Watermark Embedding Scheme with Variance of Chromatic Components †
Abstract
1. Introduction
2. Methods
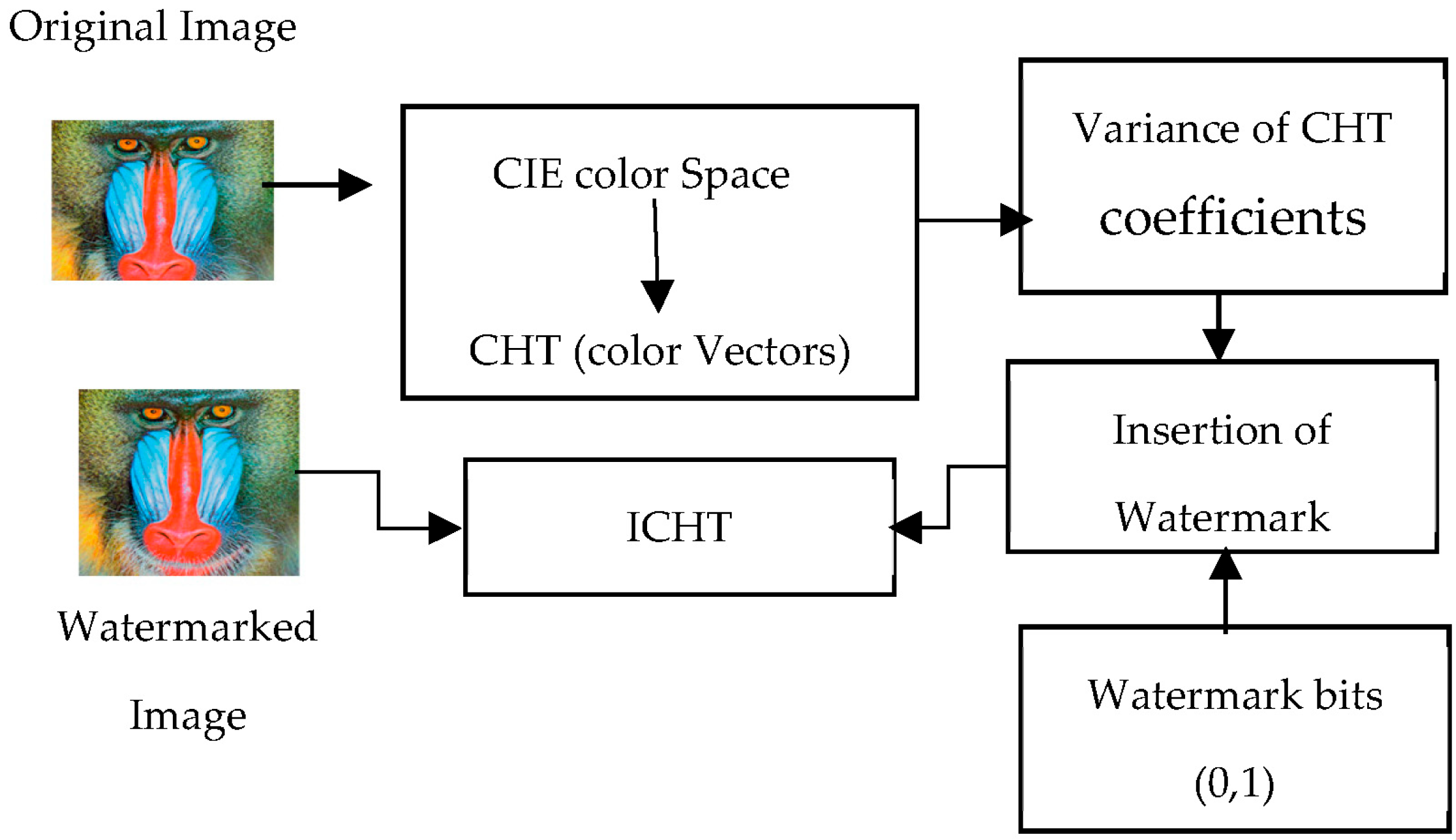
2.1. Steps of the Embedding Scheme
- Converting color images into international commission on illumination (CIE) color spaces, such as Luv and La*b*;
- Dividing images into 8 × 8 blocks;
- Transforming the chromatic components into sequency domain;
- Calculating the variance of the sequency domain coefficients;
- Setting the threshold value for the variance;
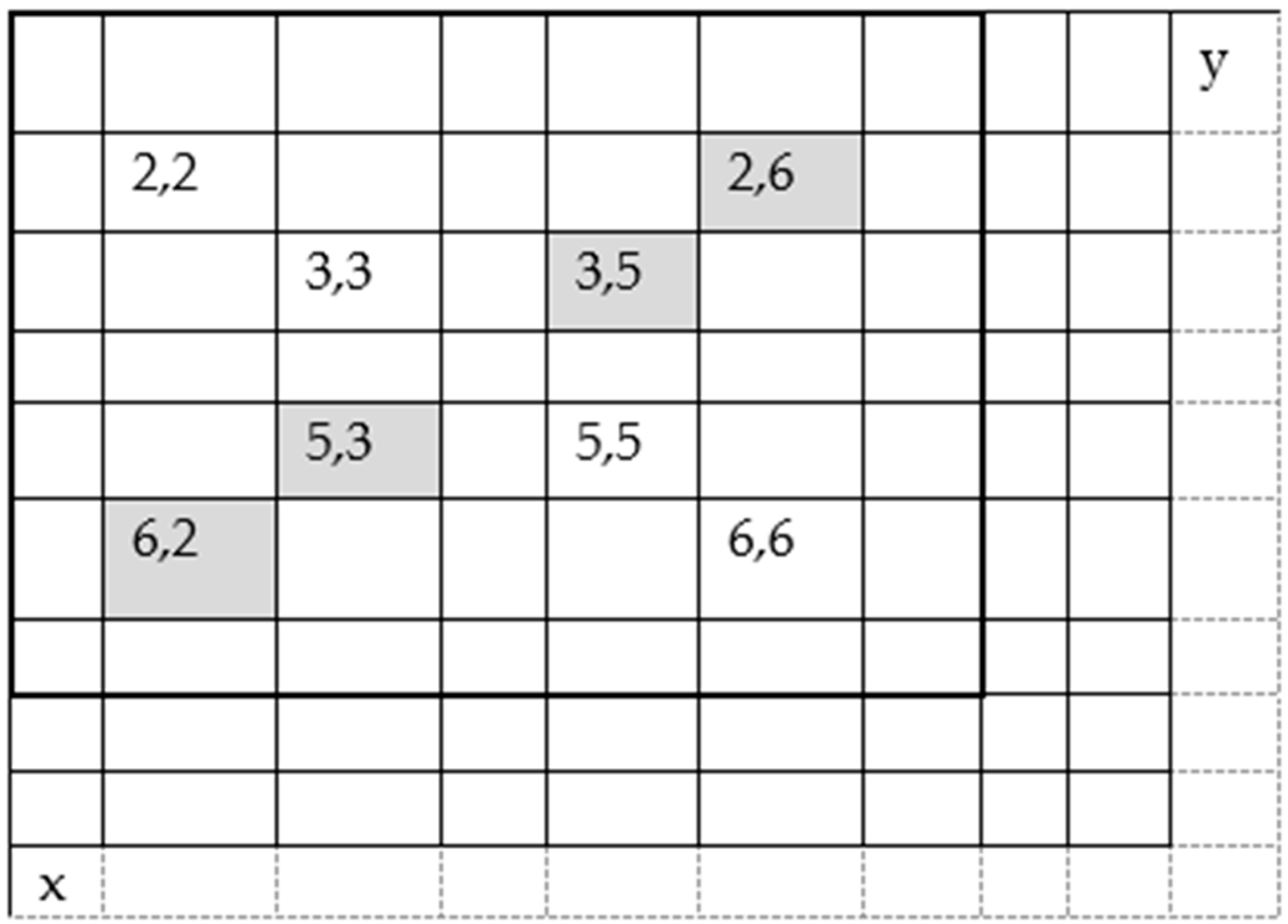
- Selecting the watermark coefficients from the spatio-chromatic coefficients on the bases of variance as shown in Figure 2;
- Generating the watermark bits zero and one;
- Inserting the watermark into the host image according to binary bits and variance;
- Taking inverse transforms of the watermarked image;
- Converting into an RGB image.
2.2. Complex Hadamard Transform
2.2.1. Sequency-Ordered CHT
2.2.2. Conjugate Symmetric SCHT
3. Embedding Process
4. Decoding Process
5. Discrete Cosine Transform
- Read the actual image and divide it into 8 by 8 blocks that do not overlap;
- Each non-overlapping block’s forward DCT should be calculated;
- The highest coefficient selection criteria and HVS block selection criteria are applied;
- Add a secret image to the relevant frequency coefficient;
- Each block undergoes an inverse DCT transformation.
6. Result and Discussion
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Hernandez, J.R.; Amado, M.; Perez-Gonzalez, F. DCT-domain watermarking techniques for still images: Detector performance analysis and a new structure. IEEE Trans. Image Process. 2000, 9, 55–68. [Google Scholar] [CrossRef] [PubMed]
- Molina, J.; Ponomaryov, V.; Reyes, R.; Sadovnychiy, S.; Cruz, C. Watermarking Framework for Authentication and Self-recovery of Tampered Colour Images. IEEE Lat. Am. Trans. 2020, 18, 631–638. [Google Scholar] [CrossRef]
- Shen, X.; Ni, Z.; Yang, W.; Zhang, X.; Wang, S.; Kwong, S. Just Noticeable Distortion Profile Inference: A Patch-Level Structural Visibility Learning Approach. IEEE Trans. Image Process. 2021, 30, 26–38. [Google Scholar] [CrossRef] [PubMed]
- Gong, Q.; Wang, Y.; Yan, X.; Liu, L. Efficient and Lossless Polynomial-Based Secret Image Sharing for Color Images. IEEE Access 2019, 7, 113216–113222. [Google Scholar] [CrossRef]
- Su, Q.; Liu, D.; Yuan, Z.; Wang, G.; Zhang, X.; Chen, B.; Yao, T. New Rapid and Robust Color Image Watermarking Technique in Spatial Domain. IEEE Access 2019, 7, 30398–30409. [Google Scholar] [CrossRef]
- Xiong, X. Novel Scheme of Reversible Watermarking with a Complementary Embedding Strategy. IEEE Access 2019, 7, 136592–136603. [Google Scholar] [CrossRef]
- Liu, Y. On the Concatenated Transmission Scheme with the Low-Complexity Symbol-Level Watermark Decoder for Recovering the Synchronization. IEEE Access 2019, 7, 160927–160933. [Google Scholar] [CrossRef]
- Solachidis, V.; Pitas, I. Watermarking polygonal lines using Fourier descriptors. IEEE Comput. Graph. Appl. 2004, 24, 44–51. [Google Scholar] [CrossRef] [PubMed]
- Li, D.; Zhang, C.; Liu, H.; Su, J.; Tan, X.; Liu, Q.; Liao, G. A Fast Cross-Range Scaling Algorithm for ISAR Images Based on the 2-D Discrete Wavelet Transform and Pseudopolar Fourier Transform. IEEE Trans. Geosci. Remote Sens. 2019, 57, 4231–4245. [Google Scholar] [CrossRef]
- Lee, G.; Choe, Y. Image Compression Based on a Partially Rotated Discrete Cosine Transform with a Principal Orientation. IEEE Access 2021, 9, 101773–101786. [Google Scholar] [CrossRef]
- Zheng, P.; Huang, J. Efficient Encrypted Images Filtering and Transform Coding with Walsh-Hadamard Transform and Parallelization. IEEE Trans. Image Process. 2018, 27, 2541–2556. [Google Scholar] [CrossRef] [PubMed]
- Wu, J.; Wu, F.; Dong, Z.; Song, K.; Kong, Y.; Senhadji, L.; Shu, H. Fast Gray Code Kernel Algorithm for the Sliding Conjugate Symmetric Sequency-Ordered Complex Hadamard Transform. IEEE Access 2018, 6, 56029–56045. [Google Scholar] [CrossRef]
- Aung, A.; Ng, B.P.; Rahardja, S. Sequency-Ordered Complex Hadamard Transform: Properties, Computational Complexity and Applications. IEEE Trans. Signal Process. 2008, 56, 3562–3571. [Google Scholar] [CrossRef]
- Wu, J.; Wang, L.; Yang, G.; Senhadji, L.; Luo, L.; Shu, H. Sliding Conjugate Symmetric Sequency-Ordered Complex Hadamard Transform: Fast Algorithm and Applications. IEEE Trans. Circuits Syst. I Regul. Pap. 2012, 59, 1321–1334. [Google Scholar] [CrossRef]
- Perez-Daniel, K.R.; Garcia-Ugalde, F.; Sanchez, V. Watermarking of HDR Images in the Spatial Domain with HVS-Imperceptibility. IEEE Access 2020, 8, 156801–156817. [Google Scholar] [CrossRef]
- Bae, S.; Kim, M. A Novel Generalized DCT-Based JND Profile Based on an Elaborate CM-JND Model for Variable Block-Sized Transforms in Monochrome Images. IEEE Trans. Image Process. 2014, 23, 3227–3240. [Google Scholar] [PubMed]
- Seo, S.; Ki, S.; Kim, M. A Novel Just-Noticeable-Difference-Based Saliency-Channel Attention Residual Network for Full-Reference Image Quality Predictions. IEEE Trans. Circuits Syst. Video Technol. 2021, 31, 2602–2616. [Google Scholar] [CrossRef]
- Khan, M.F.; Monir, S.M.; Naseem, I.; Khan, B.M. Adaptive just-noticeable difference profile for image hashing. Comput. Electr. Eng. 2021, 90, 106967. [Google Scholar] [CrossRef]
- Guoqing, X.; Rongyan, Z. Shape description and retrieval using Conjugate Symmetric Sequency-Ordered Complex Hadamard Transform. In Proceedings of the 2015 12th International Computer Conference on Wavelet Active Media Technology and Information Processing (ICCWAMTIP), Chengdu, China, 18–20 December 2015; IEEE: New York, NY, USA; pp. 330–333. [Google Scholar]
- Aung, A.; Ng, B.P.; Rahardja, S. Conjugate Symmetric Sequency-Ordered Complex Hadamard Transform. IEEE Trans. Signal Process. 2009, 57, 2582–2593. [Google Scholar] [CrossRef]
- Joseph, H.; Rajan, B.K. Image Security Enhancement using DCT & DWT Watermarking Technique. In Proceedings of the 2020 International Conference on Communication and Signal Processing (ICCSP), Chennai, India, 28–30 July 2020; IEEE: New York, NY, USA; pp. 0940–0945. [Google Scholar]


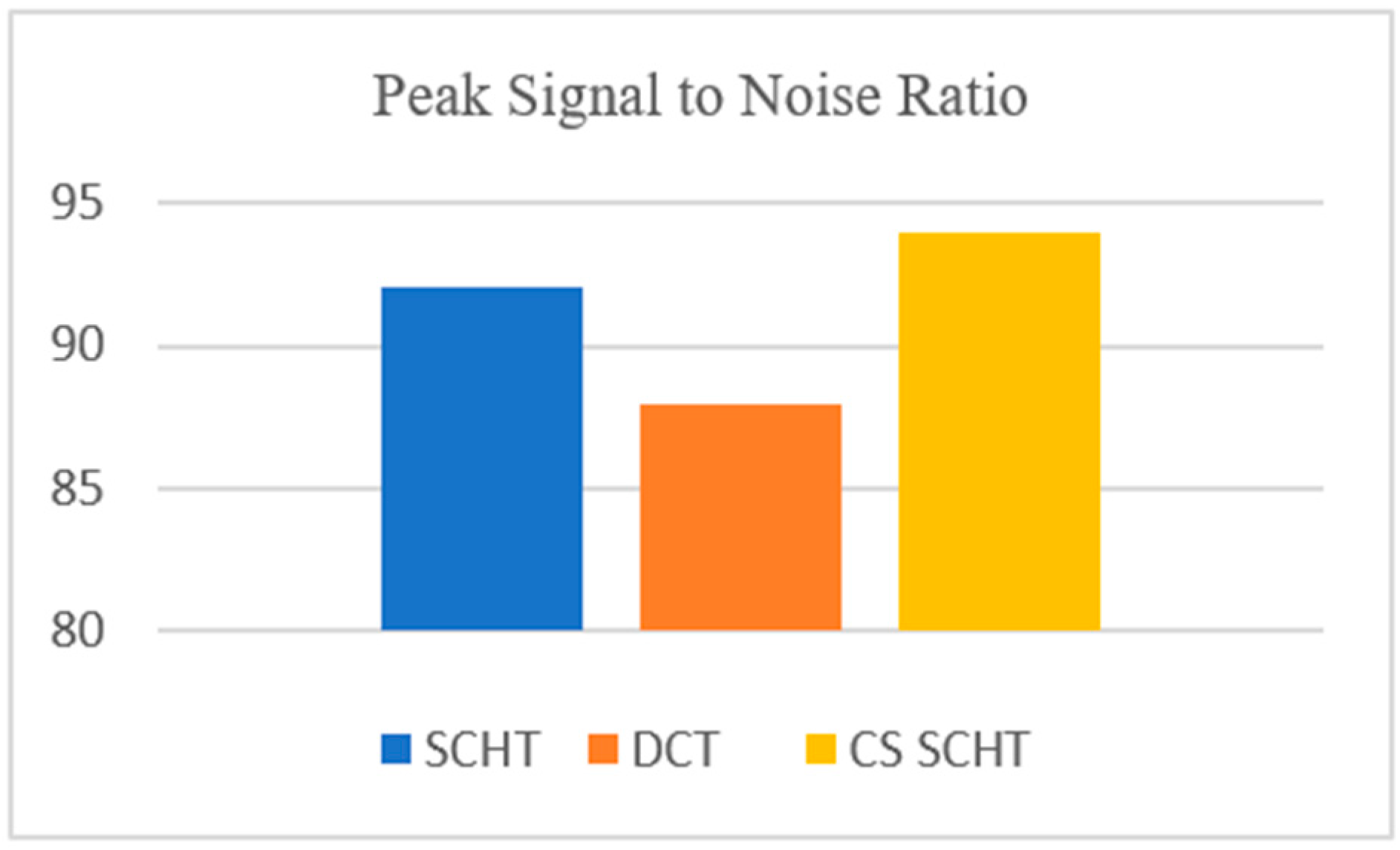
| Watermarking Technique | PSNR |
|---|---|
| CS SCHT | 94.0070 |
| SCHT | 92.0482 |
| DCT | 87.9364 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dur-e-Jabeen; Waqqas, F.; Shaukat, H.; Fatima, M.; Iftikhar, R.; Khan, T. Watermark Embedding Scheme with Variance of Chromatic Components. Eng. Proc. 2023, 32, 26. https://doi.org/10.3390/engproc2023032026
Dur-e-Jabeen, Waqqas F, Shaukat H, Fatima M, Iftikhar R, Khan T. Watermark Embedding Scheme with Variance of Chromatic Components. Engineering Proceedings. 2023; 32(1):26. https://doi.org/10.3390/engproc2023032026
Chicago/Turabian StyleDur-e-Jabeen, Faiza Waqqas, Habib Shaukat, Maria Fatima, Rumaisa Iftikhar, and Tehmina Khan. 2023. "Watermark Embedding Scheme with Variance of Chromatic Components" Engineering Proceedings 32, no. 1: 26. https://doi.org/10.3390/engproc2023032026
APA StyleDur-e-Jabeen, Waqqas, F., Shaukat, H., Fatima, M., Iftikhar, R., & Khan, T. (2023). Watermark Embedding Scheme with Variance of Chromatic Components. Engineering Proceedings, 32(1), 26. https://doi.org/10.3390/engproc2023032026






