Simulating Collaboration in Small Modular Nuclear Reactor Cybersecurity with Agent-Based Models
Abstract
1. Introduction
Contributions
- We review existing nuclear cybersecurity standards, provide a history and description of types of computer simulation which could be helpful in studying SMR cybersecurity, and review the current research on computer simulation in cybersecurity.
- We point out the value of collaboration in cybersecurity, identify the Common Criteria as an underutilized tool in nuclear cybersecurity, and provide recommendations for using agent-based modeling to study the effects of collaboration through the Common Criteria on SMR cybersecurity.
- We propose, build, and study the results of an agent-based model to examine the effects of collaboration between SMRs and vendors of cyber-physical control systems to harden the cybersecurity of SMRs. To our knowledge, no other published research has employed ABM to model the effects of collaboration with third parties in nuclear cybersecurity.
2. Existing Nuclear Cybersecurity Standards
3. History and Description of Simulation Types
4. Review of Computer Simulation in Cybersecurity
5. Cyber Collaboration and the Common Criteria
5.1. Recommendations for SMR Cybersecurity
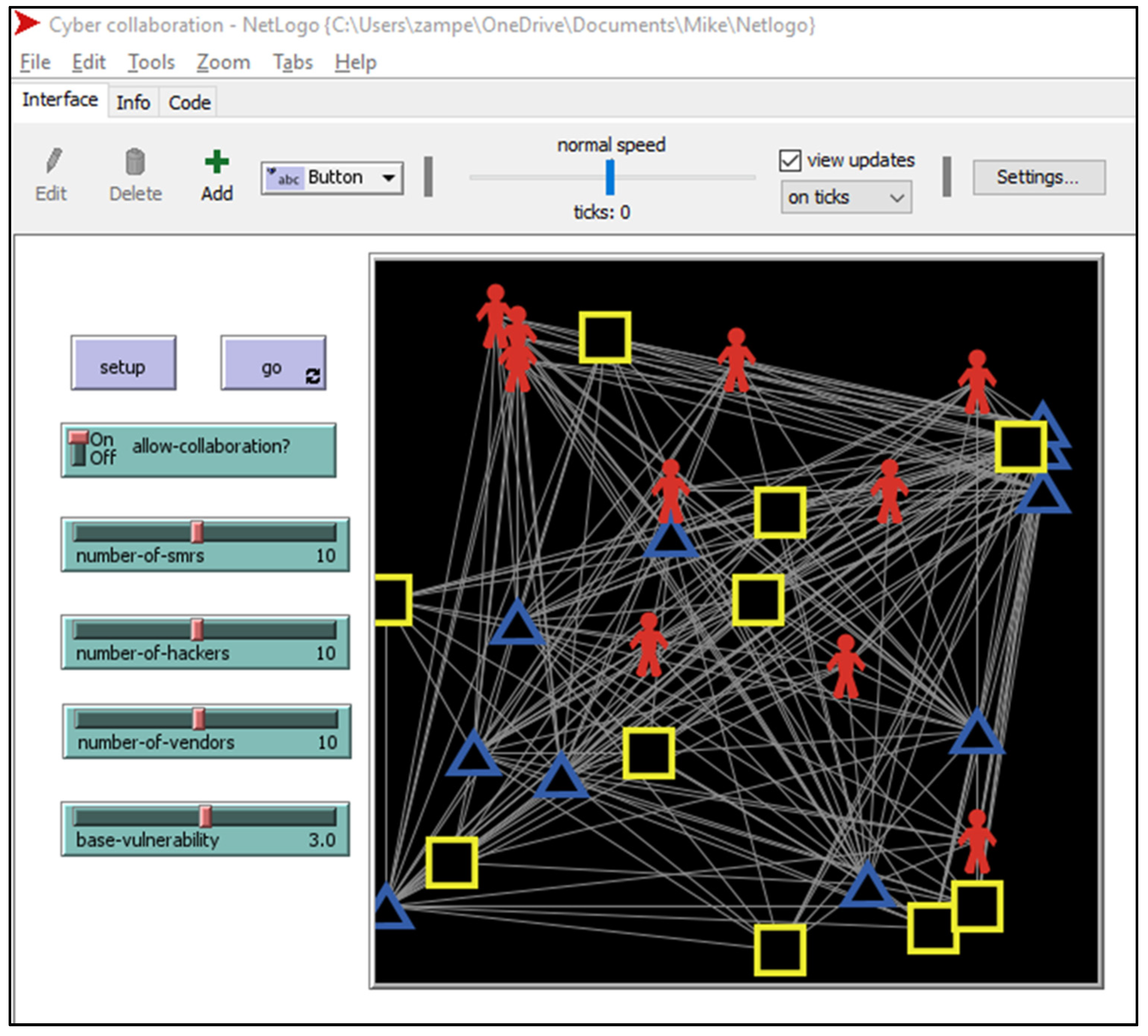
5.2. Proposed ABM Model
- Purpose—to demonstrate the concept of using ABM to study the benefits of collaboration between SMRs and cyber physical system vendors to improve cybersecurity infrastructure.
- Entities—include SMRs, vendors, and hackers. SMRs are characterized by randomized cyber-defense skills, collaboration skills, cyber vulnerability levels, and status as operating normally or hacked. Vendors share the characteristic of collaboration skills. Hackers have cyber-attack skills.
- ○
- SMR and Hacker randomized initial cyber defense or attack skill designed to have a mean of 1 with high values being stronger
- ▪
- set skill 0.1 + random-float 1.8
- ○
- SMR and Vendor initial collaboration skill
- ▪
- set collaborative-ability 0.1 + random-float 0.6
- ○
- SMR initial cyber vulnerability level set to a base level ± some randomized amount of the base level
- ▪
- set vulnerability base-vulnerability + (−1 ^ (random 2) * random-float (0.5 * base-vulnerability))
- Process—each hacker first launches attacks on some number of the unhacked SMRs during each step in the simulation. Next, SMRs initiate collaboration efforts with one of the vendors during each step. Successful hacks result in the SMR changing color and the skill of the hacker increasing by some small random increment. Hacked SMRs come back online after a random number (Poisson (2)) of simulation steps. Successful collaboration efforts result in the skills of both the SMR and vendor increasing by some small random increment up to some limit (0.8). Also, a counter is incremented that results in a decrease in SMR cyber vulnerability once a specific number (10) of successful collaborations is met.
- ○
- Hacker attack strength and randomized success of attack effort (SMRs turn red when successfully hacked)
- ▪
- let attack-strength [vulnerability] of target * skill/[skill] of target
- ▪
- if attack-strength > random-float 100 [ask target [set color red + 2]
- ○
- SMR-Vendor collaboration effort strength and randomized success leading to increase in collaboration counter and randomized decrease in SMR cyber vulnerability (with diminishing returns) after 10 successful collaboration attempts
- ▪
- let collaboration-strength [collaborative-ability] of collaborator * collaborative-ability
- ▪
- if collaboration-strength > random-float 1 [set collaboration-counter collaboration-counter + 1if collaboration-counter >= 10 [set change-in-vulnerability vulnerability *random-float 0.15 * (exp (−0.003 * ticks))set vulnerability (vulnerability—change-in-vulnerability)set collaboration-counter 0
- ○
- Hacked SMRs (color red+2) come back online after randomized down time
- ▪
- ask turtles with [color = red + 2] [ifelse countdown <= 0[set color blueset countdown random-poisson 2][set countdown countdown—1]]
- Emergence—the primary emergent output of the model is the time-average of SMRs in a hacked state.
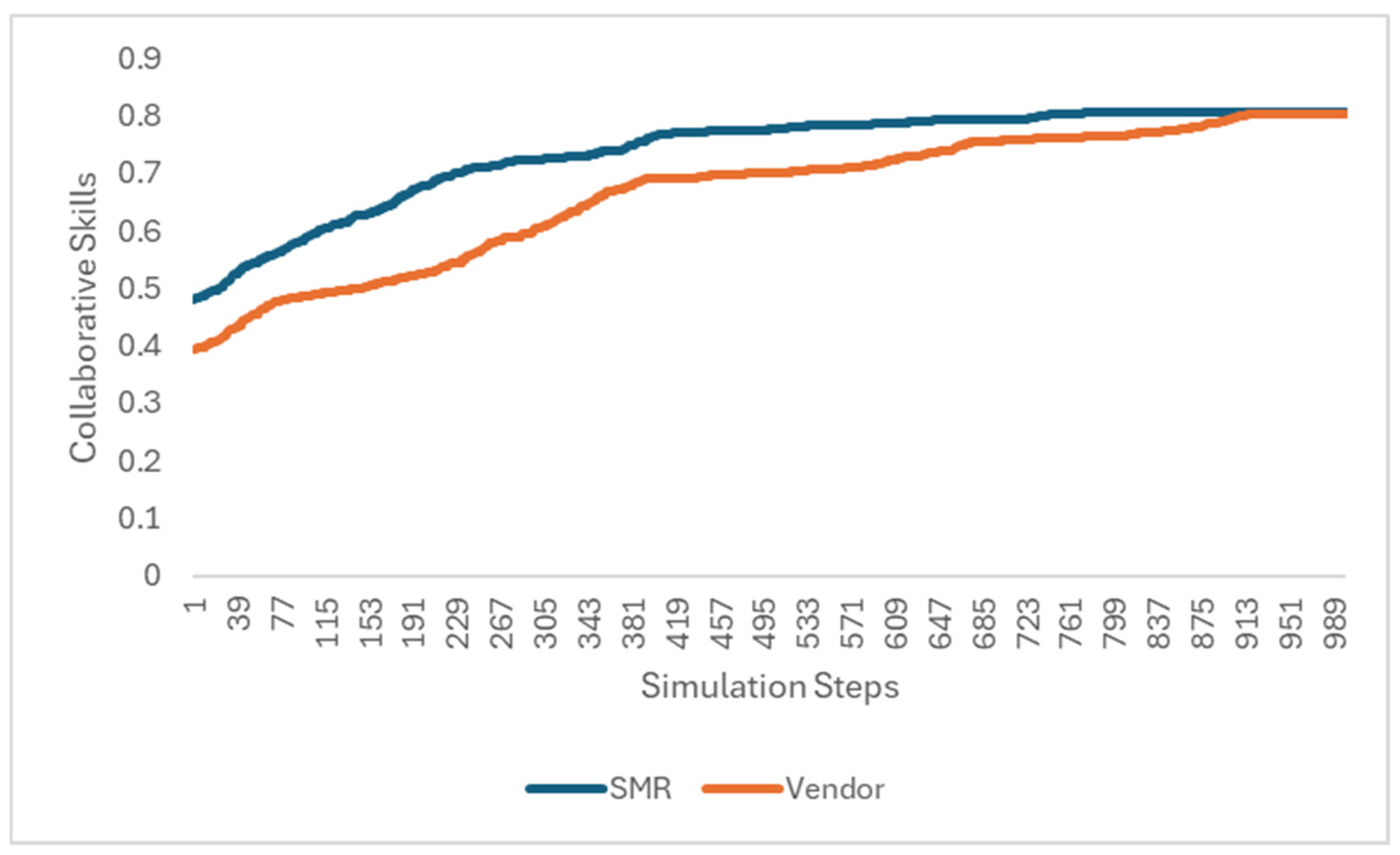
- Adaptation—the attack skills of the hackers and collaboration skills of the SMRs and vendors adapt to the progressions of the model.
- ○
- Change in hacker skill after successful hack is random with diminishing returns
- ▪
- set change-in-skill skill * (random-float 0.003) * (exp (−0.003 * ticks))set skill skill + change-in-skill
- ○
- Change in collaboration skills of SMRs and Vendors after successful collaboration, randomized, up to a determined limit. Note that the initiator is the SMR and the collaborator is the Vendor.
- ▪
- if collaborative-ability < 0.8 [set collaborative-ability collaborative-ability * (1 +random-float 0.03)]if [collaborative-ability] of collaborator < 0.8 [ask collaborator [set collaborative-abilitycollaborative-ability * (1 + random-float 0.03)]]
- Interactions—attacks by hackers on SMRs as well as collaboration between SMRs and vendors are assumed in this model.
- Stochasticity—randomization is introduced in:
- ○
- the outcomes of cyber-attacks and collaboration efforts,
- ○
- the recovery timeline of hacked SMRs,
- ○
- the incremental increases of hacker skills or SMR/vendor collaboration skills,
- ○
- and the decrease in SMR vulnerability due to successful collaborations.
- Initialization—the simulation initialization of variables includes numbers of each agent type and base vulnerability of the SMRs.
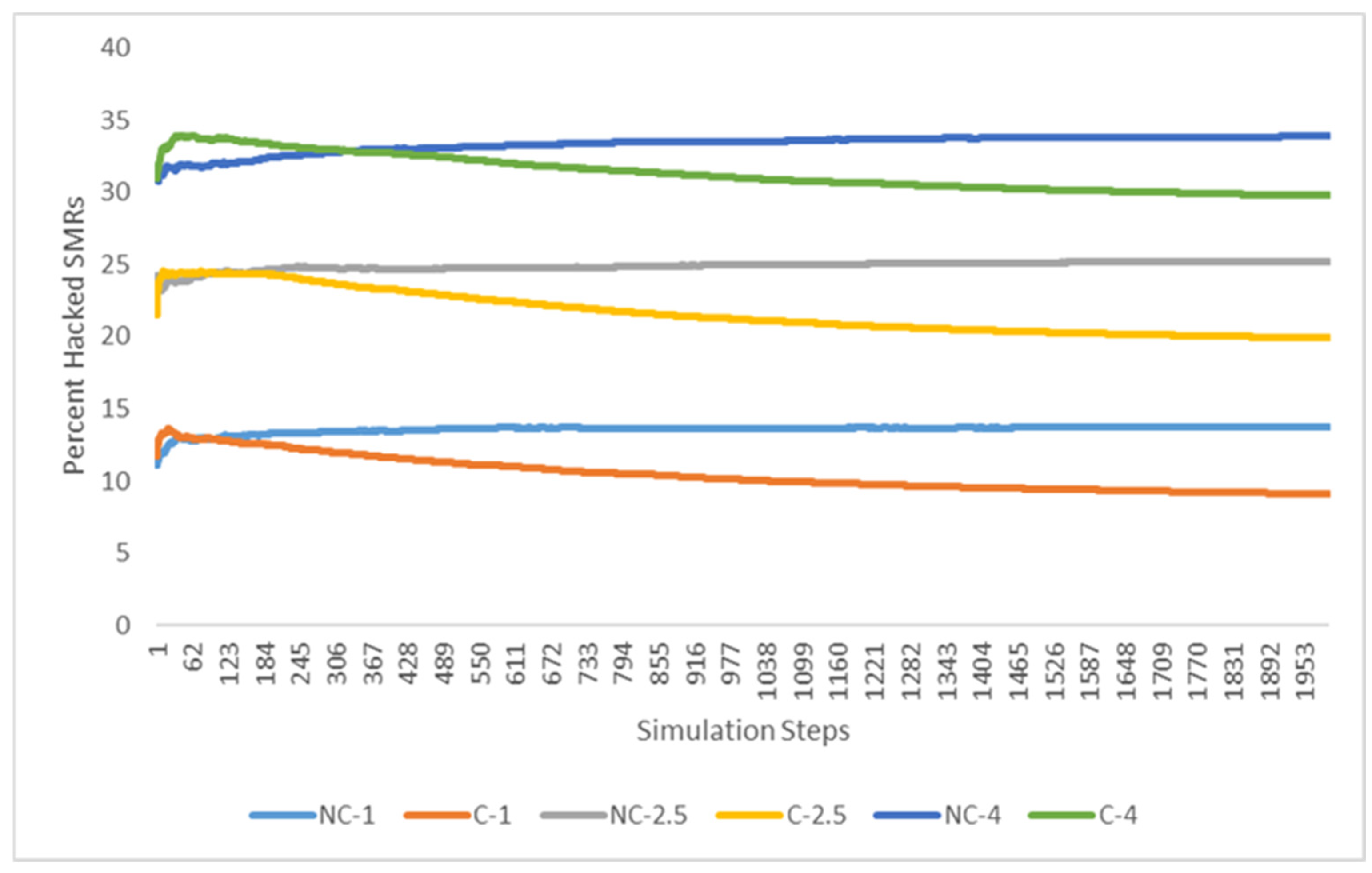
5.3. Simulation Results and Experimentation
6. Conclusions, Limitations, and Future Research
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ayodeji, A.; Mohamed, M.; Li, L.; Di Buono, A.; Pierce, I.; Ahmed, H. Cyber security in the nuclear industry: A closer look at digital control systems, networks and human factors. Prog. Nucl. Energy 2023, 161, 104738. [Google Scholar] [CrossRef]
- Ding, J.; Qammar, A.; Zhang, Z.; Karim, A.; Ning, H. Cyber threats to smart grids: Review, taxonomy, potential solutions, and future directions. Energies 2022, 15, 6799. [Google Scholar] [CrossRef]
- Abdelkader, S.; Amissah, J.; Kinga, S.; Mugerwa, G.; Emmanuel, E.; Mansour, D.A.; Bajaj, M.; Blazek, V.; Prokop, L. Securing modern power systems: Implementing comprehensive strategies to enhance resilience and reliability against cyber-attacks. Results Eng. 2024, 23, 102647. [Google Scholar] [CrossRef]
- Linnosmaa, J.; Papakonstantinou, N.; Malm, T.; Kotelba, A.; Pärssinen, J. Survey of Cybersecurity Standards for Nuclear Instrumentation and Control Systems. In International Symposium on Future I&C for Nuclear Power Plants, ISOFIC 2021: Online; Okayama University: Okayama, Japan, 2021; Available online: https://cris.vtt.fi/ws/portalfiles/portal/53942179/Linnosmaa_ISOFIC_2021.pdf (accessed on 22 August 2025).
- World Nuclear News. High Support for Advanced Nuclear Worldwide, Survey Finds. 10 May 2023. Available online: https://world-nuclear-news.org/Articles/High-support-for-advanced-nuclear-worldwide,-surve (accessed on 22 August 2025).
- Collins, J. Executive Gets 15 Months in Prison in Doomed Nuclear Project; The Associated Press: New York City, NY, USA, 8 March 2023; Available online: https://apnews.com/article/stephen-byrne-scana-power-plant-prison-c97cb1aaa33c991020551b2ae5c4dd85 (accessed on 22 August 2025).
- Crumbley, D.L. Sad Saga of the Financial Fraud of South Carolina’s Two Failed Nuclear Power Plants. J. Forensic Investig. Account. 2022, 14, 212–228. [Google Scholar]
- Plumer, B. U.S. Nuclear Comeback Stalls as Two Reactors Are Abandoned. The New York Times. 31 July 2017. Available online: https://www.nytimes.com/2017/07/31/climate/nuclear-power-project-canceled-in-south-carolina.html (accessed on 22 August 2025).
- Mignacca, B.; Locatelli, G. Economics and finance of Small Modular Reactors: A systematic review and research agenda. Renew. Sustain. Energy Rev. 2020, 118, 109519. [Google Scholar] [CrossRef]
- Dominion Energy. Virginia Elective and Power Company’s Report of its 2023 Integrated Resource Plan. 1 May 2023. Available online: https://rga.lis.virginia.gov/Published/2023/RD214 (accessed on 22 August 2025).
- Hoak, A. Gov. Youngkin’s Plan to Bring Small Modular Reactor to Southwest Virginia Hits Roadblock. WCYB, 3 March 2023. Available online: https://wcyb.com/news/local/plan-to-bring-small-modular-reactor-to-southwest-virginia-hits-roadblock-governor-glenn-youngkin-smr-energy-innovation-hub-lawmakers-republican-delegate-israel-oquinn-invest-swva-will-payne-southwest-virginia-energy-and-research-development-authority (accessed on 22 August 2025).
- Conover, E. Tech Companies Want Small Nuclear Reactors. Here’s How They’d Work. ScienceNews, 23 October 2024. Available online: https://www.sciencenews.org/article/small-modular-nuclear-reactors-amazon (accessed on 22 August 2025).
- Dalton, D. Nuclear Investment Makes Comeback, with Spending Set to Exceed $70 Billion and Promise of Further Growth. Nucnet, 5 June 2025. Available online: https://www.nucnet.org/news/nuclear-investment-makes-comeback-with-spending-set-to-exceed-usd70-billion-and-promise-of-further-growth-6-4-2025 (accessed on 22 August 2025).
- Hirdaris, S.E.; Cheng, Y.F.; Shallcross, P.; Bonafoux, J.; Carlson, D.; Prince, B.; Sarris, G.A. Considerations on the potential use of Nuclear Small Modular Reactor (SMR) technology for merchant marine propulsion. Ocean Eng. 2014, 79, 101–130. [Google Scholar] [CrossRef]
- Ingersoll, D.T.; Carelli, M.D. (Eds.) Handbook of Small Modular Nuclear Reactors; Woodhead Publishing: Sawston, UK, 2020. [Google Scholar]
- Derr, E. Nuclear Needs Small Amounts of Land to Deliver Big Amounts of Electricity. NEI, 29 April 2022. Available online: https://nei.org/news/2022/nuclear-brings-more-electricity-with-less-land (accessed on 22 August 2025).
- GAO. Nuclear Microreactors; U.S. Government Accountability Office: Washington, DC, USA, 2020. Available online: https://www.gao.gov/products/gao-20-380sp (accessed on 22 August 2025).
- NuScale. VOYGR Power Plants; NuScale: Corvallis, OR, USA, 2023; Available online: https://www.nuscalepower.com/en/products/voygr-smr-plants (accessed on 22 August 2025).
- Testoni, R.; Bersano, A.; Segantin, S. Review of nuclear microreactors: Status, potentialities and challenges. Prog. Nucl. Energy 2021, 138, 103822. [Google Scholar] [CrossRef]
- Liu, Z.; Fan, J. Technology readiness assessment of small modular reactor (SMR) designs. Prog. Nucl. Energy 2014, 70, 20–28. [Google Scholar] [CrossRef]
- Yin, S.; Zhang, Y.; Tian, W.; Qiu, S.; Su, G.H.; Gao, X. Simulation of the small modular reactor severe accident scenario response to SBO using MELCOR code. Prog. Nucl. Energy 2016, 86, 87–96. [Google Scholar] [CrossRef]
- Locatelli, G.; Boarin, S.; Pellegrino, F.; Ricotti, M.E. Load following with Small Modular Reactors (SMR): A real options analysis. Energy 2015, 80, 41–54. [Google Scholar] [CrossRef]
- Common Criteria. The Common Criteria. Available online: https://www.commoncriteriaportal.org/ (accessed on 22 August 2025).
- Francia, G.A., III; Francia, X.P.; Bridges, C. Agent-Based Modeling of Entity Behavior in Cybersecurity. In Advances in Cybersecurity Management; Springer International Publishing: Cham, Switzerland, 2021; pp. 3–18. [Google Scholar] [CrossRef]
- Husák, M.; Kašpar, J. Towards predicting cyber attacks using information exchange and data mining. In Proceedings of the 2018 14th International Wireless Communications & Mobile Computing Conference (IWCMC), Limassol, Cyprus, 25–29 June 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 536–541. [Google Scholar] [CrossRef]
- Rajivan, P.; Cooke, N. Impact of team collaboration on cybersecurity situational awareness. In Theory and Models for Cyber Situation Awareness; Springer International Publishing: Cham, Switzerland, 2017; pp. 203–226. [Google Scholar] [CrossRef]
- U.S. Nuclear Regulatory Commission. Regulatory Guide 5.71 Cyber Security Programs for Nuclear Facilities; Office of Nuclear Regulatory Research: Rockville, MD, USA, 2010. Available online: https://www.nrc.gov/docs/ML0903/ML090340159.pdf (accessed on 22 August 2025).
- International Nuclear Safety Advisory Group. Defense in Depth in Nuclear Safety, INSAG-10; International Atomic Energy Agency: Vienna, Austria, 1996; Available online: https://www-pub.iaea.org/MTCD/Publications/PDF/Pub1013e_web.pdf (accessed on 22 August 2025).
- Krause, T.; Ernst, R.; Klaer, B.; Hacker, I.; Henze, M. Cybersecurity in Power Grids: Challenges and Opportunities. Sensors 2021, 21, 6225. [Google Scholar] [CrossRef] [PubMed]
- Duguay, R. Small modular reactors and advanced reactor security: Regulatory perspectives on integrating physical and cyber security by design to protect against malicious acts and evolving threats. Int. J. Nucl. Secur. 2020, 7, 2. [Google Scholar] [CrossRef]
- Langner, R. Stuxnet: Dissecting a cyberwarfare weapon. IEEE Secur. Priv. 2011, 9, 49–51. [Google Scholar] [CrossRef]
- Gibson, M.; Elks, C.; Tantawy, A.; Hite, R.; Gautham, S.; Jayakumar, A.; Deloglos, C. Achieving Verifiable and High Integrity Instrumentation and Control Systems Through Complexity Awareness and Constrained Design; No. DOE/NEUP-15-8044; Electric Power Research Institute (EPRI): Charlotte, NC, USA, 2019. Available online: https://www.osti.gov/servlets/purl/1547345 (accessed on 22 August 2025).
- Van Dine, A.; Assante, M.; Stoutland, P. Outpacing Cyber Threats. Priorities for Cybersecurity at Nuclear Facilities; Nuclear Threat Initiative: Washington, DC, USA, 2016; Available online: https://media.nti.org/documents/NTI_CyberThreats__FINAL.pdf (accessed on 22 August 2025).
- MITRE. MITRE ATT&CK. Retreived June 4, 2025. Available online: https://attack.mitre.org/ (accessed on 22 August 2025).
- Engström, V.; Lagerström, R. Two decades of cyberattack simulations: A systematic literature review. Comput. Secur. 2022, 116, 102681. [Google Scholar] [CrossRef]
- Chen, J.; Shi, Y. Stochastic model predictive control framework for resilient cyber-physical systems: Review and perspectives. Philos. Trans. R. Soc. A 2021, 379, 20200371. [Google Scholar] [CrossRef]
- Kotenko, I.; Saenko, I.; Privalov, A.; Lauta, O. Ensuring SDN resilience under the influence of cyber attacks: Combining methods of topological transformation of stochastic networks, markov processes, and neural networks. Big Data Cogn. Comput. 2023, 7, 66. [Google Scholar] [CrossRef]
- Brito, T.B.; Trevisan, E.F.C.; Botter, R.C. A conceptual comparison between discrete and continuous simulation to motivate the hybrid simulation methodology. In Proceedings of the 2011 Winter Simulation Conference (WSC), Phoenix, AZ, USA, 11–14 December 2011; IEEE: Piscataway, NJ, USA; pp. 3910–3922. [Google Scholar] [CrossRef]
- Sarker, I.H. Deep cybersecurity: A comprehensive overview from neural network and deep learning perspective. SN Comput. Sci. 2021, 2, 154. [Google Scholar] [CrossRef]
- Siebers, P.O.; Macal, C.M.; Garnett, J.; Buxton, D.; Pidd, M. Discrete-event simulation is dead, long live agent-based simulation! J. Simul. 2010, 4, 204–210. [Google Scholar] [CrossRef]
- Robinson, S. Discrete-event simulation: From the pioneers to the present, what next? J. Oper. Res. Soc. 2005, 56, 619–629. [Google Scholar] [CrossRef]
- Macal, C.; North, M. Introductory tutorial: Agent-based modeling and simulation. In Proceedings of the Winter Simulation Conference 2014, Savannah, GA, USA, 7–10 December 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 6–20. [Google Scholar] [CrossRef]
- Kelton, W.D.; Zupick, N.B.; Ivey, N.; Sadowski, R.P. Simulation with Arena, 7th ed.; McGraw Hill Education: Columbus, OH, USA, 2024. [Google Scholar]
- Milov, O.; Hrebeniuk, A.; Nalyvaiko, A.; Nyemkova, E.; Opirskyy, I.; Pasko, I.; Rzayev, K.; Salii, A.; Synytsina, U.; Soloviova, O. Development of the space-time structure of the methodology for modeling the behavior of antagonistic agents of the security system. East.-Eur. J. Enterp. Technol. 2020, 6, 108. [Google Scholar] [CrossRef]
- Law, A.M.; Kelton, W.D. Simulation Modeling and Analysis, 3rd ed.; McGraw Hill: Columbus, OH, USA, 2000. [Google Scholar]
- Kara, S.; Hizal, S.; Zengin, A. Design and Implementation of a DEVS-Based Cyber-Attack Simulator for Cyber Security. Int. J. Simul. Model. (IJSIMM) 2022, 21, 53–64. [Google Scholar] [CrossRef]
- Abercrombie, R.K.; Schlicher, B.G.; Sheldon, F.T. Security analysis of selected AMI failure scenarios using agent based game theoretic simulation. In Proceedings of the 2014 47th Hawaii International Conference on System Sciences, Waikoloa, HI, USA, 6–9 January 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 2015–2024. [Google Scholar] [CrossRef]
- Rafferty, L.; Iqbal, F.; Aleem, S.; Lu, Z.; Huang, S.C.; Hung, P.C. Intelligent multi-agent collaboration model for smart home IoT security. In Proceedings of the 2018 IEEE international congress on internet of things (ICIOT), San Francisco, CA, USA, 2–7 July 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 65–71. [Google Scholar] [CrossRef]
- Kim, S.; Heo, G.; Zio, E.; Shin, J.; Song, J.G. Cyber attack taxonomy for digital environment in nuclear power plants. Nucl. Eng. Technol. 2020, 52, 995–1001. [Google Scholar] [CrossRef]
- Chaudhary, S.; Gkioulos, V.; Katsikas, S. Developing metrics to assess the effectiveness of cybersecurity awareness program. J. Cybersecur. 2022, 8, tyac006. [Google Scholar] [CrossRef]
- Husák, M.; Komárková, J.; Bou-Harb, E.; Čeleda, P. Survey of attack projection, prediction, and forecasting in cyber security. IEEE Commun. Surv. Tutor. 2018, 21, 640–660. [Google Scholar] [CrossRef]
- Garcia Contreras, A.F.; Ceberio, M.; Kreinovich, V. Plans are worthless but planning is everything: A theoretical explanation of Eisenhower’s observation. In Decision Making Under Constraints; Springer: Cham, Switzerland, 2020; pp. 93–98. [Google Scholar] [CrossRef]
- Schrom, E.; Kinzig, A.; Forrest, S.; Graham, A.L.; Levin, S.A.; Bergstrom, C.T.; Castillo-Chavez, C.; Collins, J.P.; De Boer, R.J.; Doupé, A.; et al. Challenges in cybersecurity: Lessons from biological defense systems. Math. Biosci. 2023, 362, 109024. [Google Scholar] [CrossRef]
- Tagarev, T. Towards the design of a collaborative cybersecurity networked organisation: Identification and prioritisation of governance needs and objectives. Future Internet 2020, 12, 62. [Google Scholar] [CrossRef]
- Yoon, K.; Chang, S.Y. Teaching team collaboration in cybersecurity: A case study from the transactive memory systems perspective. In Proceedings of the 2021 IEEE Global Engineering Education Conference (EDUCON), Vienna, Austria, 21–23 April 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 841–845. [Google Scholar] [CrossRef]
- Kavak, H.; Padilla, J.J.; Vernon-Bido, D.; Diallo, S.Y.; Gore, R.; Shetty, S. Simulation for cybersecurity: State of the art and future directions. J. Cybersecur. 2021, 7, tyab005. [Google Scholar] [CrossRef]
- International Organization for Standardization. ISO/IEC 15408 Information Security, Cybersecurity and Privacy Protection. 2022. Available online: https://www.iso.org/standard/72891.html (accessed on 22 August 2025).
- Dar, S.A.; Shairgojri, A.A. Proposed Arrangements and Cyber Security Challenges in Nuclear Domain: An Explanatory study Of India. BOHR Int. J. Comput. Sci. 2022, 1, 104–109. [Google Scholar] [CrossRef]
- King James Bible; Cambridge University Press: Cambridge, UK, 2017.
- Son, J.; Choi, J.; Yoon, H. New complementary points of cyber security schemes for critical digital assets at nuclear power plants. IEEE Access 2019, 7, 78379–78390. [Google Scholar] [CrossRef]
- Turner, L. Common Criteria for Nuclear Cyber Security. In Proceedings of the International Conference on Nuclear Security 2020, Vienna, Austria, 10–14 February 2020; Available online: https://conferences.iaea.org/event/181/contributions/15797/ (accessed on 22 August 2025).
- Aamoth, B.; Lee, W.E.; Ahmed, H. Net-Zero Through Small Modular Reactors-Cybersecurity Considerations. In Proceedings of the IECON 2022—48th Annual Conference of the IEEE Industrial Electronics Society, Brussels, Belgium, 17–20 October 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–5. [Google Scholar] [CrossRef]
- CNBC. Dow CEO Jim Fitterling on Advanced Nuclear Reactor Project in Texas. Squawk on the Street. 12 May 2023. Available online: https://www.cnbc.com/video/2023/05/12/dow-ceo-jim-fitterling-on-advanced-nuclear-reactor-project-in-texas.html (accessed on 22 August 2025).
- Ingersoll, D.T.; Houghton, Z.J.; Bromm, R.; Desportes, C. NuScale small modular reactor for co-generation of electricity and water. Desalination 2014, 340, 84–93. [Google Scholar] [CrossRef]
- Shropshire, D.; Purvins, A.; Papaioannou, I.; Maschio, I. Benefits and cost implications from integrating small flexible nuclear reactors with off-shore wind farms in a virtual power plant. Energy Policy 2012, 46, 558–573. [Google Scholar] [CrossRef]
- Khan, A.A.; Beg, O.A. Cyber Vulnerabilities of Modern Power Systems. In Power Systems Cybersecurity. Power Systems; Haes Alhelou, H., Hatziargyriou, N., Dong, Z.Y., Eds.; Springer: Cham, Switzerland, 2023. [Google Scholar] [CrossRef]
- Macal, C.M. Tutorial on agent-based modeling and simulation: ABM design for the zombie apocalypse. In Proceedings of the 2018 Winter Simulation Conference (WSC), Gothenburg, Sweden, 9–12 December 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 207–221. [Google Scholar] [CrossRef]
- Wood, D.J.; Gray, B. Toward a Comprehensive Theory of Collaboration. J. Appl. Behav. Sci. 1991, 27, 139–162. [Google Scholar] [CrossRef]
- Alozie, N.; Yang, H.; Rachmatullah, A.; Lopez-Prado, B. Toward A More Comprehensive Definition of Collaboration: Scholarly Literature vs. Practitioners. In Proceedings of the 17th International Conference of the Learning Sciences—ICLS 2023; International Society of the Learning Sciences: Montreal, QC, Canada, 2023; pp. 1246–1249. [Google Scholar] [CrossRef]
- Wilensky, U. NetLogo. 1999. Available online: https://www.netlogo.org/ (accessed on 22 August 2025).
- Howe, C.; McWilliam, D.; Cross, G. Chance favours only the prepared mind: Incubation and the delayed effects of peer collaboration. Br. J. Psychol. 2005, 96, 67–93. [Google Scholar] [CrossRef]
- Axelrod, R. The Complexity of Cooperation: Agent-Based Models of Competition and Collaboration: Agent-Based Models of Competition and Collaboration; Princeton University Press: Princeton, NJ, USA, 1997. [Google Scholar]
- Grimm, V.; Berger, U.; DeAngelis, D.L.; Polhill, J.G.; Giske, J.; Railsback, S.F. The ODD protocol: A review and first update. Ecol. Model. 2010, 221, 2760–2768. [Google Scholar] [CrossRef]
- Macal, C.M. Everything you need to know about agent-based modelling and simulation. J. Simul. 2016, 10, 144–156. [Google Scholar] [CrossRef]
- Grimm, V.; Railsback, S.F.; Vincenot, C.E.; Berger, U.; Gallagher, C.; DeAngelis, D.L.; Edmonds, B.; Ge, J.; Giske, J.; Groeneveld, J.; et al. The ODD protocol for describing agent-based and other simulation models: A second update to improve clarity, replication, and structural realism. J. Artif. Soc. Soc. Simul. 2020, 23, 7. [Google Scholar] [CrossRef]
- Grimm, V.; Berger, U.; Calabrese, J.M.; Cortés-Avizanda, A.; Ferrer, J.; Franz, M.; Groeneveld, J.; Hartig, F.; Jakoby, O.; Jovani, R.; et al. Using the ODD protocol and NetLogo to replicate agent-based models. Ecol. Model. 2025, 501, 110967. [Google Scholar] [CrossRef]
- Son, J.; Rojas, E.M. Evolution of collaboration in temporary project teams: An agent-based modeling and simulation approach. J. Constr. Eng. Manag. 2011, 137, 619–628. [Google Scholar] [CrossRef]
- O’Sullivan, T.M.; Ramsay, J. Science and stovepipes: The covid/climate mandate for intelligence analysis and education. J. Homel. Secur. Educ. 2023, 16, 1–7. [Google Scholar]
- Schot, E.; Tummers, L.; Noordegraaf, M. Working on working together. A systematic review on how healthcare professionals contribute to interprofessional collaboration. J. Interprofessional Care 2020, 34, 332–342. [Google Scholar] [CrossRef] [PubMed]
- Morgan, G.; Gordijn, B. A care-based stakeholder approach to ethics of cybersecurity in business. In The Ethics of Cybersecurity; Springer International Publishing: Cham, Switzerland, 2020; pp. 119–138. [Google Scholar]
- CISA. Critical Infrastructure Sectors; Cybersecurity & Infrastructure Security Agency: Washington, DC, USA. Available online: https://www.cisa.gov/topics/critical-infrastructure-security-and-resilience/critical-infrastructure-sectors (accessed on 22 August 2025).
| Nuclear Reactor Type | Power Output | Installation Size |
|---|---|---|
| Conventional Reactor | ~1000 MWe | 1.3 square miles |
| Small Modular Reactor | <300 MWe | 0.05 square miles |
| Microreactor | <20 MWe | One shipping container |
| Hacker Identity | Hacker Motivations |
|---|---|
| Terrorists | Obtain nuclear material for weapons use or initiate nuclear accident to create chaos. |
| Nation-states | Weaken enemies or steal information. |
| Ransomware hackers | Profit by locking and/or threatening powerplant systems for a ransom. |
| Activists | Gain awareness for a specific social or civil cause. |
| Agent-Based Modeling (ABM) | Discrete Event Simulation (DES) |
|---|---|
|
|
|
| Possible SMR Cyberattack Routes | ABM/Common Criteria Simulation Options |
|---|---|
| Part supply chain | Collaboration among members of the supply chain to improve cybersecurity |
| Enhanced use of digital controls | Cyber-defense agents coordinating with vendor agents through the Common Criteria to reduce vulnerabilities |
| Minimal on-site staffing | Low staffing worker agents to study threat of inside attack or outcomes of successful cyberattack |
| Digital integration with other industrial systems | Cyber-attack agents attempting to attack SMRs through the connected industrial systems, along with the effects of collaboration among the connected industries |
| Low Small Modular Reactor | High Small Modular Reactor | |||||||
|---|---|---|---|---|---|---|---|---|
| Low Hacker | High Hacker | Low Hacker | High Hacker | |||||
| Low Vendor | High Vendor | Low Vendor | High Vendor | Low Vendor | High Vendor | Low Vendor | High Vendor | |
| No Collaboration | 17.4% ± 2.0% | 16.6% ± 1.6% | 34.5% ± 2.1% | 34.8% ± 1.9% | 16.4% ± 1.0% | 15.3% ± 1.1% | 33.4% ± 1.1% | 32.3% ± 1.2% |
| With Collaboration | 11.9% ± 1.3% | 13.6% ± 1.7% | 31.1% ± 2.2% | 29.1% ± 1.9% | 9.5% ± 0.9% | 11.5% ± 1.3% | 24.4% ± 1.3% | 25.9% ± 1.6% |
| Reduction in means w/& w/o collab | 31.67% | 18.06% | 10.02% | 16.42% | 42.01% | 24.72% | 26.88% | 19.94% |
| p-value for one-sided T-test | <0.001 | 0.006 | 0.015 | <0.001 | <0.001 | <0.001 | <0.001 | <0.001 |
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zamperini, M.B.; Schwerha, D.J. Simulating Collaboration in Small Modular Nuclear Reactor Cybersecurity with Agent-Based Models. J. Cybersecur. Priv. 2025, 5, 83. https://doi.org/10.3390/jcp5040083
Zamperini MB, Schwerha DJ. Simulating Collaboration in Small Modular Nuclear Reactor Cybersecurity with Agent-Based Models. Journal of Cybersecurity and Privacy. 2025; 5(4):83. https://doi.org/10.3390/jcp5040083
Chicago/Turabian StyleZamperini, Michael B., and Diana J. Schwerha. 2025. "Simulating Collaboration in Small Modular Nuclear Reactor Cybersecurity with Agent-Based Models" Journal of Cybersecurity and Privacy 5, no. 4: 83. https://doi.org/10.3390/jcp5040083
APA StyleZamperini, M. B., & Schwerha, D. J. (2025). Simulating Collaboration in Small Modular Nuclear Reactor Cybersecurity with Agent-Based Models. Journal of Cybersecurity and Privacy, 5(4), 83. https://doi.org/10.3390/jcp5040083








