RACHEIM: Reinforced Reliable Computing in Cloud by Ensuring Restricted Access Control
Abstract
1. Introduction
1.1. Cloud Security
- Google Cloud APIs often use service accounts and OAuth scopes;
- Azure APIs rely heavily on Azure AD app registrations, tokens, and permissions (delegated or application) via the Microsoft Identity Platform.
1.2. Motivation
- Forever 21 data breach: In August 2023, over 500,000 customers’ data was compromised that leaked the details of client names, dates of birth, bank account details, and Social Security numbers to an illegal third-party that gained access.
- Discord.io Data Breach: Discord.io suffered a data breach in August 2023 in which nearly 760,000 users’ data was impacted through leakage of confidential information such as usernames and passwords.
- Pizza Hut/KFC Data Breach: Personal data of customers was made publicly accessible during a ransomware attack in January 2023.
- Data Leakage in ChatGPT: A major security issue identified in March 2023 was in ChatGPT’s version 4 (GPT-4), developed by OpenAI, San Francisco, United States. The vulnerability in its open-source library led to the unintended disclosure of users’ personal information, including their chat histories and credit card details.
- The Security breach of Facebook: In April 2019, this breach impacted approximately 540,000 user records, while around 49 million records were affected in the Instagram security breach data loss in May 2019.
- (i)
- Encryption that maintains authentication and confidentiality. IBE ensures that only verified users can decrypt: confirms user identity. Broadcast encryption maintains data confidentiality during group transmission.
- (ii)
- Access control to enforce role-based permissions.
1.3. Key Contributions
- To propose a secure framework that enables resource computation at the Cloud Service Provider using hard security mechanisms such as access control and cryptography;
- To provide dynamic access control by supporting real-time updates to Access Control Lists and revocation lists and by managing access privileges and membership credentials through identity validation and role hierarchies;
- To develop an efficient revocation and user management scheme that ensures seamless control over user access in dynamic environments;
- To secure role-based access control by binding each role to a secret value, validated via the ACL to prevent misuse or unauthorized privilege escalation;
- To ensure secure distribution and access of decryption keys to authorized users only;
- To prevent unauthorized service access by issuing randomized role secret values and encryption keys, effectively invalidating malicious or revoked users.
2. Literature Survey
2.1. Cloud Security Using Cryptographic Approaches
2.2. Cloud Security Using Access Control Schemes
2.3. Identified Research Gaps and Objectives
- Integration of partial homomorphic encryption to perform operations on encrypted data without revealing plaintext;
- Use of access control mechanisms to restrict unauthorized data access, even from internal CSP actors;
- Encryption key management strategies that prevent CSP-level decryption, ensuring end-to-end confidentiality.
- Dynamic updates to ACL and revocation list;
- Role hierarchy and identity validation;
- Use of role secret values and ACL for validation;
- Invalidating unauthorized users.
3. Proposed Model—Reinforced Restricted Access to Handle Vulnerable CSP Using Homomorphic Encryption and Ensure Identity Management (RACHEIM)
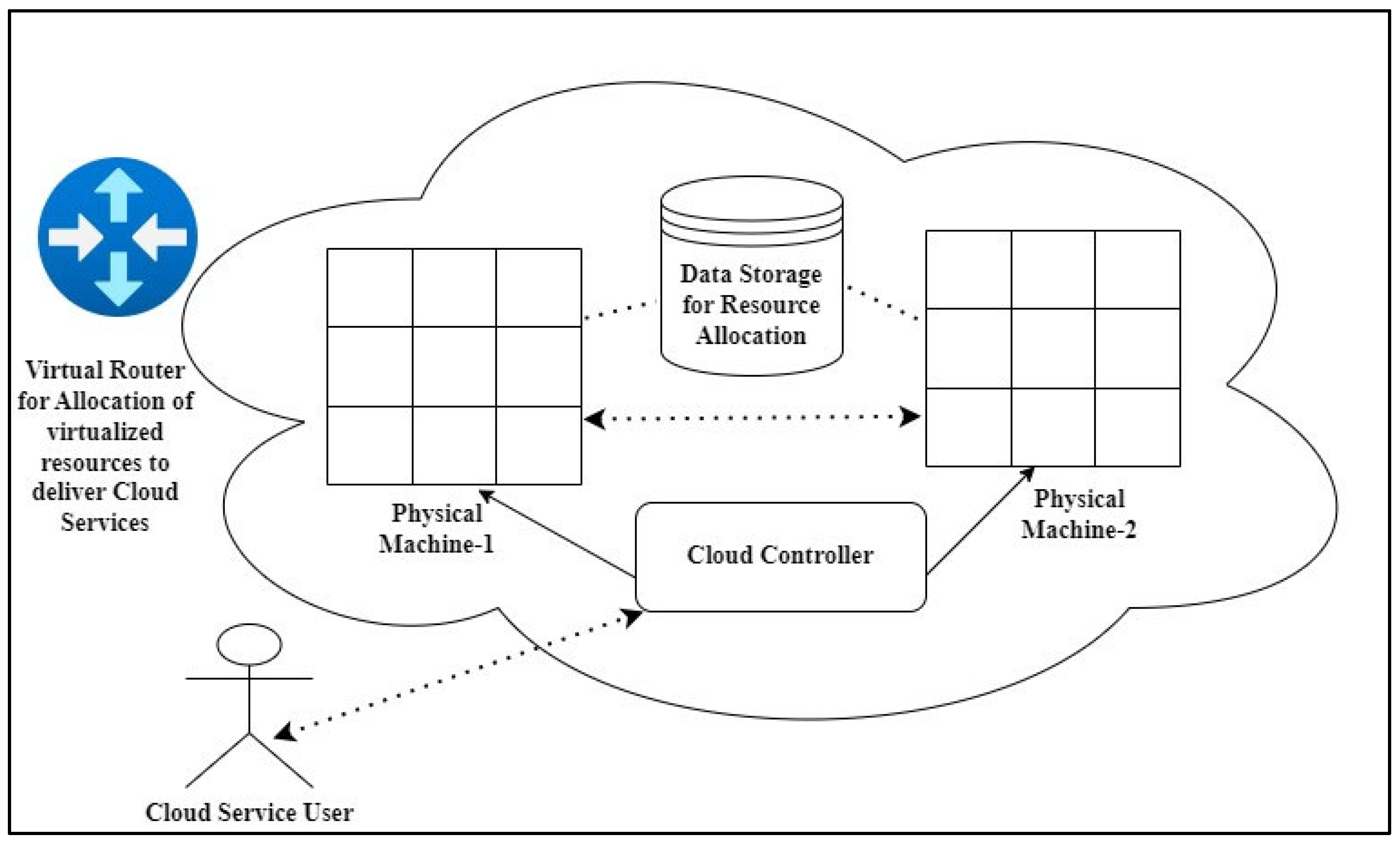
3.1. Working Principle of RACHEIM
- (i)
- Data Owner: The data owner is the primary entity whose data is under consideration for resource computation. Since the local servers of business enterprises have a heavy load of data, they often outsource their data for resource computations to cloud servers. Outsourcing of the data increases the possibility of data breach issues.
- (ii)
- Cipher Cloud Gateway: The cipher cloud gateway encapsulates the owner’s data with the arithmetic operator received from him with a homomorphic encryption function.
- (iii)
- Service User: A service user in the RACHEIM model has two variants: (a) an authentic user that has a valid user-to-role membership in the ACL; (b) an adversary that aims to inject malicious script in the Cloud domain through the service request.
- (iv)
- Access Control List (ACL): An ACL is a set of rules that specify which users/ roles are authorized to access data. The permission to grant a service is validated by authenticating appropriate role mapping in the ACL. If, for a requested service, a role-to-user mapping is not found in the ACL, then the respective request is revoked, and restricted access control is ensured.
- (v)
- Trusted Manager Module (TMM): This module manages the relationship among the roles in the role-based hierarchy. The TMM supervises the privilege rights and manages them strictly according to the authorized roles. Once the data access rights and permissions are validated, the TMM generates the keys for authentic service users and roles. The TMM is an integral component of RACHEIM.
- (vi)
- Role Monitor Module (RMM): This module administers the roles. Hence, contrary to the traditional RBAC schemes, the need to assign role managers for individual tasks is eliminated in this work. Both the TMM and the RMM are extensive entities for handling system credentials.
- (vii)
- Revocation List: A user may have had a valid user-to-role membership in the ACL at a particular instant. However, if the user behaves maliciously later by either issuing random service requests or by issuing computational resources beyond the controlled range of the assumed threshold. Such users are then revoked from the ACL and put on the revocation list. The administrator revokes the user through the system call
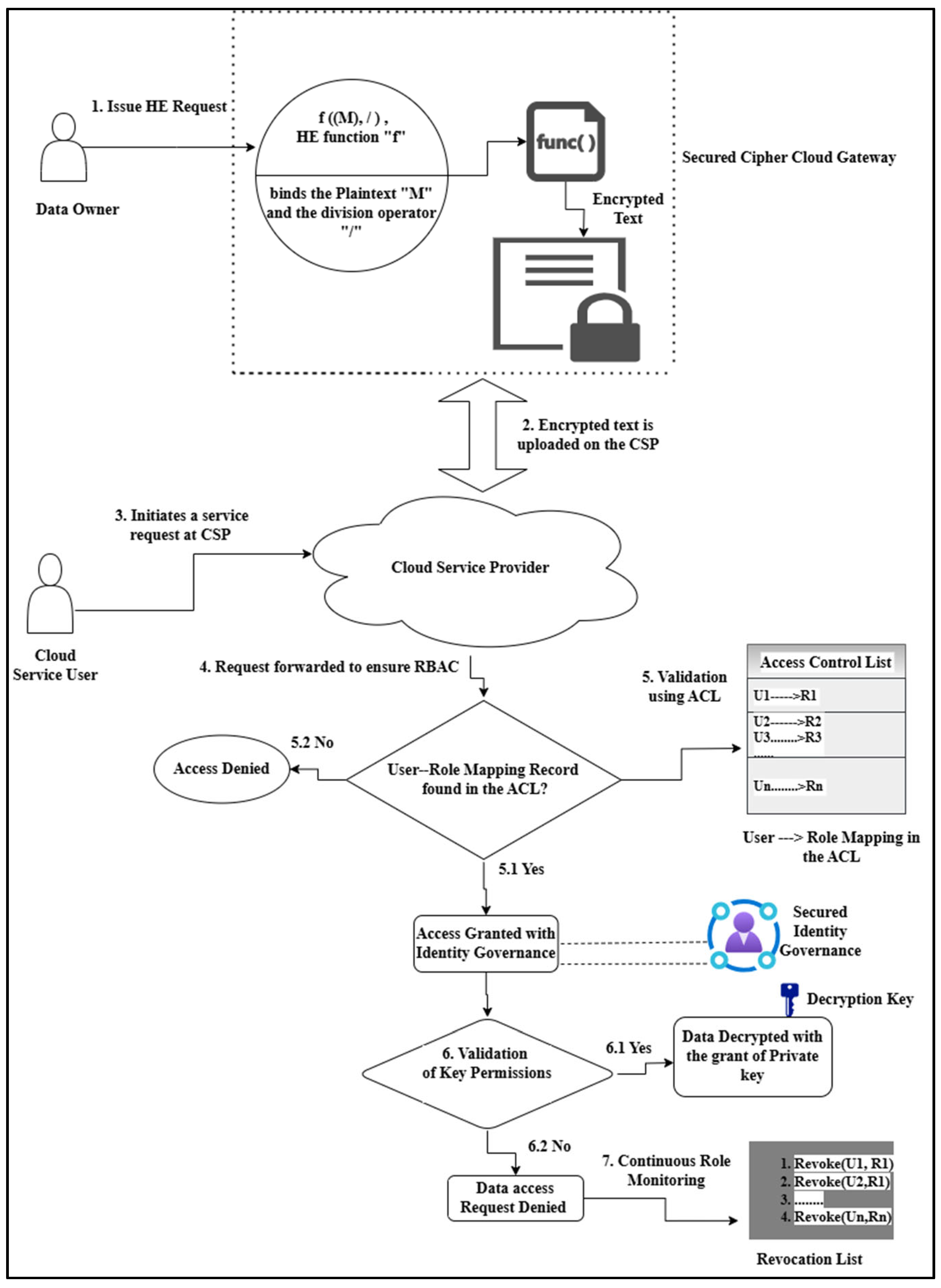
3.2. Identity and Key Validation in RACHEIM
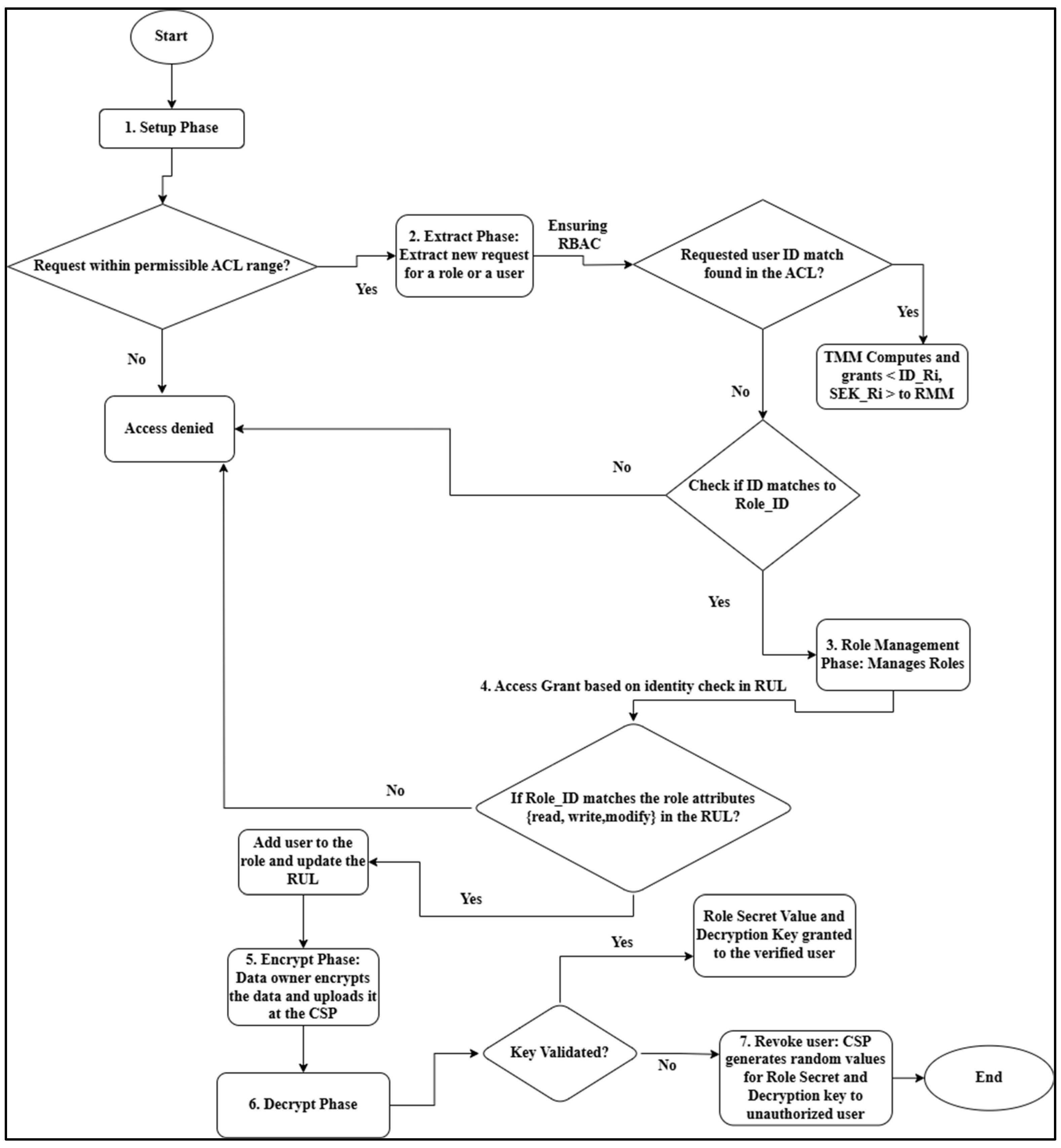
3.3. Algorithmic Procedure for RACHEIM
| Algorithm 1: RACHEIM |
| Function Setup() |
| { |
| Initiate the system and permit requests; |
| if (the request is within the permissible range of created ACL) |
| Permit request to enter Extract phase; |
| else |
| Reject the request; |
| } |
| Function Extract() |
| { |
| Input: new request (either or ); |
| if (request == new request) |
| { |
| Check ACL for the mapping of to ; |
| if (requested ID == ) |
| TMM computes and grants to the user; |
| else if (ID == ) |
| TMM computes and grants the tuple <> to RMM; |
| } |
| } |
| Function Role_Management() |
| { |
| Input: , {RUL}, role_attributes = {read, write, modify}; |
| if (attributes of match attributes of any role in {RUL}) |
| { |
| Assign a new parent role ID; |
| Update the role hierarchy; |
| } |
| } |
| Function Add_User_to_Role() |
| { |
| Input: , {RUL}, ; |
| if ( ∉ {RUL}) |
| { |
| RMM sends a tuple <> to CSP; |
| if (CSP returns a valid value for ) |
| Add user to the role ; |
| else |
| Reject the add user request; |
| } |
| } |
| Function Revoke_User() |
| { |
| Input: , {RUL}, Role (); |
| For each user where the value is inconsistent with CSP: |
| { |
| (i) RMM initiates (, revoke) at the CSP’s end; |
| (ii) CSP generates random values of secret keys: |
| and to prevent nefarious activities by the revoked users; |
| } |
| } |
| Function Encrypt() |
| { |
| The data owner encrypts a message V (Plaintext) related to role |
| using Equations (1) and (2) through a secure encryption scheme; |
| Generate Ciphertext (C) and send to CSP; |
| Ciphertext can only be decrypted by authenticated users; |
| } |
| Function Decrypt() |
| { |
| Input: , Role(); |
| if ( ∈ {RUL}) |
| { |
| CSP returns to the user; |
| User sends tuple <CT, > to CSP; |
| Access is granted and file is decrypted using Equation (3); |
| } |
| else if (∉ {RUL} OR ∈ {revoked user list}) |
| { |
| CSP generates random values: |
| and for unauthorized request IDs; |
| } |
| } |
- (i)
- Setup: This procedure handles new service requests. A service request can be for the addition of a new user_id or a new role_id. The proposed model restricts a limit on the number of role_ids an SU holds in a role-based hierarchy. Any service request exceeding the permissible limit is rejected at the administrator end by the TMM and at the extraction stage by the monitor role module (RMM).
- (ii)
- Extraction: This stage forwards the service requests initiated during the setup phase to the Trusted Group Manager module. Following calculations are carried out by the TMM. New service request parameters are matched with the existing identities (roles or users) in the ACL. If a match is found for a role, i.e., if , the TMM evaluates the secret value for the role as , where is the hash function generated to calculate the role secret value and decryption key. This secret key value is forwarded to the monitor module in the next stage.
- (iii)
- Role Management: This phase manages the entries of the role user list (RUL) and the computed role secret values for a role generated in the previous stage. The RMM analyses the attributes of a new role ( request. If a match is found between the new role and the existing role in the role user list, the new role is added to the role hierarchy with the parent role . The role hierarchy is then updated accordingly.
- (iv)
- Grant Access: This phase is critical to the security of the cloud framework. During addition of a service user, two aspects must be taken care of—a new user may be requesting the system access or an existing user requesting a service. This sub-section of the RACHEIM assumes that a new user initiating the service request for role acquisition has never had the system access. Hence, when a user Uk with identity initiates a request to join a role Ri,, the RMM adds the user to the role user list and forwards it to the cloud. The SP validates the characteristics of the user from the RUL. If a match is found, the RMM adds the role to the role hierarchy and assigns it suitable user-to-role membership.
- (v)
- Encrypt: The data owner encrypts the original message M with respect to a role using the tuple . Then, the encrypted data is sent to the cloud domain.
- (vi)
- Decrypt: Identity validation and restricted access control are the major concerns of the proposed work. Granting a decryption key to a service user gives him complete data access. This work suggests the authentication of a service user at two stages. Initially, a check is made of the identity of the requesting user . If a match is found, role mapping for the user_id is validated. If, for a user_id, the legitimate mapping credentials exists then the user is subsequently given the decryption key, . However, if a match is not found, then the decryption key request is rejected.
- (vii)
- Revoke: The role secret values computed by the TMM play a crucial part in validating the authenticity of a service user. The role secret value plays a crucial role in removing an SU from the assigned role. Every user ID whose differs from the CSP role secret key value is added to the revocation list. The RMM issues ( to the CSP and random values of and values, are generated by the CSP to manage the revoked users at later stages. The flowchart for the algorithmic procedure of the proposed model is depicted in Figure 3.
3.4. Security Analysis of RACHEIM
3.4.1. Privilege Escalation and Service-Injection Attack
- Ensuring that the role R1 has permissions strictly required for role hierarchy control, not unnecessary access to sensitive data;
- Following Key Isolation Rule for each role that maintains cryptographic separation between the roles, so that even if R1 is compromised, it does not expose the access keys to roles R2-R6;
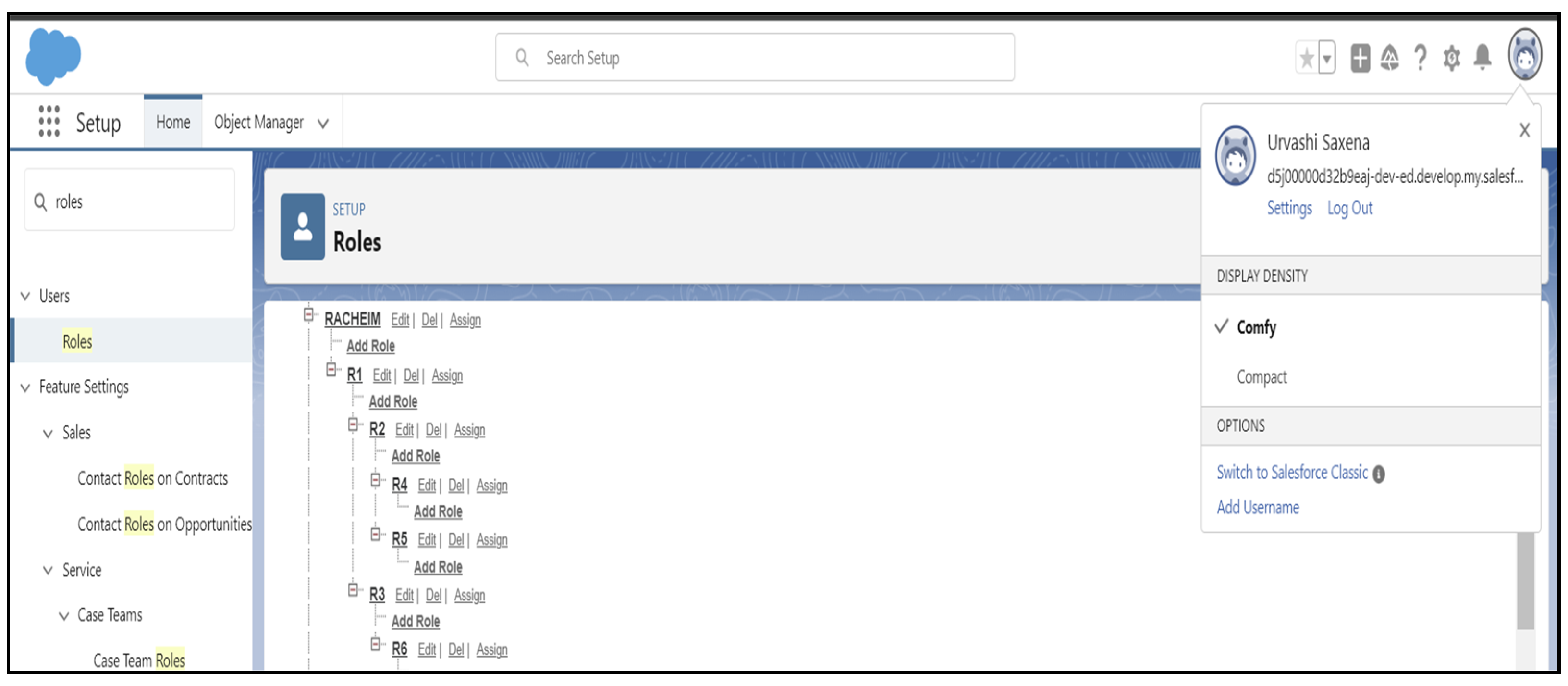
- Appropriate validation rules are executed at each stage for every role using Salesforce Cloud to check user-to-role mapping and access permissions;
- Continuously monitoring role inheritance hierarchy to identify any excessive privilege propagation.
3.4.2. Scheme to Monitor Sybil Attack
3.4.3. Scheme for Dynamic Update of Access Parameters and Handling Revoked Users
3.4.4. Threat-Response Mapping for RACHEIM
4. Simulation Results
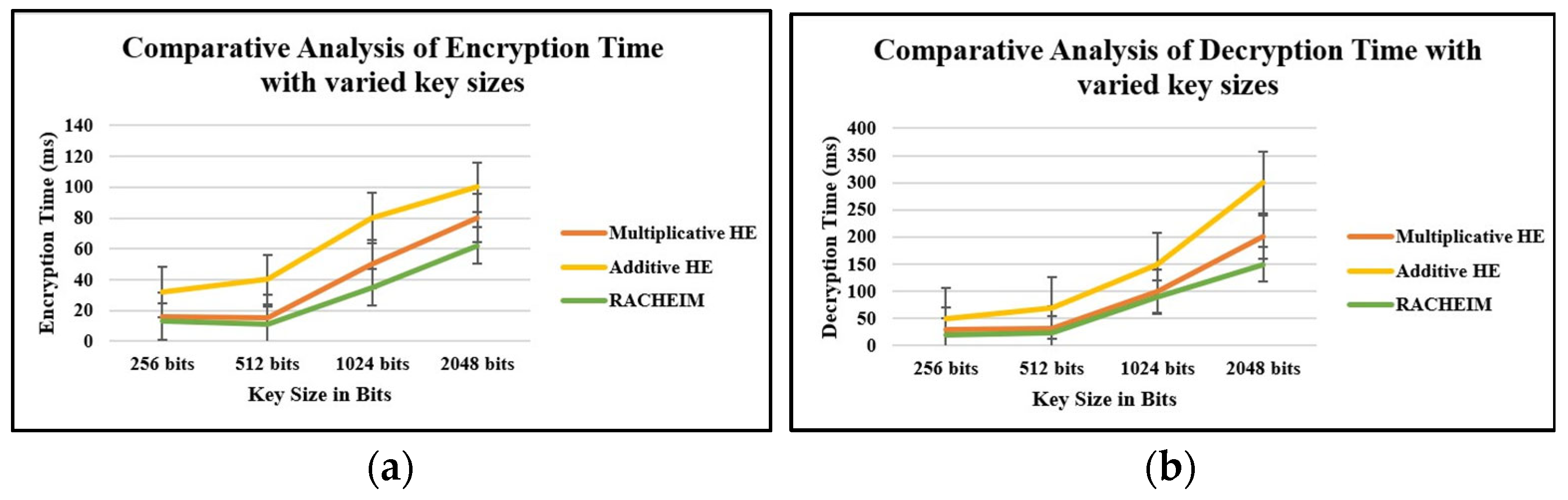
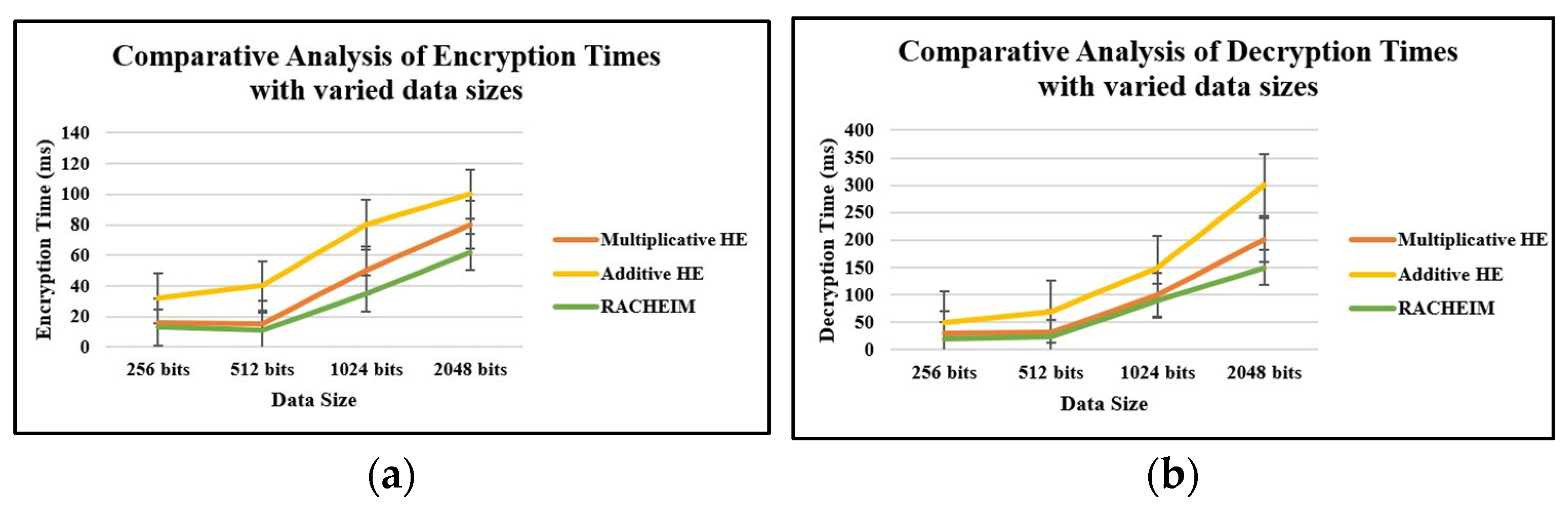
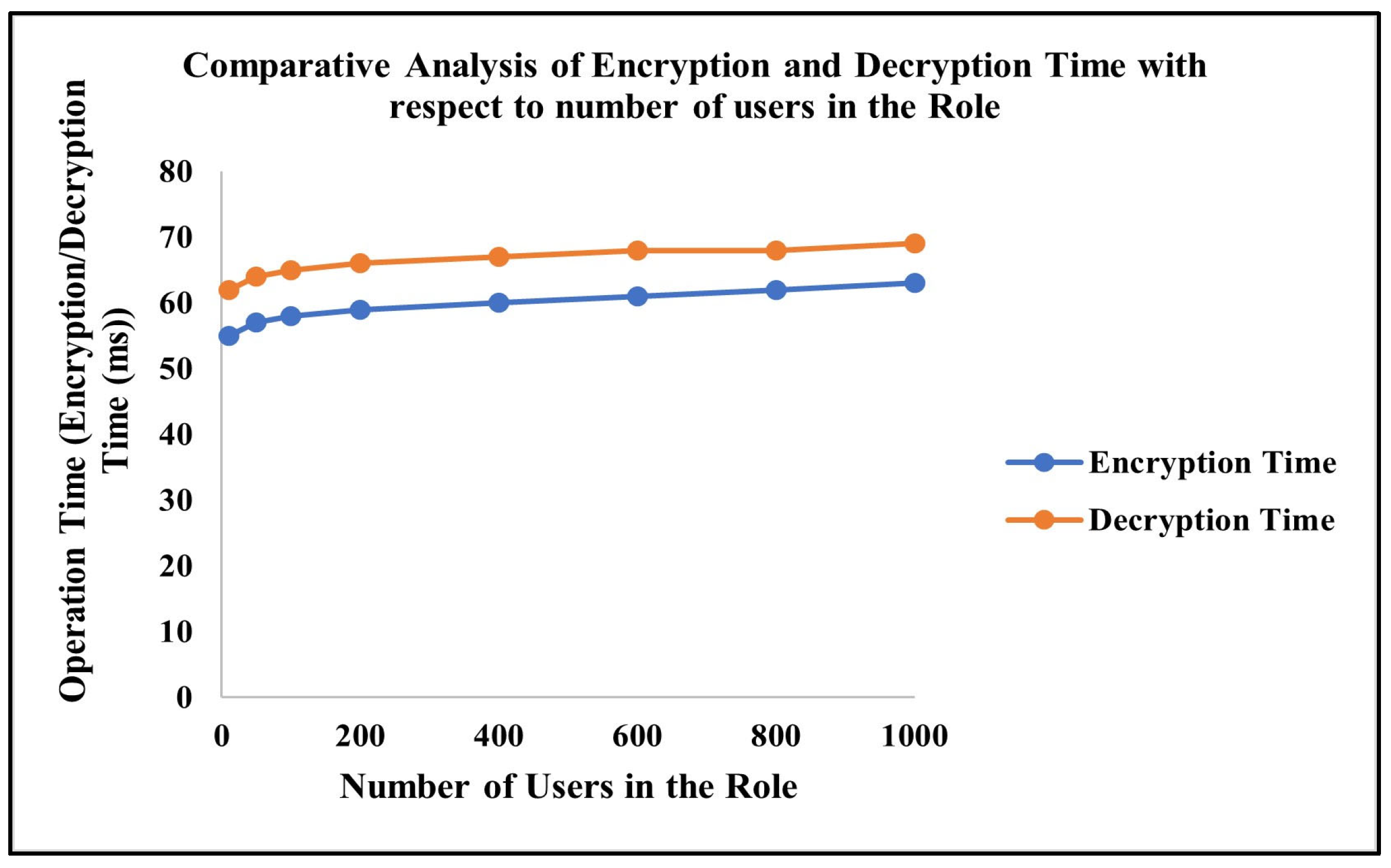
4.1. Analysis Based on Time
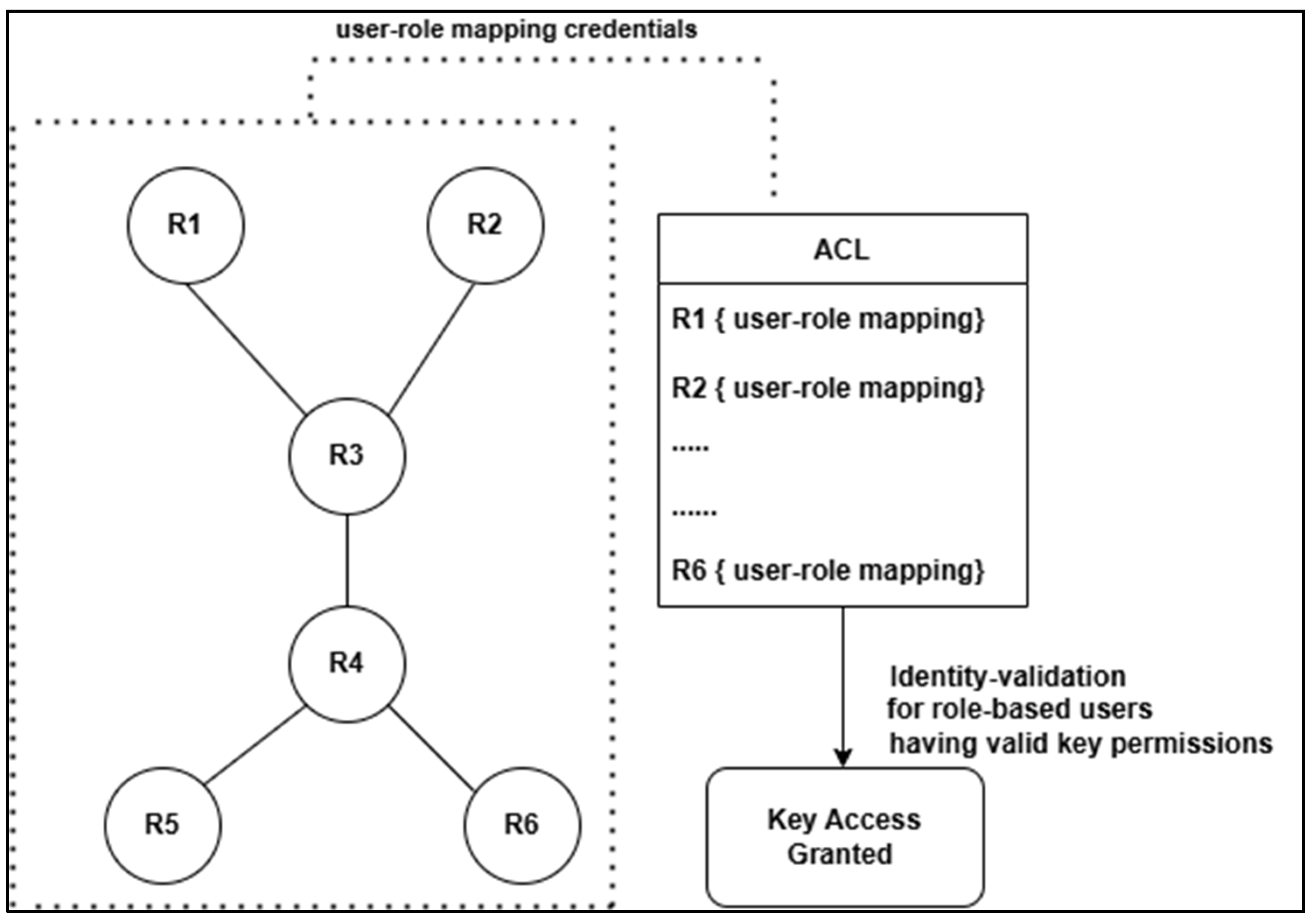
4.2. Role Hierarchy Validation
4.3. Performance Overhead and Scalability Analysis
- The proposed work has been simulated using the Salesforce cloud platform that supports dynamic user role configurations, hierarchical access models, and scalable resource provisioning. This enabled the validation of the system’s performance in the context of evolving access demands and enterprise role hierarchies.
- The proposed approach incorporates partial homomorphic encryption specifically for securing sensitive access control elements such as role secret values and user decryption keys, rather than encrypting bulk data. This selective encryption strategy significantly reduces computational costs and ensures that performance bottlenecks are avoided during frequent access validations.
- Furthermore, to enhance scalability, the RACHEIM model leverages Salesforce’s metadata-driven policy management, which allows for dynamic updates of access control policies and inheritance hierarchies without requiring re-encryption of existing data. The work also implements a checkpoint-based validation mechanisms which limits redundant cryptographic operations and further minimizes latency, particularly as the role hierarchy expands.
5. Formal Analysis of RACHEIM
6. Conclusions
7. Future Work and Limitations
- Providing secure access enforcement to spatial data and user-generated assets stored in the cloud through role-tokenized credentials;
- Allowing dynamic role mapping and key distribution for participants in collaborative environments (e.g., multiple VR users with differing access levels);
- Preserving data confidentiality during real-time computations (e.g., rendering 3D models or avatar interactions) via partial homomorphic encryption without revealing plaintext data to the cloud or third parties.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| ABAC | Attribute-Based Access Control |
| ABE | Attribute-Based Encryption |
| ACL | Access Control List |
| AD | Active Directory |
| AES | Advanced Encryption Standard |
| API | Application Programming Interface |
| AR | Augmented Reality |
| AWS | Amazon Web Services |
| B2B | Business-to-Business |
| B2C | Business-to-Customer |
| CCG | Cipher Cloud Gateway |
| CDC | Cloud Data Centre |
| CIA | Confidentiality, Integrity, and Availability |
| CRM | Customer Relationship Management |
| CSP | Cloud Service Provider |
| DES | Data Encryption Standard |
| DoS | Denial-of-Service |
| FHE | Fully Homomorphic Encryption |
| HE | Homomorphic Encryption |
| HIBE | Hierarchical Identity-Based Encryption |
| HKM | Hierarchical Key Management |
| IAM | Identity and Access Management |
| IBE | Identity-Based Encryption |
| ICS | Industrial Control System |
| MFA | Multi-Factor Authentication |
| OAuth | Open Authorization |
| OCI | Oracle Cloud Infrastructure |
| PHE | Partial Homomorphic Encryption |
| RBAC | Role-Based Access Control |
| RBAHE | Role-Based Access Using Homomorphic Encryption |
| RBAIBE | Role-Based Access Using Identity-Based Encryption |
| RBE | Role-Based Encryption |
| RMM | Role Monitor Module |
| RSA | Rivest Shamir Adleman |
| RUL | Role User List |
| SLA | Service Level Agreement |
| SP | Service Provider |
| SSO | Single-Sign-On |
| SU | Service User |
| TMS | Trust Management System |
| TMM | Trusted Manager Module |
| VR | Virtual Reality |
| XSS | Cross-Site Scripting |
References
- Drapkin, A. Data Breaches That Have Happened in 2022 and 2023 So Far; Tech.co: London, UK, 2023. [Google Scholar]
- Bassett, G.; Hylender, C.D.; Langlois, P.; Pinto, A.; Widup, S. Data Breach Investigations Report; Verizon Business: New York, NY, USA, 2021. [Google Scholar]
- Hakim, A.R.; Ramli, K.; Gunawan, T.S.; Windarta, S. A Novel Digital Forensic Framework for Data Breach Investigation. IEEE Access 2023, 11, 42644–42659. [Google Scholar] [CrossRef]
- IBM Security. Cost of a Data Breach Report; IBM Corporation: Armonk, NY, USA, 2021; Available online: https://www.ibm.com/reports/data-breach (accessed on 5 April 2025).
- IBM Security. Identity Comes Under Attack, Straining Enterprises Recovery Time from Breaches; IBM Corporation: Armonk, NY, USA, 2024; Available online: https://newsroom.ibm.com/2024-02-21-IBM-Report-Identity-Comes-Under-Attack,-Straining-Enterprises-Recovery-Time-from-Breaches (accessed on 7 April 2025).
- Morgan, S. Cybercrime to Cost the World $10.5 Trillion Annually by 2025. Cybercrime Mag. 2020, 13, 11. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-Based Encryption for Fine-Grained Access Control of Encrypted Data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; pp. 89–98. [Google Scholar]
- Hong, M.Q.; Wang, P.Y.; Zhao, W.B. Homomorphic Encryption Scheme Based on Elliptic Curve Cryptography for Privacy Protection of Cloud Computing. In Proceedings of the 2016 IEEE 2nd International Conference on Big Data Security on Cloud (Big Data Security), IEEE International Conference on High Performance and Smart Computing (HPSC), and IEEE International Conference on Intelligent Data and Security (IDS), New York, NY, USA, 9–10 April 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 152–157. [Google Scholar]
- Yu, S.; Wang, C.; Ren, K.; Lou, W. Achieving secure, scalable, and fine-grained data access control in cloud computing. In Proceedings of the 2010 IEEE INFOCOM, San Diego, CA, USA, 14–19 March 2010; pp. 1–9. [Google Scholar]
- Zhu, Y.; Ma, D.; Hu, C.J.; Huang, D. How to use attribute-based encryption to implement role-based access control in the cloud. In Proceedings of the 2013 International Workshop on Security in Cloud Computing, Hangzhou, China, 8 May 2013; pp. 33–40. [Google Scholar]
- Ngo, C.; Demchenko, Y.; de Laat, C. Multi-tenant attribute-based access control for cloud infrastructure services. J. Inf. Secur. Appl. 2016, 27, 65–84. [Google Scholar] [CrossRef]
- Duncan, R. A multi-cloud world requires a multi-cloud security approach. Comput. Fraud. Secur. 2020, 2020, 11–12. [Google Scholar] [CrossRef]
- Scott, B. How a zero-trust approach can help to secure your AWS environment. Netw. Secur. 2018, 2018, 5–8. [Google Scholar] [CrossRef]
- Jain, P.; Lu, E. Identity and Access Management-Introducing Oracle Universal Authenticator for Secure and Seamless Access. 2024. Available online: https://www.oracle.com/au/security/identity-management/access-management/ (accessed on 5 April 2025).
- Ritcher, F. Cloud Infrastructure Market. 2025. Available online: https://www.statista.com/chart/18819/worldwide-market-share-of-leading-cloud-infrastructure-service-providers (accessed on 9 April 2025).
- Gunda, S. Azure Synapse Analytics Security White Paper: Access Control—Azure Synapse Analytics. 2023. Available online: https://learn.microsoft.com/en-us/azure/synapse-analytics/guidance/security-white-paper-access-control#synapse-role-based-access-control (accessed on 22 March 2025).
- Amazon Web Services, Inc. AWS Whitepapers & Guides. Available online: https://aws.amazon.com/whitepapers (accessed on 30 May 2025).
- Microsoft. What Is Identity and Access Management (IAM)? Microsoft Corporation: Redmond, WA, USA, 2023; Available online: https://www.microsoft.com/en-au/security/business/security-101/what-is-identity-access-management-iam (accessed on 4 April 2025).
- Google Cloud. Google Cloud Whitepapers. Available online: https://cloud.google.com (accessed on 7 April 2025).
- Google Cloud. Identity and Access Management Documentation. Available online: https://cloud.google.com/iam/docs (accessed on 4 April 2025).
- IBM Security. Cost of a Data Breach; IBM Corp.: Armonk, NY, USA, 2023; Available online: https://www.ibm.com/reports/data-breach (accessed on 7 April 2025).
- Farokhi, F.; Shames, I.; Batterham, N. Secure and private control using semi-homomorphic encryption. Control Eng. Pract. 2017, 67, 13–20. [Google Scholar] [CrossRef]
- Wei, Z. A Pairing-Based Homomorphic Encryption Scheme for Multi-User Settings. In Cryptography: Breakthroughs in Research and Practice; IGI Global: Hershey, PA, USA, 2020; pp. 295–305. [Google Scholar]
- Zaraket, C.; Hariss, K.; Chamoun, M.; Nicolas, T. Cloud-based private data analytic using secure computation over encrypted data. J. King Saud Univ. Comput. Inf. Sci. 2022, 34, 4931–4942. [Google Scholar] [CrossRef]
- Cheon, J.H.; Kim, A.; Kim, M.; Song, Y. Homomorphic encryption for arithmetic of approximate numbers. In Proceedings of the Advances in Cryptology—ASIACRYPT 2017: 23rd International Conference on the Theory and Applications of Cryptology and Information Security, Hong Kong, China, 3–7 December 2017; pp. 409–437. [Google Scholar]
- Moon, S.; Lee, Y. An Efficient Encrypted Floating—Point Representation Using HEAAN and TFHE. Secur. Commun. Netw. 2020, 2020, 1250295. [Google Scholar] [CrossRef]
- Youn, T.Y.; Jho, N.S.; Chang, K.Y. Design of additive homomorphic encryption with multiple message spaces for secure and practical storage services over encrypted data. J. Supercomput. 2018, 74, 3620–3638. [Google Scholar] [CrossRef]
- Besharati, E.; Naderan, M.; Namjoo, E. LR-HIDS: Logistic Regression Host-Based Intrusion Detection System for Cloud Environments. J. Ambient. Intell. Humaniz. Comput. 2019, 10, 3669–3692. [Google Scholar] [CrossRef]
- Zhu, Y.; Hu, H.X.; Ahn, G.J.; Wang, H.X.; Wang, S.B. Provably Secure Role-Based Encryption with Revocation Mechanism. J. Comput. Sci. Technol. 2011, 26, 697–710. [Google Scholar] [CrossRef][Green Version]
- Blundo, C.; Cimato, S.; De Capitani di Vimercati, S.; De Santis, A.; Foresti, S.; Paraboschi, S.; Samarati, P. Efficient Key Management for Enforcing Access Control in Outsourced Scenarios. In Emerging Challenges for Security, Privacy and Trust—Proceedings of the 24th IFIP TC 11 International Information Security Conference (SEC 2009), Pafos, Cyprus, 18–20 May 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 364–375. [Google Scholar]
- Karthika, A.; Muthukumaran, N. An ADS-PAYG Approach Using Trust Factor Against Economic Denial of Sustainability Attacks in Cloud Storage. Wirel. Pers. Commun. 2022, 122, 69–85. [Google Scholar] [CrossRef]
- Zhou, L.; Varadharajan, V.; Hitchens, M. Trust Enhanced Cryptographic Role-Based Access Control for Secure Cloud Data Storage. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2381–2395. [Google Scholar] [CrossRef]
- Ghafoorian, M.; Abbasinezhad-Mood, D.; Shakeri, H. A Thorough Trust and Reputation Based RBAC Model for Secure Data Storage in the Cloud. IEEE Trans. Parallel Distrib. Syst. 2018, 30, 778–788. [Google Scholar] [CrossRef]
- Mahajan, S.; Mahajan, S.; Jadhav, S.; Kolate, S. Trust Management in E-Commerce Websites. Int. Res. J. Eng. Technol. 2017, 4, 2934–2936. [Google Scholar]
- Noor, T.H.; Sheng, Q.Z.; Yao, L.; Dustdar, S.; Ngu, A.H. CloudArmor: Supporting Reputation-Based Trust Management for Cloud Services. IEEE Trans. Parallel Distrib. Syst. 2015, 27, 367–380. [Google Scholar] [CrossRef]
- Almanasir, R.; Al-solomon, D.; Indrawes, S.; Almaiah, M.; Islam, U.; Alshar’e, M. Classification of threats and countermeasures of cloud computing. J. Cyber Secur. Risk Audit. 2025, 2, 27–42. [Google Scholar] [CrossRef]
- Aljumaiah, O.; Jiang, W.; Addula, S.R.; Almaiah, M.A. Analyzing cybersecurity risks and threats in IT infrastructure based on NIST framework. J. Cyber Secur. Risk Audit. 2025, 2, 12–26. [Google Scholar] [CrossRef]
- Almuqren, A.A. Cybersecurity threats, countermeasures and mitigation techniques on the IoT: Future research directions. J. Cyber Secur. Risk Audit. 2025, 1, 1–11. [Google Scholar] [CrossRef]
- Alshuaibi, A.; Almaayah, M.; Ali, A. Machine learning for cybersecurity issues: A systematic review. J. Cyber Secur. Risk Audit. 2025, 1, 36–46. [Google Scholar] [CrossRef]
- Alotaibi, E.; Sulaiman, R.B.; Almaiah, M. Assessment of cybersecurity threats and defense mechanisms in wireless sensor networks. J. Cyber Secur. Risk Audit. 2025, 1, 47–59. [Google Scholar] [CrossRef]
- Uikey, C.; Bhilare, D.S. TrustRBAC: Trust Role-Based Access Control Model in Multi-Domain Cloud Environments. In Proceedings of the 2017 International Conference on Information, Communication, Instrumentation and Control (ICICIC), Indore, India, 17–19 August 2017; pp. 1–7. [Google Scholar]
- Verizon. Data Breach Investigations Report; Verizon Enterprise Solutions: New York, NY, USA, 2021; Available online: http://www.verizonbusiness.com/resources/security/data_breach_report.pdf (accessed on 5 June 2025).
- Mattila, M.; Yrjölä, M.; Hautamäki, P. Digital Transformation of Business-to-Business Sales: What Needs to Be Unlearned? J. Pers. Sell. Sales Manag. 2021, 41, 113–129. [Google Scholar] [CrossRef]
- Bulao, J. How Many Companies Use Cloud Computing in 2022? All You Need To Know. 2022. Available online: https://techjury.net/blog/how-many-companies-use-cloud-computing/#gref (accessed on 5 April 2025).
- Biham, E.; Shamir, A. Differential Cryptanalysis. J. Cryptol. 2011, 24, 332–336. [Google Scholar]
- Daemen, J.; Rijmen, V. The Design of Rijndael; Springer-Verlag: New York, NY, USA, 2002; Volume 2. [Google Scholar]
- Gentry, C. A Fully Homomorphic Encryption Scheme; Stanford University: Stanford, CA, USA, 2009. [Google Scholar]
- Brakerski, Z.; Vaikuntanathan, V. Efficient Fully Homomorphic Encryption from (Standard) LWE. SIAM J. Comput. 2014, 43, 831–871. [Google Scholar] [CrossRef]
- Brakerski, Z.; Vaikuntanathan, V. Fully Homomorphic Encryption from Ring-LWE and Security for Key Dependent Messages. In Proceedings of the Annual Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 505–524. [Google Scholar]
- Boneh, D.; Goh, E.J.; Nissim, K. Evaluating 2-DNF Formulas on Ciphertexts. In Proceedings of the 2nd Theory of Cryptography Conference (TCC 2005), Cambridge, MA, USA, 10–12 February 2005; Springer: Berlin/Heidelberg, Germany, 2005; Volume 2, pp. 325–341. [Google Scholar]
- Cheon, J.H.; Coron, J.S.; Kim, J.; Lee, M.S.; Lepoint, T.; Tibouchi, M.; Yun, A. Batch Fully Homomorphic Encryption over the Integers. In Proceedings of the 32nd Annual International Conference on the Theory and Applications of Cryptographic Techniques—EUROCRYPT 2013, Athens, Greece, 26–30 May 2013; Springer: Berlin/Heidelberg, Germany, 2013; Volume 32, pp. 315–335. [Google Scholar]
- Cheon, J.H.; Lee, H.T.; Seo, J.H. A New Additive Homomorphic Encryption Based on the Co-ACD Problem. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014; ACM: New York, NY, USA, 2014; pp. 287–298. [Google Scholar]
- Coron, J.S.; Mandal, A.; Naccache, D.; Tibouchi, M. Fully Homomorphic Encryption over the Integers with Shorter Public Keys. In Proceedings of the Annual Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 487–504. [Google Scholar]
- Coron, J.S.; Naccache, D.; Tibouchi, M. Public Key Compression and Modulus Switching for Fully Homomorphic Encryption over the Integers. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques (EUROCRYPT 2012), Cambridge, UK, 15–19 April 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 446–464. [Google Scholar]
- Van Dijk, M.; Gentry, C.; Halevi, S.; Vaikuntanathan, V. Fully Homomorphic Encryption over the Integers. In Proceedings of the Advances in Cryptology–EUROCRYPT 2010: 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques, French Riviera, France, 30 May–3 June 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 24–43. [Google Scholar]
- Gentry, C. Fully Homomorphic Encryption Using Ideal Lattices. In Proceedings of the 41st Annual ACM Symposium on Theory of Computing (STOC 2009), Bethesda, MD, USA, 31 May–2 June 2009; ACM: New York, NY, USA, 2009; pp. 169–178. [Google Scholar]
- Gentry, C.; Halevi, S. Implementing Gentry’s Fully-Homomorphic Encryption Scheme. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques (EUROCRYPT 2011), Tallinn, Estonia, 15–19 May 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 129–148. [Google Scholar]
- Gentry, C.; Halevi, S.; Smart, N.P. Fully Homomorphic Encryption with Polylog Overhead. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques (EUROCRYPT 2012), Cambridge, UK, 15–19 April 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 465–482. [Google Scholar]
- Gentry, C.; Halevi, S.; Vaikuntanathan, V. A Simple BGN-Type Cryptosystem from LWE. In Proceedings of the Advances in Cryptology–EUROCRYPT 2010: 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques, French Riviera, France, 30 May–3 June 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 506–522. [Google Scholar]
- Aftab, M.U.; Qin, Z.; Quadri, S.F.; Zakria; Javed, A.; Nie, X. Role-Based ABAC Model for Implementing Least Privileges. In Proceedings of the 2019 8th International Conference on Software and Computer Applications (ICSCA 2019), Penang, Malaysia, 19–21 February 2019; pp. 467–471. [Google Scholar]
- Rashid, A.; Masood, A.; Abbas, H. Cryptographic Framework for Role Control Remedy: A Secure Role Engineering Mechanism for Single Authority Organizations. Future Gener. Comput. Syst. 2021, 117, 245–258. [Google Scholar] [CrossRef]
- Ragothaman, K.; Wang, Y.; Rimal, B.; Lawrence, M. Access Control for IoT: A Survey of Existing Research, Dynamic Policies and Future Directions. Sensors 2023, 23, 1805. [Google Scholar] [CrossRef]
- Teh, J.S.; Alawida, M.; Sii, Y.C. Implementation and Practical Problems of Chaos-Based Cryptography Revisited. J. Inf. Secur. Appl. 2020, 50, 102421. [Google Scholar] [CrossRef]
- Zhou, L.; Varadharajan, V.; Hitchens, M. Enforcing role-based access control for secure data storage in the cloud. Comput. J. 2011, 54, 1675–1687. [Google Scholar] [CrossRef]
- Balamurugan, B.; Venkata Krishna, P. Enhanced role-based access control for cloud security. In Artificial Intelligence and Evolutionary Algorithms in Engineering Systems: Proceedings of ICAEES 2014; Springer: New Delhi, India, 2015; Volume 1, pp. 837–852. [Google Scholar]
- Sultan, N.H.; Varadharajan, V.; Zhou, L.; Barbhuiya, F.A. A role-based encryption (RBE) scheme for securing outsourced cloud data in a multi-organization context. IEEE Trans. Serv. Comput. 2022, 16, 1647–1661. [Google Scholar]
- Chen, H.C. A trusted user-to-role and role-to-key access control scheme. Soft Comput. 2016, 20, 1721–1733. [Google Scholar] [CrossRef]
- Zhou, X.; Liu, J.; Liu, W.; Wu, Q. Anonymous role-based access control on e-health records. In Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security (AsiaCCS ’16), Xi’an, China, 30 May–3 June 2016; pp. 559–570. [Google Scholar]
- Sandhu, R.; Bhamidipati, V.; Munawer, Q. The ARBAC97 model for role-based administration of roles. ACM Trans. Inf. Syst. Secur. 1999, 2, 105–135. [Google Scholar]
- Sandhu, R.; Munawer, Q. The ARBAC99 model for administration of roles. In Proceedings of the 15th Annual Computer Security Applications Conference (ACSAC’99), Phoenix, AZ, USA, 6–10 December 1999; pp. 229–238. [Google Scholar]
- Oh, S.; Sandhu, R. A model for role administration using organization structure. In Proceedings of the Seventh ACM Symposium on Access Control Models and Technologies (SACMAT ‘02), Monterey, CA, USA, 3–4 June 2002; pp. 155–162. [Google Scholar]
- Oh, S.; Sandhu, R.; Zhang, X. An effective role administration model using organization structure. ACM Trans. Inf. Syst. Secur. 2006, 9, 113–137. [Google Scholar] [CrossRef][Green Version]
- Crampton, J. Administrative scope and role hierarchy operations. In Proceedings of the Seventh ACM Symposium on Access Control Models and Technologies (SACMAT 2002), Monterey, CA, USA, 3–4 June 2002; pp. 145–154. [Google Scholar]
- Akl, S.G.; Taylor, P.D. Cryptographic solution to a problem of access control in a hierarchy. ACM Trans. Comput. Syst. 1983, 1, 239–248. [Google Scholar] [CrossRef]
- Miklau, G.; Suciu, D. Controlling access to published data using cryptography. In Proceedings of the 2003 VLDB Conference, Berlin, Germany, 9–12 September 2003; Morgan Kaufmann: San Francisco, CA, USA, 2003; pp. 898–909. [Google Scholar]
- Di Vimercati, S.D.C.; Foresti, S.; Jajodia, S.; Paraboschi, S.; Samarati, P. A data outsourcing architecture combining cryptography and access control. In Proceedings of the 2007 ACM Workshop on Computer Security Architecture (CSAW 2007), Fairfax, VA, USA, 2 November 2007; pp. 63–69. [Google Scholar]
- Hassen, H.R.; Bouabdallah, A.; Bettahar, H.; Challal, Y. Key management for content access control in a hierarchy. Comput. Netw. 2007, 51, 3197–3219. [Google Scholar] [CrossRef]
- Atallah, M.J.; Blanton, M.; Frikken, K.B. Key Management for Non-Tree Access Hierarchies. In Proceedings of the Eleventh ACM Symposium on Access Control Models and Technologies (SACMAT ’06), Lake Tahoe, CA, USA, 7–9 June 2006; pp. 11–18. [Google Scholar]
- Gentry, C.; Silverberg, A. Hierarchical ID-based cryptography. In Proceedings of the Advances in Cryptology—ASIACRYPT 2002: 8th International Conference on the Theory and Application of Cryptology and Information Security, Queenstown, New Zealand, 1–5 December 2002; Proceedings 8. Springer: Berlin/Heidelberg, Germany, 2002; pp. 548–566. [Google Scholar]
- Boneh, D.; Boyen, X.; Goh, E.J. Hierarchical identity-based encryption with constant size ciphertext. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 440–456. [Google Scholar]
- Di Vimercati, S.D.C.; Foresti, S.; Jajodia, S.; Paraboschi, S.; Samarati, P. Over-encryption: Management of access control evolution on outsourced data. In Proceedings of the 33rd International Conference on Very Large Data Bases, Vienna, Austria, 23–27 September 2007; pp. 123–134. [Google Scholar]
- Teli, T.A.; Masoodi, F.S.; Bahmdi, A.M. HIBE: Hierarchical Identity-Based Encryption. In Functional Encryption; Springer International Publishing: Cham, Switzerland, 2021; pp. 187–203. [Google Scholar]
- Atallah, M.J.; Blanton, M.; Fazio, N.; Frikken, K.B. Dynamic and efficient key management for access hierarchies. ACM Trans. Inf. Syst. Secur. 2009, 12, 1–43. [Google Scholar] [CrossRef]
- Yuan, S.; Reniers, G.; Yang, M. Integrated management of safety and security barriers in chemical plants to cope with emerging cyber-physical attack risks under uncertainties. Reliab. Eng. Syst. Saf. 2024, 250, 110320. [Google Scholar] [CrossRef]
- Levitin, G.; Xing, L.; Dai, Y. Security and reliability of N-version cloud-based task solvers with individual version cancellation under data theft attacks. Reliab. Eng. Syst. Saf. 2021, 216, 107920. [Google Scholar] [CrossRef]
- Saxena, U.R.; Alam, T. Role-based access using partial homomorphic encryption for securing cloud data. Int. J. Syst. Assur. Eng. Manag. 2023, 14, 950–966. [Google Scholar] [CrossRef]
- Saxena, U.R.; Alam, T. Role based access control using identity and broadcast-based encryption for securing cloud data. J. Comput. Virol. Hacking Tech. 2022, 18, 171–182. [Google Scholar] [CrossRef]
- Saxena, U.R.; Alam, T. Provisioning trust-oriented role-based access control for maintaining data integrity in cloud. Int. J. Syst. Assur. Eng. Manag. 2023, 14, 2559–2578. [Google Scholar] [CrossRef]
- Saxena, U.R.; Alam, T. Recommendation-based trust computation and rating prediction model for security enhancement in cloud computing systems. Serv. Orient. Comput. Appl. 2023, 17, 239–257. [Google Scholar] [CrossRef]
- Saxena, U.R.; Alam, T. Modified identify and broadcast-based encryption scheme to secure cloud. In Proceedings of the 2022 International Conference on Computational Intelligence and Sustainable Engineering Solutions (CISES), Agra, India, 6–7 May 2022; pp. 289–294. [Google Scholar]
- Grillenmeier, G. Ransomware–One of the Biggest Threats Facing Enterprises Today. Netw. Secur. 2022, 2022, 3–5. [Google Scholar] [CrossRef]
- El Makkaoui, K.; Ezzati, A.; Beni-Hssane, A.; Ouhmad, S. Fast Cloud–Paillier Homomorphic Schemes for Protecting Confidentiality of Sensitive Data in Cloud Computing. J. Ambient Intell. Humaniz. Comput. 2020, 11, 2205–2214. [Google Scholar] [CrossRef]
- Tariq, H.; Agarwal, P. Secure Keyword Search Using Dual Encryption in Cloud Computing. Int. J. Inf. Technol. 2020, 12, 1063–1072. [Google Scholar] [CrossRef]
- Erickson, J. Prediction: 80% of Enterprise IT Will Move to the Cloud by 2025. 2019. Available online: https://www.forbes.com/sites/oracle/2019/02/07/prediction-80-of-enterprise-it-will-move-to-the-cloud-by-2025/?sh=91d331e2a676 (accessed on 5 April 2025).
- Canetti, R.; Krawczyk, H. Analysis of Key-Exchange Protocols and Their Use for Building Secure Channels. In Advances in Cryptology—EUROCRYPT 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 453–474. [Google Scholar]
| Research Work | Contributions | Gaps |
|---|---|---|
| [43] | Demonstrates growth in B2B and B2C cloud adoption. | Does not address cloud security or access control. |
| [44] | Forecasts over 70% business workload will migrate to cloud by 2025. | Security challenges with increased cloud adoption not addressed. |
| [45,46] | Enable convenient storage of encrypted data using DES and AES. | Incapable of computation without revealing secret key. |
| [47] | Introduced homomorphic encryption for computation on encrypted data. | Limited efficiency and practical implementation concerns. |
| [48,49,50,51,52,53,54,55,56,57,58,59] | Describes evolution of Fully Homomorphic Encryption (FHE) for cloud security. | Challenges in practical deployment of FHE due to high overhead. |
| [60] | ABAC allows flexible access control through attribute-based rules. | Lacks detailed encryption scheme integration. |
| [61,62] | Highlights the necessity of secure access models in growing cloud environments. | Conventional models lack access enforcement mechanisms. |
| [63,64] | Points out the limitations of conventional encryption in enforcing access rights. | Do not enforce user role privileges securely. |
| [66] | Proposed Role-Based Encryption (RBE) to secure cloud access control. | Limited to role mapping; lacks dynamic revocation handling. |
| [32,67,68] | Proposed models address nefarious activity but not cloud attacks explicitly. | No mechanisms for direct mitigation of attacks. |
| [69,70,71,72,73] | RBAC evolution and improvement over time. | Does not support encryption-integrated access control. |
| [74] | Introduced hierarchical cryptographic models for access control. | Initial model, lacks revocation and audit features. |
| [75,76,77,78] | Suggested economic schemes for outsourcing access control. | Limited to policy definition without cryptographic depth. |
| [79,80,81] | Proposed HIBE to control access using hierarchical identities. | Requires full hierarchical structure; rigid in dynamic settings. |
| [82] | Suggested private key generation scheme in HIBE; suffers single-point failure. | Fails under root key compromise; lacks resilience. |
| [83] | Shifted to Hierarchical Key Management (HKM). | Does not integrate cryptographic access validation. |
| [84] | Introduced Industrial Control System (ICS) vulnerability and cyber-physical attack assessments. | Lacks mitigation schemes if system is compromised. |
| [85] | Proposed probabilistic task reliability model under unauthorized access. | Ignores task dependency and synchronization challenges. |
| Parameters | Description |
|---|---|
| Distinct and independent large prime numbers | |
| Public Key Components | |
| Private Key Components | |
| Cipher Text values are derived after encryption and on which computation operation is performed. | |
| Cipher Text variable that stores the result of the computation. | |
| Euler totient | |
| ID value assigned to the user | |
| ID value assigned to the role | |
| Timestamp-based threshold value for the number computational resource request issued from a role | |
| Request ID for user | |
| Request ID for role | |
| Role user list | |
| Role Secret Value for the role | |
| Decryption key for user | |
| Encryption key for role | |
| Trusted Monitor Manager | |
| Role Monitor Module | |
| Cloud service provider | |
| Instruction to revoke a user with identity | |
| Random role secret value for role | |
| Random decryption key for user | |
| Role | |
| Hash function (generated to compute role secret value and decryption key) | |
| Access Control List (ACL) | |
| User— | |
| Attacker | |
| Set of fake role identities created by the attacker | |
| Set of role identities created by the challenger | |
| Set of revoked users maintained by the challenger |
| Threat Category (STRIDE) | Potential Attack Scenario | Mitigation Strategy Proposed in RACHEIM | Security Mechanism Employed |
|---|---|---|---|
| Spoofing | Impersonation of a legitimate user to gain unauthorized access. | User identity is validated against the ACL and role hierarchy before request processing. | Role–user mapping validation, ACL checks, and role secret verification. |
| Tampering | Malicious modification of data during processing or transit. | CSP performs computations only on encrypted data without access to plaintext. | Partial homomorphic encryption (PHE) for secure data processing. |
| Repudiation | Malicious user denies initiating or performing an action. | All user role transactions are logged and verified against time-stamped request tokens and identity credentials. | Immutable logging and authenticated role-token validation. |
| Information Disclosure | Exposure of sensitive data to unauthorized users or CSP. | Encrypted data and role-based decryption keys prevent CSP or unauthorized roles from accessing content. | Encryption with hidden content from CSP; role-bound decryption. |
| Denial-of-Service (DoS) | Overloading the system with invalid or excessive requests. | Requests are validated in two checkpoints: identity-role mapping and privilege validation before execution. | Request throttling and dual-stage access validation mechanism. |
| Escalation of Privileges | Unauthorized user tries to perform privileged operations. | Access is restricted based on hierarchical role parameters and identity checks; revoked roles cannot regain privileges. | Hierarchical role-based access control (RBAC) with dynamic revocation support. |
| Scheme | Homomorphic Type | Key Size (bits) | Ciphertext Size (KB) | Encryption Time (ms) | Decryption Time (ms) | Homomorphic Op. Time (ms) |
|---|---|---|---|---|---|---|
| RACHEIM (Proposed) | Partial (Division-based) | 2048 | 1.1 | 10.3 | 6.2 | 13.1 |
| Paillier (Additive HE) | Partial (Additive) | 2048 | 1.5 | 12.4 | 6.8 | 15.2 |
| RSA (Multiplicative HE) | Partial (Multiplicative) | 2048 | 1.8 | 14.7 | 8.3 | 17.5 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Saxena, U.R.; Kadel, R. RACHEIM: Reinforced Reliable Computing in Cloud by Ensuring Restricted Access Control. Network 2025, 5, 19. https://doi.org/10.3390/network5020019
Saxena UR, Kadel R. RACHEIM: Reinforced Reliable Computing in Cloud by Ensuring Restricted Access Control. Network. 2025; 5(2):19. https://doi.org/10.3390/network5020019
Chicago/Turabian StyleSaxena, Urvashi Rahul, and Rajan Kadel. 2025. "RACHEIM: Reinforced Reliable Computing in Cloud by Ensuring Restricted Access Control" Network 5, no. 2: 19. https://doi.org/10.3390/network5020019
APA StyleSaxena, U. R., & Kadel, R. (2025). RACHEIM: Reinforced Reliable Computing in Cloud by Ensuring Restricted Access Control. Network, 5(2), 19. https://doi.org/10.3390/network5020019







