1. Introduction
Today’s civil aviation scene is seeing Automatic Dependent Surveillance-Broadcast (ADS-B) being mandated by more Air Navigation Service Providers (ANSP) globally [
1]. It is auspicious in providing additional capability to Air Traffic Control (ATC) for aircraft monitoring and surveillance through simple data types over open channels. Simplicity in operability coupled with high accuracy satellite navigation features [
2] has made it a favourable additional surveillance mechanism besides the complex legacy radar detection systems.
Despite all of its advantages, ADS-B is also vulnerable to various kinds of cyber attacks [
3]. Among the pertinent attacks which are easy to launch and yet require few hacking skills and knowledge are false message injection types of attacks such as ghost aircraft spoofing [
4]. This type of attack aims to confuse ATC and increase their work burden in identifying which aircraft is legitimate and which is a ghost. A recent survey [
5] that analysed the risk severity of several possible attacks on Air Traffic Management (ATM) categorised ADS-B-based cyber attacks as high risk, while [
6] particularly categorised ghost injection spoofing attacks targeting ground stations as an attack type that could create a high negative impact based on a defined scale level which is low, medium, and high. The impact levels in both studies were referring to consequences in terms of physical damage such as mid-air collisions or service deficiencies such as flight delays and cancellation.
While most previous studies, such as [
7,
8], demonstrated how ghost aircraft spoofing attacks can bring chaos to ATC’s surveillance system, only a few have explored the operational resilience of ATM through an effective contingency plan whenever hit by cyber attacks. ATM relies heavily on electronic systems for processing a huge amount of data [
9]. Therefore, disruptions to its capability to execute its critical function would eventually disrupt the flow of air traffic. The cyber-physical system of the ATM domain would experience a huge blow if any of its cyber components such as the ADS-B surveillance system are compromised as described in [
10]. Furthermore, research on radar or other surveillance systems jamming technologies, for instance [
11,
12], is being highly pursued by certain quarters in the name of ensuring public safety and security. There is the possibility that if these technologies are manipulated by adversarial entities they could cause havoc, even to the extent of causing damage to the critical infrastructure and leading to human casualties. These possibilities motivate us to study the impact of such attacks, also known as ghost aircraft spoofing attacks, so as to understand their immediate impact on ATM and to explore viable mitigation techniques in order to prevent such a catastrophic event from happening.
For this purpose, we collaborated with the Civil Aviation Authority of Malaysia (CAAM) in forming a framework that assesses the trajectory of a ghost aircraft and the risks of collision with a real aircraft which is heading towards an airport to begin approach procedures. By using the ADS-B data provided by CAAM, our study is able to demonstrate how real traffic is impacted by a single ghost aircraft occurrence. After learning the immediate impact, we developed a tactical manoeuvring framework with safety and efficiency as its clear quality objectives.
2. Related Works
To begin analysing the attack behaviour and its impact on aircraft during descent, one of the pertinent aspects of our study was to identify the risk factors, one of which is collision during mid-air.
2.1. Collision Risk Assessment
Numerous previous studies have proposed risk assessment frameworks to assess hazards in air traffic flow. One of the notable frameworks is the Collision Risk Model (CRM) that assesses the probability of mid-air collisions through the consideration of multiple factors such as flight trajectories, ground speed and traffic in the surrounding airspace.
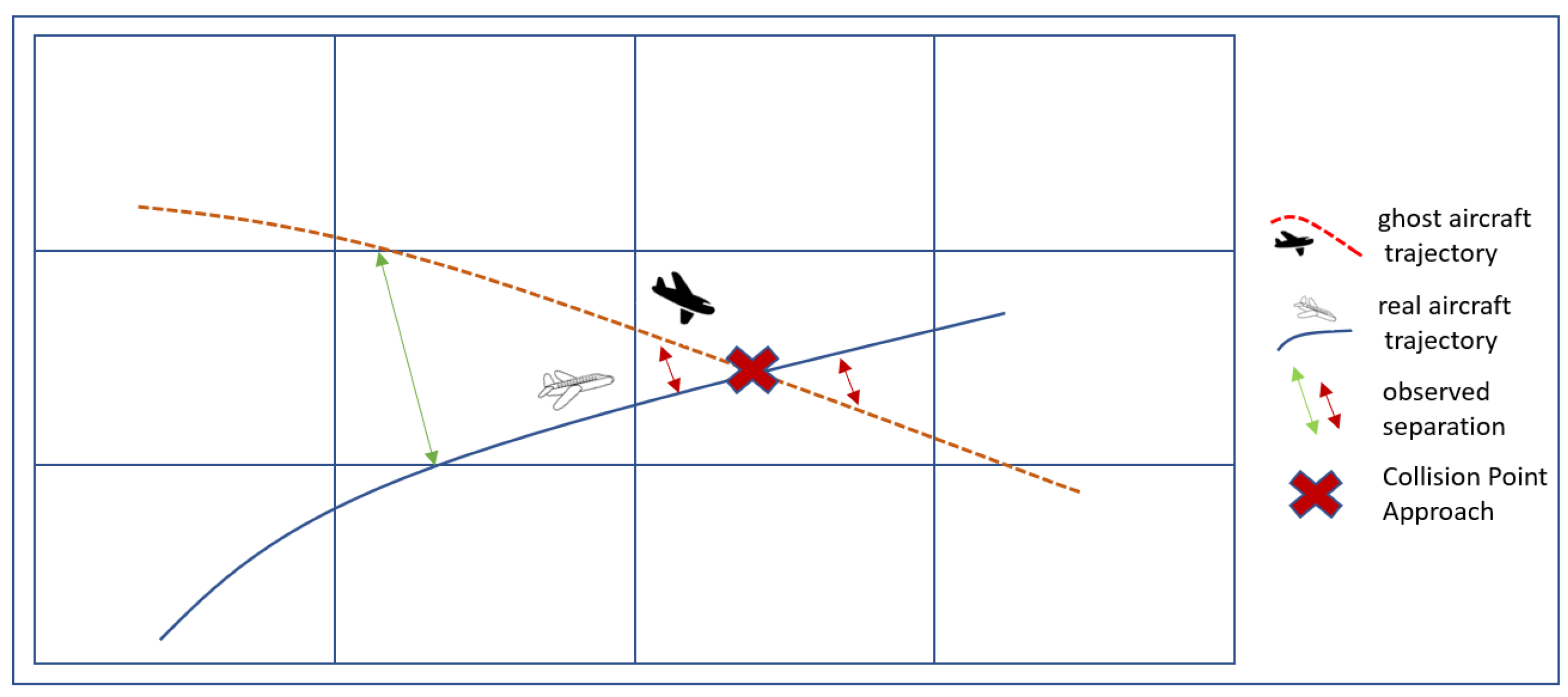
Figure 1 below shows the closest point right before aircraft get into a collision mid-air. We adopted the idea presented in [
13] by applying concept of risk modelling for mid-air collision and framed the entire problem in the context of an ADS-B message injection attack. It is interesting to see how the turn of events during the attack incident can be analysed in depth through a discrete approach. The appearance of a ghost aircraft should be taken seriously due to the limited knowledge at that particular point in time. As safety is paramount, risks to flights when in mid-air require resolution as early as possible before the situation worsens.
2.2. ATC Response during Cyber Incidents
The ATC role is pivotal in incident mitigation. Among the related studies that specifically discuss mitigation techniques carried out by ATC during cyber incidents is [
14]. The idea for this study was rearranging the progression queues of en-route aircraft from certain air space sectors after they were hit by cyber attacks. In the experiments, ATC would be manipulating the queues using a specific algorithm in order to minimize the impact of certain attack types. As our simulation only involved a single aircraft, the only thing in common with our study is the importance of time progression in the context of critical events that take place once intervention is carried out by ATC. Despite manipulating arrival queues, we provided a tactical solution and close guidance for a single aircraft. Another study by [
15] analysed the impact of ADS-B ghost aircraft spoofing and how the impact can be quantified in terms of delay in arrivals and the number of affected aircraft. The study clearly mentioned ATC’s responses in handling unidentified aircraft—ghost aircraft—by slowing down the traffic flow due to the verification procedures of the ghost aircraft. In our proposed framework, we also mention delays induced by the ATC response through diverting the flight path due to collision risks with the ghost aircraft. The delay magnitude is constant in [
15], while in our study, reducing the time delay is the novelty that we aim to achieve through our proposed framework.
3. Research Methods
We applied a scenario-based analysis that does not involve real attack execution either physically or through electronic means. Even though the scenario-based analysis was developed qualitatively, we discussed thoroughly with CAAM and received input from the perspective of a national aviation regulatory body on the features and characteristics of a high impact message injection attack. Next, we discussed possible mitigation techniques that could be undertaken to address the incident. For this purpose, we developed the conceptual framework and tested the performance of the technique through simulations using ADS-B data officially obtained from CAAM. Similar to the majority of research that defines parameters and the scope of their work, our study is also bound to specific assumptions to ensure the objectives would be fulfilled.
3.1. High Impact Attack Scenario
An attacker who knows how ATC would respond to the launched attacks would be able to launch the most disruptive attacks. A previous study by [
16] predicts the decision making process carried out by an attacker targeting a Cyber-Physical System (CPS) through attack tree analysis and its probable consequences. Even though the study did not specifically touch on any kinds of aviation CPS, the main takeaway is that a well prepared attacker might craft a devastating attack on the ADS-B system through actions in series of events. Each event leads to another and as the stages progress, the consequences of disruption to the ATM become greater and greater. Now there are several available open sources of ADS-B data, enabling the live tracking of flights across the globe. This free and accessible information could somehow nurture understanding on the frequently used routes, and how a normal flight profile should look when flying over a certain air space. Knowledge on normalcy in air traffic can be used negatively by anyone with ill intent. Based on the criticality of possible impacts that could be caused by ghost aircraft spoofing attacks, we have identified three primary criteria for our attack scenario. The identified criteria are:
The behaviour of a ghost aircraft influences the ATC in its responses. A credible ghost aircraft supposedly imitates the characteristics of a legitimate aircraft. When flying in a certain airspace, the profile of speed, altitude and trajectory plays a significant role in the imitation game. The longer the ATC takes time to verify the ghost aircraft’s identity, the deeper the confusion that can be instilled by the attacker which will gradually create greater disruption to the air traffic flow. Therefore, the attacker would tune these vital parameters in accordance with the profile of a legitimate aircraft to avoid easily being singled out as an anomaly by the ATC.
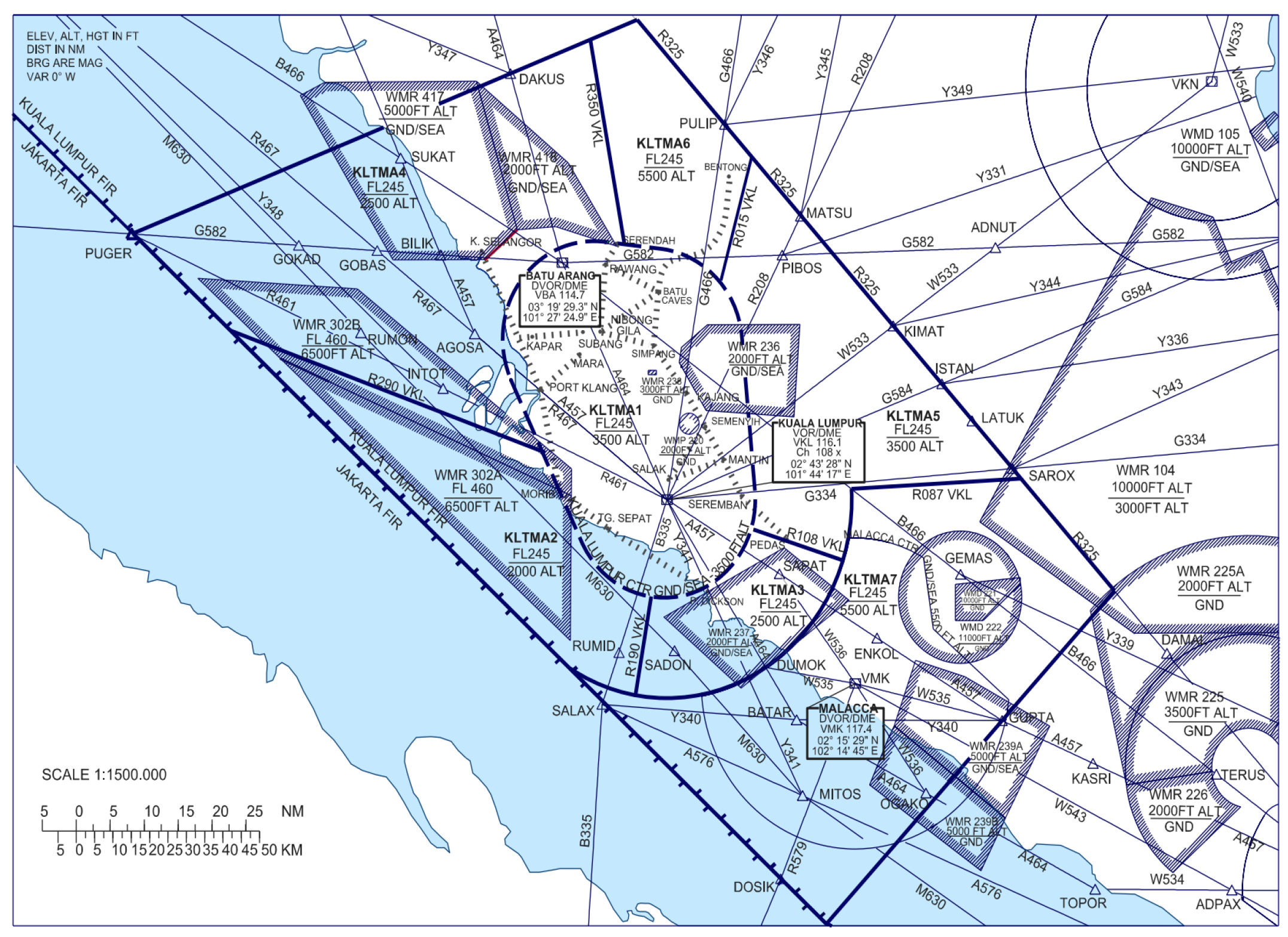
The location of the spoofing incident is also a main factor in determining the type of response that should be taken by the ATC. According to CAAM, the Kuala Lumpur Terminal Manoeuvring Area (TMA), shown in
Figure 2 [
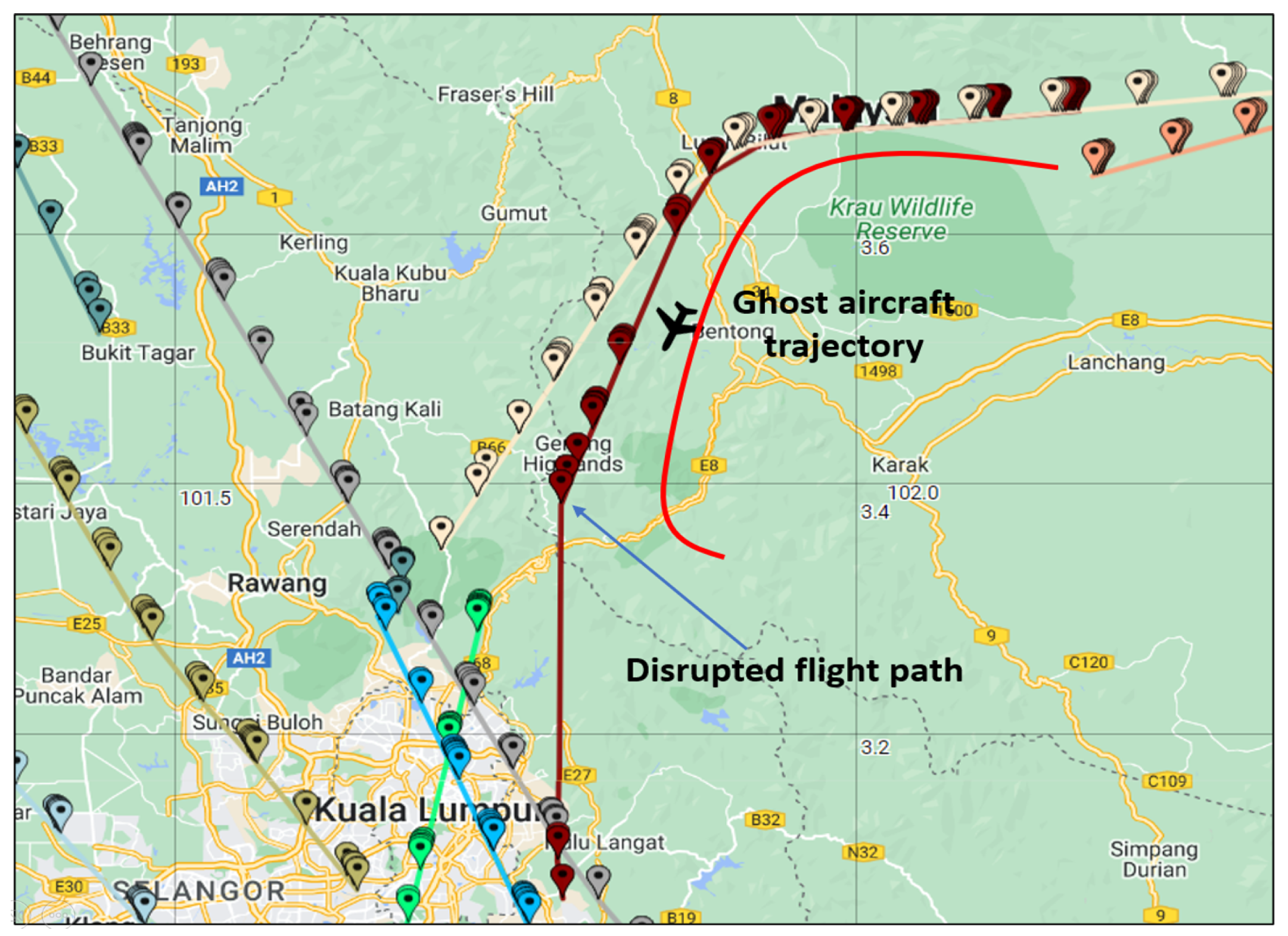
17], is a high density airspace that also includes airport airspace. Usually, the volume of traffic is very high with flight phases of descending, climbing and en route. The appearance of a ghost aircraft at the TMA border and flying towards the TMA would definitely catch the serious attention of ATC, as shown as the red curvy trajectory closing in to the real legit flight represented by the dak red ADSB track heading south in
Figure 3. We used both tracks to model and simulate our proposed benchmarking trajectory in addressing this attack. There were also other TMA-inbound flights as depicted in beige, green and fluorescent green ADS-B tracks. However these flights were not interrupted. Once the ADS-B surveillance system detects that a ghost aircraft is closing in on the TMA, ATC will divert other conflicting flights not to fly too close to the unverified ghost aircraft. Rectifying this situation would cost numerous diversions on various scales and these diversions would result in delays either to arrivals or departures. Other than this, the attacker would not want his strings of ghost aircraft attack to be identified by ATC through visual observation. Transmitting the false message in the TMA area or too close to airport airspace would trigger ATC Tower and, with the help of bypassing pilots, they could determine the non-existence of the ghost aircraft. This is why the anonymity of not being able to be scrutinized through optical equipment or physical check is important to ensure attack persistence.
3.2. Simulation of ATC Response during Cyber Incident—Tactical Manoeuvring during Descent
As in
Figure 3, we created an attack scenario of a ghost aircraft trajectory interfering with the normal trajectory of an aircraft that has begun descending towards Kuala Lumpur International Airport (KLIA) from 1000 h until 1005 h on 6 January 2020. The ghost aircraft (red trajectory) was injected theoretically in the scneraio-based analysis nearby the Eastern border of the Lumpur TMA. When the ATC detected a possible collision, and after trying to verify the ghost aircraft but to no avail, the ATC would take standard preventive actions by alerting the legitimate aircraft and to slow the affected aircraft down and divert its route.
Several assumptions were applied throughout the simulation which are as follows:
This scenario is declared as an emergency due to other surveillance methods such as radar and multi-lateration also being suppressed and jammed by adversarial actions. Only the ADS-B system was available and running;
The tactical manoeuvring technique was not influenced by the presence of the surrounding traffic. This was mainly due to the real traffic conditions based on the tested data. The weather was fine with no warnings issued by Notice to Air Men (NOTAM) or any other communication lines;
A non-standard descent procedure was simulated due to emergency status;
The injected ghost aircraft used the same descent profile as the real aircraft except its trajectory was designed with one less way point for simulation purposes.
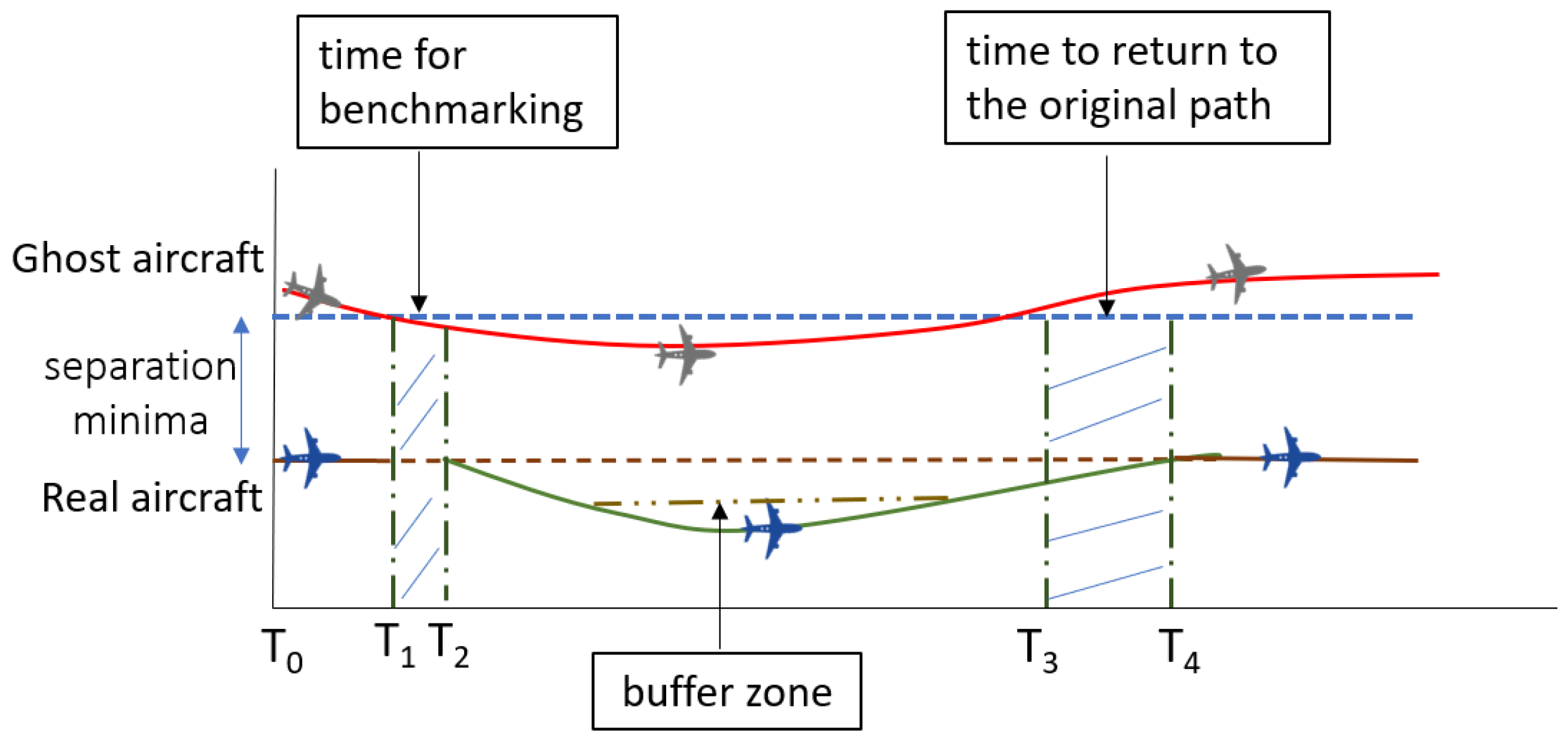
The main principle of our proposed framework is about constantly benchmarking the trajectory of the ghost aircraft. The tactical diversion adheres to a 6 nautical miles (6nm) lateral separation minima including a threshold of 1 nm buffer airspace. In the event of further incursion inwardly by the ghost trajectory, the tactical diversion will move further away from the ghost trajectory. At the time this event is happening, the separation minima is still more than or equal to 5 nm. The existence of buffer airspace is also meant to accommodate non-instantaneous processing by the aircraft’s pilot based on recommendations given by the framework. The concept of the proposed framework is as shown in
Figure 4.
In order to populate the required data to run the simulation in Matlab, we converted the lat–long data obtained from the ADS-B file and converted it into XY coordinates before plotting it on a Cartesian plane. The same was performed for the ground speed, which was converted from knots to meters per second and altitude, which was from feet to meters. Trajectory data for the real aircraft and the ghost aircraft are as shown in
Table 1 and
Table 2. Meanwhile our proposed tactical diversion trajectory and the conventional simplistic diversion trajectory data can be referred at
Table 3 and
Table 4 respectively.
4. Simulation Results
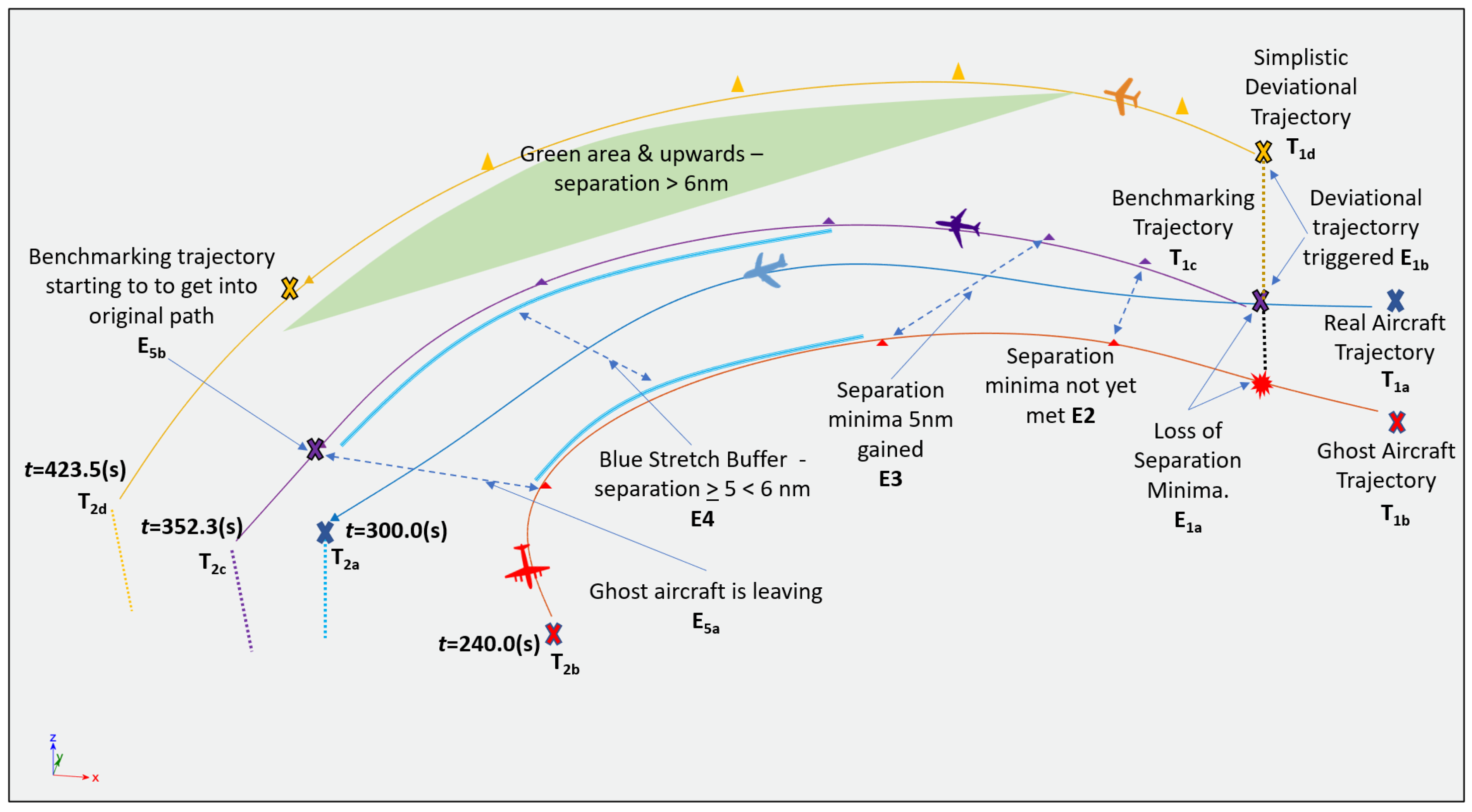
Our simulation results, as shown in
Figure 5, show that our proposed ATC level tactical manoeuvring—
which started at coordinate x = −5464 m, y = −952 m—took 352.3 s to get close to the track of the original trajectory—
, which began at coordinate x = −122.2 m, y = −14.0 m. Throughout the entire simulation, the plotted trajectories adhered to the separation minima rule whilst both the ghost aircraft and the legitimate aircraft continued to descend with a similar profile. The benchmarked tactical manoeuvring was triggered when the ATC spotted that the ghost aircraft was closing into the real aircraft’s path and eventually arrived at a location less than 6nm away, in particular, at
from coordinate
, which is x = −2572 m and y = −9577 m. At the time the real flight trajectory arrives at the finishing point at
t = 300 s, the simplistic deviation,
, was only able to reach a location close to coordinate x = −43,672 and y = −18,045, approximately 66.7% from its full trajectory course. At the end of the simulation, the simplistic deviation took a total of 423 s to arrive at the end of its trajectory.
Apart from the time taken by both compared trajectories to finish its course, other readings, such as trajectory data, are shown in
Table 3 and
Table 4 accordingly. The state of the tactical manoeuvring trajectory framework can be described as:
The current state of each of the trajectories is as per the progression of the trajectory at the inferred time
(
). Properties for a trajectory,
T, at any state
Based on the proposed tactical manouevring framework’s linear separation,
e at
n state,
with
Tc is the proposed tactical trajectory for deviation and
Tb is the ghost aircraft trajectory.
5. Discussion
Based on the results, it is obvious that the conventional simplistic deviation trajectory requires more time to reach the location close to the tactical benchmarking trajectory. A visual observation of the end state of the simplistic deviation trajectory is suggesting a substantive distance to fly before being able to join the original flight path. We can also infer that the distances travelled by each trajectory differ from each other based on their time of arrivals through comparison with the original real aircraft’s trajectory as the focal point. The difference between and (at endpoint) is more than 52.3 s as of t = 300 s. This is primarily due to the tactical benchmarking trajectory had flown longer distance and at lower speeds.
Meanwhile, the difference between the coordinates of and is more than 1 nm apart from a fixed angle. This tells us that, with a faster speed profile, there is a possibility that tactical benchmarking and a simplistic deviation trajectory would be able to get closer to the real trajectory by covering more distance, thus be able to complete its designated path within the simulation run time. However, this argument is still inconclusive as the original ADS-B data that were used were insufficient to produce a clear projection of each of the trajectories into airport airspace. Nevertheless, based on the findings of 300 to 423.5 s of the simulation run, the tactical benchmarking trajectory provides a guided trajectory that is safe and quicker to merge with the original trajectory compared to the simplistic deviation trajectory resulting from a generic and unguided action by the ATC.
Furthermore, the analysis of discrete events within our proposed framework always looks for the optimal state by safely and quickly finding an updated path to join the original trajectory depending several conditions such as current surrounding air traffic and consideration of existence of of meteorological factors. Besides these clear advantages, we are also considering the possibility of coming out with an optimization option in our future work in terms of determining the economical aspect of trajectories based on fuel consumption rate by comparing the fuel burn rate in a simplistic diversion against the fuel burn rate in the tactical benchmarked trajectory mode.
6. Conclusions
Our proposed ATC level tactical manoeuvring has been proven as an ideal framework in ADS-B false message injection cyber attack especially in situations whereby nature of such attacks could not be verified in the early stages as what our crafted high impact attack scenario had demonstrated. With safety as the utmost priority, adherence to safe distance and concurrently trying as best as possible not to deviate excessively from the original flight path. This could only be achieved through consistent benchmarking of the ghost aircraft trajectory with defined separation thresholds so that ideal deviation in the proposed trajectory is sustained throughout the attack period.
Author Contributions
Running simulations and paper writing, M.R.K.; review, insights and supervision, M.D.H.; review, insights and supervision, Y.T.; review, insights and supervision, Y.K. All authors have read and agreed to the published version of the manuscript.
Funding
The authors would like to thank Japan’s Industrial Cyber Security Center of Excellence (ICSCoE) for funding this research.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
ADS-B dataset that was applied was officially obtained from CAAM together with the agency’s consent in conducting the research. Results data are exhibited as trajectory data as per
Table 3 and
Table 4 on page 6 and
Figure 5 on page 7 of this manuscript.
Conflicts of Interest
The authors declare no conflict of interest in conducting this research.
References
- Davidson, J. ADS-B Update 2022—Where Are We Now. Available online: https://www.universalweather.com/blog/ads-b-update-2022/ (accessed on 23 May 2022).
- Federal Aviation Administration (FAA). Benefits. Available online: https://www.faa.gov/air_traffic/technology/equipadsb/capabilities/benefits/ (accessed on 23 May 2022).
- Riahi Manesh, M.; Kaabouch, N. Analysis of vulnerabilities, attacks, countermeasures and overall risk of the Automatic Dependent Surveillance-Broadcast (ADS-B) system. Int. J. Crit. Infrastruct. Prot 2017, 19, 16–31. [Google Scholar] [CrossRef]
- Lykou, G.; Iakovakis, G.; Gritzalis, D. Aviation Cybersecurity and Cyber-Resilience: Assessing Risk in Air Traffic Management. In Critical Infrastructure Security and Resilience; Springer: Cham, Switzerland, 2019; Volume 1, pp. 245–260. [Google Scholar] [CrossRef]
- Wu, Z.; Shang, T.; Guo, A. Security Issues in Automatic Dependent Surveillance—Broadcast (ADS-B): A Survey. IEEE Access 2020, 8, 122147–122167. [Google Scholar] [CrossRef]
- Harrison, E.; Zaidenberg, N. Survey of Cyber Threats in Air Traffic Control and Aircraft Communications Systems. In Intelligent Systems, Control and Automation: Science and Engineering; Springer: Cham, Switzerland, 2018; Volume 93, pp. 199–217. [Google Scholar]
- Mirzaei, K.; Pessanha De Carvalho, B.; Pschorn, P. Security of ADS-B: Attack Scenarios. EasyChair Preprint No. 851. 2019. Available online: https://easychair.org/publications/preprint_open/DpM4 (accessed on 10 June 2022).
- Meng, Q.; Hsu, L.T.; Xu, B.; Luo, X.; El-Mowafy, A. A GPS spoofing generator using an open sourced vector tracking-based receiver. Sensors 2019, 19, 3993. [Google Scholar] [CrossRef] [PubMed]
- Monteiro, M.; Sarmento, T.; Barreto, A.; Costa, P.; Hieb, M. An Integrated Mission and Cyber Simulation for Air Traffic Control. In Proceedings of the IEEE Conference on Intelligent Transportation Systems (ITSC), Rio de Janeiro, Brazil, 1–4 November 2016; pp. 2687–2692. [Google Scholar]
- Alsulami, A.; Zein-Sabatto, S. Resilient Cyber-Security Approach for Aviation Cyber-Physical Systems Protection against Sensor Spoofing Attacks. In Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC 2021), Virtual, 27–30 January 2021; pp. 565–571. [Google Scholar]
- Zhouyan, S.H.; Min, W.A.; Lu, Z.H.; Linzhi, M.A. Research on Track Deception Technology Based on Jamming of Flexible Lines by Jammers. MATEC Web Conf. 2018, 176, 01039. [Google Scholar] [CrossRef][Green Version]
- Mehmood, S.; Malik, A.N.; Qureshi, I.M.; Khan, M.Z.; Zaman, F. A Novel Deceptive Jamming Approach for Hiding Actual Target and Generating False Targets. Wirel. Commun. Mob. Comput. 2021, 2021, 8844630. [Google Scholar] [CrossRef]
- Nieto, F.J.S. Collision Risk Model for High Density Airspaces. In Risk Assessment in Air Traffic Management; Pérez Castán, J.A., Sanz, Á.R., Eds.; IntechOpen: Madrid, Spain, 2020; pp. 3–15. [Google Scholar]
- Roy, S.; Sridhar, B. Cyber- Threat assessment for the air traffic management system: A network controls approach. In Proceedings of the 16th AIAA Aviation Technology, Integration, and Operations Conference, Washington, DC, USA, 13–17 June 2016. [Google Scholar]
- Kamaruzzaman, M.R.; Sane, B.O.; Fall, D.; Taenaka, Y.; Kadobayashi, Y. Analyzing Cascading Effects of Automatic Dependent Surveillance-Broadcast (ADSB) Spoofing Attacks Using Discrete Event Model of Air Traffic Control Response and AGMOD Dynamics. In Proceedings of the IEEE Cyber Security and Resilience, Rhodes, Greece, 26–28 July 2021. [Google Scholar]
- Orojloo, H.; Abdollahi Azgomi, M. Predicting the behaviour of attackers and the consequences of attacks against cyber-physical systems. Secur. Commun. Netw. 2016, 9, 6111–6336. [Google Scholar] [CrossRef]
- WMKK AD2.24: Charts Related to an Aerodome: AD-2-WMKK-4-1. Available online: https://aip.caam.gov.my/aip/eAIP/2023-02-23-AIRAC/html/index-en-MS.html (accessed on 5 June 2022).
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).