A Survey on Architectural Approaches for 6G Networks: Implementation Challenges, Current Trends, and Future Directions
Abstract
1. Introduction
1.1. Related Surveys
1.2. Contributions
- Integration of various technologies and key factors towards 6G architectural design. In the same context, potential limitations for each case are highlighted.
- Discussion of the current trends of 6G architectural design based on the presented works. To this end, the most important driving factors are also highlighted, such as AI/ML.
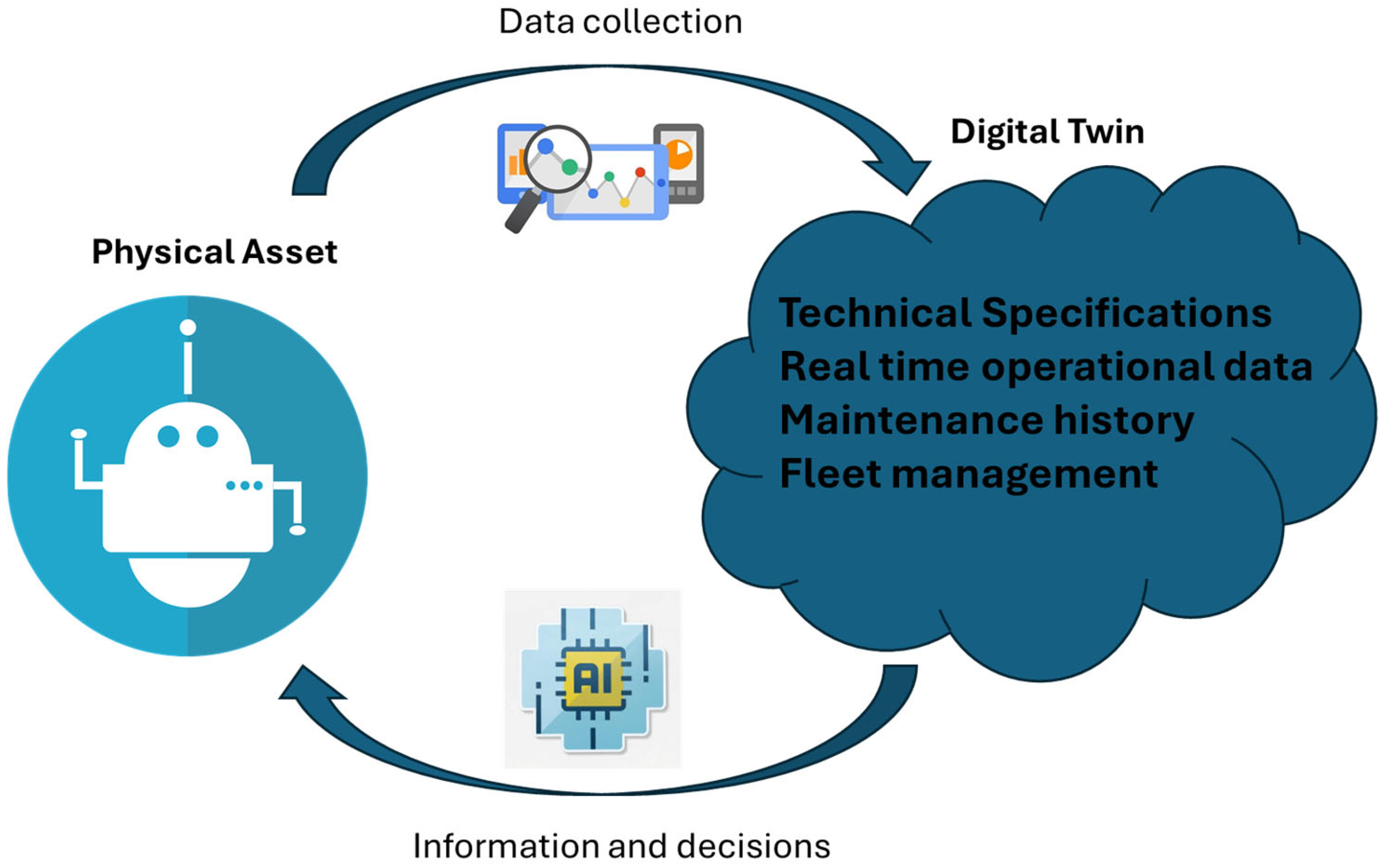
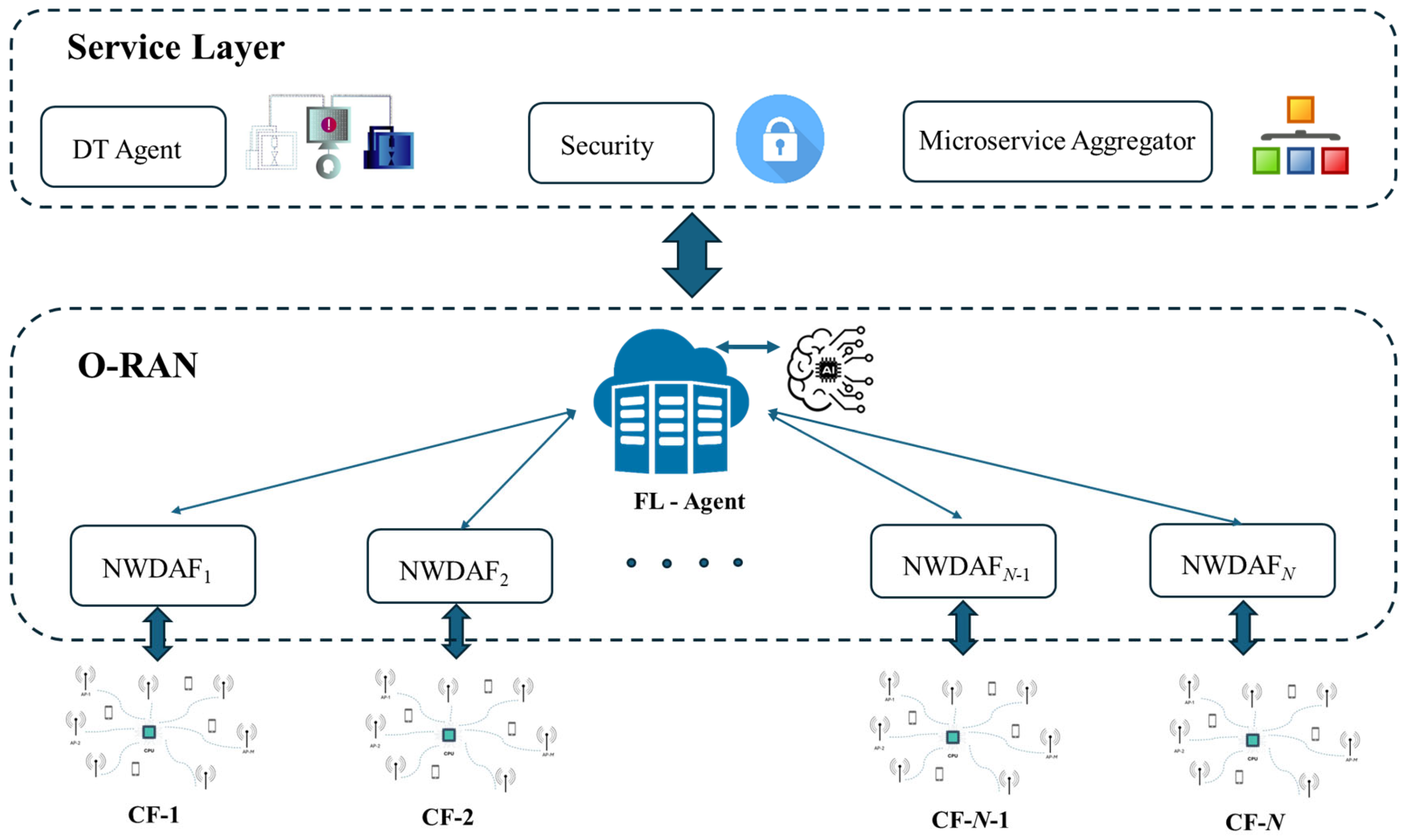
- Presentation of a high-level approach of the 6G concept that integrates secure data collection, flexible network deployment based on O-RAN specifications, privacy preserving decentralized machine learning, and digital twins and secure service provisioning. To this end, the synergy among well-established 5G network functions (NFs) is highlighted, such as the network data analytics function (NWDAF).
- Identification of limitations that should also be considered in the design and deployment of 6G networks.
2. 6G Key Enabling Technologies
2.1. AI/ML
2.2. Cell-Free Architectural Approaches
2.3. Advanced Physical-Layer Technologies
2.4. O-RAN
2.5. Blockchain Technology
2.6. Digital Twins
3. Architectural Approaches
4. Discussion—Open Issues
- Deployment capabilities and costs throughout large geographical areas. To this end, the support of ultra-high data rates with minimal latency necessitates dense deployments that may increase the cost of 6G infrastructures.
- In the same context, the 6G approach should be also adopted by lightweight devices that will have the capability to run light versions of the 6G architecture.
- Although ML models are a key innovation approach in 5G/6G networks, improved model performance is often accompanied by increased model complexity. In this context, a key innovation over the last few years is the concept of explainable artificial intelligence (XAI), a field that is concerned with the development of new methods that explain and interpret ML models [84,85]. The main focus is on the reasoning behind the decisions or predictions made by the AI algorithms to make them more understandable and transparent. Therefore, XAI assists in making ML models lead to decisions that are not based on irrelevant or otherwise unfair criteria.
- Integration of various cutting-edge technologies. As discussed thoroughly in this article, a key concept in 6G networks will be the integration of various technologies, both in the physical and in the network layer. Hence, a challenging issue would be to limit overall complexity and signaling burden. For example, since 6G networks involve the collection of a vast amount of data, appropriate processing algorithms are required that can effectively manage this volume. In the same context, more complex transceiver designs are required to support transmission in much larger frequencies compared to 5G, as is the concept of ultra-dense massive MIMO systems. Moreover, the adoption of certain technologies that facilitate the transition to the 6G era might come in contrast to other important features, such as security by design. For example, as discussed in this work, O-RAN introduces several potential security risks due to its open and disaggregated architecture.
- Coexistence with previous generations of networks. As also anticipated in the 5G era, the full transition to a new generation of networks will gradually take place. Until then, coexistence with well-established protocols is of utmost importance. In this case, one solution that has been proposed is the one in [78], where nested networks are formulated. In this context, small 6G cells can be deployed in areas with increased traffic distribution and can communicate with large 5G cells. However, there are not many works in the literature that, on the one hand, deal with the coexistence of 5G/6G and associated issues (e.g., handover and mobility management, resource allocation, etc.), and, on the other hand, with interference mitigation mechanisms. To this end, the work in [86] presents an interference analysis for the coexistence of terrestrial networks with satellite services. In this work, extensive simulations are carried out regarding cellular coexistence with low-earth-orbit (LEO) satellites in the 47.2–50.2 GHz band.
- Novel channel estimation techniques for THz communications. An efficient channel estimation is of vital importance to help THz communication systems achieve their full potential. Conventional channel estimation techniques that are used in currently established networks, such as least-squares algorithms in the uplink received signals, are practically inefficient for THz systems because of their large computation overhead.
- Energy harvesting strategies for low-power consumption networks. Since 6G networks deal with the integration of various low -power devices, there is a need to identify suitable energy-efficient mechanisms for such devices. To this end, energy harvesting is defined as the process of extracting energy from external network sources (e.g., solar energy) that is later either used to power network devices or is preserved for wireless autonomous devices, like wearable biomedical monitoring sensors.
- In the same context, ML models can also leverage energy efficiency in network design. To this end, a model can be trained to constantly monitor the network traffic and computational burden of each node in the network. Hence, this makes it possible to implement energy-saving techniques like turning down specific base stations or lowering their power consumption during these periods.
- Integration of non-terrestrial networks (NTNs) over 6G interfaces [87]. In this context, NTNs could supplement terrestrial 6G infrastructure by extending coverage to remote and under-served areas, where deploying traditional terrestrial networks is challenging or economically impractical. In the same framework, the potential of stringent IoT services worldwide is leveraged. In this context, a promising secure transmission technology rooted in information theory is wireless covert communication, which can conceal the presence of transmission so as to eliminate possible attack threats [88].
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| 3GPP | Third Generation Partnership Project |
| 5G | Fifth generation |
| 6G | Sixth generation |
| AI | Artificial intelligence |
| AP | Access point |
| API | Application programming interface |
| AR | Augmented reality |
| BS | Base station |
| CF | Cell free |
| CGC | City gateway cloud |
| CN | Core network |
| CU | Centralized unit |
| CP | Control plane |
| CPU | Central processing unit |
| CRAN | Cloud RAN |
| D2D | Device to device |
| DAS | Distributed antenna system |
| DL | Deep learning |
| DLT | Distributed ledger technology |
| DRL | Deep reinforcement learning |
| DT | Digital twin |
| DTE | Distributed trustable engine |
| DU | Distributed unit |
| eMBB | Enhanced mobile broadband |
| FH | Front haul |
| FL | Federated learning |
| FSO | Free space optical |
| IBI | Intent-based interface |
| IBN | Intent-based networking |
| IEC | IoT–edge–cloud |
| IoT | Internet of Things |
| IRS | Intelligent reflecting surface |
| ISAC | Integrated sensing and communication |
| JSAC | Joint sensing and communication |
| LEO | Low earth orbit |
| M2M | Machine to machine |
| MEC | Multi-access edge computing |
| MIMO | Multiple input multiple output |
| mMIMO | Massive MIMO |
| ML | Machine learning |
| mMTC | Massive machine-type communications |
| mmWave | Millimeter wave |
| MS | Mobile station |
| NF | Network function |
| NFV | Network function virtualization |
| NN | Neural network |
| NOMA | Non-orthogonal multiple access |
| O-RAN | Open radio access network |
| PQC | Post-quantum cryptography |
| QoS | Quality of service |
| RAN | Radio access network |
| RIC | RAN intelligent controller |
| RIS | Reconfigurable intelligent surface |
| RL | Reinforcement learning |
| RN | Relay node |
| RRM | Radio resource management |
| RU | Radio unit |
| RUPA | Recursive user plane architecture |
| SBA | Service-based architecture |
| SDN | Software-defined networking |
| SMO | Service management and orchestration |
| SSC | Smart sustainable city |
| THz | Terahertz |
| UDN | Ultra-dense networks |
| URLLC | Ultra-reliable low-latency communications |
| UP | User plane |
| VANET | Vehicular ad hoc network |
| V2X | Vehicle to everything |
| VR | Virtual reality |
| XAI | Explainable artificial intelligence |
References
- Popovski, P.; Trillingsgaard, K.F.; Simeone, O.; Durisi, G. 5G Wireless Network Slicing for eMBB, URLLC, and mMTC: A Communication-Theoretic View. IEEE Access 2018, 6, 55765–55779. [Google Scholar] [CrossRef]
- Khan, B.S.; Jangsher, S.; Ahmed, A.; Al-Dweik, A. URLLC and eMBB in 5G Industrial IoT: A Survey. IEEE Open J. Commun. Soc. 2022, 3, 1134–1163. [Google Scholar] [CrossRef]
- Chaudhary, U.; Ali, M.F.; Rajkumar, S.; Jayakody, D.N.K. Sensing and Secure NOMA-Assisted mMTC Wireless Networks. Electronics 2023, 12, 2322. [Google Scholar] [CrossRef]
- Bang, J.; Chung, H.; Hong, J.; Seo, H.; Choi, J.; Kim, S. Millimeter-Wave Communications: Recent Developments and Challenges of Hardware and Beam Management Algorithms. IEEE Commun. Mag. 2021, 59, 86–92. [Google Scholar] [CrossRef]
- Lee, B.M. Massive MIMO for Massive Industrial Internet of Things Networks: Operation, Performance, and Challenges. IEEE Trans. Cogn. Commun. Netw. 2024, 10, 2119–2135. [Google Scholar] [CrossRef]
- Ogundokun, R.O.; Awotunde, J.B.; Imoize, A.L.; Li, C.-T.; Abdulahi, A.T.; Adelodun, A.B.; Sur, S.N.; Lee, C.-C. Non-Orthogonal Multiple Access Enabled Mobile Edge Computing in 6G Communications: A Systematic Literature Review. Sustainability 2023, 15, 7315. [Google Scholar] [CrossRef]
- Adoga, H.U.; Pezaros, D.P. Network Function Virtualization and Service Function Chaining Frameworks: A Comprehensive Review of Requirements, Objectives, Implementations, and Open Research Challenges. Future Internet 2022, 14, 59. [Google Scholar] [CrossRef]
- Hussain, M.; Shah, N.; Amin, R.; Alshamrani, S.S.; Alotaibi, A.; Raza, S.M. Software-Defined Networking: Categories, Analysis, and Future Directions. Sensors 2022, 22, 5551. [Google Scholar] [CrossRef]
- Zieba, M.; Natkaniec, M.; Borylo, P. Cloud-Enabled Deployment of 5G Core Network with Analytics Features. Appl. Sci. 2024, 14, 7018. [Google Scholar] [CrossRef]
- Stoynov, V.; Poulkov, V.; Valkova-Jarvis, Z.; Iliev, G.; Koleva, P. Ultra-Dense Networks: Taxonomy and Key Performance Indicators. Symmetry 2023, 15, 2. [Google Scholar] [CrossRef]
- Pons, M.; Valenzuela, E.; Rodríguez, B.; Nolazco-Flores, J.A.; Del-Valle-Soto, C. Utilization of 5G Technologies in IoT Applications: Current Limitations by Interference and Network Optimization Difficulties—A Review. Sensors 2023, 23, 3876. [Google Scholar] [CrossRef] [PubMed]
- Gkagkas, G.; Vergados, D.J.; Michalas, A.; Dossis, M. The Advantage of the 5G Network for Enhancing the Internet of Things and the Evolution of the 6G Network. Sensors 2024, 24, 2455. [Google Scholar] [CrossRef] [PubMed]
- Giordani, M.; Polese, M.; Mezzavilla, M.; Rangan, S.; Zorzi, M. Toward 6G Networks: Use Cases and Technologies. IEEE Commun. Mag. 2020, 58, 55–61. [Google Scholar] [CrossRef]
- Siddiky, M.N.A.; Rahman, M.E.; Uzzal, M.S.; Kabir, H.M.D. A Comprehensive Exploration of 6G Wireless Communication Technologies. Computers 2025, 14, 15. [Google Scholar] [CrossRef]
- Kamath, S.; Anand, S.; Buchke, S.; Agnihotri, K. A Review of Recent Developments in 6G Communications Systems. Eng. Proc. 2023, 59, 167. [Google Scholar] [CrossRef]
- Bono, F.M.; Polinelli, A.; Radicioni, L.; Benedetti, L.; Castelli-Dezza, F.; Cinquemani, S.; Belloli, M. Wireless Accelerometer Architecture for Bridge SHM: From Sensor Design to System Deployment. Future Internet 2025, 17, 29. [Google Scholar] [CrossRef]
- Dala Pegorara Souto, V.; Dester, P.S.; Soares Pereira Facina, M.; Gomes Silva, D.; de Figueiredo, F.A.P.; Rodrigues de Lima Tejerina, G.; Silveira Santos Filho, J.C.; Silveira Ferreira, J.; Mendes, L.L.; Souza, R.D.; et al. Emerging MIMO Technologies for 6G Networks. Sensors 2023, 23, 1921. [Google Scholar] [CrossRef]
- Zhao, L.; Zhou, G.; Zheng, G.; You, X.; Hanzo, L. Open-Source Multi-Access Edge Computing for 6G: Opportunities and Challenges. IEEE Access 2021, 9, 158426–158439. [Google Scholar] [CrossRef]
- Leivadeas, A.; Falkner, M. A Survey on Intent-Based Networking. IEEE Commun. Surv. Tutor. 2023, 25, 625–655. [Google Scholar] [CrossRef]
- Chen, T.; Kuklinski, S.; Pateromichelakis, E.; Samdanis, K.; Kourtis, A.; Nikaein, N.; Skarmeta, A. Service-oriented Architecture Evolution towards 6G Networks. In Proceedings of the IEEE Conference on Standards for Communications and Networking (CSCN), Munich, Germany, 6–8 November 2023; pp. 8–14. [Google Scholar] [CrossRef]
- Erfanian, J.; Lister, D.; Zhao, Q.; Wikström, G.; Chen, Y. 6G Vision & Analysis of Potential Use Cases. IEEE Commun. Mag. 2023, 61, 12–14. [Google Scholar] [CrossRef]
- Gkonis, P.K.; Lavdas, S.; Vardoulias, G.; Trakadas, P.; Sarakis, L.; Papadopoulos, K. System Level Performance Assessment of Large-Scale Cell-Free Massive MIMO Orientations with Cooperative Beamforming. IEEE Access 2024, 12, 92073–92086. [Google Scholar] [CrossRef]
- Ayub Khan, A.; Laghari, A.A.; Baqasah, A.M.; Alroobaea, R.; Gadekallu, T.R.; Sampedro, G.A.; Zhu, Y. ORAN-B5G: A Next-Generation Open Radio Access Network Architecture with Machine Learning for Beyond 5G in Industrial 5.0. IEEE Trans. Green Commun. Netw. 2024, 8, 1026–1036. [Google Scholar] [CrossRef]
- Corici, M.-I.; Eichhorn, F.; Bless, R.; Gundall, M.; Lindenschmitt, D.; Bloessl, B.; Petrova, M.; Wimmer, L.; Kreuch, R.; Magedanz, T.; et al. Organic 6G Networks: Vision, Requirements, and Research Approaches. IEEE Access 2023, 11, 70698–70715. [Google Scholar] [CrossRef]
- Kehelwala, J.; Siriwardhana, Y.; Hewa, T.; Liyanage, M.; Ylianttila, M. Decentralized Learning for 6G Security: Open Issues and Future Directions. In Proceedings of the Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), Antwerp, Belgium, 3–6 June 2024; pp. 1175–1180. [Google Scholar] [CrossRef]
- Muscinelli, E.; Shinde, S.S.; Tarchi, D. Overview of Distributed Machine Learning Techniques for 6G Networks. Algorithms 2022, 15, 210. [Google Scholar] [CrossRef]
- Nomikos, N.; Xylouris, G.; Patsourakis, G.; Nikolakakis, V.; Giannopoulos, A.; Mandilaris, C.; Gkonis, P.; Skianis, C.; Trakadas, P. A Distributed Trustable Framework for AI-Aided Anomaly Detection. Electronics 2025, 14, 410. [Google Scholar] [CrossRef]
- Ismail, S.F.; Kadhim, D.J. Towards 6G Technology: Insights into Resource Management for Cloud RAN Deployment. IoT 2024, 5, 409–448. [Google Scholar] [CrossRef]
- Rojek, I.; Kotlarz, P.; Dorożyński, J.; Mikołajewski, D. Sixth-Generation (6G) Networks for Improved Machine-to-Machine (M2M) Communication in Industry 4.0. Electronics 2024, 13, 1832. [Google Scholar] [CrossRef]
- Jiang, W.; Zhou, Q.; He, J.; Habibi, M.A.; Melnyk, S.; El-Absi, M.; Han, B.; Di Renzo, M.; Schotten, H.D.; Luo, F.L.; et al. Terahertz Communications and Sensing for 6G and Beyond: A Comprehensive Review. IEEE Commun. Surv. Tutor. 2024, 26, 2326–2381. [Google Scholar] [CrossRef]
- Chataut, R.; Nankya, M.; Akl, R. 6G Networks and the AI Revolution—Exploring Technologies, Applications, and Emerging Challenges. Sensors 2024, 24, 1888. [Google Scholar] [CrossRef]
- Li, L. A Survey on Intelligence-Endogenous Network: Architecture and Technologies for Future 6G. Intell. Converg. Netw. 2024, 5, 53–67. [Google Scholar] [CrossRef]
- Giannopoulos, A.; Spantideas, S.; Kapsalis, N.; Karkazis, P.; Trakadas, P. Deep Reinforcement Learning for Energy-Efficient Multi-Channel Transmissions in 5G Cognitive HetNets: Centralized, Decentralized and Transfer Learning Based Solutions. IEEE Access 2021, 9, 129358–129374. [Google Scholar] [CrossRef]
- Adeogun, R.; Berardinelli, G. Multi-Agent Dynamic Resource Allocation in 6G in-X Subnetworks with Limited Sensing Information. Sensors 2022, 22, 5062. [Google Scholar] [CrossRef] [PubMed]
- Maduranga, M.W.P.; Tilwari, V.; Rathnayake, R.M.M.R.; Sandamini, C. AI-Enabled 6G Internet of Things: Opportunities, Key Technologies, Challenges, and Future Directions. Telecom 2024, 5, 804–822. [Google Scholar] [CrossRef]
- Liberti, F.; Berardi, D.; Martini, B. Federated Learning in Dynamic and Heterogeneous Environments: Advantages, Performances, and Privacy Problems. Appl. Sci. 2024, 14, 8490. [Google Scholar] [CrossRef]
- Papadopoulos, C.; Kollias, K.-F.; Fragulis, G.F. Recent Advancements in Federated Learning: State of the Art, Fundamentals, Principles, IoT Applications and Future Trends. Future Internet 2024, 16, 415. [Google Scholar] [CrossRef]
- Kassam, J.; Castanheira, D.; Silva, A.; Dinis, R.; Gameiro, A. A Review on Cell-Free Massive MIMO Systems. Electronics 2023, 12, 1001. [Google Scholar] [CrossRef]
- Bartsiokas, I.A.; Gkonis, P.K.; Kaklamani, D.I.; Venieris, I.S. A DL-Enabled Relay Node Placement and Selection Framework in Multicellular Networks. IEEE Access 2023, 11, 65153–65169. [Google Scholar] [CrossRef]
- Farhad, A.; Pyun, J.-Y. Terahertz Meets AI: The State of the Art. Sensors 2023, 23, 5034. [Google Scholar] [CrossRef]
- Boulogeorgos, A.-A.A.; Papasotiriou, E.N.; Alexiou, A. Analytical Performance Assessment of THz Wireless Systems. IEEE Access 2019, 7, 11436–11453. [Google Scholar] [CrossRef]
- Giannopoulos, A.; Spantideas, S.; Kapsalis, N.; Gkonis, P.; Sarakis, L.; Capsalis, C.; Vecchio, M.; Trakadas, P. Supporting Intelligence in Disaggregated Open Radio Access Networks: Architectural Principles, AI/ML Workflow, and Use Cases. IEEE Access 2022, 10, 39580–39595. [Google Scholar] [CrossRef]
- O-RAN Alliance. O-RAN AI/ML Workflow Description and Requirements, version 01.01; O-RAN Alliance: Alfter, Germany, 2020. [Google Scholar]
- O-RAN Working Group 3. O-RAN Near-Real-Time RAN Intelligent Controller Architecture & E2 General Aspects and Principles, version 1.01; O-RAN Working Group 3: Alfter, Germany, 2020. [Google Scholar]
- Pajooh, H.H.; Demidenko, S.; Aslam, S.; Harris, M. Blockchain and 6G-Enabled IoT. Inventions 2022, 7, 109. [Google Scholar] [CrossRef]
- Gkonis, P.; Giannopoulos, A.; Trakadas, P.; Masip-Bruin, X.; D’Andria, F. A Survey on IoT-Edge-Cloud Continuum Systems: Status, Challenges, Use Cases, and Open Issues. Future Internet 2023, 15, 383. [Google Scholar] [CrossRef]
- Zuo, Y.; Guo, J.; Gao, N.; Zhu, Y.; Jin, S.; Li, X. A Survey of Blockchain and Artificial Intelligence for 6G Wireless Communications. IEEE Commun. Surv. Tutor. 2023, 25, 2494–2528. [Google Scholar] [CrossRef]
- Nie, S.; Ren, J.; Wu, R.; Han, P.; Han, Z.; Wan, W. Zero-Trust Access Control Mechanism Based on Blockchain and Inner-Product Encryption in the Internet of Things in a 6G Environment. Sensors 2025, 25, 550. [Google Scholar] [CrossRef]
- Ma, Z.; Chen, X.; Sun, T.; Wang, X.; Wu, Y.C.; Zhou, M. Blockchain-Based Zero-Trust Supply Chain Security Integrated with Deep Reinforcement Learning for Inventory Optimization. Future Internet 2024, 16, 163. [Google Scholar] [CrossRef]
- Tao, Z.; Xu, W.; Huang, Y.; Wang, X.; You, X. Wireless Network Digital Twin for 6G: Generative AI as a Key Enabler. IEEE Wirel. Commun. 2024, 31, 24–31. [Google Scholar] [CrossRef]
- Qi, F.; Xie, W.; Liu, L.; Hong, T.; Zhou, F. UAV Digital Twin Based Wireless Channel Modeling for 6G Green IoT. Drones 2023, 7, 562. [Google Scholar] [CrossRef]
- Crespo-Aguado, M.; Lozano, R.; Hernandez-Gobertti, F.; Molner, N.; Gomez-Barquero, D. Flexible Hyper-Distributed IoT–Edge–Cloud Platform for Real-Time Digital Twin Applications on 6G-Intended Testbeds for Logistics and Industry. Future Internet 2024, 16, 431. [Google Scholar] [CrossRef]
- Berardinelli, G.; Mogensen, P.; Adeogun, R.O. 6G subnetworks for Life-Critical Communication. In Proceedings of the 2020 2nd 6G Wireless Summit (6G SUMMIT), Levi, Finland, 17–20 March 2020; pp. 1–5. [Google Scholar]
- Fu, Y.; Shan, Y.; Zhu, Q.; Hung, K.; Wu, Y.; Quek, T.Q.S. A Distributed Microservice-Aware Paradigm for 6G: Challenges, Principles, and Research Opportunities. IEEE Netw. 2024, 38, 163–170. [Google Scholar] [CrossRef]
- Corici, M.; Troudt, E.; Magedanz, T. An Organic 6G Core Network Architecture. In Proceedings of the 25th Conference on Innovation in Clouds, Internet and Networks (ICIN), Paris, France, 7–10 March 2022; pp. 1–7. [Google Scholar] [CrossRef]
- Granelli, F.; Qaisi, M.; Kapsalis, P.; Gkonis, P.; Nomikos, N.; Zacarias, I.; Jukan, A.; Trakadas, P. AI/ML-Assisted Threat Detection and Mitigation in 6G Networks with Digital Twins: The HORSE Approach. In Proceedings of the IEEE 29th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Athens, Greece, 21–23 October 2024. [Google Scholar]
- Girelli Consolaro, N.; Shinde, S.S.; Naseh, D.; Tarchi, D. Analysis and Performance Evaluation of Transfer Learning Algorithms for 6G Wireless Networks. Electronics 2023, 12, 3327. [Google Scholar] [CrossRef]
- Tripi, G.; Iacobelli, A.; Rinieri, L.; Prandini, M. Security and Trust in the 6G Era: Risks and Mitigations. Electronics 2024, 13, 2162. [Google Scholar] [CrossRef]
- Alwakeel, A.M.; Alnaim, A.K. Network Slicing in 6G: A Strategic Framework for IoT in Smart Cities. Sensors 2024, 24, 4254. [Google Scholar] [CrossRef] [PubMed]
- Zong, J.; Liu, Y.; Liu, H.; Wang, Q.; Chen, P. 6G Cell-Free Network Architecture. In Proceedings of the IEEE 2nd International Conference on Electronic Technology, Communication and Information (ICETCI), Changchun, China, 27–29 May 2022; pp. 421–425. [Google Scholar] [CrossRef]
- Mitra, P.; Bhattacharjee, R.; Chatterjee, T.; De, S.; Karmakar, R.; Ghosh, A.; Adhikari, T. Towards 6G Communications: Architecture, Challenges, and Future Directions. In Proceedings of the 12th International Conference on Computing Communication and Networking Technologies (ICCCNT), Kharagpur, India, 6–8 July 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Polese, M.; Dohler, M.; Dressler, F.; Erol-Kantarci, M.; Jana, R.; Knopp, R.; Melodia, T. Empowering the 6G Cellular Architecture with Open RAN. IEEE J. Sel. Areas Commun. 2024, 42, 245–262. [Google Scholar] [CrossRef]
- Bao, S.; Sun, W.; Xu, H. A Native Intelligent and Security 6G Network Architecture. In Proceedings of the IEEE/CIC International Conference on Communications in China (ICCC Workshops), Sanshui, Foshan, China, 7–9 August 2022; pp. 395–400. [Google Scholar] [CrossRef]
- Duan, X.D.; Wang, X.Y.; Lu, L.; Shi, N.X.; Liu, C.; Zhang, T.; Sun, T. 6G Architecture Design: From Overall, Logical and Networking Perspective. IEEE Commun. Mag. 2023, 61, 158–164. [Google Scholar] [CrossRef]
- Vizzarri, A.; Mazzenga, F. 6G Use Cases and Scenarios: A Comparison Analysis Between ITU and Other Initiatives. Future Internet 2024, 16, 404. [Google Scholar] [CrossRef]
- Wang, X.; Liu, C.; He, J.; Shi, N.; Zhang, T.; Pan, X. 6G Network Architecture Based on Digital Twin: Modeling, Evaluation, and Optimization. IEEE Netw. 2024, 38, 15–21. [Google Scholar] [CrossRef]
- Giménez-Antón, S.; Grasa, E.; Perelló, J.; Cárdenas, A. 6G-RUPA: A Flexible, Scalable, and Energy-Efficient User Plane Architecture for Next-Generation Mobile Networks. Computers 2024, 13, 186. [Google Scholar] [CrossRef]
- An, X.; Wu, J.; Tong, W.; Zhu, P.; Chen, Y. 6G Network Architecture Vision. In Proceedings of the Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), Porto, Portugal, 3–6 June 2021; pp. 592–597. [Google Scholar] [CrossRef]
- Ericson, M.; Condoluci, M.; Rugeland, P.; Wänstedt, S.; Abad, M.S.; Haliloglu, O.; Saimler, M.; Feltrin, L. 6G Architectural Trends and Enablers. In Proceedings of the IEEE 4th 5G World Forum (5GWF), Montreal, QC, Canada, 13–15 October 2021; pp. 406–411. [Google Scholar] [CrossRef]
- Lu, L.; Liu, C.; Zhang, C.; Hu, Z.; Lin, S.; Liu, Z.; Zhang, M.; Liu, X.; Chen, J. Architecture for Self-Evolution of 6G Core Network Based on Intelligent Decision Making. Electronics 2023, 12, 3255. [Google Scholar] [CrossRef]
- Liu, B.; Luo, J.; Su, X. The Framework of 6G Self-Evolving Networks and the Decision-Making Scheme for Massive IoT. Appl. Sci. 2021, 11, 9353. [Google Scholar] [CrossRef]
- Ziegler, V.; Viswanathan, H.; Flinck, H.; Hoffmann, M.; Räisänen, V.; Hätönen, K. 6G Architecture to Connect the Worlds. IEEE Access 2020, 8, 173508–173520. [Google Scholar] [CrossRef]
- Hoffmann, M.; Kunzmann, G.; Dudda, T.; Irmer, R.; Jukan, A.; Macher, G.; Ahmad, A.; Beenen, F.R.; Bröring, A.; Fellhauer, F.; et al. A Secure and Resilient 6G Architecture Vision of the German Flagship Project 6G-ANNA. IEEE Access 2023, 11, 102643–102660. [Google Scholar] [CrossRef]
- Singh, M.; Pottoo, S.N.; Armghan, A.; Aliqab, K.; Alsharari, M.; Abd El-Mottaleb, S.A. 6G Network Architecture Using FSO-PDM/PV-OCDMA System with Weather Performance Analysis. Appl. Sci. 2022, 12, 11374. [Google Scholar] [CrossRef]
- Habibi, M.A.; Han, B.; Fellan, A.; Jiang, W.; Sánchez, A.G.; Pavon, I.L.; Boubendir, A.; Schotten, H.D. Toward an Open, Intelligent, and End-to-End Architectural Framework for Network Slicing in 6G Communication Systems. IEEE Open J. Commun. Soc. 2023, 4, 1615–1658. [Google Scholar] [CrossRef]
- Kim, N.; Kim, G.; Shim, S.; Jang, S.; Song, J.; Lee, B. Key Technologies for 6G-Enabled Smart Sustainable City. Electronics 2024, 13, 268. [Google Scholar] [CrossRef]
- Sharma, S.; Popli, R.; Singh, S.; Chhabra, G.; Saini, G.S.; Singh, M.; Sandhu, A.; Sharma, A.; Kumar, R. The Role of 6G Technologies in Advancing Smart City Applications: Opportunities and Challenges. Sustainability 2024, 16, 7039. [Google Scholar] [CrossRef]
- Farooq, M.S.; Nadir, R.M.; Rustam, F.; Hur, S.; Park, Y.; Ashraf, I. Nested Bee Hive: A Conceptual Multilayer Architecture for 6G in Futuristic Sustainable Smart Cities. Sensors 2022, 22, 5950. [Google Scholar] [CrossRef]
- Akgul, O.U.; Ericson, M.; Burguera, P.G.; Arar, B.; Khorsandi, B.M.; Querio, R.; Varvara, A.; Harkous, H.; Wänstedt, S.; Groshev, M.; et al. Discussion on 6G Architecture Evolution: Challenges and Emerging Technology Trends. In Proceedings of the Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), Antwerp, Belgium, 3–6 June 2024; pp. 664–669. [Google Scholar] [CrossRef]
- Szilagyi, P.; Contreras-Murillo, L.M.; Menéndez, D.R.; Giardina, P.; De la Oliva, A. 6G Architecture for Enabling Predictable, Reliable and Deterministic Networks: The PREDICT6G Case. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Dubai, United Arab Emirates, 21–24 April 2024. [Google Scholar] [CrossRef]
- Serôdio, C.; Cunha, J.; Candela, G.; Rodriguez, S.; Sousa, X.R.; Branco, F. The 6G Ecosystem as Support for IoE and Private Networks: Vision, Requirements, and Challenges. Future Internet 2023, 15, 348. [Google Scholar] [CrossRef]
- ETSI TS 129 520, 3GPP; Network Data Analytics Services, Release 15. European Telecommunications Standards Institute: Sophia Antipolis, France, 2019.
- Gkonis, P.K.; Nomikos, N.; Trakadas, P.; Sarakis, L.; Xylouris, G.; Masip-Bruin, X.; Martrat, J. Leveraging Network Data Analytics Function and Machine Learning for Data Collection, Resource Optimization, Security and Privacy in 6G Networks. IEEE Access 2024, 12, 21320–21336. [Google Scholar] [CrossRef]
- Linardatos, P.; Papastefanopoulos, V.; Kotsiantis, S. Explainable AI: A Review of Machine Learning Interpretability Methods. Entropy 2021, 23, 18. [Google Scholar] [CrossRef]
- Hamida, S.U.; Chowdhury, M.J.M.; Chakraborty, N.R.; Biswas, K.; Sami, S.K. Exploring the Landscape of Explainable Artificial Intelligence (XAI): A Systematic Review of Techniques and Applications. Big Data Cogn. Comput. 2024, 8, 149. [Google Scholar] [CrossRef]
- Lim, Β.; Vu, M. Interference Analysis for Coexistence of Terrestrial Networks with Satellite Services. IEEE Trans. Wirel. Commun. 2024, 23, 3146–3161. [Google Scholar] [CrossRef]
- An, J.; Kang, B.; Ouyang, Q.; Pan, J.; Ye, N. Covert Communications Meet 6G NTN: A Comprehensive Enabler for Safety-Critical IoT. IEEE Netw. 2024, 38, 17–24. [Google Scholar] [CrossRef]
- Qiao, G.; Bilal, M.; Liu, S.; Babar, Z.; Ma, Z. Biologically inspired covert underwater acoustic communication—A review. Phys. Commun. 2018, 30, 107–114. [Google Scholar] [CrossRef]







| Related Work | Year | Topic | Key Contributions |
|---|---|---|---|
| [28] | 2024 | CRAN | Resource management in CRAN Machine learning in 6G |
| [29] | 2024 | M2M communications in the 6G era | Security and privacy concerns Integration with edge computing |
| [30] | 2024 | Joint sensing and communication in the 6G era | Transceiver requirements Antenna design and beamforming for high path loss compensation |
| [31] | 2024 | Key enabling technologies for 6G networks Potential of AI/ML | The role of AI in 6G networks Critical challenges in the deployment of 6G |
| [32] | 2024 | AI-enabled 6G networks | Architecture of endogenous networks Applications of AI in intelligence-endogenous 6G networks |
| Our work | - | Current trends in the architectural design of 6G networks | State-of-the-art approaches to the architectural design of 6G networks A high-level approach to 6G network architecture |
| Related Work | Main Concept | Key 6G-Enabling Technologies | ||||
|---|---|---|---|---|---|---|
| AI/ML | Digital Twins | Open Interfaces | Network Slicing | Cell-Free Approaches | ||
| [55] | Organic 6G networks | √ | ||||
| [56] | Threat prediction and mitigation | √ | √ | |||
| [59] | Network slicing | √ | ||||
| [60] | Cell-free networks | √ | ||||
| [61] | 6G vision | √ | ||||
| [62] | Open RAN | √ | √ | |||
| [63] | Multi-layered architecture | √ | √ | √ | ||
| [64] | 6G multi-layer vision | √ | √ | |||
| [66] | 6G architectural design based on DTs | √ | ||||
| [67] | Flexible layered architecture | √ | √ | |||
| [68] | Basic 6G trends | √ | √ | |||
| [70] | Self-evolving 6G networks | √ | ||||
| [71] | Deep reinforcement learning in 6G networks | √ | ||||
| [72] | Building blocks for 6G | √ | √ | |||
| [73] | 6G project ANNA | √ | √ | |||
| [75] | Slicing concept in 6G | √ | √ | √ | ||
| [76] | 6G for smart cities | √ | ||||
| [77] | 6G for smart cities | √ | ||||
| [78] | 6G for smart cities | √ | ||||
| [79] | Current 6G trends | √ | √ | |||
| [80] | PREDICT-6G | √ | √ | |||
| [81] | Advanced 6G use cases | √ | √ | |||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gkonis, P.K.; Giannopoulos, A.; Nomikos, N.; Trakadas, P.; Sarakis, L.; Masip-Bruin, X. A Survey on Architectural Approaches for 6G Networks: Implementation Challenges, Current Trends, and Future Directions. Telecom 2025, 6, 27. https://doi.org/10.3390/telecom6020027
Gkonis PK, Giannopoulos A, Nomikos N, Trakadas P, Sarakis L, Masip-Bruin X. A Survey on Architectural Approaches for 6G Networks: Implementation Challenges, Current Trends, and Future Directions. Telecom. 2025; 6(2):27. https://doi.org/10.3390/telecom6020027
Chicago/Turabian StyleGkonis, Panagiotis K., Anastasios Giannopoulos, Nikolaos Nomikos, Panagiotis Trakadas, Lambros Sarakis, and Xavi Masip-Bruin. 2025. "A Survey on Architectural Approaches for 6G Networks: Implementation Challenges, Current Trends, and Future Directions" Telecom 6, no. 2: 27. https://doi.org/10.3390/telecom6020027
APA StyleGkonis, P. K., Giannopoulos, A., Nomikos, N., Trakadas, P., Sarakis, L., & Masip-Bruin, X. (2025). A Survey on Architectural Approaches for 6G Networks: Implementation Challenges, Current Trends, and Future Directions. Telecom, 6(2), 27. https://doi.org/10.3390/telecom6020027










