1. Introduction
Legacy Ethernet infrastructure, known as brownfield networks, remains the dominant physical layer in small and medium enterprises (SMEs). Many such networks were cabled a decade or more ago and lack the flexibility demanded by zero-trust security models. Retrofitting cables or replacing switches is often unfeasible due to budget, downtime, or heritage constraints. Brownfield deployments, therefore, face a chronic gap between static Layer-1 realities and dynamic cyber-threat landscapes.
Classical remedies do not close this gap. Static virtual local area networks (VLANs) provide only coarse isolation and rely on error-prone manual procedures [
1]. Software-defined networking (SDN) enables fine-grained flow control, yet its specialized hardware and steep learning curve translate into capital and operational costs that most SMEs cannot bear. Meanwhile, the attack surface is expanding. Cloud migration, remote work, and commodity IoTs drive lateral-movement risk beyond what perimeter firewalls can defend. Organizations require a control plane that is programmable, context-aware, and economically viable.
In this study, we developed a modular, cost-conscious, adaptive zero-trust control plane tailored to brownfield Ethernet deployments. The system’s architecture is explicitly designed to ride on the existing copper and commodity managed switches, thus avoiding specialized hardware upgrades or disruptive physical rewiring. At its core, the system combines AI-assisted security operations (SecOps) telemetry with an optimization and policy-generation pipeline. First, telemetry and contextual asset data feed a genetic-algorithm (GA) engine that computes risk-aware Institute of Electrical and Electronics Engineers (IEEE) 802.1Q VLAN assignments. Second, the resulting segmentation context is translated into pfSense firewall policies by a large language model (LLM) guided through structured prompt engineering and hardened by dual-stage validation.
These components execute within a closed-loop feedback regime in which tightly coupled stages, which are telemetry ingestion, VLAN optimization, rule synthesis, verification, and enforcement, are orchestrated over standards-compliant south-bound interfaces (simple network management protocol (SNMP), Network Configuration Protocol/Representational State Transfer (NETCONF/REST)). Continuous injection of threat intelligence and runtime alerts allows the control plane to adapt policy state without manual intervention, aligning with zero-trust principles of least privilege and explicit, context-driven access. Since the system overlays rather than replaces the installed Ethernet fabric, it offers a low capital expenditure (CapEx) and operationally tractable alternative to full SDN migration. This enables progressive micro-segmentation, breaking down traditional broad, functionally defined subnets into multiple dedicated VLANs, greatly strengthening security posture while preserving required business workflows.
The remainder of this article is structured as follows.
Section 2 reviews the related works.
Section 3 describes the proposed methodology and design in detail.
Section 4 reports and discusses the experimental results. Finally,
Section 5 concludes the study and outlines directions for future research.
2. Background and Related Work
Brownfield networks continue to anchor connectivity in SMEs because rewiring or wholesale equipment replacement is cost-prohibitive and operationally risky [
2,
3]. Yet these static Layer-1 topologies are colliding with an escalating threat landscape marked by cloud workload sprawl, ubiquitous IoT endpoints, and supply-chain-driven attacks, all of which enlarge the lateral-movement surface that perimeter firewalls were never designed to police [
4,
5]. The conventional remedies, such as logical segmentation with port-based or IEEE 802.1Q VLANs, reduce broadcast domains but are chronically undermined by decades of undocumented modification, permissive “any-any” rules, and configuration drift, creating a false sense of isolation while leaving exploitation paths wide open [
6]. Micro-segmentation platforms promise finer controls, yet they require extensive flow discovery, inline enforcement points, and policy sets that scale into tens of thousands of objects, which is an operational burden that few SMEs can sustain [
7]. SDN offers controller-based programmability and zero-trust compatible flow steering, but brownfield adoption typically demands a disruptive “rip-and-replace” cycle plus high capital outlay for SDN-capable switches and redundant controllers. Techno-economic analyses consistently flag CapEx as the dominant barrier to SDN retrofits in legacy plants [
8,
9].
Against this backdrop, security architects are converging on overlay approaches that inject adaptive controls without disturbing the physical fabric. The conceptual pivot is provided by Zero Trust Architecture (ZTA), which dispenses with location-based trust and demands continuous, identity-centric verification [
10,
11]. The National Institute of Standards and Technology (NIST)’s canonical model frames this verification loop around a policy engine fed by rich telemetry and threat intelligence, implicitly inviting automation-friendly integration [
12]. Cloud-native security information and event management (SIEM)/security orchestration, automation, and response (SOAR) platforms have risen to a mandate. New-generation services or products provide elastic log ingestion, built-in user-behavior and entity-behavior analytics, and playbook automation that decreases the dwell time of intrusions [
13]. When augmented with machine-learning analytics and retrieval-augmented generation (RAG), these platforms can translate high-level intent and contextual asset data into actionable responses that close the semantic gap between zero-trust policy objectives and low-level device configurations [
14,
15,
16]. LLMs synthesize firewall rules directly from natural-language constraints, while genetic algorithms excel at optimizing segmentation layouts under complex risk functions [
17]. Collectively, these advances motivate an overlay security architecture that couples AI-assisted SecOps with legacy Layer-2 automation, offering SMEs a reproducible, low-CapEx pathway from flat networks to dynamically protected zones without the disruptive economics of full SDN migration.
The results indicate that there is an urgent need for a solution that reuses installed Ethernet plants, automates least-privilege segmentation with minimal human input, and embeds policy enforcement that drives threat detection.
3. Methodology and System Design
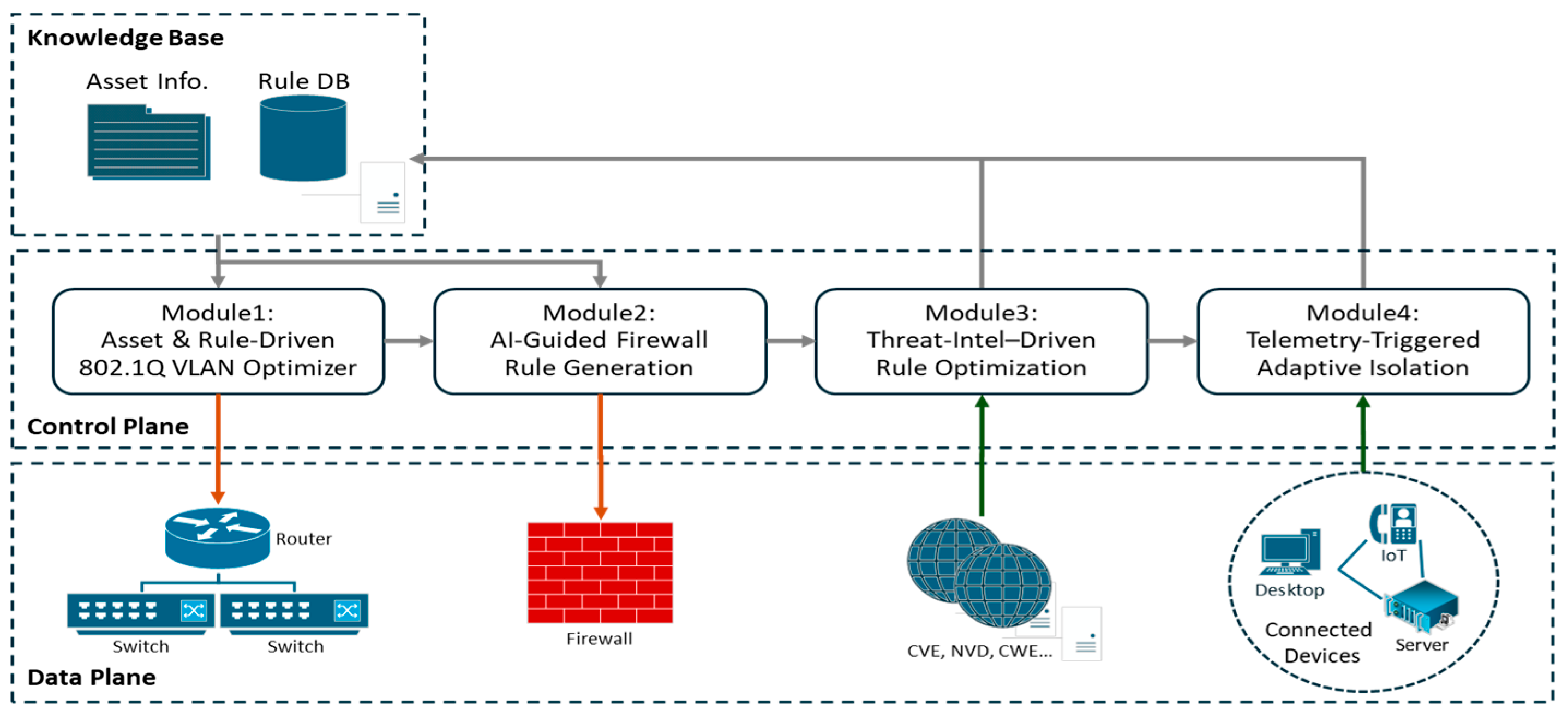
We developed an adaptive zero-trust control plane that overlays existing managed switches, avoiding specialized hardware upgrades. The modular architecture incorporates four rigorously integrated modules, as shown in
Figure 1, forming a continuous closed-loop feedback system.
3.1. Mudule 1: Asset and Rule-Driven VLAN Optimizer
Asset enumeration is carried out using a standardized JavaScript object notation (JSON)-based schema that captures each device’s identification (ID), Internet Protocol (IP) address, functional role, and organizational mapping. This structured model supports validation, extensibility, and cross-source correlation, enabling scalability across diverse network architectures. Topology is derived automatically by analyzing link layer discovery protocol (LLDP) data to construct a Layer-2 connectivity graph, which is reconciled with data from systems like NetBox [
18]. This ensures the accurate detection of cable drift and the inclusion of inactive links, forming a reliable foundation for segmentation and policy generation.
To quantify the potential risks associated with traffic between any two assets
i and
j, a multidimensional pairwise risk function is defined as follows.
Here, each factor captures a distinct dimension of security exposure, including functional criticality, institutional and data-context adjustments, security posture, and regulatory/compliance obligations. The model incorporates base risk (0.1–1.0), contextual adjustments, posture-based multipliers, and regulatory penalties aligned with frameworks such as the International Organization for Standardization (ISO)/International Electrotechnical Commission (IEC) 27001 [
19]. A floor value of 0.05 ensures topological coverage. This extensible formulation enables risk-aware VLAN clustering adaptable across enterprise sectors.
GA employs integer encoding, where each chromosome represents a complete VLAN assignment across assets, and a post-decoding repair operator ensures feasibility. To improve diversity and prevent premature convergence, initial populations include four heuristic seed classes: legacy mapping, institutional units, security tiers, and policy-constrained random assignments. Candidate solutions are evaluated using a composite cost function. The objective of GA is to identify the solution that minimizes this cost function, which is defined as follows.
Here, = sums the risk scores within each VLAN; penalizes violations of strict constraints (e.g., compliance); penalizes configurations that disrupt necessary communications; rewards adherence to best practices like least privilege; and rewards reduced administrative overhead. Weights () allow for customization based on institutional priorities, with all weights set to 1.0 during our experiments.
The evolutionary design is optimized for VLAN segmentation, using tournament selection to balance convergence and diversity. Single-point crossover forms offspring by swapping chromosome segments, while mutation follows a heuristic distribution in which 40% group similar assets, 30% reduce VLAN count, 20% create new VLANs, and 10% apply random changes. Parameters were tuned to ensure stability with a population size of 50, up to 500 generations, a crossover probability of 0.8, and a mutation probability of 0.15. This configuration consistently achieves robust convergence across heterogeneous topologies and is used as the default in this study.
3.2. Mudule 2: AI-Guided Firewall Rule Generation
Building on the VLAN optimization, this study proposes an automated firewall policy generation mechanism to enforce least-privilege access under zero-trust principles. The fine-grained service communication matrix (SCM), as shown in
Table 1, represents all required inter-VLAN service flows and serves as the authoritative input for pfSense rule synthesis. Dynamic subnet sizing ensures efficient address utilization by tailoring each VLAN’s prefix length to endpoint count plus buffer capacity. The SCM population follows a layered authorization model that includes infrastructure services, cross-departmental flows, administrative access, and a global default-deny policy. This ensures only essential communications are permitted. The resulting SCM enables deterministic, auditable, and automation-ready firewall rule deployment.
High-fidelity pfSense rule generation is achieved using GPT-4o, guided by prompt engineering and a RAG framework grounded in firewall best practices [
20]. A two-tier prompt strategy is used. A persistent system prompt embeds expertise in pfSense syntax, zero-trust principles, and compliance, while dynamic per-task prompts encode VLAN roles, protocols, ports, and policy modifiers. The results follow a canonical JSON schema through an automated validation process to ensure no errors before deployment.
To address LLM hallucinations and semantic drift, a Dual-Agent validation mechanism is used. Stage 1 performs syntactic validation of schema, entity formats, and field normalization. Failing rules are auto-corrected and re-prompted. Stage 2 involves conducting behavioral testing in a pfSense sandbox, verifying traffic control semantics, and detecting conflicts. A three-tier remediation process that includes repair, simplification, and fallback deployment ensures only validated, secure rules are pushed to production, maintaining operational safety and auditability.
3.3. Module 3: Threat-Intel-Driven Rule Optimization
To enable proactive vulnerability management in brownfield networks, a daily threat-intelligence (TI) pipeline is implemented, incorporating three key stages. First, the system collects and normalizes advisories from sources such as National Vulnerability Database (NVD), Common Vulnerabilities and Exposures (CVE) feeds, and MITRE Common Weakness Enumeration (CWE), converting them into a unified format containing CVE IDs, CVSS scores, affected products, and mitigation data. Second, asset correlations are performed by matching these advisories against a local asset catalog using Common platform enumeration. Matches are annotated with severity and exploitability context. Third, for each confirmed vulnerability, GPT-4o generates a temporary pfSense rule by combining CVE-specific and local network contexts. All rules are validated through a Dual-Agent validation mechanism described above to ensure correctness and security. This pipeline enables automated, zero-trust-aligned mitigation of threats with minimal delay.
3.4. Module 4: Telemetry-Triggered Adaptive Isolation
Reactive defense against emerging threats is enabled by a closed-loop RAG mechanism that connects live events with historical threat intelligence and automated responses. A local vector database stores embedded CVE texts, vendor bulletins, and incident reports. When a security event occurs, key indicators (e.g., IP, port, intrusion detection system hits) are used to retrieve relevant intelligence. This context is passed to GPT-4o, which generates a temporary pfSense rule and analyst guidance. All outputs are validated before deployment, and confirmed responses update the risk model to support dynamic VLAN re-segmentation, thereby creating a self-reinforcing zero-trust posture.
For high-confidence alerts, automated containment is triggered. Affected devices are quarantined at Layer 2 and isolated via high-priority firewall rules. Configuration changes are executed over NETCONF/REST or SNMPv3 with full audit logging. Incident metadata is embedded into the knowledge base to enhance future detection accuracy and reduce false positives.
These actions provide a rapid, vendor-agnostic containment capability coupled with a learning feedback channel that continually sharpens detection fidelity and response precision.
4. Results and Discussion
4.1. Experimental Scenario
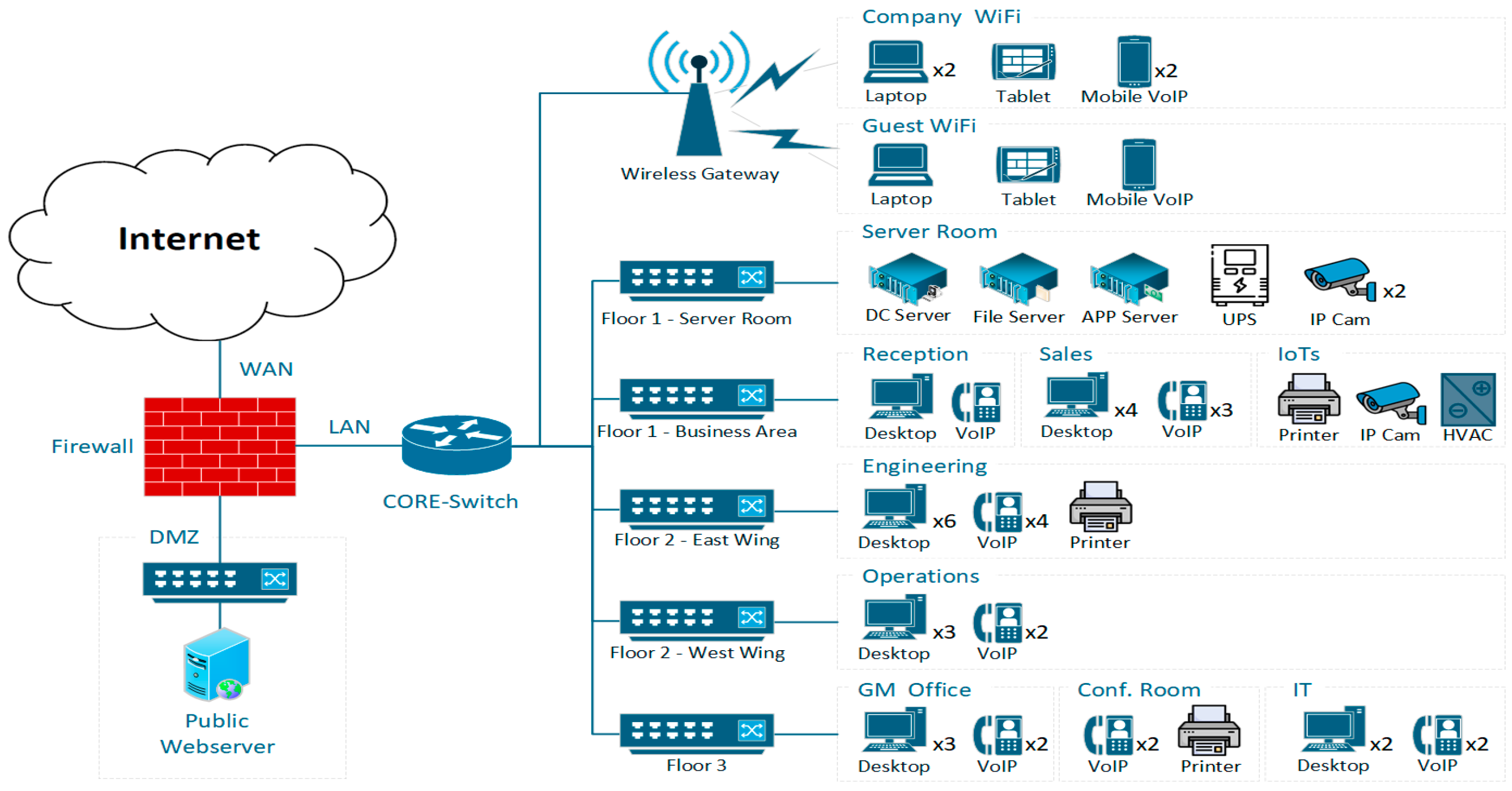
The experimental testbed is shown in
Figure 2. It is a typical SME network with diverse host roles and trust boundaries, comprising 53 endpoints, including 18 workstations across six departments, 4 mission-critical servers, 16 voice over internet protocol (VoIP) phones, 5 wireless access devices, 3 guest endpoints, and 7 Internet of Things (IoT) sensors, respectively. This heterogeneous mix supports testing of both user-centric and device-centric traffic segmentation. Initially, the network used a flat, functionally partitioned structure with seven/24 subnets following the RFC1918 addressing. The physical topology follows a core-access hierarchy with one core switch linked to five access switches, reflecting typical brownfield deployments. Logical-to-physical mappings are cataloged to support VLAN optimization and isolation validation without new hardware.
4.2. GA Optimization
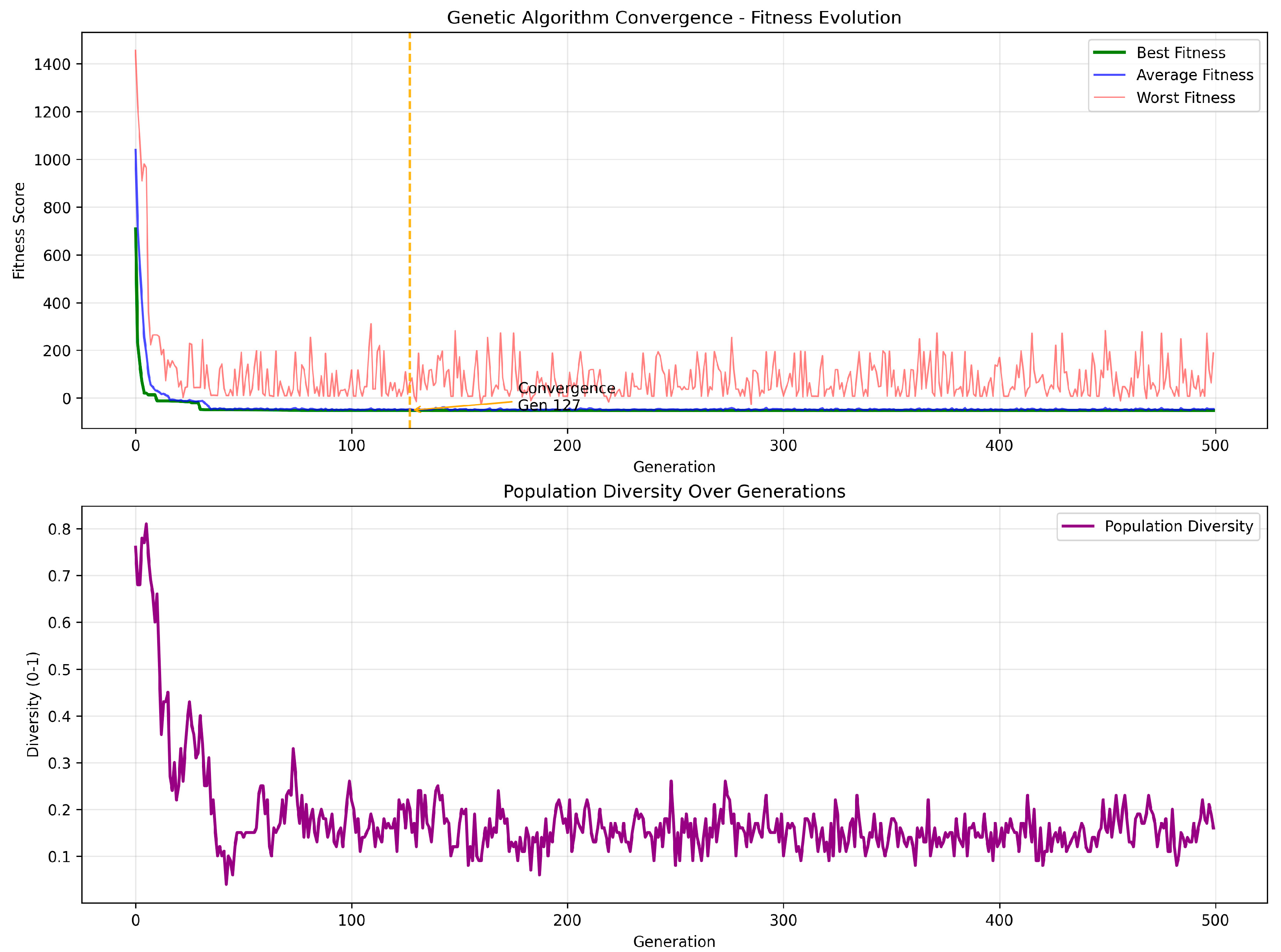
Using the proposed GA, we observed robust convergence to an intricate network segmentation problem. As shown in
Figure 3, the top plot illustrates the convergence behavior of the GA in terms of fitness scores across generations, showing rapid improvement within the first 50 generations and convergence at generation 120–150. The bottom plot shows population diversity declining as the algorithm converges, with a final diversity score of 0.160, indicating the effective exploitation of the search space after sufficient exploration. This early, steep descent indicates a well-structured optimization landscape and shows that the evolutionary operators designed in this study can efficiently exploit directional cues in the search space.
After optimization, the network is markedly improved. The original seven broad functional subnets are refined into 34 purpose-specific VLANs listed in
Table 2. This fine-grained micro-segmentation substantially strengthens the overall security posture while preserving business feasibility.
In the management plane, the core switch, firewall, and other key infrastructure components were placed in a dedicated management VLAN, isolating management traffic from production traffic. This reflects established infrastructure-security best practices and improves ongoing operations. In the server tier, a service-oriented isolation policy was achieved.
Compliance outcomes improve across multiple cybersecurity frameworks. The ISO/IEC 27001 [
19] compliance score rose from 62.3 to 94.7%, while alignment with the NIST Cybersecurity Framework increased from 58.9 to 91.2%. These gains demonstrate that the framework proposed in this study provides an effective technical pathway toward a mature ZTA.
4.3. Evaluation of AI-Guided Firewall Rule Generation
The generated firewall rules prioritize core infrastructure services such as Domain Name System, Dynamic Host Configuration Protocol, Network Time Protocol, and Lightweight Directory Access Protocol, ensuring baseline network functionality. VoIP traffic is supported through session initiation protocol and real-time transport protocol, with bidirectional rules balancing performance and security. Administrative services such as SNMP and Secure Shell are restricted to authorized interfaces, while zero-trust isolation policies govern guest access, IoT communications, and enforce a default-deny baseline.
All 851 generated rules conform to the pfSense syntax, with complete metadata fields and standardized naming for automated deployment and lifecycle management. Dual-Agent validation confirms 100% rule acceptance, although 188 warnings that mostly lacked logging on key services highlighted the importance of validation for audit readiness. Without this layer, critical telemetry could have been missed. Ultimately, the policy set aligns with business needs, enforces least-privilege access, enables thorough auditability, and significantly reduces lateral attack surfaces.
5. Conclusions
We developed a modular, AI-assisted zero-trust control plane for brownfield Ethernet networks, offering a cost-effective alternative to SDN retrofits. The architecture integrates a GA-based VLAN optimizer, LLM-driven firewall rule generation, TI-guided policy synthesis, and telemetry-triggered isolation. By automating policy enforcement through standards-compliant interfaces, the system bridges high-level zero-trust intent with low-level configurations. Deployment results on an SME testbed demonstrate that the original seven subnets are refined into 34 purpose-specific VLANs, improving lateral movement containment. ISO/IEC 27001 [
19] compliance is up from 62.3 to 94.7%, and NIST Cybersecurity Framework alignment has risen from 58.9% to 91.2%. All 851 AI-generated firewall rules pass Dual-Agent validation, with over 90% of warnings linked to enhanced logging and not syntax errors, highlighting operational rigor.
The system needs to be evaluated for long-term deployment stability by integrating adaptive learning for evolving threats, extending support to hybrid cloud/container environments, and developing formal policy compliance verification. These directions aim to enhance the architecture’s scalability, resilience, and contextual awareness of SMEs.
Author Contributions
Conceptualization, all authors; Methodology, all authors; Software, H.-S.W.; Validation, R.-C.W.; Formal analysis, H.-S.W.; Resources, R.-C.W.; Data curation, all authors; Writing—original draft, R.-C.W.; Writing—review & editing, R.-C.W.; Visualization, all authors; Supervision, R.-C.W.; Project administration, R.-C.W.; Funding acquisition, none. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data presented in this study are available on request from the corresponding author. The data are not publicly available due to privacy restrictions.
Conflicts of Interest
The authors declare no conflict of interest.
References
- DiCola, N. VLANs Are Not a Microsegmentation Strategy-Here’s Why You Need to Upgrade. Available online: https://zeronetworks.com/blog/vlans-are-not-a-microsegmentation-strategy (accessed on 15 June 2025).
- Rahman, M.; Piryani, K.O.; Sanchez, A.M.; Munikoti, S.; De La Torre, L.; Levin, M.S.; Akbar, M.; Hossain, M.; Hasan, M.; Halappanavar, M. Retrieval Augmented Generation for Robust Cyber Defense; Pacific Northwest National Laboratory (PNNL): Richland, WA, USA, 2024. [Google Scholar]
- Junior, C.R.; Becker, I.; Johnson, S. Unaware, unfunded and uneducated: A systematic review of SME cybersecurity. arXiv 2023, arXiv:2309.17186. [Google Scholar] [CrossRef]
- Hussain, B.; Elmedany, W.; Sharif, M.S. The Internet of Things Security Issues and Countermeasures in Network Layer: A Systematic Literature Review. In Proceedings of the 2022 International Conference on Data Analytics for Business and Industry (ICDABI), Sakhir, Bahrai, 25–26 October 2022; pp. 787–793. [Google Scholar]
- Bellamkonda, S. Zero Trust Architecture Implementation: Strategies, Challenges, and Best Practices. Int. J. Commun. Netw. Inf. Secur. 2022, 14, 587–591. [Google Scholar]
- DiCola, N. Network Segmentation vs. VLAN: Which Strategy Delivers True Security? Available online: https://zeronetworks.com/blog/network-segmentation-vs-vlan-strategy-security (accessed on 15 June 2025).
- Olaoye, G.; Luz, A.; John, O.; Akinleye, D. Network Segmentation and Micro-Segmentation Within Virtual Device Contexts. 2021. Available online: https://www.researchgate.net/publication/385788684_Network_Segmentation_and_Micro-Segmentation_within_Virtual_Device_Contexts (accessed on 15 June 2025).
- Kundimana, G.; Vyukusenge, A.; Tsym, A. Networks modernization using SDN and NFV technologies. In Proceedings of the 2021 Systems of Signals Generating and Processing in the Field of on Board Communications, Moscow, Russia, 16–18 March 2021; pp. 1–5. [Google Scholar]
- Dorsch, N.; Kurtz, F.; Wietfeld, C. On the economic benefits of software-defined networking and network slicing for smart grid communications. NETNOMICS Econ. Res. Electron. Netw. 2018, 19, 1–30. [Google Scholar] [CrossRef]
- Syed, N.F.; Shah, S.W.; Shaghaghi, A.; Anwar, A.; Baig, Z.; Doss, R. Zero trust architecture (ZTA): A comprehensive survey. IEEE Access 2022, 10, 57143–57179. [Google Scholar] [CrossRef]
- Bashi, Z.S.M.A.; Senan, S. A Comprehensive Review of Zero Trust Network Architecture (ZTNA) and Deployment Frameworks. Int. J. Perceptive Cogn. Comput. 2025, 11, 148–153. [Google Scholar] [CrossRef]
- Rose, S. Planning for a Zero Trust Architecture: A Planning Guide for Federal Administrators. National Institute of Standards and Technology White Paper 20, 2022. Available online: https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.20.pdf (accessed on 4 February 2026).
- González-Granadillo, G.; González-Zarzosa, S.; Diaz, R. Security information and event management (SIEM): Analysis, trends, and usage in critical infrastructures. Sensors 2021, 21, 4759. [Google Scholar] [CrossRef] [PubMed]
- SentinelOne, AI SecOps Implementation: Best Practices. 2025. Available online: https://www.sentinelone.com/cybersecurity-101/data-and-ai/ai-secops/ (accessed on 15 June 2025).
- Kurnia, R.; Widyatama, F.; Wibawa, I.M.; Brata, Z.A.; Nelistiani, G.A.; Kim, H. Enhancing Security Operations Center: Wazuh Security Event Response with Retrieval-Augmented-Generation-Driven. Sensors 2025, 25, 870. [Google Scholar] [CrossRef] [PubMed]
- Dearien, J.; Watkins, T. Migrating an Existing Network to OT SDN. Schweitzer Engineering Laboratories, Inc. White Paper, 2022. Available online: https://selinc.com/api/download/bltccb6632dcab34352 (accessed on 15 June 2025).
- Saura, P.F.; Jayaram, K.R.; Isahagian, V.; Bernabé, J.B.; Skarmeta, A. On Automating Security Policies with Contemporary LLMs. arXiv 2025, arXiv:2506.04838. [Google Scholar] [CrossRef]
- NetBox Labs. Available online: https://netboxlabs.com/ (accessed on 15 June 2025).
- ISO/IEC 27001:2022; Information Technology—Security Techniques—Information Security Management Systems—Requirements. International Organization for Standardization and International Electrotechnical Commission: Geneva, Switzerland, 2022.
- Rubicon Communications LLC (Netgate). Firewall Rule Best Practices. Available online: https://docs.netgate.com/pfsense/en/latest/firewall/best-practices.html (accessed on 15 June 2025).
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |