A Secure and Scalable Authentication and Communication Protocol for Smart Grids
Abstract
1. Introduction
- Development of a secure and lightweight cryptographic protocol that addresses the evolving needs of smart grid infrastructure while ensuring strong protection against potential security threats, thereby maintaining the integrity and reliability of smart grids.
- Efficient implementation of the proposed protocol across diverse platforms to ensure a thorough evaluation of its performance for different smart grid nodes with varying computation capabilities.
- Experimental evaluation of performance, scalability, and security of the proposed protocol under real-world conditions. Our evaluation includes testing across both high-performance and resource-constrained devices and assessing resilience against cyber threats to ensure the robustness and reliability of the protocol for effective deployment in smart grid systems.
2. Background
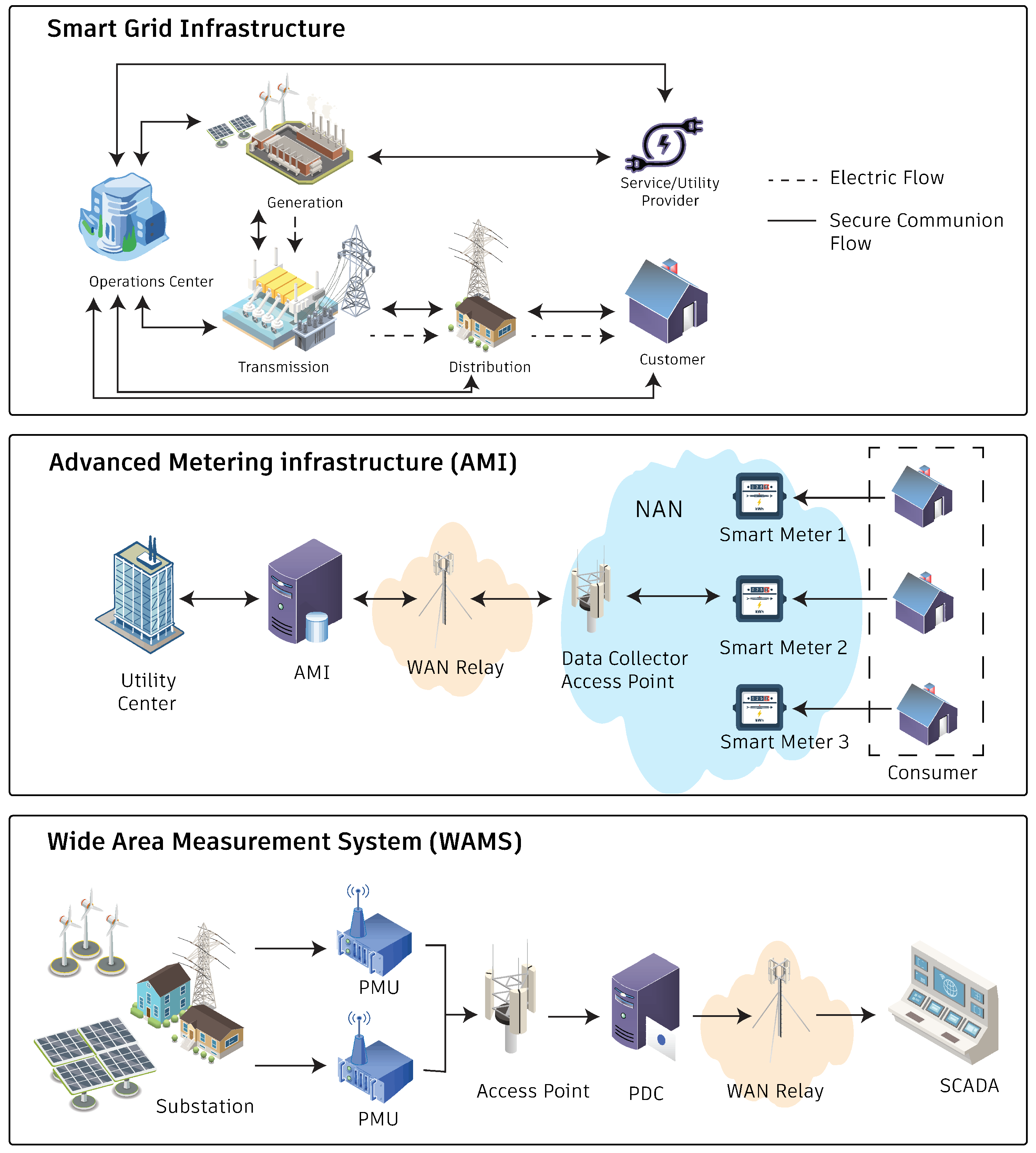
2.1. Vulnerabilities of Smart Grid Infrastracture
2.2. Related Work
3. Methodology
3.1. System Architecture
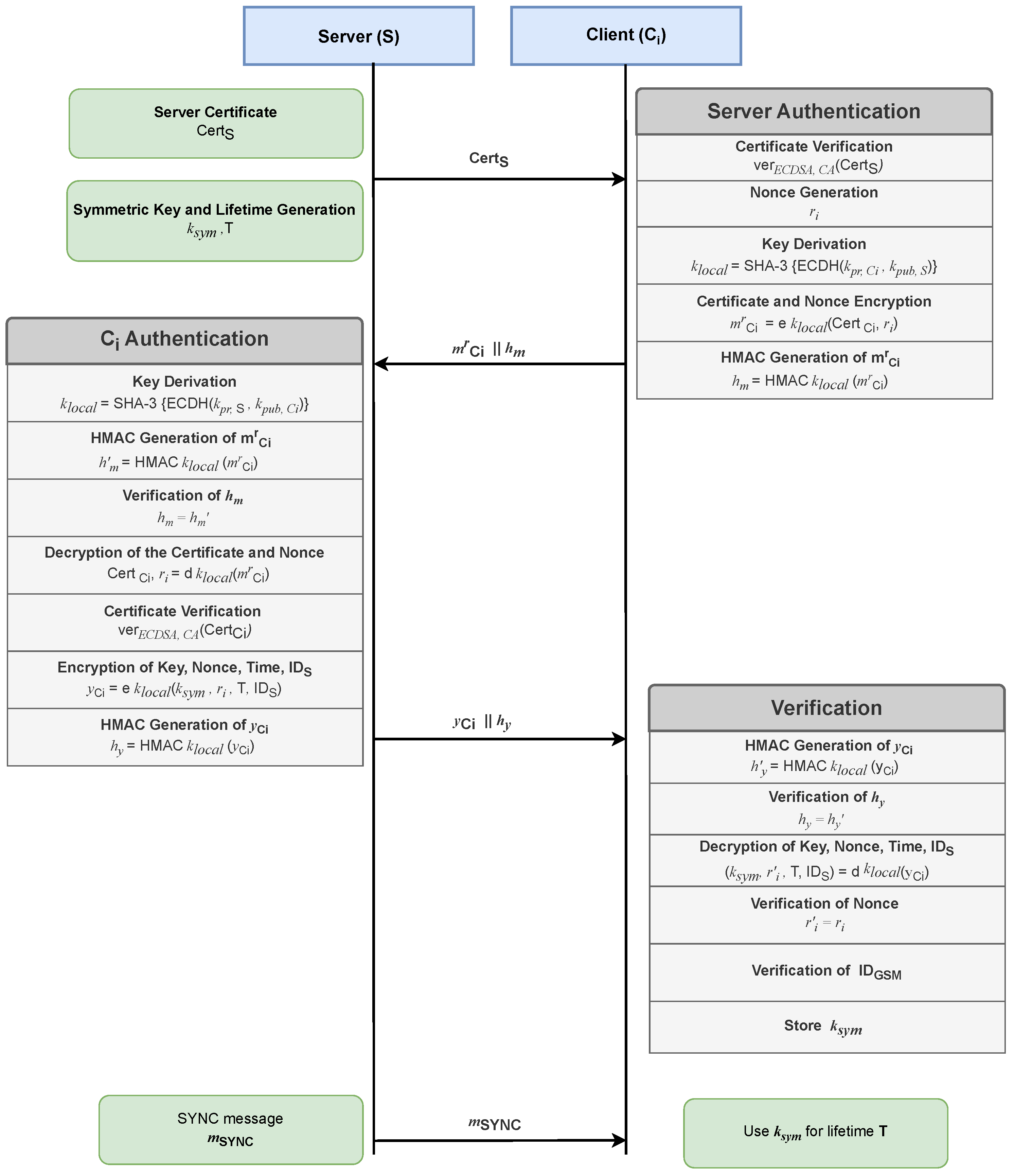
3.2. Proposed Protocol Design
3.2.1. Certificate Authority (CA) Initialization
3.2.2. Server Authentication
3.2.3. Client Authentication
3.2.4. Symmetric Key Establishment
3.2.5. Secure Communication
3.2.6. Security Analysis
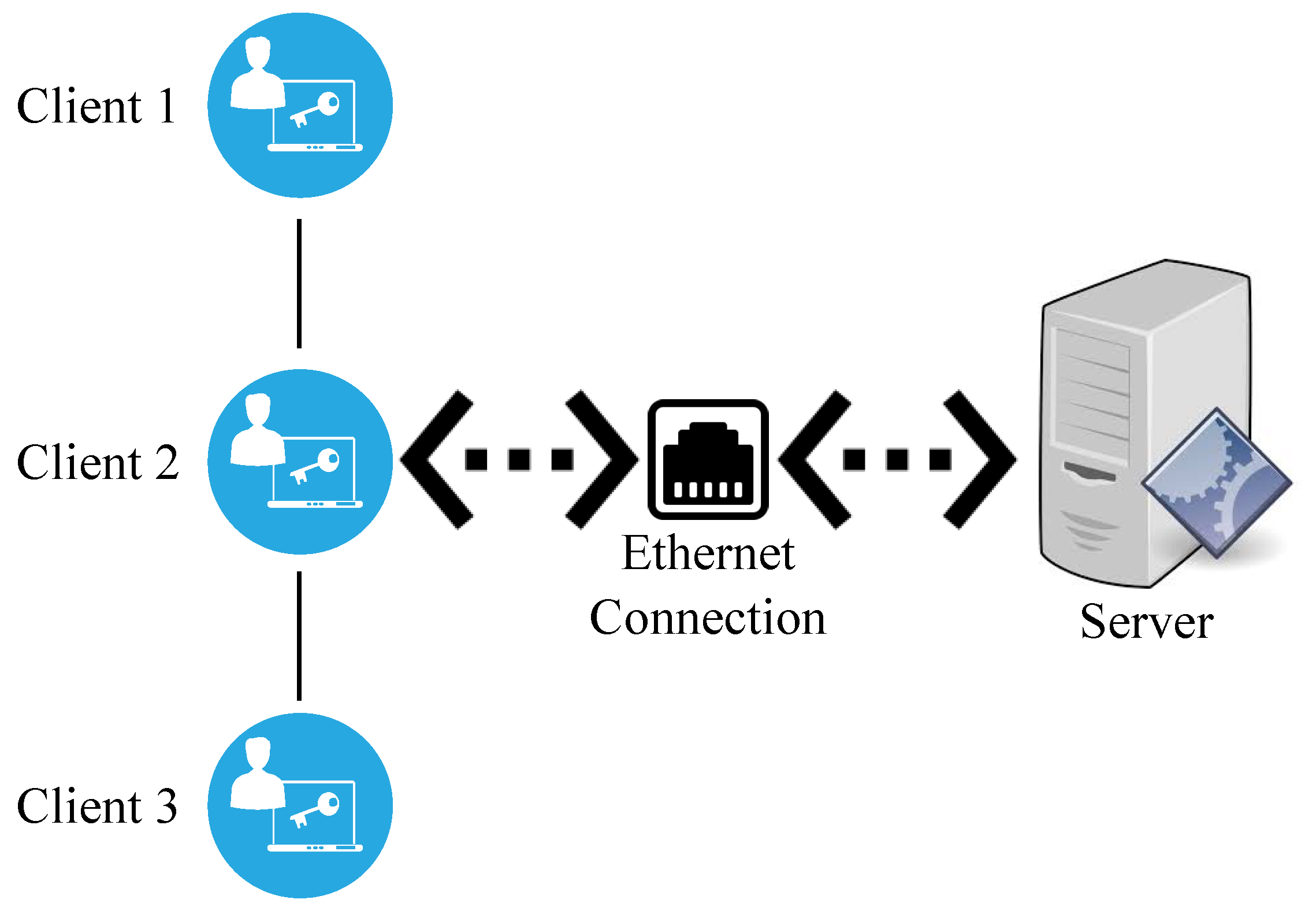
4. Experimental Setup
4.1. Hardware Configuration
4.2. Software Configuration
- /authenticate: handles client authentication using ECDSA.
- /exchange-ecc: establishes a shared secret using ECC-based ECDH.
- /send-message: facilitates secure message exchange using AES-256-CBC encryption.
4.3. Experimental Scenarios
- Secure Authentication and Communication: Legitimate clients authenticated with the server performed ECDH-based key exchange and securely exchanged encrypted messages using AES. The decrypted message was verified on the server side to ensure successful decryption.
- Authentication Failure: Malicious clients attempting to access the server were denied after failed authentication attempts. Such events were logged for further investigation.
- Network Delays: Manual delays were introduced to assess the protocol’s robustness under varying communication delays.
4.4. Evaluation Metrics
- Time analysis: The time taken for each protocol step was recorded to assess the system’s responsiveness, including authentication, key exchange, and message exchange.
- Throughput: The server’s capability to manage multiple clients was assessed by systematically increasing the number of connected clients to 10, 50, and 100.
- Power analysis: The power consumption of the protocol quantification during its execution.
- Cryptographic Overhead: The time taken to perform ECDH key exchange and AES encryption/decryption operations was measured.
4.5. Key Generation and Security Measures
5. Results
5.1. Performance Analysis
5.1.1. Time Analysis Based on Each Cryptographic Operation
5.1.2. Time Analysis Based on Steps Involved in Protocol
5.1.3. Throughput Analysis
5.1.4. Resource Utilization and Energy Efficiency
- Memory Usage: Peak memory utilization remained below 6 MB for both the client and server, even under high load conditions. The memory usage results indicate modest overhead for devices operating with limited resources/memory.
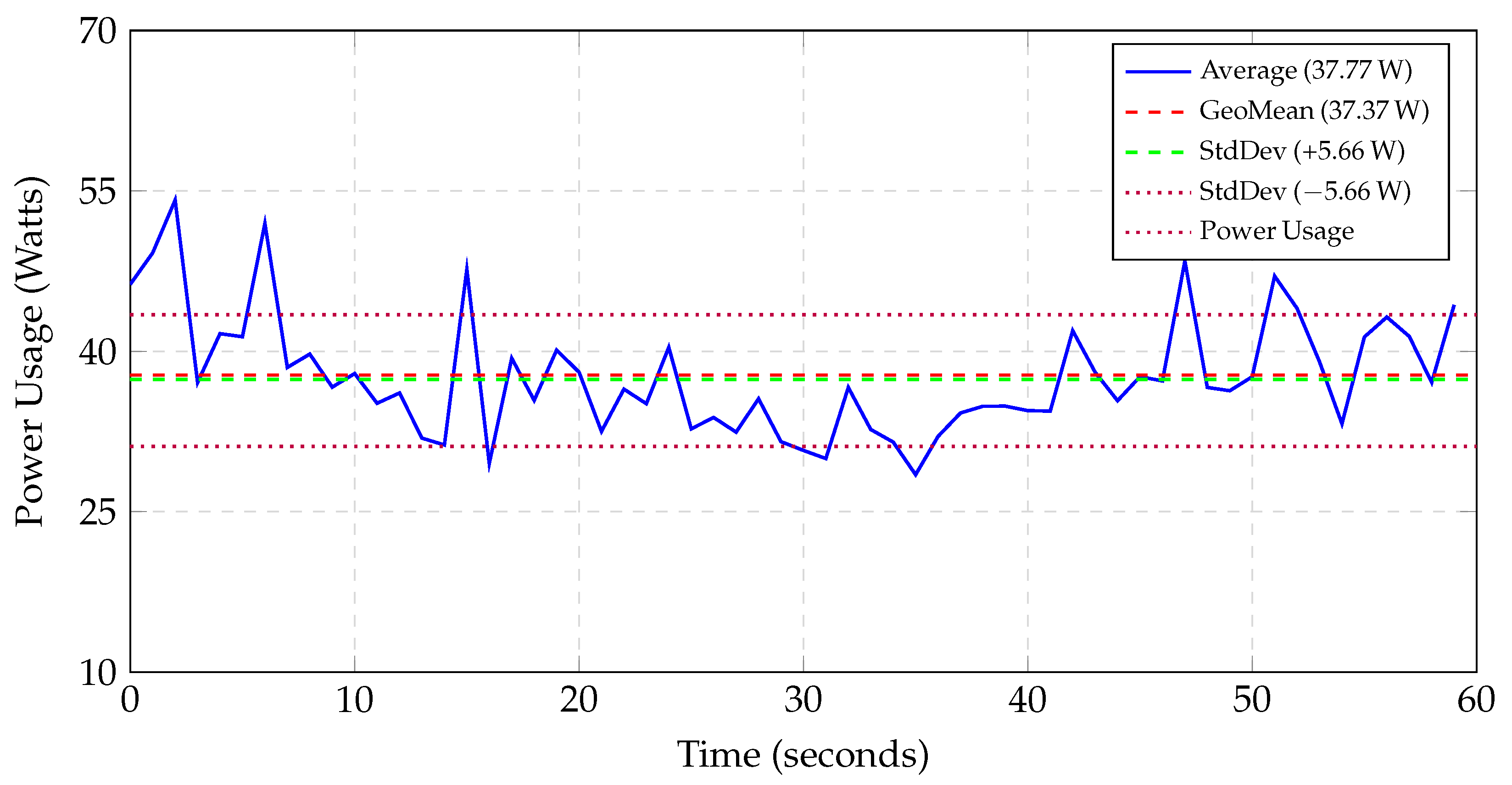
- Power Consumption: Figure 5 presents the power consumption metrics observed during the execution of the protocol. The power consumption data were collected using the powerstat tool, which captured readings at one second intervals over a total duration of 60 s. These readings were sourced from RAPL (Running Average Power Limit), an Intel processor feature that allows real-time measurements of CPU and RAM. To enhance accuracy, we collected power readings at a frequency of 10 samples per second, computing the average of these 10 readings for each second over a total duration of 60 s. This averaging approach smooths out transient fluctuations and provides a more reliable representation of the protocol’s power consumption. While short-term variations were observed, the overall trend remained stable. During the execution of the proposed protocol, the system exhibited an average power consumption of 37.77 watts, accompanied by a geometric mean of 37.37 watts and a standard deviation of 5.66 watts. The maximum recorded power consumption was 54.14 watts, while the minimum was 28.46 watts. The close alignment between the arithmetic average and the geometric mean indicates a stable power consumption pattern with minimal skewness. Furthermore, the moderate standard deviation reinforces this observation, suggesting that the power demands of the protocol remain consistent throughout the cryptographic operations executed. These findings underscore the protocol’s efficiency and its appropriateness for energy-constrained environments, where predictable and moderate power usage is crucial.
- Power Efficiency: An assessment based on average power consumption and throughput data reveals that the protocol achieves a commendable balance between performance and power usage. For instance, with a throughput of 594 requests per second, the estimated energy cost per request is approximately 0.063 watts/second, showcasing its energy efficiency.
5.1.5. Security Metrics and Failure Recovery
5.2. Comparison with State-of-the-Art Methods
5.3. Discussion on Smart Grid Security Standards and Real-World Applicability
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Nafi, N.S.; Ahmed, K.; Gregory, M.A.; Datta, M. A survey of smart grid architectures, applications, benefits and standardization. J. Netw. Comput. Appl. 2016, 76, 23–36. [Google Scholar] [CrossRef]
- Babayomi, O.; Zhang, Z.; Dragicevic, T.; Hu, J.; Rodriguez, J. Smart grid evolution: Predictive control of distributed energy resources—A review. Int. J. Electr. Power Energy Syst. 2023, 147, 108812. [Google Scholar]
- Mohassel, R.R.; Fung, A.S.; Mohammadi, F.; Raahemifar, K. A survey on advanced metering infrastructure and its application in smart grids. In Proceedings of the 2014 IEEE 27th Canadian Conference on Electrical and Computer Engineering (CCECE), Toronto, ON, Canada, 4–7 May 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 1–8. [Google Scholar]
- Sayed, K.; Gabbar, H.A. SCADA and smart energy grid control automation. In Smart Energy Grid Engineering; Elsevier: Amsterdam, The Netherlands, 2017; pp. 481–514. [Google Scholar]
- Amiri, S.S.; Rahmani, M.; McDonald, J.D. An updated review on distribution management systems within a smart grid structure. In Proceedings of the 2021 11th Smart Grid Conference (SGC), Tabriz, Iran, 7–9 December 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–5. [Google Scholar]
- Bagherzadeh, L.; Shahinzadeh, H.; Shayeghi, H.; Dejamkhooy, A.; Bayindir, R.; Iranpour, M. Integration of cloud computing and IoT (CloudIoT) in smart grids: Benefits, challenges, and solutions. In Proceedings of the 2020 International Conference on Computational Intelligence for Smart Power System and Sustainable Energy (CISPSSE), Keonjhar, India, 29–31 July 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–8. [Google Scholar]
- Faquir, D.; Chouliaras, N.; Sofia, V.; Olga, K.; Maglaras, L. Cybersecurity in smart grids, challenges and solutions. AIMS Electron. Electr. Eng. 2021, 5, 24–37. [Google Scholar]
- Leszczyna, R. A review of standards with cybersecurity requirements for smart grid. Comput. Secur. 2018, 77, 262–276. [Google Scholar] [CrossRef]
- Admass, W.S.; Munaye, Y.Y.; Diro, A.A. Cyber security: State of the art, challenges and future directions. Cyber Secur. Appl. 2024, 2, 100031. [Google Scholar]
- Martin, K.; Brunello, G.; Adamiak, M.; Antonova, G.; Begovic, M.; Benmouyal, G.; Bui, P.; Falk, H.; Gharpure, V.; Goldstein, A.; et al. An overview of the IEEE standard C37. 118.2—synchrophasor data transfer for power systems. IEEE Trans. Smart Grid 2014, 5, 1980–1984. [Google Scholar]
- Khan, R.; McLaughlin, K.; Laverty, D.; Sezer, S. Analysis of IEEE C37. 118 and IEC 61850-90-5 synchrophasor communication frameworks. In Proceedings of the 2016 IEEE Power and Energy Society General Meeting (PESGM), Boston, MA, USA, 17–21 July 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–5. [Google Scholar]
- Burgos, D.L. DoS Threat to Smart Grids: Review, Analysis, and Challenges. 2024. Available online: https://ntnuopen.ntnu.no/ntnu-xmlui/handle/11250/3154983#:~:text=The%20cumulative%20effect%20of%20DoS,for%20maintaining%20uninterrupted%20service%20in%publisher:{NTNU} (accessed on 20 December 2024).
- Amara, M.; Siad, A. Elliptic curve cryptography and its applications. In Proceedings of the International Workshop on Systems, Signal Processing and Their Applications, WOSSPA, Tipaza, Algeria, 9–11 May 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 247–250. [Google Scholar]
- Haakegaard, R.; Lang, J. The Elliptic Curve Diffie-Hellman (ecdh). 2015. Available online: https:////koclab.cs.ucsb.edu/teaching/ecc/project/2015Projects/Haakegaard+Lang.pdf (accessed on 20 December 2024).
- Abdullah, A.M. Advanced encryption standard (AES) algorithm to encrypt and decrypt data. Cryptogr. Netw. Secur. 2017, 16, 11. [Google Scholar]
- Joseph, A.; Balachandra, P. Smart Grid to Energy Internet: A Systematic Review of Transitioning Electricity Systems. IEEE Access 2020, 8, 215787–215805. [Google Scholar] [CrossRef]
- Saidani Neffati, O.; Sengan, S.; Thangavelu, K.D.; Dilip Kumar, S.; Setiawan, R.; Elangovan, M.; Mani, D.; Velayutham, P. Migrating from traditional grid to smart grid in smart cities promoted in developing country. Sustain. Energy Technol. Assess. 2021, 45, 101125. [Google Scholar] [CrossRef]
- Kakran, S.; Chanana, S. Smart operations of smart grids integrated with distributed generation: A review. Renew. Sustain. Energy Rev. 2018, 81, 524–535. [Google Scholar] [CrossRef]
- Yang, Q.; An, D.; Min, R.; Yu, W.; Yang, X.; Zhao, W. On Optimal PMU Placement-Based Defense Against Data Integrity Attacks in Smart Grid. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1735–1750. [Google Scholar] [CrossRef]
- Blair, S.M.; Syed, M.H.; Roscoe, A.J.; Burt, G.M.; Braun, J.P. Measurement and Analysis of PMU Reporting Latency for Smart Grid Protection and Control Applications. IEEE Access 2019, 7, 48689–48698. [Google Scholar] [CrossRef]
- Swain, K.P.; Tiwari, A.; Sharma, A.; Chakrabarti, S.; Karkare, A. Comprehensive Demonstration of Man-in-the-Middle Attack in PDC and PMU Network. In Proceedings of the 2022 22nd National Power Systems Conference (NPSC), New Delhi, India, 17–19 December 2022; pp. 213–217. [Google Scholar] [CrossRef]
- Zhang, K.; Hu, Z.; Zhan, Y.; Wang, X.; Guo, K. A Smart Grid AMI Intrusion Detection Strategy Based on Extreme Learning Machine. Energies 2020, 13, 4907. [Google Scholar] [CrossRef]
- Abir, S.M.A.A.; Anwar, A.; Choi, J.; Kayes, A.S.M. IoT-Enabled Smart Energy Grid: Applications and Challenges. IEEE Access 2021, 9, 50961–50981. [Google Scholar] [CrossRef]
- Alaklabi, A.; Munir, A.; Asfand Hafeez, M.; Khan Khattak, M.A. Z-Crypt: Chirp Z-Transform-Based Image Encryption Leveraging Chaotic Logistic Maps and Substitution Permutation Network. IEEE Access 2024, 12, 123401–123422. [Google Scholar] [CrossRef]
- Wu, Y.; Guo, H.; Han, Y.; Li, S.; Liu, J. A Security-Enhanced Authentication and Key Agreement Protocol in Smart Grid. IEEE Trans. Ind. Inform. 2024, 20, 11449–11457. [Google Scholar] [CrossRef]
- Hasan, M.K.; Habib, A.A.; Shukur, Z.; Ibrahim, F.; Islam, S.; Razzaque, M.A. Review on cyber-physical and cyber-security system in smart grid: Standards, protocols, constraints, and recommendations. J. Netw. Comput. Appl. 2023, 209, 103540. [Google Scholar] [CrossRef]
- Liu, M.; Teng, F.; Zhang, Z.; Ge, P.; Sun, M.; Deng, R.; Cheng, P.; Chen, J. Enhancing Cyber-Resiliency of DER-Based Smart Grid: A Survey. IEEE Trans. Smart Grid 2024, 15, 4998–5030. [Google Scholar] [CrossRef]
- Acharya, S.; Dvorkin, Y.; Pandžić, H.; Karri, R. Cybersecurity of Smart Electric Vehicle Charging: A Power Grid Perspective. IEEE Access 2020, 8, 214434–214453. [Google Scholar] [CrossRef]
- Potvin, M.; Eng, P. The AURORA vulnerability: The sword of Damocles over the heads of rotating machines. In Proceedings of the CIGRE Canada Conference, Le Westin Montréal, QC, Canada, 16–19 September 2019. [Google Scholar]
- Bakić, B.; Milić, M.; Antović, I.; Savić, D.; Stojanović, T. 10 years since Stuxnet: What have we learned from this mysterious computer software worm? In Proceedings of the 2021 25th International Conference on Information Technology (IT), Zabljak, Montenegro, 16–20 February 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–4. [Google Scholar]
- Symantec, O. Dragonfly: Western Energy Sector Targeted by Sophisticated Attack Group. 2017. Available online: https://www.security.com/threat-intelligence/dragonfly-energy-sector-cyber-attacks (accessed on 20 December 2024).
- Case, D.U. Analysis of the Cyber Attack on the Ukrainian Power Grid; Electricity Information Sharing and Analysis Center (E-ISAC): Washington, DC, USA, 2016; Volume 388, p. 3. [Google Scholar]
- Pape, T. Insomnolence: The Sociability of Sleep at Agora Hydro-Québec. 2024. Available online: https://necsus-ejms.org/insomnolence-the-sociability-of-sleep-at-agora-hydro-quebec/ (accessed on 21 December 2024).
- Milanov, E. The RSA Algorithm; RSA Laboratories: Hebron CT, USA, 2009; pp. 1–11. [Google Scholar]
- Maurer, U.M.; Wolf, S. The diffie–hellman protocol. Des. Codes Cryptogr. 2000, 19, 147–171. [Google Scholar] [CrossRef]
- Fouda, M.M.; Fadlullah, Z.M.; Kato, N.; Lu, R.; Shen, X.S. A lightweight message authentication scheme for smart grid communications. IEEE Trans. Smart Grid 2011, 2, 675–685. [Google Scholar]
- Nicanfar, H.; Leung, V.C. Multilayer consensus ECC-based password authenticated key-exchange (MCEPAK) protocol for smart grid system. IEEE Trans. Smart Grid 2013, 4, 253–264. [Google Scholar] [CrossRef]
- Tanveer, M.; Kumar, N.; Naushad, A.; Chaudhry, S.A. A robust access control protocol for the smart grid systems. IEEE Internet Things J. 2021, 9, 6855–6865. [Google Scholar]
- Hu, S.; Chen, Y.; Zheng, Y.; Xing, B.; Li, Y.; Zhang, L.; Chen, L. Provably secure ECC-based authentication and key agreement scheme for advanced metering infrastructure in the smart grid. IEEE Trans. Ind. Inform. 2022, 19, 5985–5994. [Google Scholar] [CrossRef]
- Chai, S.; Yin, H.; Xing, B.; Li, Z.; Guo, Y.; Zhang, D.; Zhang, X.; He, D.; Zhang, J.; Yu, X.; et al. Provably secure and lightweight authentication key agreement scheme for smart meters. IEEE Trans. Smart Grid 2023, 14, 3816–3827. [Google Scholar]
- Al-Riyami, S.S.; Paterson, K.G. Certificateless Public Key Cryptography, Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security; Springer: Berlin/Heidelberg, Germany, 2003; pp. 452–473. [Google Scholar]
- Liu, S.; Liu, Y.; Liu, W.; Zhang, Y. A certificateless multi-dimensional data aggregation scheme for smart grid. J. Syst. Archit. 2023, 140, 102890. [Google Scholar] [CrossRef]
- Wang, W.; Xu, H.; Alazab, M.; Gadekallu, T.R.; Han, Z.; Su, C. Blockchain-based reliable and efficient certificateless signature for IIoT devices. IEEE Trans. Ind. Inform. 2021, 18, 7059–7067. [Google Scholar]
- Munir, A.; Gordon-Ross, A.; Lysecky, S.; Lysecky, R. A lightweight dynamic optimization methodology and application metrics estimation model for wireless sensor networks. Sustain. Comput. Inform. Syst. 2013, 3, 94–108. [Google Scholar]
- Garg, S.; Kaur, K.; Kaddoum, G.; Rodrigues, J.J.; Guizani, M. Secure and lightweight authentication scheme for smart metering infrastructure in smart grid. IEEE Trans. Ind. Inform. 2019, 16, 3548–3557. [Google Scholar] [CrossRef]
- Bergman Martinkauppi, L.; He, Q. Performance Evaluation and Comparison of Standard Cryptographic Algorithms and Chinese Cryptographic Algorithms. Master’s Thesis, Blekinge Institute of Technology, Karlskrona, Sweden, 2019. [Google Scholar]

| Reference | Cryptographic Approach | Key Features/Advantages | Limitations |
|---|---|---|---|
| Fouda et al. [36] | Authentication and key agreement (AKA) protocol | Early establishment of secure communication channels | Lacks anonymity and scalability. |
| Nicanfar et al. [37] | ECC-based, X.1035 standard and Diffie–Hellmanbased protocol | Provides basic authentication and key agreement | Does not ensure user anonymity and untraceability. |
| Tanveer et al. [38] | Authenticated encryption with associative data (AEAD) primitives used as accesscontrol protocol | Efficient protocol design | Limited anonymity and vulnerability to certain attacks. |
| Hu et al. [39] | ECC-based authentication and key agreement (AKA) protocol | Enables secure registration over open channels; flexible design | Relies on a fully trusted registration center. |
| Chai et al. [40] | SM2-based authentication and key exchange | Provides user anonymity;exhibits low computational overhead | Requires secure channels during the registration phase. |
| Al-Riyami & Paterson [41] | Certificateless publickey cryptography | Eliminates the need for traditional certificates; efficientkey management | Scalability issues; dependency on centralized keygeneration centers. |
| Liu et al. [42] | Certificateless aggregation with Paillier encryption | Enables secure data aggregation; reduces computational overhead for smart meters | Potential collision risks and implementation challenges. |
| Wang et al. [43] | Certificateless with blockchain | Offers decentralization and enhanced transparency | Significant computational overhead; less practical for resource-constrained devices. |
| Protocol Steps | Server | Client | |
|---|---|---|---|
| Core-i7 | ESP-8266 | ||
| Time (ms) | |||
| Authentication (Signing) | 0.019 | 0.021 | 1.979 |
| Authentication (Verification) | 0.066 | 1.247 | 4.070 |
| Local Key Derivation | 1.268 | 2.597 | 4.601 |
| HMAC Generation | 0.006 | 0.009 | 0.040 |
| HMAC Verification | 0.008 | 0.011 | 0.400 |
| AES Encryption | 0.002 | 0.003 | 0.158 |
| AES Decryption | 0.002 | 0.005 | 0.138 |
| Protocol Steps | Server | Client | |
|---|---|---|---|
| Core-i7 | Esp-8266 | ||
| Time (ms) | |||
| Step 2 | 0.015 | 2.767 | 41.143 |
| Step 3 | 3.766 | – | – |
| Step 4 | – | 0.039 | 0.283 |
| Total Time | 3.940 | 3.469 | 44.426 |
| No. of Clients | Total Response Time (ms) | Throughput (Clients/s) | ||
|---|---|---|---|---|
| Core-i7 | ESP-8266 | Core-i7 | ESP-8266 | |
| 1 | 3.47 | 41.14 | 288.27 | 24.30 |
| 10 | 36.90 | 427.27 | 271.01 | 23.40 |
| 50 | 189.21 | 2198.15 | 264.56 | 22.75 |
| 100 | 387.28 | 4589.67 | 258.21 | 21.79 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hafeez, M.A.; Shakib, K.H.; Munir, A. A Secure and Scalable Authentication and Communication Protocol for Smart Grids. J. Cybersecur. Priv. 2025, 5, 11. https://doi.org/10.3390/jcp5020011
Hafeez MA, Shakib KH, Munir A. A Secure and Scalable Authentication and Communication Protocol for Smart Grids. Journal of Cybersecurity and Privacy. 2025; 5(2):11. https://doi.org/10.3390/jcp5020011
Chicago/Turabian StyleHafeez, Muhammad Asfand, Kazi Hassan Shakib, and Arslan Munir. 2025. "A Secure and Scalable Authentication and Communication Protocol for Smart Grids" Journal of Cybersecurity and Privacy 5, no. 2: 11. https://doi.org/10.3390/jcp5020011
APA StyleHafeez, M. A., Shakib, K. H., & Munir, A. (2025). A Secure and Scalable Authentication and Communication Protocol for Smart Grids. Journal of Cybersecurity and Privacy, 5(2), 11. https://doi.org/10.3390/jcp5020011







