Detection of Hacker Intention Using Deep Packet Inspection
Abstract
1. Introduction
2. Related Work
- SYN (synchronize): packets that are used to begin a connection.
- ACK (acknowledgment): packets that are used to confirm receipt of data packets; also used for confirmation of initiation request and tear down requests.
- RST (reset): indicates that the connection is down or perhaps that the service is not accepting the requests.
- FIN (finish): signifies that the connection is being torn down. Both the sender and receiver send FIN packets for graceful termination of the connection.
- PSH (push): signifies that the incoming data should be passed to the application directly instead of being buffered.
- URG (urgent): signifies that the data carried by the packet should be processed immediately by the TCP stack.
- CWR (congestion window reduced) indicates the TCP segment has been received with the ECE flag set.
- ECE: signifies that TCP peer is Explicit Congestion Notification (ECN)-capable.
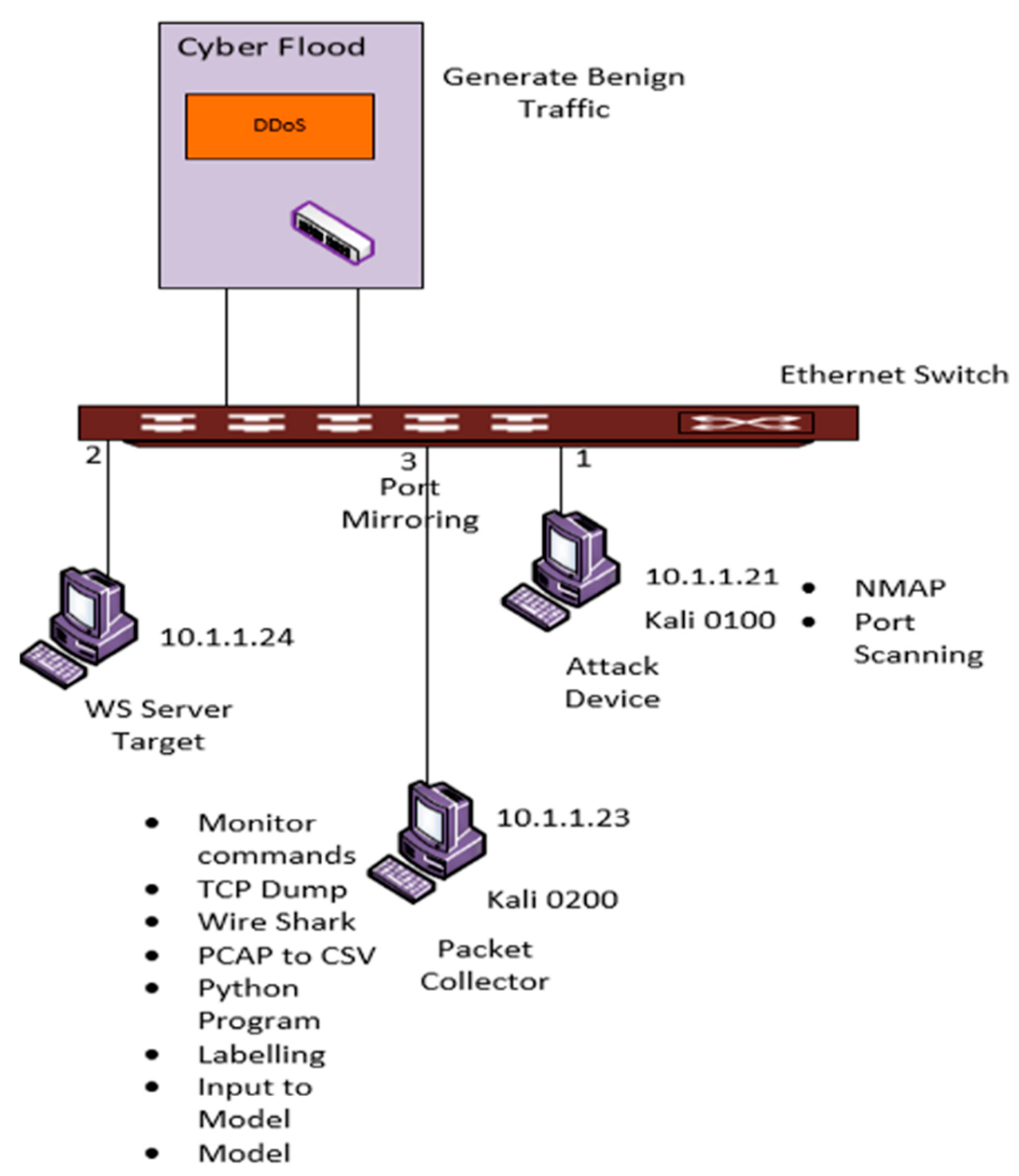
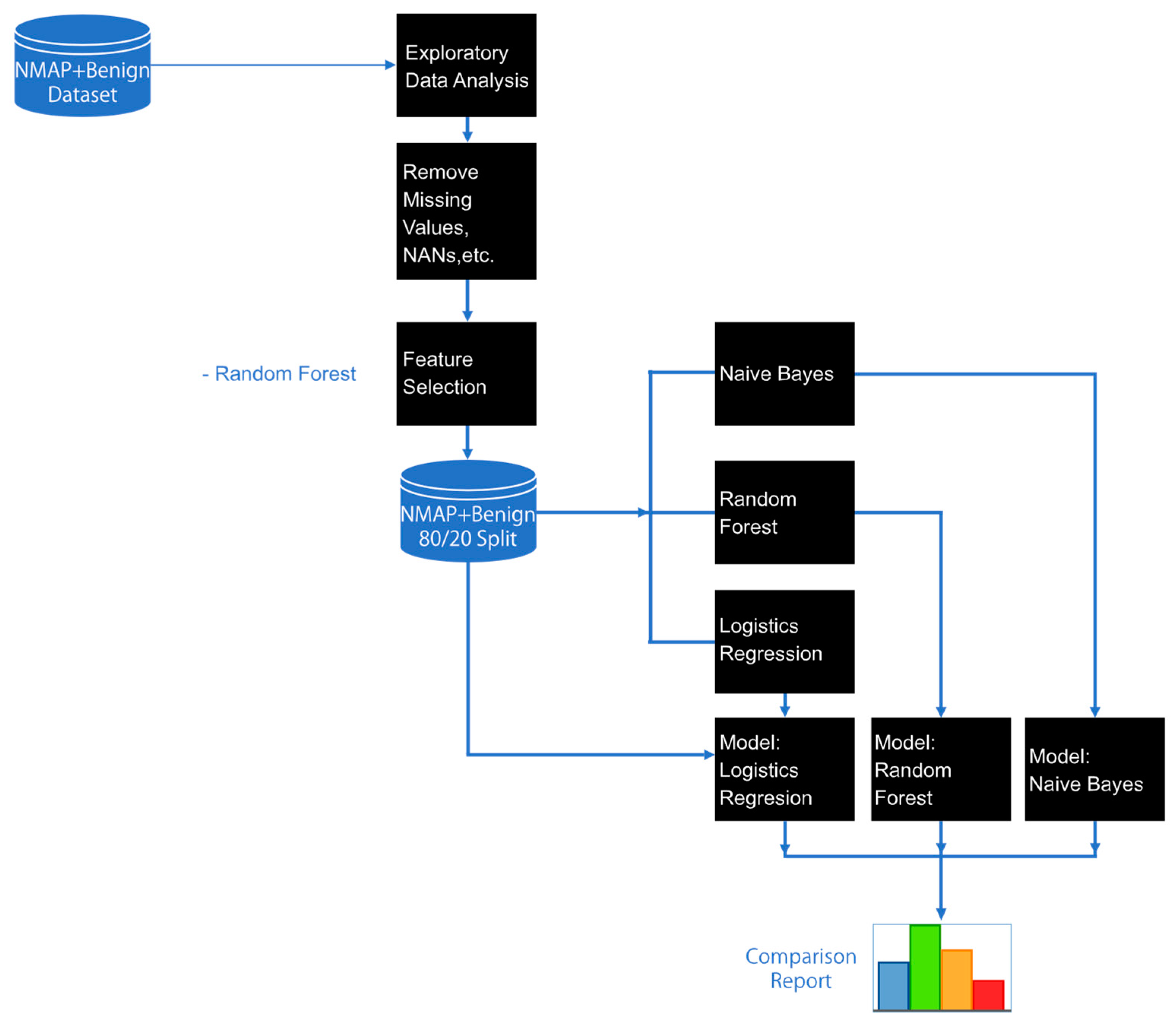
3. Methodology
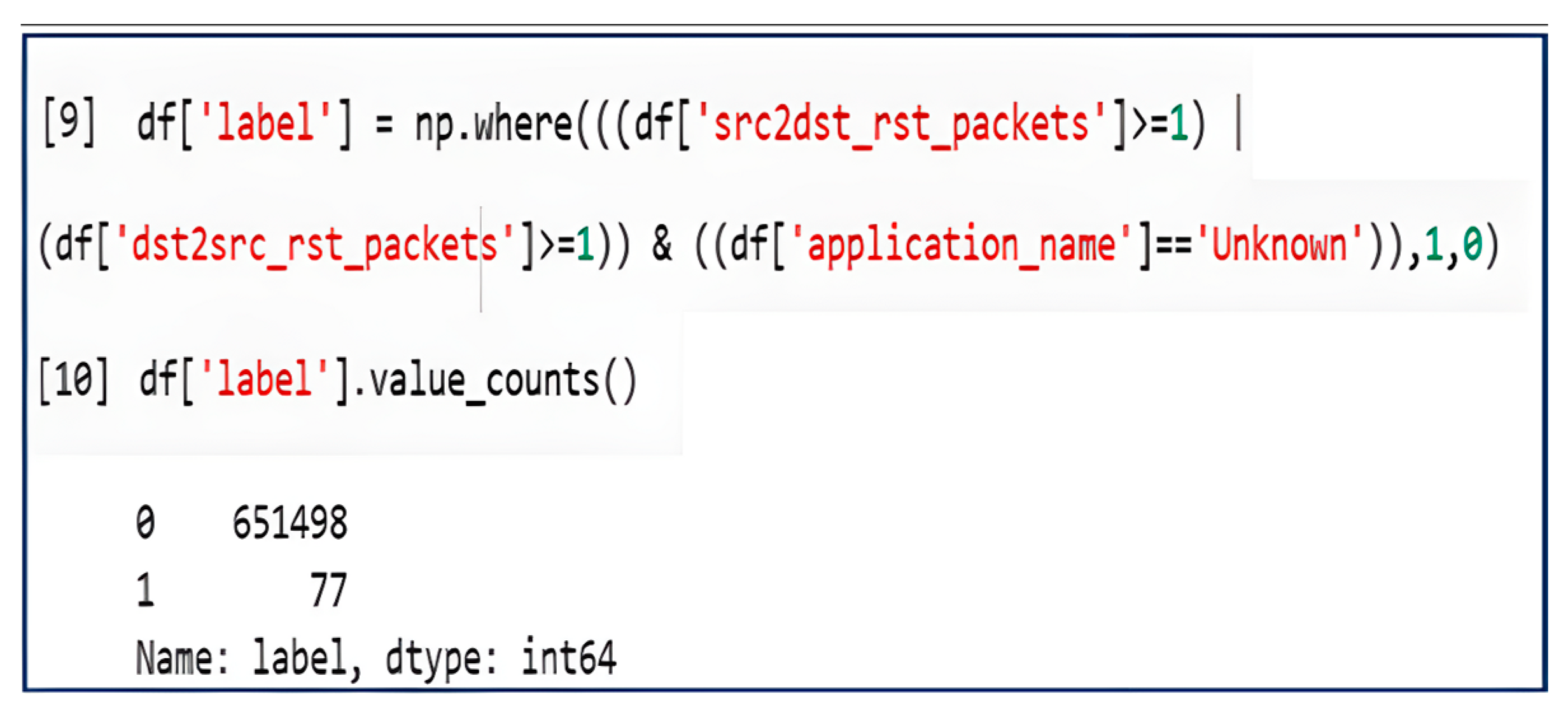
4. Results
5. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Engebretson, P. The Basics of Hacking and Penetration Testing; Syngress-Elsevier Publishing: Amsterdam, The Netherlands, 1974. [Google Scholar]
- Brook, C. What Is Deep Packet Inspection? And How It Really Works. Fortinet Digital Guardian. Available online: https://www.digitalguardian.com/blog/what-deep-packet-inspection-how-it-works-use-cases-dpi-and-more (accessed on 3 September 2024).
- Aouini, Z.; Pekar, A. NFStream: A flexible network data analysis framework. Comput. Netw. 2022, 204, 108719. [Google Scholar] [CrossRef]
- Deri, L.; Martinelli, M.; Cardigliano, A. nDPI: Open-source high speed packet inspection. In Proceedings of the 2014 International Wireless Communications and Mobile Computing Conference (IWCMC), Nicosia, Cyprus, 4–8 August 2014. [Google Scholar]
- Lyon, G. Nmap Official Website. Available online: https://nmap.org/ (accessed on 12 April 2023).
- Ann, E. Use Nmap to Discover Vulnerabilities, Launch DoS Attacks, and More. Null Byte. Available online: https://null-byte.wonderhowto.com/how-to/use-nmap-7-discover-vulnerabilities-launch-dos-attacks-and-more-0168788/ (accessed on 3 September 2024).
- Brice, Hannah. The Ultimate Guide to Cyber Deception Technology. LUPOVIS. Available online: https://www.lupovis.io/the-ultimate-guide-to-cyber-deception-technology/ (accessed on 12 August 2024).
- Kurose, J.F.; Ross, K.W. Computer Networking: A Top-Down Approach, 7th ed.; Pearson Publishing: Upper Saddle River, NJ, USA, 2017. [Google Scholar]
- Liao, S.; Zhou, C.; Zhao, Y.; Zhang, Z.; Zhang, C.; Gao, Y.; Zhong, G. A Comprehensive Detection Approach of Nmap: Principles, Rules and Experiments. In Proceedings of the 2020 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Chonqing, China, 29–30 October 2020; pp. 64–71. [Google Scholar]
- Apostol, I.; Preda, M.; Bica, I. IoT Botnet Anomaly Detection Using Unsupervised Deep Learning. Electronics 2021, 10, 1876. [Google Scholar] [CrossRef]
- Gill, M.S.; Lindskog, D.; Zavarsky, P. Profiling Network Traffic Behavior for the Purpose of Anomaly-Based Intrusion Detection. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 885–890. [Google Scholar]
- Fukushima, M.; Goto, S. Analysis of TCP Flags in Congested Network. IEICE Trans. Inf. Syst. 2000, E83-D, 996–1002. [Google Scholar] [CrossRef]
- Muraleedharan, N. Analysis of TCP flow data for traffic anomaly and scan detection. In Proceedings of the 16th IEEE International Conference on Networks, New Delhi, India, 12–14 December 2008; pp. 1–4. [Google Scholar]
- Balram, S.; Wiscy, M. Detection of TCP SYN Scanning Using Packet Counts and Neural Network. In Proceedings of the SITIS ‘08: Proceedings of the 2008 IEEE International Conference on Signal Image Technology and Internet Based Systems, Washington, DC, USA, 30 November–3 December 2008. [Google Scholar]
- Cao, D. Understanding TCP Flags SYN ACK RST FIN URG PSH. Available online: https://www.howtouselinux.com/post/tcp-flags (accessed on 3 September 2024).
- Bhuyan, M.H.; Bhattacharyya, D.K.; Kalita, J.K. AOCD: An Adaptive Outlier Based Coordinated Scan Detection Approach. Int. J. Netw. Secur. 2012, 14, 339–351. [Google Scholar]
- SECURE Center, Network Lab Setup Diagram, Prairie View A&M University. Available online: http://pvamu1.s3-website-us-east-1.amazonaws.com/ (accessed on 3 September 2024).
- Shafiq, M.; Tian, Z.; Sun, Y.; Du, X. Selection of effective machine learning algorithm and Bot-IoT attacks traffic classification for internet of things in smart city. Future Gener. Comput. Syst. 2020, 107, 433–442. [Google Scholar] [CrossRef]
- Shaukat, K.; Luo, S.; Varadharajan, V.; Hameed, I.A.; Xu, M. A Survey on Machine Learning Techniques for Cyber Security in the Last Decade. IEEE Access 2020, 8, 222310–222354. [Google Scholar] [CrossRef]
- Hanna, K.T. What is SYN Scanning. TechTarget. Available online: https://www.techtarget.com/searchnetworking/definition/SYN-scanning (accessed on 1 August 2023).
- Paliwal, A. The Ultimate Port Scanning Guide.: Part 3-Port Scans. SecOps Solution. Available online: https://www.secopsolution.com/blog/the-ultimate-port-scanning-guide (accessed on 3 September 2024).
- Huh, K. Surviving in a Random Forest with Imbalanced Datasets. Medium. Available online: https://medium.com/sfu-cspmp/surviving-in-a-random-forest-with-imbalanced-datasets-b98b963d52eb (accessed on 2 September 2024).
- Luo, H.; Pan, X.; Wang, Q.; Ye, S.; Qian, Y. Logistic Regression and Random Forest for Effective Imbalanced Classification. In Proceedings of the 2019 IEEE 43rd Annual Computer Software and Applications Conference (COMPSAC), Milwaukee, WI, USA, 15–19 July 2019; IEEE: Piscataway, NJ, USA, 2019; Volume 1, pp. 916–917. [Google Scholar] [CrossRef]
- RITP. Logistic Regression and Regularization: Avoiding Overfitting and Improving Generalization. Medium. Available online: https://medium.com/@rithpansanga/logistic-regression-and-regularization-avoiding-overfitting-and-improving-generalization-e9afdcddd09d (accessed on 2 September 2024).
- Rennie, J.D.; Shih, L.; Teevan, J.; Karger, D.R. Tackling the Poor Assumptions of Naive Bayes Text Classifiers. In Proceedings of the 20th International Conference on Machine Learning (ICML), Virtual, 21 August 2003; pp. 616–623. [Google Scholar]

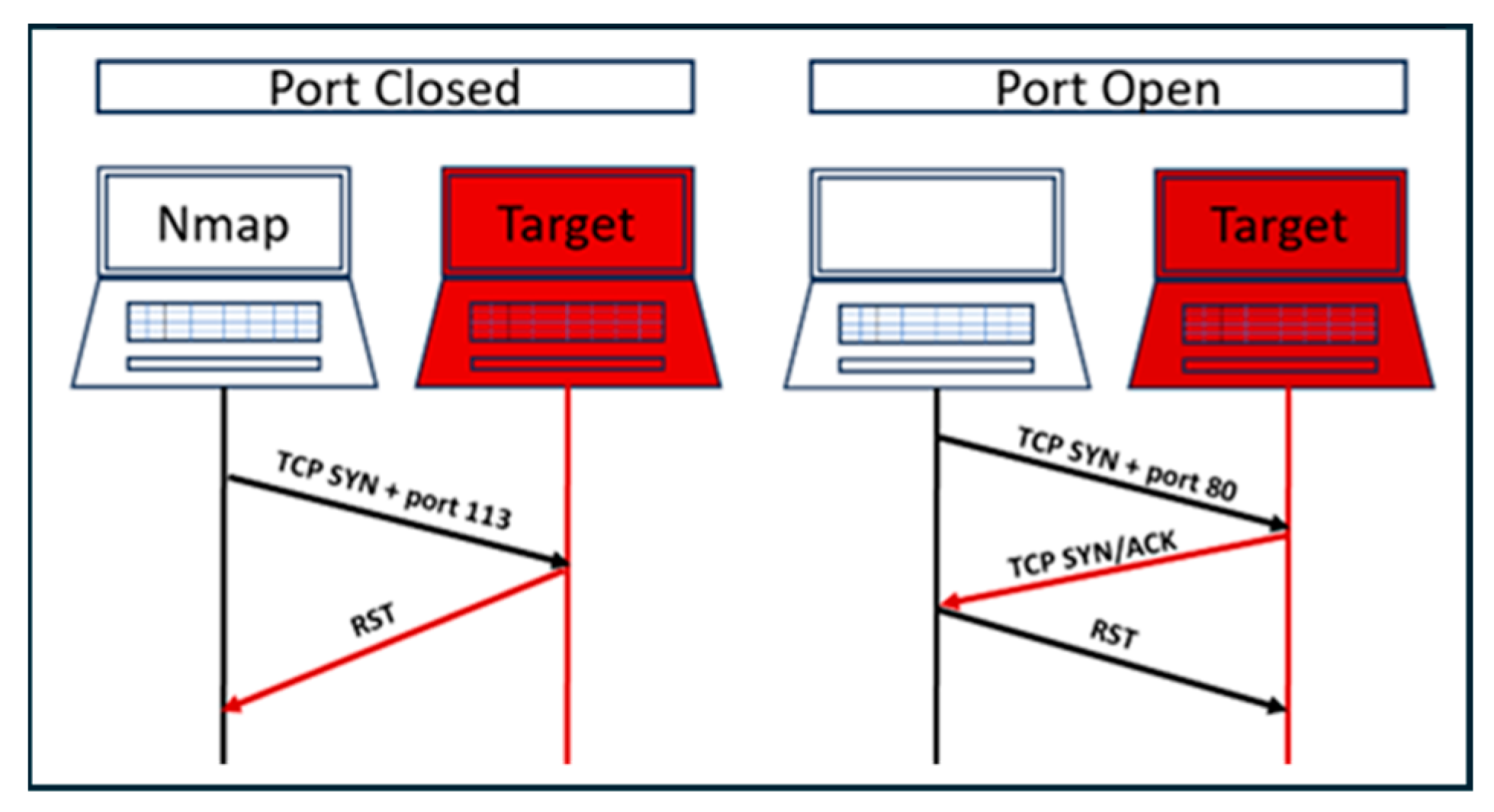



| Port Scan Technique | Protocol | TCP Flag | Target Reply (Open Port) | Target Reply (Closed Port) |
|---|---|---|---|---|
| TCP Connect | TCP | SYN | ACK | RST |
| SYN Scan | TCP | SYN | ACK | RST |
| SYN/ACK Scan | TCP | SYN/ACK | RST | RST |
| FIN Scan | TCP | FIN | No | RST |
| ACK Scan | TCP | ACK | No | RST |
| NULL Scan | TCP | No | No | RST |
| Probe Type | Nmap Command Issued | Short Description |
|---|---|---|
| Nmap host scan | sudo nmap 172.16.1.20 | Default method of scanning the host for identifying open ports. |
| Nmap ping scan | sudo nmap -sn 172.16.1.20 | Does Nmap host discovery to determine available hosts without port scan. |
| TCP SYN scan | sudo nmap -sS 172.16.1.20 | TCP packet sent with SYN flag set; after receiving response in the form of SYN-ACK, it disconnects by sending RST flag. Also known as stealth scan. |
| TCP connect scan | sudo nmap -sT 172.16.1.20 | Attempts TCP connection during the scan by issuing a TCP connect call. Default TCP scan when SYN scan is not an option. |
| TCP ACK scan | sudo nmap -sA 172.16.1.20 | Determines whether the port is filtered or unfiltered |
| TCP window scan | sudo nmap -sW 172.16.1.20 | Similar to ACK scan except it exploits implementation details of certain systems to differentiate open ports from closed ports. It also can determine if port is filtered. |
| UDP scan | sudo nmap -sU 172.16.1.20 | Used with UDP protocol to determine open, closed, filtered state of UDP ports |
| Null scan | sudo nmap -sN 172.16.1.20 | Scan with TCP header zero to determine state of port (open, closed, filtered). |
| FIN scan | sudo nmap -sF 172.16.1.20 | Scan with FIN flag set to determine state of port (open, closed, filtered). |
| XMAS scan | sudo nmap -sX 172.16.1.20 | Send packet with FIN, URG and PUSH flags set to determine state of port (open, closed, filtered). |
| Metrics | Logistic Regression (Class Weights) | Random Forest (Class Weights) | Gaussian Naïve Bayes (Class Weights) | Logistic Regression (SMOTE) | Random Forest (SMOTE) | Gaussian Naïve Bayes (SMOTE) |
|---|---|---|---|---|---|---|
| Accuracy | 1.0 | 1.0 | 0.977270 | 0.999985 | 1.0 | 0.996278 |
| Precision | 1.0 | 1.0 | 0.005039 | 0.882353 | 1.0 | 0.03 |
| Recall | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 |
| F1 Score | 1.0 | 1.0 | 0.010027 | 0.9375 | 1.0 | 0.058252 |
| AUC_ROC | 1.0 | 1.0 | 0.988634 | 0.999992 | 1.0 | 1.0 |
| Training Time | 24.253008 | 7.964047 | 0.110240 | 17.384840 | 19.179496 | 0.250027 |
| Pred Time | 0.202459 | 0.496398 | 0.015879 | 0.129446 | 0.506340 | 0.016541 |
| Detection Rate | 0.999885 | 0.999885 | 0.977155 | 0.999870 | 0.9999885 | 0.996163 |
| Memory Usage MB | 0.001340 | 0.091180 | 0.00143 | 0.001330 | 0.092680 | 0.001410 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Foreman, J.; Waters, W.L.; Kamhoua, C.A.; Hemida, A.H.A.; Acosta, J.C.; Dike, B.C. Detection of Hacker Intention Using Deep Packet Inspection. J. Cybersecur. Priv. 2024, 4, 794-804. https://doi.org/10.3390/jcp4040037
Foreman J, Waters WL, Kamhoua CA, Hemida AHA, Acosta JC, Dike BC. Detection of Hacker Intention Using Deep Packet Inspection. Journal of Cybersecurity and Privacy. 2024; 4(4):794-804. https://doi.org/10.3390/jcp4040037
Chicago/Turabian StyleForeman, Justin, Willie L. Waters, Charles A. Kamhoua, Ahmed H. Anwar Hemida, Jaime C. Acosta, and Blessing C. Dike. 2024. "Detection of Hacker Intention Using Deep Packet Inspection" Journal of Cybersecurity and Privacy 4, no. 4: 794-804. https://doi.org/10.3390/jcp4040037
APA StyleForeman, J., Waters, W. L., Kamhoua, C. A., Hemida, A. H. A., Acosta, J. C., & Dike, B. C. (2024). Detection of Hacker Intention Using Deep Packet Inspection. Journal of Cybersecurity and Privacy, 4(4), 794-804. https://doi.org/10.3390/jcp4040037






