Secure Internet of Things Device with Single-Channel Communication for Resource-Constrained Applications †
Abstract
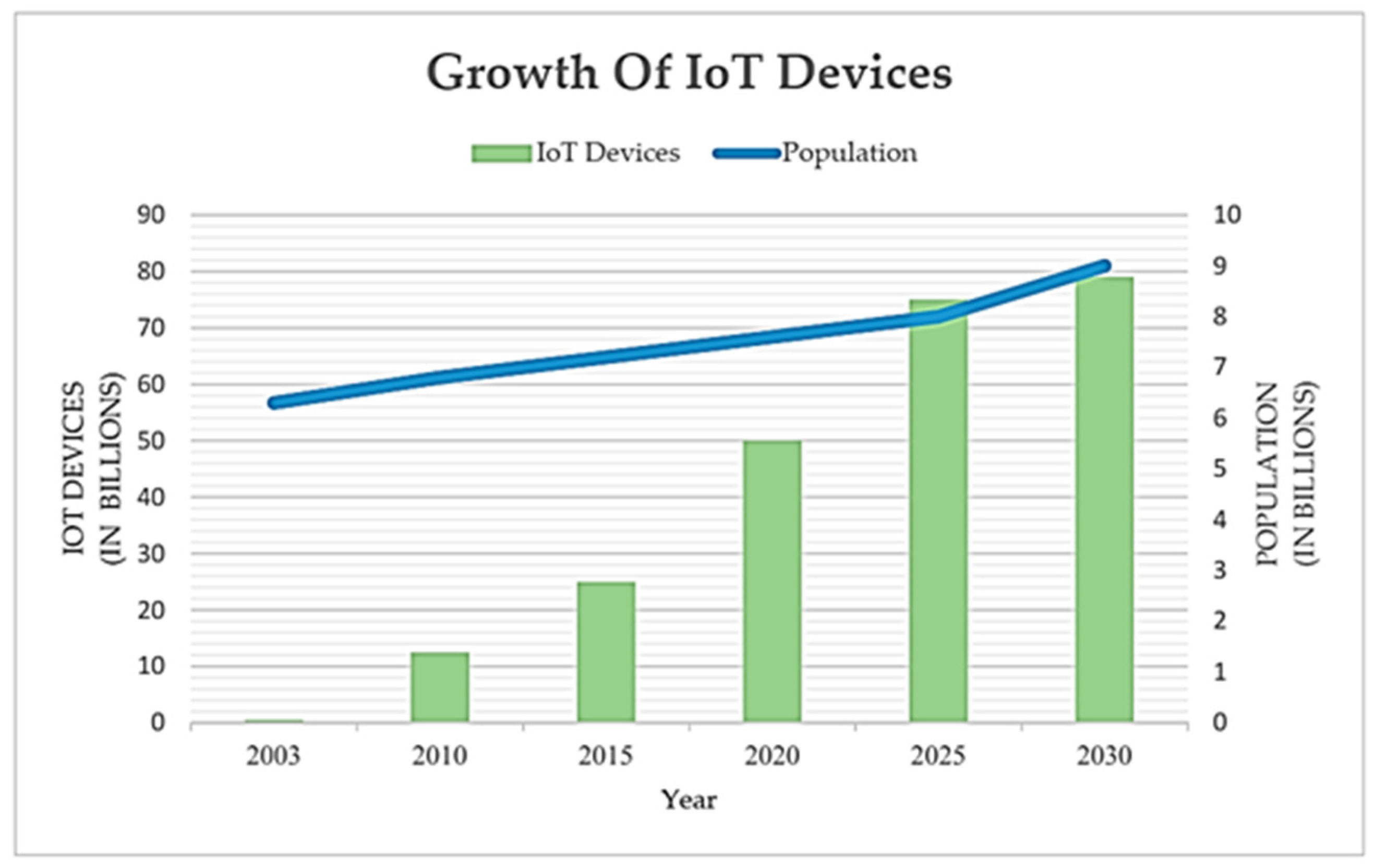
1. Introduction
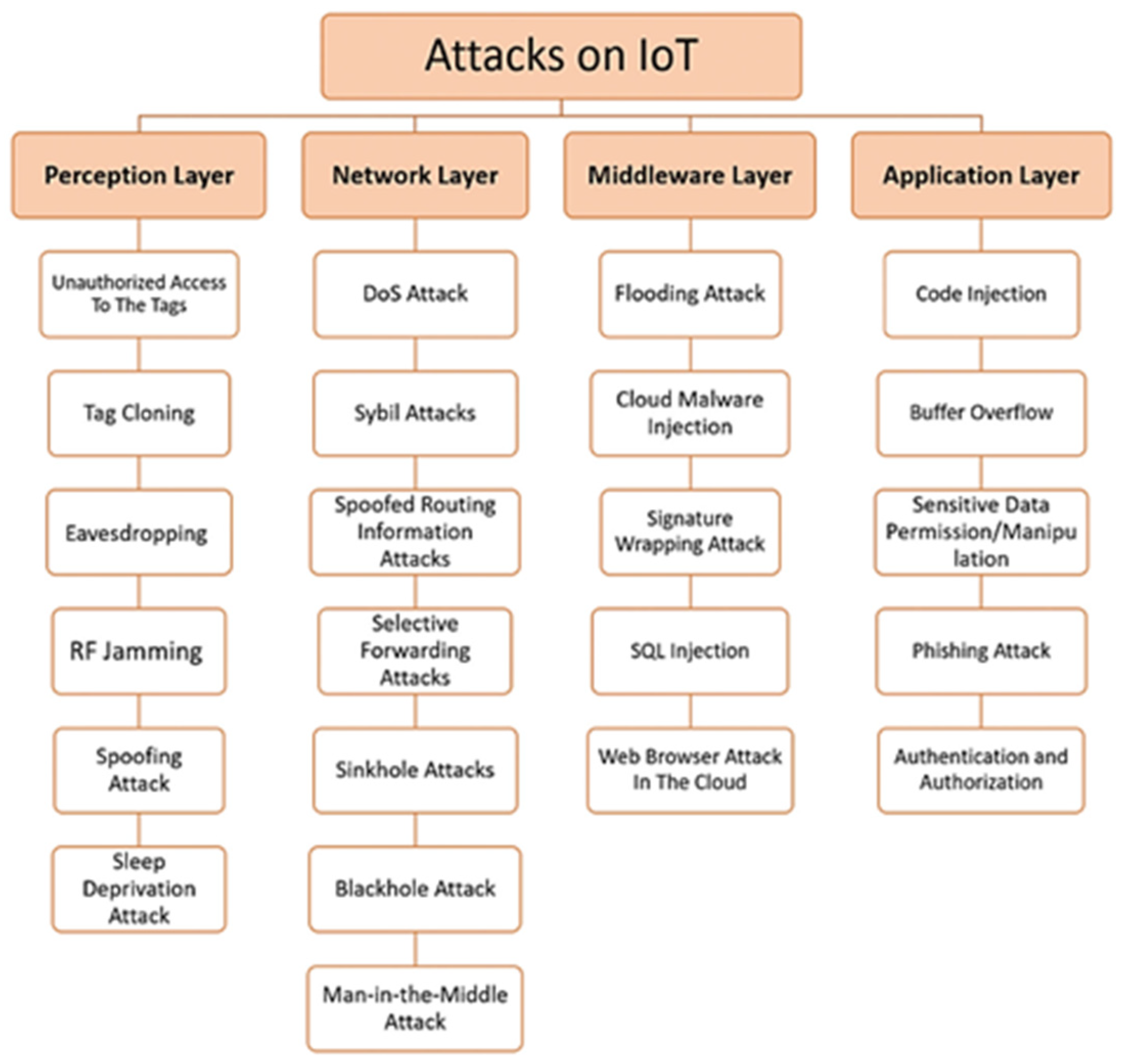
2. Literature Review
3. Proposed System
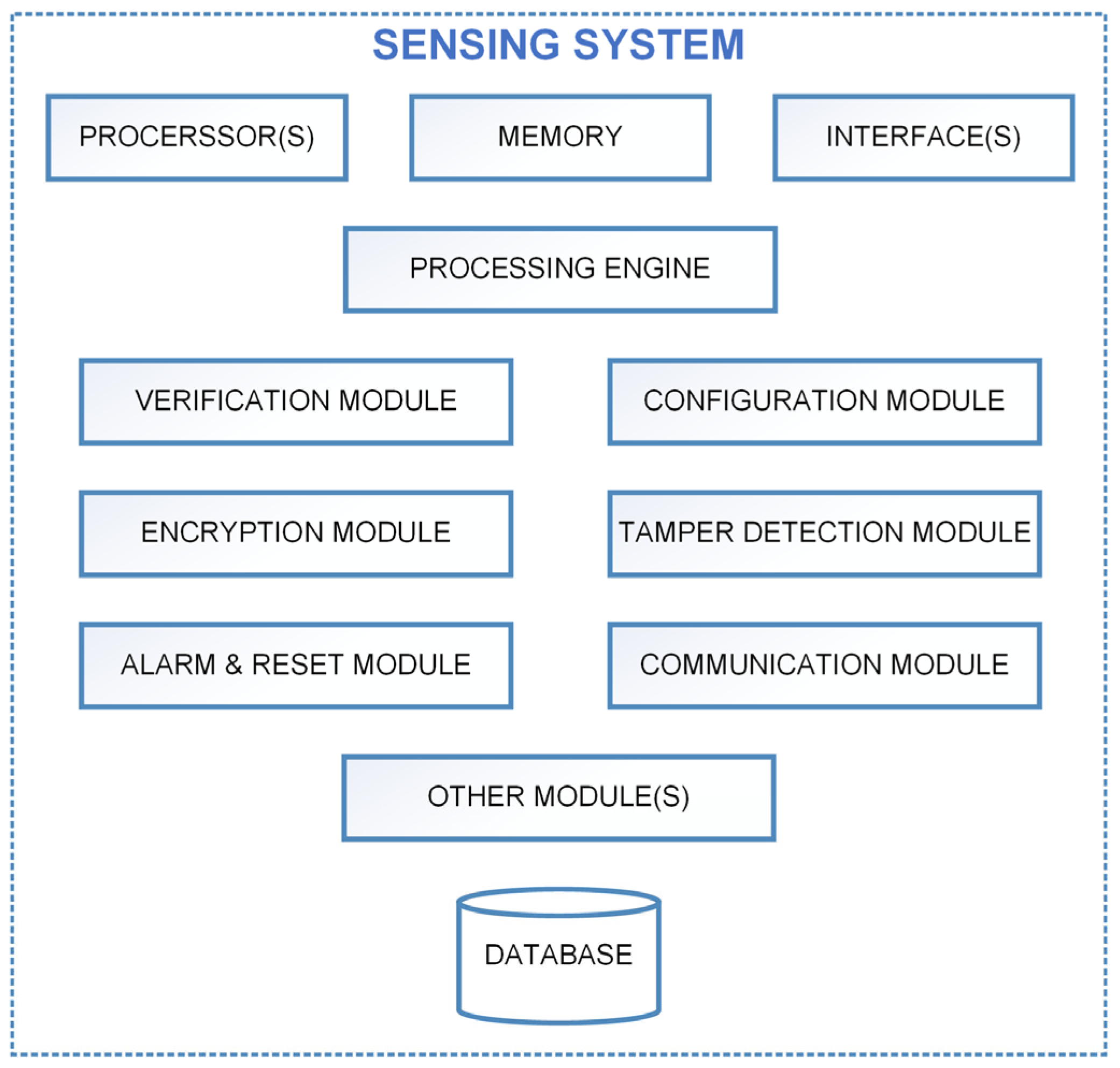
3.1. System Architecture
- Sensing Device: It is the central element of the IoT system, responsible for sensing and collecting data from its environment. It is connected to a processor which performs necessary operations on the data sensed by it.
- Memory: The memory stores the processor-executable instructions that dictate the system’s behavior. It also temporarily stores the sensor data before they are encrypted and transmitted.
- Custom Port and Master Device: The sensing device interfaces with a master device through a custom UART port. The custom port integrates an embedded authentication protocol, utilizing cryptographic handshakes to prevent unauthorized connections, ensuring high security in resource-constrained environments. The master device plays a crucial role in configuring the sensing device and sending the control signals. A 115,200 bps data rate is used, as it balances the need for real-time data transfer with minimal processing overhead, ensuring consistent performance in constrained environments
- Pressure-Sealed Casing: The IP65 casing houses the sensing device and is equipped with a pressure monitoring sensor to detect any unauthorized attempts to open it. A drop in the internal pressure indicates tampering, prompting the system to initiate security protocols.
- One-Way Communication Channel: To transmit data from the sensing device to a designated source address, the system utilizes a one-way communication channel and LoRa (Long Range) communication module. This allows only data transmission, and prevents any inbound communication attempts that could be exploited by attackers.
- Processor: It is the main control unit of the system and executes all the instructions stored in the memory for various tasks. It is also responsible for the authentication of the master device, the processing of the control signal, the encryption of data to be transmitted, and the monitoring of the pressure within the sealed casing to detect tampering attempts.
3.2. Methodology
- Verification of the Master Device: The process begins with the docking of a master device to the custom port of the sensing device. The custom port ensures that only compatible devices can connect. Upon docking, the custom port authentication and handshake protocol is initiated, verifying the identity of the master device. The UART protocol is modified to include an additional control byte in each data packet, which serves as a unique signature to disambiguate the communication within the system. This step is crucial in preventing unauthorized devices from accessing the sensing device or from initiating man-in-the middle attacks.
- Reception of Control Signals: Once the master device is authenticated, the processor receives control signals from it. These signals may include configuration instructions or commands for the sensing device.
- Data Encryption and Transmission: The sensed data is processed by the processor and encrypted using the AES-128 encryption algorithm before the transmission, to prevent unauthorized access. This is achieved by a one-way communication channel, which restricts only the transmission of data and not its reception thereby reducing the risk of remote attacks.
- Tampering Detection: The system will continuously monitor the pressure within the sealed casing of the sensor system. If any pressure drop is detected, a tampering detection mechanism is activated, and a pre-defined series of steps, as a security measure, is initiated.
- Security Response: When tampering is detected, an alarm is triggered by the system to alert the user or system administrator. At the same time, the processor within the sensor system initiates a reset of the sensing device, thereby erasing all stored data and returning the device to its original factory settings. This ensures that sensitive data are always protected, even in the event of a physical security breach of the system.
- Post-event Handling: Once the device has been reset, it can only be reconfigured by an authorized master device, which again undergoes the previous steps of verification. This re-initialization process makes sure that the device is again secured and that no residual vulnerabilities from the previous tampered state are carried over.
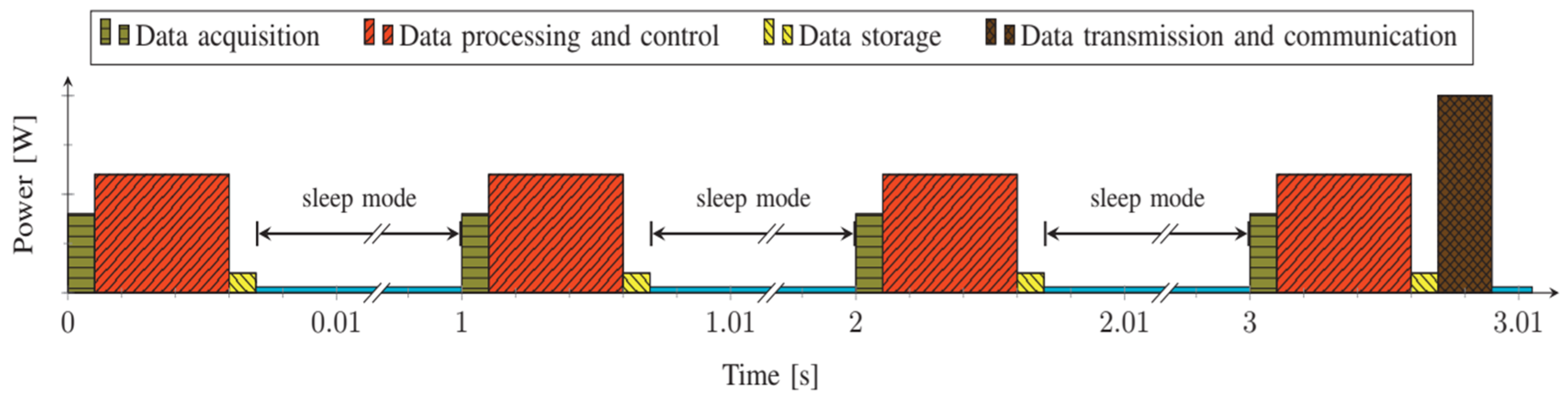
4. Discussion
5. Conclusions
6. Patents
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Gupta, B.B.; Quamara, M. An overview of Internet of Things (IoT): Architectural aspects, challenges, and protocols. Concurr. Comput. Pract. Exp. 2020, 32, e4946. [Google Scholar] [CrossRef]
- Anand, P.; Singh, Y.; Selwal, A.; Singh, P.K.; Felseghi, R.A.; Raboaca, M.S. Iovt: Internet of vulnerable things? Threat architecture, attack surfaces, and vulnerabilities in internet of things and its applications towards smart grids. Energies 2020, 13, 4813. [Google Scholar] [CrossRef]
- Siwakoti, Y.R.; Bhurtel, M.; Rawat, D.B.; Oest, A.; Johnson, R. Advances in IoT security: Vulnerabilities, enabled criminal services, attacks, and countermeasures. IEEE Internet Things J. 2023, 10, 11224–11239. [Google Scholar] [CrossRef]
- Alqarawi, G.; Alkhalifah, B.; Alharbi, N.; El Khediri, S. Internet-of-things security and vulnerabilities: Case study. J. Appl. Secur. Res. 2023, 18, 559–575. [Google Scholar] [CrossRef]
- Chen, K.; Zhang, S.; Li, Z.; Zhang, Y.; Deng, Q.; Ray, S.; Jin, Y. Internet-of-things security and vulnerabilities: Taxonomy, challenges, and practice. J. Hardw. Syst. Secur. 2018, 2, 97–110. [Google Scholar] [CrossRef]
- Mahbub, M. Progressive researches on IoT security: An exhaustive analysis from the perspective of protocols, vulnerabilities, and preemptive architectonics. J. Netw. Comput. Appl. 2020, 168, 102761. [Google Scholar] [CrossRef]
- Imdad, M.; Jacob, D.W.; Mahdin, H.; Baharum, Z.; Shaharudin, S.M.; Azmi, M.S. Internet of things (IoT); security requirements, attacks and counter measures. Indones. J. Electr. Eng. Comput. Sci. 2020, 18, 1520–1530. [Google Scholar]
- Robles, R.; Endencio-Robles, D. State of internet of things (IoT) security attacks, vulnerabilities and solutions. Comput. Rev. J. 2019, 3, 255–263. [Google Scholar]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A survey on IoT security: Application areas, security threats, and solution architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Rahimi, H.; Zibaeenejad, A.; Rajabzadeh, P.; Safavi, A.A. On the security of the 5G-IoT architecture. In Proceedings of the International Conference on Smart Cities and Internet of Things, Mashhad, Iran, 26–27 September 2018; pp. 1–8. [Google Scholar]
- Kamble, A.; Bhutad, S. Survey on Internet of Things (IoT) security issues & solutions. In Proceedings of the 2018 2nd International Conference on Inventive Systems and Control (ICISC), Coimbatore, India, 19–20 January 2018; pp. 307–312. [Google Scholar]
- Kumar, S.A.; Vealey, T.; Srivastava, H. Security in internet of things: Challenges, solutions and future directions. In Proceedings of the 2016 49th Hawaii International Conference on System Sciences (HICSS), Koloa, HI, USA, 5–8 January 2016; pp. 5772–5781. [Google Scholar]
- Muhammad, F.; Anjum, W.; Mazhar, K.S. A critical analysis on the security concerns of internet of things (IoT). Int. J. Comput. Appl. 2015, 111, 1–6. [Google Scholar]
- Khattak, H.A.; Shah, M.A.; Khan, S.; Ali, I.; Imran, M. Perception layer security in Internet of Things. Future Gener. Comput. Syst. 2019, 100, 144–164. [Google Scholar] [CrossRef]
- Tuan, T.A.; Long, H.V.; Son, L.H.; Kumar, R.; Priyadarshini, I.; Son, N.T.K. Performance evaluation of Botnet DDoS attack detection using machine learning. Evol. Intell. 2020, 13, 283–294. [Google Scholar] [CrossRef]
- Hossain, M.M.; Fotouhi, M.; Hasan, R. Towards an analysis of security issues, challenges, and open problems in the internet of things. In Proceedings of the 2015 IEEE World Congress on Services, New York, NY, USA, 17 August 2015; pp. 21–28. [Google Scholar]
- Vishwakarma, R.; Jain, A.K. A survey of DDoS attacking techniques and defence mechanisms in the IoT network. Telecommun. Syst. 2020, 73, 3–25. [Google Scholar] [CrossRef]
- Gavra, V.-D.; Dobra, I.-M.; Pop, O.A. A survey on threats and security solutions for IoT. In Proceedings of the 2020 43rd International Spring Seminar on Electronics Technology (ISSE), Demanovska Valley, Slovakia, 14–15 May 2020; pp. 1–5. [Google Scholar]
- Zhao, W.; Yang, S.; Luo, X. On threat analysis of IoT-based systems: A survey. In Proceedings of the 2020 IEEE International Conference on Smart Internet of Things (SmartIoT), Beijing, China, 14–16 August 2020; pp. 205–212. [Google Scholar]
- Obaidat, M.A.; Obeidat, S.; Holst, J.; Al Hayajneh, A.; Brown, J. A comprehensive and systematic survey on the internet of things: Security and privacy challenges, security frameworks, enabling technologies, threats, vulnerabilities and countermeasures. Computers 2020, 9, 44. [Google Scholar] [CrossRef]
- Grammatikis, P.I.R.; Sarigiannidis, P.G.; Moscholios, I.D. Securing the Internet of Things: Challenges, threats and solutions. Internet Things 2019, 5, 41–70. [Google Scholar] [CrossRef]
- Ghasemi, M.; Saadaat, M.; Ghollasi, O. Threats of social engineering attacks against security of Internet of Things (IoT). In Fundamental Research in Electrical Engineering: The Selected Papers of the First International Conference on Fundamental Research in Electrical Engineering; Springer: Singapore, 2019; pp. 957–968. [Google Scholar]
- Henkel, J.; Pagani, S.; Amrouch, H.; Bauer, L.; Samie, F. Ultra-low power and dependability for IoT devices (Invited paper for IoT technologies). In Proceedings of the 2017 Design, Automation & Test in Europe Conference & Exhibition (DATE), Lausanne, Switzerland, 27–31 May 2017; pp. 954–959. [Google Scholar]
- Prasad, A.; Chawda, P. Power management factors and techniques for IoT design devices. In Proceedings of the 2018 19th International Symposium on Quality Electronic Design (ISQED), Santa Clara, CA, USA, 13–14 March 2018; pp. 364–369. [Google Scholar]
- Silva, A.; Liu, M.; Moghaddam, M. Power-Management Techniques for Wireless Sensor Networks and Similar Low-Power Communication Devices Based on Nonrechargeable Batteries. J. Comput. Netw. Commun. 2012, 2012, 757291. [Google Scholar] [CrossRef]


| Attack Vector | Description | System Response |
|---|---|---|
| Physical Tampering | Attempts to open or manipulate the device physically. | Device is disabled, all stored data is erased, and an alert is triggered. |
| DDoS Attacks | Distributed-denial-of-service attacks to overwhelm the device with network traffic. | Device remains unaffected, as the one-way communication channel does not allow inbound communication. |
| Device Signal Interference | Attempts to jam or interfere with the device’s wireless signals. | No impact, as the device does not use a wireless receiver for data reception, only one-way transmission. |
| Device Spoofing | An attacker attempts to mimic the device to impersonate its communication. |
|
| Operating Mode | MCU | Sensors | Radio |
|---|---|---|---|
| Active (regular operation) | 5 mW | 30 mW | 350 mW |
| Inactive (power saving) | 2 µW | 5 µW | 20 µW |
| Inactive (power gating) | 2 µW | 1 µW | 2 µW |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gupta, A.; Sawhney, S.; Ahmed, S. Secure Internet of Things Device with Single-Channel Communication for Resource-Constrained Applications. Eng. Proc. 2024, 78, 9. https://doi.org/10.3390/engproc2024078009
Gupta A, Sawhney S, Ahmed S. Secure Internet of Things Device with Single-Channel Communication for Resource-Constrained Applications. Engineering Proceedings. 2024; 78(1):9. https://doi.org/10.3390/engproc2024078009
Chicago/Turabian StyleGupta, Ankur, Sahil Sawhney, and Suhaib Ahmed. 2024. "Secure Internet of Things Device with Single-Channel Communication for Resource-Constrained Applications" Engineering Proceedings 78, no. 1: 9. https://doi.org/10.3390/engproc2024078009
APA StyleGupta, A., Sawhney, S., & Ahmed, S. (2024). Secure Internet of Things Device with Single-Channel Communication for Resource-Constrained Applications. Engineering Proceedings, 78(1), 9. https://doi.org/10.3390/engproc2024078009