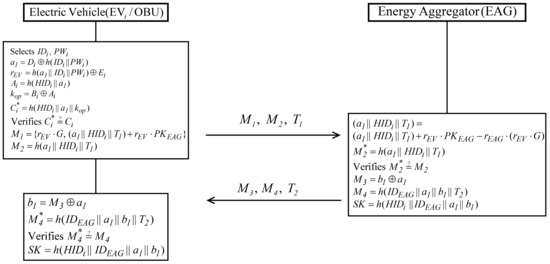
Figure 7.
Authentication phase of proposed scheme.
- Step 1:
- EV inputs identity and password ; and calculates , , , , and . Then, EV checks whether . If valid, EV computes , and ; and sends , , to EAG.
- Step 2:
- After receiving , , from EV, EAG calculates using the private key . Then EAG computes and verifies . If valid, EAG authenticates EV and calculates , , and session key . Finally, EAG sends , , to EV.
- Step 3:
- When EV receives , , from EAG, it computes and , and verifies . If valid, mutual authentication between EV and EAG has been accomplished. EV calculates a shared session key, .
5.4. Charging Phase
Charging commences after successfully completing authentication. Figure 8 shows the charging phase with detailed steps as follows.
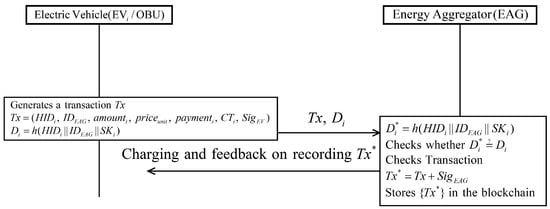
Figure 8.
Charging phase of proposed scheme.
- Step 1:
- EV generates a transaction including ; ; charging records, prices, charging time , signature of EV and information of payment, and EV computes . After that, EV sends to the EAG.
- Step 2:
- After receiving the message from EV, EAG checks whether . If it is correct, EAG checks whether the transaction information is correct. Then, EAG adds the own signature to the transaction. Finally, the charging is started and EAG records the transaction on the blockchain.
6. Security Analysis
This section demonstrates that the proposed system is secure against various attacks using informal analysis and proves the system provides secure mutual authentication using BAN logic [34], a widely accepted formal security analysis. We also show it is secure against replay and man-in-the-middle attacks using automated validation of internet security protocols and applications (AVISPA) [35] which is a formal security verification tool.
6.1. Informal Security Analysis
We perform informal security analysis to evaluate the proposed system security, and show the system can resist impersonation, replay, perfect forward secrecy, and session key disclosure attacks; and also provides secure mutual authentication and anonymity.
6.1.1. Impersonation Attack
If adversary EV attempts to impersonate a legitimate user EV, EV must successfully generate a request message . However, EV cannot calculate the request message because they cannot obtain EV’s random number , and real identity . EV also cannot obtain EV’s sensitive information because transmitted message is encrypted by EV. Therefore, the proposed protocol prevents impersonation attack.
6.1.2. Session Key Disclosure Attack
In the proposed system, the adversary EV cannot generate a valid session key because EV cannot obtain EV’s real identity ; or random numbers, and , generated by EAG. EV also cannot decrypt without EV’s private key . Therefore, the proposed protocol can resist session key disclosure attack.
6.1.3. Perfect Forward Secrecy
Even if an EV long-term private parameter of EV is compromised, EV does not obtain the previous session key. Suppose the long-term private parameter is leaked. EV cannot obtain because they cannot decrypt without the correct private key. Therefore, the proposed protocol guarantees perfect forward secrecy.
6.1.4. Replay Attack
Suppose EV attempted a replay attack using previous transmitted messages. However, EV cannot reuse previous messages, because all transmitted messages include timestamps, and EV and EAG check all transmitted messages including the timestamps are correct. Therefore, the proposed protocol prevents replay attack.
6.1.5. Mutual Authentication
Section 6.1.1 and Section 6.1.2 demonstrate that EV cannot impersonate EV and obtain the session key. All transmitted parameters are checked by EV and EV. When EAG receives the request message from EV, EAG decrypts using its own private key, and verifies . If valid, EAG authenticates EV. When EV receives response from EAG, it computes and , and then verifies . If valid, EV authenticates EAG. Therefore, the proposed system provides secure mutual authentication because EV and EAG successfully authenticate each other using private keys.
6.1.6. Anonymity
Suppose EV intercepts all previous transmitted messages to attempt to obtain EV’s real identity. However, all EV parameters, including , are masked by hash or encryption. Therefore, the proposed protocol ensures anonymity.
6.2. Security Analysis Using BAN Logic
We perform a security analysis using BAN logic to demonstrate the proposed system provides secure mutual authentication between EV and EAG. Table 2 introduces BAN logic notations and defines the goals, rules, idealized forms, and assumptions to perform BAN logic analysis.

Table 2.
Notations for BAN logic.
BAN Logic Rules
The BAN logic rules are as follows.
- 1.
- Message meaning rule:
- 2.
- Nonce verification rule:
- 3.
- Jurisdiction rule:
- 4.
- Freshness rule:
- 5.
- Belief rule:
6.3. Goals
We define the following security goals to prove the proposed system ensures secure mutual authentication.
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
6.3.1. Idealized Forms
The idealized forms are given below.
- :
- :
- :
- :
6.3.2. Assumptions
We define the following initial assumptions for the BAN logic proof.
- :
- :
- :
- :
- :
- :
- :
- :
6.3.3. Proof using BAN Logic
The detailed steps of the BAN logic proof are as follows.
- Step 1:
- From ,
- Step 2:
- From the message meaning rule with and ,
- Step 3:
- Using the freshness rule with ,
- Step 4:
- From the nonce verification rule with and ,
- Step 5:
- Since the session key , from and ,
- Step 6:
- From the jurisdiction rule with and ,
- Step 7:
- From the ,
- Step 8:
- Using the message meaning rule with and ,
- Step 9:
- From the freshness rule with ,
- Step 10:
- From the nonce verification rule with and ,
- Step 11:
- Since the session key , from and ,
- Step 12:
- From the jurisdiction rule with and ,
Therefore, the proposed protocol achieves secure mutual authentication between EV and EAG.
6.4. Formal Security AVISPA Tool for Formal Security Verification
To prove the proposed system is secure against replay and man-in-the-middle attacks, we performed formal security analysis using AVISPA [35], a widely accepted formal security verification tool to check systems or protocols can resist replay and man-in-the-middle attacks [36,37,38,39].
The AVISPA module was written in a high level protocol specification language (HLPSL) [40] and consists of four backends: Tree Automate-based Protocol Analyser (TA4SP), SAT-based Model-Checker (SATMC), CL-based Attack Searcher(CL-AtSe) [41] and On-the-Fly Model-Checker(OFMC) [42]. Detailed AVISPA and HLPSL are presented in [35,40].
6.4.1. HLPSL Specification of AVISPA Simulation
The HLPSL consists of three components: role, session, and environment, where role denotes entity, session includes system parameters, and environment includes intruder knowledge, security goal and authentication goal. Figure 9, Figure 10 and Figure 11 show HLPSL specifications for EV, EAG, and OP, respectively. Figure 12 shows session and environment roles.

Figure 9.
Specification of the electronic vehicle.

Figure 10.
Specification of the energy aggregator.

Figure 11.
Specification of the operator.

Figure 12.
Specification of the session.
Figure 9 shows the role for EV. In state 0, EV receives the start request and performs registration. EV sends the registration request to OP via a secure channel, updates the state value to 2, and then checks whether the entity is a legitimate user using the secret function.
In state 4, EV receives response from OP through a secure channel and sends the login request to EAG via an open channel. EV also declares witness to prove that is a weakness authentication factor. EV receives the response from OP, and then calculates the session key and updates the state value to 6.
6.4.2. AVISPA Verification Results
We used AVISPA with security protocol animator (SAPN) [43] to evaluate whether the proposed system was secure against replay and man-in-the-middle attacks. HLPSL is translated to intermediate format (IF) and the simulation results are presented in output format (OF). OFMC and CL-AtSe check whether our proposed system prevent replay and man-in-the-middle attacks. Figure 13 shows that OFMC backend visited 114 nodes with 0.72 s search time, and CL-AtSe backend analyzed the 2 states with 0.05 s translation time.
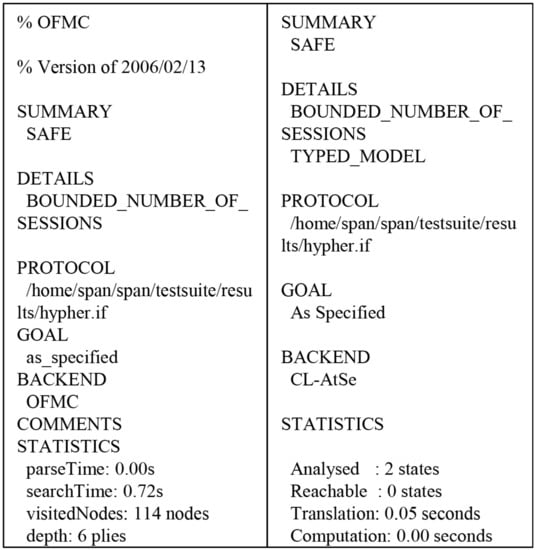
Figure 13.
AVISPA simulation results.
7. Performance Analysis
This section compares the proposed system computation and communication costs with related schemes [20,44,45]. Figure 14, Figure 15 and Figure 16 present the actual data workflow transmitted on our system to help understand the results of performance analysis. In Figure 14, operator provides the data for scheduling to EV and consensus nodes on blockchain verifty the validity of transactions.
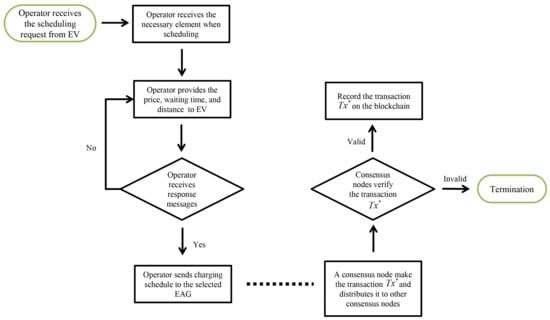
Figure 14.
Actual data workflow of network.
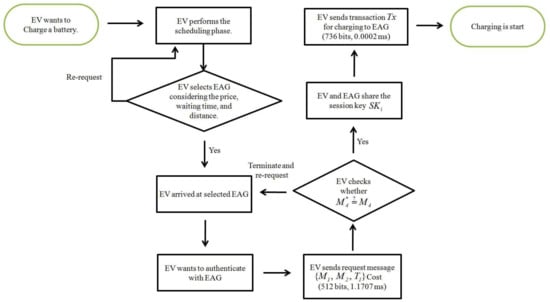
Figure 15.
Actual data workflow of EV.
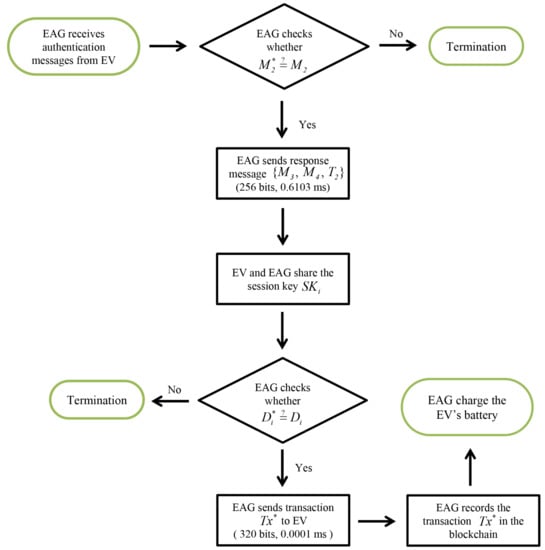
Figure 16.
Actual data workflow of EAG.
7.1. Computation Cost
We compare computation overheads for the proposed system with related schemes [20,44,45], using the parameters from [46,47].
- Bilinear pairing, ms.
- Scalar multiplication with bilinear pairing, ms.
- Point addition with bilinear pairing, ms.
- Scalar multiplication with elliptic curve cryptography, ms.
- Point addition with elliptic curve cryptography, ms.
- Encryption with elliptic curve cryptography, ms.
- Decryption with elliptic curve cryptography, ms.
- Hash, ms.
- Map-to-point, ms.
Table 3 compares computation costs for the considered schemes. In Figure 15, the EV’s computation costs of our system are (1.1707 + 0.0002 = 1.1709 ms), including and . In Figure 16, the EAG’s computation costs of our system are (0.6103 + 0.0001 = 0.6104 ms), including and .

Table 3.
Computation costs for related schemes.
In Huang et al.’s system [20], EV’s total computation costs are (0.4459 + 0.0001 = 0.4460 ms), including , and . EAG’s total computation cost is 0.8882 ms, including , and .
The total cost for the proposed and Huang et al.’s scheme = 1.7811 and 1.3343 ms, respectively. Although the proposed protocol computation cost of somewhat higher than the Huang et al.’s scheme, it provides better efficiency and security than other related schemes.
7.2. Communication Cost
We compare communication overheads for the proposed system with related schemes [20,44,45]. We assume timestamp, random number and identity are 32, 64, and 128 bits, respectively [48,49,50]; and elliptic curve cryptography encryption and hash function are 320 and 160 bits, respectively. For the proposed system, we assume group G is generated by P with order q on elliptic curve cryptography mod p, where p and q are 160 bits prime numbers. Similarly, , , and G are 1024, 160, and 320 bits, respectively. In Figure 15, the EV’s communication costs of our system are (512 + 736 = 1248 bits), including charging request messages and transaction . In Figure 16, the EAG’s communication costs of our system are (256 + 320 = 576 bits), including response messages and transaction .
In Huang et al.’s system [20], EV’s total communication costs are (2368 + 160 = 2528 bits), including charging requset messages , response messages and charging request messages . EAG’s total communication costs are 1760 bits, including response messages and .
Table 4 shows communication cost results for all considered schemes. More particularly, the communication cost is efficient compared with other schemes in view of EVs. It is a very important advantage because EV is equipped with resourse-constrained devices as sensors. Thus, the proposed system provides more efficient communication than all other considered schemes.

Table 4.
Communication costs.
8. Conclusions
With the rapid development of the IoT and embedded technologies, drivers can access various services. However, these services are vulnerable to potential attacks such as replay, impersonation and session key disclosure attacks because they are provided through public channels. Many traditional cryptographic algorithms such as RSA also are suitable to vehicular networks because a vehicle is equipped with resource-constrained sensors. Therefore, secure mutual authentication and key agreement are very important security requirements to guarantee privacy of users, considering the resource-constrained sensors.
This paper demonstrated that Huang et al.’s scheme does not provide high efficiency and security of keys, and has various authentication flaws, including excess deposits, inefficient transaction generation, and excess transaction fees. We proposed a secure charging system for electric vehicles based on blockchain to address these weaknesses, providing high efficiency, anonymity, perfect forward secrecy, and secure mutual authentication. We demonstrated that the proposed system prevents impersonation, session key disclosure, and replay attacks, proved secure mutual authentication between EV and EAG using BAN logic, and confirmed resistance to replay and man-in-the-middle attacks using AVISPA. We compared computation and communication costs with related schemes, and showed that the proposed scheme was superior to all considered schemes. Thus, the proposed system could be applied to IoT-based practical EV charging systems for resource-constrained devices.
Author Contributions
Conceptualization, M.K.; Formal analysis, K.P. and S.Y.; Software, J.L.; Supervision, Y.P.; Validation, K.P. and Y.P.; Writing—original draft, M.K.; Writing—review & editing, K.P., S.Y., Y.P., S.-W.L. and B.C.
Funding
This work was supported by Institute for Information & communications Technology Promotion(IITP) grant funded by the Korea government(MSIT) (No.2018-0-00312, Developing technologies to predict, detect, respond, and automatically diagnose security threats to automotive Ethernet-based vehicle).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Cheung, V. South Korea Releases Electric Public Transportation System. Available online: http://globalenergyinitiative.org/south-koreareleases-electric-public-transportation-system.html (accessed on 11 May 2019).
- Lo, N.-W.; Tasi, J.-L. An efficient conditional privacy-preserving authentication scheme for vehicular sensor networks without pairings. IEEE Trans. Intell. Transport. Syst. 2016, 17, 1319–1328. [Google Scholar] [CrossRef]
- Kumari, S.; Karuppiah, M.; Li, X.; Wu, F.; Das, A.K. An enhanced and secure trust-extended authentication mechanism for vehicular ad-hoc networks. Secur. Commun. Netw. 2016, 9, 4255–4271. [Google Scholar] [CrossRef]
- Chin, W.-L.; Li, W.; Chen, H.-H. Energy big data security threats in IoT-based smart grid communications. IEEE Commun. Mag. 2017, 55, 70–75. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, Y.; Chang, G. Efficient privacy-preserving dual authentication and key agreement scheme for secure V2V communications in an IoV paradigm. IEEE Trans. Intell. Transport. Syst. 2017, 18, 2740–2749. [Google Scholar] [CrossRef]
- Mohit, P.; Amin, R.; Biswas, G.P. Design of authentication protocol for wireless sensor network-based smart vehicular system. Veh. Commun. 2017, 9, 64–71. [Google Scholar] [CrossRef]
- Guo, L.; Dong, M.; Ota, K.; Li, Q.; Ye, T.; Wu, J.; Li, J. A secure mechanism for big data collection in large scale internet of vehicle. IEEE Internet Things J. 2017, 4, 601–610. [Google Scholar] [CrossRef]
- Zhou, Y.; Zhao, X.; Jiang, Y.; Shang, F.; Deng, S.; Wang, X. An enhanced privacy-preserving authentication scheme for vehicle sensor networks. Sensors 2017, 17, 2854. [Google Scholar] [CrossRef]
- Shen, J.; Zhou, T.; Wei, F.; Sun, X.; Xiang, Y. Privacy-preserving and lightweight key agreement protocol for V2G in the social internet-of-things. IEEE Internet Things J. 2018, 5, 2526–2536. [Google Scholar] [CrossRef]
- Wu, L.; Sun, Q.; Wang, X.; Wang, J.; Yu, S.; Zou, Y.; Liu, B.; Zhu, Z. An efficient privacy-preserving mutual authentication scheme for secure V2V communication in vehicular ad hoc network. IEEE Access 2019, 7, 55050–55063. [Google Scholar] [CrossRef]
- Gan, L.; Topcu, U.; Low, S.H. Optimal decentralized protocol for electric vehicle charging. IEEE Trans. Power Syst. 2013, 28, 940–951. [Google Scholar] [CrossRef]
- Xu, Y.; Pan, F.; Tong, L. Dynamic Scheduling for Charging Electric Vehicles: A Priority Rule. IEEE. Trans. Autom. Control 2016, 61, 4094–4099. [Google Scholar] [CrossRef]
- Lu, J.L.; Yeh, M.Y.; Hsu, Y.C.; Yang, S.N.; Gan, C.H.; Chen, M.S. Operating electric taxi fleets: A new dispatching strategy with charging plans. In Proceedings of the 2012 IEEE International Electric Vehicle Conference, Greenville, SC, USA, 4–8 March 2012; pp. 1–8. [Google Scholar]
- Kim, H.J.; Lee, J.; Park, G.L.; Kang, M.J.; Kang, M. An efficient scheduling scheme on charging stations for smart transportation. In Proceedings of the International Conference on Security-Enriched Urban Computing and Smart Grid, Daejeon, Korea, 15–17 September 2010; pp. 274–278. [Google Scholar]
- Tian, Z.; Jung, T.; Wang, Y.; Zhang, F.; Tu, L.; Xu, C.; Tian, C.; Li, X. Real-time charging station recommendation system for electric-vehicle taxis. IEEE Trans. Intell. Transp. Syst. 2016, 17, 3098–3109. [Google Scholar] [CrossRef]
- Tang, W.; Zhang, Y.J.A. A model predictive control approach for lowcomplexity electric vehicle charging scheduling: Optimality and scalability. IEEE Trans. Power Syst. 2016, 32, 1050–1063. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 27 May 2019).
- Pub, N.F. Secure Hash Standard. Available online: https://csrc.nist.gov/csrc/media/publications/fips/180/\2/archive/2002-08-01/documents/fips180-2withchangenotice.pdf (accessed on 27 May 2019).
- Available online: https://www.hyperledger.org/resources/publications#white-papers (accessed on 27 May 2019).
- Huang, X.; Xu, C.; Wang, P.; Liu, H. LNSC: A Security Model for Electric Vehicle and Charging Pile Management Based on Blockchain Ecosystem. IEEE Access 2018, 6, 13565–313574. [Google Scholar] [CrossRef]
- Poon, J.; Dryja, T. The Bitcoin Lightning Network: Scalable Off-Chain Instant Payments. Available online: http://www.theblockchain.com/docs/Lightning%20Network (accessed on 27 May 2019).
- Surhone, L.M.; Timpledon, M.T.; Marseken, S.F. Smart Contract; Betascript Publishing: Saarbrücken, Germany, 2010; pp. 1–72. ISBN 978-613-0-48941-0. [Google Scholar]
- Roman, R.; Alcaraz, C.; Lopez, J.; Sklavos, N. Key management systems for sensor networks in the context of the Internet of Things. Comput. Electr. Eng. 2011, 37, 147–159. [Google Scholar] [CrossRef]
- Turkanovic, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Amin, R.; Biswas, G. A secure light weight scheme for user authentication and key agreement in multi-gateway based wireless sensor networks. Ad Hoc Netw. 2016, 36, 58–80. [Google Scholar] [CrossRef]
- Lu, Y.; Li, L.; Peng, H.; Yang, Y. An energy efficient mutual authentication and key agreement scheme preserving anonymity for wireless sensor networks. Sensors 2016, 16, 837. [Google Scholar] [CrossRef]
- Magazzeni, D.; McBurney, P.; Nash, W. Validation and verification of smart contracts: A research agenda. Computer 2017, 50, 50–57. [Google Scholar] [CrossRef]
- Dubois, A.; Wehenkel, A.; Fonteneau, R.; Olivier, F.; Ernst, D. An app-based algorithmic approach for harvesting local and renewable energy using electric vehicles. In Proceedings of the 9th International Conference on Agents and Artificial Intelligence, Porto, Protugal, 24–26 February 2017; pp. 322–327. [Google Scholar]
- Knirsch, F.; Unterweger, A.; Engel, D. Privacy-preserving blockchain based electric vehicle charging with dynamic tariff decisions. Comput. Sci. Res. Dev. 2017, 33, 71–79. [Google Scholar] [CrossRef]
- Li, Z.; Kang, J.; Yu, R.; Ye, D.; Deng, Q.; Zhang, Y. Consortium Blockchain for Secure Energy Trading in Industrial Internet of Things. IEEE Trans. Ind. Inf. 2017, 14, 3690–3700. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Odelu, V.; Reddy, A.G.; Park, K.; Park, Y. Design of lightweight authentication and key agreement protocol for vehicular ad hoc networks. IEEE Access 2017, 5, 14966–14980. [Google Scholar] [CrossRef]
- Messerges, T.S.; Dabbish, E.A.; Sloan, R.H. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2002, 51, 541–552. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Proceedings of the Annual International Cryptology Conference (CRYPTO), Santa Barbara, CA, USA, 15–19 August 1999; pp. 388–397. [Google Scholar]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar]
- AVISPA. Automated Validation of Internet Security Protocols and Applications. Available online: http://www.avispaproject.org/ (accessed on 10 May 2019).
- Park, K.; Park, Y.; Park, Y.; Reddy, A.G.; Das, A.K. Provably secure and efficient authentication protocol for roaming service in global mobility networks. IEEE Access 2017, 5, 25110–25125. [Google Scholar] [CrossRef]
- Park, K.; Park, Y.; Park, Y.; Das, A.K. 2PAKEP: Provably secure and efficient two-party authenticated Key exchange protocol for mobile environment. IEEE Access 2018, 6, 30225–30241. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.; Lee, K.; Park, K.; Park, Y. Secure authentication protocol for wireless sensor networks in vehicular communications. Sensors 2018, 18, 3191. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Choo, K.R.; Kumar, N.; Park, Y. Efficient and secure time-key based single sign-on authentication for mobile devices. IEEE Access 2017, 5, 27707–27721. [Google Scholar] [CrossRef]
- Von Oheimb, D. The high-level protocol specification language HLPSL developed in the EU project avispa. In Proceedings of the APPSEM 2005 Workshop, Tallinn, Finland, 13–15 September 2005; pp. 1–2. [Google Scholar]
- Turuani, M. The CL-Atse protocol analyser. In Proceedings of the 17th International Conference on Rewriting Techniques and Applications (RTA), Seattle, WA, USA, 12–14 August 2006; pp. 277–286. [Google Scholar]
- Basin, D.; Modersheim, S.; Vigano, L. OFMC: A symbolic model checker for security protocols. Int. J. Inf. Secur. 2005, 4, 181–208. [Google Scholar] [CrossRef]
- SPAN: A Security Protocol Animator for AVISPA. Available online: http://www.avispa-project.org/ (accessed on 4 May 2019).
- Lai, C.; Lu, R.; Li, H.; Zheng, D.; Shen, X.S. Secure machine-type communications in LTE networks. Wirel. Commun. Mob. Comput. 2016, 16, 1495–1509. [Google Scholar] [CrossRef]
- Qiu, Y.; Ma, M.; Wang, X. A proxy signature-based handover authentication scheme for LTE wireless networks. J. Netw. Comput. Appl. 2017, 83, 63–71. [Google Scholar] [CrossRef]
- Islam, S.K.H.; Obaidat, M.S.; Vijayakumar, P.; Abdulhay, E.; Li, F.; Reddy, M.K.C. A robust and efficient password-based conditional privacy preserving authentication and group-key agreement protocol for VANETs. Future Gener. Comput. Syst. 2018, 84, 216–227. [Google Scholar] [CrossRef]
- Nkenyereye, L.; Kwon, J.; Choi, Y. Secure and lightweight cloud-assisted video reporting protocol over 5G-enabled vehicular networks. Sensors 2017, 17, 2191. [Google Scholar] [CrossRef] [PubMed]
- Lee, H.; Lee, D.; Moon, J.; Jung, J.; Kang, D.; Kim, H.; Won, D. An improved anonymous authentication scheme for roaming in ubiquitous networks. PLoS ONE 2018, 13, e0193366. [Google Scholar] [CrossRef]
- Yu, Y.; Li, Y.; Du, X.; Chen, R.; Yang, B. Content protection in named data networking: Challenges and potential solutions. IEEE Commun. Mag. 2018, 56, 82–87. [Google Scholar] [CrossRef]
- Ying, B.; Nayak, A. Lightweight remote user authentication protocol for multi-server 5G networks using self-certified public key cryptography. J. Netw. Comput. Appl. 2019, 131, 66–74. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).