2. Related Works
Phishing remains a prevalent cybersecurity threat, exploiting deception and human fallibility to circumvent technical safeguards and infiltrate organizational systems. Although technological countermeasures are crucial, a growing body of research highlights the importance of addressing the human element through targeted education and behavioral interventions. This review consolidates findings from recent studies examining the efficacy of simulated phishing attacks, cybersecurity training, and behavioral insights into phishing vulnerability, offering context for the current research conducted at a Croatian university.
Simulation-based phishing interventions have emerged as a prevalent method for evaluating and enhancing employee awareness and security. Ahmad et al. [
1] created a simulation-based training platform integrated with interactive learning tools, which markedly enhanced users’ proficiency in identifying and responding to phishing emails. Their methodology also prioritized real-time feedback and user engagement, two crucial components identified as essential for improving training retention. Hillman et al. [
2] conducted a comprehensive enterprise study, demonstrating that contextual and personalized phishing simulations were more effective in provoking authentic user behavior; however, they observed that training administered immediately before simulations did not necessarily reduce click-through rates. This suggests that the timing of simulations and the realism of scenarios may be more essential than the closeness of training.
Alternative educational paradigms, including serious games and microlearning methodologies, have been thoroughly investigated. Kävrestad et al. [
3] evaluated two methodologies—game-based learning and context-based micro-training (CBMT)—and found that both were effective in teaching users how to recognize phishing emails. CBMT demonstrated marginally greater efficacy, presumably attributable to its provision of pertinent information at the time of decision-making. In a similar vein, Jayakrishnan et al. [
4] presented “PickMail,” a serious game designed to simulate email evaluation tasks, achieving a 92.6% accuracy rate in phishing detection among trained participants. Wen et al. [
5] developed a role-playing game that simulated phishing attacks, demonstrating that users not only retained greater knowledge but also exhibited higher engagement compared to those trained with conventional materials.
Extensive data analysis has also guided training methodologies. Sutter et al. [
6] employed machine learning models to forecast user vulnerability to phishing by examining over 144 simulation campaigns involving 31,000 participants. Their model effectively evaluated the “difficulty” of phishing emails and predicted potential compromise rates, providing a proactive approach for tailoring training. They underscored that group-level training is inferior to user-specific targeting, indicating a necessity for personalized interventions.
Demographic and psychological factors significantly influence phishing behavior. Beu et al. [
7] examined variables including employee tenure, satisfaction, and self-efficacy, discovering that newer and less satisfied employees exhibited a markedly higher propensity to interact with phishing content. Khan and Muntaha [
8] similarly indicated that although cybersecurity training enhances general awareness, its enduring impact is significantly influenced by its ability to cater to user diversity in technical proficiency and personal motivation. Yeoh et al. [
9] corroborated these findings within an operant conditioning framework, observing that reinforcement and behavioral feedback loops significantly improved the learning outcomes of phishing simulations.
Numerous case studies suggest that environmental factors, including seasonal timing, occupational position, and organizational framework, can influence phishing outcomes. Ciupe and Orza [
10] examined simulation data from a technical university and noted heightened vulnerability during academic intervals. Sirawongphatsara et al. [
11] investigated the influence of various phishing email content types on behavior through two simulation rounds within a railway organization, emphasizing that the framing and familiarity of the content significantly affected user responses. McElwee et al. [
12] asserted that behavior-based controls, including recurrent training and observation, proved more efficacious than performance-based metrics in diminishing phishing success rates.
Phishing resistance is often viewed as a function of end-user attentiveness; nevertheless, new studies increasingly ascribe success rates to the growing sophistication of attacker methodologies. Osamor et al. [
13] delineate the progression of phishing from basic mass email initiatives to modern, AI-enhanced, context-aware assaults. Their findings highlight the growing impact of phishing-as-a-service (PhaaS) platforms and machine learning algorithms that can generate misleading content tailored to specific corporate contexts. Kumar et al. [
14] further illustrate that phishing emails generated by large language models far exceed traditional spam in provoking user engagement, primarily due to their human-like linguistic composition and ability to circumvent rule-based filtering systems. Heiding et al. [
15] empirically validate this transition, demonstrating that completely automated spear-phishing tactics produced by generative models can achieve or surpass a 50% click-through rate, competing with carefully constructed human efforts. In a similar vein, Chen et al. [
16] introduce the Phishing Evolution Network (PEN), a dynamic adversarial architecture that utilizes massive language models to develop innovative phishing variants continually. This method not only enhances realism and message variety but also enables attackers to circumvent static detection systems, thereby diminishing the effectiveness of conventional rule-based defenses.
Cross-cultural and sector-specific research further substantiates the intricacy of phishing defense. Aljeaid et al. [
17] conducted phishing simulations in Saudi Arabia, highlighting the importance of iterative testing cycles and debriefings. Chatchalermpun et al. [
18] documented findings from a nationwide exercise in Thailand’s financial sector, indicating that although numerous users disregarded phishing attempts, a substantial fraction still engaged with harmful links. These findings underscore the global significance of phishing threats and the varying levels of preparedness among sectors.
The psychological and cognitive aspects of phishing have been examined. Bayl-Smith et al. [
19] found that the perceived severity of threats and the efficacy of responses were crucial in predicting whether employees reported or engaged with phishing emails. Kudalkar et al. [
20] conducted an extensive user survey revealing that most participants had previously experienced phishing and demonstrated a desire for additional education, indicating a growing demand for training and awareness that has not yet been effectively addressed. Cranford and Lebiere [
21] employed a cognitive simulation model to forecast phishing responses, demonstrating that variables such as memory recency and similarity affect user behavior, indicating that susceptibility to phishing is both situational and psychologically structured.
To mitigate variability in individual risk, Vishwanath [
22] introduced a Cyber Risk Index (CRI) that operates similarly to a credit score, allowing organizations to distribute training and administrative privileges based on a user’s risk profile. This tailored methodology diverges from conventional role-based access, providing a means to synchronize cybersecurity strategy with behavioral data. Scherb et al. [
23] adopted an innovative approach by developing a game that enables users to design and execute phishing attacks, thereby enhancing their comprehension of attacker strategies and vulnerabilities.
Institutional case studies provide additional insight into simulation results in educational settings. Khan and Muntaha [
8] emphasized the necessity for adaptive modules in cybersecurity education programs. In contrast, Jansson and Solms [
24] demonstrated that integrated phishing simulations, accompanied by immediate training, can rapidly enhance resilience against phishing attacks. Finally, Sutter et al. [
6] developed a machine learning classifier to assess the detectability of phishing emails, enabling institutions to tailor training initiatives to user profiles and projected risks.
Collectively, these studies establish a strong evidentiary basis demonstrating that phishing awareness can be markedly enhanced through simulation, focused education, behavioral reinforcement, and adaptive modeling. A significant limitation in most previous research is the segregation of simulation-based and training-based methodologies into distinct interventions. Limited research has directly contrasted these two methodologies within the same organizational framework, particularly in a practical institutional setting such as a university. Moreover, although numerous studies highlight the significance of training content or delivery methods, fewer investigate the influence of external contexts, such as email timing or organizational culture, on user alertness and decision-making.
This study examines the results of phishing simulations and formal cybersecurity education at a Croatian university to address the existing gaps. This research provides new insights into the real-world interaction between types of educational interventions and institutional factors by comparing behavioral responses to three phishing simulations and a single structured training module while analyzing user demographics and response timing. It highlights the significant impact of temporal context, particularly pre-holiday periods, on determining susceptibility to the disease. These findings challenge the presumption that increased training invariably leads to improved outcomes, highlighting the need for dynamic, integrated, and context-sensitive strategies in phishing defense.
3. Methodology
This section outlines the methodological framework employed to systematically evaluate the efficacy of phishing threat detection techniques in an organizational setting. A mixed-method research approach was used, combining quantitative and qualitative methods to provide comprehensive and triangulated insights into phishing detection capabilities and educational outcomes.
The study’s participants were selected from the organization’s employees, with a specific focus on individuals who had access to organizational email accounts and essential data resources. A purposive sampling strategy was employed to ensure participant diversity in terms of professional roles, technical proficiency, and prior experiences with phishing incidents. The sample consisted of 237 participants, offering a representative cohort for strong analytical generalization.
To accurately assess the effectiveness of phishing detection techniques, controlled simulation environments were carefully created to mimic realistic operational scenarios typically encountered in organizational contexts. This simulated environment precisely replicated the organization’s genuine digital infrastructure. In this controlled environment, various phishing attack scenarios were methodically conducted, encompassing fraudulent emails with malicious hyperlinks, harmful file attachments, and advanced social engineering techniques. Each scenario was deliberately designed to represent authentic cybersecurity threats faced in actual corporate settings.
An integrated e-learning platform was implemented to complement the threat detection assessment, providing interactive educational modules that enhance employees’ awareness and response skills regarding phishing attacks. The organized curriculum included theoretical instruction, practical exercises, and evaluative quizzes to assess and reinforce ongoing knowledge. During this study, participants maintained continuous access to the e-learning resource, with comprehensive metrics on engagement, progression through content modules, and assessment results systematically recorded and analyzed.
3.1. Sample Selection, Criteria, Methodology Description
This section outlines a detailed methodological framework for systematically assessing and comparing the efficacy of two strategies designed to reduce employee vulnerability to phishing attacks. To maintain confidentiality and safeguard participant privacy, everyone was assigned a pseudonym in the format “User xxx,” where “xxx” represents a unique numerical identifier. The true identities associated with these pseudonyms are known exclusively to the author.
The primary objectives of this study were threefold: first, to determine which method—simulated phishing exercises or structured online educational interventions—is more effective in diminishing employee susceptibility to phishing threats; second, to assess the long-term effects of each intervention on employee resilience against phishing attacks; and third, to identify and analyze factors that influence the efficacy or limitations of each method.
A systematic, phased research design consisted of three sequential stages: initial assessment, intervention, and final evaluation. In the preliminary phase, a baseline evaluation was performed via simulated phishing attacks on 220 employees, establishing an initial standard for phishing vulnerability within the organization.
In the intervention phase, the sample was increased to 237 employees, randomly divided into two equally representative groups to guarantee diversity across different departmental functions, hierarchical levels, and access to sensitive information. Randomized assignment was employed to reduce selection bias and preserve representational integrity. Group A (n = 117) participated in supplementary controlled phishing simulations to assess susceptibility without an educational intervention. In contrast, Group B (n = 120) participated in an online academic program designed to enhance awareness and defensive skills against phishing threats. This e-learning program included modules on recognizing phishing emails, optimal information security practices, and procedures for reporting suspicious digital communications.
The efficacy of the two interventions was quantitatively evaluated during the final assessment phase via subsequent simulated phishing attacks. Outcomes from follow-up phishing simulations for Group A were meticulously documented, enabling comparative analyses with baseline susceptibility metrics. In Group B, the completion rates of the educational modules were recorded, along with performance metrics that indicated the participants’ understanding and practical implementation of the instructed cybersecurity practices.
The data gathered during these phases were analyzed to measure variations in employee vulnerability to phishing threats resulting from each intervention method. The results offered empirically based insights, facilitating informed conclusions about the relative effectiveness of simulated phishing exercises compared to structured cybersecurity education. This research offers practical recommendations for organizations to enhance their cybersecurity and protect vital data against phishing attacks.
This study notably lacked a third group functioning as a neutral control without intervention. The division of participants into simulation-based and education-based interventions, along with the absence of a non-intervention control group, limits the capacity to attribute the observed behavioral changes exclusively to the interventions. Subsequent research should include a genuine control group to distinguish the impacts of environmental variables or temporal fluctuations in phishing vulnerability.
3.2. Attack Simulation and E-Learning Environment Description
The phishing simulation was executed utilizing the Microsoft Defender for Office 365 platform, as outlined in official Microsoft documentation. This platform is specifically designed to provide extensive protection against sophisticated cyber threats, including phishing, ransomware, and related cyberattacks. This advanced tool enables organizations to conduct realistic phishing simulations and deliver targeted educational content, thereby enhancing employee skills in identifying and mitigating phishing threats. The license granted for this study allowed complete access to all essential functionalities needed to create realistic phishing scenarios. Mastery of each simulation configuration tool was crucial for precisely executing these simulations.
The simulation parameters were based on social engineering techniques from the MITRE ATT&CK framework, a widely acknowledged repository of cyber adversaries’ tactics, methods, and procedures (TTPs). This framework relies on empirical observations and serves as a definitive knowledge repository for constructing resilient threat models and strategic defense strategies, enabling organizations to effectively prevent, detect, and respond to cyber incidents.
Phishing attack simulations in Microsoft Defender can be customized to meet goals. Seven distinct scenario types were present: credential harvesting (theft of usernames and passwords), malicious email attachments, links within email attachments leading to harmful content, links in the email body directing to malicious content, links to compromised but legitimate websites, launching Azure-based applications seeking unauthorized data access, and instructional scenarios for reporting phishing attempts.
Content creation is essential for the authenticity and efficacy of simulations. Microsoft Defender offers a range of predefined templates, each tailored for specific scenarios, that users can examine and select as appropriate. The platform also facilitates the creation of tailored content, which requires intricate manual configuration of specific attack parameters.
Phishing emails must meet several criteria, including defining the sender’s identity, specifying the email source address, customizing the subject line, tailoring linguistic elements to recipient demographics, and embedding phishing links. Email content can be manually created, selected from pre-designed templates, or tailored through direct HTML editing, providing detailed personalization options.
A crucial component of the simulation entails the deliberate selection of user groups. Participant selection may be entered manually or imported in bulk via a .csv file. Integration with Azure Active Directory (Azure AD) guarantees email authenticity and limits access to verified organizational accounts. Filtering criteria encompass departmental affiliation, geographic location, or other specified parameters. Furthermore, a thorough organizational simulation is achievable, with options for selective exclusion if required.
Complementary cybersecurity education was provided via the Moodle LMS platform, an open-source system that offers comprehensive tools for creating, managing, and delivering customized educational content. Moodle’s flexibility and advanced administrative features facilitated the delivery of tailored educational experiences that closely matched organizational needs.
The educational content employed in Moodle was created using the Articulate 360 platform, particularly through the Rise 360 authoring tool. Moodle offers inherent content creation features; however, Articulate 360′s suite provides superior interactive elements, such as simulations, quizzes, and gamified components, which markedly improve learner engagement. The Articulate platform is user-friendly, facilitating swift content creation without extensive technical knowledge and automatically optimizing content for various device formats, including desktops, tablets, and smartphones. Moreover, Articulate 360 facilitates real-time collaborative authoring and reviewing, thereby enhancing the efficiency of content production workflows.
To ensure compatibility and comprehensive tracking of educational outcomes, the produced content was exported in SCORM (Sharable Content Object Reference Model) and xAPI (Experience API, also known as Tin Can API) formats. SCORM standards consistently monitor course completion, engagement time, and assessment scores across Learning Management System (LMS) platforms. The xAPI standard facilitates detailed tracking across diverse educational settings—formal, informal, online, and offline—without dependence on LMS infrastructures, offering enhanced flexibility in learning analytics and reporting.
4. Environmental Development and Implementation
On 28 March 2024, a controlled phishing attack simulation was conducted using the Microsoft Defender for Office 365 platform to establish a baseline assessment of employee vulnerability to phishing threats. The simulation employed the “Link to Malware” social engineering technique, as outlined in the MITRE ATT&CK framework. This scenario involved the incorporation of misleading hyperlinks within email content to assess users’ attentiveness and behavioral responses to potential malware threats.
The educational material incorporated into this simulation was Microsoft’s pre-established Google Security Check template, chosen for its authentic depiction of frequently encountered security alerts, thereby augmenting the authenticity of the simulated threat. The outcomes of this baseline simulation provided essential insights into the organization’s initial cybersecurity stance among its workforce, thereby guiding focused measures to enhance phishing resilience. The specific configuration of the simulation parameters employed in this exercise is thoroughly outlined in
Table 1, ensuring reproducibility and enabling future analytical comparisons:
A phishing simulation was conducted using a “SecurityCheck” attachment embedded in a Word document to mimic standard malicious attachments in actual phishing incidents closely. The simulation incorporated Microsoft-recommended cybersecurity training, and the campaign was scheduled for seven days. Participants who engaged with the embedded phishing link were directed to Microsoft Landing Page Template 5, a predetermined instructional webpage to enhance awareness and educate users on optimal strategies for identifying and countering phishing threats.
Furthermore, an optional Microsoft default notification was enabled, offering users affirmative reinforcement messages, training reminders, and explicit instructions concerning cybersecurity tasks and training goals. The campaign was promptly launched after all simulation parameters had been fully configured.
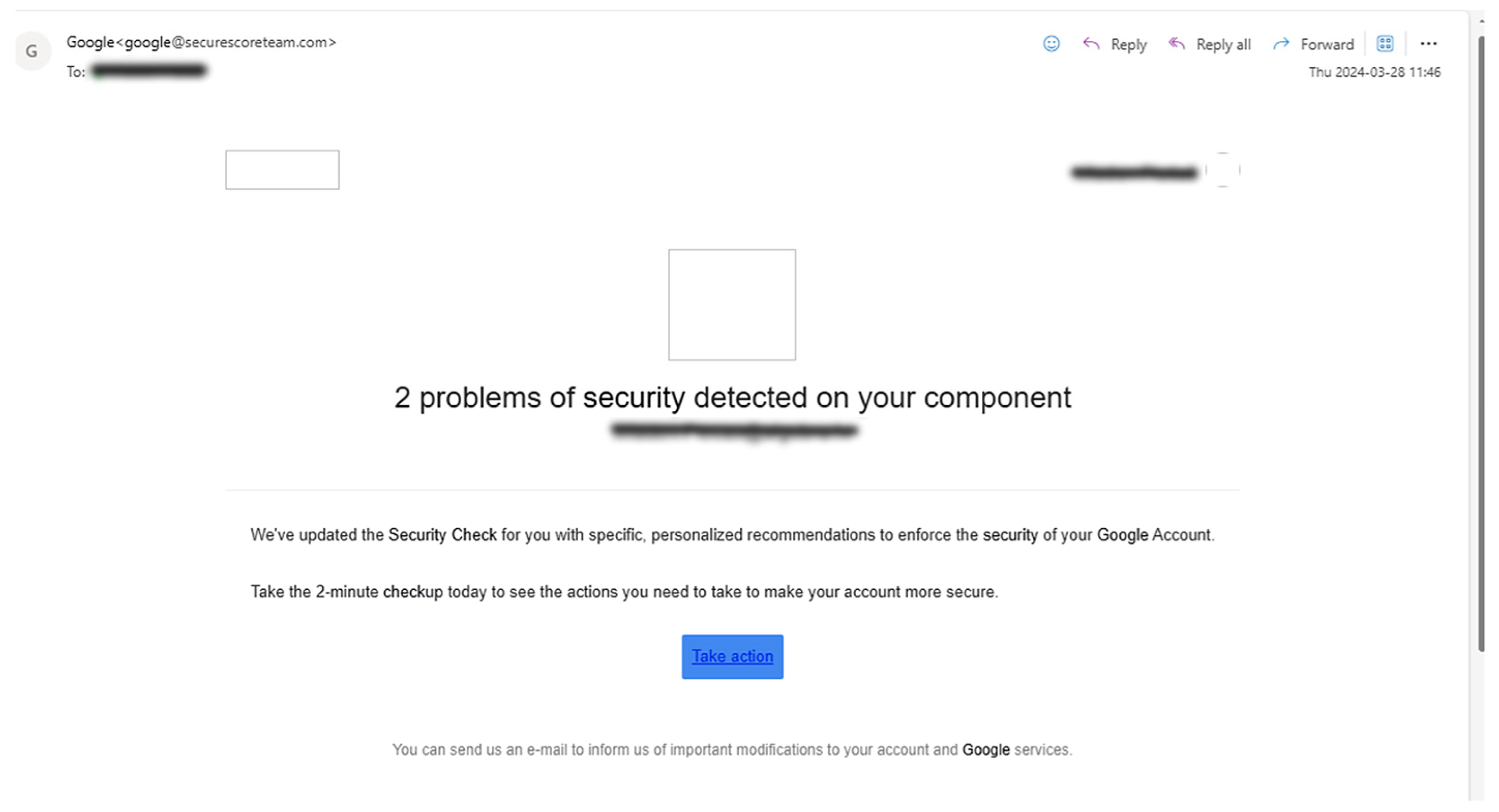
Figure 1 depicts a phishing email disseminated to the company’s designated mailing list, including 220 employees:
The effective execution of this simulated attack yielded empirical data on initial employee vulnerability, which was later analyzed to inform organizational strategies aimed at bolstering resilience against future phishing threats.
A phishing email typically contains several markers that help identify it as deceptive. Upon initial examination, recipients can identify the email’s fraudulent nature through inconsistencies in the sender’s domain, which markedly diverges from Google’s legitimate domain. Additional indicators of phishing encompass the rudimentary composition of the email, coupled with an intentional textual emphasis in yellow. These visual markers serve as deliberate indicators to guide participants in identifying shared characteristics associated with phishing content. Moreover, recipients can discern the dubious nature of interactive elements, such as the “Take action” button, by merely hovering their cursor. This action promptly discloses a concealed URL directing to an unknown website not associated with authentic Google services.
Following the conclusion of the initial phishing simulation campaign, tailored educational materials were created to enhance learning outcomes and bolster cybersecurity awareness. The content was produced using the Articulate 360 online platform, which is recognized for its user-friendly interface and powerful features for creating engaging and interactive educational resources.
Customized educational content titled “Phishing 2024 Mladen” was created for this study. The course homepage utilized a standard template from Articulate 360, chosen for its everyday familiarity among users, thereby enhancing navigation and learner engagement. While primarily following established style templates for uniformity, targeted text formatting modifications were applied in certain sections to improve readability and instructional effectiveness. Furthermore, multimedia resources were incorporated from the platform’s integrated Content Library, with images refined and edited using the platform’s image cropping feature.
The content structure conformed to the optimal guidelines established by the Rise 360 authoring tool. The homepage presented the course and divided the content into five sequential units, methodically directing users through increasingly intricate concepts related to phishing scams. Each instructional unit was meticulously designed to provide participants with extensive knowledge and practical skills for identifying, analyzing, and mitigating phishing threats.
Table 2 outlines the introductory lesson. It provides an overview of phishing, including its historical background, standard techniques utilized by perpetrators, the structure of phishing emails, and the psychological strategies employed to undermine victim alertness.
The lesson also outlined preventive strategies, such as cultivating familiarity with organizational protocols, enhancing situational awareness, and conducting comprehensive assessments of potentially harmful communications. It also introduced participants to vishing—telephone-based phishing—which continues to be a significant cyber threat, highlighting recognition strategies and defensive measures.
This structured educational method systematically enhanced participants’ capacity to identify and counter phishing threats, significantly bolstering organizational cybersecurity resilience.
The second phase of the phishing attack simulation occurred on 22 October 2024, titled “Final”. The campaign was carefully designed and executed using the Attack Simulation Training module of Microsoft Defender for Office 365. The simulation employed a social engineering tactic aimed at credential harvesting, explicitly targeting the acquisition of usernames and passwords.
Unlike prior simulations, the attack content used in this campaign was specifically crafted rather than derived from pre-existing templates offered by Microsoft. The email configuration was organized into two main segments. The initial segment involved specifying the sender’s display name, the sender’s email address, and the subject line of the phishing email and incorporating misleading phishing links. The additional configuration options were maintained at their default settings, as the author determined that these specific settings would not substantially affect the attack’s efficacy.
Table 3 presents a comprehensive summary of all configured parameters, ensuring transparency and reproducibility for future analytical evaluations and comparative analyses:
The system determines the anticipated percentage of compromise, not the individual who generates the malicious email.
A portion of the email content is derived from a prior assessment executed by the IT manager. Subtle modifications have been implemented to eliminate redundancy and align with the objectives of this phishing simulation. Customizing email content can significantly impact the success rate of phishing attacks, leading to numerous attempts and failures in this endeavor. The email’s content was generated, and a harmful link to a counterfeit Microsoft page was embedded:
https://www.doctrical.fr/, accessed on 18 March 2025. The “edit hyperlink” feature altered the display of the link in the word Link, concealing the actual URL of the fraudulent website. This link will gather user data, specifically a username and password. The second segment involves the generation of a counterfeit email, as illustrated in
Figure 2:
Upon concluding the “Final” phishing attack content, distribution parameters were defined using the “Target Users” feature, which identified the recipients of the simulated malicious email. To optimize the selection process and enhance data management, 50% of the organization’s complete distribution list, titled “Employees all,” was exported into a .csv file named “Group A”. This file facilitated the mass importation of specific user addresses into the phishing simulation environment. Consequently, an Excel spreadsheet was created to systematically store and manage addresses extracted from the “Group A” dataset, thereby improving data utility in subsequent analytical phases.
A specific educational intervention titled “Phishing Attack Training” was established in the next phase. This intervention connected participants directly to the online academic content developed earlier in this study. Participants were given seven days to complete the training, which aligned with the objectives and timelines of the primary phishing simulation campaign.
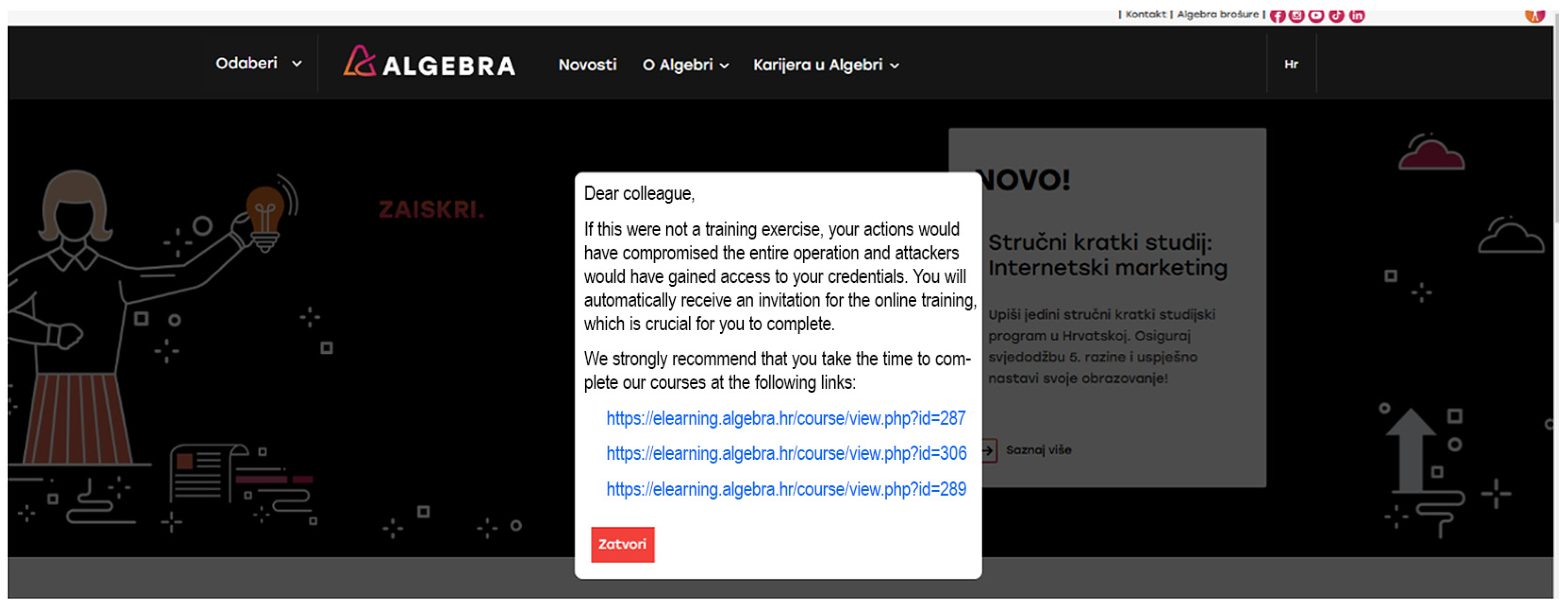
A counterfeit webpage replicating the genuine Algebra website was developed to enhance the realism and credibility of the phishing scenario. This webpage was carefully created by extracting and modifying source code from the authentic Algebra site to replicate its visual and structural features closely. Tailored textual content was deliberately incorporated into this counterfeit page, intended to display immediately upon user access, as illustrated in
Figure 3. This intentional design decision enhanced the simulation’s realism, thus yielding more precise insights into participant behaviors and vulnerability to advanced phishing strategies:
Upon clicking the phishing link, users were promptly informed that they had fallen victim to a simulated phishing attack. The notification additionally conveyed an impending invitation to engage in the specially curated online educational course, as previously outlined in this study. The notification also included links to relevant cybersecurity training resources, offering users the opportunity to enhance their cybersecurity knowledge.
An automated notification was concurrently sent to the users’ email inboxes, urging them to access the e-learning material. This message was carefully crafted with respectful language and a calming tone to alleviate potential anxiety associated with the simulation. The message contained a direct hyperlink titled “E-seminar: Phishing 2024—IT Department|Algebra”, directing recipients to the specific Moodle course accessible online.
Additionally, the platform offered an optional feature to dispatch periodic email reminders to promote sustained engagement with the e-learning material. These reminders can be scheduled to occur either every three days or every other week. Although activating these reminders was not mandatory, providing automated notifications was highly advised as a strategic approach to sustain user engagement and enhance learning outcomes effectively.
Encouragement messages are essential in phishing campaign simulations, as they foster proactive user actions, including reporting suspicious emails. Efficient spam reporting enables organizational cybersecurity teams to refine and optimize protective strategies, thereby strengthening the overall security posture.
The definition and implementation of the encouragement message concluded the preparatory phase for initiating the second phishing attack simulation. Throughout the simulation, the platform generated an extensive, real-time report detailing the attributes of the phishing content and the behavioral responses of the targeted users. The reports were consistently available during the simulation, offering significant insights into user interactions and incident response dynamics.
Two days after the initial phishing simulation was successfully implemented, the remaining users from the “Employees All” distribution list—those excluded from Group A—were integrated into this study. These users were compiled into a new dataset designated “Group B”, and their email addresses were used in a blind carbon copy (BCC) communication titled “IMPORTANT!—Cybersecurity”.
The content of this email deliberately emulates the structure and tone of the phishing emails utilized in the simulation to ensure consistency while reinforcing authentic communication practices. To foster trust and distinguish the message as genuine, the email was dispatched from a legitimate and familiar sender address recognized by all members of Group B. Efforts were made to ensure that the message was free of grammatical errors, thereby enhancing its credibility and authenticity. Notably, it contained a secure and authenticated hyperlink that led the recipient to the official course, “Phishing 2024—IT Department”. This meticulous design ensured that recipients could securely access authentic educational resources.
Members of Group B were not required to complete the cybersecurity training course, as the campaign’s configuration at that time did not permit mandatory participation. As a result, no definitive deadline was established for completing the course. This voluntary strategy was implemented to enhance user engagement while considering the varied professional commitments that could have impeded participation.
The third and final phase of this study commenced on 23 December 2024, following the completion of the second phase of phishing resilience testing, characterized by the initiation of a new simulation. This final scenario simulated a situation in which an attacker had successfully compromised an employee’s account, gaining access credentials to the organization’s Outlook-based email system. By employing these credentials, the attacker accessed the company’s internal email directory and subsequently sent a phishing email to all users in the “Employees All” distribution group. The email included a link to a fraudulent website that was designed to collect additional usernames and passwords.
Before conducting this attack, the simulated adversary was presumed to have analyzed patterns of organizational email communication, thereby acquiring insights into potential behavioral vulnerabilities that could be exploited to enhance the efficacy of the phishing attempt.
The “Final mail_Copy” simulation was created and implemented on the Microsoft Defender for Office 365 platform. The selected social engineering method concentrated on credential harvesting. The sender’s display name and email address were derived from the credentials of a real employee, which have been anonymized in this document for privacy through the use of pseudonyms. The email was deliberately designed to capitalize on the seasonal context, leveraging the pre-holiday ambiance and overall employee complacency to diminish recipients’ alertness and increase the likelihood of successful credential theft. The simulation’s email parameters are configured as outlined in
Table 4:
The phishing email was meticulously crafted to ensure grammatical precision and authenticity, resembling the writing style of the employee whose identity was impersonated as the sender. A misleading hyperlink labeled “Link” was incorporated into the email to augment the message’s credibility. This link directed recipients to a fraudulent Microsoft login page at
https://www.doctrical.fr/ (accessed on 18 March 2025), specifically engineered to obtain user credentials, including usernames and passwords, illegally.
Figure 4 illustrates the visual representation of the phishing email and the corresponding malicious landing page:
The counterfeit webpage’s visual layout was meticulously crafted to closely mimic the authentic Microsoft sign-in interface, thereby enhancing the likelihood of misleading users. Regardless of the credentials entered by the user, the site was designed to allow progression to the next page. This secondary page notified users that they were subjects of a phishing simulation and underscored the necessity of updating their understanding of phishing defense strategies.
After the phishing simulation content was created, all employees categorized within the “Employees All” distribution group were included in the simulation. The user data was extracted into a .csv file and subsequently imported into the simulation platform via the “Import” function, ensuring the complete inclusion of all intended participants as simulation targets.
The explicitly mentioned configuration parameters were preserved from the previous “Final” simulation setup. The campaign duration was modified to two days, consistent with the phishing email’s content, which indicated that the related giveaway would be active for only two days.
The following sections of this paper detail and examine the comprehensive results and analyses of all the simulations performed.
5. Results
This section delineates critical research findings regarding the efficacy of educational programs and phishing attack simulations. Data were gathered utilizing integrated reporting tools within the employed platforms, specifically Microsoft Defender for Office 365, which provides real-time reporting functionalities.
5.1. First Phishing Attack
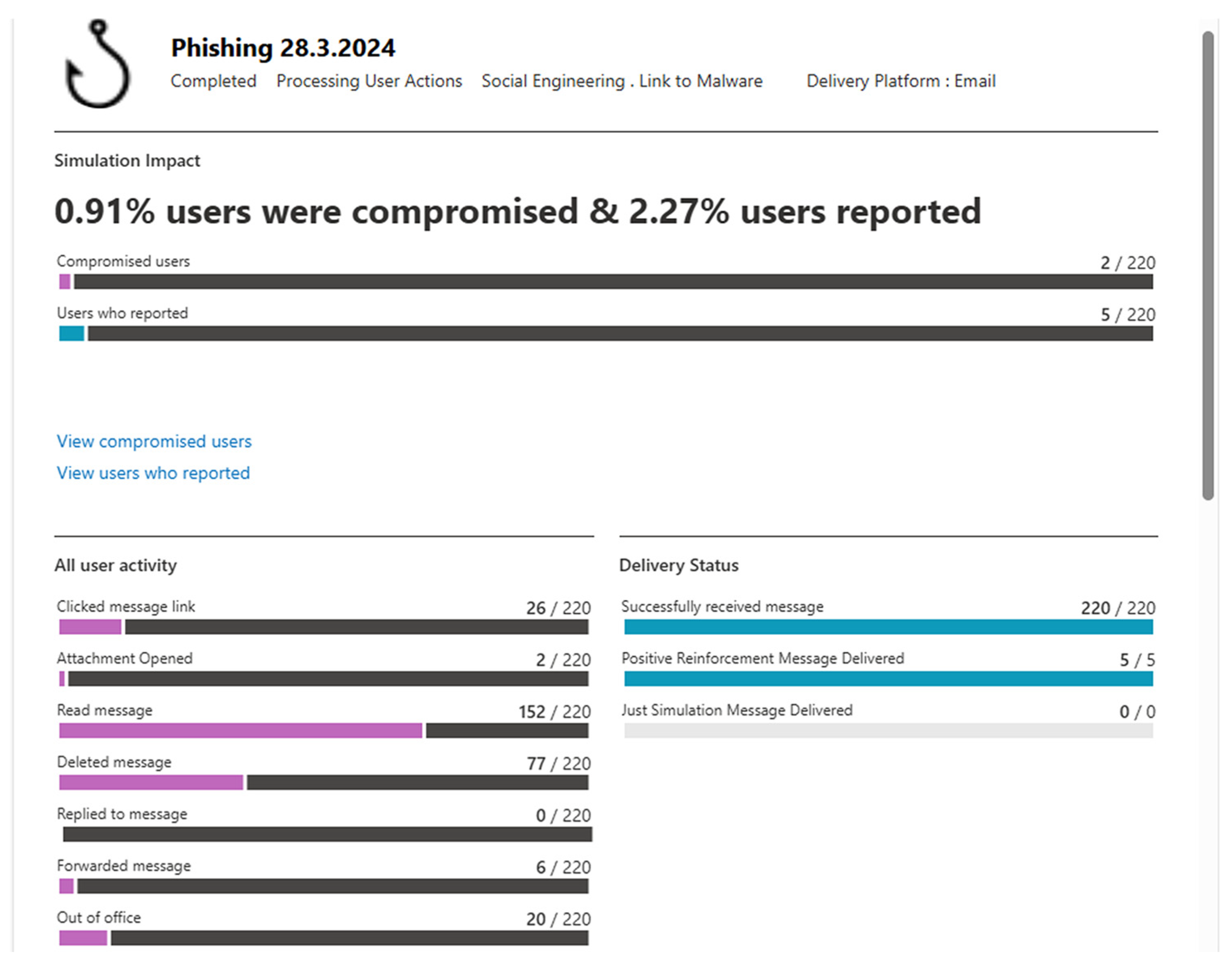
The preliminary phishing attack, which set this study’s baseline (zero point), was executed on 28 March 2024, under the simulation title “Phishing 28.03.2024”.
Figure 5 illustrates the simulation, revealing that, despite 10% of participants having out-of-office settings enabled, a considerable number still accessed the phishing email:
A total of 26 users clicked the embedded link; however, clicking alone did not signify a complete compromise, as the attachment also needed to be opened to categorize the user as “compromised”. A significant observation is the elevated rate of message deletion among recipients.
The gathered simulation data were exported to a .csv file and subsequently imported into an Excel spreadsheet named “The first attack of all zaposlenici.xlsx”. That facilitated the extraction and analysis of demographic data, educational qualifications, departmental affiliation, and age group.
Table 5 presents a departmental analysis of compromises during the initial phishing scenario. A chi-square test was performed to determine whether the number of compromised users varied significantly among departments. The outcome was χ
2(15, N = 220) = 4.06,
p = 0.998, indicating no statistically significant disparities among departments. The absence of variance is probably attributable to the exceedingly low compromise rate during the initial campaign, which affected only two users, both from the higher education department. These findings underscore that initial simulations may fail to reveal departmental vulnerability patterns due to restricted attacker success or initial user prudence.
The statistical findings in
Table 6, which assessed phishing susceptibility by age group in the initial simulation, correspond to those in
Table 5, which investigated the same variable across departments. In both instances, the chi-square tests revealed no statistically significant differences.
The results from
Table 7, which examined compromise rates according to professional credentials, exhibit a similar pattern to those in
Table 5 and
Table 6. Due to the limited number of users (only two) in the initial simulation, there is insufficient statistical variance to determine any significant correlation between certification level and susceptibility to phishing.
This outcome is logical, given the organization’s educational goals. We shall now examine the data about the second phishing attack.
5.2. Second Phishing Attack
During the second phase of this research, participants were systematically divided into two equal-sized cohorts to facilitate comparative analysis of different intervention strategies.
Group A was subjected to a structured phishing simulation to assess behavioral responses in a controlled threat environment.
Group B was instructed to complete an online educational module titled “Phishing 2024—IT Department”, designed to improve phishing awareness and preventative behavior through theoretical instruction.
The following section presents the results obtained from Group A, focusing on the outcomes of the phishing simulation and associated behavioral indicators.
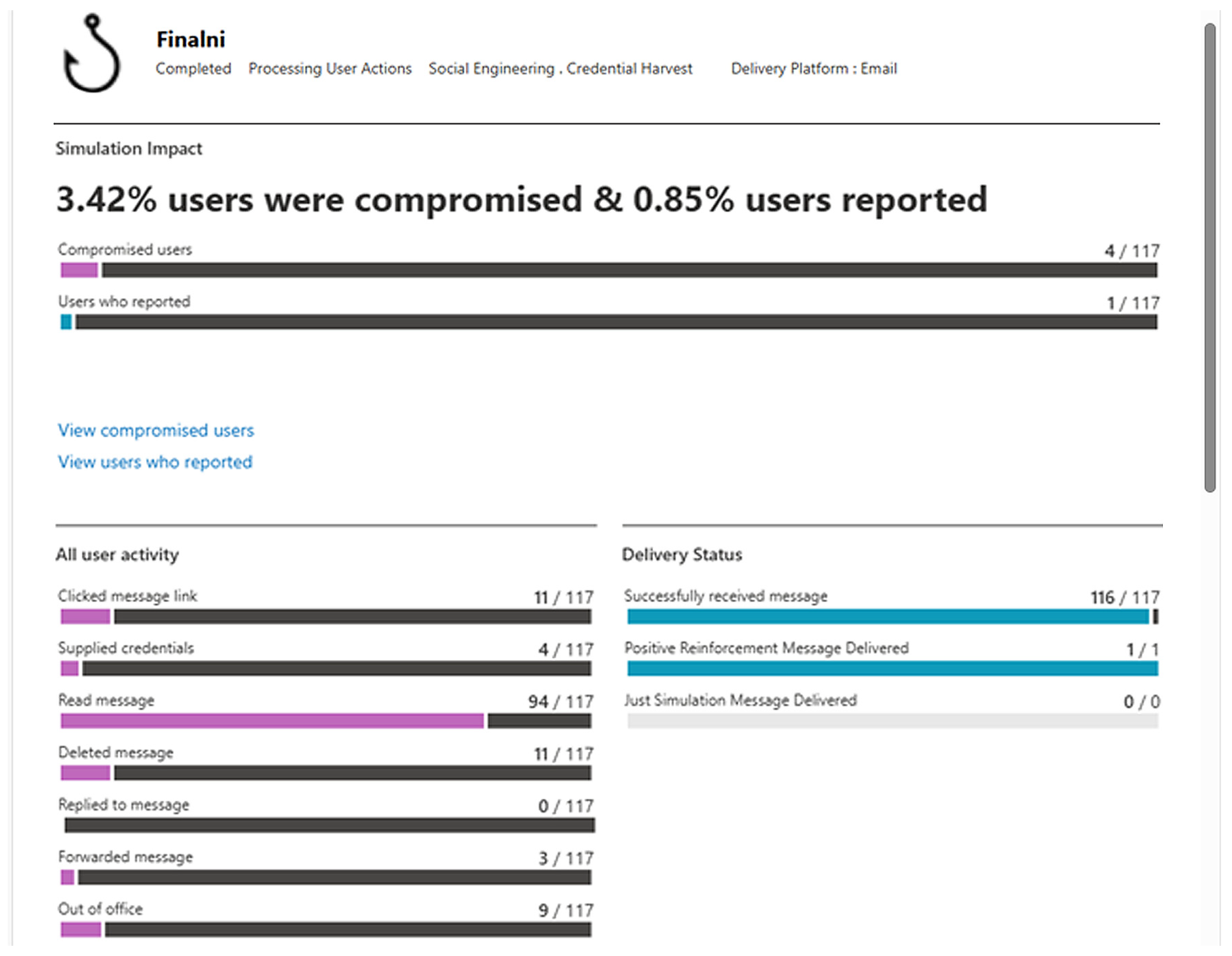
Figure 6 presents the outcomes of the second phishing simulation, executed on 22 October 2024, under the operating designation Final.
Figure 6 illustrates a markedly reduced rate of employee vulnerability, indicating an enhancement in organizational resistance against phishing threats. Significantly, one person did not receive the phishing email, thereby validating the precision and timeliness of the internal distribution list.
The simulation yielded a restricted number of incidents: merely three internal communications were transmitted, and one phishing attempt was documented. These results underscore the persistent necessity to enhance user knowledge and advocate for proactive phishing detection and reporting policies inside the company.
Table 8 presents departmental compromise data from the second phishing simulation. A chi-square test for independence revealed no statistically significant difference in phishing susceptibility across departments (χ
2(14, N = 118) = 3.67,
p = 0.997).
Only four users were compromised overall (three from higher education and one from sales), which again reflects limited attacker success and reinforces the observation that early simulations typically generate low statistical power. These findings further support the strategy of conducting multiple simulation rounds to obtain clearer risk patterns.
The results from
Table 9, which presents compromise data by age group during the second simulation, are consistent with those observed in
Table 8. With only four users compromised overall, the data lacks sufficient variability to identify any meaningful differences in phishing susceptibility across age groups. As such, statistical analysis does not indicate age, which is a significant factor in this simulation round.
A similar pattern is evident in
Table 10, which examines the number of compromised users by professional qualifications. Given that only four employees were compromised in total during the second simulation, there is insufficient statistical variability to establish any significant relationship between educational qualifications and phishing susceptibility.
Simultaneously with the phishing simulation administered to Group A, participants in Group B underwent a preventive educational intervention. This cohort was directed to complete the online course named “Phishing 2024—IT Department,” aimed at enhancing conceptual comprehension and identification of phishing attacks. This section presents the results of the intervention, highlighting the participants’ post-training evaluation outcomes and assessing the potential impact of structured education on phishing awareness and readiness.
Attendance data from Moodle was exported to an Excel sheet for analysis, offering a direct tabular format due to the lack of a simplified graphical reporting option in Moodle.
Table 11 displays the distribution of users by department and their corresponding completion rates for the phishing awareness course assigned to Group B. A chi-square test for independence was conducted to assess whether departmental affiliation influenced the likelihood of course completion. The result (χ
2(10, N = 130) = 9.14,
p = 0.519) revealed no statistically significant differences across departments.
These findings suggest that factors beyond the organizational unit, such as individual engagement, perceived relevance, or institutional encouragement, may have played a more significant role in determining training completion rates. To enhance the effectiveness of educational interventions, future strategies may need to incorporate more targeted motivational or supervisory mechanisms.
Table 12 analyzes compromise rates by age group during the second phishing simulation. A chi-square test was performed to determine whether the likelihood of falling victim to phishing significantly varied across age categories. The result (χ
2(5, N = 119) = 8.84,
p = 0.116) did not reach statistical significance, although the 40–49 age group accounted for the most significant number of compromised users.
These findings suggest a possible trend that merits further investigation into larger or repeated samples but do not provide sufficient evidence to conclude that age was a statistically reliable predictor of phishing susceptibility in this simulation round.
Table 13 presents phishing compromise data stratified by professional qualifications during the second simulation. A chi-square test for independence revealed no statistically significant differences across qualification levels (χ
2(4, N =120) = 7.74,
p = 0.101).
While users with secondary education exhibited a proportionally higher rate of compromise, and those with advanced degrees showed lower rates, the results did not reach statistical significance. These findings suggest a potential trend that warrants further exploration in larger studies. Still, they do not support a definitive conclusion regarding educational background as a determinant of phishing susceptibility.
The second phase of this study entailed a comparative evaluation of two unique interventions: direct phishing simulation (Group A) and structured educational training (Group B). Although the aggregate number of compromised users in the phishing simulation was low, the data indicate developing patterns of vulnerability, notably among certain age and education demographics, but none achieved statistical significance. The examination of training participation highlighted the consistency of course completion within departments, suggesting that factors such as individual motivation and corporate culture may be more significant than institutional affiliation. These findings highlight the intricacy of user behavior in phishing scenarios and advocate for the implementation of multifaceted defensive solutions. The subsequent section presents the findings of the third phishing attempt, evaluating enduring behavioral patterns and the aggregate effect of the implemented interventions.
5.3. Third Phishing Attack
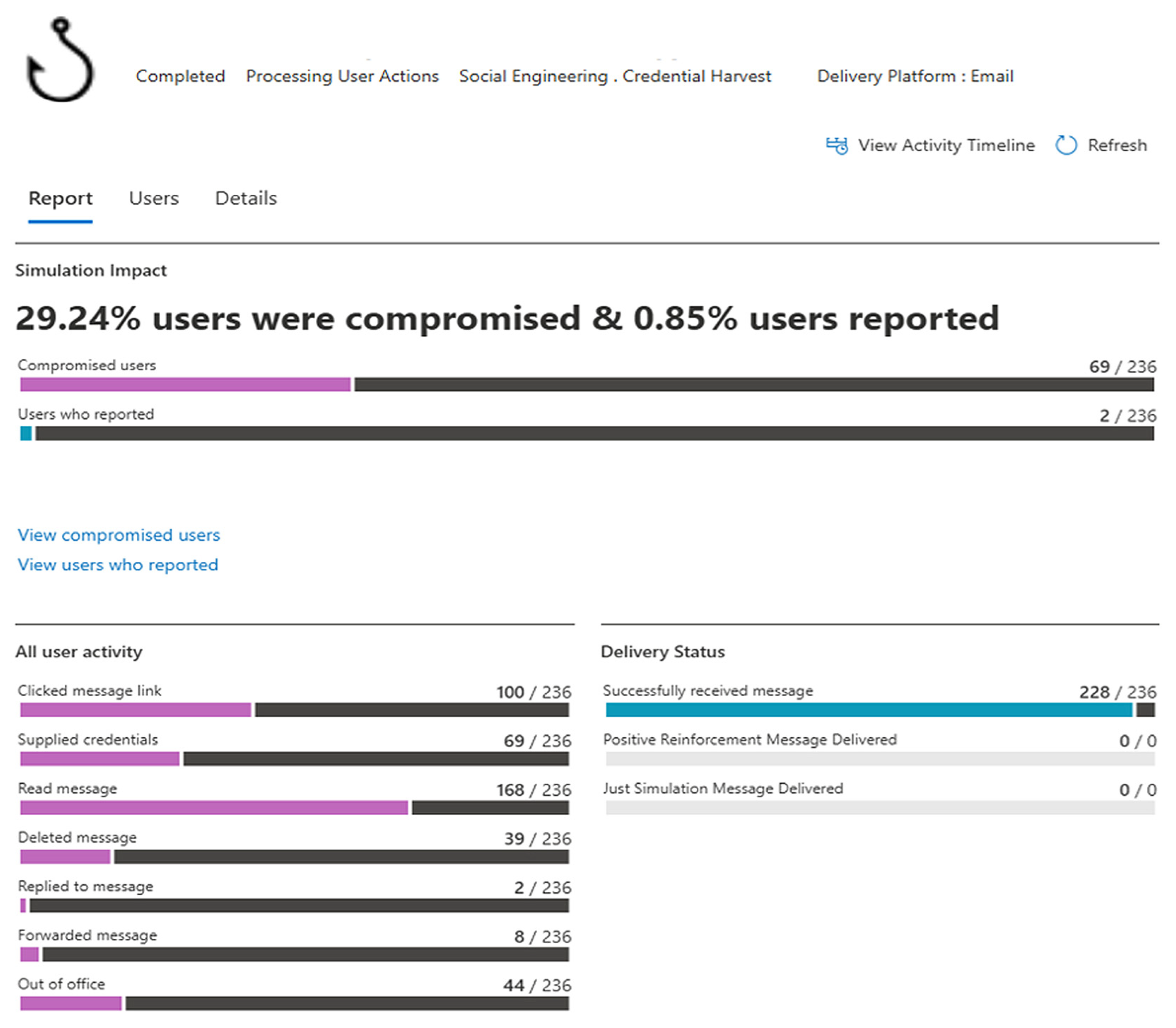
The third and final phishing attack was executed, yielding results consistent with prior simulations. Data were gathered using Microsoft Defender for Office 365 and compiled into the Excel file “Third Attack All Employees”.
Figure 7 presents a graphical summary of the results:
The third simulation demonstrated a significantly elevated phishing success rate. The timing of the attack, coinciding with the pre-holiday period, is posited to have been significant. During this interval, employee vigilance typically diminishes due to extensive vacation planning, making them more vulnerable to phishing threats. This contextual factor was foreseen during the simulation planning and validated by the outcomes.
The third phishing simulation’s graphical outcomes indicate that many employees were absent from the office during the attack period. This phenomenon aligns with the pre-holiday season, when numerous employees take planned leave. Such conditions inherently increase an organization’s susceptibility to phishing threats, as reduced workforce presence and diminished vigilance may undermine its overall security posture.
Reorganizing demographic data into structured tables facilitated a comprehensive and meticulous analysis in subsequent sections. An extra column was added to these tables to explicitly record the number of individuals who failed in the third phishing simulation. Additionally, the dataset was divided to differentiate between employees who had undergone phishing awareness training and those who engaged exclusively in the second phishing simulation.
Table 14 delineates departmental vulnerabilities identified during the third phishing simulation. The results demonstrate significantly elevated attack success rates in the Higher Education and Sales departments.
Table 14 compares phishing compromise rates in the third simulation between participants who received online training and those who had previously participated in a phishing simulation. A chi-square test for independence was conducted to determine whether the type of prior intervention had a significant influence on phishing susceptibility. The result (χ
2(1, N = 237) = 1.07,
p = 0.300) indicated no statistically significant difference between the two groups.
Although the group that completed the educational training demonstrated a slightly lower compromise rate in absolute terms, the lack of statistical significance suggests that both forms of intervention may have a comparable effect in mitigating phishing risk. These findings underscore the importance of continually reinforcing both practical and theoretical approaches to sustain organizational resilience.
Table 15 illustrates the distribution of phishing susceptibility in the third simulation, categorized by age groups and differentiated by prior intervention type (training versus simulation). A chi-square test for independence was performed to determine whether the type of intervention had a significant influence on phishing vulnerability among different age groups. The analysis revealed no significant difference (χ
2(1, N = 237) = 1.61,
p = 0.204), suggesting that phishing susceptibility was not substantially affected by the type of intervention when accounting for age.
The findings suggest that both interventions may have similar protective effects across all age demographics and that continuous or integrated techniques may be necessary to achieve more robust and enduring behavioral modifications.
Table 16 displays phishing compromise rates from the third simulation, categorized by participants’ professional qualifications and the type of intervention they had previously undergone. A chi-square test for independence was conducted to assess whether formal education level affected the efficacy of either intervention. The outcome (χ
2(1, N = 231) = 1.04,
p = 0.307) indicated no statistically significant difference in results between the training and simulation groups.
The data indicate that educational background did not significantly influence the efficacy of either method in reducing phishing risk. Consequently, both intervention modalities appear to yield comparable outcomes across all qualification levels, underscoring the importance of integrating practical and theoretical approaches to engage a diverse user demographic.
The third phishing simulation demonstrated a significantly elevated compromise rate compared to earlier rounds, possibly due to seasonal contextual elements. Notwithstanding these heightened risk levels, the comparative examination of intervention strategies—phishing simulation versus structured training—did not reveal statistically significant variations across departmental, age, or professional qualification categories.
Chi-square tests did not reveal significant differences in phishing sensitivity related to previous exposure to educational or simulated interventions. This consistency across demographic and organizational levels indicates that both types of intervention have a similar impact on user behavior in the near run.
These findings highlight the inherent limitations of singular training or simulation exercises and advocate for the integration of both practical and theoretical components within ongoing cybersecurity awareness initiatives. Consistent, targeted actions tailored to the organizational context and temporal weaknesses may provide stronger protection against social engineering risks.
5.4. Additional Analysis
Based on these results, we were able to establish additional correlations between various attacks at different stages and individuals responding to one or more attacks.
Table 17 monitors the evolution of employee vulnerability across the three simulations within a uniform participant group:
The data suggests a troubling trend: employee resilience declines following successive assaults.
Table 18 illustrates the relationship between educational engagement and phishing resilience:
Further analysis was performed to investigate the cumulative impact of multiple phishing simulations compared to a mixed-method strategy that incorporated instruction.
Table 17 delineates the progression of vulnerability among participants who engaged in all three scenarios. The substantial rise in the number of compromised persons during the third attack (from 1 to 39) indicates a marked deterioration in resilience over time.
Table 18 contrasts this with users who, after the initial phishing simulation, participated in formal phishing awareness education and then faced a third attack. Notwithstanding an early compromise in one instance, the total of compromised users in the third attack was 30, which is fewer than the 39 recorded in the simulation-only cohort.
A chi-square test for independence was conducted to determine if this difference was statistically significant. The outcome (χ2(1, N = 237) = 2.57, p = 0.109) demonstrates no statistically significant disparity between the two paths. Nonetheless, the outcome suggests a possible trend supporting educational intervention. That indicates that although neither method offers complete protection, structured education may provide some improvement in long-term resistance to phishing compared to simulations alone.
Table 18 underscores a troubling implication: of the 30 employees who underwent phishing awareness training and engaged in all three simulations, all 30 ultimately failed the third simulation. That raises doubts about the sustainability and effectiveness of a singular educational effort. Although training may enhance immediate awareness of phishing strategies, its efficacy appears to wane over time, particularly during high-pressure or low-alert periods (e.g., holidays). That also suggests a possible overestimation of training retention or a disconnect between the training material and the evolving strategies of threats.
These findings indicate the requirement for
Increased frequency and adaptable training cycles, potentially incorporating just-in-time refreshers.
Dynamic simulation content that updates to represent emerging danger vectors.
Incorporation of behavioral analytics to customize training intensity and frequency.
Both tables demonstrate that static methodologies are inadequate. Organizations should implement continuous, behavior-aware, and adaptive defensive techniques to maintain high levels of end-user alertness and resilience.
5.5. Advantages and Disadvantages of Using Phishing vs. Education
Developing online training on phishing awareness is technically uncomplicated, as contemporary drag-and-drop authoring tools provide pre-designed templates, multimedia components, assessments, one-click publishing to a learning platform, automated email invitations, and dashboards that track course engagement, participation duration, and assessment outcomes. However, converting that convenience into genuinely impactful lessons continues to be labor-intensive: designers must still create realistic examples, compose clear explanations, record voice-overs or videos, and update content as scams progress. Licenses can burden limited budgets; even polished modules may fail if employees perceive them as routine obligations. Simulated phishing campaigns advance beyond static lessons by enabling organizers to deploy pre-constructed scenarios within an hour, incorporate just-in-time prompts, schedule subsequent micro-lessons, and collect detailed metrics, such as click-through rates, form submissions, and response times, all of which inform subsequent enhancements. Cloning and modifying scenarios accelerate iteration and facilitate alignment with seasonal threats or departmental workflows. Nonetheless, the service typically requires an additional security subscription and necessitates heightened administrative privileges; devising credible, organization-specific lures still depletes creative resources; inadequately designed exercises may incite anger, embarrassment, or stress among employees who perceive themselves as deceived. Effective communication, supportive leadership, and a feedback mechanism can alleviate those risks. Collectively, structured e-learning establishes foundational knowledge, whereas meticulously orchestrated simulations enhance it through practical application, forming a multifaceted defense if teams maintain equilibrium among innovative endeavors, licensing expenditures, and employee morale.