A Review on Models and Applications of Quantum Computing
Abstract
1. Introduction
2. Theoretical Foundations
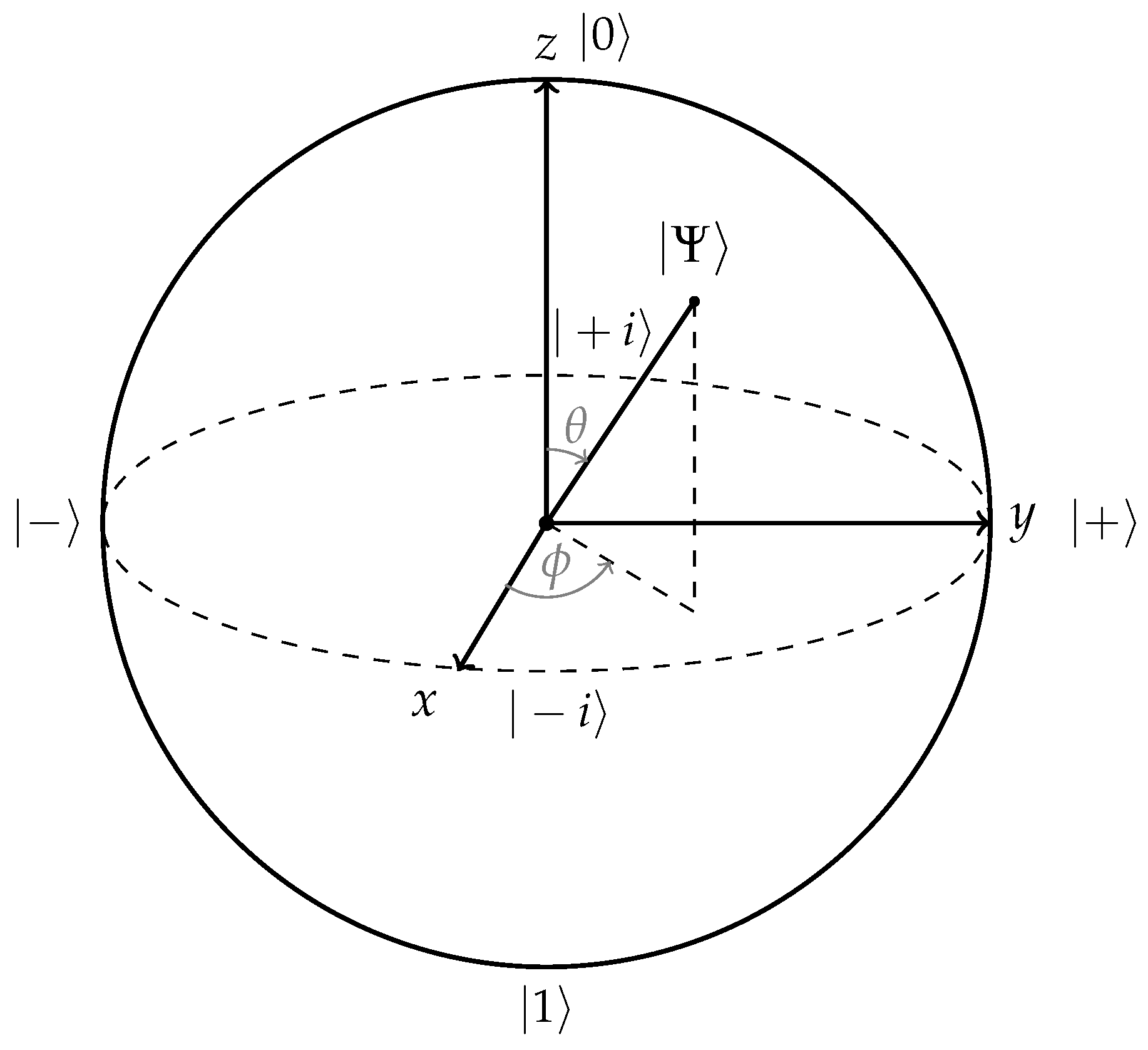
2.1. Qubits and Superposition
2.2. Entanglement
2.3. No-Cloning Theorem
3. Quantum Computation Models
3.1. Gate Model
3.2. Quantum Adiabatic Model
3.3. Measurement-Based Quantum Computation
3.4. Quantum Turing Machine
- Q is a finite set of internal (control) states;
- is a finite tape alphabet containing a blank symbol, #;
- is the transition function, a map defining amplitudes of transitions:
- is the initial state;
- is the accepting state;
- is the rejecting state ();
- is the Hilbert space spanned by basis states:where , is the tape content, and is the position of the head.
4. Quantum Algorithms
4.1. Quantum Search
4.2. Quantum Factoring
4.3. Quantum Singular Value Transformation
5. Quantum Machine Learning
5.1. Quantum Hopfield Networks
5.2. Quantum Support Vector Machines (QSVMs)
6. Software Ecosystem
6.1. Case Study: QSVM vs. Classical SVM
6.2. Limitations
7. Conclusions and Future Prospects
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Benioff, P. Quantum mechanical Hamiltonian models of Turing machines. J. Stat. Phys. 1982, 29, 515–546. [Google Scholar] [CrossRef]
- Feynman, R.P. Simulating Physics with Computers. Int. J. Theor. Phys. 1982, 21, 467–488. [Google Scholar] [CrossRef]
- Deutsch, D. Quantum theory, the Church–Turing principle and the universal quantum computer. Proc. R. Soc. London. A. Math. Phys. Sci. 1985, 400, 97–117. [Google Scholar]
- Preskill, J. Quantum computing in the NISQ era and beyond. Quantum 2018, 2, 79. [Google Scholar] [CrossRef]
- Barkoutsos, P.K.; Gonthier, J.F.; Sokolov, I.; Moll, N.; Salis, G.; Fuhrer, A.; Ganzhorn, M.; Egger, D.J.; Troyer, M.; Mezzacapo, A.; et al. Quantum algorithms for electronic structure calculations: Particle-hole Hamiltonian and optimized wave-function expansions. Phys. Rev. A 2018, 98, 022322. [Google Scholar] [CrossRef]
- Farhi, E.; Goldstone, J.; Gutmann, S. A quantum approximate optimization algorithm. arXiv 2014, arXiv:1411.4028. [Google Scholar] [CrossRef]
- Cerezo, M.; Arrasmith, A.; Babbush, R.; Benjamin, S.C.; Endo, S.; Fujii, K.; McClean, J.R.; Mitarai, K.; Yuan, X.; Cincio, L.; et al. Variational quantum algorithms. Nat. Rev. Phys. 2021, 3, 625–644. [Google Scholar] [CrossRef]
- Main, D.; Drmota, P.; Nadlinger, D.; Ainley, E.; Agrawal, A.; Nichol, B.; Srinivas, R.; Araneda, G.; Lucas, D. Distributed quantum computing across an optical network link. Nature 2025, 638, 383–388. [Google Scholar] [CrossRef]
- Gill, S.S.; Kumar, A.; Singh, H.; Singh, M.; Kaur, K.; Usman, M.; Buyya, R. Quantum computing: A taxonomy, systematic review and future directions. Software Pract. Exp. 2022, 52, 66–114. [Google Scholar] [CrossRef]
- Gill, S.S.; Cetinkaya, O.; Marrone, S.; Claudino, D.; Haunschild, D.; Schlote, L.; Wu, H.; Ottaviani, C.; Liu, X.; Machupalli, S.P.; et al. Quantum computing: Vision and challenges. In Quantum Computing; Elsevier: Amsterdam, The Netherlands, 2025; pp. 19–42. [Google Scholar]
- Paudel, H.P.; Syamlal, M.; Crawford, S.E.; Lee, Y.L.; Shugayev, R.A.; Lu, P.; Ohodnicki, P.R.; Mollot, D.; Duan, Y. Quantum computing and simulations for energy applications: Review and perspective. ACS Eng. Au 2022, 2, 151–196. [Google Scholar] [CrossRef]
- Rietsche, R.; Dremel, C.; Bosch, S.; Steinacker, L.; Meckel, M.; Leimeister, J.M. Quantum computing. Electron. Mark. 2022, 32, 2525–2536. [Google Scholar] [CrossRef]
- Putranto, D.S.C.; Wardhani, R.W.; Ji, J.; Kim, H. A Deep Inside Quantum Technology Industry Trends and Future Implications. IEEE Access 2024, 12, 115776–115801. [Google Scholar] [CrossRef]
- Javadi-Abhari, A.; Treinish, M.; Krsulich, K.; Wood, C.J.; Lishman, J.; Gacon, J.; Martiel, S.; Nation, P.D.; Bishop, L.S.; Cross, A.W.; et al. Quantum computing with Qiskit. arXiv 2024, arXiv:2405.08810. [Google Scholar] [CrossRef]
- Griffiths, D.J.; Schroeter, D.F. Introduction to Quantum Mechanics; Cambridge University Press: Cambridge, UK, 2018. [Google Scholar]
- Yanofsky, N.S.; Mannucci, M.A. Quantum computing for Computer Scientists; Cambridge University Press: Cambridge, UK, 2008. [Google Scholar]
- Blais, A.; Grimsmo, A.L.; Girvin, S.M.; Wallraff, A. Circuit quantum electrodynamics. Rev. Mod. Phys. 2021, 93, 025005. [Google Scholar] [CrossRef]
- Manzano, D. A short introduction to the Lindblad master equation. Aip Adv. 2020, 10, 025106. [Google Scholar] [CrossRef]
- Coles, P.J.; Berta, M.; Tomamichel, M.; Wehner, S. Entropic uncertainty relations and their applications. Rev. Mod. Phys. 2017, 89, 015002. [Google Scholar] [CrossRef]
- Caspani, L.; Xiong, C.; Eggleton, B.J.; Bajoni, D.; Liscidini, M.; Galli, M.; Morandotti, R.; Moss, D.J. Integrated sources of photon quantum states based on nonlinear optics. Light. Sci. Appl. 2017, 6, e17100. [Google Scholar] [CrossRef] [PubMed]
- Zhang, C.; Huang, Y.F.; Liu, B.H.; Li, C.F.; Guo, G.C. Spontaneous parametric down-conversion sources for multiphoton experiments. Adv. Quantum Technol. 2021, 4, 2000132. [Google Scholar] [CrossRef]
- Li, B.; Yuan, Z.; Williams, J.; Jin, W.; Beckert, A.; Xie, T.; Guo, J.; Feshali, A.; Paniccia, M.; Faraon, A.; et al. Down-converted photon pairs in a high-Q silicon nitride microresonator. Nature 2025, 639, 922–927. [Google Scholar] [CrossRef] [PubMed]
- Krstić, A.; Setzpfandt, F.; Saravi, S. Nonperturbative theory of spontaneous parametric down-conversion in open and dispersive optical systems. Phys. Rev. Res. 2023, 5, 043228. [Google Scholar] [CrossRef]
- Scala, F.; Nigro, D.; Gerace, D. Deterministic entangling gates with nonlinear quantum photonic interferometers. Commun. Phys. 2024, 7, 118. [Google Scholar] [CrossRef]
- Zhang, Z.; Scully, M.O.; Agarwal, G.S. Quantum entanglement between two magnon modes via Kerr nonlinearity driven far from equilibrium. Phys. Rev. Res. 2019, 1, 023021. [Google Scholar] [CrossRef]
- Massembele, D.K.; Djorwé, P.; Sarma, A.K.; Abdel-Aty, A.H.; Engo, S.N. Quantum entanglement assisted via Duffing nonlinearity. Phys. Rev. A 2024, 110, 043502. [Google Scholar] [CrossRef]
- Lyu, X.; Kallioniemi, L.; Cai, H.; An, L.; Duan, R.; Wu, S.J.; Tan, Q.; Zhang, C.; He, R.; Miao, Y.; et al. Boosting classical and quantum nonlinear processes in ultrathin van der Waals materials. Nat. Commun. 2025, 16, 4987. [Google Scholar] [CrossRef]
- Akin, J.; Zhao, Y.; Kwiat, P.G.; Goldschmidt, E.A.; Fang, K. Faithful quantum teleportation via a nanophotonic nonlinear Bell state analyzer. Phys. Rev. Lett. 2025, 134, 160802. [Google Scholar] [CrossRef] [PubMed]
- Fabre, C.; Treps, N. Modes and states in quantum optics. Rev. Mod. Phys. 2020, 92, 035005. [Google Scholar] [CrossRef]
- Wootters, W.K.; Zurek, W.H. A single quantum cannot be cloned. Nature 1982, 299, 802–803. [Google Scholar] [CrossRef]
- Dieks, D. Communication by EPR devices. Phys. Lett. A 1982, 92, 271–272. [Google Scholar] [CrossRef]
- Pan, D.; Long, G.L.; Yin, L.; Sheng, Y.B.; Ruan, D.; Ng, S.X.; Lu, J.; Hanzo, L. The evolution of quantum secure direct communication: On the road to the qinternet. IEEE Commun. Surv. Tutorials 2024, 26, 1898–1949. [Google Scholar] [CrossRef]
- Zhou, L.; Xu, B.W.; Zhong, W.; Sheng, Y.B. Device-independent quantum secure direct communication with single-photon sources. Phys. Rev. Appl. 2023, 19, 014036. [Google Scholar] [CrossRef]
- Zhao, P.; Zhong, W.; Du, M.M.; Li, X.Y.; Zhou, L.; Sheng, Y.B. Quantum secure direct communication with hybrid entanglement. Front. Phys. 2024, 19, 51201. [Google Scholar] [CrossRef]
- Deutsch, D.E. Quantum computational networks. Proc. R. Soc. London. A. Math. Phys. Sci. 1989, 425, 73–90. [Google Scholar]
- Landauer, R. Irreversibility and heat generation in the computing process. IBM J. Res. Dev. 1961, 5, 183–191. [Google Scholar] [CrossRef]
- Born, M.; Fock, V. Beweis des adiabatensatzes. Z. Für Phys. 1928, 51, 165–180. [Google Scholar] [CrossRef]
- Farhi, E.; Goldstone, J.; Gutmann, S.; Sipser, M. Quantum computation by adiabatic evolution. arXiv 2000, arXiv:quantph/0001106. [Google Scholar]
- Aharonov, D.; Van Dam, W.; Kempe, J.; Landau, Z.; Lloyd, S.; Regev, O. Adiabatic quantum computation is equivalent to standard quantum computation. SIAM Rev. 2008, 50, 755–787. [Google Scholar] [CrossRef]
- Sarovar, M.; Young, K.C. Error suppression and error correction in adiabatic quantum computation: Non-equilibrium dynamics. New J. Phys. 2013, 15, 125032. [Google Scholar] [CrossRef]
- Albash, T.; Lidar, D.A. Adiabatic quantum computation. Rev. Mod. Phys. 2018, 90, 015002. [Google Scholar] [CrossRef]
- Schiffer, B.F.; Tura, J.; Cirac, J.I. Adiabatic spectroscopy and a variational quantum adiabatic algorithm. PRX Quantum 2022, 3, 020347. [Google Scholar] [CrossRef]
- Dooley, S.; Kells, G.; Katsura, H.; Dorlas, T.C. Simulating quantum circuits by adiabatic computation: Improved spectral gap bounds. Phys. Rev. A 2020, 101, 042302. [Google Scholar] [CrossRef]
- Crosson, E.; Lidar, D. Prospects for quantum enhancement with diabatic quantum annealing. Nat. Rev. Phys. 2021, 3, 466–489. [Google Scholar] [CrossRef]
- Hastings, M.B. Quantum adiabatic computation with a constant gap is not useful in one dimension. Phys. Rev. Lett. 2009, 103, 050502. [Google Scholar] [CrossRef]
- Yao, J.; Lin, L.; Bukov, M. Reinforcement learning for many-body ground-state preparation inspired by counterdiabatic driving. Phys. Rev. X 2021, 11, 031070. [Google Scholar] [CrossRef]
- Torrontegui, E.; Martínez-Garaot, S.; Ruschhaupt, A.; Muga, J.G. Shortcuts to adiabaticity: Fast-forward approach. Phys. Rev. A Atomic Mol. Opt. Phys. 2012, 86, 013601. [Google Scholar] [CrossRef]
- Raussendorf, R.; Briegel, H.J. A one-way quantum computer. Phys. Rev. Lett. 2001, 86, 5188. [Google Scholar] [CrossRef] [PubMed]
- Raussendorf, R.; Browne, D.E.; Briegel, H.J. Measurement-based quantum computation on cluster states. Phys. Rev. A 2003, 68, 022312. [Google Scholar] [CrossRef]
- Wei, T.C. Measurement-based quantum computation. arXiv 2021, arXiv:2109.10111. [Google Scholar]
- Lanyon, B.; Jurcevic, P.; Zwerger, M.; Hempel, C.; Martinez, E.; Dür, W.; Briegel, H.; Blatt, R.; Roos, C.F. Measurement-based quantum computation with trapped ions. Phys. Rev. Lett. 2013, 111, 210501. [Google Scholar] [CrossRef]
- Else, D.V.; Schwarz, I.; Bartlett, S.D.; Doherty, A.C. Symmetry-protected phases for measurement-based quantum computation. Phys. Rev. Lett. 2012, 108, 240505. [Google Scholar] [CrossRef]
- Larsen, M.V.; Chamberland, C.; Noh, K.; Neergaard-Nielsen, J.S.; Andersen, U.L. Fault-tolerant continuous-variable measurement-based quantum computation architecture. Prx Quantum 2021, 2, 030325. [Google Scholar] [CrossRef]
- Lee, S.H.; Jeong, H. Universal hardware-efficient topological measurement-based quantum computation via color-code-based cluster states. Phys. Rev. Res. 2022, 4, 013010. [Google Scholar] [CrossRef]
- Yamasaki, H.; Fukui, K.; Takeuchi, Y.; Tani, S.; Koashi, M. Polylog-overhead highly fault-tolerant measurement-based quantum computation: All-Gaussian implementation with Gottesman-Kitaev-Preskill code. arXiv 2020, arXiv:2006.05416. [Google Scholar]
- Majumder, A.; Krumm, M.; Radkohl, T.; Fiderer, L.J.; Nautrup, H.P.; Jerbi, S.; Briegel, H.J. Variational measurement-based quantum computation for generative modeling. Phys. Rev. A 2024, 110, 062616. [Google Scholar] [CrossRef]
- Bernstein, E.; Vazirani, U. Quantum complexity theory. In Proceedings of the Twenty-Fifth Annual ACM Symposium on Theory of Computing, San Diego, CA, USA, 16–18 May 1993; pp. 11–20. [Google Scholar]
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996; pp. 212–219. [Google Scholar]
- Brassard, G.; Hoyer, P.; Mosca, M.; Tapp, A. Quantum amplitude amplification and estimation. arXiv 2000, arXiv:quantph/0005055. [Google Scholar]
- Bennett, C.H.; Bernstein, E.; Brassard, G.; Vazirani, U. Strengths and weaknesses of quantum computing. SIAM J. Comput. 1997, 26, 1510–1523. [Google Scholar] [CrossRef]
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Kitaev, A.Y. Quantum computations: Algorithms and error correction. Russ. Math. Surv. 1997, 52, 1191. [Google Scholar] [CrossRef]
- Gidney, C.; Ekerå, M. How to factor 2048 bit RSA integers in 8 hours using 20 million noisy qubits. Quantum 2021, 5, 433. [Google Scholar] [CrossRef]
- Gilyén, A.; Su, Y.; Low, G.H.; Wiebe, N. Quantum singular value transformation and beyond: Exponential improvements for quantum matrix arithmetics. In Proceedings of the 51st Annual ACM SIGACT Symposium on Theory of Computing, Phoenix, AZ, USA, 23–26 June 2019; pp. 193–204. [Google Scholar]
- Haah, J. Product decomposition of periodic functions in quantum signal processing. Quantum 2019, 3, 190. [Google Scholar] [CrossRef]
- Gharibian, S.; Le Gall, F. Dequantizing the quantum singular value transformation: Hardness and applications to quantum chemistry and the quantum PCP conjecture. In Proceedings of the 54th Annual ACM SIGACT Symposium on Theory of Computing, Rome, Italy, 20–24 June 2022; pp. 19–32. [Google Scholar]
- Hopfield, J.J. Neural networks and physical systems with emergent collective computational abilities. Proc. Natl. Acad. Sci. USA 1982, 79, 2554–2558. [Google Scholar] [CrossRef] [PubMed]
- Folli, V.; Leonetti, M.; Ruocco, G. On the maximum storage capacity of the Hopfield model. Front. Comput. Neurosci. 2017, 10, 144. [Google Scholar] [CrossRef] [PubMed]
- Rebentrost, P.; Bromley, T.R.; Weedbrook, C.; Lloyd, S. Quantum Hopfield neural network. Phys. Rev. A 2018, 98, 042308. [Google Scholar] [CrossRef]
- Harrow, A.W.; Hassidim, A.; Lloyd, S. Quantum algorithm for linear systems of equations. Phys. Rev. Lett. 2009, 103, 150502. [Google Scholar] [CrossRef] [PubMed]
- Shewchuk, J.R. An Introduction to the Conjugate Gradient Method Without the Agonizing Pain; Technical Report; Carnegie Mellon University: Pittsburgh, PA, USA, 1994. [Google Scholar]
- Rotondo, P.; Marcuzzi, M.; Garrahan, J.P.; Lesanovsky, I.; Müller, M. Open quantum generalisation of Hopfield neural networks. J. Phys. A Math. Theor. 2018, 51, 115301. [Google Scholar] [CrossRef]
- Ventura, D.; Martinez, T. Quantum associative memory with exponential capacity. In Proceedings of the 1998 IEEE International Joint Conference on Neural Networks Proceedings. IEEE World Congress on Computational Intelligence (Cat. No.98CH36227), Anchorage, AK, USA, 4–9 May 1998; Volume 1, pp. 509–513. [Google Scholar] [CrossRef]
- Seddiqi, H.; Humble, T.S. Adiabatic quantum optimization for associative memory recall. Front. Phys. 2014, 2, 79. [Google Scholar] [CrossRef]
- Cortes, C.; Vapnik, V. Support-vector networks. Mach. Learn. 1995, 20, 273–297. [Google Scholar] [CrossRef]
- Hofmann, T.; Schölkopf, B.; Smola, A.J. Kernel Methods in Machine Learning; Cambridge University Press: Cambridge, UK, 2008. [Google Scholar]
- Havlíček, V.; Córcoles, A.D.; Temme, K.; Harrow, A.W.; Kandala, A.; Chow, J.M.; Gambetta, J.M. Supervised learning with quantum-enhanced feature spaces. Nature 2019, 567, 209–212. [Google Scholar] [CrossRef] [PubMed]
- Buhrman, H.; Cleve, R.; Watrous, J.; De Wolf, R. Quantum fingerprinting. Phys. Rev. Lett. 2001, 87, 167902. [Google Scholar] [CrossRef]
- Rebentrost, P.; Mohseni, M.; Lloyd, S. Quantum support vector machine for big data classification. Phys. Rev. Lett. 2014, 113, 130503. [Google Scholar] [CrossRef]
- Bergholm, V.; Izaac, J.; Schuld, M.; Gogolin, C.; Ahmed, S.; Ajith, V.; Alam, M.S.; Alonso-Linaje, G.; AkashNarayanan, B.; Asadi, A.; et al. PennyLane: Automatic differentiation of hybrid quantum-classical computations. arXiv 2022, arXiv:1811.04968. [Google Scholar]
- Developers, C. Cirq; Zenodo: Genève, Switzerland, 2025. [Google Scholar] [CrossRef]
- Häner, T.; Steiger, D.S.; Svore, K.; Troyer, M. A software methodology for compiling quantum programs. Quantum Sci. Technol. 2018, 3, 020501. [Google Scholar] [CrossRef]
- Steiger, D.S.; Häner, T.; Troyer, M. ProjectQ: An open source software framework for quantum computing. Quantum 2018, 2, 49. [Google Scholar] [CrossRef]
- Svore, K.; Geller, A.; Troyer, M.; Azariah, J.; Granade, C.; Heim, B.; Kliuchnikov, V.; Mykhailova, M.; Paz, A.; Roetteler, M. Q#: Enabling Scalable Quantum Computing and Development with a High-level DSL. In Proceedings of the Real World Domain Specific Languages Workshop 2018, Vienna, Austria, 24 February 2018; p. RWDSL2018. [Google Scholar] [CrossRef]
- Fishman, M.; White, S.R.; Stoudenmire, E.M. The ITensor Software Library for Tensor Network Calculations. arXiv 2020, arXiv:2007.14822. [Google Scholar] [CrossRef]
- Kadowaki, T.; Nishimori, H. Quantum annealing in the transverse Ising model. Phys. Rev. E 1998, 58, 5355. [Google Scholar] [CrossRef]
- Schuld, M.; Killoran, N. Quantum machine learning in feature Hilbert spaces. Phys. Rev. Lett. 2019, 122, 040504. [Google Scholar] [CrossRef] [PubMed]
- Farhi, E.; Neven, H. Classification with quantum neural networks on near term processors. arXiv 2018, arXiv:1802.06002. [Google Scholar] [CrossRef]
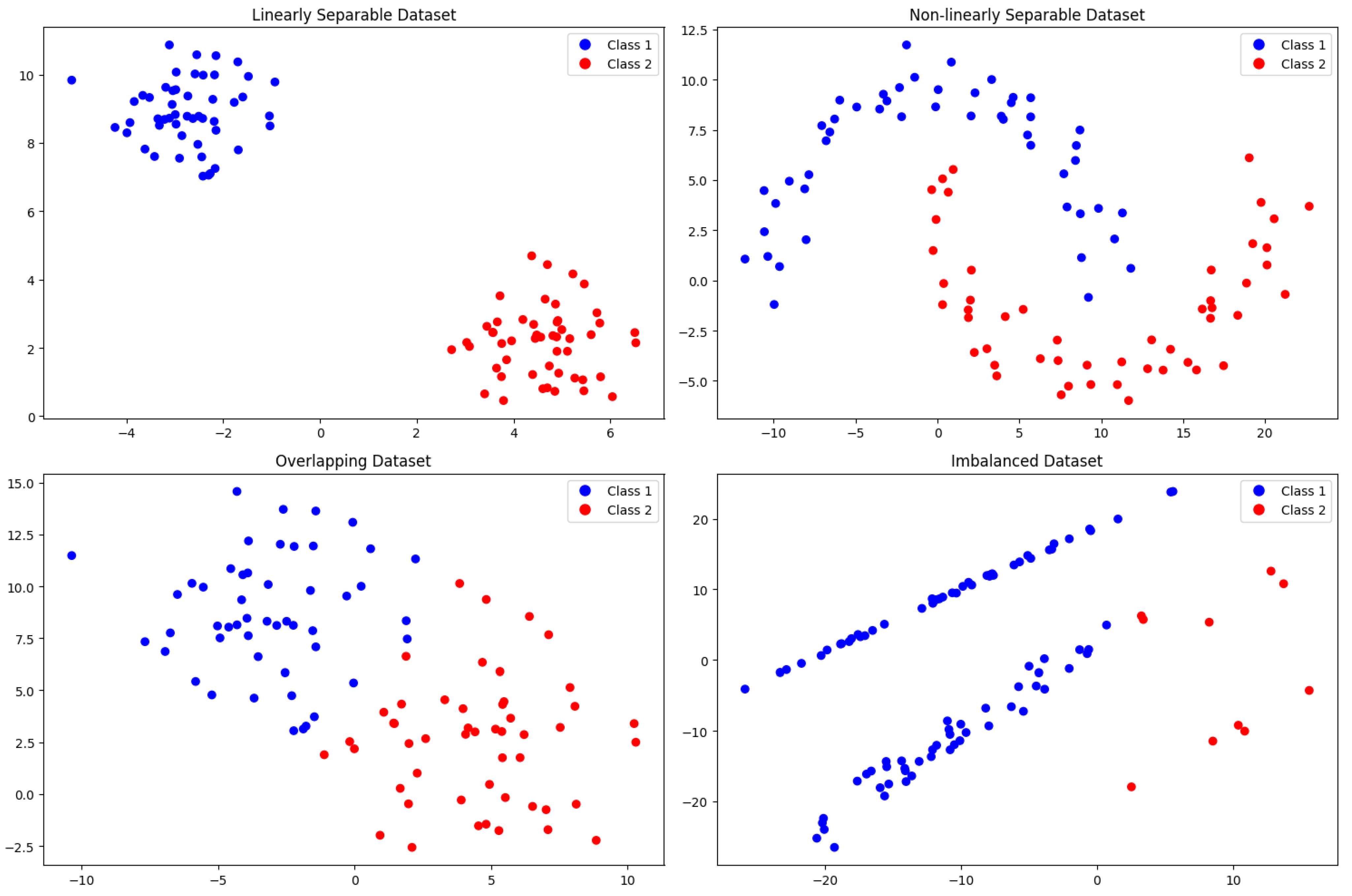
| Dataset | Generation Parameters | Classical SVM Metrics | |||||
|---|---|---|---|---|---|---|---|
| Samples/Features | Key Params | Split (Train/Test) | Acc | Prec | Rec | F1 | |
| Linearly Separable | 100/2 | centers = 2, cluster_std = 1.0 | 80/20 | 1.00 | 1.00 | 1.00 | 1.00 |
| Nonlinearly Separable | 100/2 | noise = 0.1, scaled ×10 | 80/20 | 1.00 | 1.00 | 1.00 | 1.00 |
| Overlapping | 100/2 | centers = 2, cluster_std = 3.0 | 80/20 | 0.95 | 0.90 | 1.00 | 0.94 |
| High-Dimensional | 100/10 | informative = 7, redundant = 3 | 80/20 | 0.75 | 0.54 | 1.00 | 0.70 |
| Imbalanced | 100/2 | weights = [0.9, 0.1], scaled ×10 | 80/20 (strat.) | 1.00 | 1.00 | 1.00 | 1.00 |
| Dataset | Quantum SVM Metrics | ||||||
| Acc | Prec | Rec | F1 | ||||
| Linearly Separable | 0.85 | 0.80 | 0.88 | 0.84 | |||
| Nonlinearly Separable | 0.80 | 0.62 | 0.83 | 0.71 | |||
| Overlapping | 0.45 | 0.37 | 0.33 | 0.35 | |||
| High-Dimensional | 0.30 | 0.30 | 1.00 | 0.46 | |||
| Imbalanced | 0.70 | 0.85 * | 0.70 * | 0.76 * | |||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Grigoryan, E.; Kumar, S.; Pinheiro, P.R. A Review on Models and Applications of Quantum Computing. Quantum Rep. 2025, 7, 39. https://doi.org/10.3390/quantum7030039
Grigoryan E, Kumar S, Pinheiro PR. A Review on Models and Applications of Quantum Computing. Quantum Reports. 2025; 7(3):39. https://doi.org/10.3390/quantum7030039
Chicago/Turabian StyleGrigoryan, Eduard, Sachin Kumar, and Placido Rogério Pinheiro. 2025. "A Review on Models and Applications of Quantum Computing" Quantum Reports 7, no. 3: 39. https://doi.org/10.3390/quantum7030039
APA StyleGrigoryan, E., Kumar, S., & Pinheiro, P. R. (2025). A Review on Models and Applications of Quantum Computing. Quantum Reports, 7(3), 39. https://doi.org/10.3390/quantum7030039







