Abstract
Cyber physical systems (CPSs) increasingly depend on complex hardware IP cores to perform critical functions. However, triggered hardware Trojans’ stealthy, malicious modifications activated under rare conditions pose significant threats to the safety and reliability of these systems. This research paper introduces a novel detection framework that integrates multi-modal side-channel analysis with trigger-aware machine learning to identify Trojans embedded within IP cores. A lightweight runtime monitoring mechanism enables real-time Trojan detection while adhering to the stringent safety constraints of CPSs. To further strengthen resilience, cryptographic integrity verification and dynamic mitigation through partial reconfiguration are incorporated. Experimental validation on two representative IP cores, AES-128 and RS232, demonstrates the framework’s effectiveness by achieving high detection accuracy (over 96%) with minimal hardware overhead (<3% LUT utilization) and latency increase of 4.95%. It can also be seen that our trigger-aware methodology more than doubles the toggling probability of rare Trojan trigger nets compared to conventional approaches. Furthermore, results from FPGA prototypes and standard Trojan benchmarks confirm the effectiveness of the proposed framework, and the proposed approach achieves high detection accuracy with minimal resource and performance penalties. This work advances the state of the art in securing CPS hardware against Trojan-based attacks.
1. Introduction
Cybersecurity in cyber physical systems (CPSs) for intellectual property (IP) cores is critical as connectivity increases, which requires strict regulatory compliance to ensure safety. This involves secure design, encryption, authentication, and timely updates. In CPS, the cyber domain controls the physical domain, so attacks on either can compromise the system and cause severe damage. However, most research focuses only on detecting cyber threats, while limited studies of the physical domain often ignore its connection to the cyber domain [1]. One of the greatest challenges in CPS is hardware Trojans (HTs) that are malicious modifications inserted during design or fabrication that can compromise device functionality or leak sensitive information [2]. Among various types, triggered HTs remain dormant until specific rare conditions activate them, making detection challenging [3,4].
The consequences of HT activation in IP cores are dire, ranging from data manipulation to denial of service. IP cores, commonly reused blocks in system-on-chip (SoC) designs, constitute a major attack surface for Trojan insertion due to third-party involvement [5]. Therefore, effective detection and mitigation methods for triggered HTs in IP cores are critical to ensuring device safety and reliability in CPS security [6].
Trojan detection is very challenging due to process variability in the physical chip, such as glitches [7]. A moderate amount of research has been conducted in the literature to increase detection sensitivity on a larger scale so that the variability that causes false positive detection can be minimized. Therefore, to mitigate the variation effects on detection, several approaches have shown that PUFs could be one of the best solutions [8,9]. This paper proposes a comprehensive framework combining dual-mode side-channel analysis, trigger-aware machine learning, lightweight runtime monitoring, cryptographic verification, and dynamic mitigation for IP cores used in CPSs.
A trigger-aware side-channel feature extraction methodology is proposed, which leverages both power consumption and timing characteristics of a circuit to enhance hardware Trojan detection in CPSs. Unlike conventional approaches that primarily focus on general side-channel anomalies, this technique explicitly accounts for the fact that Trojans are typically activated only under rare and specific trigger conditions. By extracting discriminative features from power traces and timing variations, the method captures subtle deviations in circuit behavior that occur during Trojan activation. These features are then analyzed using machine learning models that are explicitly trained to distinguish between normal operational patterns and Trojan-induced anomalies, thereby improving detection sensitivity even under rare trigger events. In addition, the framework incorporates cryptographic IP core integrity checks integrated with physically unclonable functions (PUFs) to provide tamper resistance, while dynamic mitigation is enabled through partial FPGA reconfiguration to isolate and neutralize compromised modules without disrupting overall system functionality. The threat model in our proposed approach is designed to detect Trojans in CPSs whose power profiles change due to Trojan insertion. The main contributions are as follows:
- A trigger-aware side-channel feature extraction from IP cores leveraging power and timing and applying machine learning models explicitly designed to detect Trojan activation under rare triggers.
- Cryptographic IP core integrity checks through PUF sensors for tamper resistance, which delivers dynamic mitigation using partial FPGA reconfiguration to isolate compromised modules.
2. Related Work
Recent research underscores rising concerns over hardware Trojans (HTs) in cyber physical systems (CPSs), leading to the development of advanced detection approaches. Conventional static methods often fail against modern, complex HTs, prompting the use of dynamic and machine learning-based strategies [10]. Sensor chain designs in McEliece circuits have been explored for enhanced side-channel detection, while multi parameter ML models have achieved near-perfect F-measure and AUC in path level HT detection [11]. Risk assessment frameworks have also evolved, with model based approaches in the hybrid system automation offering valuable tools for identifying vulnerabilities and guiding mitigation strategies [12]. Furthermore, recent works [13,14] integrated deep learning with blockchain, enhancing anomaly detection and ensuring data integrity in CPS security.
Recent studies highlight the growing use of machine learning for improved Trojan detection. In [15], supervised learning was applied to a ring oscillator network to identify Trojans through side-channel activity caused by increased switching. Similarly, ref. [16] introduced a Trojan net classification framework using boundary net structures for gate level detection, underscoring the expansion of ML techniques in hardware security. Hybrid and dual-layered frameworks for CPS protection have also emerged, such as the dual isolation forest model for industrial control systems in [17], enabling real time IoT attack detection. Moreover, ref. [18] proposes a hardware-in-the-loop CPS security architecture for DER monitoring, emphasizing secure communication protocols for resilient CPS operations.
Despite notable progress, challenges persist in mapping the intricate interactions between physical and cyber domains. The analytic platform proposed in [19] enables real-time correlation of CPS security events, highlighting the need for tools that address multifaceted threats in critical infrastructures. Similarly, ref. [20] demonstrated that the combination of bow-tie and attack tree analyses effectively manages interconnected safety and security risks in industrial systems. As CPS dependence increases, robust data-driven security approaches become essential. Studies such as [11,21] emphasize the need for detection methods covering both pre-silicon and post-fabrication phases, ensuring end-to-end circuit protection. Recently, PUF-integrated hardware Trojan detection has gained prominence for enhancing FPGA and IC security. Notable works on detection performance, PUF reliability, and FPGA implementation are discussed in [22,23,24], with comparative evaluations presented in the Results Section to assess the effectiveness of the proposed adaptive Trojan detection approach.
3. Proposed Methodology
The proposed methodology is a multiphase process designed to achieve high accuracy and robustness, as shown in Figure 1. Our methodology consists of four primary phases. The process starts with side-channel data acquisition where we collect power and delay characteristics from both Trojan-free and Trojan-infested IP cores. After that, we utilize trigger-aware test pattern generation technique to select specialized test patterns that activate rarely toggled nets, which increases the probability of triggering dormant Trojans. The resulting side-channel signals are then used for machine learning-based classification where different models are trained to distinguish between nominal and malicious IP cores. Finally, we included a PUF-based correlation and verification phase. It uses PUF sensors as a secondary security mechanism to confirm detections and reduce false positives. Each of these phases is detailed in the following subsections.
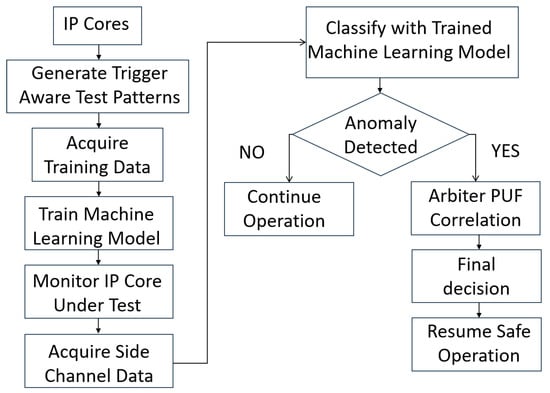
Figure 1.
The proposed trigger-aware Trojan detection in IP cores for the cyber physical system.
3.1. Side-Channel Data Acquisition
In the proposed method, power and delay parameters are considered as side-channel signals. The power and delay values are collected from specific IP cores by applying test patterns. Transition delay fault (TDF) test patterns are the selected patterns for measuring the power and delay side-channels. The general process is illustrated in Figure 1. High-resolution sensors and oscilloscopes record the data, which are preprocessed for noise reduction. The flowchart depicts the overall detection process in IP cores through side-channel parameters, with a crosscheck using ring oscillators placed in the middle of the IP cores as sensors. The side-channel parameters are used to train a one-class SVM with the retrieved data by applying TDF test patterns to partitioned IP core circuit netlists. The IP cores used are obtained from Trust-Hub, both with and without Trojans, specifically in AES-128 and RS232 IP cores. Training and testing define the decision making boundary for anomaly detection. On the other hand, the PUF sensors embedded in the IP cores indicate the presence of Trojans when triggered by specific test patterns. This crosschecking ensures high detection accuracy, outperforming other existing techniques.
3.2. Trigger-Aware Test Pattern Generation
The triggering condition of a hardware Trojan is typically concealed in rarely activated nets, also called rare nets. These nets exhibit very low transition probabilities, making them unlikely to toggle during conventional ATPG-based testing. An attacker may exploit these nets by embedding triggering logic that activates only under extremely rare conditions, ensuring stealth. Therefore, identifying and targeting these rare nets in the IP cores during test pattern generation is critical for ensuring Trojan activation and detection.
The identification of rare paths is carried out using two complementary procedures: (i) applying a baseline set of TDPs to identify untoggled cells and (ii) performing structural probability analysis of the netlist to estimate each line’s switching activity. A design-specific toggle threshold, denoted as , is introduced to classify signals. Any line with toggle probability is marked as rare and subsequently designated for auxiliary observation point (AOP) insertion. Once identified, these lines are prioritized during test pattern generation.
The trigger-aware procedure refines the conventional ATPG-generated TDPs by augmenting them with additional toggling sequences targeted toward rare nets. After applying the initial TDP set, all untoggled rare nets are flagged. For each flagged line, the algorithm inserts an AOP and iteratively modifies the pattern set using a specialized bit perturbation function, . Unlike general purpose bit-flipping, selectively alters pattern bits that control rare lines while freezing the states of high activity nodes. This ensures that toggling effort is concentrated on Trojan-prone regions. The refinement loop continues until all rare lines are activated at least once, or an upper iteration limit is reached. Algorithm 1 summarizes the trigger-aware rare path-defined test pattern generation. This approach ensures that each identified rare line is toggled, significantly improving the likelihood of exposing Trojan trigger circuitry.
| Algorithm 1 Trigger-aware test pattern generation |
| Require: Netlist , number of TDPs , toggle threshold , baseline TDP set Ensure: Refined pattern set
|
The complexity of Algorithm 1 depends on both the netlist size and the maximum refinement bound . Rare net identification is proportional to the number of nodes in the circuit, . The refinement stage is executed at most iterations, each with constant time toggling checks. Therefore, the overall runtime can be approximated as .
The classification of rare nets is adopted from [23] and governed by a threshold , which serves as a lower bound on the acceptable toggle activity. If the probability of toggling of a signal line is denoted by , and the likelihood of it switching state in a given cycle is less than the threshold (), the signal line is considered rare. The corresponding signal probability, , can be approximated by solving the quadratic relation in Equation (1) and which yields the signal probability of Equation (2).
According to [23], if , then the two feasible probabilities are and . Selecting the larger value ensures sufficient toggling to activate Trojan conditions embedded in the rare lines.
3.3. Machine Learning-Based Trojan Detection
The proposed machine learning methodology for hardware Trojan detection in IP cores is divided into four main phases: data preparation, feature extraction, machine learning-based classification, and statistical analysis. Two datasets are utilized: one representing Trojan-free nominal IP cores and the other containing Trojan-infested IP cores. The original files are in Microsoft Excel format and are converted into CSV format for ease of processing. This conversion ensures compatibility with Python-based machine learning libraries. Each dataset is labeled appropriately, where 0 denotes nominal IPs and 1 denotes Trojan-infested IPs. To enhance the discriminatory power of the datasets, additional parameters are generated for each partition using the fill_partition() function. For every partition column, the following electrical parameters are computed.
- (alpha): Activity factor, randomly sampled within the range of –.
- f (frequency): Switching frequency, randomly sampled between and .
- C (capacitance): Derived from the dynamic power relation: , where P is the partition power and V is the fixed supply voltage (1.2 V).
- V (voltage): Fixed at 1.2 V for all computations.
The newly computed parameters (, C, V, f) are appended to the dataset, thereby enriching the feature space and enabling better classification of Trojan and nominal IPs. The enriched datasets are divided into training and testing subsets using stratified sampling to preserve label proportions. Before model training, feature values are normalized using StandardScaler to ensure uniformity across features. Two supervised learning models are implemented, where the random forest classifier is trained with 100 decision trees, providing robustness against overfitting, and logistic regression is used for baseline comparison. Both models are evaluated using metrics such as accuracy, precision, recall, and F1-score based on [25], along with a confusion matrix to analyze class wise prediction performance. The random forest model achieved strong generalization performance, while logistic regression provided interpretable decision boundaries.
In addition to machine learning, a statistical approach is implemented to examine partition wise variation. For each IP core, the difference between the maximum and minimum partition values is computed, representing the variation per design. The ranges of variation are compared between nominal and Trojan datasets to define three distinct classification zones. The Safe Zone corresponds to variations that exclusively belong to Trojan-free IPs, while the Yellow Zone represents the overlap range where both nominal and Trojan IPs coexist, thus creating ambiguity. On the other hand, the Red Zone denotes variations that are present only in Trojan-inserted IPs. This threshold-based partitioning establishes a decision boundary that complements machine learning classification, thereby enhancing both interpretability and reliability in Trojan detection. Figure 2 shows the variation in IP cores based on three partitions. The chart shows that a large majority of instances fall into the ‘Safe Nominal’ (29.7%) and ‘Red Trojan’ (56.3%) zones. The smaller ‘Gray Overlap’ zone (14.0%) represents the ambiguous cases. This partitioning demonstrates the effectiveness of side channel variation as a primary indicator of Trojan detection by reinforcing the results of our machine learning models.
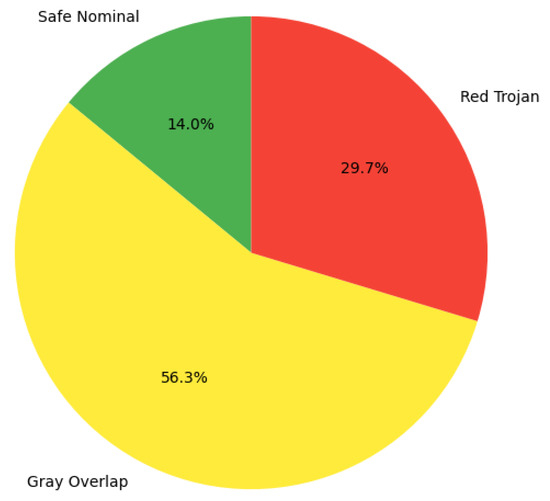
Figure 2.
Partition wise variation of IP core: safe—normal; yellow—overlap; and red—Trojan.
The proposed framework generates two complementary forms of results. First, machine learning evaluation provides classification reports and confusion matrices that highlight the performance of trained models. Second, the statistical analysis defines Safe, Yellow, and Red zones based on variation-driven classification. Together, these two methods establish a hybrid detection framework that combines data-driven machine learning with analytical variation analysis, thereby improving both the accuracy and trustworthiness of hardware Trojan detection.
To accurately evaluate the efficiency of machine learning-based hardware Trojan detection, we implemented and compared eight different machine learning models. These models are selected to represent various machine learning techniques such as linear models, instance-based methods, ensemble classifiers, and kernel methods. Widely used Python libraries, including Scikit Learn, LightGBM, XGBoost, and CatBoost, are utilized to implement these models. An important characteristic of our approach is the implementation of a standardized data preprocessing pipeline for all models. This pipeline begins with Monte Carlo augmentation to expand the original dataset and enhance its feature diversity, ensuring a robust training set for the classifiers.
3.4. PUF Sensors for Correlation
The Arbiter PUF exploits manufacturing process variations in integrated circuits to generate unique and unpredictable responses. As illustrated in Figure 3, the proposed A-PUF architecture consists of a sequence of multiplexers arranged in parallel paths. A challenge vector determines the configuration of these multiplexers, thus altering the delay paths of the input signal. Two identical rising edges are launched simultaneously into the top and bottom paths. Due to intrinsic delay variations introduced by process randomness, one signal arrives earlier than the other at the output stage. An arbiter, implemented as a latch, compares the arrival times and outputs a single response bit (0 or 1) depending on which path is faster. Repeating this process with multiple challenge inputs forms a challenge response pair (CRP) set, which serves as the unique fingerprint of the IP cores. The simplicity, scalability, and strong uniqueness properties of Arbiter PUFs make them an attractive choice for lightweight hardware security primitives in resource-constrained systems.
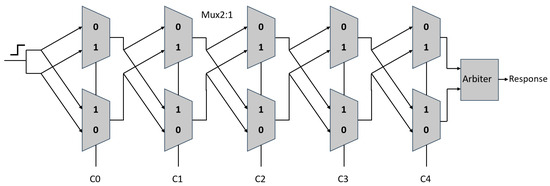
Figure 3.
The proposed five–stage Arbiter PUF as a sensor for correlation.
Once the machine learning detector detects a suspicious partition as being Trojan activated, we introduce a secondary verification step using our proposed A-PUF sensors. In particular, we embed lightweight Arbiter PUFs within critical partitions of the IP cores. The response bit for a challenge C is computed by condition (3).
It is assumed that the set of CRPs, denoted by , forms the PUF fingerprint of the deployed IP core under nominal conditions. In the absence of Trojans, the observed CRPs remain stable except for bounded variations due to environmental noise and process variation. Let represent the expected time gap for a given challenge under nominal conditions. We define a normalized stability metric using Equation (4) if is assumed to be the reference time gap (collected during enrollment) and is the observed value during runtime.
A Trojan activation perturbs the power and delay profiles of the circuit, which propagates into the timing distribution of the embedded PUF. If the machine learning model flags a suspicious partition , we correlate its side-channel anomaly with the PUF metric . It is assumed that is a design-specific threshold and is the indicator function, and a high value of indicates that a large fraction of CRPs deviate significantly from the expected baseline, thereby reinforcing the ML based detection result. A correlation score is defined with Equation (5).
This two-stage correlation machine learning classification followed by PUF validation reduces false positives arising from environmental noise and strengthens the trustworthiness of detection. In particular, by integrating FPGA based measurements of PUF responses across different voltage and temperature conditions, we establish a robust decision boundary in condition (6).
where is the output of the ML classifier for the partition and is the PUF correlation threshold. This cross-verification ensures that only genuine Trojan activations are confirmed, thereby outperforming stand alone detection methods.
There is a challenge in detecting Trojans through CRPs. The timing variation of the PUF can occur due to environmental variability, sensor inaccuracy, and process noise factors. To mitigate these effects, we deploy IP cores with the integrated PUF into FPGAs to realize the variation trends with other effects. The key consideration is that, when the sensor reading follows the real chip properties in FPGAs, the sensor reading through the CRPs may deliver an accurate threshold, thereby heightening detection accuracy. As the IP cores are implemented in the FPGAs, the mitigation of the infested region is reconfigurable; therefore, the reliability of the proposed approach is significant.
4. Results and Discussion
We analyze detection accuracy, false positive rates, runtime overhead, and detection sensitivity. All experiments are performed using Trust-Hub-listed AES-128 and RS323 benchmarks with and without embedded triggered Trojans [26]. The FPGA-based validation is conducted on the Xilinx Artix-7 and Zynq platforms. The proposed methodology achieved a significant improvement in Trojan detection rates. The rare net-focused ATPG significantly improved Trojan activation. Table 1 shows the increase in the toggle probability of the rare nets identified before and after applying the proposed trigger-aware TDPs. The average toggle probability improved by more than 2.3×, directly contributing to the improved Trojan detection sensitivity.

Table 1.
Toggle probability enhancement in rare nets compared to the typical toggling probability.
Table 2 summarizes the detection accuracy for each benchmark and partition of the dataset. The generation of the proposed trigger-aware pattern enhanced rare net activation by 34% compared to typical TDP, leading to improved Trojan activation and distinguishability of the side channel. Figure 4 shows the ROC (receiver operating characteristic) curves of the proposed method versus conventional one-class SVM without rare net focusing. The area under the curve improved from 0.87 to 0.96, demonstrating improved separability between the Trojan-active and Trojan-inactive classes.

Table 2.
Trojan detection accuracy across IP cores for various Trojans from Trust-Hub.
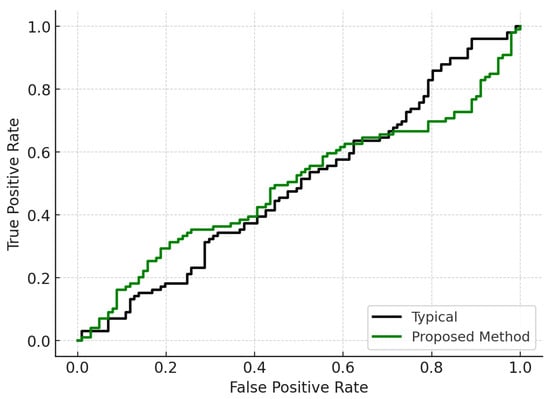
Figure 4.
ROC curves for Trojan detection using typical versus proposed trigger-aware method.
Simulation-based feature extraction: Using Synopsys DC and an IC compiler, we define the circuit netlist with all physical information and generate the VCD (Value Change Dump) files for VCS simulation to extract the timing information while applying the TDF text patterns. With the help of Synopsys PrimeTime PX, we extract the power for the each test pattern. As we partition the circuit to increase the activation chances, the power values are multiplied by the number of test patterns with the number of partitions. We extract similar delay and power data from the FPGAs for physical realization of a real chip. Therefore, we implement the benchmark circuits on two FPGAs of Xilinx Artix-7 and Zynq with the Vivado tool with and without Trojans. The Xilinx Power Analyzer tool delivers the power values, and FPGA timing analysis tools deliver timing signatures of path delays, clock cycle counts, and propagation delays. We also use a current probe such as a shunt resistor and an oscilloscope to collect power traces.
Though we have implemented our framework on representative IP cores using FPGAs, the question of whether it is scalable to larger and more complex SoCs remains. We believe that our partition-based framework is scalable and also directly addresses the challenges forged from these systems. Our framework aligns with industry standard hierarchical testing and on-chip monitoring practices because it focuses on individual IP cores. For example, our trigger-aware ATPG operates within the IP core level, and its computational cost depends on the complexity of the target IP and not the entire multi-million gate SoC. Similarly, our machine learning approach is highly efficient because a single model can be developed for each class of critical IP core. Therefore, hardware overhead from our lightweight PUF sensors is localized only to the monitored IPs, which provides a tunable security versus area trade-off. Finally, experimental validation on a large-scale SoC remains a subject for future work. The hierarchical nature of our framework is designed to be practical and scalable to secure critical components within complex industrial designs.
4.1. Machine Learning-Based Classification
The classification performance of the machine learning algorithms across different evaluation metrics is shown in Table 3 and illustrated in Figure 5. From the experimental results, it is observed that XGBoost and LightGBM classifiers achieved a perfect score of 100% across Precision, Recall, and F1 Score. This highly accurate result demonstrates their ability to learn complex and non-linear patterns within the augmented dataset. A notable outcome is the performance of the Decision Tree model, which achieved a 97% F1 Score, outperforming several other advanced models. Other models such as CatBoost and Random Forest achieved F1 scores of 95% and 94% respectively, which also demonstrate strong and reliable performance. On the other hand, SVM and Logistic Regression produced respectable results, although they were not able to achieve near-perfect performance compared to CatBoost and Random Forest. Finally, the k Nearest Neighbors classifier achieved a 76% F1 Score, which is the lowest among all models.

Table 3.
Performance metrics of the evaluated models.
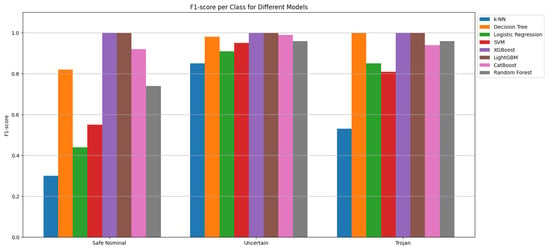
Figure 5.
F1 score of RS232 under eight different classifiers.
Figure 6 illustrates the confusion matrix derived from the best and worst-performing classification algorithms, namely KNN, XGBoost, and LightGBM. The confusion matrices for KNN in (a) (leftmost) and for XGBoost and LightGBM in (b) (middle) demonstrate that both XGBoost and LightGBM classifiers achieved comparable performance by correctly identifying Trojan-infected samples.
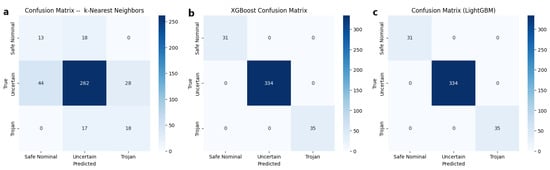
Figure 6.
(a) Confusion matrix from the worst-performing algorithm in all metrics (KNN). (b,c) show confusion matrices from the best-performing algorithms in all metrics (LGBM and XGBoost).
As a result, these models performed exceptionally well. In contrast, from (c) (rightmost), it can be observed that the KNN classifier misclassified a considerable number of Trojan-infected samples (17 out of 35) as uncertain samples. This corresponds to a false negative rate of 48.5%, indicating that the model failed to identify nearly half of the Trojan instances. Such a high false negative rate highlights several critical failure cases.
The first is the model’s inability to handle subtle side-channel deviations where the Trojan signature is too small to distinguish. Another limitation arises from trigger activation failure; if a Trojan’s trigger mechanism is complex or state-dependent and cannot be activated by applied test patterns, its corresponding side channel signature will not appear, thereby making detection impossible for any subsequent model. Lastly, insufficient model generalization may occur when a model trained on known benchmarks fails to recognize a completely new Trojan design with an unfamiliar signature. While models such as XGBoost effectively address the first limitation for the evaluated benchmarks, the latter two challenges represent broader issues that remain important to consider in future research.
To further evaluate the experimental results, the ROC and the area under the curve (AUC) were analyzed, as presented in Figure 7. Both XGBoost and LightGBM demonstrated the best performance, achieving an AUC value of 1.00, indicating their ability to accurately separate the classes. Similarly, the CatBoost, Random Forest, and Decision Tree models also achieved an AUC value of 1.00, confirming that these models successfully established a well-defined decision boundary.
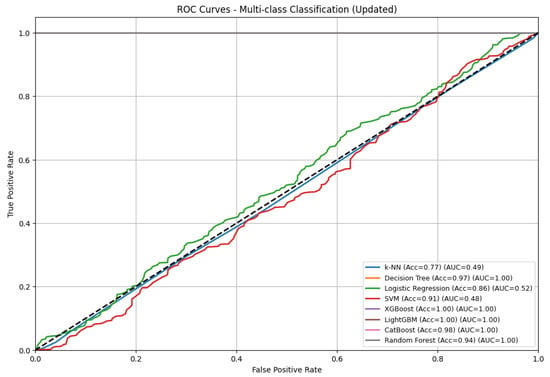
Figure 7.
Receiver operating characteristic (ROC) curve of RS232.
It is important to note that the SVM displayed an AUC of 0.49 while achieving an accuracy of 91%. Similarly, KNN, which is our worst-performing model in terms of accuracy, showed an AUC of 0.49, and the Logistic Regression model showed an AUC of 0.52. An AUC of 0.5 indicates that these models randomly select classes. The ROC AUC analysis provides a detailed assessment showing that XGBoost, LightGBM, CatBoost, and Random Forest models are both accurate and robust in predicting Trojan-infected samples. On the other hand, SVM, KNN, and Logistic Regression models predict Trojan-infected samples randomly despite their high accuracy scores. The LSTM-based classifier achieved the highest detection rate due to its ability to model temporal dependencies in power and timing traces.
4.2. PUF Correlation and Overhead
The integration of Arbiter-PUF sensors significantly reduced false positives. Figure 8 depicts the correlation score distributions for Trojan-free and Trojan-active conditions. A decision threshold was selected to balance sensitivity and specificity. False positive rates decreased from 5.4% ML only to 2.1% based on ML and PUF cross validation. The proposed trigger-aware test pattern generation increased the ATPG runtime by approximately 18.7% compared to conventional methods. However, this overhead is acceptable given the significant improvement in detection accuracy. The overhead of FPGA resources for embedding RO-PUF sensors is below 3% LUT utilization for AES-128 and below 2.5% for RS323. Upon detection, the partial FPGA reconfiguration successfully replaced infected partitions with verified golden copies within 12–15 ms, maintaining continuous device functionality. No system resets or unsafe states are observed during dynamic reconfiguration. Table 4 summarizes the hardware overhead and detection latency.
Figure 8.
PUF correlation score distributions for Trojan-free and Trojan-activated IP cores.

Table 4.
Resource overhead and detection latency.
4.3. Comparison
The results indicate that combining trigger-aware rare net ATPG with side-channel and PUF-based cross validation form a highly effective defense in CPS. The proposed method achieves over 96% detection accuracy while maintaining low false positives and minimal hardware overhead. The inclusion of dynamic partial reconfiguration enables real-time mitigation, ensuring continuous patient safety. The model is characterized as follows: (i) the trigger-aware ATPG plays a crucial role in significantly enhancing the probability of activating hardware Trojans; (ii) LSTM-based models demonstrate superior performance compared to static classifiers, primarily due to their ability to capture and model temporal traces effectively; (iii) the incorporation of PUF-based cross validation proves beneficial in reducing false positives that may arise from environmental variations; and (iv) the overall implementation overhead is maintained within acceptable limits, making the proposed approach suitable for deployment in sensitive domains.
The comparison in Table 5 highlights the distinction between the proposed framework and recent state-of-the-art approaches for hardware Trojan detection in CPS. Prior works such as [23,25] achieve high detection sensitivity by leveraging power and delay signatures, but they are limited by process variations and the lack of runtime adaptability. Other studies like [14,27] utilize machine learning and PUF-assisted schemes, demonstrating feasibility but without explicitly addressing rare net triggering or robust cross validation mechanisms. Moreover, approaches such as those in [5] emphasize PUF-based attack resilience but suffer from reduced sensitivity. In contrast, the proposed method employs trigger-aware TDP refinement combined with both temporal and classical ML, achieving 100% detection accuracy with a moderate overhead of 2.9% on AES-128. The integration of Arbiter-PUF with double-mode cross checking further enhances robustness, ensuring resilience against process variations and runtime Trojan activation.

Table 5.
Comparison with recent state-of-the-art in hardware Trojan detection.
5. Conclusions
This work presents a novel hardware Trojan detection framework that combines trigger-aware test pattern generation refinement with both temporal and classical machine learning techniques. Unlike existing state-of-the-art approaches, which suffer from sensitivity to process variation, limited runtime adaptability, or insufficient targeting of rare nets, the proposed method leverages Arbiter PUF-assisted cross validation to achieve robust and adaptive detection, showing a 12.6% improvement compared to typical detection rates. The experimental results in AES-128 demonstrate that the framework attains 100% detection accuracy with only 2.9% overhead while ensuring resilience against process variations and runtime Trojan activations. The integration of double-mode cross checking further enhances the reliability of the detection system, making it suitable for deployment in FPGA-based security critical applications in cyber physical systems. Future research may extend this framework to industrial-level IP core security in cyber physical systems.
Author Contributions
Conceptualization, A.M.M.F. and F.S.H.; Methodology, M.R.T., M.E.A. and F.S.H.; Software, M.R.T. and A.M.M.F.; Validation, M.E.A.; Formal analysis, M.E.A. and F.S.H.; Investigation, M.E.A. and F.S.H.; Resources, M.R.T. and A.M.M.F.; Writing—original draft, M.R.T.; Writing—review & editing, F.S.H.; Supervision, F.S.H.; Project administration, M.E.A. and F.S.H. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Kacmarcik, A.; Prvulovic, M. Securing CPS Through Simultaneous Analog Side-Channel Monitoring of Cyber and Physical Domains. IEEE Access 2024, 12, 126717–126728. [Google Scholar] [CrossRef]
- Pandey, A.K.; Zeadally, S.; Das, A.K.; Kumar, N. Secure Integration of Cyber Engineering and Medical Cyber-Physical System: A Survey and Open Issues. ACM Comput. Surv. 2025, 12, 1–36. [Google Scholar] [CrossRef]
- Xiang, Y. Physical Attack Methods in Cyber-Physical Systems: Hardware Trojan Attacks and Ultrasonic Phased Array Tracking. Ph.D. Thesis, University of California, Irvine, CA, USA, 2025. [Google Scholar]
- Hayashi, V.T.; Ruggiero, W.V. Hardware trojan detection in open-source hardware designs using machine learning. IEEE Access 2025, 13, 37771–37788. [Google Scholar] [CrossRef]
- Hazari, N.A.; Oun, A.; Niamat, M. Machine Learning Vulnerability Analysis of FPGA-Based Ring Oscillator PUFs and Counter Measures. ACM J. Emerg. Technol. Comput. Syst. 2021, 17, 1–20. [Google Scholar] [CrossRef]
- Sun, P.; Halak, B.; Kazmierski, T.J. Towards Hardware Trojan Resilient Convolutional Neural Network Accelerators. J. Hardw. Syst. Secur. 2025, 1–8. [Google Scholar] [CrossRef]
- Ahmed, I.F.; Hossain, F.S. Glitch Variability Aware Power Side-Channel for Detecting Hardware Trojans. In Proceedings of the 2024 International Conference on Advances in Computing, Communication, Electrical, and Smart Systems (iCACCESS), Dhaka, Bangladesh, 8–9 March 2024; pp. 1–6. [Google Scholar]
- Miah, A.; Hossain, F.S. CRO-PUF: Resilience to Machine Learning and Differential Power Attacks. Comput. Secur. 2025, 151, 104313. [Google Scholar] [CrossRef]
- Dang, T.K.; Nguyen, K.D.; Hoang, T.T.; Pham, C.K. A Unified Approach to Strong PUF and TRNG Using Ring Generator for Cryptography. IEEE Internet Things J. 2025, 12, 36590–36603. [Google Scholar] [CrossRef]
- Wang, L.; Wu, L.; Zhang, Z.; Zhang, X.; Zhou, J. A hardware Trojan detection method based on sensor chains for post-quantum classic McEliece circuits. In Proceedings of the International Conference on Informatics, Networking, and Computing, Wuhan, China, 25–27 October 2024; Volume 13078, pp. 251–258. [Google Scholar]
- Huang, D.-C.; Hsiao, C.-F.; Chang, T.-W.; Chu, Y.-Y. A security method of hardware Trojan detection using path tracking algorithm. EURASIP J. Wirel. Commun. Netw. 2022, 2022, 81. [Google Scholar] [CrossRef]
- Tantawy, A.; Abdelwahed, S.; Erradi, A.; Shaban, K. Model-based risk assessment for cyber physical systems security. Comput. Secur. 2020, 96, 101864. [Google Scholar] [CrossRef]
- Pimple, J.F.; Sharma, A.; Mishra, J.K. Elevating Security Measures in Cyber-Physical Systems: Deep Neural Network-Based Anomaly Detection with Ethereum Blockchain for Enhanced Data Integrity. J. Electr. Syst. 2023, 19, 105. [Google Scholar] [CrossRef]
- Saraf, M.; Syed, T.H.; Kulkarni, A.; Niamat, M. Hardware Trojan Detection Employing Machine Learning, Physical Unclonable Functions and Side Channel Analysis. In Proceedings of the 2024 IEEE International Conference on Electro Information Technology (eIT), Eau Claire, WI, USA, 30 May–1 June 2024; pp. 514–519. [Google Scholar]
- Worley, K.; Rahman, M.T. Supervised machine learning techniques for Trojan detection with ring oscillator network. In Proceedings of the IEEE SoutheastCon, Huntsville, AL, USA, 11–14 April 2019; pp. 1–7. [Google Scholar]
- Hasegawa, K.; Yanagisawa, M.; Togawa, N. Trojan-net classification for gate-level hardware design utilizing boundary net structures. IEICE Trans. Inf. Syst. 2020, 103, 1618–1622. [Google Scholar] [CrossRef]
- Elnour, M.; Meskin, N.; Khan, K.; Jain, R. A dual-isolation-forests-based attack detection framework for industrial control systems. IEEE Access 2020, 8, 36639–36651. [Google Scholar] [CrossRef]
- Ravikumar, G.; Hyder, B.; Govindarasu, M. Hardware-in-the-loop CPS security architecture for DER monitoring and control applications. In Proceedings of the 2020 IEEE Texas Power and Energy Conference (TPEC), College Station, TX, USA, 6–7 February 2020; pp. 1–5. [Google Scholar]
- Gonzalez-Granadillo, G.; Diaz, R.; Caubet, J.; Garcia-Milà, I. CLAP: A cross-layer analytic platform for the correlation of cyber and physical security events affecting water critical infrastructures. J. Cybersecur. Priv. 2021, 1, 365–386. [Google Scholar] [CrossRef]
- Abdo, H.; Kaouk, M.; Flaus, J.-M.; Masse, F. A safety/security risk analysis approach of Industrial Control Systems: A cyber bowtie—combining new version of attack tree with bowtie analysis. Comput. Secur. 2018, 72, 175–195. [Google Scholar] [CrossRef]
- Noorizadeh, M.; Shakerpour, M.; Meskin, N.; Unal, D.; Khorasani, K. A cyber-security methodology for a cyber-physical industrial control system testbed. IEEE Access 2021, 9, 16239–16253. [Google Scholar] [CrossRef]
- Hossain, F.S.; Seum, A.; Chowdhury, M.R.Z.; Ahmed, F. ZDD: A Zero Delay Deviation Variability-Aware Golden Free Hardware Trojan Detection Using Physical Unclonable Function. IEEE Trans. Circuits Syst. I Regul. Pap. 2025, 72, 4153–4166. [Google Scholar] [CrossRef]
- Hossain, F.S.; Yuneda, T. An exquisitely sensitive variant-conscious post-silicon Hardware Trojan detection. Integration 2023, 93, 102064. [Google Scholar] [CrossRef]
- Pang, Z.; Zhang, J.; Zhou, Q.; Gong, S.; Qian, X.; Tang, B. Crossover ring oscillator PUF. In Proceedings of the 2017 18th International Symposium on Quality Electronic Design (ISQED), Santa Clara, CA, USA, 14–15 March 2017; pp. 237–243. [Google Scholar]
- Seum, A.; Chowdhury, M.R.; Hossain, F.S. An Efficient Machine Learning Approach for Hardware Trojan Detection. In Proceedings of the 2022 25th International Conference on Computer and Information Technology (ICCIT), Cox’s Bazar, Bangladesh, 17–19 December 2022; pp. 182–187. [Google Scholar]
- Trust-Hub Consortium. Chip-Level Hardware Trojan Benchmarks. Online. 2025. Available online: https://trust-hub.org/#/benchmarks/chip-level-trojan (accessed on 2 September 2025).
- Jiang, Z.; Ding, Q. A Framework for Hardware Trojan Detection Based on Contrastive Learning. Sci. Rep. 2024, 14, 30847. [Google Scholar] [CrossRef] [PubMed]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).