A Survey on Immersive Cyber Situational Awareness Systems
Abstract
1. Introduction
- It provides an overarching analysis of ICSA visualization and interaction techniques identified in the literature. Each visualization and interaction technique is reported in the context of perception, comprehension, and projection of ICSA systems. The visualization and interaction techniques are categorized based on a novel taxonomy separately.
- It gives a comprehensive analysis of the situational awareness levels achieved for ICSA in the literature. For the first time, each level of situational awareness is described in the context of ICSA. The existing literature is categorized based on the defined levels of ICSA (i.e., perception, comprehension, projection).
- It presents a high-level investigation of evaluation mechanisms used to validate ICSA systems. Each evaluation mechanism has been critically examined, focusing on ICSA usability evaluation, user demographics, performance, and cognition metrics. The evaluation mechanisms are categorized based on the methodology employed for validating ICSA systems.
- It presents a combined analysis of ICSA visualization/interaction techniques, evaluation mechanisms, and levels of ICSA. This thorough analysis leads to the development of a reference framework for designing and evaluating ICSA systems. Additionally, the analysis suggests future research directions and highlights the industrial implications of ICSA systems.
2. Research Methodology
2.1. Research Questions
2.2. Search Strategy
- Search Method: We first designed an inclusive search string containing the terms related to our research questions. Then, we ran the search string on Scopus to retrieve the maximum number of relevant studies on ICSA systems.
- Search Terms: Our search string included all the terms that are relevant to the research objectives (i.e., RQs) of this survey. Figure 1 shows the developed search string that is mainly composed of two parts: (i) the first part consisted of different “immersive technologies”, and (ii) the second part contained the synonyms and relevant terms of “cybersecurity” and “cyber situational awareness”. It is important to note that the terms were searched in the title, keywords, and abstract of the papers available at Scopus to identify and extract the relevant literature on ICSA systems.
- Data Sources: Similar to [21], we used the Scopus search engine only to identify the relevant literature on ICSA systems for this survey. This is mainly because of the observations reported in [22,23,24,25], which justify that Scopus indexes a large amount of peer-reviewed papers and journals indexed by many other digital databases such as IEEE Xplore, ACM Digital Library, Science Direct, SpringerLink, and Wiley Online Library.
2.3. Inclusion and Exclusion Criteria
2.4. Study Selection
- Automatic Search: We ran our search string on the Scopus search engine to identify existing literature on ICSA systems. As a result, we retrieved 3536 potential studies.
- Title-Based Selection: We analyzed the title of the 3536 studies. If a paper title was relevant to the research questions of this survey, we included that paper. In case we were not sure about the relevance of a paper, that paper was transferred to the next phase. At the end of this phase, we had 327 papers.
- Duplication Removal: As we only consulted one database (i.e., Scopus) to retrieve the existing literature, no duplicate study was found during our study selection process.
- Abstract-Based Selection: We thoroughly read the abstracts and conclusions of the remaining 327 studies to check their relevance to our research questions. Here, we also applied the inclusion and exclusion criteria (Table 2) to the abstracts of papers. Consequently, this phase reduced the pool of papers from 327 to 139.
- Full-Text-Based Selection: We read the full text of 139 studies, and applied the inclusion and exclusion criteria on them. As a result, we obtained 36 relevant studies.
- Snowballing: We performed forward and backward snowballing [26] on the 36 studies to identify more literature on ICSA systems. This gave us 7 potentially relevant studies that were then passed through our inclusion and exclusion criteria. Consequently, we finalized 43 relevant studies for this survey.
2.5. Data Extraction and Synthesis
2.5.1. Data Extraction
2.5.2. Data Synthesis
- Familiarizing with Data: We obtained an initial understanding of the extracted visualization techniques (D9), interaction features (D10), levels of cyber situational awareness (D11), and evaluation mechanisms (D12) for ICSA systems.
- Generating Initial Codes: We developed a rudimentary list of similar visualization techniques, interaction features, cyber situational awareness levels, and evaluation mechanisms for ICSA systems. In some cases, we re-examined the retrieved studies to verify the developed list.
- Searching for Themes: We categorized the initial codes for each data item into potential themes. For example, visualization techniques based on icons are combined under the theme of “Iconic Displays”.
- Reviewing and Refining Themes: We analyzed the identified themes against each other to detect similar and irrelevant themes. For example, spatial visualizations and geometric visualizations were merged with each other due to their same characteristics.
- Defining and Naming Themes: A clear and concise name was defined for each theme.
3. Visualization and Interaction Techniques
3.1. Visualization Techniques for ICSA
3.2. Interaction Techniques for ICSA
4. Levels of Immersive Cyber Situational Awareness
4.1. Perception
4.2. Comprehension
4.3. Projection
5. Evaluation Mechanisms for ICSA Systems
6. Discussion
6.1. A Reference Framework for Designing and Analyzing ICSA Systems
6.2. Future Research Areas
6.3. Industrial Implications of ICSA Systems
6.4. Limitations
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Williams, C.M.; Chaturvedi, R.; Chakravarthy, K. Cybersecurity risks in a pandemic. J. Med. Internet Res. 2020, 22, e23692. [Google Scholar] [CrossRef] [PubMed]
- Arogbodo, M. Impacts of the COVID-19 Pandemic on Online Security Behavior Within the UK Educational Industry. 2022. Available online: https://osf.io/preprints/psyarxiv/h5qgk_v1 (accessed on 12 July 2024).
- Mouna, B.; Yassine, M. Business Leadership in E-Commerce in the USA: The Impact of Blockchain Technology. Bus. Ethics Leadersh. 2024, 8, 116–128. [Google Scholar] [CrossRef]
- Kuzior, A.; Tiutiunyk, I.; Zielińska, A.; Kelemen, R. Cybersecurity and cybercrime: Current trends and threats. J. Int. Stud. 2024, 17, 220. [Google Scholar] [CrossRef]
- 2024 Data Breach Investigations Report. 2024. Available online: https://www.verizon.com/business/resources/reports/2024-dbir-data-breach-investigations-report.pdf (accessed on 3 May 2025).
- Thirupathi, L.; Vasundara, B.; Sundaragiri, D.; Ch, V.B.; Gugulothu, R.; Pulyala, R. Understanding and Addressing Human Factors in Cybersecurity Vulnerabilities. In Human Impact on Security and Privacy: Network and Human Security, Social Media, and Devices; IGI Global: Hershey, PA, USA, 2025; pp. 13–38. [Google Scholar]
- Button, M.; Shepherd, D.; Blackbourn, D.; Sugiura, L.; Kapend, R.; Wang, V. Assessing the seriousness of cybercrime: The case of computer misuse crime in the United Kingdom and the victims’ perspective. Criminol. Crim. Justice 2025, 25, 670–691. [Google Scholar] [CrossRef]
- Endsley, M.R. Design and evaluation for situation awareness enhancement. Proc. Hum. Factors Soc. Annu. Meet. 1988, 32, 97–101. [Google Scholar] [CrossRef]
- Ullah, F.; Ye, X.; Fatima, U.; Akhtar, Z.; Wu, Y.; Ahmad, H. What Skills Do Cyber Security Professionals Need? arXiv 2025, arXiv:2502.13658. [Google Scholar]
- Barford, P.; Dacier, M.; Dietterich, T.G.; Fredrikson, M.; Giffin, J.; Jajodia, S.; Jha, S.; Li, J.; Liu, P.; Ning, P.; et al. Cyber SA: Situational awareness for cyber defense. In Cyber Situational Awareness; Springer: Berlin/Heidelberg, Germany, 2010; pp. 3–13. [Google Scholar]
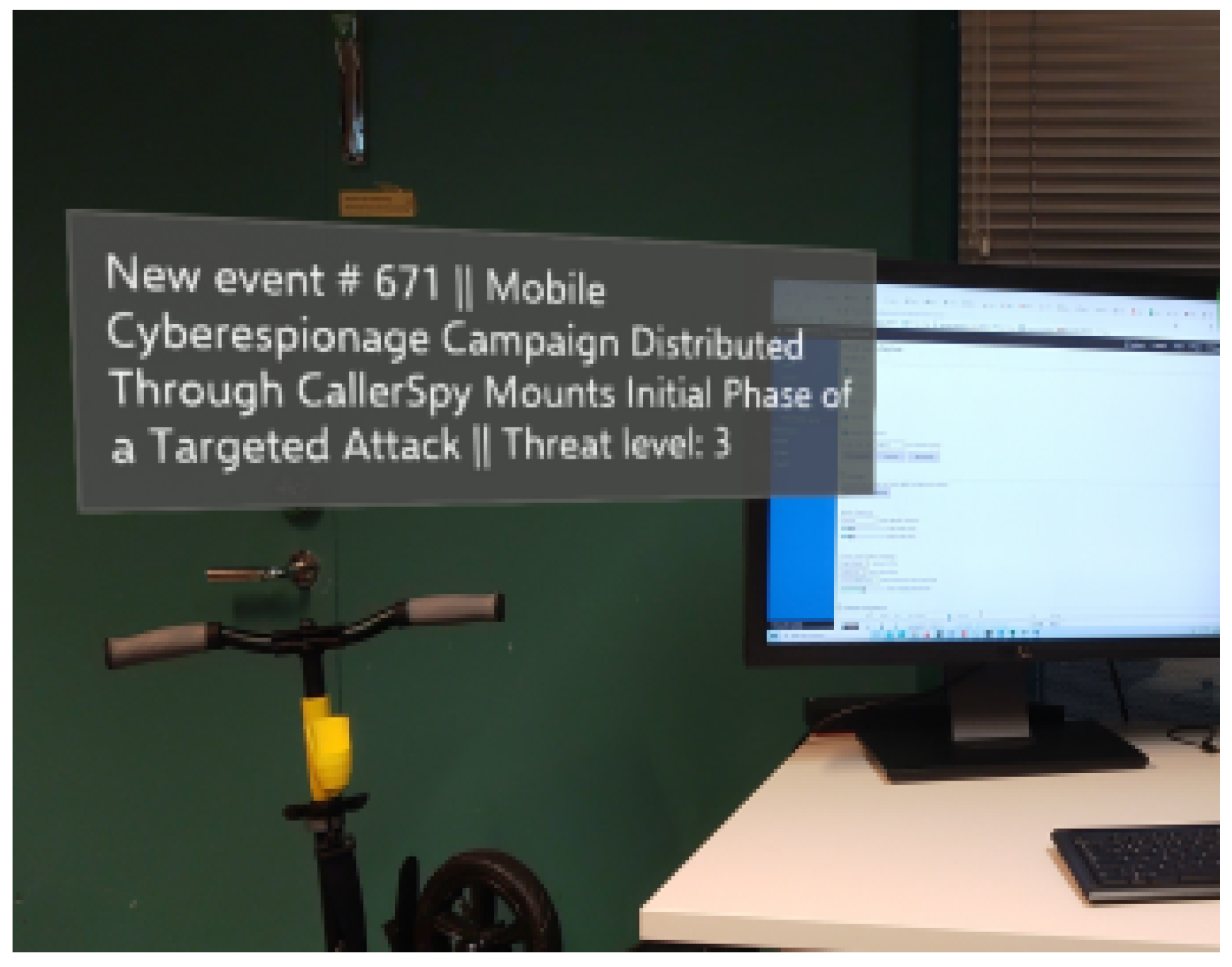
- Sukhija, N.; Haser, C.; Bautista, E. Employing Augmented Reality for Cybersecurity Operations in High Performance Computing Environments. In Proceedings of the Practice and Experience in Advanced Research Computing on Rise of the Machines (Learning), Chicago, IL, USA, 28 July–1 August 2019; pp. 1–4. [Google Scholar]
- Mattina, B.; Yeung, F.; Hsu, A.; Savoy, D.; Tront, J.; Raymond, D. MARCS: Mobile augmented reality for cybersecurity. In Proceedings of the 12th Annual Conference on Cyber and Information Security Research, Oak Ridge, TN, USA, 4–6 April 2017; pp. 1–4. [Google Scholar]
- Chopra, S.; Ahmad, H.; Goel, D.; Szabo, C. ChatNVD: Advancing Cybersecurity Vulnerability Assessment with Large Language Models. arXiv 2024, arXiv:2412.04756. [Google Scholar]
- Beitzel, S.; Dykstra, J.; Huver, S.; Kaplan, M.; Loushine, M.; Youzwak, J. Cognitive performance impact of augmented reality for network operations tasks. In Advances in Human Factors in Cybersecurity; Springer: Berlin/Heidelberg, Germany, 2016; pp. 139–151. [Google Scholar]
- Korkiakoski, M.; Sadiq, F.; Setianto, F.; Latif, U.K.; Alavesa, P.; Kostakos, P. Using smart glasses for monitoring cyber threat intelligence feeds. In Proceedings of the 2021 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining, The Hague, The Netherlands, 8–11 November 2021; pp. 630–634. [Google Scholar]
- Munsinger, B.; Beebe, N.; Richardson, T. Virtual reality for improving cyber situational awareness in security operations centers. Comput. Secur. 2023, 132, 103368. [Google Scholar] [CrossRef]
- Alnajim, A.M.; Habib, S.; Islam, M.; AlRawashdeh, H.S.; Wasim, M. Exploring cybersecurity education and training techniques: A comprehensive review of traditional, virtual reality, and augmented reality approaches. Symmetry 2023, 15, 2175. [Google Scholar] [CrossRef]
- Abu Deeb, F. Enhancing Cybersecurity with Extended Reality: A Systematic Review. J. Comput. Inf. Syst. 2024, 1–15. [Google Scholar] [CrossRef]
- Skorenkyy, Y.; Kozak, R.; Zagorodna, N.; Kramar, O.; Baran, I. Use of augmented reality-enabled prototyping of cyber-physical systems for improving cyber-security education. J. Phys. Conf. Ser. 2021, 1840, 012026. [Google Scholar] [CrossRef]
- Puttawong, N.; Visoottiviseth, V.; Haga, J. VRFiWall virtual reality edutainment for firewall security concepts. In Proceedings of the 2017 2nd International Conference on Information Technology (INCIT), Nakhonpathom, Thailand, 2–3 November 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–6. [Google Scholar]
- Dissanayake, N.; Jayatilaka, A.; Zahedi, M.; Babar, M.A. Software security patch management-A systematic literature review of challenges, approaches, tools and practices. Inf. Softw. Technol. 2022, 144, 106771. [Google Scholar] [CrossRef]
- Shahin, M.; Babar, M.A.; Zhu, L. Continuous integration, delivery and deployment: A systematic review on approaches, tools, challenges and practices. IEEE Access 2017, 5, 3909–3943. [Google Scholar] [CrossRef]
- Kitchenham, B.; Pretorius, R.; Budgen, D.; Brereton, O.P.; Turner, M.; Niazi, M.; Linkman, S. Systematic literature reviews in software engineering–a tertiary study. Inf. Softw. Technol. 2010, 52, 792–805. [Google Scholar] [CrossRef]
- Zahedi, M.; Shahin, M.; Babar, M.A. A systematic review of knowledge sharing challenges and practices in global software development. Int. J. Inf. Manag. 2016, 36, 995–1019. [Google Scholar] [CrossRef]
- Shahin, M.; Babar, M.A.; Chauhan, M.A. Architectural design space for modelling and simulation as a service: A review. J. Syst. Softw. 2020, 170, 110752. [Google Scholar] [CrossRef]
- Wohlin, C. Guidelines for snowballing in systematic literature studies and a replication in software engineering. In Proceedings of the 18th International Conference on Evaluation and Assessment in Software Engineering, London, UK, 13–14 May 2014. [Google Scholar]
- Braun, V.; Clarke, V. Using thematic analysis in psychology. Qual. Res. Psychol. 2006, 3, 77–101. [Google Scholar] [CrossRef]
- Dwyer, T.; Marriott, K.; Isenberg, T.; Klein, K.; Riche, N.; Schreiber, F.; Stuerzlinger, W.; Thomas, B.H. Immersive analytics: An introduction. In Immersive Analytics; Springer: Berlin/Heidelberg, Germany, 2018; pp. 1–23. [Google Scholar]
- Beitzel, S.; Dykstra, J.; Toliver, P.; Youzwak, J. Exploring 3d cybersecurity visualization with the microsoft hololens. In Proceedings of the International Conference on Applied Human Factors and Ergonomics, Los Angeles, CA, USA, 17–21 July 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 197–207. [Google Scholar]
- Ma, C.; Kulshrestha, S.; Shi, W.; Okada, Y.; Bose, R. E-learning material development framework supporting VR/AR based on linked data for IoT security education. In Proceedings of the International Conference on Emerging Internetworking, Data & Web Technologies, Tirana, Albania, 15–17 March 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 479–491. [Google Scholar]
- Delcombel, N.; Kabil, A.; Duval, T.; Pahl, M.O. CyberCopter: A 3D helical visualisation for periodic signals of cyber attacks. In Proceedings of the VR4Sec 2021 (Security for XR and XR for Security), Virtual, 6 August 2021. [Google Scholar]
- Kabil, A.; Duval, T.; Cuppens, N.; Le Comte, G.; Halgand, Y.; Ponchel, C. 3D cybercop: A collaborative platform for cybersecurity data analysis and training. In Proceedings of the International Conference on Cooperative Design, Visualization and Engineering, Hangzhou, China, 21–24 October 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 176–183. [Google Scholar]
- Kabil, A.; Duval, T.; Cuppens, N. Alert characterization by non-expert users in a cybersecurity virtual environment: A usability study. In Proceedings of the International Conference on Augmented Reality, Virtual Reality and Computer Graphics, Lecce, Italy, 7–10 September 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 82–101. [Google Scholar]
- Kullman, K.; Asher, N.B.; Sample, C. Operator impressions of 3D visualizations for cybersecurity analysts. In Proceedings of the 18th European Conference on Cyber Warfare and Security, ECCWS 2019: University of Coimbra, Coimbra, Portugal, 4–5 July 2019; ACPI: Reading, UK, 2019; pp. 257–266. [Google Scholar]
- Ask, T.F.; Kullman, K.; Sütterlin, S.; Knox, B.J.; Engel, D.; Lugo, R.G. A 3D mixed reality visualization of network topology and activity results in better dyadic cyber team communication and cyber situational awareness. Front. Big Data 2023, 6, 1042783. [Google Scholar] [CrossRef]
- Kullman, K.; Cowley, J.; Ben-Asher, N. Enhancing cyber defense situational awareness using 3D visualizations. In Proceedings of the 13th International Conference on Cyber Warfare and Security ICCWS 2018: National Defense University, Washington, DC, USA, 8–9 March 2018; pp. 369–378. [Google Scholar]
- Beitzel, S.; Dykstra, J.; Toliver, P.; Youzwak, J. Network anomaly analysis using the Microsoft HoloLens. Proc. Hum. Factors Ergon. Soc. Annu. Meet. 2018, 62, 2094–2098. [Google Scholar] [CrossRef]
- Alqahtani, H.; Kavakli-Thorne, M. Design and evaluation of an augmented reality game for cybersecurity awareness (cybar). Information 2020, 11, 121. [Google Scholar] [CrossRef]
- Seo, J.H.; Bruner, M.; Payne, A.; Gober, N.; McMullen, D.; Chakravorty, D.K. Using virtual reality to enforce principles of cybersecurity. J. Comput. Sci. Educ. 2019, 10, 81–87. [Google Scholar] [CrossRef] [PubMed]
- Chu, E.S.; Payne, A.; Seo, J.H.; Chakravorty, D.; McMullen, D. Data center physical security training VR to support procedural memory tasks. In Proceedings of the International Conference on Human-Computer Interaction, Orlando, FL, USA, 26–31 July 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 353–358. [Google Scholar]
- Jin, G.; Tu, M.; Kim, T.H.; Heffron, J.; White, J. Game based cybersecurity training for high school students. In Proceedings of the ACM Technical Symposium on Computer Science Education, Baltimore, MD, USA, 21–24 February 2018; pp. 68–73. [Google Scholar]
- Salazar, M.; Gaviria, J.; Laorden, C.; Bringas, P.G. Enhancing cybersecurity learning through an augmented reality-based serious game. In Proceedings of the 2013 IEEE Global Engineering Education Conference (EDUCON), Berlin, Germany, 13–15 March 2013; pp. 602–607. [Google Scholar]
- Garae, J.; Ko, R.K.; Kho, J.; Suwadi, S.; Will, M.A.; Apperley, M. Visualizing the new zealand cyber security challenge for attack behaviors. In Proceedings of the 2017 IEEE Trustcom/BigDataSE/ICESS, Sydney, NSW, Australia, 1–4 August 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1123–1130. [Google Scholar]
- Kasurinen, J. Usability issues of virtual reality learning simulator in healthcare and cybersecurity. Procedia Comput. Sci. 2017, 119, 341–349. [Google Scholar] [CrossRef]
- Sharma, A.; Palrecha, D.; Parekh, M. Security Awareness Game (Augmented Reality). In Proceedings of the International Conference on Sustainable Computing in Science, Technology and Management (SUSCOM), Amity University Rajasthan, Jaipur, India, 26–28 February 2019. [Google Scholar]
- Chiou, Y.M.; Shen, C.C.; Mouza, C.; Rutherford, T. Augmented Reality-Based Cybersecurity Education on Phishing. In Proceedings of the 2021 IEEE International Conference on Artificial Intelligence and Virtual Reality (AIVR), Taichung, Taiwan, 15–17 November 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 228–231. [Google Scholar]
- Faisal, K.; Nikitha, K.; Portia, P. Augmented Reality Mobile Forensic Laboratory (AMFL). In Proceedings of the 10th International Multi-Conference on Complexity, Informatics and Cybernetics (IMCIC 2019), Orlando, FL, USA, 12–15 March 2019. [Google Scholar]
- Rana, S.; Alhamdani, W. Exploring the Need to Study the Efficacy of VR Training Compared to Traditional Cybersecurity Training. Int. J. Comput. Inf. Eng. 2014. [Google Scholar]
- Goel, D.; Ahmad, H.; Jain, A.K.; Goel, N.K. Machine Learning Driven Smishing Detection Framework for Mobile Security. arXiv 2024, arXiv:2412.09641. [Google Scholar]
- Kabil, A.; Duval, T.; Cuppens, N.; Le Comte, G.; Halgand, Y.; Ponchel, C. Why should we use 3d collaborative virtual environments for cyber security? In Proceedings of the 2018 IEEE Fourth VR International Workshop on Collaborative Virtual Environments (3DCVE), Reutlingen, Germany, 19 March 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–2. [Google Scholar]
- Korkiakoski, M.; Antila, A.; Annamaa, J.; Sheikhi, S.; Alavesa, P.; Kostakos, P. Hack the Room: Exploring the potential of an augmented reality game for teaching cyber security. In Proceedings of the Augmented Humans International Conference 2023, Glasgow, UK, 12–14 March 2023; pp. 349–353. [Google Scholar]
- Manoharan, A.; Sriskantharajah, A.; Herath, H.; Guruge, L.; Yasakethu, S. MetaHuman based phishing attacks in the metaverse realm: Awareness for cyber security education. Educ. Inf. Technol. 2025, 1–27. [Google Scholar] [CrossRef]
- Chakal, K.; Korkiakoski, M.; Mehmood, H.; Anagnostopoulos, T.; Alavesa, P.; Kostakos, P. Augmented Reality Integration for Real-Time Security and Maintenance in IoT-Enabled Smart Campuses. In Proceedings of the 2023 IEEE 31st International Conference on Network Protocols (ICNP), Reykjavik, Iceland, 10–13 October 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–6. [Google Scholar]
- Bernsland, M.; Moshfegh, A.; Lindén, K.; Bajin, S.; Quintero, L.; Solsona Belenguer, J.; Rostami, A. Cs: No–an extended reality experience for cyber security education. In Proceedings of the 2022 ACM International Conference on Interactive Media Experiences, Aveiro, Portugal, 22–24 June 2022; pp. 287–292. [Google Scholar]
- Hunter, J.; Porter, M.; Williams, B. Towards a theoretical framework for situational awareness in paramedicine. Saf. Sci. 2020, 122, 104528. [Google Scholar] [CrossRef]
- Riley, J.M.; Endsley, M.R.; Bolstad, C.A.; Cuevas, H.M. Collaborative planning and situation awareness in Army command and control. Ergonomics 2006, 49, 1139–1153. [Google Scholar] [CrossRef]
- Onwubiko, C. Understanding Cyber Situation Awareness. Int. J. Cyber Situational Aware. 2016, 1, 11–30. [Google Scholar] [CrossRef]
- Alqahtani, H.; Kavakli-Thorne, M. Exploring factors affecting user’s cybersecurity behaviour by using mobile augmented reality app (CybAR). In Proceedings of the 2020 12th International Conference on Computer and Automation Engineering, Sydney, Australia, 14–16 February 2020; pp. 129–135. [Google Scholar]
- Shen, C.C.; Chiou, Y.M.; Mouza, C.; Rutherford, T. Work-in-progress-design and evaluation of mixed reality programs for cybersecurity education. In Proceedings of the 2021 7th International Conference of the Immersive Learning Research Network (iLRN), Eureka, CA, USA, 17 May–10 June 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–3. [Google Scholar]
- Wagner, P.; Alharthi, D. Leveraging VR/AR/MR/XR Technologies to Improve Cybersecurity Education, Training, and Operations. J. Cybersecur. Educ. Res. Pract. 2023, 2024, 7. [Google Scholar] [CrossRef]
- Kommera, N.; Kaleem, F.; Harooni, S.M.S. Smart augmented reality glasses in cybersecurity and forensic education. In Proceedings of the 2016 IEEE Conference on Intelligence and Security Informatics (ISI), Tucson, AZ, USA, 28–30 September 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 279–281. [Google Scholar]
- Chen, W.; He, Y.; Tian, X.; He, W. Exploring cybersecurity education at the K-12 level. In Proceedings of the SITE Interactive Conference, Online, 26–28 October 2021; Association for the Advancement of Computing in Education (AACE): Chesapeake, Virginia, 2021; pp. 108–114. [Google Scholar]
- Kullman, K.; Ryan, M.; Trossbach, L. VR/MR supporting the future of defensive cyber operations. IFAC-PapersOnLine 2019, 52, 181–186. [Google Scholar] [CrossRef]
- Veneruso, S.V.; Ferro, L.S.; Marrella, A.; Mecella, M.; Catarci, T. CyberVR: An interactive learning experience in virtual reality for cybersecurity related issues. In Proceedings of the International Conference on Advanced Visual Interfaces, Salerno, Italy, 28 September–October 2020; pp. 1–8. [Google Scholar]
- Kaneko, K.; Tsutsumi, Y.; Sharma, S.; Okada, Y. PACKUARIUM: Network packet visualization using mixed reality for detecting bot IoT device of DDoS attack. In Advances in Internet, Data and Web Technologies, Proceedings of the 8th International Conference on Emerging Internet, Data and Web Technologies (EIDWT-2020), Kitakyushu, Japan, 24–26 February 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 361–372. [Google Scholar]
- Homps, F.; Beugin, Y.; Vuillemot, R. ReViVD: Exploration and filtering of trajectories in an immersive environment using 3D shapes. In Proceedings of the 2020 IEEE Conference on Virtual Reality and 3D User Interfaces (VR), Atlanta, GA, USA, 22–26 March 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 729–737. [Google Scholar]
- Kraus, M.; Fuchs, J.; Sommer, B.; Klein, K.; Engelke, U.; Keim, D.; Schreiber, F. Immersive analytics with abstract 3D visualizations: A survey. Comput. Graph. Forum 2022, 41, 201–229. [Google Scholar] [CrossRef]
- Kraus, M.; Angerbauer, K.; Buchmüller, J.; Schweitzer, D.; Keim, D.A.; Sedlmair, M.; Fuchs, J. Assessing 2d and 3d heatmaps for comparative analysis: An empirical study. In Proceedings of the 2020 CHI Conference on Human Factors in Computing Systems, Honolulu, HI, USA, 25–30 April 2020; pp. 1–14. [Google Scholar]
- Benko, H.; Ishak, E.W.; Feiner, S. Collaborative mixed reality visualization of an archaeological excavation. In Proceedings of the Third IEEE and ACM International Symposium on Mixed and Augmented Reality, Arlington, VA, USA, 2–5 November 2004; IEEE: Piscataway, NJ, USA, 2004; pp. 132–140. [Google Scholar]
- Fonnet, A.; Prie, Y. Survey of immersive analytics. IEEE Trans. Vis. Comput. Graph. 2019, 27, 2101–2122. [Google Scholar] [CrossRef] [PubMed]
- Alismail, A.; Altulaihan, E.; Rahman, M.H.; Sufian, A. A systematic literature review on cybersecurity threats of virtual reality (vr) and augmented reality (ar). In Data Intelligence and Cognitive Informatics: Proceedings of ICDICI 2022, Tirunelveli, Tamil Nadu, 6–7 July 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 761–774. [Google Scholar]
- Cantelli-Forti, A.; Capria, A.; Saverino, A.L.; Berizzi, F.; Adami, D.; Callegari, C. Critical infrastructure protection system design based on SCOUT multitech seCurity system for intercOnnected space control groUnd staTions. Int. J. Crit. Infrastruct. Prot. 2021, 32, 100407. [Google Scholar] [CrossRef]

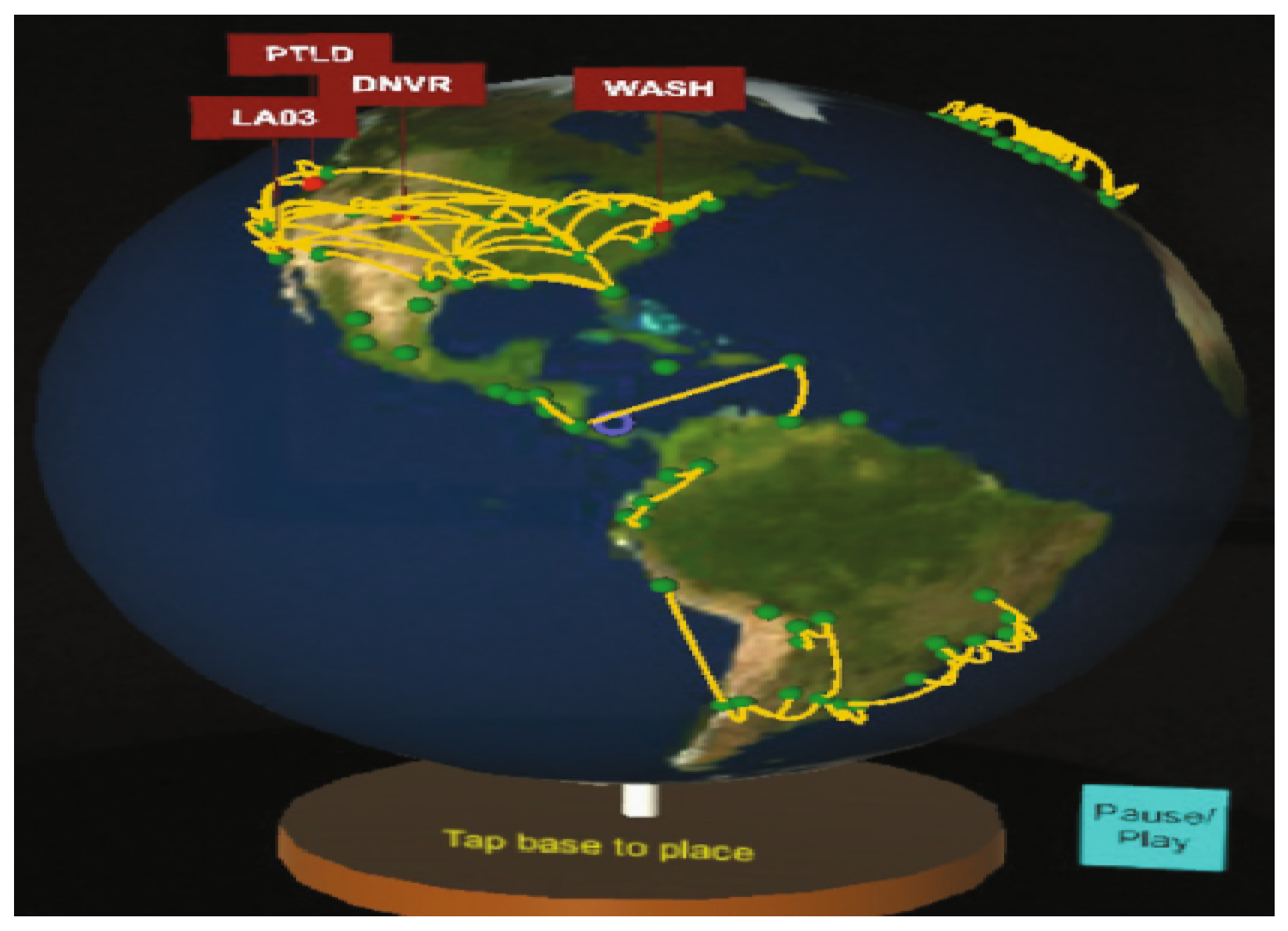
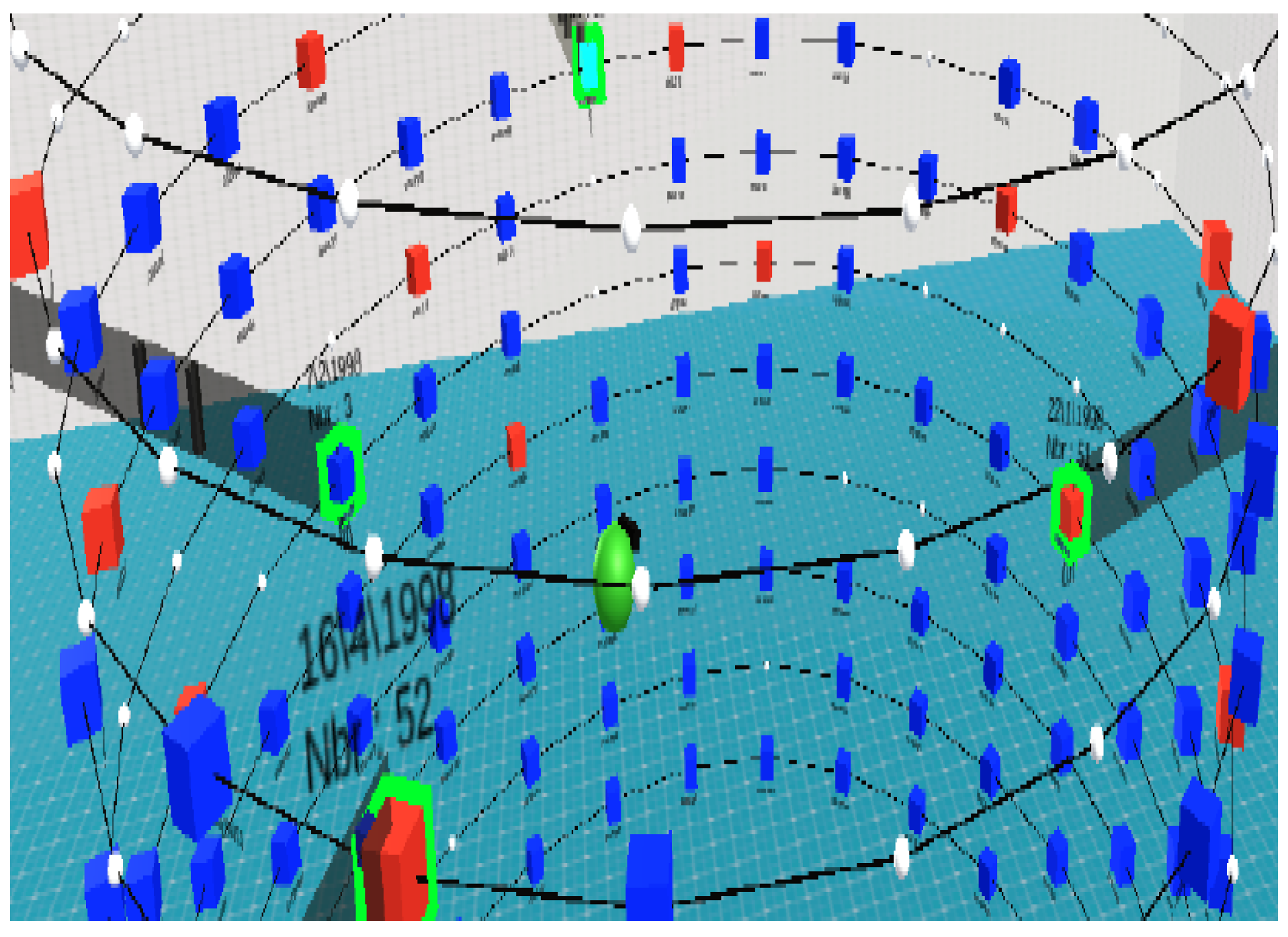
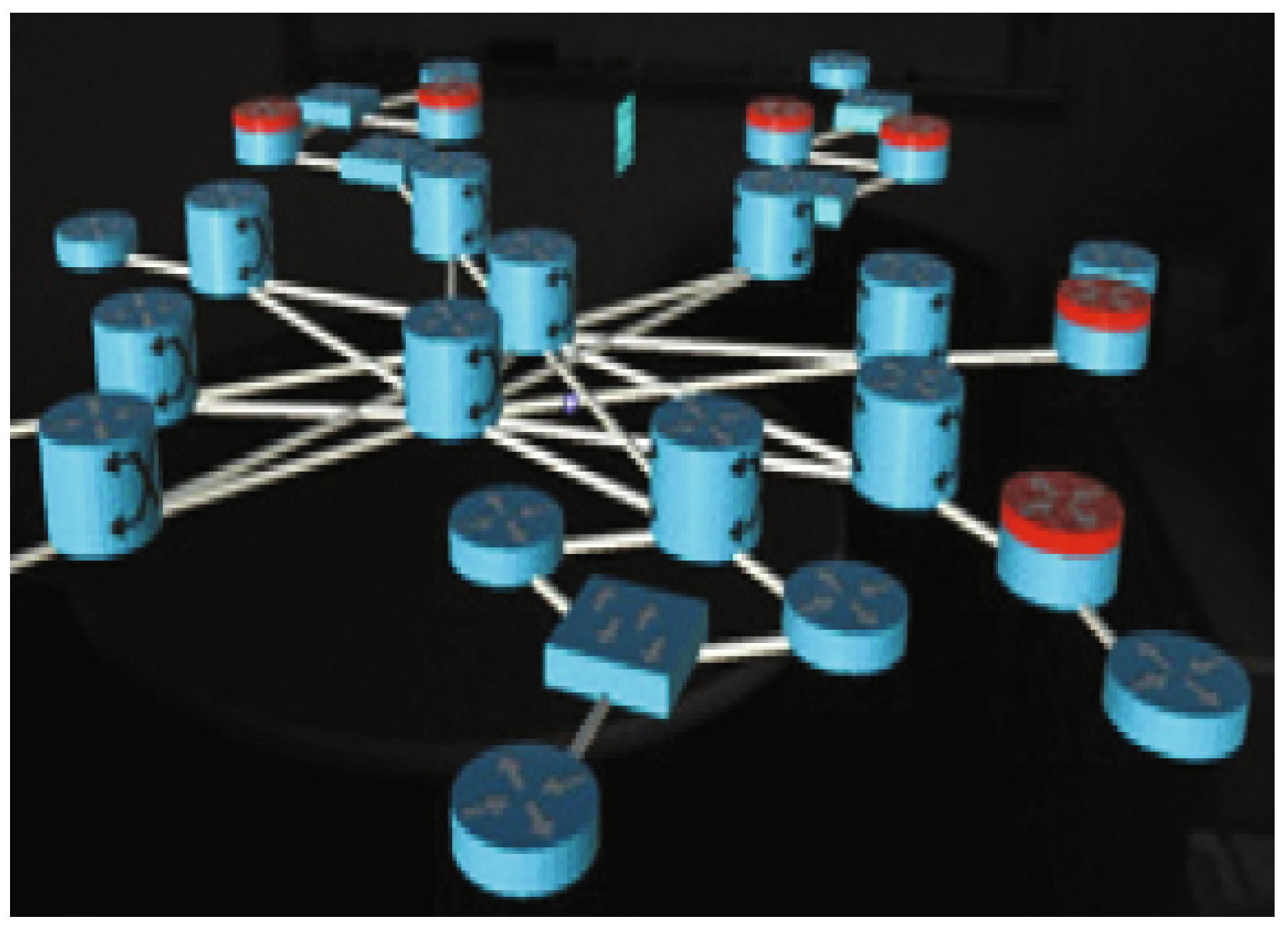
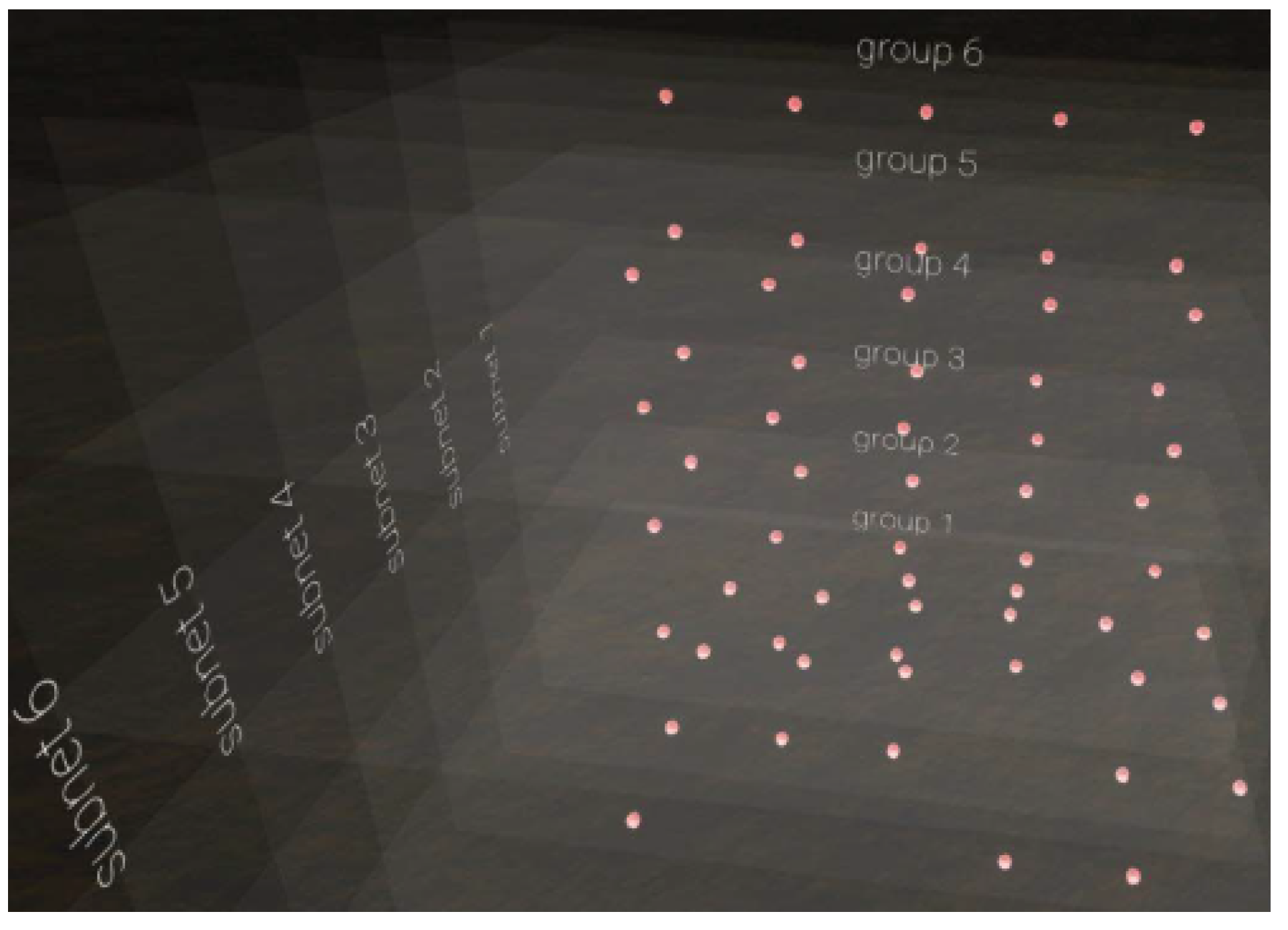




| Research Question | Motivation |
|---|---|
| RQ1:What are the visualization and interaction techniques used by ICSA systems? | To identify visualization techniques and interaction features used by immersive technologies for cyber situational awareness. |
| RQ2: What level of cyber situational awareness is facilitated by immersive technologies in ICSA systems? | To identify perception, comprehension, and projection of cyber situational awareness in ICSA systems. |
| RQ3: How are ICSA systems evaluated? | To identify evaluation techniques for validating ICSA systems. |
| Inclusion Criteria |
|---|
| I1: A study that is related to the use of immersive technologies for cybersecurity purposes |
| I2: A study is selected irrespective of its publication date |
| Exclusion Criteria |
| E1: A study that is written in a language other than English |
| E2: Books, workshop articles and non-peer-reviewed papers |
| E3: Full text is not accessible |
| ID | Data Item | Description | Research Questions |
|---|---|---|---|
| D1 | Title | The title of the paper | Demographic data |
| D2 | Author(s) | The author(s) of the paper | Demographic data |
| D3 | Venue | The publication venue | Demographic data |
| D4 | Year | The year of the publication | Demographic data |
| D5 | Publication type | The type of publication (e.g., journal paper, conference paper) | Demographic data |
| D6 | Area of focus | The focus of the paper in ICSA domain | Demographic data |
| D7 | Target user(s) | The intended user(s) (e.g., security analyst) | Demographic data |
| D8 | Software and hardware tools | The software/hardware tools used for ICSA systems | Demographic data |
| D9 | Visualization techniques | The visualization techniques for ICSA systems | RQ1 |
| D10 | Interaction techniques | The interaction techniques for ICSA systems | RQ1 |
| D11 | Cyber situational awareness level | The level of cyber situational awareness achieved for ICSA systems | RQ2 |
| D12 | Evaluation mechanisms | The evaluation mechanisms used to validate ICSA systems | RQ3 |
| D13 | Future work | The reported future work | Discussion |
| Visualization Techniques | Papers |
|---|---|
| Geographical Displays | [11,12,29,30] |
| Metaphorical Displays | [31] |
| Node-Link Graphs | [29,32,33,34,35] |
| Scatterplots | [36] |
| Three-Dimensional Bar Charts | [37] |
| Volume | [11,14,15,20,29,31,32,33,38,39,40,41,42,43,44,45] |
| Icons/Symbols/Glyphs | [12,29,41,42,45,46,47] |
| Animation/Video Displays | [11,46,47] |
| Pictures | [45,48] |
| Two-Dimensional Displays | [14,15,29,32,33,38,39,40,47] |
| List/Table/Text Displays | [11,12,31,33,38,39,40,45,46,47] |
| Interaction Techniques | Papers |
|---|---|
| Select | [11,12,20,29,30,31,32,33,36,37,38,39,40,42,45,46,47,50,51,52] |
| Navigate | [11,20,29,30,31,32,33,38,39,40,46,47,50] |
| Details on Demand | [11,12,20,29,30,31,32,33,37,38,39,40,45,46,47,53,54] |
| Arrange/Change | [29,30,31,32,33,36,37,39,40,46] |
| Filter | [29,31,32] |
| Extract/Share | [32,50] |
| Aggregate/Relate | [31,32,36,37] |
| Annotate | [31,32] |
| Record | [33] |
| Levels of ICSA | Papers |
|---|---|
| Perception | [11,12,14,15,20,30,31,32,33,36,37,39,40,41,42,43,44,45,46,47,51,53,58,59,60,61,62] |
| Comprehension | [29,31,32,33,34,37,38,46,54,63,64,65] |
| Projection | [11,35,38,46] |
| Paper | Evaluation Mechanism | Users’ Demographics | Performance Metrics | Cognition Metrics | Results |
|---|---|---|---|---|---|
| Mattina et al. [12] | Questionnaire | User time-on-task; User fact recall | Users’ performance is improved | ||
| Korkiakoski et al. [15] | SART Questionnaire; Analysis of variance with p-value Test | 6 participants; 3 males and 3 females | No. of completed tasks | Understanding of situational awareness depends on gender | |
| Alqahtani et al. [38] | Questionnaire with five-point Likert scale | 91 participants; 59% male and 41% female; Age between 18 and 65 | AR-based game increases cyber situational awareness | ||
| Beitzel et al. [14] | Capture the flag exercise; Post-task survey; NASA TLX Assessment | 7 participants; 7 male; Age is between 34 and 60; Ethnicity: Caucasian | Total elapsed time; Average response time; Countermeasure failure rate; Success EOIs; Failed EOIs | Mental demand; Physical demand; Temporal demand; Frustration | AR improves both performance and cognition of users |
| Seo et al. [39] | Questionnaire | 25 participants | Memory test | Interactive immersion in VR is beneficial for long-term memorization of cyber situational awareness | |
| Chu et al. [40] | Questionnaire; Interview | 6 participants with no cybersecurity knowledge | Memory test | Cyber situational awareness training through VR is more engaging than video training. | |
| Jin et al. [41] | Questionnaire with 5-point Likert scale; Analysis of variance with p-value Test | 181 participants; 123 male and 58 female | Immersive game-based learning for cyber situational awareness is more effective for males than females | ||
| Kabil et al. [33] | SUS usability questionnaire; Analysis of variance with p-value Test; Cybersickness questionnaire | 30 participants with no cybersecurity knowledge | Physiological disorder | Users had good performance with no discomfort | |
| Salazar et al. [42] | Questionnaire with 5-point Likert scale | 208 participants; Age between 14 and 19 | Knowledge acquisition; Vulnerability detection; Defense preparation | Confidence in technology | AR-based games improve both performance and cognition |
| Rana et al. [48] | Post-task quiz and survey with statistical analysis (t-test) | 100 participants with cybersecurity knowledge | VR cybersecurity training is more effective than video-based methods | ||
| Delcombel et al. [31] | SUS usability questionnaire | 8 participants; 3 male and 5 female; Age: 23 to 30 | Task completion time; Task accuracy | Users’ task performance is enhanced in immersive environments | |
| Kaleem et al. [47] | Pre- and post-task survey with 5-point Likert scale and statistical analysis | 20 participants | AR has a positive impact on cybersecurity learning | ||
| Kasurinen et al. [44] | Pre- and post-task survey | task completion time; No. of unforced errors | VR learning environments is beneficial for understanding cyber situational awareness | ||
| Puttawong et al. [20] | Pre- and post-task survey | Participants have cybersecurity knowledge | VR environments are productive for cybersecurity education | ||
| Kommera et al. [61] | Pre- and post-task survey; Satisfaction survey | AR provides insights in cybersecurity forensic education |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ahmad, H.; Ullah, F.; Jafri, R. A Survey on Immersive Cyber Situational Awareness Systems. J. Cybersecur. Priv. 2025, 5, 33. https://doi.org/10.3390/jcp5020033
Ahmad H, Ullah F, Jafri R. A Survey on Immersive Cyber Situational Awareness Systems. Journal of Cybersecurity and Privacy. 2025; 5(2):33. https://doi.org/10.3390/jcp5020033
Chicago/Turabian StyleAhmad, Hussain, Faheem Ullah, and Rehan Jafri. 2025. "A Survey on Immersive Cyber Situational Awareness Systems" Journal of Cybersecurity and Privacy 5, no. 2: 33. https://doi.org/10.3390/jcp5020033
APA StyleAhmad, H., Ullah, F., & Jafri, R. (2025). A Survey on Immersive Cyber Situational Awareness Systems. Journal of Cybersecurity and Privacy, 5(2), 33. https://doi.org/10.3390/jcp5020033





