1. Introduction
Cybersecurity is an emerging field within computer science that protects computer networks, information systems, and data from cybercriminals, hackers, and data breaches. Cyber threats increase due to the progression of the latest technologies, combined with the extended adoption of integrated applications. The growing frequency of such incidents and their level of complexity make the traditional protection methods insufficient, which is why new, more effective, and predictive measures are required [
1]. This is where artificial intelligence (AI) is a pioneering force in revolutionising cybersecurity technologies.
Over the years, AI and ML have emerged as significant contributors to today’s cybersecurity strategies [
2]. These technologies utilise data analytical models to enhance threat identification and mitigation more efficiently, coupled with accuracy, than traditional methods [
3]. AI is the branch of computer science which replicates human cognitive abilities, particularly in making decisions and solving problems [
4]. AI is further divided into ML, in general, and DL, in particular, which incorporates complex neural networks to analyse large chunks of data, seeking to identify one previously unknown pattern typical for a cyber threat [
5].
Dasgupta, Akhtar [
6] stated that intrusion detection, anomaly detection, and malware classification are some tasks in which ML techniques have been applied to achieve better results in cybersecurity. ML algorithms can, for instance, learn from network traffic to detect outliers or learn from malware features. In contrast, DL excels at more sophisticated threat detection tasks, including the categorisation of zero-day vulnerabilities or being shielded against particularly sophisticated phishing methods [
7].
According to the type of learning, ML models can be supervised, unsupervised and semi-supervised. Supervised ML models learn from labelled data; unsupervised ML models learn from unlabelled data; and semi-supervised ML models learn from a combination of both [
8]. Apart from the core of ML, ML’s subset DL uses neural networks with several layers (hence, ‘deep’) for working with large datasets to understand complex and large patterns like images, sound, and sequential data [
9]. A notable use case for DL in cybersecurity is forming advanced threat detection systems, which can decipher novel cyber-attack types by studying large amounts of unstructured data in network traffic, system logs, and other such data [
10].
ML models need to analyse vast data to identify complex cyber threats, which requires substantial computational power. For example, IDS and malware analysis require massive data processing and robust decision making in real time [
11]. This high computational demand emerged when processing the multi-dimensional network traffic data, analysing patterns from the data and implementing the complex learning models are needed. The computational complexity of some of the most used ML algorithms is presented in
Table 1.
ML-based cybersecurity solutions comprised human resources, the regulatory framework, and cryptography, underscoring the importance of multidisciplinary interconnection [
13]. The cybersecurity regulations, along with the legal limitations, ensure data privacy and compliance. At the same time, cryptography techniques support data encryption for securing information. Finally, human awareness, training, and explainable AI are crucial in shaping security measures for an enhanced secure environment against attacks.
ML and DL have been growing across a wide array of cybersecurity domains. Endpoint security leverages ML to identify malware by analysing the behaviour of files and applications [
14]. In the threat intelligence sphere, DL models are employed to analyse large amounts of data from various repositories to derive more accurate predictions of imminent cyber threats [
15].
A comprehensive analysis is essential to uncovering ML and DL’s role in cybersecurity. It will help enhance the security system’s efficiency, accuracy, and scalability. The holistic view of these advanced techniques is crucial for understanding the mechanism of automatic threat detection, reducing false positives and improving response times. ML and DL establish the future of cybersecurity, possessing the ability to assimilate data presented and respond to previously concealed challenges. They offer proactive and intelligent defence against dynamic, evolving cyber threats.
2. Literature Review
The expansion of the academic literature in cybersecurity indicates that AI, ML, and DL are becoming emerging technologies that can be leveraged to tackle current complex problems. Key insights in this literature review are synthesised directly from other studies discussing how this technology changed cybersecurity practices from 2016 to 2025. In this scientometric study, the author synthesised key ideas from various studies on how AI has transformed cybersecurity practice. Through these studies, the utilisation of ML techniques has grown to combat the exponential increase in the complexity of cyber threats and how cybersecurity has evolved over the decades.
Traditionally, rule-based methodologies are employed in cybersecurity for detection and response to cyber threats [
16]. Yet, traditional methods have become futile in addressing the growing complexity of the latest cyber-attacks, including advanced persistent threats (APTs) and zero-day attacks. As the volume of data generated in digital environments increased, the demand for more dynamic and adaptive solutions arose. Against this backdrop, AI and machine learning held out the promise of helping deal with these evolving troubles.
Several studies examine the growing development of AI, ML, and DL techniques in the realm of cybersecurity [
17,
18,
19,
20,
21,
22]. Sajid, Malik [
23] shows how machine learning algorithms can enhance IDS. These algorithms learn to identify landscapes in network traffic dynamics and act on these threats independently without human intervention. Meanwhile, Alzonem, Albrecht [
24] explores the application of DL models, especially convolutional neural networks (CNNs), to enhance malware detection and mitigation. Unlike traditional detection systems, which operate on beaconing known signatures, DL models learn behavioural patterns to detect new, mutated types of malware.
Furthermore, deep learning and machine learning are utilised to predict and prevent phishing attacks by looking at users’ behaviours to find anomalies within email communications [
25,
26]. According to Tamal, Islam [
27], ML algorithms, especially supervised learning models, have been effectively trained with large datasets of phishing emails to improve prediction accuracy. Machine learning algorithms are capable of swiftly analysing a large volume of data. Organisations can use these studies’ implications to discuss other applications of these algorithms and detect fraudulent behaviour by recognising unusual patterns in financial transactions.
Several studies have critically investigated the role of ML and DL across various cybersecurity domains. A survey on malware detection examined how we can use ensemble learning techniques that combine multiple ML models to increase detection accuracy [
28]. Abbasi, Shahraki [
29] demonstrated that deep learning can detect anomalous network traffic more efficiently than traditional methods.
Finally, research on AI in cybersecurity applications for local government has shown its enormous potential. Boppiniti [
30] indicates that AI-driven systems are increasingly used to manage public data and protect them from cyber threats. At the same time, Daneshjou, Smith [
31] raises challenges about AI implementation, such as concerns over data privacy loss, the possibility of algorithmic bias or bias in the data themselves, and the requirement for rigorous testing to confirm that these systems are working as intended.
While these promise to be heartening developments, they also come with challenges. Studies discuss the limitations of AI and ML, such as the requirement for more accessible and high-quality datasets to train the models effectively [
32,
33,
34,
35,
36,
37]. Moreover, the insufficient explainability and transparency of AI-driven decisions are of great concern, particularly in high-stakes cybersecurity scenarios [
38]. Several studies request more research on improving AI models’ interpretability so cybersecurity professionals can understand and trust the AI models’ decisions.
Overall, the reviewed literature presents scientometric analysis as a method to understand research trends and limitations. Although these studies were subject to geographical biases, limitations associated with the database, and subjectiveness in the qualitative approach, they provide valuable resources to inform future research directions. Also, expanding the scope of these studies to include more interdisciplinary approaches, diverse geographical contexts, and empirical analyses could significantly enhance our understanding of the complex dynamics within these fields [
39,
40,
41,
42].
Future cybersecurity AI, ML, and DL research will focus on emerging systems more adaptable to evolving cyber threats. According to Ajala, Okoye [
43], AI and ML can have great potential in building autonomous cybersecurity systems that function autonomously to discover, analyse and respond to threats in real time. However, these models need further advancements in their accuracy and efficiency. Additionally, with the further development of cyber threats becoming more complex and sophisticated, interest in interdisciplinary approaches that combine AI with other fields like cryptography and human behaviour analysis has also been sparked. For instance, deep learning can be integrated into threat intelligence systems to detect more advanced attack patterns and predict potential vulnerabilities before exploitation [
44,
45].
This study presents a detailed investigation of the historical progression of ML and DL in cybersecurity, providing valuable insights that will help practitioners make more informed decisions about future AI implementation technologies in the field.
The following are the research focuses of this study:
To investigate the sequential growth and trends in publications from 2016 to 2025 to know the future potential of this research area;
To systematically map out the top-performing authors, influential countries and significant institutions in this field, thereby presenting a framework for potential researchers and stakeholders for future research;
To evaluate the co-authorship network between countries and researchers, highlighting their relationship by publication counts and total link strength (TLS);
To identify the research trends and patterns using comprehensive keyword analysis.
3. Methodology
The present study performs a scientometric review of the current scholarly literature, investigating the application of AI, ML, and DL in cybersecurity. Scientometrics is a research methodology to study the scientific literature through publication patterns, citation trends and research development [
46]. It enables the quantification and visualisation of research evolution and deeper insights, for instance, on emerging trends, methodologies, and knowledge networks in different domains. The main goal of this scientometric study is to discover the global research trends concerning the implementation of ML and DL technologies in the cybersecurity domain and to identify the influential contributions of researchers, institutions, organisations, and countries.
The Scopus database was chosen for this analysis due to the vast coverage of high-impact articles in all aspects of scientific studies, high-quality indexed journals and its reliability for scientometrics studies. Scopus is deeply trusted to provide comprehensive citation data and to conduct bibliometric research [
47]. Moreover, the potential reason for choosing the current time frame, January 2016 to January 2025, was to focus on the latest and most advanced research and developments in the field. The data were gathered from 2016 to 2026 due to the significant growth of ML and cybersecurity research and ongoing trends. Hence, the chosen time frame confirms that scientometric analysis is related to more recent research and discussions.
With extensive metadata, the database is suitable for scientometric tools, such as VOSviewer, which facilitates data export in formats supporting bibliometric analysis. The relevant publications were retrieved on 24 December 2024, employing a Boolean search strategy. The Boolean search string is given below:
(TITLE-ABS-KEY (machine AND learning OR machine-learning) OR TITLE-ABS-KEY (deep AND learning OR deep-learning) AND TITLE-ABS-KEY (cybersecurity)) AND PUBYEAR > 2014 AND PUBYEAR < 2026 AND (LIMIT-TO (DOCTYPE, “ar”) OR LIMIT-TO (DOCTYPE, “re”)) AND (LIMIT-TO (PUBSTAGE, “final”)) AND (LIMIT-TO (LANGUAGE, “English”)).
Boolean search was used because it filters large datasets with the Boolean operators and keywords used in the research [
48]. The search minimises irrelevant studies and ensures the query retrieves more relevant results. Hence, it improves the efficiency and transparency of the search in the data collection process.
The search produced 9813 publications, including journal articles, conference papers, review articles, and book chapters. These publications were exported to CSV format to be compatible with any bibliometric analysis software. The data were thoroughly screened for completeness, eliminating records with incomplete bibliographic information, duplicate entries, or documents that did not directly address using ML and DL technologies in cybersecurity.
Figure 1 shows a search framework for retrieving relevant documents.
Document Search Framework
Figure 1 demonstrates the document search framework using a funnel approach during this research, gradually reducing an initial collection of 9813 documents to the final 3712 counts. The main objective is to collect a complete group of high-quality articles that will later be analysed. Each phase includes a description that explores technological structures, system component assembly, and motivational design factors.
Multiple inclusion and exclusion criteria were applied to reduce the final number of articles to 3712. The first process includes using Scopus with specific keywords inserted across abstracts and keywords while including terms in the title field. This approach reaches maximum study representation while creating an inclusive final dataset. The constructed search queries aim to retrieve research themes and relevant terminology encompassing our research objectives.
In the second phase, non-relevant publications were eliminated through title-based criteria. After that, conference proceedings, reports, thesis, book chapters, preprints, and books were removed while selecting original research and review articles that achieved formal peer review. Our quality standards determine this criterion to ensure the quality and reliability, which confirms that our analysis targets only peer-reviewed scholarly publications.
The analysis moves to “in press” articles for removal because their content and citation information will likely change before becoming final publications. Our analysis relies on only complete articles because this approach reduces potential issues from temporary or developing information in preliminary texts.
The procedure ends with the removal of articles that are not written in English. Our specialised analytical apparatus operates best on English-language content, so this sorting process enhances the following analysis operations. An integrity assessment verifies that the database contains only records that contain complete metadata information and operational DOIs.
This resulted in 3712 records, and we continued to analyse these final documents. For scientometrics analysis, this study used VOSviewer, a powerful tool for analysing bibliometric networks, to visualise the data extracted from Scopus for this study [
49]. VOSviewer was used to map author co-authorship networks, country co-authorship networks, and research cluster network maps by keyword co-occurrences. The generated network maps facilitated identifying emerging trends in ML and cybersecurity, influential authors, countries and institutions, and key research areas. This tool works exceptionally well for mapping the connections between different research topics, offering a magnificent view of the development of ML and DL in cybersecurity.
Moreover, VOSviewer was used because it can perform network visualisation, user-friendliness, and co-occurrence analysis. Additionally, VOSviewer was suitable for our study objectives because it could map the keyword co-occurrence and citation analysis.
This study focuses on one tool instead of many simultaneously, avoiding the complexity of integrating multiple software platforms and making the results comparable and the visualisation clear. The generation of easy-to-understand bibliometric maps by VOSviewer makes it a powerful resource for conducting this scientometric review. This study offers a holistic overview of AI, ML, and DL research trends in cybersecurity through this methodology, exploring how these technologies have been used, the challenges encountered, and the future of this field. This research is meant to guide future research and deepen the understanding of AI, ML and DL’s role in cybersecurity practices.
4. Results and Findings
Over recent years, the research field where cybersecurity, ML, and DL intersect has grown significantly. Between 2016 and 2025, 3712 publications were written by 2865 authors from 160 organisations in 114 countries. This represents an increasing interest and collaboration in the area and makes for a fascinating and promising area of future research. The publications ranged over 159 journals, and being a vibrant and promising field, there has been a steady increase in research output. This study only considered journal articles and excluded conference proceedings or books.
Table 2 reviews the scope and scale of the research dataset and provides key data statistics. It sourced the data from Scopus bibliographic repositories, guaranteeing its coverage of trends and developments by scholarly production in cybersecurity and machine learning/deep learning, covering the last ten years (Jan 2016—25).
This statistical overview foundationally contextualises the analysis of patterns, trends, and contributions within the field, demonstrating its wide-ranging relevance and the active engagement of the global research community.
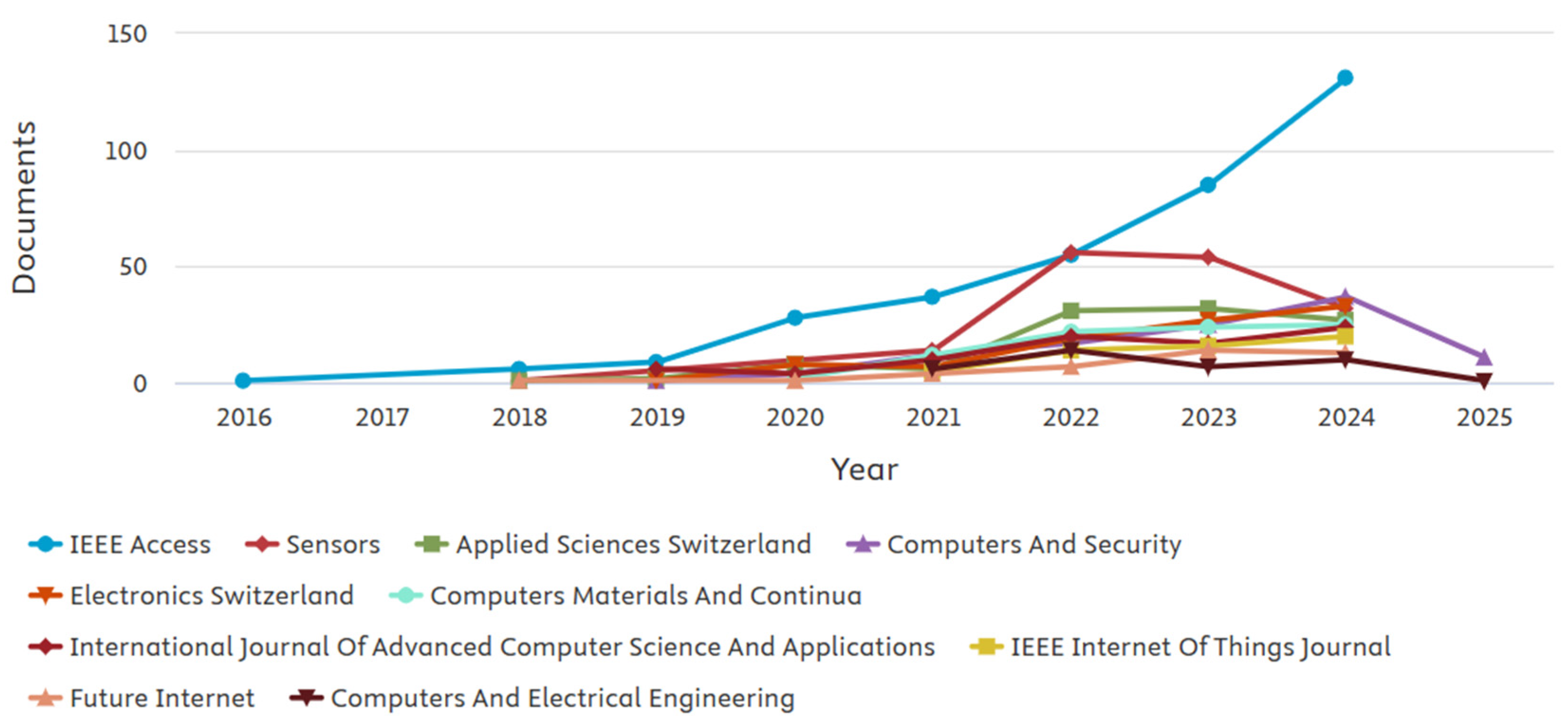
Figure 2 further highlights the publications per year by source journals.
The field is expanding quickly, as reflected by the growing number of publications each year. These findings suggest the importance of ML and DL techniques in addressing cybersecurity issues, including cyber-attack detection, anomaly detection, and network security.
4.1. Document Types in Cybersecurity and ML/DL Literature
The studies included in this research consist of articles that include in-depth studies, new findings, and practical implementation of ML/DL techniques in cybersecurity and review papers that summarise and analyse the available research to provide general prevailing patterns, challenges, and possible future research directions. These two types of research contribute significantly to strengthening our knowledge and applying ML/DL to cybersecurity, from which researchers and practitioners can benefit (see
Figure 3).
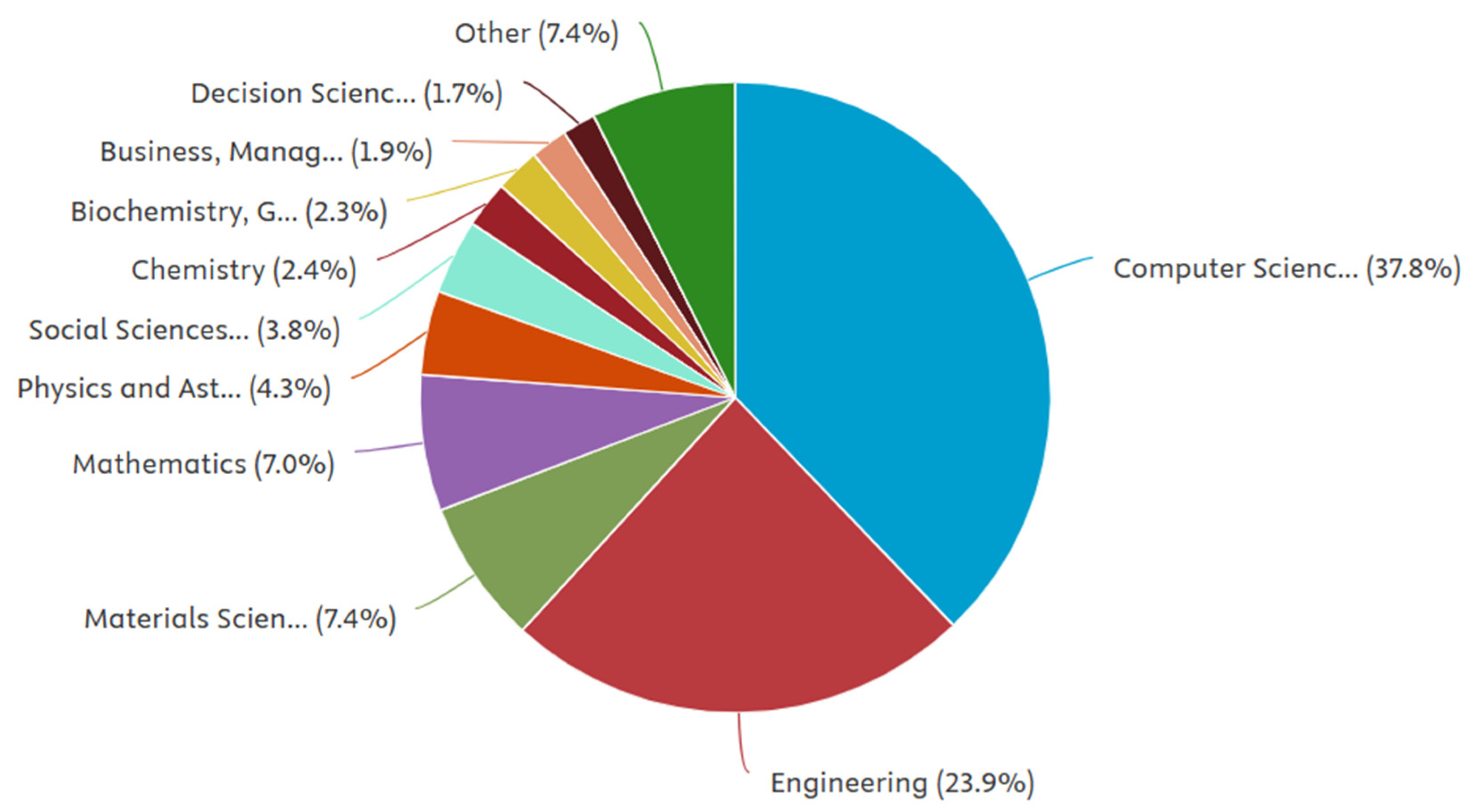
4.2. Subject Areas of Cybersecurity and ML/DL Literature
The research spans multiple subject areas, highlighting its interdisciplinary nature. For instance, L/DL models are applied in engineering and technology domains to enhance systems’ cybersecurity. Many studies concentrate on developing algorithms and analysing their applications in areas such as threat detection, anomaly detection and safeguarding data, which lies in computer science. In many studies, mathematical models were used to optimise the ML/DL algorithms to achieve better performance in cybersecurity applications. Also, some studies address medical and environmental data defence using ML/DL. Further fields are highlighted in detail in
Figure 4.
The variety itself reflects the pertinence of applying ML/DL in the context of cybersecurity into several disciplines and the potential to trigger innovation and tackle complex security problems.
4.3. Documents by Source
Finally, this section highlights the growth of research in cybersecurity and machine learning (ML)/deep learning (DL) from 2016 to 2025. Three thousand seven hundred twelve publications were recorded over this period, evidencing the growing importance of this area. The data are from Scopus and cover 114 countries, 2865 authors, 160 organisations, and 159 sources.
Figure 5 depicts the documents per year by source.
4.4. Top Ten Productive Authors in Cybersecurity and ML/DL Research
The contributions to this field are also global, as shown by the top ten prolific cybersecurity and ML/DL research authors. The most productive author on the list is I.H. Sarker from Swinburne University of Technology, Australia, who had 17 papers and a share of 0.46%. In second place come Moustafa, N. from UNSW in Australia and Srivastava, G. from Brandon University in Canada, with 16 papers (0.43%), while in third place is Motwakel, A. from Prince Sattam Bin Abdulaziz University, Saudi Arabia, with 15 publications (0.40%). The fourth rank is shared by seven authors publishing 13 papers (0.35%) from Saudi Arabia, Pakistan, Poland, Jordan, and Italy. Last, but not least, five authors shared the fifth position, having each published 12 (0.32%) papers from Saudi Arabia, Taiwan, Poland, etc. This distribution shows collaborative and international-oriented research efforts concerning cybersecurity and ML/DL, particularly the involvement of Australia and Saudi Arabia. Moreover, I.H. Sarker from Swinburne University of Technology, Australia, and Moustafa, N. from UNSW in Australia have significantly contributed to AI, cybersecurity, and ML research with their high influential publications. Their huge publications and citations advocate that their potential work supports basic research in this field of cybersecurity and ML.
Table 3 presents the scenario in detail.
4.5. Top Ten Most Productive Organisations
Saudi Arabia leads the way among educational institutions, with the top 10 most prolific cybersecurity and ML/DL research organisations. Top of the list is Princess Nourah Bint Abdulrahman University, with 87 papers (2.34%), and King Abdulaziz University, with 81 papers (2.18%). Of these, 80 papers (2.16%) were from King Saud University and Prince Sattam Bin Abdulaziz University and 72 (1.94%) from King Khalid University. Deakin University in Australia and the Lebanese American University in Lebanon are noteworthy.
Table 3 reveals that Saudi Arabia emphasises the ML and cybersecurity fields, which significantly impacts the research area. This indicates that they have invested more in research and development, especially in their initiative, Saudi Vision 2030. Hence, their recent attention on AI, cybersecurity, and intelligent devices drove them towards more research publications. Moreover, Saudi Arabia remained the top contributor due to the substantial state-sponsored research funding and support in national cybersecurity policies, similar to the United States’ National Science Foundation (NSF), China’s investment in AI-based cybersecurity, and Europe’s cybersecurity projects.
Countries from developing regions face multiple barriers, such as low government support, financial restrictions, less organisational collaboration, and a lack of an advanced security environment. Additionally, the data in
Table 4 highlight Saudi Arabia as a research hub because of its high research output from academic institutions.
4.6. Top Ten Most Productive Publication Sources
This field is very interdisciplinary, and the top ten cybersecurity and ML/DL research publication sources are the most interesting among all the results. We start with IEEE Access, leading the list with 352 published papers (9.48%), focusing on engineering and technological innovations. Following this, we observe 157 papers (4.23%) in the sensors category regarding artificial intelligence, wireless sensors and other applications. Others covered systems, communication and robotics, with 95 papers (2.56%) from Electronics (Switzerland), 107 (2.88%) from Applied Sciences Switzerland, and Computers and Security also with 107 (2.88% of the total). Overall, IEEE and Sensors appeared to be highly productive journals due to the high volume of engineering and technology research in these journals. Researchers publishing more in these journals might be due to their peer-review process and relatedness with the latest technology domains like AI, cybersecurity and innovative technologies.
Several topics and disciplines emerge from these journals, creating a space where cybersecurity and ML/DL research meet (see
Table 5).
4.7. Top Ten Most-Cited Publications
The field’s influential contributions are exhibited in the most-cited publications in cybersecurity and other publications that are most cited in ML/DL research. The article “Review of deep learning: concepts, CNN architectures, challenges, applications, future directions” leads with 3744 citations, followed by “Machine Learning: Algorithms, Real-World Applications and Research Directions” with 3026, which summarises the concepts, CNN architectures and challenges as well as applications and future directions of deep learning techniques. “Deep Learning: A Comprehensive Overview on Techniques, Taxonomy, Applications and Research Directions” lists 1205 citations of the type of applications and threats associated with DL systems. Other works mentioned in this document are highly cited and cover adversarial machine learning, blockchain with AI, ChatGPT, and healthcare. From that, it is clear that this research spans widely and is highly impactful.
Table 6 details the search results’ top ten most-cited research publications.
In summary, the data portray the exponential expansion of cybersecurity and ML/DL research, which results from many authors’ contributions in every organisation and almost all the journals worldwide. As such, this vibrant research landscape is essential to tackling contemporary cybersecurity challenges and thinking ahead about next-generation systems.
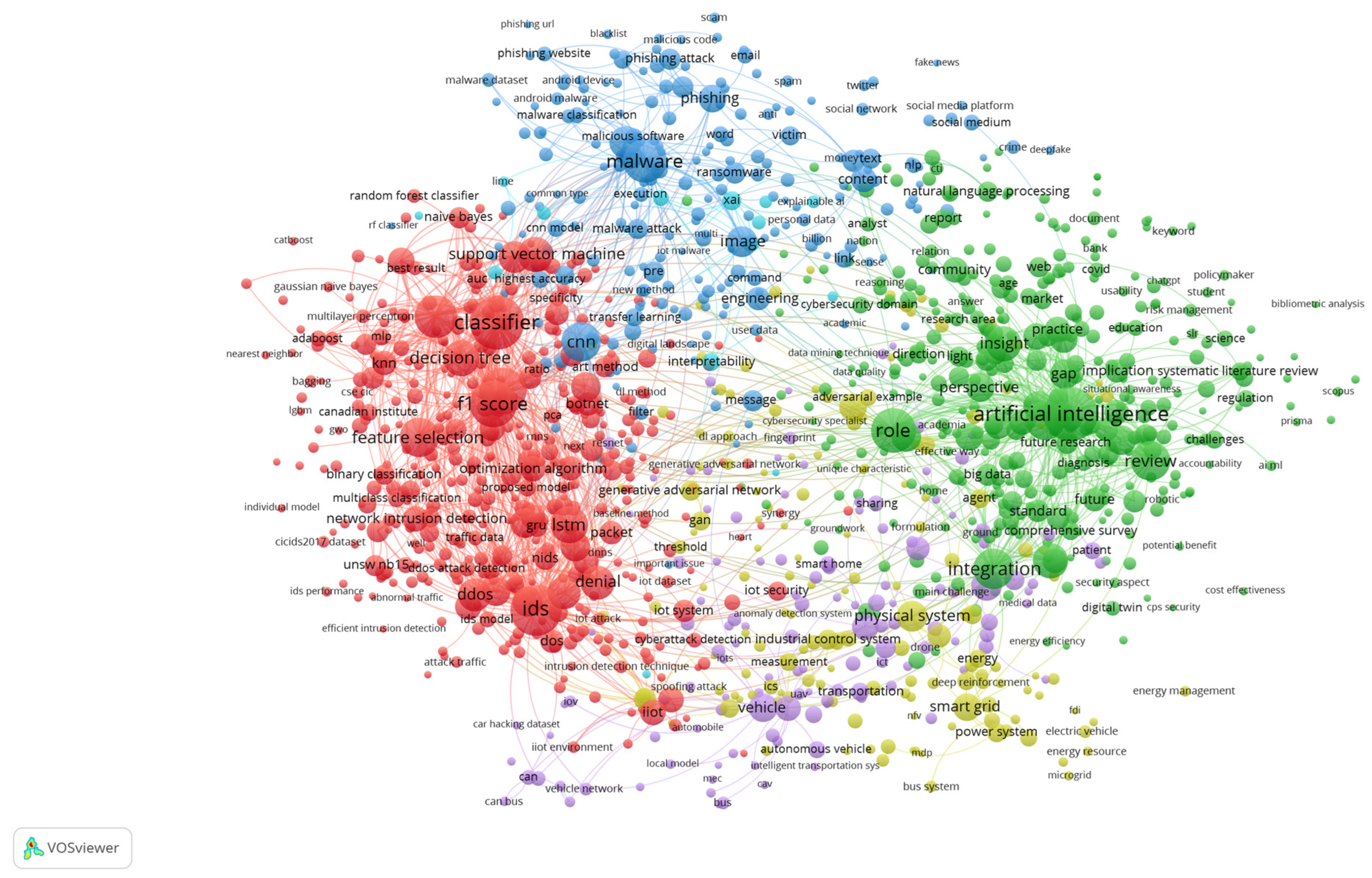
4.8. Top Ten Occurrence Keywords in Cybersecurity and ML/DL Literature
Table 7, highlighting the top ten highest-appearing keywords in the cybersecurity and machine learning/deep learning (ML/DL) literature, offers a quick overview of the topics of interest in this field. “Occurrences” stands for how often each keyword appeared in the literature, “Links” for how many edges between these keywords we had in the network, and “Total Link Strength” for the strength of connections between these keywords.
The most common word, by far, was the keyword artificial intelligence (AI), which surfaced 476 times, with a maximum link strength of 5853. It is not that surprising, though. AI is fundamental in many cybersecurity applications, mainly anomaly detection, behaviour analysis, and automation [
51]. Due to the high frequency and strong link strength, research on this subject relies heavily on AI, as multiple studies strongly agree with using AI-based models and algorithms.
The keyword “Classifier” is next to AI, as it was linked with AI 472 times in total, with a link strength of 6026. This implies that classification algorithms play a crucial part in cybersecurity where their task of identifying malicious activities (e.g., malware, intrusion) is needed. This idea is reinforced by the fact that the strength of the connection with AI also makes us realise that ML methods, like supervised learning techniques, are significant in cybersecurity. The third most frequent keyword is ‘Intrusion Detection System’ (IDS), which has 422 uses and 5499 link strength. The detection of unauthorised access or network threats is a core area of cybersecurity, and IDS reflects the continued importance of this activity. This keyword’s placement at the top emphasises the trend to build real-time, automated systems that detect and neutralise intrusions, sometimes with machine learning.
Malicious software (malware), which appeared 317 times with a link strength of 3798, has become a growing concern for cybersecurity threats. Other keywords often containing the word malware (e.g., AI, classifiers, intrusion detection) suggest that malware is relevant to multiple aspects of cybersecurity research. The strength of the connection between malware and the above technologies signals a concerted approach to deploying more advanced algorithms to contend with it.
Another keyword, “Integration”, was found 263 times, describing the rising interest in integrating various technologies and systems into cybersecurity frameworks. Given the criticality of integration for next-generation security systems involving sophisticated machine learning models, diverse detection techniques, and response strategies, it is crucial to address the complexities created by heterogeneity in accepting, handling, and managing data [
18]. With its focus on integration, this shift suggests that holistic and connected responses to cybersecurity problems are the way to move forward.
The sixth position is the convolutional neural network (CNN), which has 254 observations and a link strength of 3316. CNNs are particularly suited for pattern recognition tasks in cybersecurity, such as image analysis in malware detection or network traffic monitoring. Although the number of times it occurs is much less than keywords such as AI or classifiers, it shows that CNN is becoming part of advanced ML and DL learning models for cybersecurity.
Feature selection appears 248 times, with a link strength of 3391. The relevance of this keyword in the table is critical to optimising models for cybersecurity tasks, namely using only the most appropriate data for analysis.
Numerous classic machine learning algorithms are used in cybersecurity for classification tasks, e.g., detecting intrusions or identifying threats; among them are decision tree (210 occurrences) and support vector machine (SVM) (202 occurrences). While the number of occurrences is relatively lower than CNNs or AI, one might suspect recent research to lean more towards complex models. Yet, decision trees and SVMs serve some integral purpose in specific applications. Here, “Physical System” is ranked tenth, with 160 occurrences. The phenomenon is also expressed in
Figure 6 below.
This keyword occurs less frequently with the present study’s search query. However, it represents an emerging research space that overlaps with cybersecurity, primarily related to the Internet of Things (IoT) and how ML models can inform physical infrastructure. By looking at the frequency of this keyword, we can express that it may be less cosmic and a more tiny or emerging area of study than traditional cybersecurity interests. However, in a more significant implication, cyber-physical systems are a hot research area in today’s world of cybersecurity.
4.9. Co-Authorship Network of Most Productive Countries
The findings also highlight the co-authorship network among the top-performing productive countries. Using the table in the “Country Co-Authorship Network of Top Productive Countries”, a detailed review of the most productive countries in cybersecurity and machine learning/deep learning (ML/DL) research is performed.
Table 7 presents countries in order of the total number of publications, citations, and link strength. It provides a glimpse into international collaborations and the influence of different countries in the field.
Moreover,
Figure 7 shows global contributions to cybersecurity and ML/DL research. Countries like the USA, Australia and China are the leading countries. The maximum number of indexed papers is from these countries, and the citation rate is also high. The emerging nations, including Saudi Arabia and India, are making more contributions and profiles in the worldwide research system. Cooperation, which can also be measured by the total link strength of the organisation, is essential to emphasise the leap of progress in cybersecurity and ML/DL through international partnership. However, one must also factor in the quality of the produced research, as evidenced by the difference in citation counts, while employing the number of publications as a measure of research output. Therefore, although the USA and Australia ranked highest in publications and citations, other countries are coming up fast and writing more.
4.10. Most-Cited Countries and Their Publications
Australia ranks with 19,977 citations, a very slight distance from the USA with 19,051 citations. This implies that Australia is well represented in the field and participates in several kinds of research. However, it is always good to note that although there are more publications from Australia, it is visible that research from the USA is potentially having a more significant impact, as revealed by the citation data. The citation represents the degree of visibility and the utility of research by scholars from various countries.
China is the third on the list, with 12,094 citations. However, as presented here, China has fewer ML/DL and cybersecurity citations than Australia and the USA. Still, it is growing, and the citation records suggest that the research is making a growing impact. The total link strength, which tends to give insight into the connection between a country’s research output and other nations, displays the degree of collaboration. These collaborations, together with China’s increased participation and its place within these international co-authorship networks, highlight the fact that more members of the academic community are recognising and engaging with Chinese research.
The United Kingdom is fourth with 10,994 citations, which indicates European countries’ dominance. However, the number of such publications differs significantly between the countries, with the USA and Australia boasting more prominent citation scores than their publications. This indicates that even though the UK produced numerous publications in human resource management, its research might not have been as impactful internationally.
Saudi Arabia is in fifth position with 9281 citations, while India stands in sixth with 8072. A particular focus should be placed on Saudi Arabia as it underlines its increased participation in exploring cybersecurity and ML/DL research with support from the institutional framework and funding of advanced technologies. India, although lagging slightly, is emerging as a force in the research area, emphasising the cost-effectiveness of solutions that address cybersecurity issues, particularly in the context of developing countries. Other countries with appreciable contributions include Spain, Canada, Pakistan, and Italy, ranked seventh to tenth. For example, Spain comes seventh with 6952 citations, showing its moderate activity within the field. However, it still does not reach countries such as the USA and Australia in terms of citations. Canada and Pakistan show considerable engagement, but their research influence, as reflected in citations, might not be as widespread as that of the USA or China (see
Table 8).
4.11. Authors Co-Authorship Network
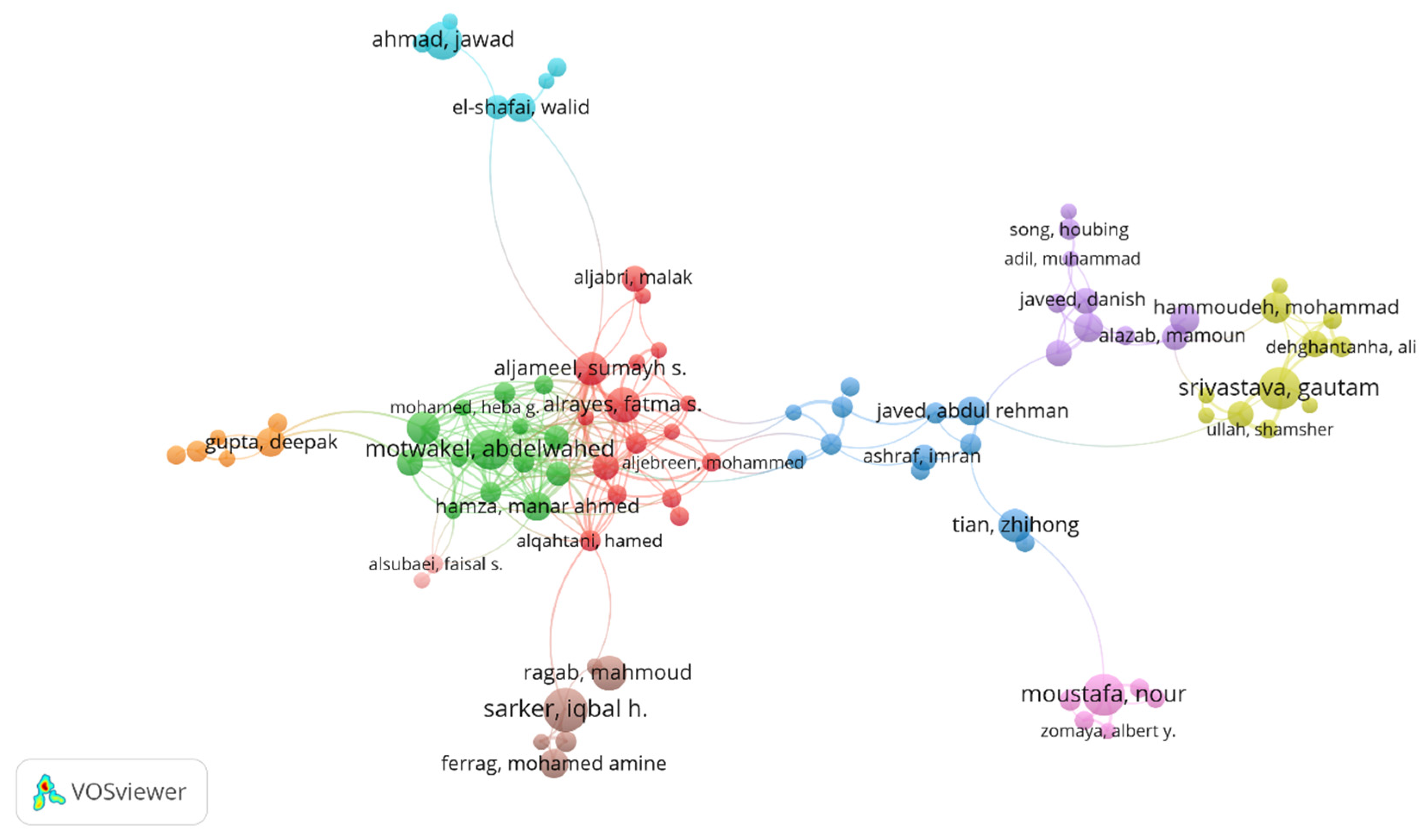
The “Authors Map”, created with VOSviewer, presents the network and connections between authors in cybersecurity, machine learning, and deep learning. VOSviewer also constructs and analyses bibliographic networks, which helps students and researchers investigate collaboration and publication trends.
Figure 8 represents the most influential authors in the current domain and provides a rough idea of the most active authors. This brings out other researchers, such as Jawad Ahmad, Walid El-Shafai, Iqbal H. Sarker, and so on, who play an essential role in the field. They are involved in various papers, meaning they are quoted or work closely with other writers quite often, which means they contribute significantly to the body of knowledge.
Finally, the diversity of authors also brings considerable collaboration between institutions and countries at a normal level. For instance, authors from Saudi Arabia, India, Australia, and the USA prove that the research world is not limited. This global collaboration is needed as people gather different approaches and significant ideas for developing cybersecurity and ML/DL. Nevertheless, the list also indicates the concentration of leading scholars. If only a few authors are presented on the map, it can mean that few authors are in the field or that only a few key scholars are frequently cited. This can sometimes cause redundancy or slow down the generation of new ideas. In addition, while the map indicates who is publishing, it does not shed as much light on what is being published, whether or not it is of high quality and perceived as impactful or whether an individual is a lead author or co-author among others.
Another factor one must consider is the distribution of male/female writers since gender parity is a contentious academic issue. By referring to the names displayed in this map, one has to agree that there seem to be gender differences, where most names are male. This raises questions about gender representation in research, mainly in technology disciplines such as cybersecurity and ML/DL. Finally, the “Authors Map” can locate interactions and groups of authors probably working on the same ideas. However, it is essential to note that the VOSviewer gives a clear nexus of author ties. Still, it does not account for the relation type and whether it is academic, interdisciplinary, or industrial.
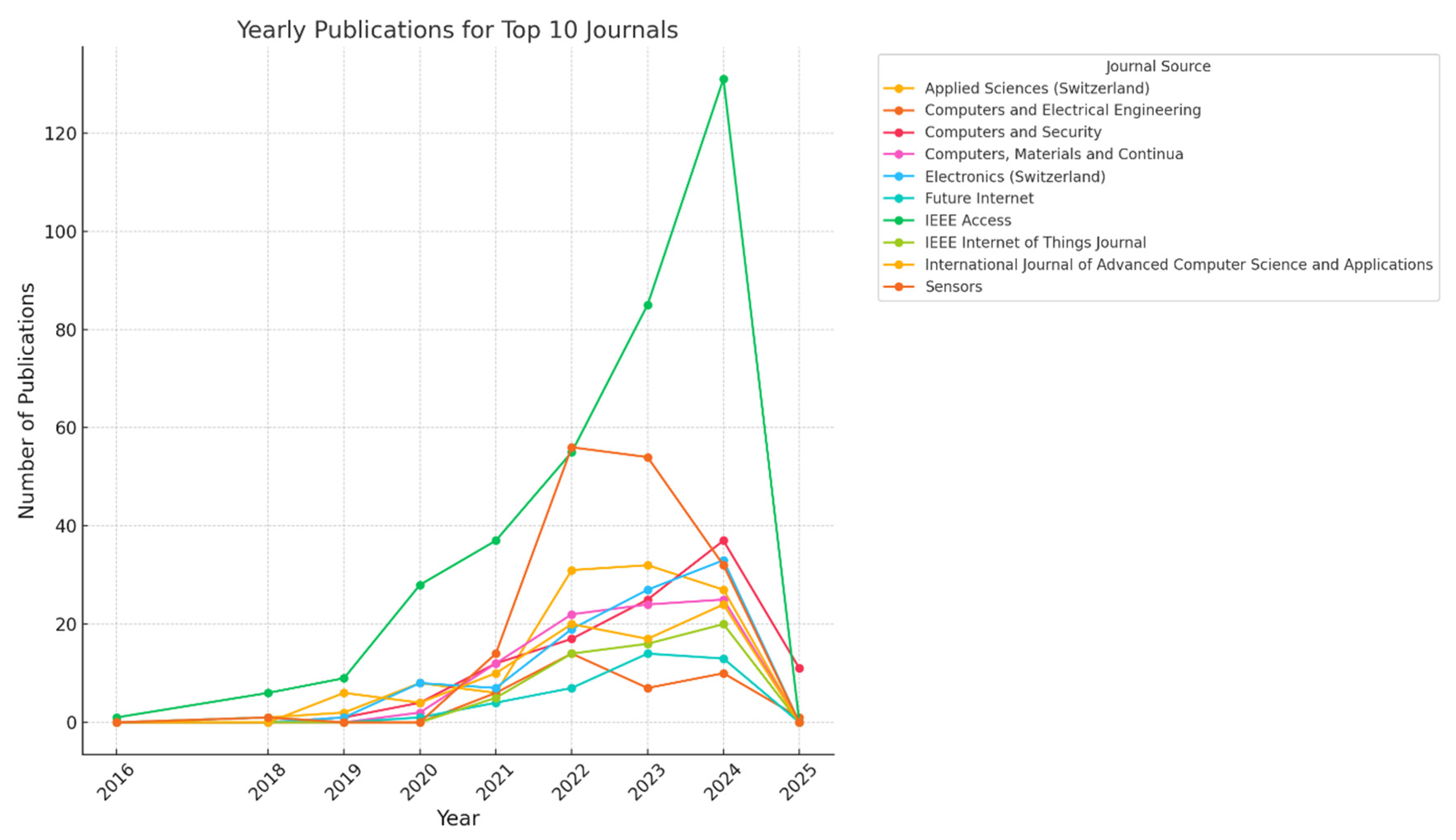
4.12. Yearly Publications by Top 10 Journals
Though the “yearly publications by top-ten Journals” data offer essential insight into the structure of cybersecurity, ML, and DL, we focused on the data related to 2016 to 2025. The data include publications from ten prominent journals:
Journal of Applied Sciences, Computers and Electrical Engineering, Computers and Security, Computer, Materials and Continua, Electronics, Future Internet, IEEE Access, IEEE Internet of Things Journal, International Journal of Advanced Computer Science and Applications, and
Sensors as presented in
Figure 9.
Based on the information from the analysed journals, this general trend presupposes an increase in publications starting from 2018. This means there was a moderate increase in interest and demand for conducting cybersecurity and ML/DL research. The upward trend demonstrates the significance of these fields in meeting today’s technological phenomena, with more writers contributing their articles to quality journals.
Some journals, such as IEEE Access and Sensors, saw activity increase sharply in 2019–2020. This could be attributed to heightened awareness of the uses of ML/DL in cybersecurity, especially since industries began ramping up their digitisation and the call for effective shielding of IT systems became keener during this period.
IEEE Access appears to have had a significantly high number of published articles recently, which supports the argument that this journal is at the forefront of transmitting new knowledge. In the same way, yet still slightly below the top 15, Sensors also produces a considerable amount of content, which can be attributed to the rising popularity of IoT and intelligent security networks involving sensors.
On the other hand, the Future Internet and Computers and Security journal may have a lower growth rate. This indicates that more focused areas of cybersecurity and ML/DL activities may receive fewer submissions than IoTs and applied sciences.
Most of the journals in the sample exhibit an overall increase in publications. Still, it is also evident that some journals act as if they are reaching their troughs or, at best, slow plateaus following their years of highest productivity. For instance, Computers and Electrical Engineering and Electronics from Switzerland show sectors where publications stop growing or shrink over time. This could mean an oversaturation in the explored research issues or that researchers have switched preferences to other journals that publish more modern or highly significant studies.
5. Discussion
Modern cybersecurity research combining ML and DL creates new waves of international cooperation, interdisciplinary techniques, and state-of-the-art defensive strategies. The same AI-based protective measures researchers worldwide operate to defend networks and data allow attackers to optimise their malicious methods. A dual-use reality between researchers and attackers has initiated a worldwide technological advancement, manifesting through rising publications and improved research topics involving side-channel attacks, blockchain defences, and adversarial learning. The field is expanding through heightened scholarly output backed by broad geographic participation and vital keyword clusters consisting of AI, classifiers, IDS, and CNNs. The growing complexity of cybersecurity demands teams to unite experts across multiple domains, including legal and ethical fields and the social sciences, to create complete cybersecurity solutions. Scholarly research output has continually expanded from 2016 to 2025, thus marking the essential position that characterises this domain and demonstrating its ongoing growth, enabled by computer threats and AI applications.
5.1. Global Involvement and Interdisciplinary Collaborations
The research on cybersecurity utilising ML and DL reaches global scope because authors participating from 114 nations collaborated mutually, as excerpted in
Figure 7. The current complexity of modern cyber threats exceeds technical difficulties; hence, cross-border and interdisciplinary partnerships prove indispensable. The combination of international organisations enables scientific teams to share talents with resources and research materials, resulting in the faster discovery of security innovations for identifying threats, evaluating weaknesses and enhancing privacy measures.
Social sciences and ethical and legal frameworks should unite with technical perspectives to address fundamental socio-technical matters, including AI decision accountability standards and ethical rules for extensive user data collection and privacy compliance frameworks. Various documented cooperative programs, such as global cyber operations ranges and joint protection systems for threat detection, demonstrate how expertise in technical and policy domains generates technologically solid and societally harmonised solutions. The combination of cybersecurity specialists and legal scholars has led to clear data protection definitions, and sociologists and psychologists have brought forward strategies to handle insider threats. Effective cybersecurity surpasses technical know-how since it needs comprehensive solutions, which unite ethical, legal, and societal perspectives.
5.2. Use of ML/DL Methods in Cybersecurity Research by Attackers and Defenders
Both cyber defence entities and attackers depend increasingly on ML/DL models to enhance their automatic approaches in their strategies. The organisations utilise real-time intrusion detection systems (IDSs), adaptive malware analysis, and large-scale network anomaly detection as their main protective functions. Manufacturers leverage SVM and decision trees alongside CNNs to analyse vast traffic or log data because these classification tools exceed traditional anomaly detection rules. The ability of ML-driven models to learn from recent data acquisitions allows them to effectively detect new threats in zero-day exploit scenarios.
Support vector machines (SVMs) and convolutional neural networks (CNNs) have considerably impacted organisations’ cybersecurity systems. SVMs are comprehensively applied in cybersecurity for their efficiency in structured and high-dimensional feature classification tasks such as IDS for detecting distributed denial of service attacks, malware classification using features like network behaviour, and network anomaly detection to detect abnormal network traffic patterns. In contrast, CNNs are effective for unstructured and multidimensional data in malware detection by image-based techniques and intrusion detection by analysing network traffic data.
Cybercriminals utilise ML/DL to create attacks, which have become more sophisticated than before. The Prabhu Kavin, Karki [
60], and Anwar [
53] academic works demonstrate that hackers employ ML techniques to disclose private user data by studying side-channel frequency interactions. Growing research shows how electromagnetic side-channel analysis of in-display fingerprint sensors combined with GenAI models and sensor analysis techniques enables adversaries to recover fingerprints, as presented in “Recovering Fingerprints from In-Display Fingerprint Sensors via Electromagnetic Side Channel” [
61] and “Accear: Accelerometer acoustic eavesdropping with unconstrained vocabulary” [
62]. Through these abilities, attackers develop better ways to evade detection, producing polytopic malware and launching massive human-plausible phishing operations. Security researchers now invest their work in developing adversarial training systems, blockchain validation, and strong data sanitisation techniques to confront modern threats [
63,
64,
65].
Adversarial learning techniques, such as the fast gradient sign method and projected gradient descent, facilitate intrusion detection, malware classification, and facial recognition. The key purpose of adversarial training is to enhance model resistance against attacks. On the other hand, federated learning helps minimise risks, provides resistance from poisoning attacks, and learns from evolving cyber threats. Security efforts evolve through an escalating competition between offensive and defensive ML/DL applications, continually impacting the cybersecurity environment.
5.3. Sequential Growth and Trends in Publications from 2016 to 2025
A bibliographic study of cybersecurity studies reveals an increasing trend of research on ML/DL applications within the field from 2016 up to 2025, as shown in
Figure 2 and
Figure 5. Yearly growth data demonstrate how theoretical work on new architecture and algorithm structures, practical IoT security, and other applications expand continuously in the field. The ongoing growth demonstrates a widespread belief that ML/DL will continue strengthening cybersecurity infrastructure, which protects conventional networks, emerging smart cities, healthcare systems, and autonomous vehicles.
The upward publication trajectory points to several promising avenues from a future potential standpoint. Research experts work on explainable AI technology alongside federated learning for privacy-conscious decentralised training systems and quantum-resistant cryptographic solutions to protect against quantum computing developments. Advanced attack vectors mature large language models, and other generative artificial intelligence applications requiring stronger defensive solutions will likely appear. Cybersecurity publications indicate that research activities will grow by uniting different fields to achieve innovative solutions that abide by rules and ethical principles.
5.4. Research Trends and Patterns by Comprehensive Keyword Analysis
Table 6 and
Figure 6 demonstrate that artificial intelligence is the dominant term. It dominates various cybersecurity operations, from anomaly identification to real-time threat awareness. Artificial intelligence is closely connected with classifiers and intrusion detection systems, demonstrating how supervised learning models detect network traffic malice and system intrusion activity. The ongoing refinement of datasets for better classification accuracy involves continuously developing malware variants that necessitate dynamic, optimised modelling approaches according to malware and feature selection mentions.
Convolutional neural network joins other important keywords to prove deep learning’s key role in processing complex data types, such as images for malicious code display or time-series signals for network analytics purposes. The identified top keywords show evidence that security experts unite different defence mechanisms to create extensive security solutions that integrate heuristic methods with ML classifiers and sensor networks with blockchain-based identity management systems. The increase in physical systems research reflects ongoing efforts to link investigations between IoT devices, critical infrastructure and industrial control networks. These keywords demonstrate how cybersecurity research expands towards multiple goals, requiring ML/DL applications and futuristic protections involving multi-level security measures and real-time information systems.
6. Conclusions
This study offers a wide-ranging bibliometric analysis of the intersection between cybersecurity, ML and DL, delineating rapid progress, essential contributors, and landmark publications in this area. A study of 3712 publications by 2865 researchers passing through 160 organisations and 159 sources shows the dynamic and interdisciplinary nature of research efforts to meet changing cybersecurity challenges.
Most striking is the significant global involvement in this field, with contributions from 114 countries. Saudi Arabia was a leader in organisational representation and the most prominent among the authors. Princess Nourah Bint Abdulrahman University and King Abdulaziz University are leading some serious academic output that firmly cements Saudi Arabia as a place to watch for cybersecurity research. The degree of this regional dominance underscores the need for sustained investment in educational and research efforts to investigate contemporary cybersecurity threats.
The prolific contributions of individual researchers such as I.H. Sarker, N. Moustafa, and G. Srivastava reflect the critical role of dedicated expertise in advancing knowledge and practical applications in cybersecurity and ML/DL. Their extensive work provides a foundation for ongoing and future research, driving innovation in detecting, mitigating, and preventing security threats.
Leading journals such as IEEE Access, Sensors and Applied Sciences Switzerland are expanding their publications to promote interdisciplinary knowledge. Exhibiting a range of diversity from engineering and sensor technology to security systems and AI applications is necessary for handling cybersecurity challenges. Moreover, this analysis highlights the profound effect of seminal works, such as “Review of Deep Learning: concepts, CNN Architectures, challenges, applications, Future Directions” and “Machine Learning: Algorithms, Real-World Applications and Research Directions”. The highly cited papers that are foundation texts always explore core concepts, techniques and applications in ML/DL for cybersecurity and, thus, contribute to how research should be conducted. Their influence shows that extensive, well-recorded research is contagious in making improvements across various fields.
The cybersecurity and ML DL research is interdisciplinary, based on the analysis discussed in this paper. Finally, it is demonstrated how innovative approaches for countering complex threats, such as artificial intelligence, blockchain, and adversarial learning, have been integrated into cybersecurity strategies. Cyber-attacks are consistently growing in scale and sophistication, and the use of ML/DL to power more adaptive and resilient systems is becoming all the more critical.
The direction of this study also points us towards an essential need for continued collaboration between researchers, organisations, and publishing platforms. Research efforts show promise for continued innovation, and the global distribution of those efforts indicates promise for continued innovation in emerging areas, like quantum-safe cryptography, autonomous cybersecurity systems, and ethical AI. However, the field also has challenges, including ensuring that research resources are accessible equitably and navigating the moral implications of deploying advanced ML/DL techniques in sensitive cybersecurity situations.
Finally, the results of this bibliometric analysis highlight the substantial advances in utilising ML and DL techniques for cybersecurity. This study identifies key contributors, trends and influential Public Space Research, laying a roadmap for future research and innovation. Continued global collaboration and investment in this field will be indispensable to keep a step ahead of upcoming threats and keep digital infrastructures safe and resilient around the globe.
6.1. Future Implications
The constant rise in publications might indicate that the research community anticipates these areas will remain significant. Projections to 2024, 2025, and beyond point to a further or even more considerable amount of publishing on these topics. This growth follows the increasing demand for cybersecurity worldwide, especially in AI, ML, and IoT development.
6.2. Practical Implications
As a direct result of this bibliometric analysis, new insights offer practical value to practitioners, policymakers, and stakeholders who aim to improve their cybersecurity strategies with ML and DL methods. The study findings serve as a guide for policymakers to implement ML-driven cybersecurity solutions in the cybersecurity infrastructure.
This study shows 114 countries participated, indicating ML/DL expertise and solutions available to address local situations. The global research perspective presents finance managers, healthcare providers, and critical infrastructure operators with the opportunity to elevate their performance by studying front-running institution methodologies, especially in fields such as real-time intrusion detection, malware categorisation, and adversarial protection. Insights from this research enable organisations to develop internal AI systems better while building up their workforce capabilities through data science education, security analyst training, and implementing broad, sophisticated security approaches fit for digitalisation.
The interdisciplinary character of cybersecurity research supports policy creation and the development of regulations that integrate technology, legal standards, and ethical practices. Modern AI architectural frameworks and blockchain security approaches require standardised guidelines and frameworks for protecting automated security operations data while preserving privacy and ensuring responsibility. Governments should team up with academic institutions, including those institutions from the study’s top rankings, to establish policies that promote responsible innovation through evidence-based methods. The advancement of adversarial ML requires strict protocols to validate AI-driven cybersecurity tools because these measures must ensure transparent operation alongside resistance to manipulations while maintaining fairness. Additionally, the ML model required significant computational resources when processing multidimensional and vast data for cyberthreat detection. Policymakers who develop educated legislative guidelines and establish industry partnerships can rapidly turn innovative research into practical cybersecurity solutions for advanced online threats.
6.3. Study Limitations
This significant growth in publications in all these journals indicates a positive trend towards progress in the cybersecurity and ML/DL fields. However, the data do not indicate the degree of influence these publications have. For example, the focus could be on the sheer volume of published articles without considering the impact of citations, which would better indicate how these studies affect the field.