A Practical Implementation of Post-Quantum Cryptography for Secure Wireless Communication †
Abstract
1. Introduction
2. Related Works
3. PQC-Based PKE Protocols for Using the PQC Algorithm in Applications
3.1. PQC Standalone PKE Protocol
| Algorithm 1 PQC standalone PKE protocol |
|
3.2. PQC–AES Hybrid PKE Protocol
| Algorithm 2 PQC–AES hybrid PKE protocol |
|
4. Practical Implementation of PQC-Based PKE Protocols
4.1. Post-Quantum Cryptography (PQC) Uses in Applications
4.1.1. Real-World Scenarios for Proposed PQC-Based Protocols
- Bob generates a pair of keys using a PQC algorithm: a public key () and a private key ().
- Bob shares his public key () with Alice while keeping the private key () secret.
- Alice prepares the data for transmission and splits it into multiple blocks if it exceeds the maximum byte size allowed by the PQC algorithm, as shown in Figure 1a.
- Alice encrypts each block sequentially using Bob’s public key (). The encrypted blocks are combined into a single encrypted file.
- Alice sends the encrypted file through a secure network.
- The access point routes the encrypted file to Bob without decrypting it.
- Bob receives the encrypted file and uses his private key () to decrypt each block.
- He reassembles the decrypted blocks to reconstruct the original document, as shown in Figure 1b.

5. Security Analysis of the Proposed Protocols
5.1. Security Analysis of the PQC Standalone PKE Protocol
5.1.1. Key Exchange (PQC KEM)
Security Assumption
Formal Statement
5.1.2. Key Confirmation
Mechanism
Security Assumption
- The collision resistance of SHA-256.
- The pseudorandomness and unforgeability properties of HMAC.
Formal Statement
5.1.3. Data Encryption and Decryption (PQC)
Security Assumption
Formal Statement
- The underlying KEM is IND-CCA2 secure.
- The public-key encryption scheme derived from it inherits this IND-CCA2 security property.
5.1.4. Replay Protection
Mechanism
- Sequence numbers are incorporated into each encrypted message.
- The receiver tracks these sequence numbers to ensure they are unique and monotonically increasing.
- Messages with duplicate or out-of-order sequence numbers are rejected.
Security Assumption
Formal Statement
5.1.5. Overall Security
Advantages
- Post-Quantum Security: Provides resistance against quantum adversaries due to reliance on PQC algorithms.
- Simplified Design: Avoids additional complexity introduced by hybrid schemes.
Limitations
- Single Point of Failure: The protocol’s security entirely depends on the strength of the PQC algorithms used (both KEM and public-key encryption). If these algorithms are compromised, both key exchange and data confidentiality are at risk.
- Performance Overhead: PQC standalone encryption/decryption operations are computationally intensive compared to symmetric cryptography like AES-256.
Formal Statement
5.2. Security Analysis of the PQC–AES Hybrid PKE Protocol
5.2.1. Security of the Key Exchange (PQC KEM)
5.2.2. Key Confirmation
5.2.3. Security of Data Encryption (AES-256)
Security Assumption
Formal Statement
5.2.4. Overall Security Argument
Formal Statement
5.3. Robustness Against Common Attack Vectors
5.3.1. Eavesdropping
PQC Standalone PKE
PQC–AES Hybrid PKE
5.3.2. Man-in-the-Middle (MITM) Attacks
5.3.3. Replay Attacks
PQC–AES Hybrid PKE (with AES-GCM)
PQC–AES Hybrid PKE (with AES-CBC or Other Modes)
5.3.4. Chosen-Ciphertext Attacks (CCAs)
5.3.5. Side-Channel Attacks
5.3.6. Known-Plaintext Attacks
6. Evaluation
6.1. Experimental Settings
6.2. Results and Discussion
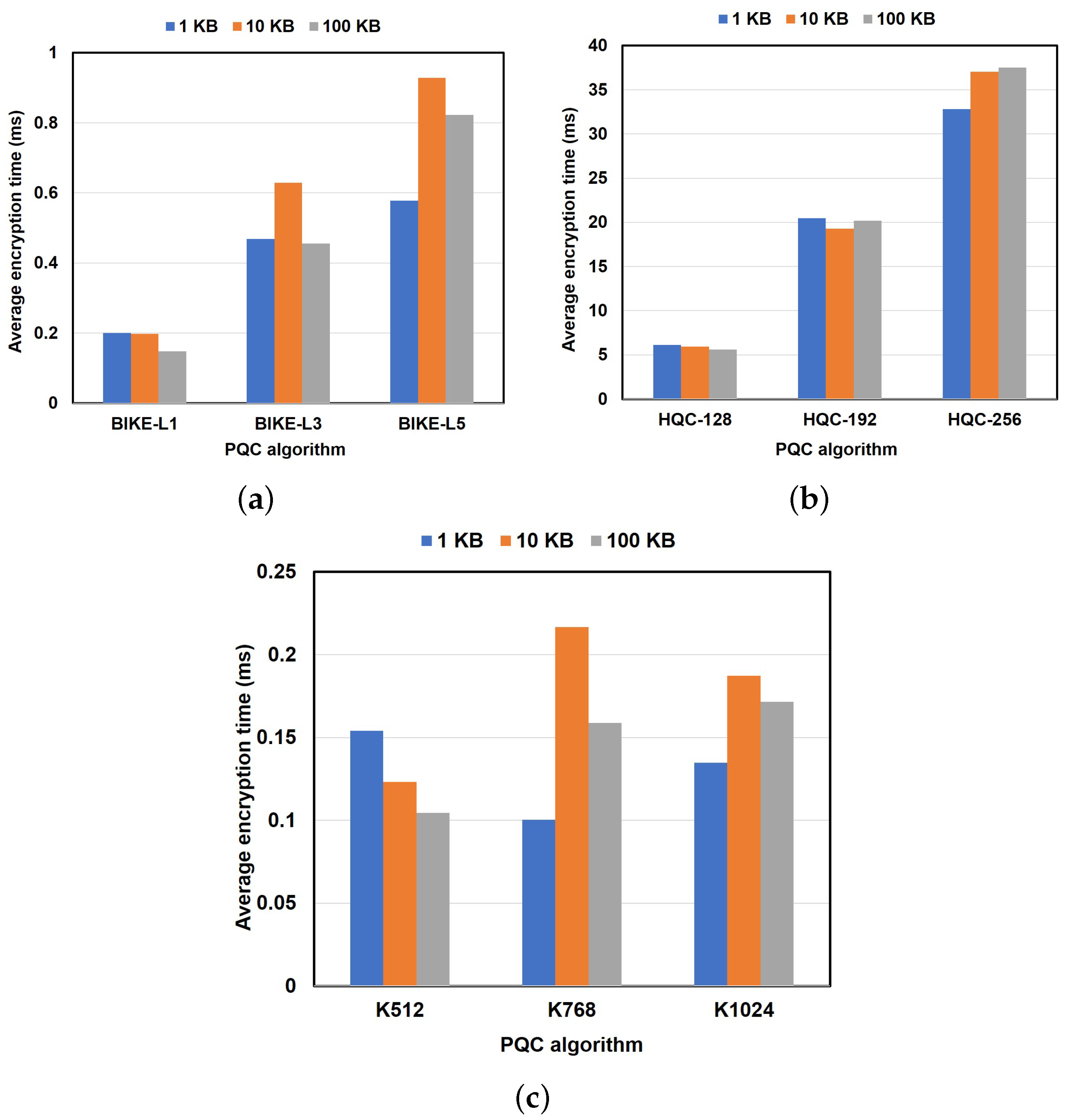
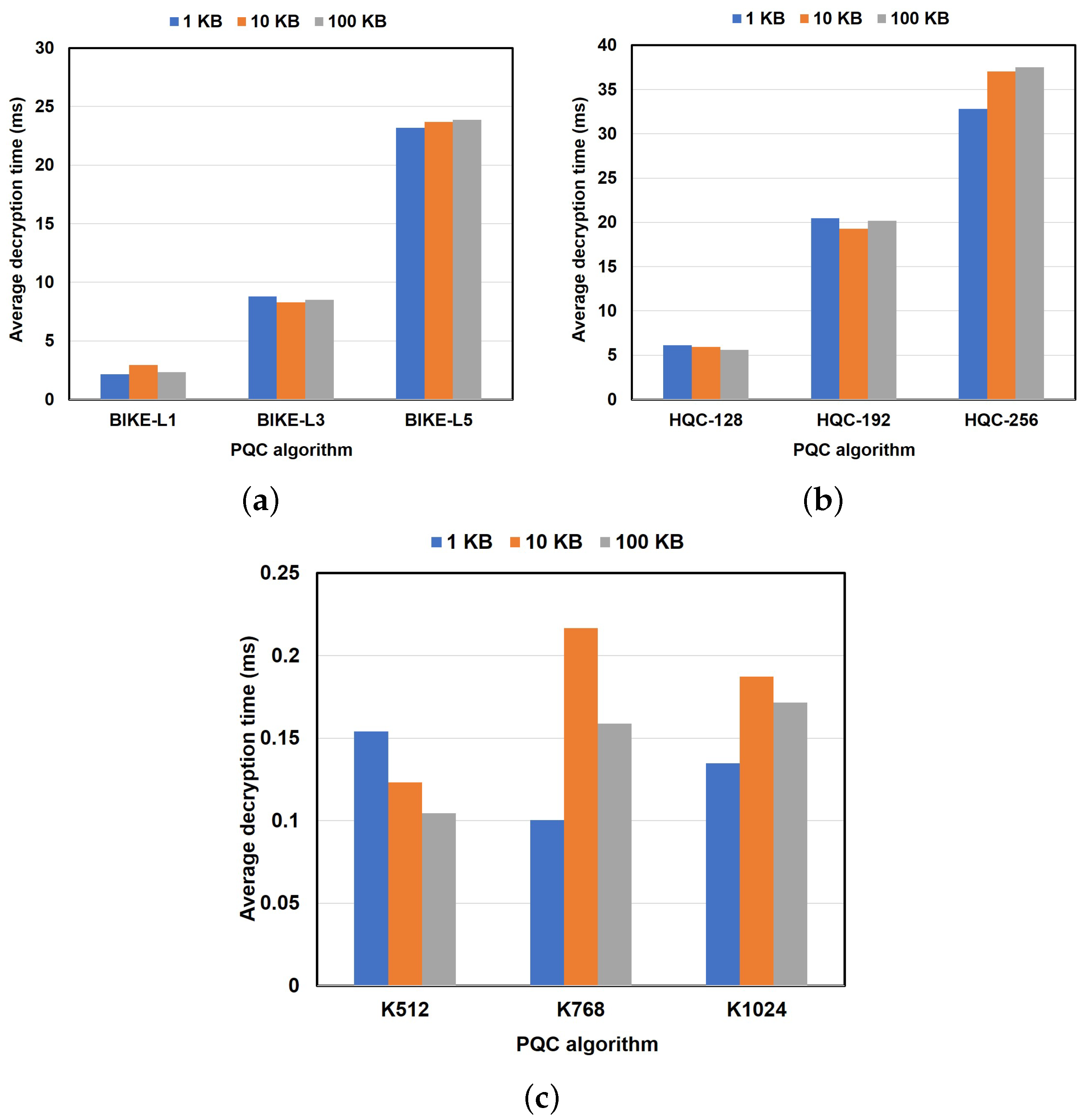
6.2.1. Performance Results of PQC Algorithm Key Generation
6.2.2. Performance Results of PQC Algorithm Encryption and Decryption
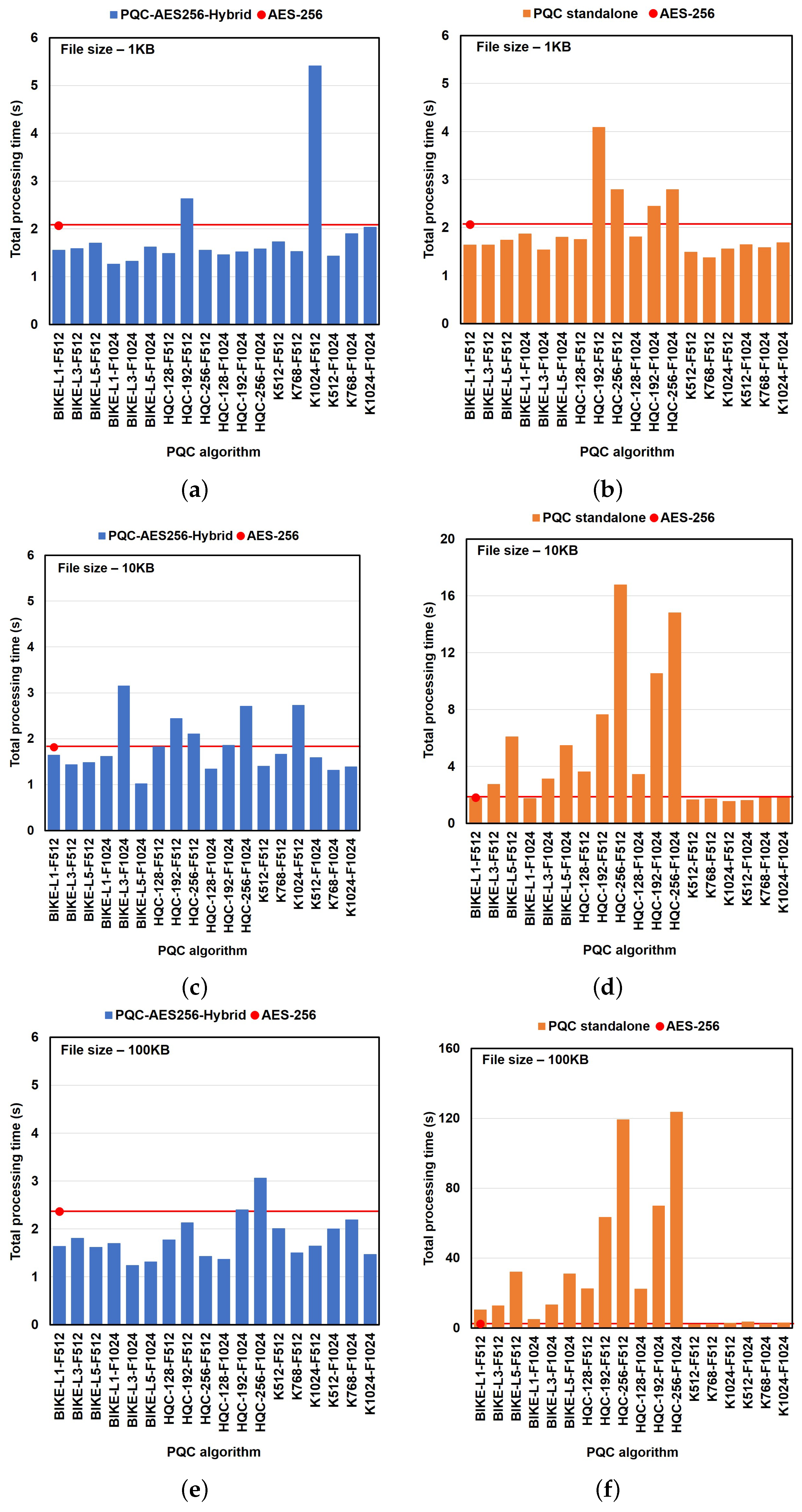
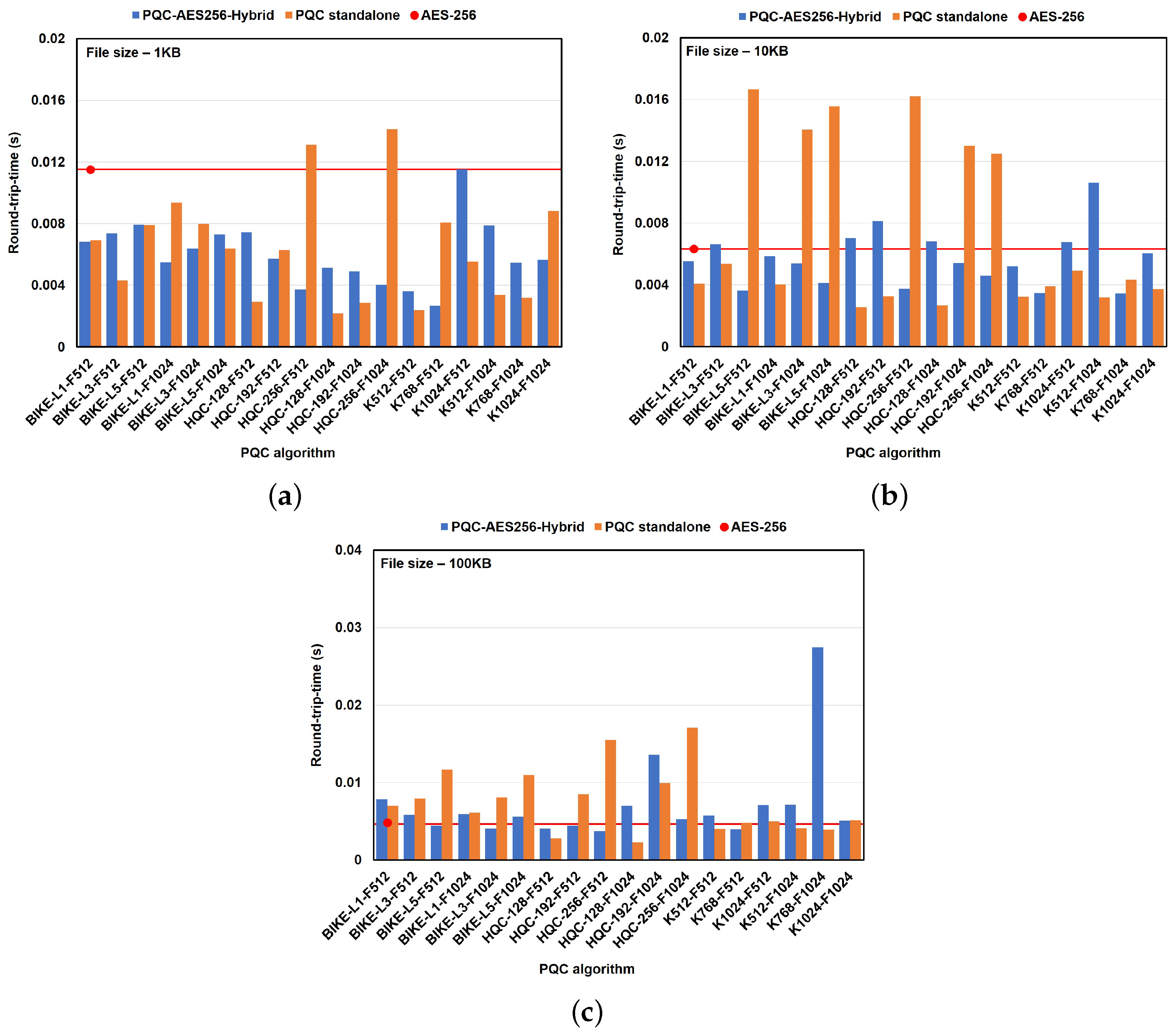
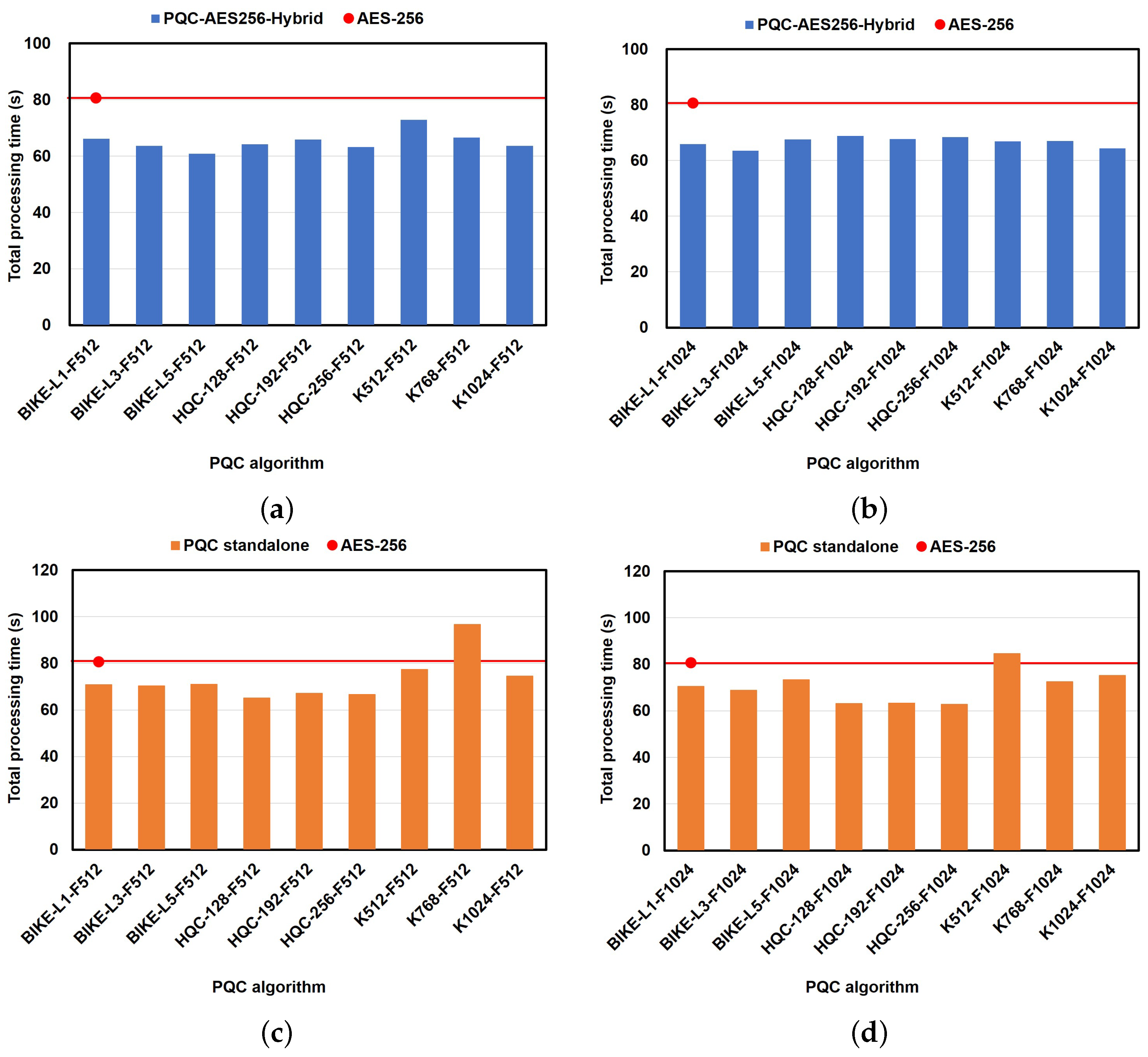
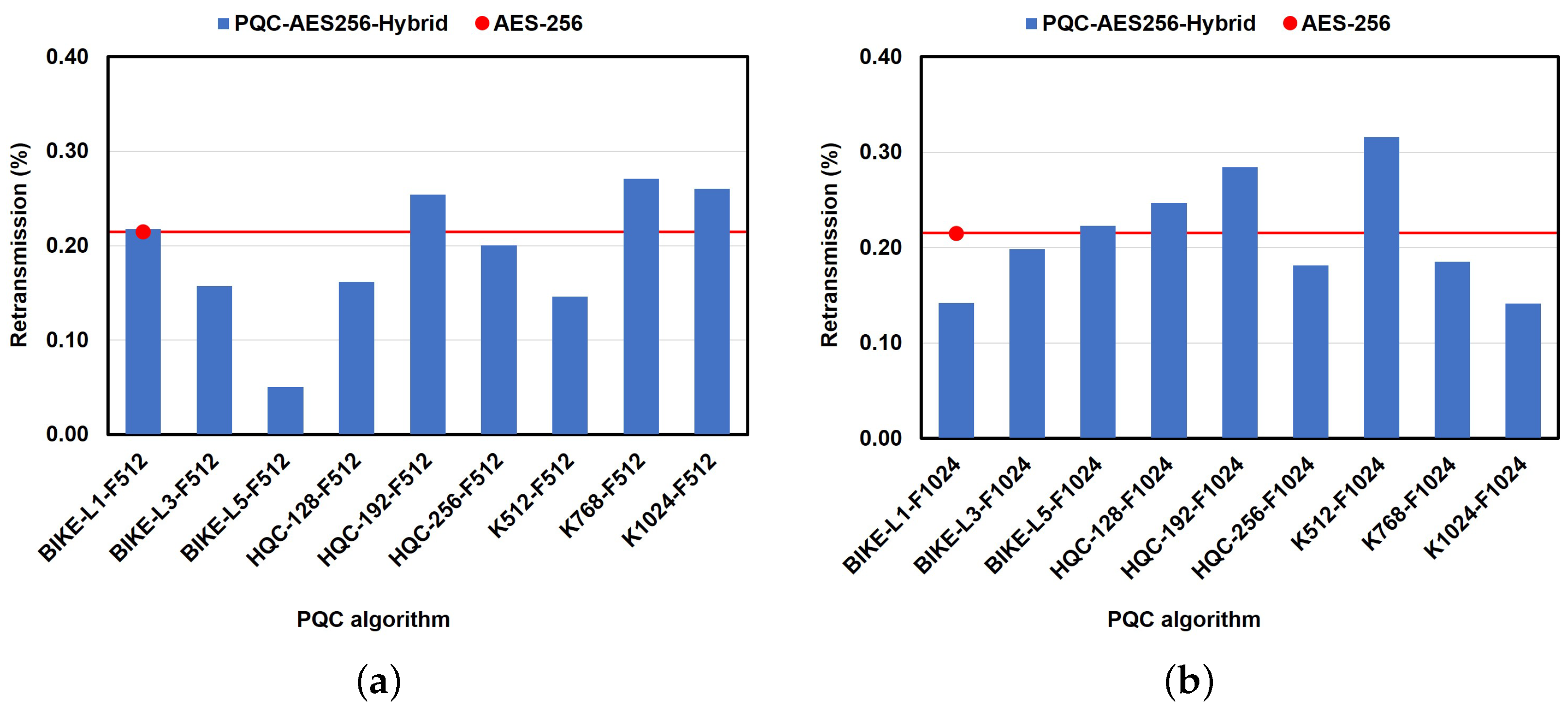
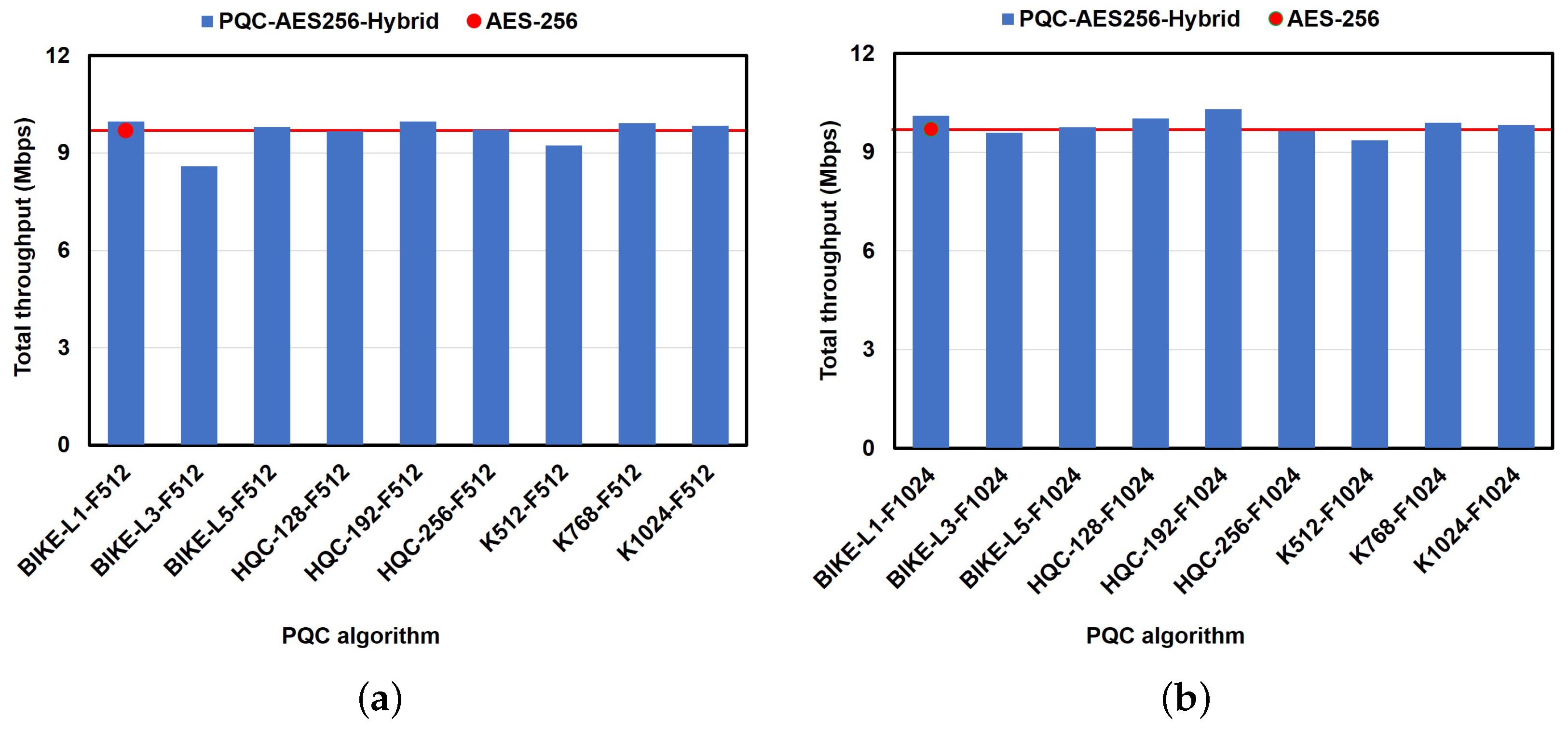
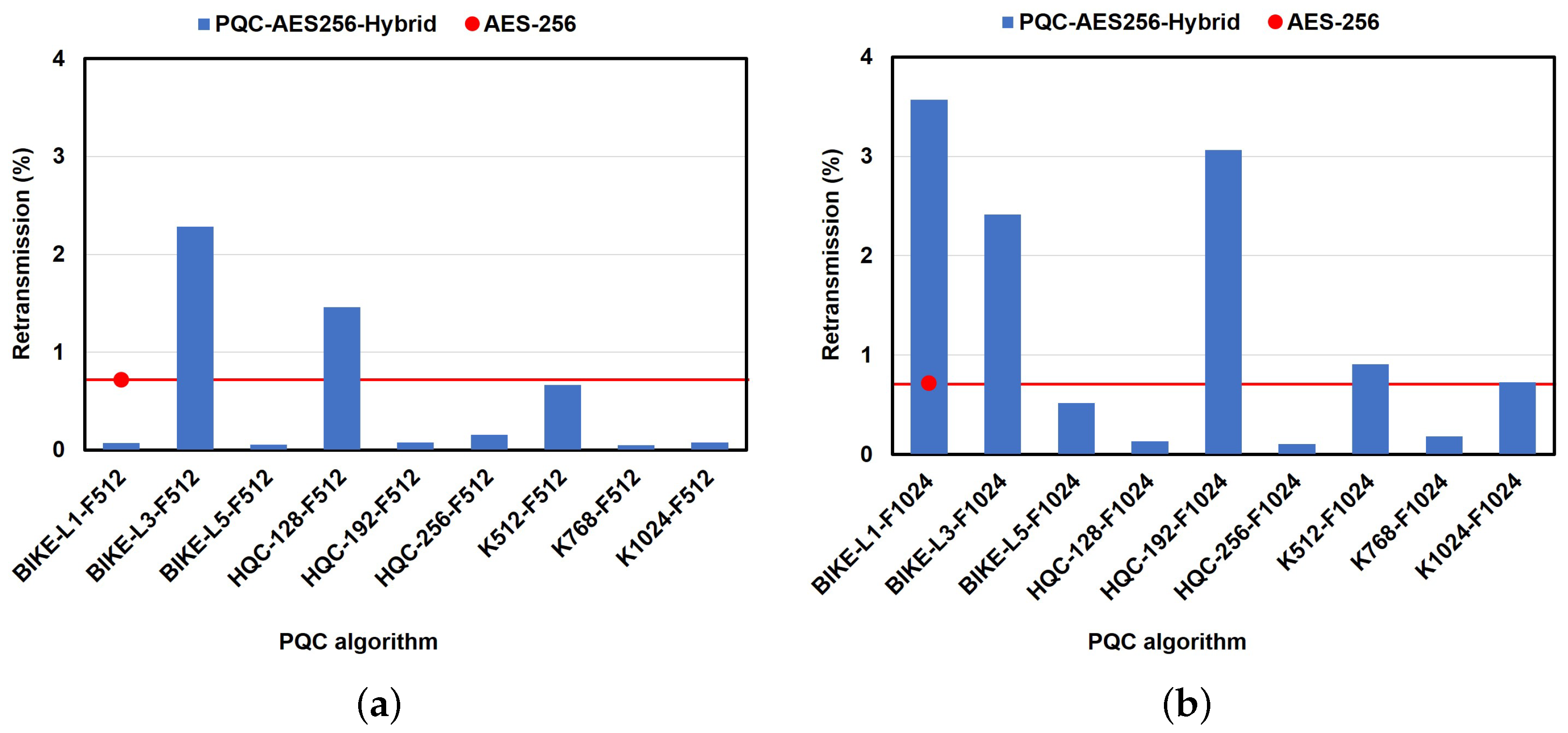
6.2.3. Impact of PQC Algorithms on Performance in the File Transfer Use Case
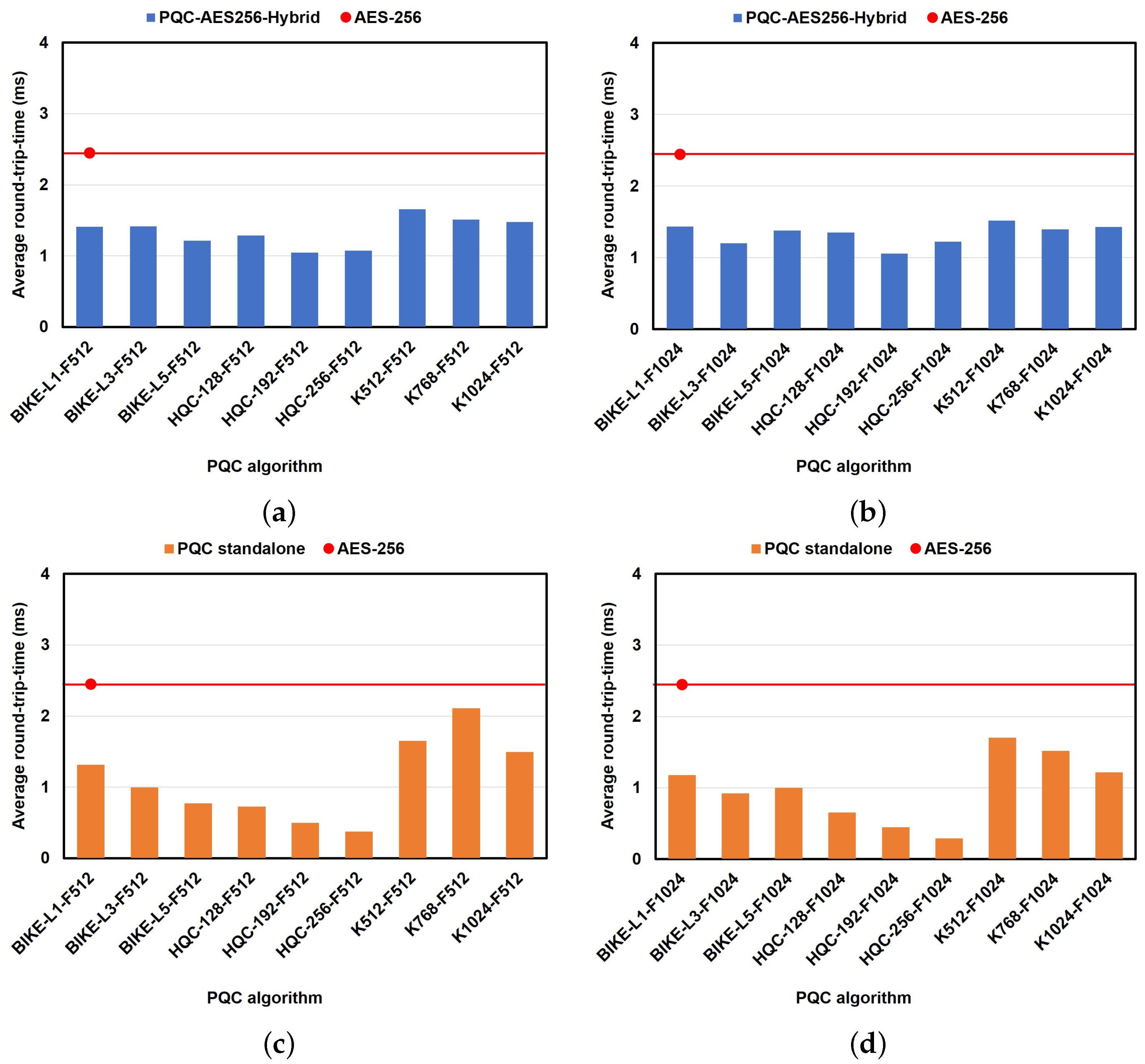
6.2.4. Impact of PQC Algorithms on Performance in the Chat-Based Use Case
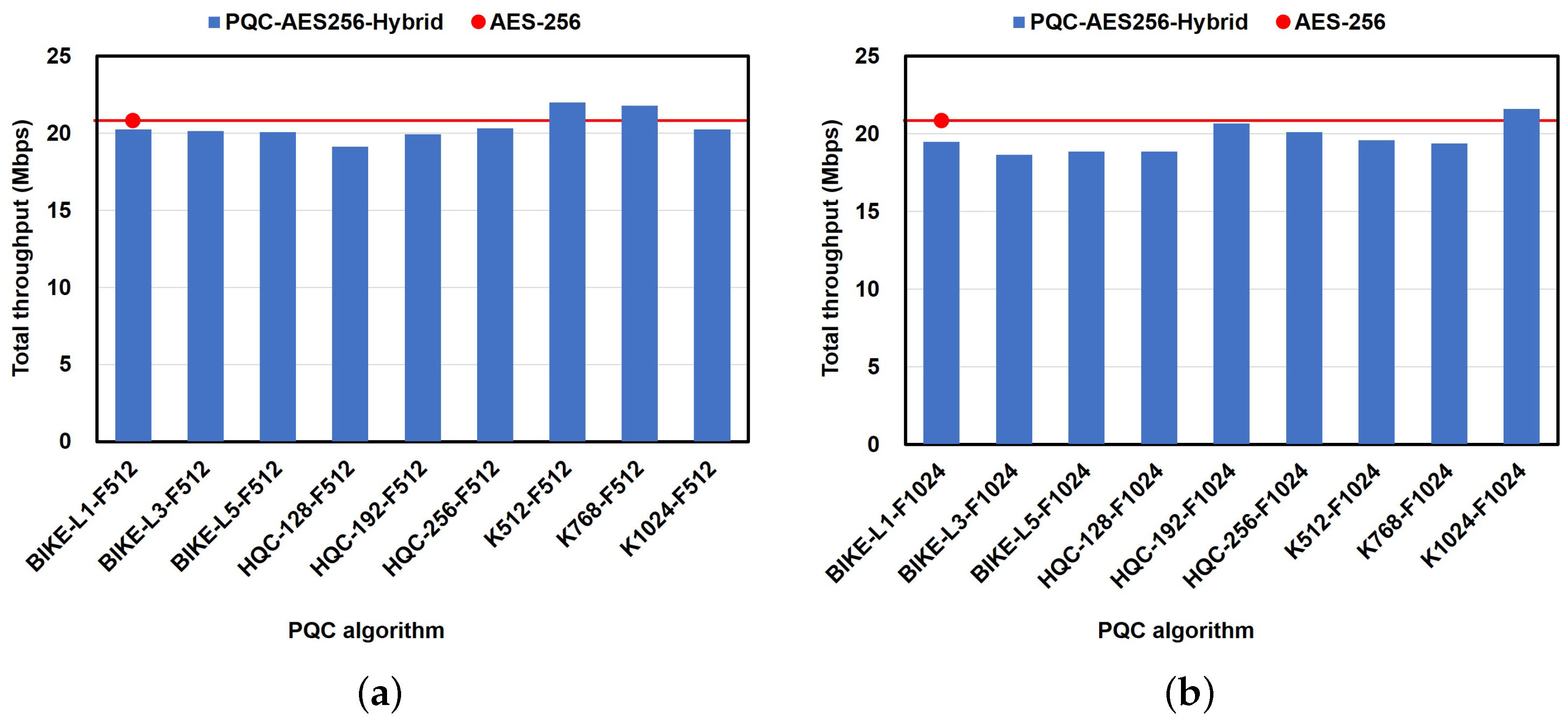
6.2.5. Impact of the PQC Algorithm on Performance in the Video-Streaming Use Case
6.2.6. Impact of the PQC Algorithm on Performance in the Live-Streaming Use Case
6.3. Limitations and Future Directions
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| PQC | Post-Quantum Cryptography |
| KEM | Key Encapsulation Mechanism |
| PKE | Public-Key Encryption |
| AES | Advanced Encryption Standard |
| NIST | National Institute of Standards and Technology |
| SSL | Secure Sockets Layer |
| TLS | Transport Layer Security |
| SSH | Secure Shell |
| MITM | Man-in-the-Middle |
| MAC | Message Authentication Code |
| KDF | Key Derivation Function |
| HKDF | Hash-Based Message Authentication Code Key Derivation Function |
| QC-MDPC | Quasi-Cyclic Moderate Density Parity Check |
| ACK | Acknowledgment |
References
- Equal1. Bell-1: The First Quantum System Purpose-Built for the HPC Era. Available online: https://www.equal1.com/post/equal1-launches-bell-1-the-first-quantum-system-purpose-built-for-the-hpc-era (accessed on 16 April 2025).
- Esmailiyan, A.; Wang, H.; Asker, M.; Koskin, E.; Leipol, D.; Bashir, I.; Xu, K.; Koziol, A.; Blokhina, E.; Staszewski, R.B. A Fully Integrated DAC for CMOS Position-Based Charge Qubits with Single-Electron Detector Loopback Testing. IEEE Solid-State Circuits Lett. 2020, 3, 354–357. [Google Scholar] [CrossRef]
- Staszewski, R.B.; Esmailiyan, A.; Wang, H.; Koskin, E.; Giounanlis, P.; Wu, X.; Koziol, A.; Sokolov, A.; Bashir, I.; Asker, M.; et al. Cryogenic Controller for Electrostatically Controlled Quantum Dots in 22-nm Quantum SoC. IEEE Open J. Solid-State Circuits Soc. 2022, 2, 103–121. [Google Scholar] [CrossRef]
- Barker, W.; Polk, W.; Souppaya, M. Getting Ready for Post-Quantum Cryptography: Exploring Challenges Associated with Adopting and Using Post-Quantum Cryptographic Algorithms; NIST Cybersecurity White Paper; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2021. [Google Scholar] [CrossRef]
- Chen, L.; Jordan, S.; Liu, Y.-K.; Moody, D.; Peralta, R.; Perlner, R.; Smith-Tone, D. Report on Post-Quantum Cryptography; NIST Internal Report 8105; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2016. [Google Scholar] [CrossRef]
- Alagic, G.; Apon, D.; Cooper, D.; Dang, Q.; Dang, T.; Kelsey, J.; Lichtinger, J.; Miller, C.; Moody, D.; Peralta, R.; et al. Status Report on the Third Round of the NIST Post-Quantum Cryptography Standardization Process; NIST Internal Report 8413-upd1; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2022. [Google Scholar] [CrossRef]
- Special Publication 800-227; Recommendations for Key-Encapsulation Mechanisms. NIST: Gaithersburg, MD, USA, 2024.
- FIPS 203; Module-Lattice-based Key-Encapsulation Mechanism. Federal Information Processing Standards Publication. NIST: Gaithersburg, MD, USA, 2024. [CrossRef]
- FIPS 204; Module-Lattice-Based Digital Signature Standard. Federal Information Processing Standards Publication. NIST: Gaithersburg, MD, USA, 2024. [CrossRef]
- FIPS 205; Stateless Hash-Based Digital Signature Standard. Federal Information Processing Standards Publication. NIST: Gaithersburg, MD, USA, 2024. [CrossRef]
- Alagic, G.; Bros, M.; Ciadoux, P.; Cooper, D.; Dang, Q.; Dang, T.; Kelsey, J.; Lichtinger, J.; Liu, Y.; Miller, C.; et al. Status Report on the Fourth Round of the NIST Post-Quantum Cryptography Standardization Process; NIST Internal Report (NIST IR 8545); National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2025. [Google Scholar] [CrossRef]
- Ojetunde, B.; Kurihara, T.; Yano, K.; Sakano, T.; Yokoyama, H. Performance Evaluation of Post-Quantum Cryptography Algorithms for Secure Communication in Wireless Networks. In Proceedings of the IEEE Consumer Communications & Networking Conference (CCNC2025), Las Vegas, NV, USA, 10–13 January 2025. [Google Scholar]
- Cooper, D.A.; Apon, D.C.; Dang, Q.H.; Davidson, M.S.; Dworkin, M.J.; Miller, C.A. Recommendation for Stateful Hash-Based Signature Schemes; NIST Special Publication 800-208; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2020. [Google Scholar] [CrossRef]
- Ghosh, S.; Upadhyay, S.; Saki, A.A. A Primer on Security of Quantum Computing. arXiv 2023, arXiv:2305.02505v1. [Google Scholar]
- Perepechaenko, M.; Kuang, R. Quantum Encryption and Decryption in IBMQ Systems using Quantum Permutation Pad. J. Commun. 2022, 17, 972–978. [Google Scholar] [CrossRef]
- Schwabe, P.; Stebila, D.; Wiggers, T. Post-Quantum TLS Without Handshake Signatures. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, Virtual Event, 9–13 November 2020; Association for Computing Machinery: New York, NY, USA; pp. 1461–1480. [Google Scholar] [CrossRef]
- Schwabe, P.; Stebila, D.; Wiggers, T. More Efficient Post-quantum KEMTLS with Pre-distributed Public Keys. In Computer Security—ESORICS 2021; Bertino, E., Shulman, H., Waidner, M., Eds.; Lecture Notes in Computer Science 12972; Springer: Cham, Switzerland, 2021. [Google Scholar] [CrossRef]
- Gunther, F.; Rastikian, S.; Towa, P.; Wiggers, T. KEMTLS with Delayed Forward Identity Protection in (Almost) a Single Round Trip. In Applied Cryptography and Network Security, ACNS 2022; Ateniese, G., Venturi, D., Eds.; Lecture Notes in Computer Science 13269; Springer: Cham, Switzerland, 2022. [Google Scholar] [CrossRef]
- Singh, R.P.; Sarma, B.K.; Saikia, A. Public Key Cryptography Using Permutation P-Polynomials over Finite Fields. Cryptology ePrint Archive, Paper 2009/208. 2009. Available online: https://eprint.iacr.org/2009/208.pdf (accessed on 4 April 2025).
- Marco, L.; Talayhan, A.; Vaudenay, S. Making Classical (Threshold) Signatures Post-Quantum for Single Use on a Public Ledger. Cryptology ePrint Archive, Paper 2023/420. 2023. Available online: https://eprint.iacr.org/2023/420 (accessed on 4 April 2025).
- da Silva Lima, P.; Ribeiro, L.A.; Queiroz, R.J.; Quintino, J.P.; Silva, F.Q.; Santos, A.L.; Roberto, J. Evaluating Kyber Post-Quantum KEM in a Mobile Application. 2021. Available online: https://csrc.nist.gov/CSRC/media/Events/third-pqc-standardization-conference/documents/accepted-papers/ribeiro-evaluating-kyber-pqc2021.pdf (accessed on 30 May 2025).
- Giron, A.A. Migrating Applications to Post-Quantum Cryptography: Beyond Algorithm Replacement. Cryptology ePrint Archive, Paper 2023/709. 2023. Available online: https://eprint.iacr.org/2023/709 (accessed on 4 April 2025).
- Liu, T.; Ramachandran, G.; Jurdak, R. Post-Quantum Cryptography for Internet of Things: A Survey on Performance and Optimization. arXiv 2024, arXiv:2401.17538. [Google Scholar]
- Asif, R. Post-Quantum Cryptosystems for Internet-of-Things: A Survey on Lattice-Based Algorithms. IoT 2021, 2, 71–91. [Google Scholar] [CrossRef]
- Li, S.; Yuxiang, C.; Lin, C.; Jing, L.; Chanchan, K.; Kuanching, L.; Wei, L.; Naixue, X. Post-Quantum Security: Opportunities and Challenges. Sensors 2023, 23, 8744. [Google Scholar] [CrossRef] [PubMed]
- Balamurugan, C.; Singh, K.; Ganesan, G.; Rajarajan, M. Post-Quantum and Code-Based Cryptography—Some Prospective Research Directions. Cryptography 2021, 5, 38. [Google Scholar] [CrossRef]
- Fakhruldeen, H.F.; Al-Kaabi, R.A.; Jabbar, F.I.; Al-Kharsan, I.H.; Shoja, S.J. Post-quantum Techniques in Wireless Network Security: An Overview. Malays. J. Fundam. Appl. Sci. 2023, 19, 337–344. [Google Scholar] [CrossRef]
- Lawo, D.C.; Abu Bakar, R.; Cano Aguilera, A.; Cugini, F.; Imaña, J.L.; Tafur Monroy, I.; Vegas Olmos, J.J. Wireless and Fiber-Based Post Quantum-Cryptography-Secured IPsec Tunnel. Future Internet 2024, 16, 300. [Google Scholar] [CrossRef]
- Liboqs. Available online: https://openquantumsafe.org/liboqs/ (accessed on 4 April 2025).
- Sharpe, R.; Warnicke, E.; Lamping, U. Wireshark User’s Guide. Version 4.5.0. Available online: https://www.wireshark.org/docs/wsug_html_chunked/ (accessed on 30 May 2025).



| Parameter | Value | |
|---|---|---|
| Server | Client | |
| PC | Mouse Laptop | Mouse Laptop |
| OS | Ubuntu 20.04 desktop | Ubuntu 20.04 desktop |
| Network/Protocol | IEEE 802.11n | IEEE 802.11n |
| Frequency band | 2.4 GHz | 2.4 GHz |
| Maximum data rate | 144 Mbps | 144 Mbps |
| Sniffer | Wireshark | Wireshark |
| PQC KEM Algorithm | Client | Server | ||||
|---|---|---|---|---|---|---|
| Avg. Key Gen. (ms) | Avg. Encap. (ms) | Avg. Decap. (ms) | Avg. Key Gen. (ms) | Avg. Encap. (ms) | Avg. Decap. (ms) | |
| BIKE-L1 | 0.43 | 0.12 | 1.64 | 1.23 | 0.12 | 1.52 |
| BIKE-L3 | 0.80 | 0.21 | 5.68 | 2.63 | 0.19 | 5.79 |
| BIKE-L5 | 1.95 | 0.36 | 14.42 | 5.05 | 0.33 | 15.94 |
| HQC-128 | 3.45 | 5.76 | 10.23 | 5.60 | 4.03 | 8.44 |
| HQC-192 | 4.88 | 12.83 | 28.11 | 9.70 | 11.99 | 32.20 |
| HQC-256 | 8.73 | 17.96 | 49.77 | 14.32 | 1.81 | 53.40 |
| K512 | 0.92 | 0.10 | 0.17 | 1.83 | 0.10 | 0.11 |
| K768 | 0.19 | 0.09 | 0.16 | 0.37 | 0.10 | 0.10 |
| K1024 | 1.00 | 0.14 | 0.18 | 0.49 | 0.09 | 0.11 |
| PQC Signature | Client | Server | ||||
|---|---|---|---|---|---|---|
| Avg. Sig. Key Gen. (ms) | Avg. Signing (ms) | Avg. Ver. (ms) | Avg. Sig. Key Gen. (ms) | Avg. Signing (ms) | Avg. Ver. (ms) | |
| F512 | 7.01 | 0.33 | 0.28 | 9.68 | 0.37 | 0.82 |
| F1024 | 19.00 | 1.43 | 0.31 | 24.51 | 0.67 | 0.79 |
| User 1 | User 2 | ||
|---|---|---|---|
| Text Message | Size (Bytes) | Text Message | Size (Bytes) |
| Hello | 5 | Hi, how are you? | 16 |
| I’m good, thanks. And you? | 26 | You are welcome. I’m fine too. | 30 |
| Are you ready for the demo? | 27 | Yes, all set. Let’s get started! | 32 |
| Great! Here’s the first part of the code. What do you think? | 60 | Looks interesting. I have a few questions about the results. | 60 |
| Sure, I can explain anything about it. | 38 | Thanks! I want to know how you handled the data preprocessing step. | 67 |
| I used the standard normalization method and added custom | 57 | That makes sense. Let’s move on to the next section. | 52 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ojetunde, B.; Kurihara, T.; Yano, K.; Sakano, T.; Yokoyama, H. A Practical Implementation of Post-Quantum Cryptography for Secure Wireless Communication. Network 2025, 5, 20. https://doi.org/10.3390/network5020020
Ojetunde B, Kurihara T, Yano K, Sakano T, Yokoyama H. A Practical Implementation of Post-Quantum Cryptography for Secure Wireless Communication. Network. 2025; 5(2):20. https://doi.org/10.3390/network5020020
Chicago/Turabian StyleOjetunde, Babatunde, Takuya Kurihara, Kazuto Yano, Toshikazu Sakano, and Hiroyuki Yokoyama. 2025. "A Practical Implementation of Post-Quantum Cryptography for Secure Wireless Communication" Network 5, no. 2: 20. https://doi.org/10.3390/network5020020
APA StyleOjetunde, B., Kurihara, T., Yano, K., Sakano, T., & Yokoyama, H. (2025). A Practical Implementation of Post-Quantum Cryptography for Secure Wireless Communication. Network, 5(2), 20. https://doi.org/10.3390/network5020020






