Abstract
Pattern recognition algorithms have been used to make it possible for computer vision to self-train and comprehend visual input. Advanced measurements have been required every time for the early detection of armed threats in order to decrease accidents and terrorist attacks. Weapon detection systems have mostly been used in public spaces such as stadiums, airports, key squares, and battlefields, whether they are in urban or rural settings, to achieve better security objectives. Based on cloud architecture, DL and ML algorithms have been used by contemporary closed-circuit television surveillance and control systems to detect weapons. In addition to using the Raspberry Pi as an edge device and an efficient model to construct a weapons detection system, edge computing is used to address these problems. The text report includes the image processing results. Soldiers can outfit themselves with the recommended edge node and headphones, and the visual data output will allow them to receive alerts about armed threats. Furthermore, we can improve our method’s performance by adding more training data and changing the network architecture. The primary object of this paper is to build a model for detecting weapons such as pistols and rifles. The model developed in this research detects weapons such as pistols and rifles in an average time of 1.30 s.
1. Introduction
Weapon detection systems use various parts and devices, from cameras and sensors to analytics software, to identify threats. An overview of these advanced security measures that are used to protect us is provided here. Armed individuals who capture territory and upend stability in a state or region are typically involved in these violent crimes. Terrorist and adversary strikes frequently take place in public spaces and at strategic locations. The early detection of weapons is one of those strategies. A human operator is needed in traditional closed-circuit television (CCTV) monitoring and control systems, which necessitate the manual operation of numerous cameras [1,2]. A notably large body of staff is needed to watch cameras over wide areas; therefore, artificial intelligence (AI) is the primary technology being used in modern weapons detection systems. Original artificial intelligence (AI) detection and identification systems’ primary duty was to identify a person by their face. Given that face recognition is one of the most significant tasks in the field of computer vision, these systems have a wide range of potential applications, ranging from in intelligence services to scholarly studies. Furthermore, a person’s posture can reveal information about the likelihood that they are brandishing a weapon [3,4]. Figure 1 shows an overview of the human vision system.

Figure 1.
Overview of the human vision system adapted from v7labs.com.
The Raspberry Pi model, described in [5,6], will be able to finish the EfficientDet model-based weapon detection work and lower the cost of the technical solution.
Research Contribution
- The model developed in this research detects weapons such as pistols and rifles in an average time of 1.30 s.
- The model decreases the amount of transmitted data and requires less network bandwidth.
- The model takes an average time of 1.30 s to execute the algorithm compared to 1.76 s for the InceptionNetV2 model.
- The model is able to compare transmission video streams at a rate of 1.8 megabytes per second.
2. Literature Review
In one study, a model was trained via the trilling technique to detect tiny weapons using the Armed CCTV Footage dataset and the Single Shot Detector MobileNet V2. Related studies on weapon detection include the work carried out in [7,8], which evaluated the sliding window approach using Faster-RCNN and VGG-16 on various datasets and videos from YouTube [9,10]. The rate of weapon detection was affected, specifically for cold-steel knives and blades. While this proved successful for indoor applications, the accuracy reduced during outdoor use due to various lighting conditions and reflections. In [11,12], the model was trained the model to stop mistaking similarly shaped objects for weapons. The method used involved training multiple CNN models to identify distinct components of the weapon, like the trigger or the muzzle, and then averaging the models to predict the presence of pistols in the images. In [13] an approach was proposed that produced higher detection rates, but also resulted in longer detection times. To identify concealed weapons, the research conducted by [14,15] relied on specialized images captured by passive millimeter-wave cameras and employed a CNN model to identify similar-shaped gray items as firearms. Figure 2 presents the taxonomy of the literature review.
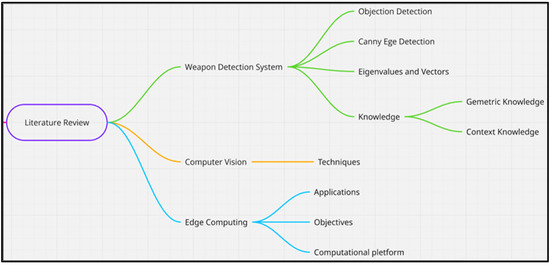
Figure 2.
The taxonomy of the literature review.
Although these systems yield good outcomes, households cannot afford the high cost of this technology. To detect firearms, the research by [16] uses an ensemble of semantic neural networks. Multiple neural networks are given distinct tasks, and the average of the outputs indicates whether a handgun was present. In [17], additional research was conducted on the Faster-RCNN model for item and pedestrian detection. In [18], support vector machines (SVMs) were employed for real-time apparel recognition from security footage. A survey titled “Advances in Deep Learning using X-ray Security Imaging”, carried out in [19], analyzed the performance of various CNN versions and other algorithms used for security in the identification of potentially dangerous objects in luggage at airports. Although their proposed model functioned effectively, regular settings, households without sufficient money, and regions with exceptionally high or low temperatures cannot use the system due to the requirement of passive millimeter-wave pictures. Using the previously mentioned literature review, attempts were made to design an optimal model to maximize the outcomes through pre-processing approaches and detect objects quickly and accurately in real time. As mentioned before, there are relevant publications that explain how deep machine learning techniques have now been applied to weapon detection. Convolutional neural networks are one of the most used traditional real-time weapons detection techniques [19]. While CNNs have performed remarkably well in image classification, they have suffered from overfitting in the absence of large datasets and Multiview cameras. To overcome these challenges, the CNN architecture has been developed to produce a Faster Region CNN. There are several uses for IoT technology, including protecting people’s safety in smart cities, smart homes, businesses, and transit [20]. Studies indicate that the usage of the cloud paradigm in the Internet of Things has resulted in inadequate network capacity, massive generated data, excessive power consumption, weak network security, and data privacy issues [21,22]. For military objectives, these Internet of Things application concerns are quite important. Since the effects of turning off the network are immeasurable, the current research is concentrated on IoT security.
3. Overview of the Weapon Detection System
TensorFlow already provides state-of-the-art object identification models, which is crucial because the goal of this study is to deploy a weapon detection system on Android rather than design a new model. TensorFlow, an open-source machine learning platform with a large, flexible ecosystem of tools and libraries, enables the utilization of state-of-the-art resources for machine learning and for creating and testing deep learning architectures [23]. The TensorFlow Object Detection API is an additional open-source software library built on top of TensorFlow that facilitates the creation, training, and implementation of detection models. TensorFlow’s pre-trained model architectures have previously undergone intensive training on a large dataset, usually consisting of image classification tasks. This allows the model to extract useful features, which is an important first step in learning how to complete new tasks. The discovery of irregular, unexpected, unpredictable, or unusual events or items that are present in a dataset and, as a result, diverge from preexisting patterns—that is, regularly recurring events or regular items in a pattern—is known as weapon or anomaly detection [24,25]. Accurate gun detection and categorization are the main goals of the proposed implementation. Systems for detecting weapons are a crucial component of both private and public security infrastructure. These solutions safeguard digital assets, stop terrorist attacks, and much more. In the modern world, these methods are necessary to guarantee safety without compromising an individual’s civil liberties. Therefore, it is crucial to comprehend the necessity of weapon detection systems before delving into the technology they use.
4. Security Weapon Detector Types
It is critical to discuss the kinds of firearm detection systems in use today. For instance, airport security uses handheld metal detectors. Furthermore, contemporary technology is being used more and more for comparable functions, like thermal imaging cameras and security. In terms of the analysis of potentially harmful products, security officers are able to examine them with greater accuracy and precision. Sophisticated analysis and signal processing algorithms are the foundation of advanced weapon detection systems’ ability to precisely recognize and identify possible threats. For this reason, in order for the system to accurately assess whether an object is a real weapon, it needs a data-rich model of an object, like a gun. Tests are conducted on the object’s physical attributes to develop this kind of model. Radar-based systems are another kind of weapon-detecting system employed in security today. These systems use electromagnetic waves to identify the location, velocity, and existence of objects. These systems have several drawbacks despite their propensity for great accuracy. Digital network technology is another option for weapon detection in addition to radar-based systems. Digital networks usually utilize detectors and cameras to identify weapons nearby. Real-time data from a variety of sources, including security cameras, sensors, and motion detectors, can be collected over these networks. As a result, the system can instantly identify dangers and notify the proper authorities of any questionable conduct. Furthermore, sophisticated algorithms are frequently incorporated into the construction of digital networks, enabling them to recognize objects of any size or shape and assisting in the reduction in false alarms brought on by outside noise.
5. Overview of Computer Vision
These devices function by detecting metal objects, such as knives or guns. Furthermore, modern technology is increasingly utilized for similar purposes, such as security X-ray equipment and thermal imaging cameras [26,27]. These methods enable security agents to evaluate potentially dangerous products more precisely and accurately. The ability of advanced weapon detection systems to accurately identify and detect threats is based on sophisticated analysis and signal processing algorithms. Because of this, the system requires a data-rich model of an object, such as a gun, in order to determine whether it is a real weapon. Tests are conducted on the object’s physical attributes to develop this kind of model. Radar-based systems are another kind of weapon-detecting system employed in security today. These systems use electromagnetic waves to identify the location, velocity, and existence of objects. These systems have drawbacks despite their propensity for great accuracy. Digital network technology is another option for weapon detection in addition to radar-based systems. Digital networks usually utilize detectors and cameras to identify weapons nearby. Real-time data from a variety of sources, including security cameras, sensors, and motion detectors, can be collected over these networks [28,29]. As a result, the system can instantly identify dangers and notify the proper authorities of any questionable conduct. Furthermore, sophisticated algorithms are frequently incorporated into the construction of digital networks, enabling them to recognize objects of any size or shape and assisting in the reduction in false alarms brought on by outside noise.
6. Overview of Edge Computing
In edge computing, data from clients are processed at the network’s edge, which is near the data’s original generation point. This is a distributed information technology architecture. Data offer some of the most significant resources for contemporary firms; they not only offer insightful information but also play a crucial role in decision-making for efficient corporate operations. With the right system in place to safeguard data from unwanted access and enable real-time operations from many locations and connected devices, the deluge of data can be handled and regulated [30,31]. It is difficult to manage the data flow when integrating a standard cloud computing network. Edge computing is therefore necessary in cloud networks to guarantee optimal information flow.
7. Materials and Methods
The Raspberry Pi 4 Model B (4 GB) with a camera was used to receive auditory notifications regarding armed threats, and to charge the Raspberry Pi, headphones and a battery bank were utilized. Raspberry Pi OS was picked as the operating system. IoT cloud platforms were used to collect analytics information because of their visual infographic expertise.
7.1. Edge Node
The Python language was chosen for recording computer vision libraries and frameworks, and the Numpy, TensorFlow, Python Imaging Library, and Pi camera libraries, as well as 2230 images from the GitHub dataset, were used, showing different types of weapons. A few samples with different weapons were picked for model training. Figure 3 shows an overview of the model’s training using TensorFlow Version 2.19.0 and Google Colab.
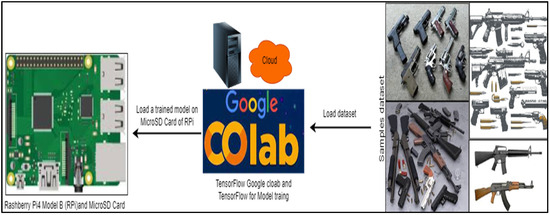
Figure 3.
Overview of model training using TensorFlow and Google Colab.
7.2. Dataset
We utilized the dataset from GitHub: https://github.com/ari-dasci, (accessed on 24 November 2024). Given the rising turmoil, we should equip security cameras with innovative technology. Thus, implementing AI in security cameras to recognize weapons automatically and notify owners is a positive way to implement AI in security. The weapon detection annotation in the Pascal VOC format is present in this dataset. We have chosen the EfficientDet model for weapons identification because it produces a smaller output model file, uses less computational power, and executes algorithms more quickly. An overview of the EfficientDet architecture is shown in Figure 4.
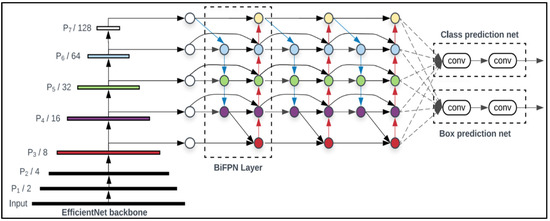
Figure 4.
Overview of the EfficientDet architecture.
With EfficientNet serving as the backbone network, EfficientDet can be thought of as a one-stage detector paradigm. The feature network, known as the bidirectional feature pyramid network (BiFPN), makes use of the level 3–7 features from the backbone network. It continuously performs top-down and bottom-up bidirectional feature fusion, producing fused features. The results and checkpoints are shown in Table 1.

Table 1.
The EfficientDet-Lite results and checkpoints.
EfficientDet-Lite0 has been selected because it is imperative to emphasize safety while offering the fastest item detection speed possible. The following is the general equation for the EfficientDet model’s compound scaling:
where f is a network scaling factor, φ is a number of network variations, β is a width scaling factor, γ is a resolution scaling factor, and α is a depth scaling factor. Scaling equities are used to obtain the BiFPN network’s depth and width:
f = α + β + γ φ φ
W 64 (1.35 = × bifpn φ)
D = + bifpn 3 φ
The following equation is used to scale the box/class prediction network:
D D = = +| | class 3 ⌊φ/3 ⌋
The following scaling equation is used to input the image resolution:
R = + × 512 φ 128
Therefore, compared to the majority of previously examined detectors, EfficientDet enables us to reduce the size of the model file by 4×–9× and requires 13×–42× less floating-point operations per second (FLOPs). Figure 5 shows a flowchart of overview of the weapons detection process.
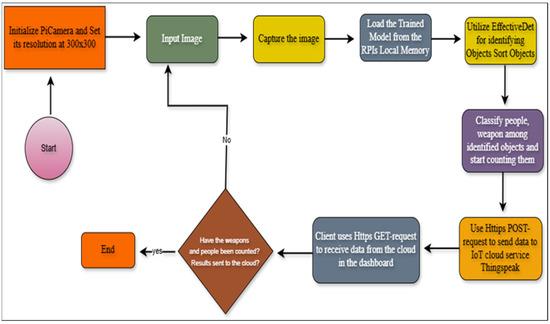
Figure 5.
Flowchart of an overview of the weapons detection process.
Firstly, the resolution of the Pi’s camera was set to 300 × 300 after it had been initialized. After that, an algorithm began using TensorFlow Lite and Google Colab to load a trained model and capture an image. Using that model and the architecture made it possible to identify items in the photographed data. A model was used to count and categorize the sorted items into four categories: human, rifle, pistol (handgun), and knife. Eventually, an HTTP request was used to transfer the outcomes to the IoT cloud platform “Thingspeak”. Subsequently, a subscriber can retrieve results by sending an HTTP GET request. The technology would notify the user audibly through headphones if an armed threat was identified.
8. Conclusions
In this paper, we used computer vision and edge computing, based on the Raspberry Pi, to build a model for detecting weapons such as pistols and rifles. The data have been taken from the Kaggle dataset. The proposed approach successfully overcomes many issues. The web application’s data presentation enables the operator to generate a report. Moreover, one suggestion is to develop an autonomous weapon recognition system that can identify weapons in 1.30 s and operate without an Internet connection. It is proposed that our research should be extended in the future to include the detection of unmanned aerial vehicles, large tanks, and explosive devices. However, there might be problems with detecting quickly moving objects, as well as detecting in areas with bad illumination and image quality, all of which can be resolved with an FPGA and a high-megapixel infrared camera.
Author Contributions
I.A.S.: Writing, editing, Data Collection, Visualization, Formation. N.Z.J.: Reviewing and editing, Supervision, Conceptualization, Editing. R.M.A.U.: Writing, editing, Data Collection, Visualization. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data will be available on request from the first author.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Abdulsalam, Y.S.; Hedabou, M. Security and privacy in cloud computing: Technical review. Futur. Internet 2021, 14, 11. [Google Scholar] [CrossRef]
- Al-Dulaimy, A.; Sharma, Y.; Khan, M.G.; Taheri, J. Introduction to edge computing. In Edge Computing: Models, Technologies and Applications; Institution of Engineering and Technology: London, UK, 2020; pp. 3–25. [Google Scholar]
- Alaqil, R.M.; Alsuhaibani, J.A.; Alhumaidi, B.A.; Alnasser, R.A.; Alotaibi, R.D.; Benhidour, H. Automatic gun detection from images using faster r-cnn. In Proceedings of the 2020 First international conference of smart systems and emerging technologies (SMARTTECH), Riyadh, Saudi Arabia, 3–5 November 2020; pp. 149–154. [Google Scholar]
- Arif, E.; Shahzad, S.K.; Mustafa, R.; Jaffar, M.A.; Iqbal, M.W. Deep Neural Networks for Gun Detection in Public Surveillance. Intell. Autom. Soft Comput. 2022, 32, 909–922. [Google Scholar] [CrossRef]
- Arslan, Y.; Canbolat, H. Performance of deep neural networks in audio surveillance. In Proceedings of the 2018 6th International Conference on Control Engineering & Information Technology (CEIT), Istanbul, Turkey, 25–27 October 2018; pp. 1–5. [Google Scholar]
- Atanov, S.K.; Seitbattalov, Z.Y.; Moldabayeva, Z.S. Development an intelligent task offloading system for edge-cloud computing paradigm. In Proceedings of the 2021 16th International Conference on Electronics Computer and Computation (ICECCO), Kaskelen, Kazakhstan, 25–26 November 2021; pp. 1–6. [Google Scholar]
- Brimzhanova, S.S.; Atanov, S.K.; Khuralay, M.; Kobelekov, K.S.; Gagarina, L.G. Cross-platform compilation of pro-gramming language Golang for Raspberry Pi. In Proceedings of the 5th International Conference on Engineering and MIS, Astana Kazakhstan, 6–8 June 2019; pp. 1–5. [Google Scholar]
- Cao, K.; Liu, Y.; Meng, G.; Sun, Q. An overview on edge computing research. IEEE Access 2020, 8, 85714–85728. [Google Scholar] [CrossRef]
- Castillo, A.; Tabik, S.; Pérez, F.; Olmos, R.; Herrera, F. Brightness guided preprocessing for automatic cold steel weapon detection in surveillance videos with deep learning. Neurocomputing 2019, 330, 151–161. [Google Scholar] [CrossRef]
- Dang, T.-V. Smart home management system with face recognition based on arcface model in deep convolutional neural network. J. Robot. Control. 2022, 3, 754–761. [Google Scholar] [CrossRef]
- Debnath, R.; Bhowmik, M.K. Novel framework for automatic localisation of gun carrying by moving person using various indoor and outdoor mimic and real-time views/Scenes. IET Image Process. 2020, 14, 4663–4675. [Google Scholar] [CrossRef]
- Debnath, R.; Bhowmik, M.K. A comprehensive survey on computer vision based concepts, methodologies, analysis and applications for automatic gun/knife detection. J. Vis. Commun. Image Represent. 2021, 78, 103165. [Google Scholar] [CrossRef]
- Duan, Q.; Wang, S.; Ansari, N. Convergence of networking and cloud/edge computing: Status, challenges, and opportunities. IEEE Netw. 2020, 34, 148–155. [Google Scholar] [CrossRef]
- El Den Mohamed, M.K.; Taha, A.; Zayed, H.H. Automatic gun detection approach for video surveillance. Int. J. Sociotechnol. Knowl. Dev. 2020, 12, 49–66. [Google Scholar] [CrossRef]
- Goenka, A.; Sitara, K. Weapon detection from surveillance images using deep learning. In Proceedings of the 2022 3rd International Conference for Emerging Technology (INCET), Belgaum, India, 27–29 May 2022; pp. 1–6. [Google Scholar]
- González, J.L.S.; Zaccaro, C.; Álvarez-García, J.A.; Morillo, L.M.S.; Caparrini, F.S. Real-time gun detection in CCTV: An open problem. Neural Netw. 2020, 132, 297–308. [Google Scholar] [CrossRef]
- Haq, N.U.; Fraz, M.M.; Hashmi, T.S.; Shahzad, M. Orientation aware weapons detection in visual data: A benchmark dataset. Computing 2022, 104, 2581–2604. [Google Scholar] [CrossRef]
- Hnoohom, N.; Chotivatunyu, P.; Jitpattanakul, A. ACF: An armed cctv footage dataset for enhancing weapon detection. Sensors 2022, 22, 7158. [Google Scholar] [CrossRef] [PubMed]
- Ingle, P.Y.; Kim, Y.-G. Real-time abnormal object detection for video surveillance in smart cities. Sensors 2022, 22, 3862. [Google Scholar] [CrossRef] [PubMed]
- Ismail, M.G.; Tarabay, F.H.; El-Masry, R.; Abd El Ghany, M.; Salem, M.A.M. Smart Cloud-Edge Video Surveillance System. In Proceedings of the 2022 11th International Conference on Modern Circuits and Systems Technologies (MOCAST), Bremen, Germany, 8–10 June 2022; pp. 1–4. [Google Scholar]
- Lamas, A.; Tabik, S.; Montes, A.C.; Pérez-Hernández, F.; García, J.; Olmos, R.; Herrera, F. Human pose estimation for mitigating false negatives in weapon detection in video-surveillance. Neurocomputing 2022, 489, 488–503. [Google Scholar] [CrossRef]
- Nassif, A.B.; Abu Talib, M.; Nasir, Q.; Albadani, H.; Dakalbab, F.M. Machine Learning for Cloud Security: A Systematic Review. IEEE Access 2021, 9, 20717–20735. [Google Scholar] [CrossRef]
- Rahmaniar, W.; Hernawan, A. Real-time human detection using deep learning on embedded platforms: A review. J. Robot. Control 2021, 2, 462–468. [Google Scholar]
- Satyanarayanan, M. The emergence of edge computing. Computer 2017, 50, 30–39. [Google Scholar] [CrossRef]
- Seitbattalov, Z.Y.; Canbolat, H.; Moldabayeva, Z.S.; Kyzyrkanov, A.E. An Intelligent Automatic Number Plate Recognition System Based on Computer Vision and Edge Computing. In Proceedings of the 2022 International Conference on Smart Information Systems and Technologies (SIST), Nur-Sultan, Kazakhstan, 28–30 April 2022; pp. 1–5. [Google Scholar]
- Shah, I.A.; Jhanjhi, N.Z.; Brohi, S.N. IoT Smart Healthcare Security Challenges and Solutions. Advances in Computational Intelligence for the Healthcare Industry 4.0. In Advances in Computational Intelligence for the Healthcare Industry 4.0; IGI Global: Hershey, PA, USA, 2024. [Google Scholar]
- Shah, I.A.; Jhanjhi, N.Z.; Brohi, S.N. Use of AI-Based Drones in Smart Cities. Cybersecurity Issues and Challenges in the Drone Industry. In Cybersecurity Issues and Challenges in the Drone Industry; IGI Global: Hershey, PA, USA, 2024. [Google Scholar]
- Shah, I.A.; Jhanjhi, N.Z.; Rajper, S. Use of Deep Learning Applications for Drone Technology. In Cybersecurity Issues and Challenges in the Drone Industry; IGI Global: Hershey, PA, USA, 2024. [Google Scholar]
- Sharma, A.; Mullana, M.M.U. Emerging Trends in Safety Issues in Cloud the Potentials of Threat Model. Int. J. Future Revolut. Comput. Sci. Commun. Eng. 2020, 3, 260–263. [Google Scholar]
- Veranyurt, O.; Sakar, C.O. Hand-gun detection in images with transfer learning-based convolutional neural networks. In Proceedings of the 2020 28th Signal Processing and Communications Applications Conference (SIU), Gaziantep, Turkey, 5–7 October 2020; pp. 1–4. [Google Scholar]
- Wu, R.; Li, J.; Ablan, C.; Guan, S.; Yao, J. Preprocessing Techniques’ Effect On Overfitting for VGG16 Fast-RCNN Pistol Detection. Int. J. Comput. Appl. 2021, 28, 1. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).