Detection of DoS Attacks in an IoT Environment with MQTT Protocol Based on Intelligent Binary Classifiers †
Abstract
:1. Introduction
2. Materials and Methods
2.1. Dataset Description
2.2. Used Techniques
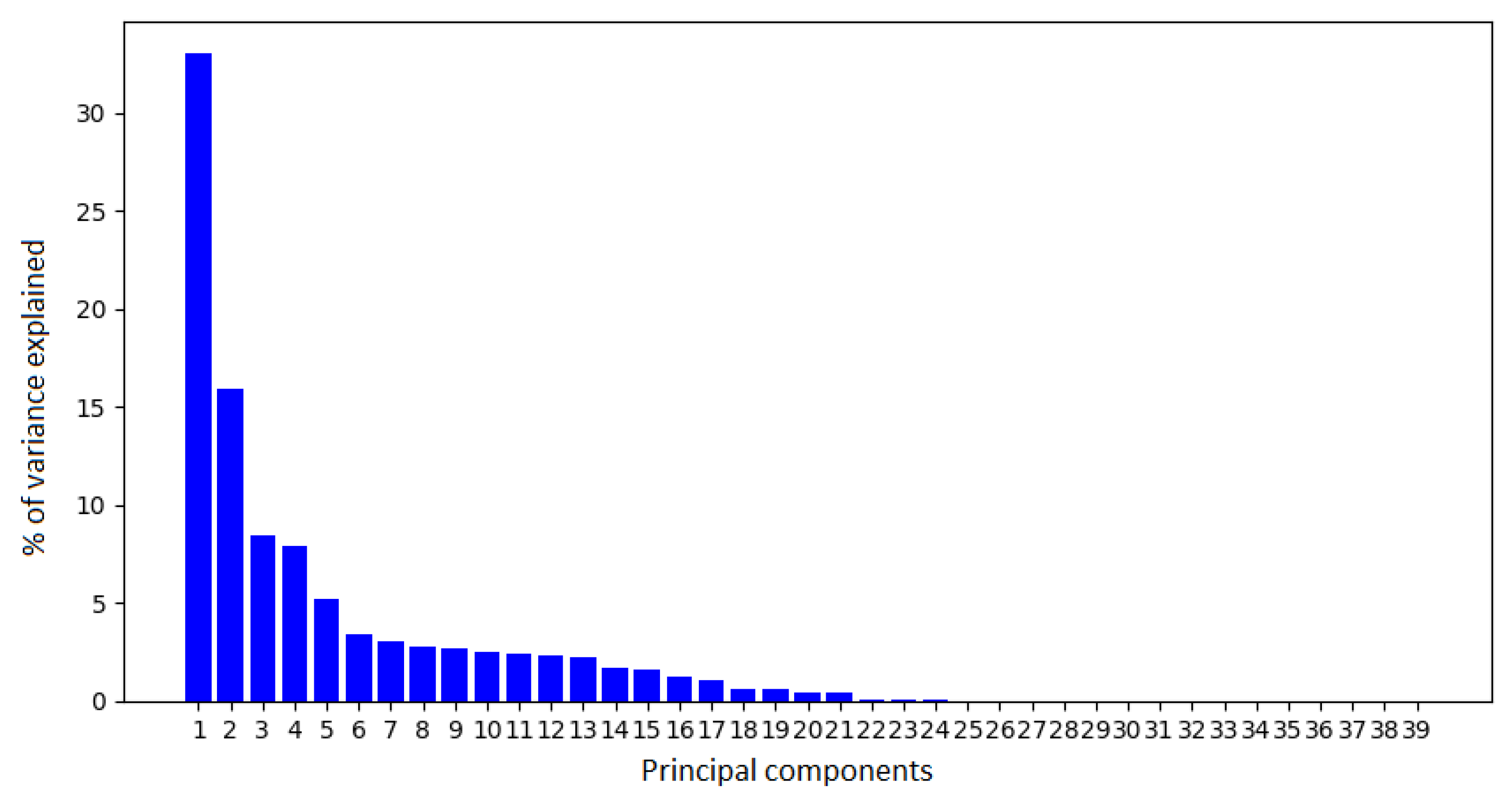
2.2.1. Principal Component Analysis
2.2.2. Classification Techniques
Logistic Regression
K Nearest Neighbours
Decision Trees
Deep Neural Networks
3. Experiments and Results
3.1. Experimental Setup
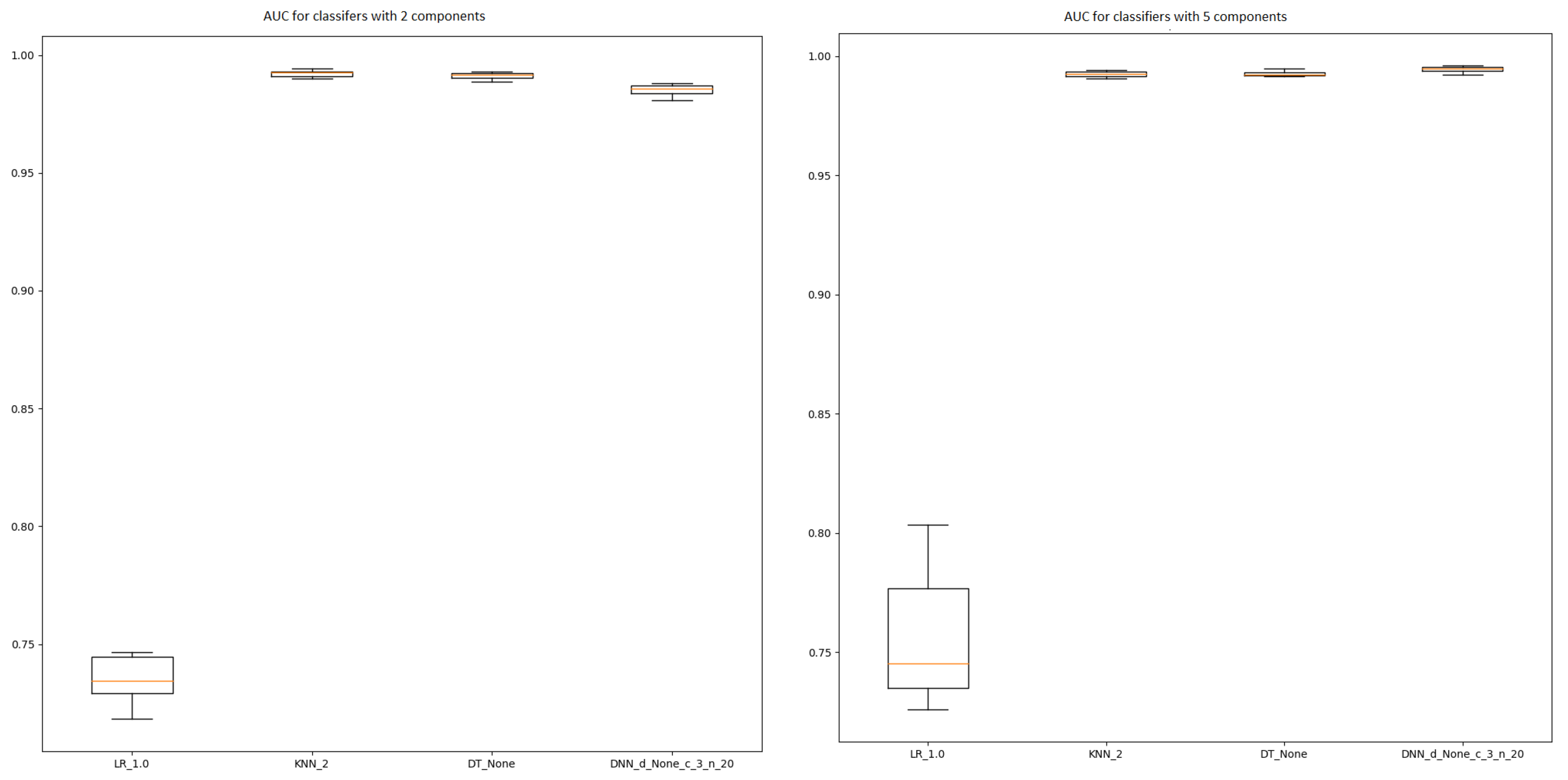
3.2. Results
4. Conclusions
Acknowledgments
References
- Lee, J.; Kao, A. Industry 4.0 Factory in Big Data Environment. tec. News. HARTING’s Technol. Newsl. 2014, 26, 8–9. [Google Scholar]
- Zhang, X.; Upton, O.; Beebe, N.L.; Choo, K.K.R. IoT Botnet Forensics: A Comprehensive Digital Forensic Case Study on Mirai Botnet Servers. Forensic Sci. Int. Digit. Investig. 2020, 32, 300926. [Google Scholar] [CrossRef]
- Liu, J.; Kantarci, B.; Adams, C. Machine learning-driven intrusion detection for Contiki-NG-based IoT networks exposed to NSL-KDD dataset. In Proceedings of the 2nd ACM Workshop on Wireless Security and Machine Learning, Linz, Austria, 13 July 2020; pp. 25–30. [Google Scholar]
- Martinez, A.M.; Kak, A.C. Pca versus lda. IEEE Trans. Pattern Anal. Mach. Intell. 2001, 23, 228–233. [Google Scholar] [CrossRef] [Green Version]
- Dreiseitl, S.; Ohno-Machado, L. Logistic regression and artificial neural network classification models: A methodology review. J. Biomed. Informat. 2002, 35, 5–6. [Google Scholar] [CrossRef] [Green Version]
- Jove, E.; Gonzalez-Cava, J.M.; Casteleiro-Roca, J.L.; Méndez-Pérez, J.A.; Reboso-Morales, J.A.; Pérez-Castelo, F.J.; de Cos Juez, F.J.; Calvo-Rolle, J.L. Modelling the hypnotic patient response in general anaesthesia using intelligent models. Log. J. IGPL 2019, 27, 189–201. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Michelena, Á.; Zayas-Gato, F.; Jove, E.; Calvo-Rolle, J.L. Detection of DoS Attacks in an IoT Environment with MQTT Protocol Based on Intelligent Binary Classifiers. Eng. Proc. 2021, 7, 16. https://doi.org/10.3390/engproc2021007016
Michelena Á, Zayas-Gato F, Jove E, Calvo-Rolle JL. Detection of DoS Attacks in an IoT Environment with MQTT Protocol Based on Intelligent Binary Classifiers. Engineering Proceedings. 2021; 7(1):16. https://doi.org/10.3390/engproc2021007016
Chicago/Turabian StyleMichelena, Álvaro, Francisco Zayas-Gato, Esteban Jove, and José Luis Calvo-Rolle. 2021. "Detection of DoS Attacks in an IoT Environment with MQTT Protocol Based on Intelligent Binary Classifiers" Engineering Proceedings 7, no. 1: 16. https://doi.org/10.3390/engproc2021007016
APA StyleMichelena, Á., Zayas-Gato, F., Jove, E., & Calvo-Rolle, J. L. (2021). Detection of DoS Attacks in an IoT Environment with MQTT Protocol Based on Intelligent Binary Classifiers. Engineering Proceedings, 7(1), 16. https://doi.org/10.3390/engproc2021007016








