UWB-Based Positioning Is Not Invulnerable from Spoofing Attacks: A Case Study of Crazyswarm †
Abstract
1. Introduction
2. Related Works
3. Threat Model
3.1. Network Model
3.2. Positioning
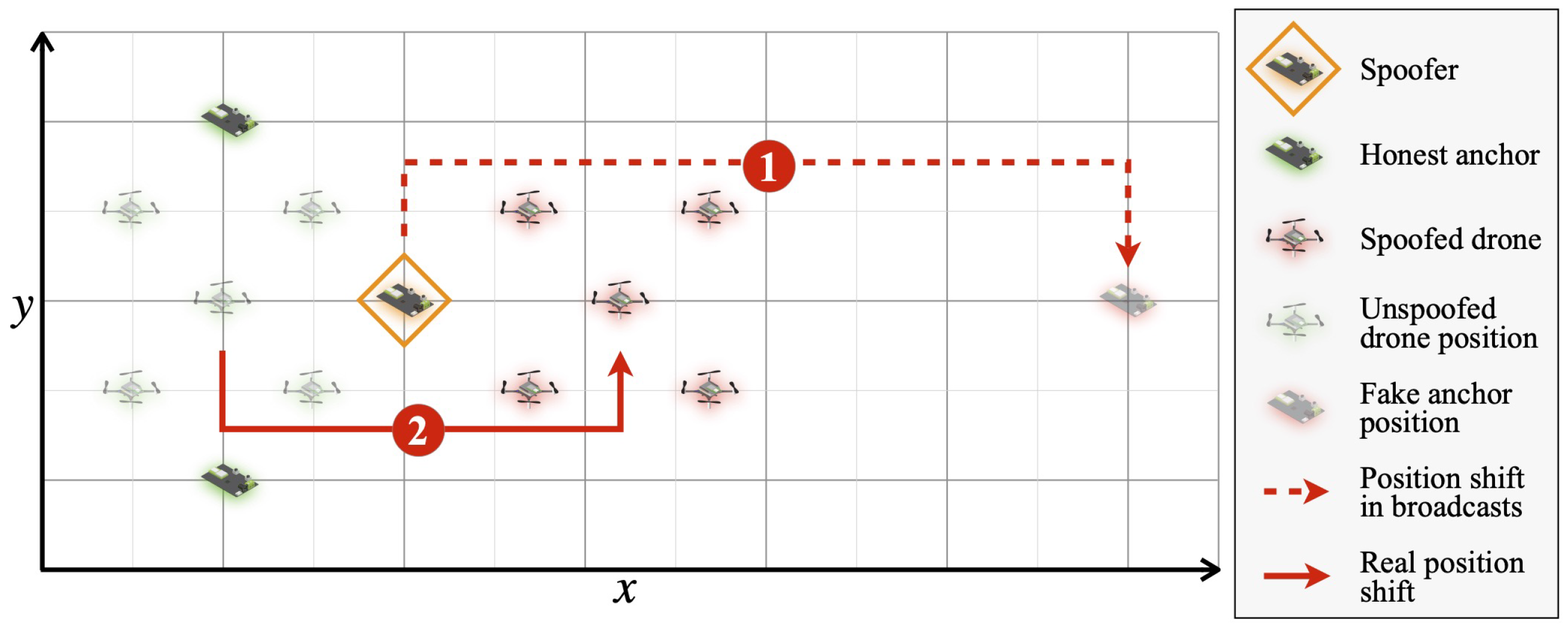
3.3. Attacker Model
3.4. Spoofing Model
4. Requirements
4.1. TDoA Mode
4.2. Spoofing Detection Method
TESLA
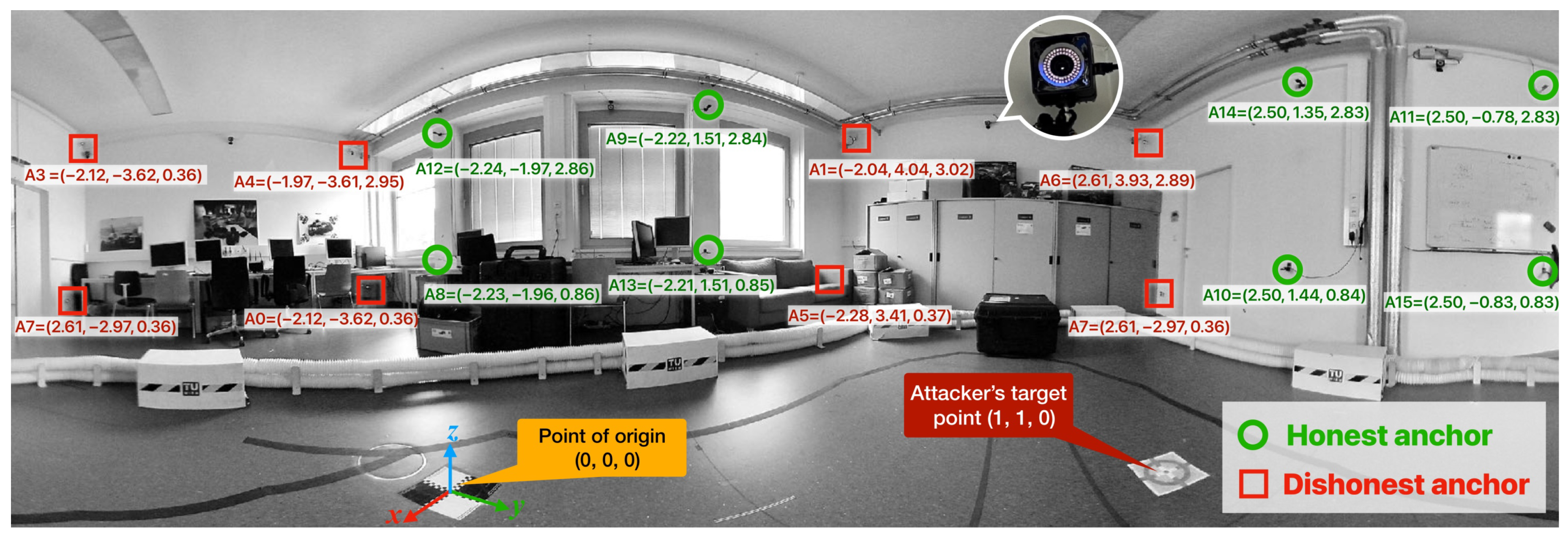
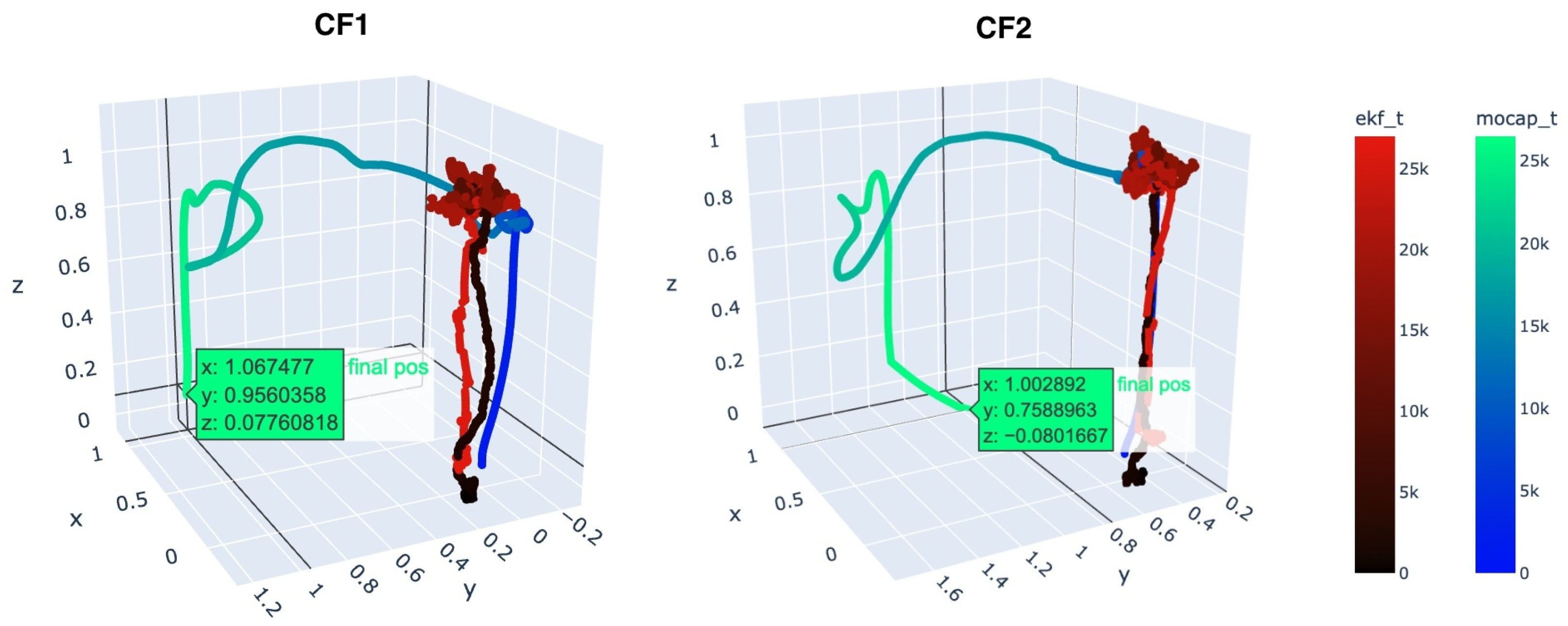
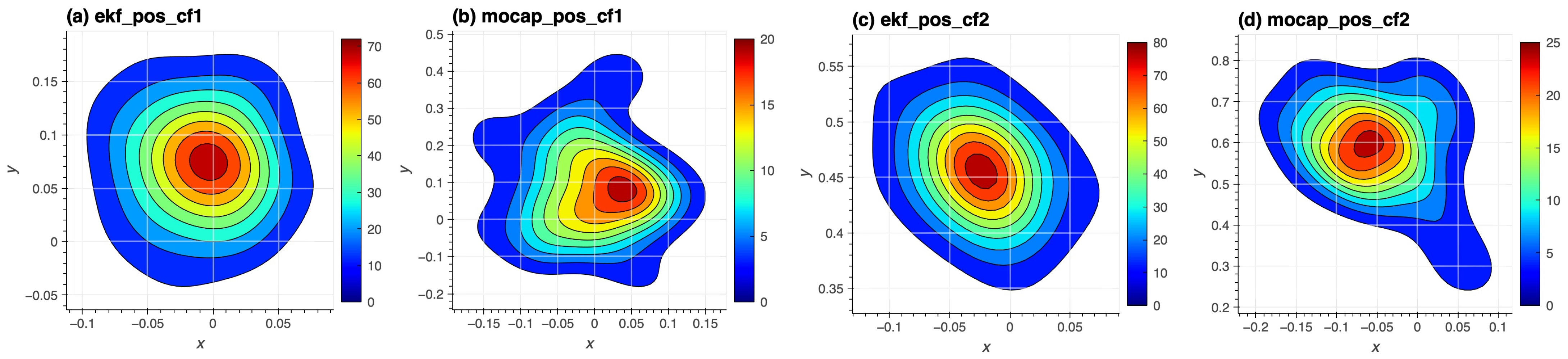
5. Experiment
5.1. Authentication Parameters
5.2. System Configuration
5.3. Algorithms
| Algorithm 1: TESLA keychain generation in and its usage |
 |
| Algorithm 2: Packet authentication in |
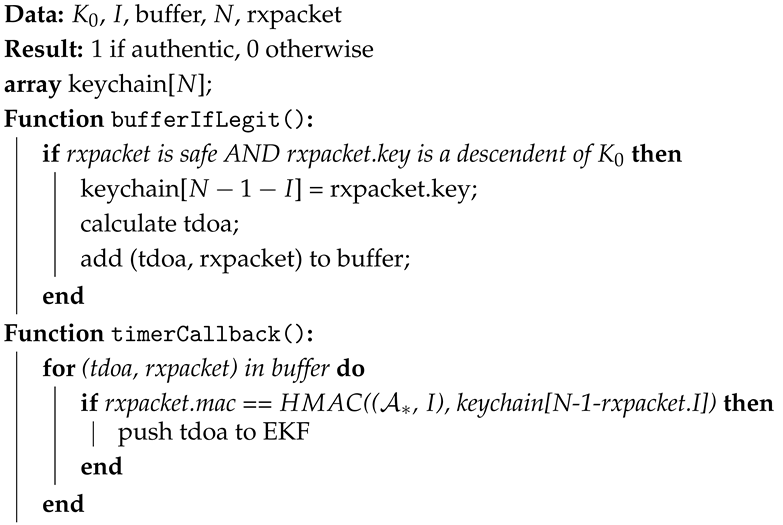 |
6. Discussion
7. Conclusions
Supplementary Materials
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Abdelkader, M.; Güler, S.; Jaleel, H.; Shamma, J.S. Aerial swarms: Recent applications and challenges. Curr. Robot. Rep. 2021, 2, 309–320. [Google Scholar] [CrossRef] [PubMed]
- FAA Aerospace Forecast Fiscal Years 2024–2044. Available online: https://www.faa.gov/dataresearch/aviation/aerospaceforecasts/faa-aerospace-forecast-fy-2024-2044 (accessed on 6 May 2024).
- Eshmawi, A.A.; Umer, M.; Ashraf, I.; Park, Y. Enhanced Machine Learning Ensemble Approach for Securing Small Unmanned Aerial Vehicles From GPS Spoofing Attacks. IEEE Access 2024, 12, 27344–27355. [Google Scholar] [CrossRef]
- Novák, A.; Kováčiková, K.; Kandera, B.; Sedláčková, A.N. Global Navigation Satellite Systems Signal Vulnerabilities in Unmanned Aerial Vehicle Operations: Impact of Affordable Software-Defined Radio. Drones 2024, 8, 109. [Google Scholar] [CrossRef]
- Humphreys, T. Statement on the Vulnerability of Civil Unmanned Aerial Vehicles and Other Systems to Civil GPS Spoofing. Available online: https://radionavlab.ae.utexas.edu/images/stories/files/papers/Testimony-Humphreys.pdf (accessed on 29 April 2025).
- Preiss, J.A.; Honig, W.; Sukhatme, G.S.; Ayanian, N. Crazyswarm: A large nano-quadcopter swarm. In Proceedings of the 2017 IEEE International Conference on Robotics and Automation (ICRA), Singapore, 29 May–3 June 2017. [Google Scholar]
- Shariat, M.; Kastner, W. Authenticated UWB-Based Positioning of Passive Drones. In Proceedings of the 2023 IEEE 19th International Conference on Factory Communication Systems (WFCS), Pavia, Italy, 26–28 April 2023; pp. 1–8. [Google Scholar]
- Zhang, Y.; Liu, W.; Fang, Y.; Wu, D. Secure localization and authentication in ultra-wideband sensor networks. IEEE J. Sel. Areas Commun. 2006, 24, 829–835. [Google Scholar] [CrossRef]
- Qiu, D.; Lo, S.; Enge, P.; Boneh, D.; Peterson, B. Geoencryption Using Loran. In Proceedings of the 2007 National Technical Meeting of The Institute of Navigation, San Diego, CA, USA, 22–24 January 2007; pp. 104–115. [Google Scholar]
- Becker, G.; Lo, S.; Lorenzo, D.D.; Qiu, D.; Paar, C.; Enge, P. Efficient authentication mechanisms for navigation systems—A radio-navigation case study. In Proceedings of the 22nd International Technical Meeting of The Satellite Division of the Institute of Navigation, Savannah, GA, USA, 22–25 September 2009; pp. 901–912. [Google Scholar]
- Guo, X.; Zhu, J. Research on security issues in Wireless Sensor Networks. In Proceedings of the 2011 International Conference on Electronic & Mechanical Engineering and Information Technology, Harbin, China, 12–14 August 2011. [Google Scholar]
- Zhang, P.; Nagarajan, S.G.; Nevat, I. Secure Location of Things (SLOT): Mitigating Localization Spoofing Attacks in the Internet of Things. IEEE Internet Things J. 2017, 4, 2199–2206. [Google Scholar] [CrossRef]
- Alawami, M.A.; Kim, H. LocAuth: A fine-grained indoor location-based authentication system using wireless networks characteristics. Comput. Secur. 2020, 89, 101683. [Google Scholar] [CrossRef]
- Prashar, D.; Rashid, M.; Siddiqui, S.T.; Kumar, D.; Nagpal, A.; AlGhamdi, A.S.; Alshamrani, S.S. SDSWSN—A secure approach for a hop-based localization algorithm using a digital signature in the wireless sensor network. Electronics 2021, 10, 3074. [Google Scholar] [CrossRef]
- Perrig, A.; Song, D.; Canetti, R.; Tygar, J.D.; Briscoe, B. Timed Efficient Stream Loss-Tolerant Authentication (TESLA): Multicast Source Authentication Transform Introduction; Technical Report RFC 4082; Internet Engineering Task Force: Fremont, CA, USA, 2005. [Google Scholar]
- ISO/IEC 29192-7:2019; Information Security—Lightweight Cryptography—Part 7: Broadcast Authentication Protocols. International Organization for Standardization: Geneva, Switzerland, 2019.
- Stocker, M.; Kowalczyk, J.; Boano, C.A.; Römer, K. Towards Secure Multicast Ranging with Ultra-Wideband Systems. In Proceedings of the 2022 International Conference on Embedded Wireless Systems and Networks, Linz, Austria, 3–5 October 2022; EWSN ’22; pp. 256–261. [Google Scholar]
- Stocker, M.; Groswindhager, B.; Boano, C.A.; Romer, K. Towards secure and scalable UWB-based positioning systems. In Proceedings of the 2020 IEEE 17th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), Virtual, 10–13 December 2020. [Google Scholar]
- Chen, H.; Dhekne, A. Spoofing Evident and Spoofing Deterrent Localization Using Ultrawideband (UWB) Active–Passive Ranging. IEEE J. Indoor Seamless Position. Navig. 2024, 2, 12–24. [Google Scholar] [CrossRef]
- Itkin, E.; Wool, A. A security analysis and revised security extension for the precision time protocol. IEEE Trans. Dependable Secure Comput. 2020, 17, 22–34. [Google Scholar] [CrossRef]
- van der Merwe, J.R.; Zubizarreta, X.; Lukčin, I.; Rügamer, A.; Felber, W. Classification of Spoofing Attack Types. In Proceedings of the 2018 European Navigation Conference (ENC), Gothenburg, Sweden, 14–17 May 2018; pp. 91–99. [Google Scholar]
- Meng, W.; Xie, L.; Xiao, W. Optimal TDOA sensor-pair placement with uncertainty in source location. IEEE Trans. Veh. Technol. 2016, 65, 9260–9271. [Google Scholar] [CrossRef]
- Zhao, W.; Goudar, A.; Qiao, X.; Schoellig, A.P. UTIL: An ultra-wideband time-difference-of-arrival indoor localization dataset. Int. J. Rob. Res. 2024, 43, 1443–1456. [Google Scholar] [CrossRef]
- Perrig, A.; Canetti, R.; Tygar, J.D.; Song, D. Efficient authentication and signing of multicast streams over lossy channels. In Proceedings of the 2000 IEEE Symposium on Security and Privacy, S&P 2000, Berkeley, CA, USA, 14–17 May 2002. [Google Scholar]
- Basin, D.; Capkun, S.; Schaller, P.; Schmidt, B. Formal reasoning about physical properties of security protocols. ACM Trans. Inf. Syst. Secur. 2011, 14, 1–28. [Google Scholar] [CrossRef]
- Ning, P.; Liu, A.; Du, W. Mitigating DoS attacks against broadcast authentication in wireless sensor networks. ACM Trans. Sen. Netw. 2008, 4, 1–35. [Google Scholar] [CrossRef]
- Annessi, R.; Fabini, J.; Zseby, T. It’s about Time: Securing Broadcast Time Synchronization with Data Origin Authentication. In Proceedings of the 2017 26th International Conference on Computer Communication and Networks (ICCCN), Vancouver, BC, Canada, 31 July–3 August 2017; pp. 1–11. [Google Scholar]
- Cancela, S.; Calle, J.D.; Fernandez-Hernandez, I. CPU consumption analysis of TESLA-based navigation message authentication. In Proceedings of the 2019 European Navigation Conference (ENC), Warsaw, Poland, 9–12 April 2019. [Google Scholar]
- Mueller, M.W.; Hamer, M.; D’Andrea, R. Fusing ultra-wideband range measurements with accelerometers and rate gyroscopes for quadrocopter state estimation. In Proceedings of the 2015 IEEE International Conference on Robotics and Automation (ICRA), Seattle, WA, USA, 26–30 May 2015. [Google Scholar]
- Mueller, M.W.; Hehn, M.; D’Andrea, R. Covariance correction step for Kalman filtering with an attitude. J. Guid. Control Dyn. 2017, 40, 2301–2306. [Google Scholar] [CrossRef]


| Symbol | Description |
|---|---|
| UWB-based anchor | |
| UWB-based passive tag (e.g., a drone) | |
| An ordered subset of , indexed by elements. | |
| An ordered subset of , indexed by elements. | |
| -norm, i.e., the Euclidean distance | |
| Collision Resistant Hash Function with x as input of arbitrarily length | |
| ith key in TESLA keychain | |
| Message Authentication Code based on with k as the key | |
| ‖ | Concatenation operation |
| N | TESLA keychain size (i.e., number of keys) |
| s | TESLA keychain seed, a pseudorandom value |
| D | TESLA interval length, measured in seconds |
| d | TESLA key disclosure delay, measured in units of D |
| I | TESLA interval index with |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shariat, M.; Gabela Majić, J.; Brandstätter, M.; Kastner, W. UWB-Based Positioning Is Not Invulnerable from Spoofing Attacks: A Case Study of Crazyswarm. Eng. Proc. 2025, 88, 43. https://doi.org/10.3390/engproc2025088043
Shariat M, Gabela Majić J, Brandstätter M, Kastner W. UWB-Based Positioning Is Not Invulnerable from Spoofing Attacks: A Case Study of Crazyswarm. Engineering Proceedings. 2025; 88(1):43. https://doi.org/10.3390/engproc2025088043
Chicago/Turabian StyleShariat, Mahyar, Jelena Gabela Majić, Max Brandstätter, and Wolfgang Kastner. 2025. "UWB-Based Positioning Is Not Invulnerable from Spoofing Attacks: A Case Study of Crazyswarm" Engineering Proceedings 88, no. 1: 43. https://doi.org/10.3390/engproc2025088043
APA StyleShariat, M., Gabela Majić, J., Brandstätter, M., & Kastner, W. (2025). UWB-Based Positioning Is Not Invulnerable from Spoofing Attacks: A Case Study of Crazyswarm. Engineering Proceedings, 88(1), 43. https://doi.org/10.3390/engproc2025088043






