SDN-Based Resilient Smart Grid: The SDN-microSENSE Architecture
Abstract
:1. Introduction
2. Related Work
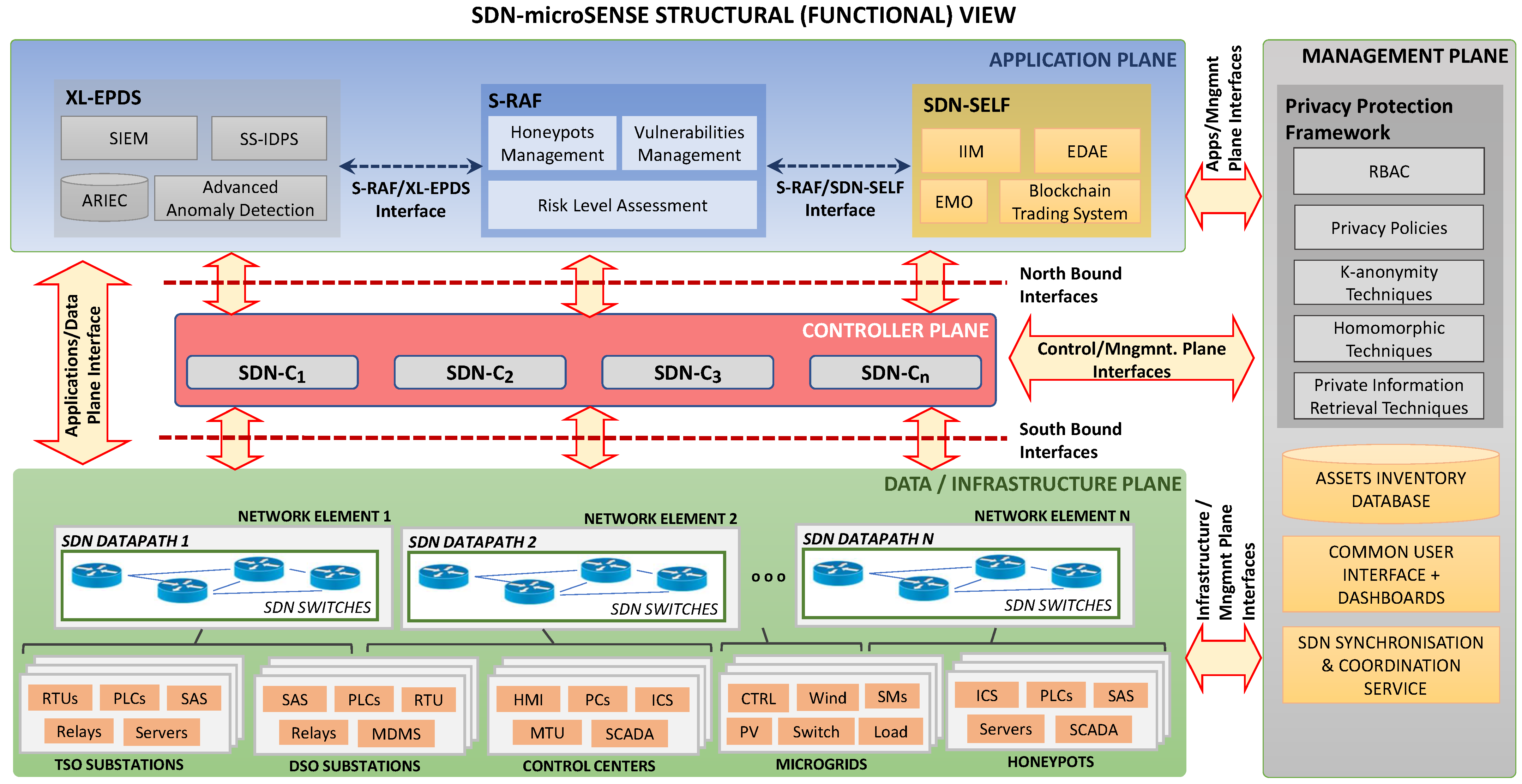
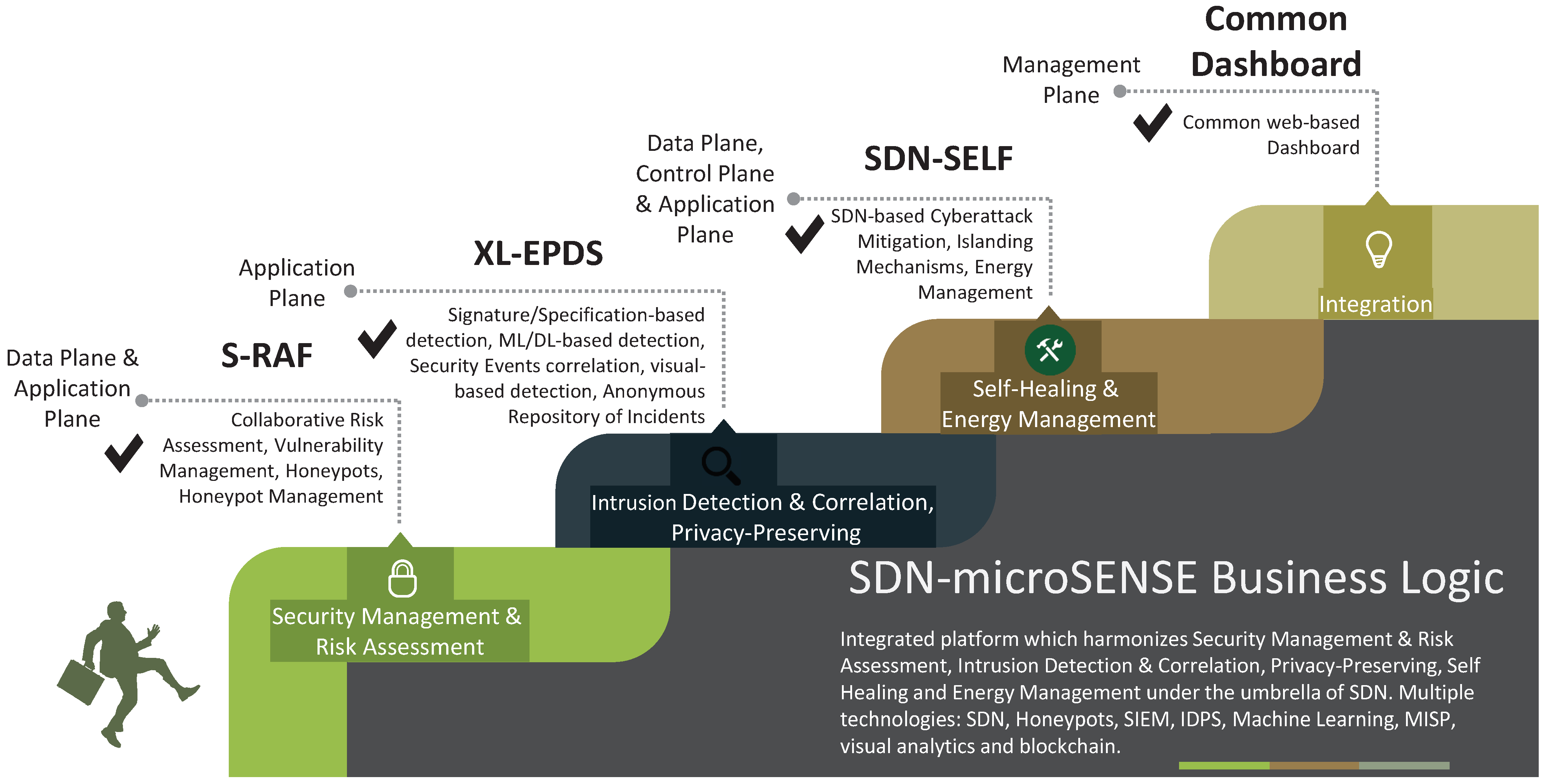
3. SDN-microSENSE Architecture
3.1. S-RAF: SDN-microSENSE Risk Assessment Framework
3.1.1. Security Management and Risk Assessment
3.1.2. EPES/SG Honeypots and Honeypot Manager
3.2. XL-EPDS: Cross Layer Energy Prevention and Detection System
3.2.1. XL-SIEM and Detectors
3.2.2. ARIEC: Cloud-Based Anonymous Repository of Incidents
3.3. SDN-SELF: SDN-enabled Self-hEaLing Framework
3.3.1. EDAE: Electric Data Analysis Engine
- Scenario A: QoS constraints are not satisfied. Supposing the communication quality is degraded in a manner that criteria of minimum latency cannot be satisfied. In that case, EDAE employs the PaDe [45] genetic algorithm in order to decompose the multi-objective problem of path reconstruction to multiple single-objective ones that are resolved using the asynchronous generalised island model to distribute the solution process [46]. The final solution (i.e., the optimal path that maximises the grid QoS and observability) is obtained as the set of the best individual solution in each single-objective island.
- Scenario B: An EPES/SG device is disconnected from the network. In a more specific scenario that a Phase Data Concentrator (PDC) is disconnected from the network, the Phasor Measurement Units (PMUs) connected to that PDC should be reallocated to the next available PDC so that the security and QoS constraints are not validated for any of the existing PMUs. In this case, a Mixed-Integer Linear Programming algorithm chooses and applies the best PMU reallocation scheme to minimise the overall network latency. This problem is also studied by [40]; however, authors are limited to maximising observability, while EDAE also addresses QoS and security requirements.
- Scenario C: Change of security risk. Supposing that the security risk of an intermediate switch changes dramatically, EDAE finds alternative paths so that the risk level of the rest infrastructure will be maintained while the QoS requirements of the rest applications are intact.
3.3.2. IIM: Islanding and optImisation fraMework
3.3.3. EMO: rEstoration Machine-learning framewOrk
- Regulating the local variables of Distributed Energy Resources (DERs) (i.e., voltage and frequency), to achieve high power quality that leads to less losses and results in more robust islands in terms of load-balancing capabilities.
- Maintaining the stability of the electrical grid and balancing the available energy of the islands.
- Managing load shedding, including decisions on when, where, and how much load should be shed according to the priorities at each island, in order to mitigate the impact to the end-users.
- Computing the energy exchange feasibility within the islands, after receiving the trading requests from the Blockchain-based Energy Trading System.
3.3.4. Blockchain-Based Energy Trading System
3.4. SDN Controller
4. SDN-microSENSE Use Cases and Implementation Considerations
- Use Case 1 - Investigation of Versatile Cyberattack Scenarios and Methodologies Against EPES: This use case deals with a variety of cybersecurity threats against substations, including station and process buses.
- Use Case 2 - Massive False Data Injection Cyberattack Against State Operation and Automatic Generation Control: This use case focuses on false-data injection attacks against the whole energy value chain, including generation (power plants), TSO and DSO substation architectures as well as smart metering infrastructures.
- Use Case 3 - Large-scale Islanding Scenario Using Real-life Infrastructure: The third use case treats the aftermath of a cyberattack or critical failure that results in an unbalanced grid. The SDN-microSENSE platform acts as a decision support system for the TSO in order to decide on intentionally islanding segments of the affected grid or to shed redundant load in order to balance energy demand and supply [49].
- Use Case 4 - EPES Cyber-defence against Coordinated Attacks: This use case aims to evaluate the SDN-microSENSE platform against the detection and mitigation of coordinated cyberattacks, taking place in substations.
- Use Case 5 - Distribution Grid Restoration in Real-world PV Microgrids: This use case deals with the detection and mitigation of cyberthreats occurring in the industrial network of a real photovoltaic station.
- Use Case 6 - Realising Private and Efficient Energy Trading among PV Prosumers: This use case realises the decentralized energy trading environment that SDN-microSENSE proposes, by involving PV prosumers.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| ABOD | Angle-Based Outlier Detection |
| ADT | Attack Defence Tree |
| APT | Advanced Persistent Threat |
| BIAD | Blockchain-based Intrusion and Anomaly Detection |
| CVE | Common Vulnerabilities and Exposures |
| CVSS | Common Vulnerability Scoring System |
| DAS | Distribution Automation System |
| DDoS | Distributed Denial-of-Service |
| DERs | Distributed Energy Resources |
| DNP3 | Distributed Network Protocol 3 |
| DSO | Distribution System Operator |
| EDAE | Electric Data Analysis Engine |
| EMO | rEstoration Machine-learning framewOrk |
| EPES | Electrical Power and Energy Systems |
| GOOSE | Generic Object Oriented Substation Event |
| HM | Honeypot Manager |
| ICD | Intelligent Capability Description |
| ICS | Industrial Control System |
| IDPS | Intrusion Detection and Prevention System |
| IDS | Intrusion Detection System |
| IIM | Islanding and optImisation fraMework |
| IIoT | Industrial Internet of Things |
| IoT | Internet of Things |
| IP | Internet Protocol |
| IT | Information Technology |
| LOF | Local Outlier Factor |
| MAC | Medium Access Control |
| MISP | Malware Information Sharing Platform |
| ML | Machine Learning |
| MQTT | Message Queuing Telemetry Transport |
| NIS | Network and Information System |
| NLP | Natural Language Processing |
| NTP | Network Time Protocol |
| ONF | Open Networking Foundation |
| OPF | Overlay Privacy Framework |
| OVS | Open vSwitch |
| PCA | Principal Component Analysis |
| PDC | Phase Data Concentrator |
| PMU | Phasor Measurement Unit |
| QoS | Quality of Service |
| RFC | Request for Comments |
| SCADA | Supervisory Control and Data Acquisition |
| SCS | Synchronisation and Coordination Service |
| SDN | Software-Defined Networking |
| SDN-C | SDN Controller |
| SDN-SELF | SDN-enabled Self-healing Framework |
| SG | Smart Grid |
| SIEM | Security Information and Event Management |
| SOS | Stochastic Outlier Selection |
| S-RAF | SDN-microSENSE Risk Assessment Framework |
| SVM | Support Vector Machine |
| TCP | Transmission Control Protocol |
| TSO | Transmission System Operator |
| VCG | Vickrey-Clarke-Groves |
| XL-EPDS | Cross-Layer Energy Prevention and Detection System |
References
- Tan, S.; De, D.; Song, W.Z.; Yang, J.; Das, S.K. Survey of security advances in smart grid: A data driven approach. IEEE Commun. Surv. Tutor. 2016, 19, 397–422. [Google Scholar] [CrossRef]
- Alshamrani, A.; Myneni, S.; Chowdhary, A.; Huang, D. A survey on advanced persistent threats: Techniques, solutions, challenges, and research opportunities. IEEE Commun. Surv. Tutor. 2019, 21, 1851–1877. [Google Scholar] [CrossRef]
- Stellios, I.; Kotzanikolaou, P.; Psarakis, M. Advanced persistent threats and zero-day exploits in industrial Internet of Things. In Security and Privacy Trends in the Industrial Internet of Things; Springer: Berlin/Heidelberg, Germany, 2019; pp. 47–68. [Google Scholar]
- Di Pinto, A.; Dragoni, Y.; Carcano, A. TRITON: The First ICS Cyber Attack on Safety Instrument Systems. In Proceedings of the Black Hat USA, Mandalay, LV, USA, 4–9 August 2018; Volume 2018, pp. 1–26. [Google Scholar]
- Radoglou-Grammatikis, P.; Siniosoglou, I.; Liatifis, T.; Kourouniadis, A.; Rompolos, K.; Sarigiannidis, P. Implementation and Detection of Modbus Cyberattacks. In Proceedings of the 2020 9th International Conference on Modern Circuits and Systems Technologies (MOCAST), Bremen, Germany, 7–9 September 2020; pp. 1–4. [Google Scholar]
- Darwish, I.; Igbe, O.; Saadawi, T. Vulnerability Assessment and Experimentation of Smart Grid DNP3. J. Cyber Secur. Mobil. 2016, 5, 23–54. [Google Scholar] [CrossRef]
- Radoglou-Grammatikis, P.; Sarigiannidis, P.; Giannoulakis, I.; Kafetzakis, E.; Panaousis, E. Attacking IEC-60870-5-104 SCADA Systems. In Proceedings of the 2019 IEEE World Congress on Services (SERVICES), Milan, Italy, 8–13 July 2019; Volume 2642, pp. 41–46. [Google Scholar]
- Radoglou-Grammatikis, P.I.; Sarigiannidis, P.G.; Moscholios, I.D. Securing the Internet of Things: Challenges, threats and solutions. Internet Things 2019, 5, 41–70. [Google Scholar] [CrossRef]
- Kumar, P.; Lin, Y.; Bai, G.; Paverd, A.; Dong, J.S.; Martin, A. Smart grid metering networks: A survey on security, privacy and open research issues. IEEE Commun. Surv. Tutor. 2019, 21, 2886–2927. [Google Scholar] [CrossRef] [Green Version]
- Stellios, I.; Kotzanikolaou, P.; Psarakis, M.; Alcaraz, C.; Lopez, J. A survey of iot-enabled cyberattacks: Assessing attack paths to critical infrastructures and services. IEEE Commun. Surv. Tutor. 2018, 20, 3453–3495. [Google Scholar] [CrossRef]
- Hassan, M.U.; Rehmani, M.H.; Chen, J. Differential privacy techniques for cyber physical systems: A survey. IEEE Commun. Surv. Tutor. 2019, 22, 746–789. [Google Scholar] [CrossRef] [Green Version]
- Karimipour, H.; Dehghantanha, A.; Parizi, R.M.; Choo, K.K.R.; Leung, H. A deep and scalable unsupervised machine learning system for cyber-attack detection in large-scale smart grids. IEEE Access 2019, 7, 80778–80788. [Google Scholar] [CrossRef]
- Nguyen, T.; Wang, S.; Alhazmi, M.; Nazemi, M.; Estebsari, A.; Dehghanian, P. Electric Power Grid Resilience to Cyber Adversaries: State of the Art. IEEE Access 2020, 8, 87592–87608. [Google Scholar] [CrossRef]
- Radoglou-Grammatikis, P.I.; Sarigiannidis, P.G. Securing the smart grid: A comprehensive compilation of intrusion detection and prevention systems. IEEE Access 2019, 7, 46595–46620. [Google Scholar] [CrossRef]
- Rehmani, M.H.; Davy, A.; Jennings, B.; Assi, C. Software defined networks-based smart grid communication: A comprehensive survey. IEEE Commun. Surv. Tutor. 2019, 21, 2637–2670. [Google Scholar] [CrossRef]
- Musleh, A.S.; Chen, G.; Dong, Z.Y. A survey on the detection algorithms for false data injection attacks in smart grids. IEEE Trans. Smart Grid 2019, 11, 2218–2234. [Google Scholar] [CrossRef]
- Radoglou-Grammatikis, P.; Sarigiannidis, P.; Liatifis, T.; Apostolakos, T.; Oikonomou, S. An overview of the firewall systems in the smart grid paradigm. In Proceedings of the 2018 Global information infrastructure and networking symposium (GIIS), Thessaloniki, Greece, 23–25 October 2018; pp. 1–4. [Google Scholar]
- Li, E.; Kang, C.; Huang, D.; Hu, M.; Chang, F.; He, L.; Li, X. Quantitative Model of Attacks on Distribution Automation Systems Based on CVSS and Attack Trees. Information 2019, 10, 251. [Google Scholar] [CrossRef] [Green Version]
- Johnson, P.; Lagerström, R.; Ekstedt, M.; Franke, U. Can the common vulnerability scoring system be trusted? a bayesian analysis. IEEE Trans. Dependable Secur. Comput. 2016, 15, 1002–1015. [Google Scholar] [CrossRef]
- Rios, E.; Rego, A.; Iturbe, E.; Higuero, M.; Larrucea, X. Continuous Quantitative Risk Management in Smart Grids Using Attack Defense Trees. Sensors 2020, 20, 4404. [Google Scholar] [CrossRef] [PubMed]
- Radoglou-Grammatikis, P.; Sarigiannidis, P.; Sarigiannidis, A.; Margounakis, D.; Tsiakalos, A.; Efstathopoulos, G. An Anomaly Detection Mechanism for IEC 60870-5-104. In Proceedings of the 2020 9th International Conference on Modern Circuits and Systems Technologies (MOCAST), Bremen, Germany, 7–9 September 2020; pp. 1–4. [Google Scholar]
- Radoglou-Grammatikis, P.; Sarigiannidis, P.; Efstathopoulos, G.; Karypidis, P.A.; Sarigiannidis, A. DIDEROT: An intrusion detection and prevention system for DNP3-based SCADA systems. In Proceedings of the 15th International Conference on Availability, Reliability and Security, Virtual Event, Ireland, 25–28 August 2020; pp. 1–8. [Google Scholar]
- Tsoukalos, M. Using tshark to watch and inspect network traffic. Linux J. 2015, 2015, 1. [Google Scholar]
- Habibi Lashkari, A.; Draper Gil, G.; Mamun, M.S.I.; Ghorbani, A.A. Characterization of Tor Traffic using Time based Features. In Proceedings of the 3rd International Conference on Information Systems Security and Privacy, Porto, Portugal, 19–21 February 2017; SCITEPRESS—Science and Technology Publications: Porto, Portugal, 2017; pp. 253–262. [Google Scholar] [CrossRef]
- Manso, P.; Moura, J.; Serrão, C. SDN-based intrusion detection system for early detection and mitigation of DDoS attacks. Information 2019, 10, 106. [Google Scholar] [CrossRef] [Green Version]
- Pfaff, B.; Pettit, J.; Koponen, T.; Jackson, E.; Zhou, A.; Rajahalme, J.; Gross, J.; Wang, A.; Stringer, J.; Shelar, P.; et al. The Design and Implementation of Open vSwitch. In 12th USENIX Symposium on Networked Systems Design and Implementation (NSDI 15); USENIX Association: Oakland, CA, USA, 2015; pp. 117–130. [Google Scholar]
- Radoglou-Grammatikis, P.; Sarigiannidis, P.; Iturbe, E.; Rios, E.; Martinez, S.; Sarigiannidis, A.; Eftathopoulos, G.; Spyridis, I.; Sesis, A.; Vakakis, N.; et al. SPEAR SIEM: A Security Information and Event Management system for the Smart Grid. Comput. Netw. 2021, 193, 108008. [Google Scholar] [CrossRef]
- Efstathopoulos, G.; Grammatikis, P.R.; Sarigiannidis, P.; Argyriou, V.; Sarigiannidis, A.; Stamatakis, K.; Angelopoulos, M.K.; Athanasopoulos, S.K. Operational data based intrusion detection system for smart grid. In Proceedings of the 2019 IEEE 24th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Limassol, Cyprus, 11–13 September 2019; pp. 1–6. [Google Scholar]
- Lazaridis, G.; Papachristou, K.; Drosou, A.; Ioannidis, D.; Chatzimisios, P.; Tzovaras, D. On the Potential of SDN Enabled Network Deployment in Tactical Environments. In IFIP Advances in Information and Communication Technology; Springer: Berlin/Heidelberg, Germany, 2021; pp. 252–263. [Google Scholar]
- Charalampos-Rafail, M.; Thanasis, K.; Vasileios, V.; Dimosthenis, I.; Dimitrios, T.; Panagiotis, S. Cyber Attack Detection and Trust Management Toolkit for Defence-Related Microgrids. In IFIP Advances in Information and Communication Technology; Springer: Berlin/Heidelberg, Germany, 2021; pp. 240–251. [Google Scholar]
- Sun, Z.; Spyridis, Y.; Lagkas, T.; Sesis, A.; Efstathopoulos, G.; Sarigiannidis, P. End-to-End Deep Graph Convolutional Neural Network Approach for Intentional Islanding in Power Systems Considering Load-Generation Balance. Sensors 2021, 21, 1650. [Google Scholar] [CrossRef]
- Ivanova, A.; Paradell, P.; Domínguez-García, J.L.; Colet, A. Intentional Islanding of Electricity Grids Using Binary Genetic Algorithm. In Proceedings of the 2020 2nd Global Power, Energy and Communication Conference (GPECOM), Izmir, Turkey, 20–23 October 2020; pp. 297–301. [Google Scholar]
- Leshem, S.; Trafford, V. Overlooking the conceptual framework. Innov. Educ. Teach. Int. 2007, 44, 93–105. [Google Scholar] [CrossRef]
- SDN Architecture; Technical Report for SDN ARCH 1.0 06062014; Open Networking Foundation: Palo Alto, CA, USA, 2014.
- Overview of RFC7426: SDN Layers and Architecture Terminology–IEEE Software Defined Networks. Available online: https://sdn.ieee.org/newsletter/september-2017/overview-of-rfc7426-sdn-layers-and-architecture-terminology (accessed on 27 April 2021).
- Holz, T.; Raynal, F. Detecting honeypots and other suspicious environments. In Proceedings of the Sixth Annual IEEE SMC Information Assurance Workshop, West Point, NY, USA, 15–17 June 2005; pp. 29–36. [Google Scholar]
- Diamantoulakis, P.; Dalamagkas, C.; Radoglou-Grammatikis, P.; Sarigiannidis, P.; Karagiannidis, G. Game Theoretic Honeypot Deployment in Smart Grid. Sensors 2020, 20, 4199. [Google Scholar] [CrossRef] [PubMed]
- Kotsiopoulos, T.; Sarigiannidis, P.; Ioannidis, D.; Tzovaras, D. Machine Learning and Deep Learning in Smart Manufacturing: The Smart Grid Paradigm. Comput. Sci. Rev. 2021, 40, 100341. [Google Scholar] [CrossRef]
- Markopoulou, D.; Papakonstantinou, V.; de Hert, P. The new EU cybersecurity framework: The NIS Directive, ENISA’s role and the General Data Protection Regulation. Comput. Law Secur. Rev. 2019, 35, 105336. [Google Scholar] [CrossRef]
- Qu, Y.; Liu, X.; Jin, D.; Hong, Y.; Chen, C. Enabling a Resilient and Self-healing PMU Infrastructure Using Centralized Network Control. In Proceedings of the 2018 ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization, Tempe, AZ, USA, 21 March 2018; ACM: Tempe, AZ, USA, 2018; pp. 13–18. [Google Scholar] [CrossRef]
- Pham, T.A.Q.; Hadjadj-Aoul, Y.; Outtagarts, A. Deep reinforcement learning based qos-aware routing in knowledge-defined networking. In Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering; Springer: Berlin/Heidelberg, Germany, 2018; pp. 14–26. [Google Scholar]
- Rezaee, M.; Yaghmaee Moghaddam, M.H. SDN-Based Quality of Service Networking for Wide Area Measurement System. IEEE Trans. Ind. Inform. 2020, 16, 3018–3028. [Google Scholar] [CrossRef]
- Hong, J.B.; Yoon, S.; Lim, H.; Kim, D.S. Optimal Network Reconfiguration for Software Defined Networks Using Shuffle-Based Online MTD. In Proceedings of the 2017 IEEE 36th Symposium on Reliable Distributed Systems (SRDS), Hong Kong, China, 26–29 September 2017; pp. 234–243. [Google Scholar] [CrossRef]
- Wang, M.; Liu, J.; Mao, J.; Cheng, H.; Chen, J.; Qi, C. RouteGuardian: Constructing secure routing paths in software-defined networking. Tsinghua Sci. Technol. 2017, 22, 400–412. [Google Scholar] [CrossRef]
- Mambrini, A.; Izzo, D. PaDe: A Parallel Algorithm Based on the MOEA/D Framework and the Island Model. In Parallel Problem Solving from Nature – PPSN XIII; Springer International Publishing: Berlin/Heidelberg, Germany, 2014; pp. 711–720. [Google Scholar] [CrossRef]
- Izzo, D.; Ruciński, M.; Biscani, F. The Generalized Island Model. In Parallel Architectures and Bioinspired Algorithms; Springer: Berlin/Heidelberg, Germany, 2012; pp. 151–169. [Google Scholar] [CrossRef]
- Sessa, P.G.; Walton, N.; Kamgarpour, M. Exploring the Vickrey-Clarke-Groves Mechanism for Electricity Markets. IFAC-PapersOnLine 2017, 50, 189–194. [Google Scholar] [CrossRef]
- Ryu SDN Framework. Available online: https://ryu-sdn.org/ (accessed on 6 July 2021).
- Towards Securing Large-Scale Grid Interconnection Infrastructures—SDN microSENSE. Available online: https://www.sdnmicrosense.eu/ (accessed on 7 July 2021).
- Sokappadu, B.; Hardin, A.; Mungur, A.; Armoogum, S. Software Defined Networks: Issues and Challenges. In Proceedings of the 2019 Conference on Next Generation Computing Applications (NextComp), Mauritius, 19–21 September 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Campus Network for High Availability Design Guide. Available online: https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Campus/HA_campus_DG/hacampusdg.html (accessed on 7 July 2021).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Grammatikis, P.R.; Sarigiannidis, P.; Dalamagkas, C.; Spyridis, Y.; Lagkas, T.; Efstathopoulos, G.; Sesis, A.; Pavon, I.L.; Burgos, R.T.; Diaz, R.; et al. SDN-Based Resilient Smart Grid: The SDN-microSENSE Architecture. Digital 2021, 1, 173-187. https://doi.org/10.3390/digital1040013
Grammatikis PR, Sarigiannidis P, Dalamagkas C, Spyridis Y, Lagkas T, Efstathopoulos G, Sesis A, Pavon IL, Burgos RT, Diaz R, et al. SDN-Based Resilient Smart Grid: The SDN-microSENSE Architecture. Digital. 2021; 1(4):173-187. https://doi.org/10.3390/digital1040013
Chicago/Turabian StyleGrammatikis, Panagiotis Radoglou, Panagiotis Sarigiannidis, Christos Dalamagkas, Yannis Spyridis, Thomas Lagkas, Georgios Efstathopoulos, Achilleas Sesis, Ignacio Labrador Pavon, Ruben Trapero Burgos, Rodrigo Diaz, and et al. 2021. "SDN-Based Resilient Smart Grid: The SDN-microSENSE Architecture" Digital 1, no. 4: 173-187. https://doi.org/10.3390/digital1040013
APA StyleGrammatikis, P. R., Sarigiannidis, P., Dalamagkas, C., Spyridis, Y., Lagkas, T., Efstathopoulos, G., Sesis, A., Pavon, I. L., Burgos, R. T., Diaz, R., Sarigiannidis, A., Papamartzivanos, D., Menesidou, S. A., Ledakis, G., Pasias, A., Kotsiopoulos, T., Drosou, A., Mavropoulos, O., Subirachs, A. C., ... Arce, A. (2021). SDN-Based Resilient Smart Grid: The SDN-microSENSE Architecture. Digital, 1(4), 173-187. https://doi.org/10.3390/digital1040013











