An End-To-End Solution Towards Authenticated Positioning Utilizing Open-Source FGI-GSRx and FGI-OSNMA †
Abstract
1. Introduction
2. OSNMA Overview
OSNMA Authentication Tags
- ADKD=0: Ephemeris, clock, and status of the satellite are authenticated in each subframe (or 30 s) delay. FGI-GSRx offers further subdivision of ADKD=0 into the following:
- -
- SelfAuthADKD=0: ADKD=0 authentication of the satellite is carried out by itself.
- -
- CrossAuthADKD=0: ADKD=0 authentication of the satellite is carried out by some other satellite.
- ADKD=4: Galileo constellation-related timing information is authenticated.
- ADKD=12: The same information as in ADKD=0 is authenticated, but there will be an additional 10 subframe (or 300 s) delay in transmitting the TESLA key needed to authenticate the tag. FGI-GSRx offers further subdivision of ADKD=12 into the following:
- -
- SlowSelfAuthADKD=12: ADKD=12 authentication of the satellite is carried out by itself.
- -
- SlowCrossAuthADKD=12: ADKD=12 authentication of the satellite is carried out by some other satellite.
3. FGI-OSNMA
- Navigation data stream: the stream containing the navigation data to be authenticated.
- Tag stream: the stream containing the authentication tags.
- TESLA key stream: the stream containing the TESLA keys that are used to recompute the tags.
- Control stream: the stream contains the current protocol configuration and this stream handles events such as key and chain revocations.
- Success: The ADKD=0 authentication was successful by self or cross-ADKD=0. The navigation message can be trusted.
- Failure: The ADKD=0 authentication was not verified by self or cross-ADKD=0. The navigation message cannot be trusted.
- Missing tag: The authentication of a given navigation message cannot be attempted because we are missing the corresponding tag.
- Missing navigation data: We have received a tag, but not the corresponding navigation data. As such, the authentication cannot be attempted.
- Failed Cyclic Redundancy Check (CRC).
- Success or failure to authenticate a TESLA root key.
4. FGI-GSRx-v2.1.0
- Cold start: In case the public key and TESLA root key are not available, the receiver shall first retrieve them directly from a web service, or possibly via SIS.
- Warm start: If the receiver has stored a previously verified public key, the receiver shall retrieve the DSM-KROOT, verify the public key, and verify the DSM-KROOT with the stored key.
- Hot start: If, in addition to a stored public key, the receiver also possesses previously verified TESLA key and chain parameters, it does not have to retrieve the DSM-KROOT. The receiver shall attempt to verify the received TESLA chain key with the stored key.
5. Experimental Setup
5.1. Live Open Sky Signal
5.2. Recording and Replaying Jammertest Data
6. Result Analysis
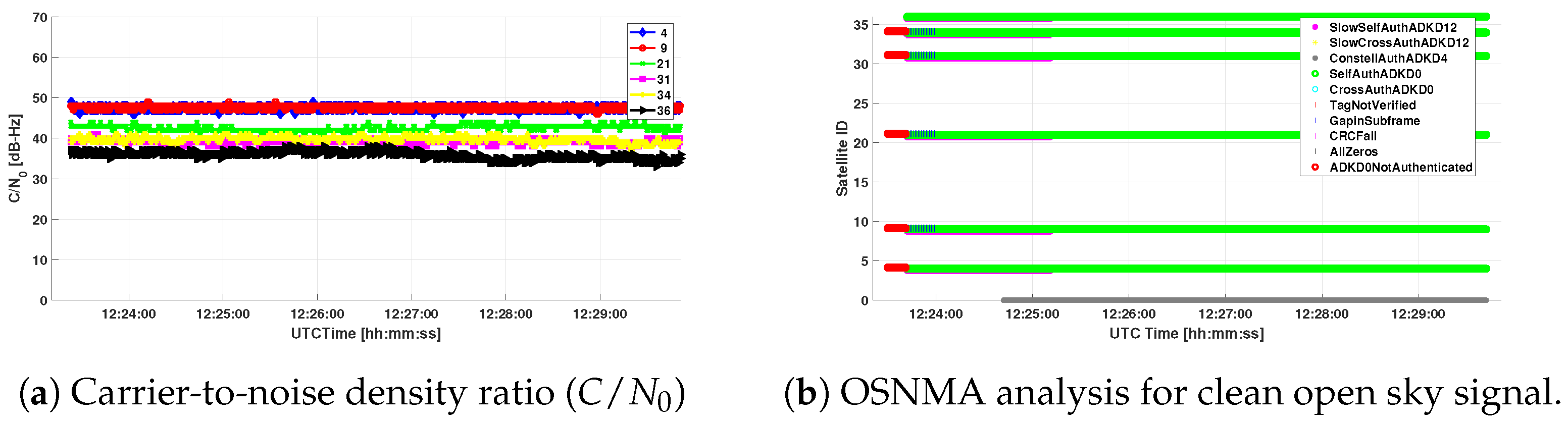
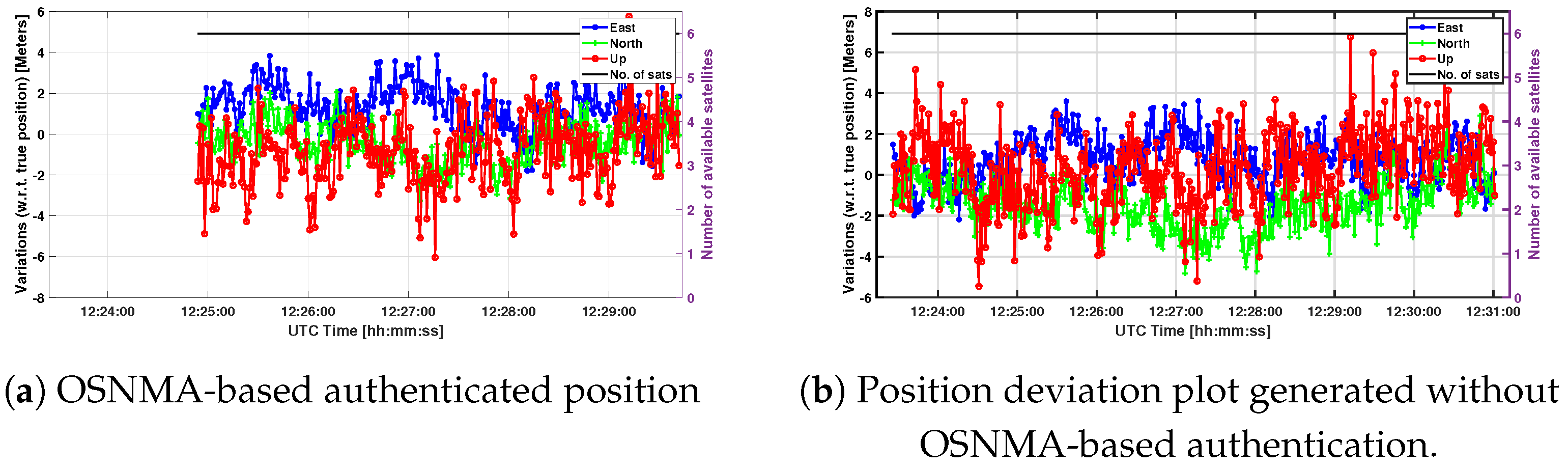
6.1. Authenticated Position Under Clean Open Sky Scenario
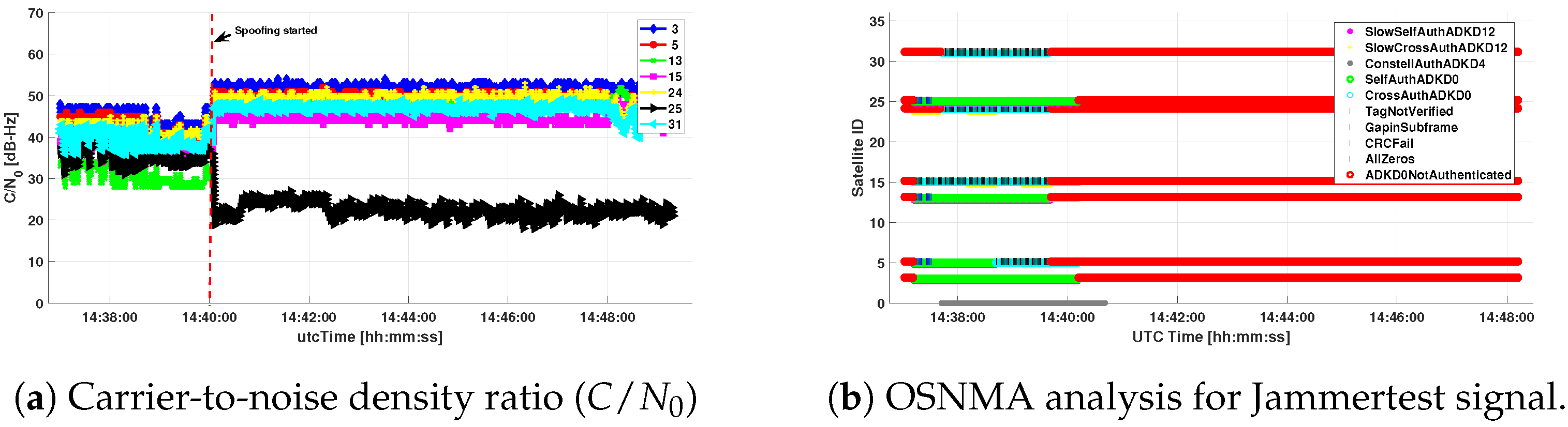
6.2. Authenticated Position in a Real-World Spoofing Scenario
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- GNSS Investment Report. Available online: https://www.euspa.europa.eu/sites/default/files/uploads/gnss_investment_report\_2021.pdf (accessed on 17 January 2024).
- Liu, Y.; Li, S.; Fu, Q.; Liu, Z. Impact Assessment of GNSS Spoofing Attacks on INS/GNSS Integrated Navigation System. Sensors 2018, 18, 1433. [Google Scholar] [CrossRef] [PubMed]
- GALILEO Open Service Navigation Message Authentication (OSNMA) Info Note. Available online: https://www.gsc-europa.eu/sites/default/files/sites/all/files/Galileo_OSNMA_Info_Note.pdf (accessed on 17 January 2024).
- Hernández, I.F.; Ashur, T.; Rijmen, V.; Sarto, C.; Cancela, S.; Calle, D. Toward an Operational Navigation Message Authentication Service: Proposal and Justification of Additional OSNMA Protocol Features. In Proceedings of the 2019 European Navigation Conference (ENC), Warsaw, Poland, 9–12 April 2019; pp. 1–6. [Google Scholar]
- Nicola, M.; Motella, B.; Pini, M.; Falletti, E. Galileo OSNMA Public Observation Phase: Signal Testing and Validation. IEEE Access 2022, 10, 27960–27969. [Google Scholar] [CrossRef]
- Motallebighomi, M.; Sathaye, H.; Singh, M.; Ranganathan, A. Cryptography is Not Enough: Relay Attacks on Authenticated GNSS Signals. arXiv 2022, arXiv:2204.11641. [Google Scholar]
- Terris-Gallego, R.; Fernandez-Hernandez, I.; López-Salcedo, J.A.; Seco-Granados, G. Guidelines for Galileo Assisted Commercial Authentication Service Implementation. In Proceedings of the International Conference on Localization and GNSS (ICL-GNSS), Tampere, Finland, 7–9 June 2022; pp. 1–7. [Google Scholar]
- Fernandez-Hernandez, I.; Cancela, S.; Terris-Gallego, R.; Seco-Granados, G.; López-Salcedo, J.A.; O’Driscoll, C.; Winkel, J.; Chiara, A.d.; Sarto, C.; Rijmen, V.; et al. Semi-Assisted Signal Authentication Based on Galileo ACAS. arXiv 2022, arXiv:2204.14026. [Google Scholar]
- Mosaic-X5, Compact, Multi-Constellation GNSS Receiver Module. Available online: https://www.septentrio.com/en/products/gps/\gnss-receiver-modules/mosaic-x5 (accessed on 19 January 2024).
- Lesjak, R.; Schweitzer, S.; Vallet García, J.M.; Diengsleder-Lambauer, K.; Solmaz, S. A Comparative Experimental Performance Assessment of RTK+OSNMA-Based Positioning for Road Vehicle Applications. Eng. Proc. 2023, 54, 45. [Google Scholar] [CrossRef]
- García, J.M.V.; Bhuiyan, M.Z.H. RTK+OSNMA Positioning for Road Applications: An Experimental Performance Analysis in Finland. Sensors 2024, 24, 621. [Google Scholar] [CrossRef] [PubMed]
- Hammarberg, T.; García, J.M.V.; Alanko, J.N.; Bhuiyan, M.Z.H. An Open Source Implementation of Galileo’s Open Service Navigation Message Authentication. In Proceedings of the 36th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS+ 2023), Denver, CO, USA, 11–15 September 2023; pp. 3774–3785. [Google Scholar]
- Hammarberg, T.; García, J.M.V.; Alanko, J.N.; Bhuiyan, M.Z.H. An Experimental Performance Assessment of Galileo OSNMA. Sensors 2024, 24, 404. [Google Scholar] [CrossRef] [PubMed]
- Takasu, T.; Yasuda, A. Development of the Low-cost RTK-GPS Receiver with an Open Source Program Package RTKLIB. In Proceedings of the International Symposium on GPS/GNSS, Seogwipo-si, Republic of Korea, 4–6 November 2009; Volume 1, pp. 1–6. [Google Scholar]
- Kai, B.; Fernández-Hernández, I.; José, A.L.; Bhuiyan, M.Z.H. GNSS Software Receivers; Cambridge University Press: Cambridge, UK, 2022. [Google Scholar]
- Liaquat, M.; Bhuiyan, M.Z.H.; Islam, S.; Pääkkönen, I.; Kaasalainen, S. An Enhanced FGI-GSRx Software-Defined Receiver for the Execution of Long Datasets. Preprints 2024, 2024050443. [Google Scholar] [CrossRef] [PubMed]
- Söderholm, S.; Bhuiyan, M.Z.H.; Thombre, S.; Ruotsalainen, L.; Kuusniemi, H. A Multi-GNSS software-defined Receiver: Design, Implementation, and Performance Benefits. Ann. Telecommun. 2016, 71, 399–410. [Google Scholar] [CrossRef]
- Islam, S.; Bhuiyan, M.Z.H.; Pääkkönen, I.; Saajasto, M.; Mäkelä, M.; Kaasalainen, S. Impact Analysis of Spoofing on Different-grade GNSS Receivers. In Proceedings of the IEEE/ION Position, Location and Navigation Symposium (PLANS), Monterey, CA, USA, 23–27 April 2023; pp. 492–499. [Google Scholar] [CrossRef]
- Islam, S.; Bhuiyan, M.Z.H.; Thombre, S.; Kaasalainen, S. Combating Single-Frequency Jamming through a Multi-Frequency, Multi-Constellation Software Receiver: A Case Study for Maritime Navigation in the Gulf of Finland. Sensors 2022, 22, 2294. [Google Scholar] [CrossRef] [PubMed]
- Perrig, A.; Tygar, J. Tesla Broadcast Authentication. In Secure Broadcast Communication; Springer: Berlin/Heidelberg, Germany, 2003; pp. 29–53. [Google Scholar]
- Galileo Open Service Navigation Message Authentication (OSNMA) Receiver Guidelines, Issue 1.3, 2024. Available online: https://www.gsc-europa.eu/sites/default/files/sites/all/files/Galileo_OSNMA_Receiver_Guidelines_v1.3.pdf (accessed on 19 January 2024).
- Galileo Open Service Navigation Message Authentication (OSNMA) Signal-In-Space Interface Control Document (SIS ICD), Issue 1.1, 2023. Available online: https://www.gsc-europa.eu/sites/default/files/sites/all/files/Galileo_OSNMA_SIS_ICD_v1.1.pdf (accessed on 17 January 2024).
- Galileo Open Service Navigation Message Authentication (OSNMA); Hernandez, I.F.; Rijmen, V.; Seco-Granados, G.; Simon, J.; Rodrıguez, I.; Calle, J.D. A Navigation Message Authentication Proposal for the Galileo Open Service. Navig. J. Inst. Navig. 2016, 63, 85–102. [Google Scholar]






| Parameters | Frequency Bands (E1B) |
|---|---|
| Center frequency (MHz) | 1569.03 |
| Sampling rate (MHz) | 26 |
| Data type | Sampling |
| Sample bit width | 8 bit |
| Bandwidth (MHz) | 4.2 |
| Availability (%) | TTFAF | ||||||
|---|---|---|---|---|---|---|---|
| Position authentication | 80.86 | 2.69 | 1.03 | 1.49 | 0.75 | 1.83 | 88 s |
| No position authentication | 100 | 2.68 | 1.45 | 1.14 | 1.84 | 1.73 | NA |
| Availability (%) | TTFAF | ||||||
|---|---|---|---|---|---|---|---|
| Position authentication | 10 | 4.38 | 3.12 | 0.98 | 2.69 | 1.11 | 90 s |
| No position authentication | 100 | 426.01 | 32.49 | 66.59 | 227.18 | 416.60 | NA |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liaquat, M.; Bhuiyan, M.Z.H.; Hammarberg, T.; Islam, S.; Saajasto, M.; Kaasalainen, S. An End-To-End Solution Towards Authenticated Positioning Utilizing Open-Source FGI-GSRx and FGI-OSNMA. Eng. Proc. 2025, 88, 58. https://doi.org/10.3390/engproc2025088058
Liaquat M, Bhuiyan MZH, Hammarberg T, Islam S, Saajasto M, Kaasalainen S. An End-To-End Solution Towards Authenticated Positioning Utilizing Open-Source FGI-GSRx and FGI-OSNMA. Engineering Proceedings. 2025; 88(1):58. https://doi.org/10.3390/engproc2025088058
Chicago/Turabian StyleLiaquat, Muwahida, Mohammad Zahidul H. Bhuiyan, Toni Hammarberg, Saiful Islam, Mika Saajasto, and Sanna Kaasalainen. 2025. "An End-To-End Solution Towards Authenticated Positioning Utilizing Open-Source FGI-GSRx and FGI-OSNMA" Engineering Proceedings 88, no. 1: 58. https://doi.org/10.3390/engproc2025088058
APA StyleLiaquat, M., Bhuiyan, M. Z. H., Hammarberg, T., Islam, S., Saajasto, M., & Kaasalainen, S. (2025). An End-To-End Solution Towards Authenticated Positioning Utilizing Open-Source FGI-GSRx and FGI-OSNMA. Engineering Proceedings, 88(1), 58. https://doi.org/10.3390/engproc2025088058






