1. Introduction
Quantum Key Distribution (QKD) is a promising technology for securing high-stakes data communications. By harnessing the principles of quantum mechanics, QKD systems generate and distribute cryptographic keys that are theoretically unbreakable. However, the implementation of QKD systems poses several challenges, particularly in the realm of monitoring and management. As the adoption of QKD technology continues to grow, the need for robust monitoring and management solutions has become increasingly pressing. The Cerberis3 QKD system from ID Quantique is designed to address these challenges, providing a comprehensive monitoring and visualization platform that enables network administrators to ensure their QKD infrastructure’s reliable and secure operation. With its advanced features and capabilities, the Cerberis3 system offers a robust solution for managing and monitoring QKD systems, ensuring the integrity of the quantum channel and the security of the generated keys. In this article, the features and capabilities of the Cerberis3 system are described, and its role in overcoming the monitoring challenges inherent to QKD deployments is explored. We will examine the key performance metrics that must be monitored, including Quantum Bit Error Rate (QBER) [
1], secret key rate, and link visibility [
2], and discuss the importance of integrating QKD systems with existing encryption vendors and network infrastructure [
3]. By understanding the Cerberis3 system’s capabilities and the challenges it addresses, organizations can leverage the power of QKD technology to secure their data in the face of emerging quantum computing threats. The Cerberis3 Quantum Key Distribution (QKD) system from ID Quantique offers advanced network monitoring capabilities that enable administrators to configure and monitor complex QKD network topologies [
4]. The system supports a range of network configurations including point-to-point, relay, ring, and hub-and-spoke topologies. Administrators can configure the Cerberis3 nodes, links, and routes through a central equipment management system (EMS) that provides status updates on each QKD node. The system also provides Syslog and SNMP feeds that can be integrated into the customer’s management system. SNMPv3 is recommended for secure monitoring, offering authentication, encryption, and fine-grained access control [
5,
6]. Key performance metrics that can be monitored and visualized for the Cerberis3 QKD system include the Quantum Bit Error Rate (QBER), the secret key rate, and the link visibility [
7,
8]. The QBER measures the errors in the quantum channel, which must be kept low to ensure secure key distribution [
8]. The secret key rate indicates the speed at which secure keys are generated and distributed [
8]. The link visibility measures the signal-to-noise ratio in the quantum channel, which impacts the maximum distance and key rate [
8]. By leveraging the advanced monitoring capabilities of the Cerberis3 system, network administrators can ensure the reliable and secure operation of their QKD infrastructure, enabling the widespread adoption of this quantum-safe technology. The Cerberis3 Quantum Key Distribution (QKD) system from ID Quantique offers advanced integration capabilities with various network topologies. This system supports deployment in any network configuration, including point-to-point, relay, ring, and hub-and-spoke topologies. Each QKD network node features a Key Management System (KMS) software 2.0.24 hosted on the Quantum Node Controller (QNC) blade, arbitrating key distribution between QKD blades and key consumers such as network encryptors. This ensures the secure distribution of keys across the network based on the recipient’s location. The QKD-based quantum-enhanced communication has been explored in detail in [
9], also covering how it may be applied in 6G-based networks. The ‘quantum Internet’ term is introduced, describing a new method for data transmission. “It is intended to be a network that can safely send quantum data across great distances, such as quantum keys, quantum entanglement, and quantum states, without running the risk of interception or modification [
9]”.
1.1. Key Integration Features
- 1.
Central Configuration and Management:
The system is managed through a central equipment management system (EMS) that provides status updates on each QKD node.
Syslog and SNMP feeds are available for integration into the customer’s management system, ensuring secure monitoring with SNMPv3.
- 2.
Interoperability:
The Cerberis3 QKD system can interface with link encryptors from major vendors, including Optical Transport Network (OTN) vendors such as ADVA and L2/L3 encryption.
ID Quantique actively participates in standardization processes, particularly at ITU and ETSI, to enhance interoperability with other security systems.
- 3.
Key Management and Monitoring:
The KMS software performs add/drop or forward functions to distribute keys based on the recipient’s location.
The system supports up to 80 encryptors through standard ETSI API or proprietary interfaces.
- 4.
Network Flexibility:
QKD blades can be housed in the same chassis for point-to-point or relay topologies or in add-on chassis connected to a QNC for more complex topologies.
The system supports operation over dark fibers and channel multiplexing over a single core, allowing for flexible deployment in various network environments.
1.2. Advantages of Using Cerberis3 in a Hub-and-Spoke Network Topology
The Cerberis3 Quantum Key Distribution (QKD) system from ID Quantique offers several advantages when deployed in a hub-and-spoke network topology:
- 1.
Centralized management: The system can be managed through a central equipment management system (EMS) that provides status updates on each QKD node, simplifying network management and troubleshooting.
- 2.
Cost-effectiveness: The hub-and-spoke topology reduces the need for redundant resources in each spoke, making it a cost-effective solution compared to mesh or ring topologies.
- 3.
Scalability: Adding new spokes to the network is easy without affecting the central hub, making it a scalable solution for growing networks.
- 4.
Security: The central hub can serve as a firewall, detecting different ports from packets and ensuring secure traffic flow. Logging is also more manageable from a central point, as all network activity passes through the hub.
- 5.
Interoperability: The Cerberis3 system can interface with link encryptors from major vendors, ensuring compatibility with existing encryption systems.
- 6.
Flexibility: The system supports various network configurations, including point-to-point, relay, ring, and hub-and-spoke topologies, allowing for flexible deployment in different network environments.
- 7.
Key management: The Key Management System (KMS) software hosted on the Quantum Node Controller (QNC) blade arbitrates key distribution between QKD blades and key consumers, ensuring secure and efficient key distribution across the network.
1.3. Describing Point-to-Point Architecture That Uses QKD for Key Management and a Monitoring System That Handles Events and Draws Graphs
Two QKD nodes are directly connected via a dedicated optical fiber link in a point-to-point QKD network. This architecture offers several key benefits:
- 1.
High bandwidth: The direct connection between the two nodes allows for high-speed data transmission, making it suitable for applications that require large data throughput.
- 2.
Simplified management: With only two nodes to manage, the point-to-point topology simplifies network administration and troubleshooting compared to more complex topologies.
- 3.
Cost-effectiveness: The point-to-point architecture can be a more cost-effective solution for small-scale deployments where only two endpoints need to be connected.
- 4.
Quantum-safe security: The QKD system generates and distributes cryptographic keys using quantum mechanical principles, ensuring that the communication channel is protected against eavesdropping and quantum computing attacks.
1.3.1. Monitoring and Visualization
To ensure the reliable and secure operation of the point-to-point QKD network, it is essential to have a comprehensive monitoring and visualization system. The Cerberis3 QKD system from ID Quantique offers advanced monitoring capabilities that enable network administrators to monitor and visualize key performance metrics.
1.3.2. Key Performance Metrics
- 1.
Quantum bit error rate (QBER): The QBER measures the errors in the quantum channel, which must be kept low to ensure secure key distribution.
- 2.
Secret key rate: The secret key rate indicates the speed at which secure keys are generated and distributed between the two QKD nodes.
- 3.
Link visibility: The link visibility measures the signal-to-noise ratio in the quantum channel, which impacts the maximum distance and key rate.
1.3.3. Monitoring and Visualization Features
- 1.
Central configuration and management: The Cerberis3 system is managed through a central equipment management system (EMS) that provides status updates on each QKD node.
- 2.
SNMP integration: The system provides Syslog and SNMPv3 feeds that can be integrated into the customer’s network management system, enabling secure monitoring and event handling.
- 3.
Graphical visualization: The monitoring system can generate graphs and visualizations of the key performance metrics, allowing network administrators to track the health and performance of the QKD network.
- 4.
Interoperability: The Cerberis3 system can interface with link encryptors from major vendors, ensuring seamless integration with existing encryption systems.
By leveraging the advanced monitoring and visualization capabilities of the Cerberis3 QKD system, network administrators can ensure the reliable and secure operation of their point-to-point QKD infrastructure, enabling the widespread adoption of this quantum-safe technology.
The Cerberis3 Quantum Key Distribution (QKD) system from ID Quantique can be integrated with existing optical transport networks (OTNs). The system supports interoperability with major OTN vendors, including ADVA and L2/L3 encryption vendors. This integration allows the Cerberis3 to interface with link encryptors from these vendors through standard and proprietary interfaces, ensuring seamless integration into existing network infrastructures. The Cerberis3 system can also interface with up to 80 encryptors through standard ETSI API or proprietary interfaces, further enhancing its compatibility with various network configurations.
2. Materials and Methods
The Cerberis3 QKD system 1.1.349 from ID Quantique, Rue Eugène-Marziano 25, 1227 Genève, Switzerland, was used for the experiments. The system consists of two QKD nodes, each equipped with a quantum key distribution module, a classical key distribution module, and a monitoring module. The nodes were connected via a dedicated optical fiber link.
2.1. Key Performance Metrics
The following key performance metrics were monitored and recorded during the experiments:
- 1.
Quantum Bit Error Rate (QBER): The QBER measures the errors in the quantum channel. It was calculated by comparing the bits Alice sent and Bob received.
- 2.
Secret key rate: The secret key rate is the rate at which secure keys are generated and distributed between the two nodes. It was calculated by analyzing the bits received by Bob and comparing them with the bits sent by Alice.
- 3.
Link visibility: The link visibility measures the signal-to-noise ratio in the quantum channel. It was calculated by analyzing the signal and noise levels in the quantum channel.
2.2. Data Collection and Analysis
Data was collected for 24 h, with the QKD system operating continuously. The data were analyzed using the Zabbix monitoring software 6.4.15 [
10], which provided the real-time monitoring and visualization of the key performance metrics implemented using Grafana [
11]. Two Fortinet FortiGate firewalls were used to set up an IPSec tunnel where QKD-generated keys were used for encryption. Two end hosts were connected on the LAN side of FortiGate firewalls, and iPerf3 was used to continuously generate traffic from Alice to Bob for monitoring purposes to determine the stability of the encrypted channel.
Figure 1 shows the setup used for the experiment, including hardware and software. Two Cerberis3 QKD nodes with default configuration were used, two Fortinet Fortigate VM firewalls were used for QKD-enabled IPsec tunnel termination, and the Zabbix 6.4.15 server version was used to monitor QKD nodes over the SNMPv3 protocol.
3. Results
A 24-h window was selected to obtain a comprehensive snapshot of the stability and performance of the QKD-enabled encryption tunnel. This duration was chosen to encompass various operational conditions, including peak usage periods and potential environmental variations affecting system performance. Critical QKD parameters were systematically monitored throughout this interval, including the key generation rate, error rates in key distribution, and the system’s resilience against potential quantum and classical attacks. These parameters were analyzed to assess the robustness of the QKD infrastructure and its efficiency in maintaining secure communication under various conditions. The findings provided insights into the reliability of QKD technology for real-world applications, identifying its strengths and potential areas for improvement in practical implementations.
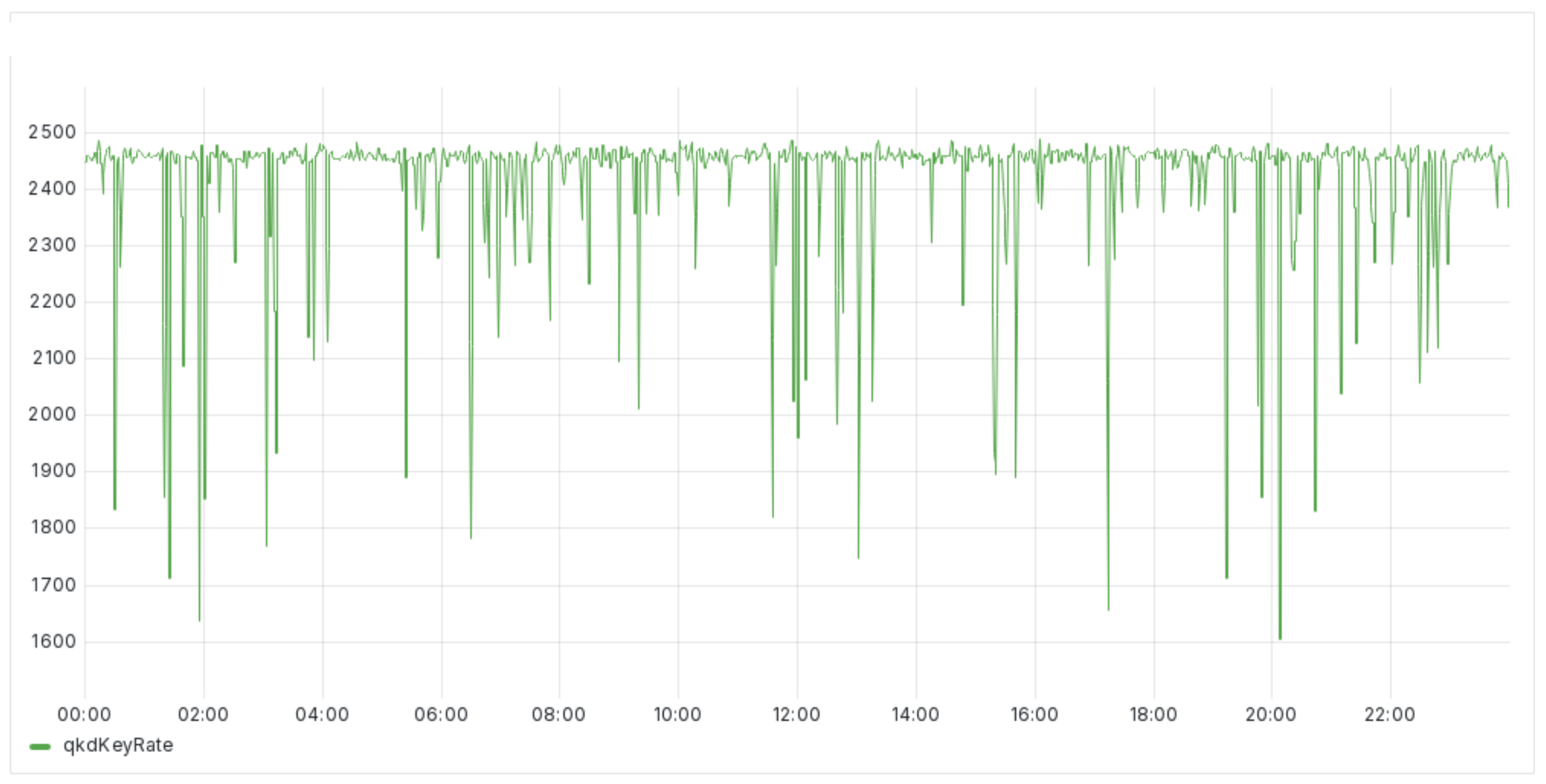
Figure 2 shows the data collected on the key rate maintained consistently during the 24 h monitoring period. This key rate proved sufficient to maintain a stable quantum key-encrypted channel, ensuring continuous and secure communication. The stability of the key rate indicates that the QKD system could generate and distribute quantum keys at a rate that met or exceeded the requirements to maintain the encrypted channel. This sustained key rate is critical for ensuring that the encryption remains robust and fluctuations in key availability do not compromise secure data transmission. The ability to maintain this rate over an extended period underscores the system’s reliability and its suitability for practical, long-term deployment in secure communication networks. For all of the following figures, the horizontal axis consists of time, in total, 24 h. The vertical axis label is given at the bottom of each figure and consists of absolute values. Values are recorded in 30-s intervals. Thus, each hour has 120 records that form a graphical representation of values over time.
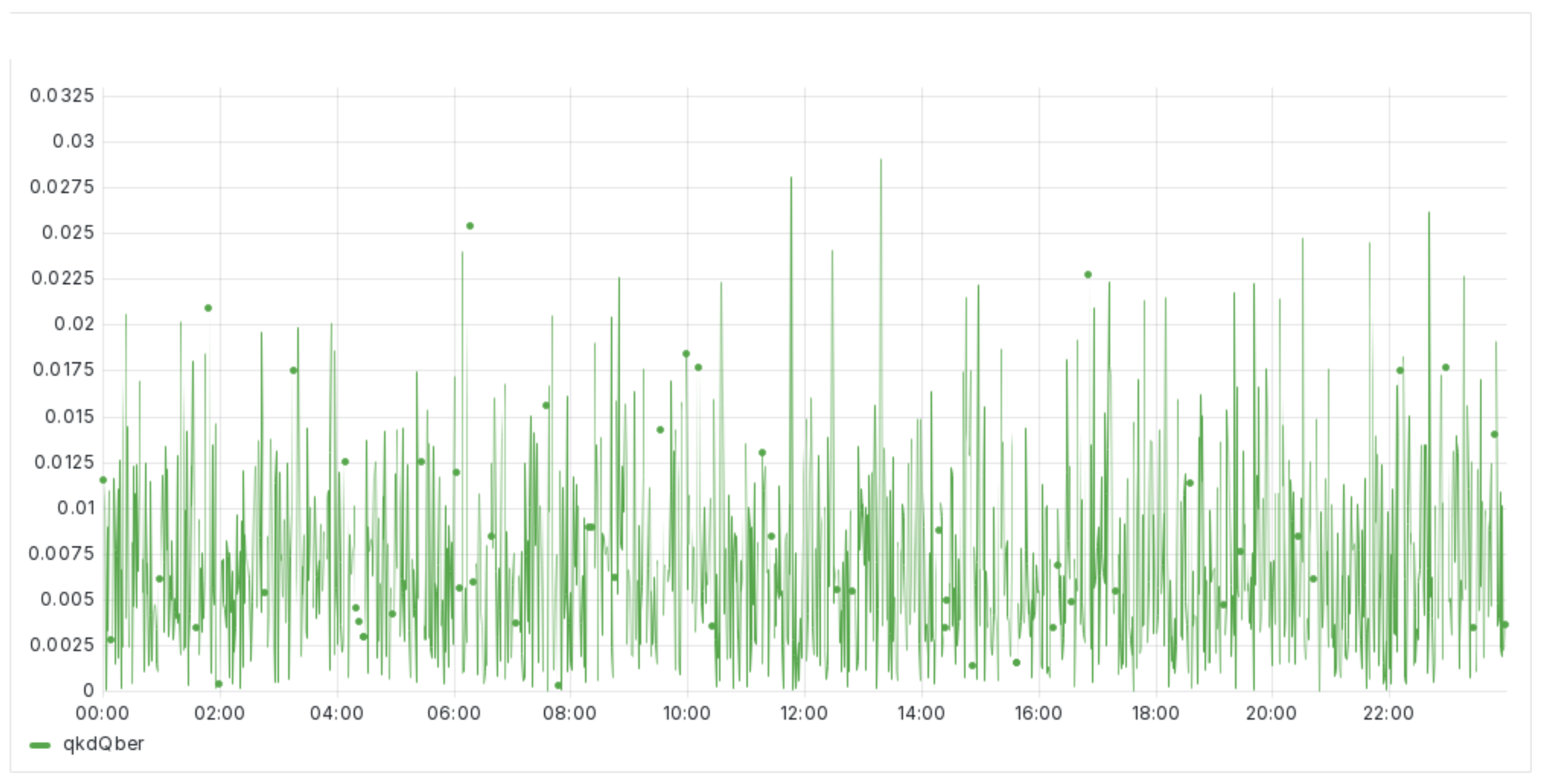
Figure 3 shows the Quantum Bit Error Rate (QBER) and the consistently sustained levels throughout the 24 h testing period. The QBER, a critical parameter in evaluating the quality of the quantum key distribution, remained within acceptable limits, indicating that the system maintained high fidelity in key transmission. Throughout the monitoring period, no anomalies or deviations were detected, suggesting that the quantum channel remained stable and free of disturbances that could degrade the quality of the transmitted keys. This stability in QBER is crucial because it reflects the system’s capability to resist noise and interference, thereby ensuring the integrity and security of the quantum key distribution process. The absence of anomalies further validates the reliability of the QKD system under continuous operation, reinforcing its potential for secure and uninterrupted communication in real-world applications.
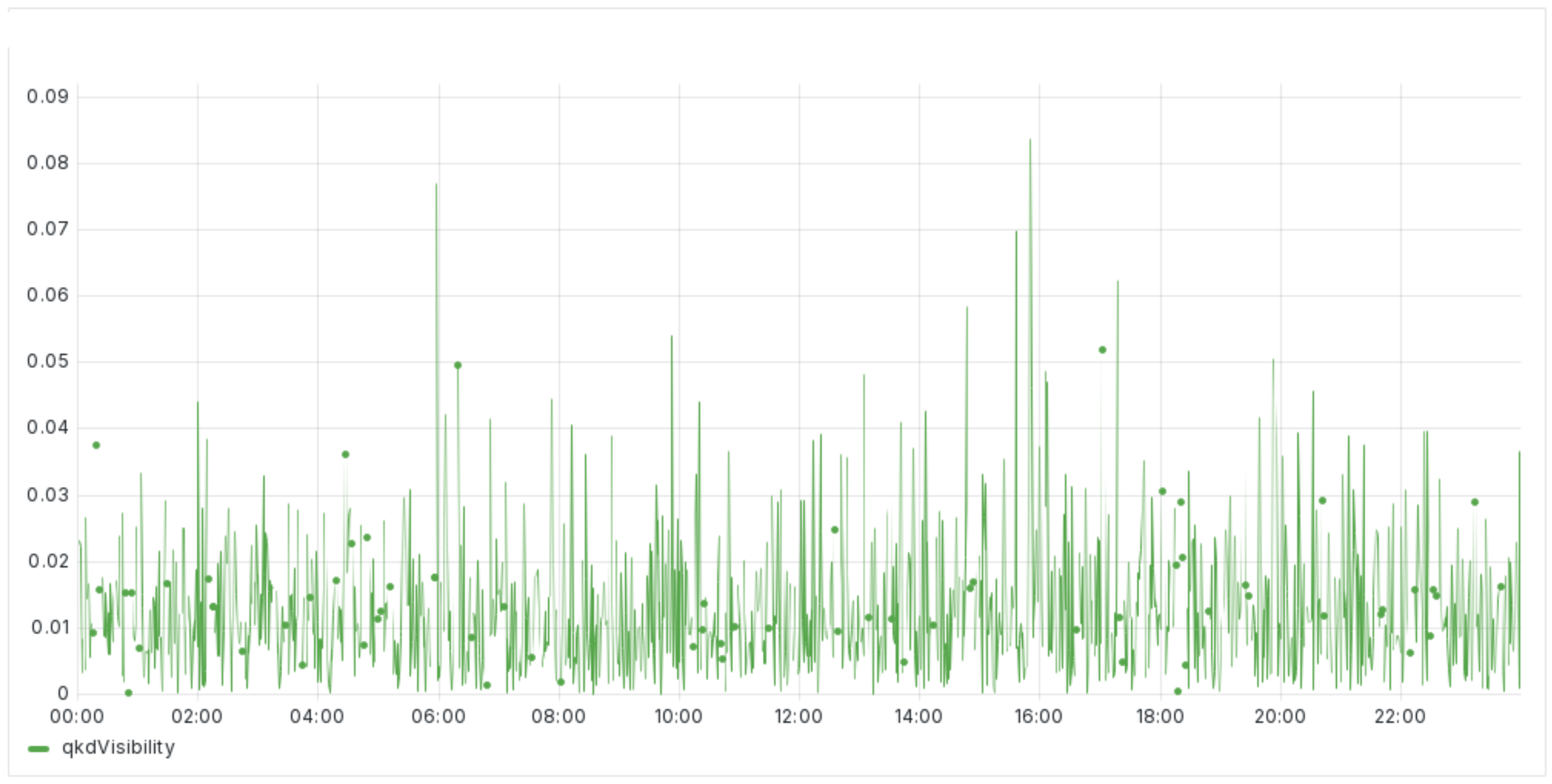
Figure 4 shows the visibility parameter that is consistently maintained throughout the 24-h monitoring period. Visibility, a key metric in quantum key distribution systems, measures the contrast between the quantum states representing ‘0’ and ‘1’ bits. High visibility indicates a clear distinction between these states, which is essential for accurate key generation and reduces the likelihood of errors during key transmission. The data show that visibility remained high and stable, suggesting that the quantum states were well defined and that the system was operating efficiently.
This sustained high visibility is crucial for ensuring the reliability and security of the quantum key distribution process, as it minimizes the potential for key errors and enhances the system’s resistance to eavesdropping. The consistent visibility observed during the testing period indicates that the QKD system was operating under optimal conditions, with minimal influence from external factors, such as environmental noise or hardware imperfections. This stability underscores the system’s robustness in maintaining high-quality quantum communication over extended periods, a critical factor for practical deployment in secure communication networks.
Figure 5 shows the number of detections recorded over a 24-h period, providing a detailed view of the system’s activity and performance during this time frame. In the Quantum Key Distribution (QKD) context, “detections” refer to the successful identification and reception of quantum signals that generate cryptographic keys. Each detection represents a successful measurement of a quantum bit (qubit) transmitted through the quantum channel.
The data captured in the figure indicate the rate and consistency of these detections, which are critical for evaluating the system’s efficiency and reliability. A stable and high detection rate suggests the QKD system effectively captures the quantum signals necessary for secure key generation. This stability is vital to maintaining a continuous and secure communication channel, as fluctuations in the detection rate could indicate issues such as signal loss, interference, or equipment malfunctions.
In addition, the figure may highlight peak activity periods, which can correspond to times of increased data transmission and quieter periods. Analyzing these patterns can provide insights into the system’s performance under different operational conditions, such as varying environmental factors or network loads.
Overall, the data on detections over the 24-h period provide a comprehensive understanding of the QKD system’s operational dynamics, contributing to assessing its capability to sustain secure and reliable quantum communications over extended durations.
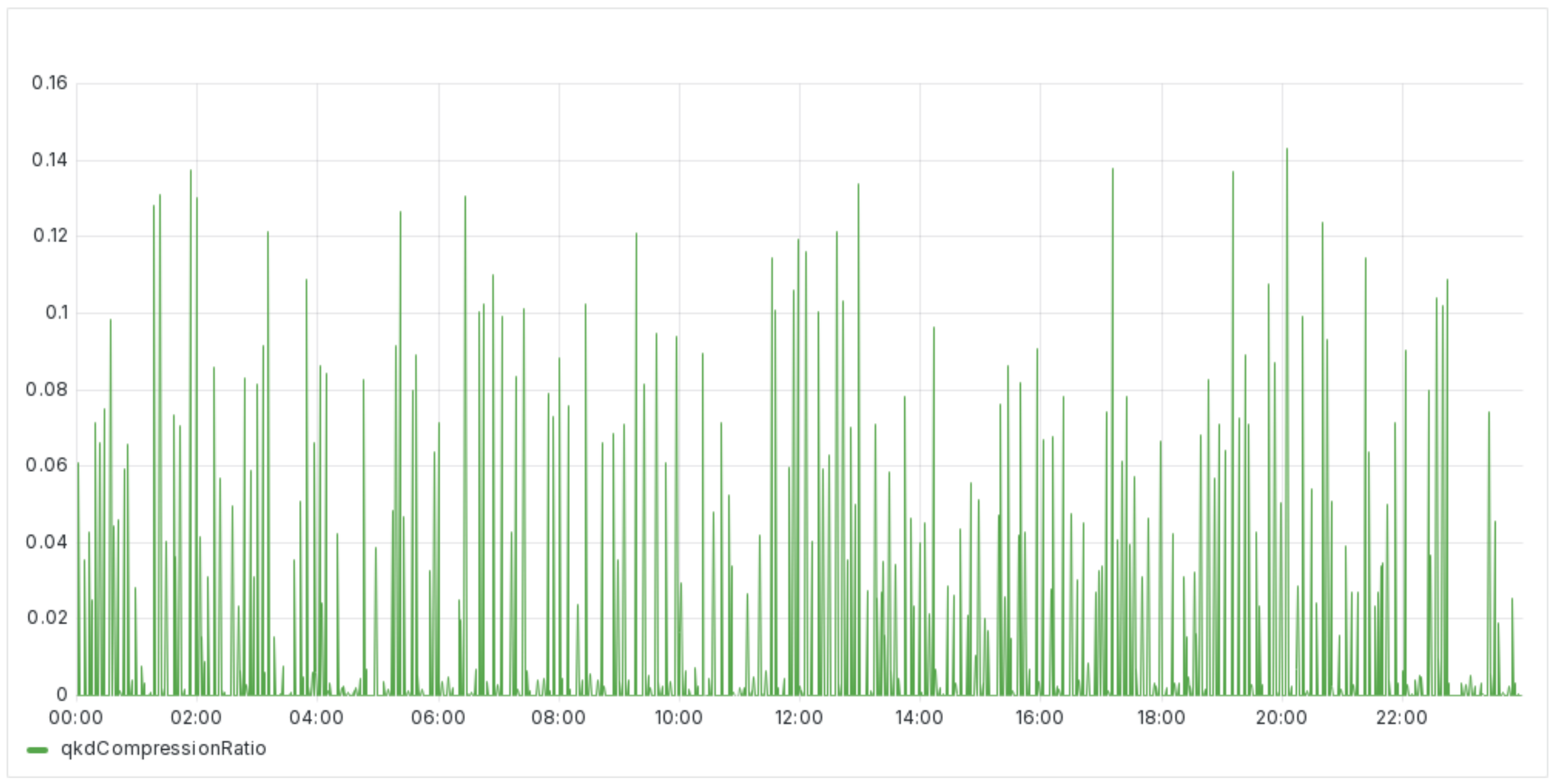
Figure 6 presents the data on compression observed over the 24-h period, a parameter closely related to the error rate in the Quantum Key Distribution (QKD) system. Compression in this context refers to reducing the redundancy in transmitted data to protect against information leakage. Given the observed error rates, it measures how much information an unauthorized third party could potentially gain about the quantum key through intercepted data.
In QKD systems, compression is a crucial step in ensuring the security of the generated keys. By assessing the compression level, we can infer the effectiveness of the privacy amplification process, which aims to eliminate any partial information that an eavesdropper might have obtained. The figure demonstrates that the compression was maintained at sufficient levels to ensure that the final key, after error correction and privacy amplification, remained secure and indistinguishable to an unauthorized observer.
The stability in compression observed over the monitoring period indicates that the system consistently managed the error rates and maintained the necessary security margins to protect the quantum key. This stability is essential for ensuring that the cryptographic strength of the key is preserved, preventing potential security breaches. The data, therefore, provide a critical validation of the QKD system’s ability to maintain secure communications, highlighting the robustness of the implemented security protocols against eavesdropping attempts.
4. Discussion
The experimental results underscore the effectiveness of the Cerberis3 Quantum Key Distribution (QKD) system by ID Quantique in generating and distributing secure cryptographic keys. The system consistently achieved a high secret key rate, crucial for supporting secure real-time communication. Additionally, the Quantum Bit Error Rate (QBER) was maintained at low levels throughout the testing period, signifying that the quantum channel was secure and reliable. This low QBER indicates minimal errors in the key generation process, reducing the compromised security likelihood.
The high link visibility observed during the experiments reflects a favorable signal-to-noise ratio within the quantum channel. This metric is important, as it demonstrates that the quantum states used for key distribution were clearly distinguishable, minimizing the risk of key errors and enhancing the overall robustness of the encryption.
The Cerberis3 QKD system, with its advanced technological features, proves to be a robust and reliable solution for organizations with stringent data security requirements. The system’s ability to maintain high secret key rates, low QBER, and excellent link visibility highlights its suitability for deployment in environments where data integrity and confidentiality are paramount. These characteristics make the Cerberis3 QKD system an ideal choice for sectors such as finance, healthcare, and government, where protecting sensitive information is critical. The results of this study reaffirm the role of the Cerberis3 system as a leading solution in the field of quantum-safe encryption technologies.
5. Conclusions
It was discovered that, despite the availability of commercially viable Quantum Key Distribution (QKD) solutions, there remains significant room for improvement in the areas of system monitoring and maintenance. Addressing this gap is crucial for accelerating the widespread adoption of QKD technologies. Enhanced monitoring and maintenance protocols would ensure the stability and reliability of these systems and build confidence in their deployment by providing a track record of stability and zero downtime.
Achieving these improvements requires a multidisciplinary approach to identify and establish appropriate thresholds for monitoring across different applications and environments. This involves collaboration between experts in quantum physics, cybersecurity, network engineering, and systems maintenance, among other fields. The goal is to develop comprehensive monitoring frameworks that can preemptively identify and mitigate potential issues, thereby enhancing the overall resilience of QKD systems.
Further studies should focus on tailoring QKD solutions to various use cases, ranging from secure communications in government and military applications to protecting sensitive data in the financial and healthcare sectors. This research would involve identifying the common variables that are critical to system reliability, such as environmental factors, hardware performance, and network conditions. By understanding these variables, it becomes possible to develop standardized metrics and protocols that ensure the consistent performance and security of QKD systems across different scenarios.
Ultimately, this approach aims to establish QKD as a trustworthy and practical solution for secure communications, paving the way for broader integration into existing and future infrastructure. This will not only enhance data security, but also contribute to the development of quantum-safe encryption standards essential for protecting information in the coming quantum era.
This monitoring approach can be used to assess various optical connections as they are used for QKD solutions and create a matrix of thresholds that must be met for a stable communication channel. This requires further experiments in different fields to see how environmental changes affect the QKD stability.