Security in Cloud-Native Services: A Survey
Abstract
:1. Introduction
- Container [43] and Microservice [44] Security: This involves securing the containerized components, such as Docker containers, used in cloud-native applications. It includes measures like vulnerability scanning, secure container image management, and runtime protection to mitigate container-specific risks, such as container escape attacks or compromised container images. Furthermore, security in cloud-native services considers the security of individual microservices and their interactions. This includes securing communication channels between microservices, implementing access controls and authentication mechanisms for inter-service communication, and ensuring proper authorization and data protection between microservices.
- Orchestration Platform Security [45]: Security considerations extend to the orchestration platforms used in cloud-native environments, such as Kubernetes. This involves securing the Kubernetes control plane, implementing secure configuration practices, and protecting critical components like the etcd data store. It also includes securing container orchestration and deployment processes to prevent unauthorized access or unauthorized changes to deployments.
- DevSecOps Practices [46]: Security in cloud-native services embraces the integration of security practices throughout the development, deployment, and operations lifecycle. It emphasizes embedding security as an integral part of the development process and implementing security automation, Continuous Security Testing, and security monitoring as part of the DevSecOps approach.
- It is the first survey that is dedicated to exploring security in cloud-native services.
- It serves as a uniquely structured mapping study that maps the key aspects of security in cloud-native services to the corresponding features, and these features to numerous contemporary solutions.
- It includes the identification of various candidate open-source technologies that are capable of supporting the realization of each explored solution.
- It showcases how these solutions can work together in order to establish each corresponding feature.
2. Challenges for Security in Cloud-Native Services
- Malware Attacks [51]: The distributed nature of cloud-native services makes them vulnerable to malware attacks. Malicious software can infiltrate one part of the infrastructure and spread across the interconnected components, potentially causing data breaches, unauthorized access, or disruption of services. Additionally, malware can be designed to exploit specific weaknesses in cloud-native architectures, compromising the security and integrity of the entire system.
- Man-in-the-Middle (MITM) Attacks [52]: The distributed nature of cloud-native services also increases the risk of Man-in-the-Middle attacks. In such attacks, an attacker intercepts and alters the communication between two parties without their knowledge. This can lead to data leakage, unauthorized access, or manipulation of sensitive information. MITM attacks can exploit vulnerabilities in communication channels, weak encryption protocols, or compromised certificates.
- DDoS Attacks [53]: Cloud-native services are also susceptible to Distributed Denial of Service (DDoS) attacks, where a large number of compromised devices flood the network or services with excessive traffic, overwhelming the infrastructure and causing service disruptions. These attacks, which are also referred to as Cloud Zombie attacks [54], can be devastating for cloud-native services as they rely heavily on network connectivity and availability [55]. Furthermore, there have been certain variations of this type of attack that are designed to exploit the autoscaling capabilities of cloud environments [56]. These variations include Yo-Yo attacks [57], which rely on producing periodic bursts of traffic to oscillate the auto-scaling system between scale-out and scale-in status inducing economic loss to the tenant.
3. Key Features for Security in Cloud-Native Services
- Strong Access Controls [67]: Implementing strict access controls, including authentication, role-based access control, and least privilege principles helps prevent unauthorized access and reduces the impact of potential breaches. Strong access controls are crucial in cloud-native services to ensure the security, confidentiality, and integrity of data and resources. Access controls govern the authentication and authorization processes, determining who can access specific resources and what actions they can perform. Here are the key reasons why strong access controls are important in cloud-native services:
- Network Segmentation [68]: Network segmentation is a security practice that involves dividing a network into smaller, isolated segments to enhance the security and control of cloud-native services. Each segment, known as a network zone or subnet, contains a specific set of resources with defined access controls. Properly segmenting the cloud-native infrastructure into isolated networks and subnets can limit the lateral movement of attackers and contain the impact of potential breaches.
- Data Encryption [69]: Ensuring that data are encrypted both at rest and in transit helps protect sensitive information from unauthorized access. Data encryption plays a vital role in ensuring the security and privacy of data in cloud-native services. As organizations increasingly adopt cloud computing and migrate their infrastructure and applications to the cloud, the need for robust data protection mechanisms becomes even more critical.
- Secure Communication [70]: Utilizing secure communication protocols, such as HTTPS, and regularly updating cryptographic libraries and certificates enhances the integrity of data transfers. Secure communication in cloud-native services involves implementing measures to protect data and ensure the confidentiality, integrity, and authenticity of information exchanged between components within the cloud-native environment.
- Continuous Monitoring [71] and Intrusion Detection [72]: Employing robust monitoring and intrusion detection systems enables the early detection of potential threats, allowing for timely response and mitigation. This includes monitoring network traffic, analyzing log data, and leveraging threat intelligence to identify and respond to suspicious activities. Monitoring the security of dynamically scaling cloud-native services is essential but can be challenging. The increased number of instances, constant changes in the infrastructure, and complex network connections make it difficult to maintain visibility and detect potential security incidents. Implementing robust security monitoring tools and practices, such as centralized logging, real-time threat detection, and anomaly detection, can help identify security breaches and enable prompt incident response.
- Disaster Recovery [73], Incident Response [74], and Data Backup [75]: Establishing comprehensive disaster recovery plans and incident response procedures ensures that organizations can quickly recover from cybersecurity incidents and minimize their impact on operations. Regularly testing and updating these plans is crucial to maintaining their effectiveness. Furthermore, cloud-native services should have regular backup schedules, reliable backup storage solutions, and well-documented recovery procedures.
- Process Automation [76]: Process automation is essential for enhancing cybersecurity in cloud-native services. It reduces human error, ensures consistency, and standardizes security practices. Automation enables quick detection and response to security events, supports scalability [77], and facilitates continuous compliance. It also integrates threat intelligence for proactive threat hunting and faster incident response. Overall, automation strengthens security, protects data, and mitigates risks in the dynamic cloud-native environment. As such, in the context of facilitating secure cloud-native services, process automation refers to areas such as service orchestration, mitigation of incidents, security management, security checks, and static application testing.
- Vulnerability Management [78]: With the dynamic nature of cloud-native environments, vulnerability management becomes complex. Traditional vulnerability management practices may not be sufficient due to the large number of instances and rapid deployment cycles. Identifying and patching vulnerabilities in a timely manner becomes crucial to preventing potential exploits. Continuous vulnerability scanning, automated patch management [79], and integration with security tools and processes can help address this challenge.
- Configuration Management [80]: Cloud-native services rely heavily on configurations that define their behavior and security settings. However, managing and enforcing consistent configurations can be challenging in a dynamic and scalable environment. Configuration drift, where instances deviate from their desired configurations over time, can lead to security vulnerabilities. Implementing configuration management tools and practices that automate configuration enforcement and regularly verify compliance can help mitigate this challenge.
- Continuous Security Testing [81]: Regular security testing [82], including vulnerability assessments, penetration testing, and security code reviews, should be integrated into the development lifecycle of cloud-native services. Adopting a DevSecOps approach, where security is incorporated throughout the software development and deployment processes, helps identify and address vulnerabilities early on and ensures that security measures are continuously tested and validated.
4. Enabling Technologies for Cybersecurity in Cloud-Native Services
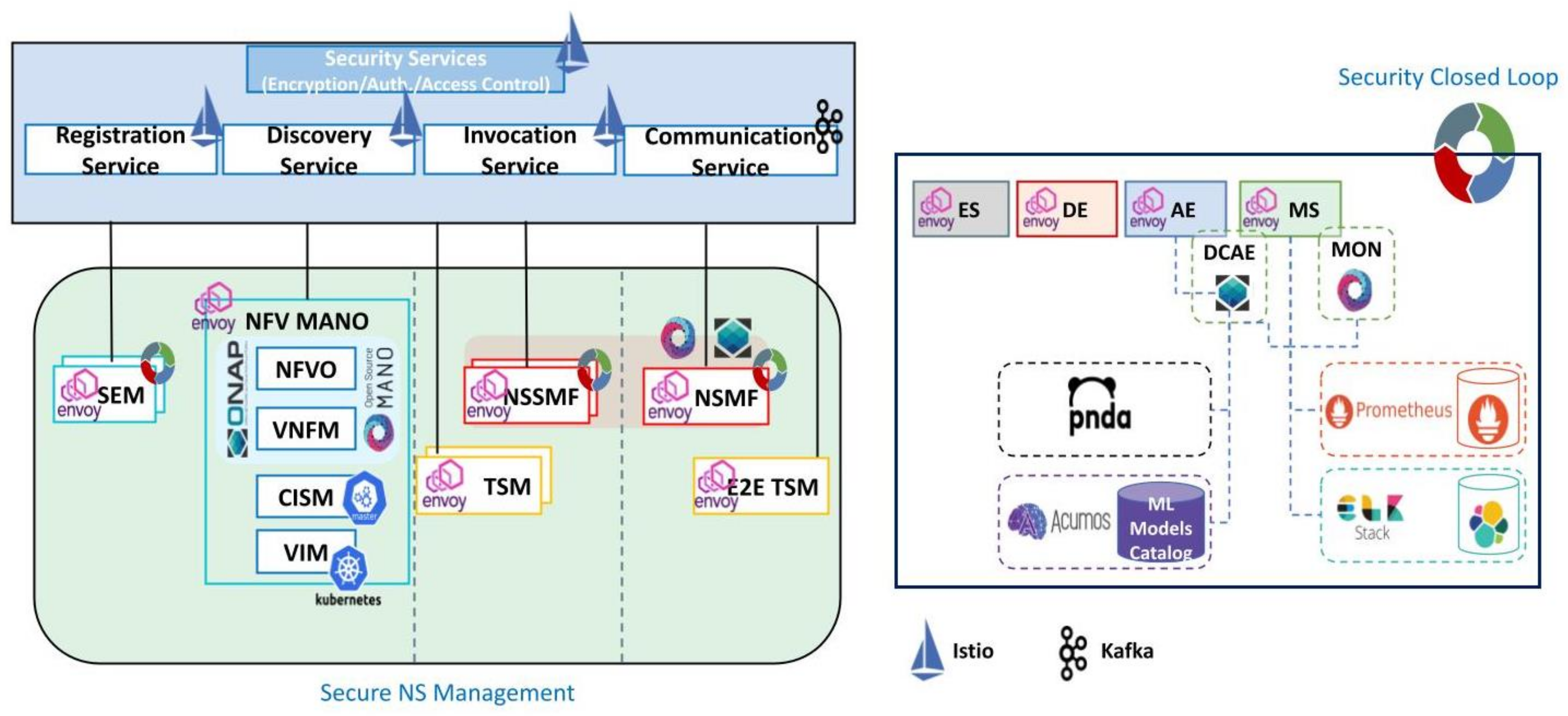
4.1. Zero-Touch Network and Service Management (ZSM)
- Automated Provisioning: It focuses on automating the provisioning process, starting from the initial setup of network devices and services. It involves automating the configuration, deployment, and activation of network resources and services without the need for manual intervention. Automated provisioning ensures consistent and reliable deployment, reducing the potential for human errors and misconfigurations.
- Service Orchestration: It emphasizes the orchestration of services across the entire network infrastructure. It involves automated coordination and management of various network functions and services, ensuring seamless integration and interoperability between different components. Service orchestration helps optimize resource utilization, enhance service delivery, and enable efficient scaling and elastic provisioning of services.
- Automated Operations and Maintenance: It promotes automation in ongoing operations and maintenance tasks. This includes automating routine management tasks, such as monitoring, performance management, fault detection, and troubleshooting. By automating these tasks, organizations can reduce manual effort, improve operational efficiency, and respond quickly to network incidents or performance issues.
- Closed-Loop Automation: It involves closed-loop automation, where automated processes continuously monitor the network, collect data, analyze it, and take proactive actions based on predefined policies and rules. Closed-loop automation enables self-healing capabilities, where network issues or service degradation can be automatically identified and remediated without human intervention.
- Analytics and Intelligence: It leverages analytics and intelligence to gain insights from network data and make data-driven decisions. By applying machine learning and artificial intelligence techniques, organizations can analyze network performance, user behavior, and security data to optimize resource allocation, detect anomalies, and enhance overall network operations and security.
- Security and Compliance: It includes incorporating security and compliance measures throughout the network and service management lifecycle. This involves integrating security controls, such as access controls, encryption, and threat detection into automated processes. It also ensures compliance with relevant regulations and standards throughout the management and operation of network services.
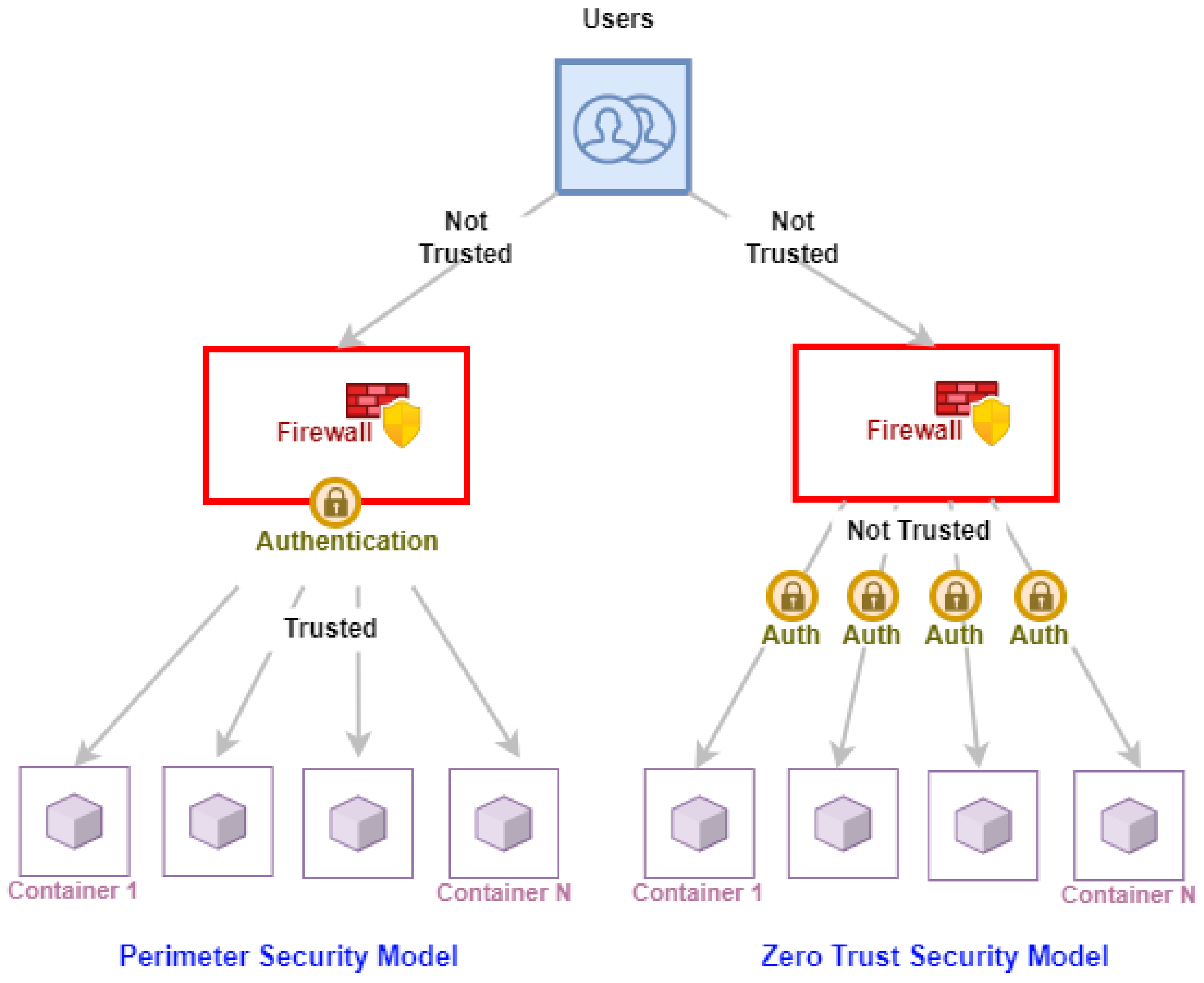
4.2. Zero-Trust Architecture (ZTA)
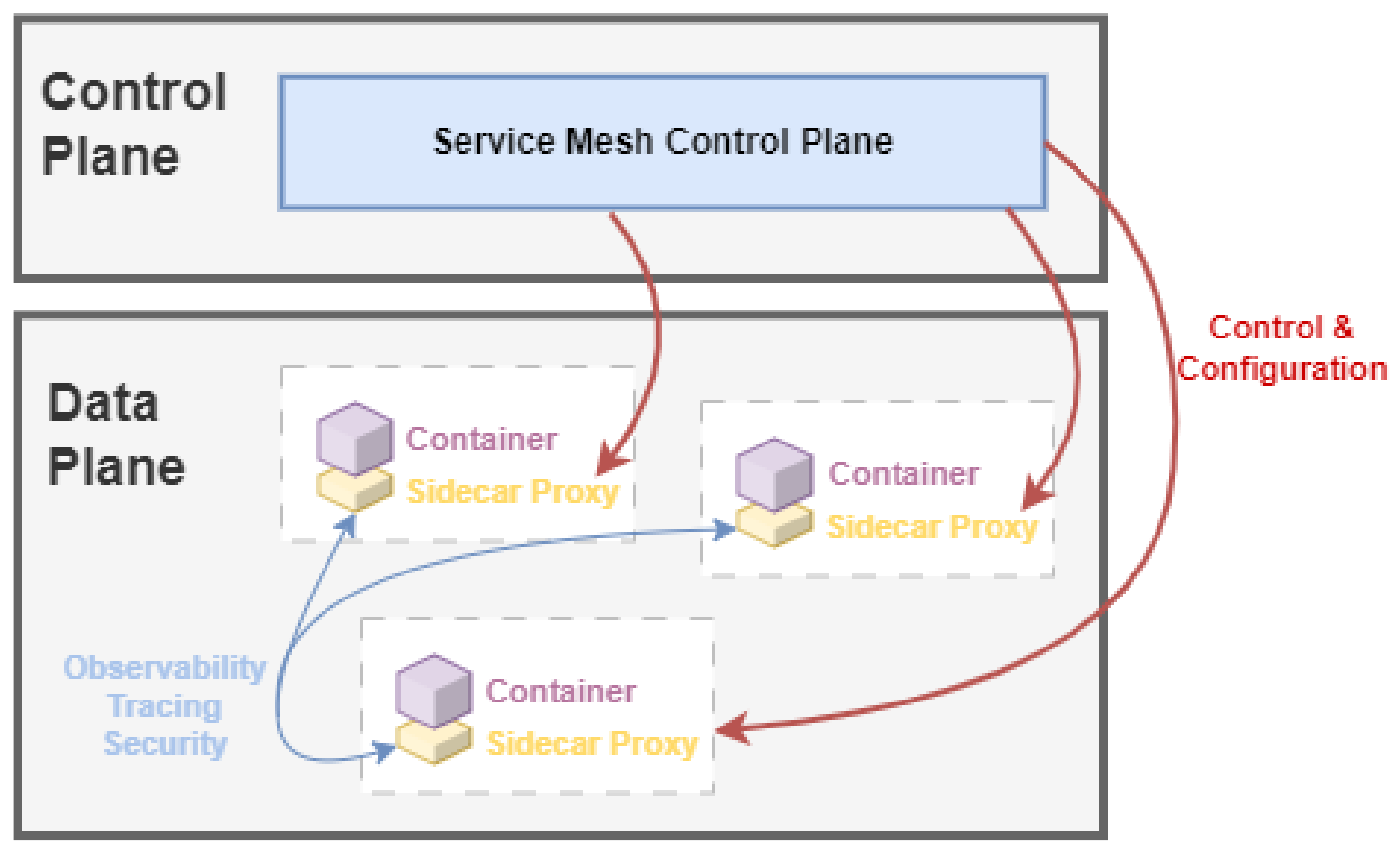
4.3. Service Mesh
- Service Registry and discovery: Mechanisms used to facilitate the process of discovery and registry of new components and services.
- Load balancing: The ability to balance network traffic depending on aspects such as latency, infrastructure, and health status.
- Fault tolerance: The ability to redirect requests to an alternate instance when the original is degraded or not available.
- Traffic monitoring: The ability to monitor all the network traffic and key metrics between the mesh of microservices.
- Encryption, Authentication, and Access Control: The possibility of dynamically encrypting the network communication on the fly as well as the possibility to authorize and authenticate network communication between services.
4.4. Native AI and Security as a Service (SECaaS)
5. Autonomic and Cognitive Security Management
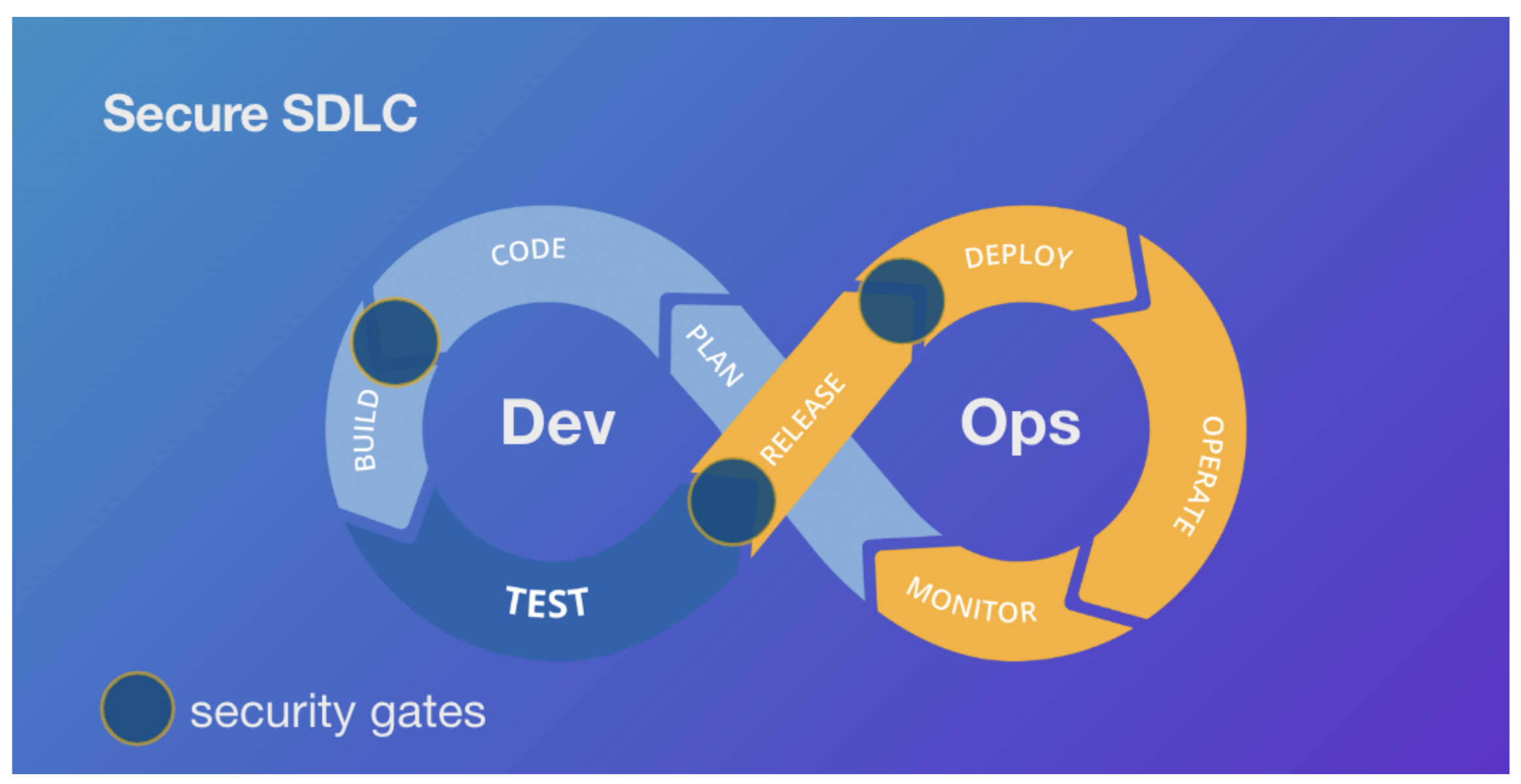
6. Secure Software Development Lifecycle (SDLC)
- Physical attack surface [126]: This includes all the physical devices, such as servers, laptops, smartphones, routers, and IoT devices, that an attacker could target to gain unauthorized access.
- Network attack surface [127]: This includes all the network infrastructure, such as firewalls, routers, switches, and gateways, that an attacker could target to penetrate the organization’s network and access its data and systems.
- Software attack surface [128]: This includes all the software components, such as applications, operating systems, and databases, that an attacker could target to exploit a vulnerability and gain unauthorized access.
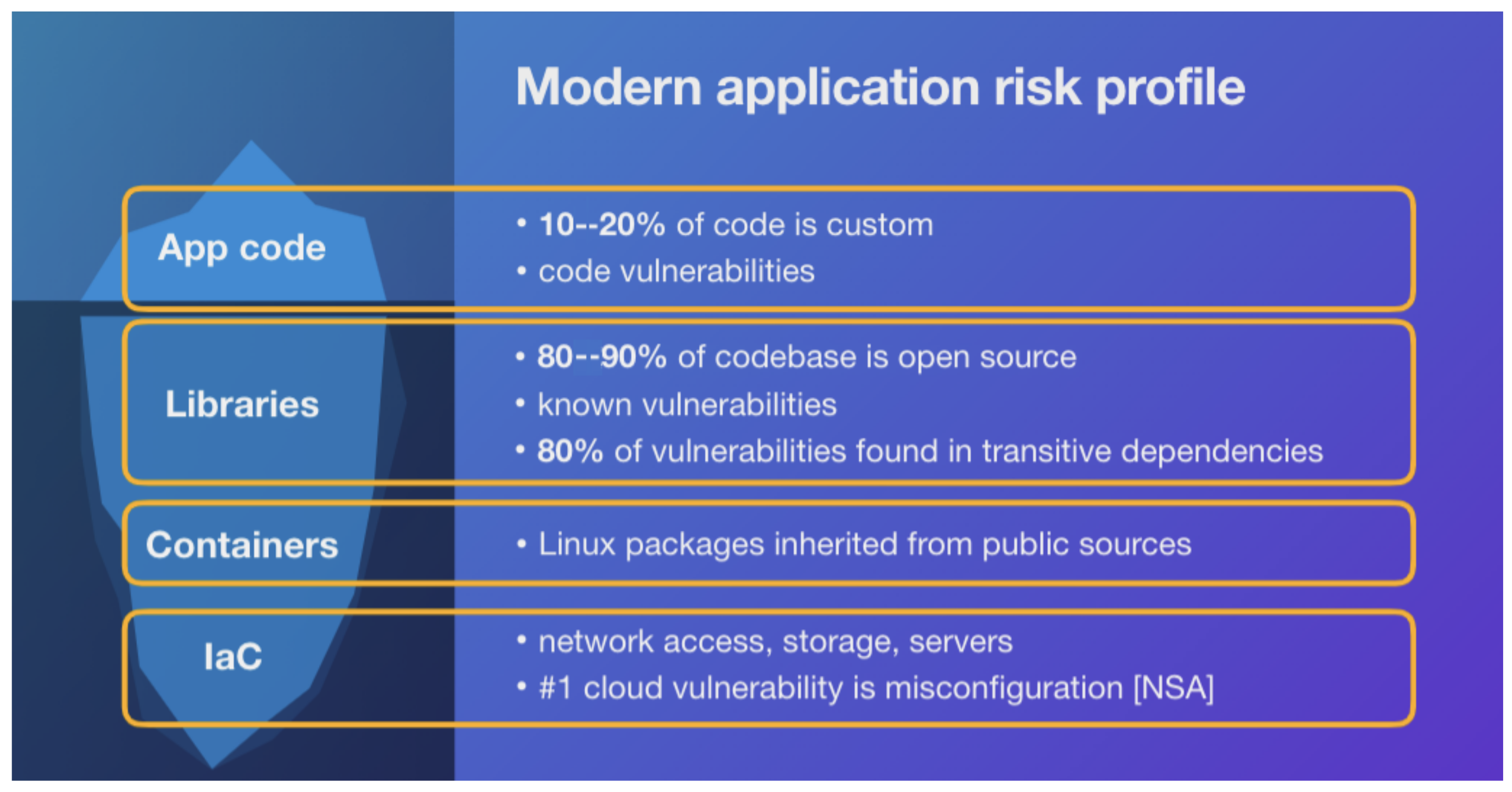
- Application code [130]: custom code may only make up to 10–20% of the codebase. Any code vulnerabilities must be identified.
- Libraries [36]: Open source code typically represents up to 80–90% of the code base, whereas open-source software can offer many benefits, such as rapid development and cost-effectiveness, and can also introduce risks. Using open-source code exposes the application to the vulnerabilities that exist in open-source libraries, which attackers can exploit.
- Containers [131]: Linux packages inherited from public sources. Cloud-native applications rely on many third-party services, which can also introduce security risks. These third-party services may have vulnerabilities or may not have adequate security controls in place. The use of microservices and container technologies in cloud-native applications has increased the complexity of the codebase. This complexity can lead to security gaps, making identifying vulnerabilities and security risks difficult.
- Infrastructure-as-Code (IaC) [132]: with IaC, developers use code to describe the desired configuration of their infrastructure, including servers, networks, storage, and other resources, and deploy the infrastructure automatically using tools like AWS Cloudformation, Terraform, or Puppet.
6.1. Security Risk Profiling and Mitigation
- The principle of least privilege: To ensure that each user has only the minimum access required to perform their tasks.
- Define who is authorized to run the scripts and who is not.
- Limit the permissions of authorized IaC users to what is necessary to perform their tasks.
- IaC scripts should ensure that the permissions granted to the various resources created are limited to what is required.
- Network segmentation: The resources and their related dependencies are all secured within a private subnet.
- Data encryption: A technique used to authenticate and encrypt data sent between two services. Mutual Transport Layer Security (mTLS) ensures that traffic is secure and trusted in both directions between a client and server, providing an additional layer of security for users who log in to a network or applications.
6.2. Shift Left and Static Testing Techniques for Enhancing Security
6.3. Continuous Security, Data Preserving, and Data Compliance
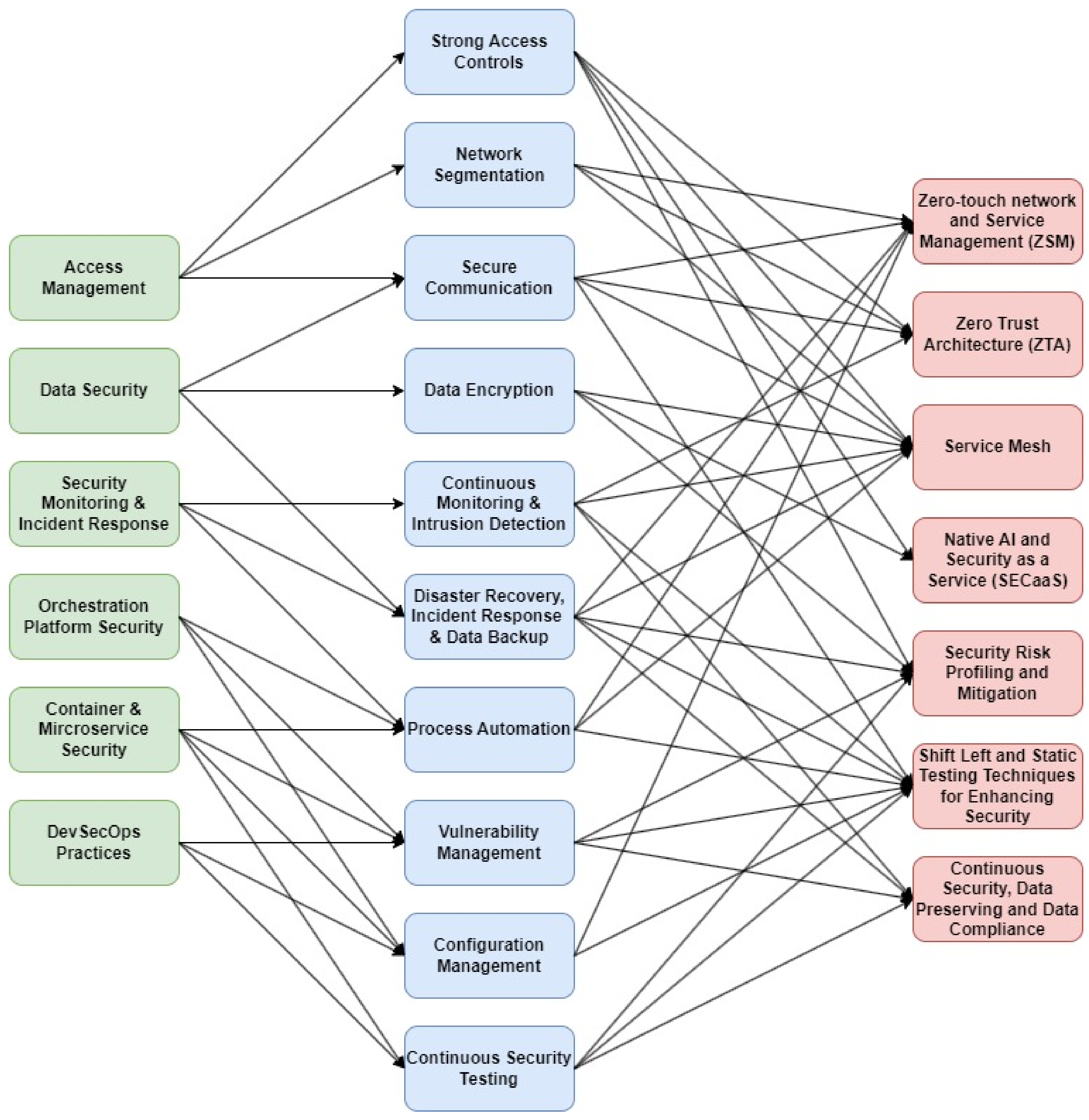
7. Solution Synergy
7.1. Strong Access Controls
7.2. Network Segmentation
7.3. Secure Communications
7.4. Data Encryption
7.5. Continuous Monitoring and Intrusion Detection
7.6. Disaster Recovery, Incident Response, and Data Backup
7.7. Process Automation
7.8. Vulnerability Management
7.9. Configuration Management
7.10. Continuous Security Testing
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Gannon, D.; Barga, R.; Sundaresan, N. Cloud-native applications. IEEE Cloud Comput. 2017, 4, 16–21. [Google Scholar] [CrossRef]
- Huang, S.Y.; Chen, C.Y.; Chen, J.Y.; Chao, H.C. A Survey on Resource Management for Cloud Native Mobile Computing: Opportunities and Challenges. Symmetry 2023, 15, 538. [Google Scholar] [CrossRef]
- Azad, N.; Hyrynsalmi, S. DevOps critical succes factors—A systematic literature review. Inf. Softw. Technol. 2023, 157, 107150. [Google Scholar] [CrossRef]
- Thatikonda, V.K. Beyond the Buzz: A Journey Through CI/CD Principles and Best Practices. Eur. J. Theor. Appl. Sci. 2023, 1, 334–340. [Google Scholar] [CrossRef]
- Kumar, M.; Mishra, S.; Lathar, N.; Singh, P. Infrastructure as Code (IaC): Insights on Various Platforms. In Sentiment Analysis and Deep Learning: Proceedings of ICSADL 2022; Springer Nature Singapore: Singapore, 2023; pp. 439–449. [Google Scholar]
- Alshuqayran, N.; Ali, N.; Evans, R. A systematic mapping study in microservice architecture. In Proceedings of the 2016 IEEE 9th International Conference on Service-Oriented Computing and Applications (SOCA), Macau, China, 4–6 November 2016; pp. 44–51. [Google Scholar]
- Ramu, V. Performance Impact of Microservices Architecture. Rev. Contemp. Sci. Acad. Stud. 2023, 3. [Google Scholar] [CrossRef]
- Kosińska, J.; Zieliński, K. Enhancement of Cloud-native applications with Autonomic Features. J. Grid Comput. 2023, 21, 44. [Google Scholar] [CrossRef]
- Poulton, N. The Kubernetes Book; Nigel Poulton Ltd.: Cheshire, UK, 2023. [Google Scholar]
- Senjab, K.; Abbas, S.; Ahmed, N.; ur Rehman Khan, A. A survey of Kubernetes scheduling algorithms. J. Cloud Comput. 2023, 12, 1–26. [Google Scholar] [CrossRef]
- Taleb, T.; Boudi, A.; Rosa, L.; Cordeiro, L.; Theodoropoulos, T.; Tserpes, K.; Dazzi, P.; Protopsaltis, A.I.; Li, R. Toward Supporting XR Services: Architecture and Enablers. IEEE Internet Things J. 2022, 10, 3567–3586. [Google Scholar] [CrossRef]
- Theodoropoulos, T.; Makris, A.; Violos, J.; Tserpes, K. An Automated Pipeline for Advanced Fault Tolerance in Edge Computing Infrastructures. In Proceedings of the 2nd Workshop on Flexible Resource and Application Management on the Edge, Minneapolis, MN, USA, 1 July 2022; pp. 19–24. [Google Scholar]
- Makris, A.; Psomakelis, E.; Theodoropoulos, T.; Tserpes, K. Towards a Distributed Storage Framework for Edge Computing Infrastructures. In Proceedings of the 2nd Workshop on Flexible Resource and Application Management on the Edge, Minneapolis, MN, USA, 1 July 2022; pp. 9–14. [Google Scholar]
- Logeshwaran, J.; Ramesh, G.; Aravindarajan, V. A secured database monitoring method to improve data backup and recovery operations in cloud computing. BOHR Int. J. Comput. Sci. 2023, 2, 1–7. [Google Scholar]
- Theodoropoulos, T.; Makris, A.; Psomakelis, E.; Carlini, E.; Mordacchini, M.; Dazzi, P.; Tserpes, K. GNOSIS: Proactive Image Placement Using Graph Neural Networks & Deep Reinforcement Learning. In Proceedings of the 2023 IEEE 16th International Conference on Cloud Computing (CLOUD), Chicago, IL, USA, 4 July 2023; pp. 120–128. [Google Scholar]
- Benzaid, C.; Boukhalfa, M.; Taleb, T. Robust Self-Protection Against Application-Layer (D)DoS Attacks in SDN Environment. In Proceedings of the 2020 IEEE Wireless Communications and Networking Conference (WCNC), Seoul, Korea, 25–28 May 2020; pp. 1–6. [Google Scholar]
- Javadpour, A.; Ja’fari, F.; Taleb, T.; Benzaid, C. Reinforcement Learning-based Slice Isolation Against DoS/DDoS Attacks in Beyond 5G Networks. IEEE Trans. Netw. Serv. Manag. 2023, 20, 3930–3946. [Google Scholar] [CrossRef]
- Theodoropoulos, T.; Makris, A.; Boudi, A.; Taleb, T.; Herzog, U.; Rosa, L.; Cordeiro, L.; Tserpes, K.; Spatafora, E.; Romussi, A.; et al. Cloud-based xr services: A survey on relevant challenges and enabling technologies. J. Netw. Netw. Appl. 2022, 2, 1–22. [Google Scholar] [CrossRef]
- Benzaid, C.; Taleb, T.; Song, J. AI-based Autonomic & Scalable Security Management Architecture for Secure Network Slicing in B5G. IEEE Netw. 2022, 36, 165–174. [Google Scholar] [CrossRef]
- Benzaid, C.; Taleb, T.; Phan, C.T.; Tselios, C.; Tsolis, G. Distributed AI-based Security for Massive Numbers of Network Slices in 5G & Beyond Mobile Systems. In Proceedings of the 2021 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), Porto, Portugal, 8–11 June 2021; pp. 401–406. [Google Scholar] [CrossRef]
- Alghofaili, Y.; Albattah, A.; Alrajeh, N.; Rassam, M.A.; Al-Rimy, B.A.S. Secure cloud infrastructure: A survey on issues, current solutions, and open challenges. Appl. Sci. 2021, 11, 9005. [Google Scholar] [CrossRef]
- Ali, M.; Khan, S.U.; Vasilakos, A.V. Security in cloud computing: Opportunities and challenges. Inf. Sci. 2015, 305, 357–383. [Google Scholar] [CrossRef]
- Tabrizchi, H.; Kuchaki Rafsanjani, M. A survey on security challenges in cloud computing: Issues, threats, and solutions. J. Supercomput. 2020, 76, 9493–9532. [Google Scholar] [CrossRef]
- Kumar, S.N.; Vajpayee, A. A survey on secure cloud: Security and privacy in cloud computing. Am. J. Syst. Softw. 2016, 4, 14–26. [Google Scholar]
- Younis, Y.A.; Kifayat, K. Secure cloud computing for critical infrastructure: A survey. Liverp. John Moores Univ. United Kingd. Tech. Rep. 2013, 1, 599–610. [Google Scholar]
- Shahzad, F. State-of-the-art survey on cloud computing security challenges, approaches and solutions. Procedia Comput. Sci. 2014, 37, 357–362. [Google Scholar] [CrossRef]
- Ramachandra, G.; Iftikhar, M.; Khan, F.A. A comprehensive survey on security in cloud computing. Procedia Comput. Sci. 2017, 110, 465–472. [Google Scholar] [CrossRef]
- Khan, M.A. A survey of security issues for cloud computing. J. Netw. Comput. Appl. 2016, 71, 11–29. [Google Scholar] [CrossRef]
- Sharma, S.; Gupta, G.; Laxmi, P. A survey on cloud security issues and techniques. arXiv 2014, arXiv:1403.5627. [Google Scholar]
- Khalil, I.M.; Khreishah, A.; Azeem, M. Cloud computing security: A survey. Computers 2014, 3, 1–35. [Google Scholar] [CrossRef]
- Singh, S.; Jeong, Y.S.; Park, J.H. A survey on cloud computing security: Issues, threats, and solutions. J. Netw. Comput. Appl. 2016, 75, 200–222. [Google Scholar] [CrossRef]
- Hussein, N.H.; Khalid, A. A survey of cloud computing security challenges and solutions. Int. J. Comput. Sci. Inf. Secur. 2016, 14, 52. [Google Scholar]
- Basu, S.; Bardhan, A.; Gupta, K.; Saha, P.; Pal, M.; Bose, M.; Basu, K.; Chaudhury, S.; Sarkar, P. Cloud computing security challenges & solutions—A survey. In Proceedings of the 2018 IEEE 8th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 8–10 January 2018; pp. 347–356. [Google Scholar]
- Parast, F.K.; Sindhav, C.; Nikam, S.; Yekta, H.I.; Kent, K.B.; Hakak, S. Cloud computing security: A survey of service-based models. Comput. Secur. 2022, 114, 102580. [Google Scholar] [CrossRef]
- Butt, U.A.; Amin, R.; Mehmood, M.; Aldabbas, H.; Alharbi, M.T.; Albaqami, N. Cloud security threats and solutions: A survey. Wirel. Pers. Commun. 2023, 128, 387–413. [Google Scholar] [CrossRef]
- Alonso, J.; Orue-Echevarria, L.; Casola, V.; Torre, A.I.; Huarte, M.; Osaba, E.; Lobo, J.L. Understanding the challenges and novel architectural models of multi-cloud native applications—A systematic literature review. J. Cloud Comput. 2023, 12, 1–34. [Google Scholar] [CrossRef]
- Wong, A.Y.; Chekole, E.G.; Ochoa, M.; Zhou, J. On the Security of Containers: Threat Modeling, Attack Analysis, and Mitigation Strategies. Comput. Secur. 2023, 128, 103140. [Google Scholar] [CrossRef]
- Karakaş, B. Others Enhancing Security in Communication Applications Deployed on Kubernetes: Best Practices and Service Mesh Analysis. 2023. Available online: https://aaltodoc.aalto.fi/handle/123456789/122929 (accessed on 15 August 2023).
- Indu, I.; Anand, P.R.; Bhaskar, V. Identity and access management in cloud environment: Mechanisms and challenges. Eng. Sci. Technol. Int. J. 2018, 21, 574–588. [Google Scholar] [CrossRef]
- Yang, P.; Xiong, N.; Ren, J. Data security and privacy protection for cloud storage: A survey. IEEE Access 2020, 8, 131723–131740. [Google Scholar] [CrossRef]
- Elsayed, M.; Zulkernine, M. Towards security monitoring for cloud analytic applications. In Proceedings of the 2018 IEEE 4th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing, (HPSC) and IEEE International Conference on Intelligent Data and Security (IDS), Omaha, NE, USA, 3–5 May 2018; pp. 69–78. [Google Scholar]
- Ozer, M.; Varlioglu, S.; Gonen, B.; Adewopo, V.; Elsayed, N.; Zengin, S. Cloud incident response: Challenges and opportunities. In Proceedings of the 2020 International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, NV, USA, 16–18 December 2020; pp. 49–54. [Google Scholar]
- Sultan, S.; Ahmad, I.; Dimitriou, T. Container security: Issues, challenges, and the road ahead. IEEE Access 2019, 7, 52976–52996. [Google Scholar] [CrossRef]
- Mateus-Coelho, N.; Cruz-Cunha, M.; Ferreira, L.G. Security in microservices architectures. Procedia Comput. Sci. 2021, 181, 1225–1236. [Google Scholar] [CrossRef]
- Islam, C.; Babar, M.A.; Nepal, S. Architecture-centric support for integrating security tools in a security orchestration platform. In Proceedings of the Software Architecture: 14th European Conference, ECSA 2020, L’Aquila, Italy, 14–18 September 2020; Proceedings 14. Springer: Berlin/Heidelberg, Germany, 2020; pp. 165–181. [Google Scholar]
- Zaydi, M.; Nassereddine, B. DevSecOps practices for an agile and secure it service management. J. Manag. Inf. Decis. Sci. 2020, 23, 134–149. [Google Scholar]
- Rahaman, M.S.; Islam, A.; Cerny, T.; Hutton, S. Static-Analysis-Based Solutions to Security Challenges in Cloud-Native Systems: Systematic Mapping Study. Sensors 2023, 23, 1755. [Google Scholar] [CrossRef]
- Cloud for Holography and Cross Reality (CHARITY). D2.1: Edge and Cloud Infrastructure Resource and Computational Continuum Orchestration System Report 2022. Available online: https://www.charity-project.eu/deliverables (accessed on 15 August 2023).
- Makris, A.; Boudi, A.; Coppola, M.; Cordeiro, L.; Corsini, M.; Dazzi, P.; Andilla, F.D.; Rozas, Y.G.; Kamarianakis, M.; Pateraki, M.; et al. Cloud for holography and augmented reality. In Proceedings of the 2021 IEEE 10th International Conference on Cloud Networking (CloudNet), Cookeville, TN, USA, 8–10 November 2021; pp. 118–126. [Google Scholar]
- Shah, Y.; Sengupta, S. A survey on Classification of Cyber-attacks on IoT and IIoT devices. In Proceedings of the 2020 11th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 28–31 October 2020; pp. 0406–0413. [Google Scholar] [CrossRef]
- Alenezi, M.N.; Alabdulrazzaq, H.; Alshaher, A.A.; Alkharang, M.M. Evolution of malware threats and techniques: A review. Int. J. Commun. Netw. Inf. Secur. 2020, 12, 326–337. [Google Scholar] [CrossRef]
- Conti, M.; Dragoni, N.; Lesyk, V. A survey of man in the middle attacks. IEEE Commun. Surv. Tutorials 2016, 18, 2027–2051. [Google Scholar] [CrossRef]
- Kumari, P.; Jain, A.K. A comprehensive study of DDoS attacks over IoT network and their countermeasures. Comput. Secur. 2023, 127, 103096. [Google Scholar] [CrossRef]
- Panchal, A.C.; Khadse, V.M.; Mahalle, P.N. Security issues in IIoT: A comprehensive survey of attacks on IIoT and its countermeasures. In Proceedings of the 2018 IEEE Global Conference on Wireless Computing and Networking (GCWCN), Lonavala, India, 23–24 November 2018; pp. 124–130. [Google Scholar]
- Bremler-Barr, A.; Brosh, E.; Sides, M. DDoS attack on cloud auto-scaling mechanisms. In Proceedings of the IEEE INFOCOM 2017-IEEE Conference on Computer Communications, Atlanta, GA, USA, 1–4 May 2017; pp. 1–9. [Google Scholar]
- Bremler-Barr, A.; Czeizler, M. Tandem Attack: DDoS Attack on Microservices Auto-scaling Mechanisms. In Proceedings of the IEEE INFOCOM 2023-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Hoboken, NJ, USA, 20 May 2023; pp. 1–2. [Google Scholar]
- Kashi, M.M.; Yazidi, A.; Haugerud, H. Mitigating Yo-Yo attacks on cloud auto-scaling. In Proceedings of the 2022 14th IFIP Wireless and Mobile Networking Conference (WMNC), Sousse, Tunisia, 17–19 October 2022; pp. 46–53. [Google Scholar] [CrossRef]
- Ur Rasool, R.; Wang, H.; Ashraf, U.; Ahmed, K.; Anwar, Z.; Rafique, W. A survey of link flooding attacks in software defined network ecosystems. J. Netw. Comput. Appl. 2020, 172, 102803. [Google Scholar] [CrossRef]
- Meier, R.; Tsankov, P.; Lenders, V.; Vanbever, L.; Vechev, M.T. NetHide: Secure and Practical Network Topology Obfuscation. In Proceedings of the USENIX Security Symposium, Baltimore, MD, USA, 15–17 August 2018. [Google Scholar]
- Kim, J.; Marin, E.; Conti, M.; Shin, S. EqualNet: A secure and practical defense for long-term network topology obfuscation. In Proceedings of the Network and Distributed Systems Security (NDSS) Symposium 2022, San Diego, CA, USA, 24–28 April 2022. [Google Scholar] [CrossRef]
- Trassare, S.T.; Beverly, R.; Alderson, D. A technique for network topology deception. In Proceedings of the MILCOM 2013—2013 IEEE Military Communications Conference, San Diego, CA, USA, 18–20 November 2013. [Google Scholar]
- Wang, Q.; Xiao, F.; Zhou, M.; Wang, Z.; Li, Q.; Li, Z. Linkbait: Active Link Obfuscation to Thwart. arXiv 2017, arXiv:1703.09521. [Google Scholar]
- Martin, A.; Raponi, S.; Combe, T.; Di Pietro, R. Docker ecosystem–vulnerability analysis. Comput. Commun. 2018, 122, 30–43. [Google Scholar] [CrossRef]
- Gruenbacher, A.; Arnold, S. AppArmor Technical Documentation. 2007. Available online: https://lkml.iu.edu/hypermail/linux/kernel/0706.1/0805/techdoc.pdf (accessed on 15 August 2023).
- McCarty, B. SELinux. 2005. Available online: https://www.oreilly.com/library/view/selinux/0596007167/ (accessed on 15 August 2023).
- Yee, G.O. Modeling and reducing the attack surface in software systems. In Proceedings of the 2019 IEEE/ACM 11th International Workshop on Modelling in Software Engineering (MiSE), Montreal, QC, Canada, 26–27 May 2019; pp. 55–62. [Google Scholar]
- Qiu, J.; Tian, Z.; Du, C.; Zuo, Q.; Su, S.; Fang, B. A survey on access control in the age of internet of things. IEEE Internet Things J. 2020, 7, 4682–4696. [Google Scholar] [CrossRef]
- Mhaskar, N.; Alabbad, M.; Khedri, R. A formal approach to network segmentation. Comput. Secur. 2021, 103, 102162. [Google Scholar] [CrossRef]
- Gupta, S.; Sacchetti, T.; Crispo, B. End-to-End Encryption for Securing Communications in Industry 4.0. In Proceedings of the 2022 4th IEEE Middle East and North Africa COMMunications Conference (MENACOMM), Amman, Jordan, 6–8 December 2022; pp. 153–158. [Google Scholar]
- Zdun, U.; Queval, P.J.; Simhandl, G.; Scandariato, R.; Chakravarty, S.; Jelic, M.; Jovanovic, A. Microservice security metrics for secure communication, identity management, and observability. ACM Trans. Softw. Eng. Methodol. 2023, 32, 1–34. [Google Scholar] [CrossRef]
- Kott, A.; Arnold, C. The promises and challenges of continuous monitoring and risk scoring. IEEE Secur. Priv. 2013, 11, 90–93. [Google Scholar] [CrossRef]
- Ayyagari, M.R.; Kesswani, N.; Kumar, M.; Kumar, K. Intrusion detection techniques in network environment: A systematic review. Wirel. Netw. 2021, 27, 1269–1285. [Google Scholar] [CrossRef]
- Tamimi, A.A.; Dawood, R.; Sadaqa, L. Disaster recovery techniques in cloud computing. In Proceedings of the 2019 IEEE Jordan International Joint Conference on Electrical Engineering and Information Technology (JEEIT), Amman, Jordan, 9–11 April 2019; pp. 845–850. [Google Scholar]
- Loukasmäki, H. Cyber Incident Response in Public Cloud: Implications of Modern Cloud Computing Characteristics for Cyber Incident Response. 2023. Available online: https://www.theseus.fi/handle/10024/803156 (accessed on 15 August 2023).
- Suguna, S.; Suhasini, A. Overview of data backup and disaster recovery in cloud. In Proceedings of the International Conference on Information Communication and Embedded Systems (ICICES2014), Chennai, India, 27–28 February 2014; pp. 1–7. [Google Scholar]
- Pandey, N.K.; Kumar, K.; Saini, G.; Mishra, A.K. Security issues and challenges in cloud of things-based applications for industrial automation. Ann. Oper. Res. 2023, 3, 20. [Google Scholar] [CrossRef]
- Sheganaku, G.; Schulte, S.; Waibel, P.; Weber, I. Cost-efficient auto-scaling of container-based elastic processes. Future Gener. Comput. Syst. 2023, 138, 296–312. [Google Scholar] [CrossRef]
- Fatima, A.; Khan, T.A.; Abdellatif, T.M.; Zulfiqar, S.; Asif, M.; Safi, W.; Al Hamadi, H.; Al-Kassem, A.H. Impact and Research Challenges of Penetrating Testing and Vulnerability Assessment on Network Threat. In Proceedings of the 2023 International Conference on Business Analytics for Technology and Security (ICBATS), Dubai, United Arab Emirates, 7–8 March 2023; pp. 1–8. [Google Scholar]
- Zheng, J.; Okamura, H.; Dohi, T. Pull-Type Security Patch Management in Intrusion Tolerant Systems: Modeling and Analysis. In Maintenance Management-Current Challenges, New Developments, and Future Directions; IntechOpen: London, UK, 2023. [Google Scholar]
- Schroeter, J.; Mucha, P.; Muth, M.; Jugel, K.; Lochau, M. Dynamic configuration management of cloud-based applications. In Proceedings of the 16th International Software Product Line Conference-Volume 2, New York, NY, USA, 2–7 September 2012; pp. 171–178. [Google Scholar]
- Kumar, R.; Goyal, R. When security meets velocity: Modeling continuous security for cloud applications using DevSecOps. In Innovative Data Communication Technologies and Application: Proceedings of ICIDCA 2020; Springer: Berlin/Heidelberg, Germany, 2021; pp. 415–432. [Google Scholar]
- Engström, V.; Johnson, P.; Lagerström, R.; Ringdahl, E.; Wällstedt, M. Automated Security Assessments of Amazon Web Services Environments. ACM Trans. Priv. Secur. 2023, 26, 1–31. [Google Scholar] [CrossRef]
- ETSI. Zero-touch network and service management (ZSM); General Security Aspects. Ref. Archit. Eur. Telecommun. Stand. Inst. (ETSI) 2021, 1, 1. Available online: https://www.etsi.org/deliver/etsi_gr/ZSM/001_099/010/01.01.01_60/gr_ZSM010v010101p.pdf (accessed on 15 August 2023).
- Benzaid, C.; Taleb, T. AI-driven Zero Touch Network and Service Management in 5G and Beyond: Challenges and Research Directions. IEEE Netw. 2020, 34, 186–194. [Google Scholar] [CrossRef]
- Theodoropoulos, T.; Violos, J.; Tsanakas, S.; Leivadeas, A.; Tserpes, K.; Varvarigou, T. Intelligent Proactive Fault Tolerance at the Edge through Resource Usage Prediction. arXiv 2023, arXiv:2302.05336. [Google Scholar] [CrossRef]
- Theodoropoulos, T.; Makris, A.; Kontopoulos, I.; Violos, J.; Tarkowski, P.; Ledwoń, Z.; Dazzi, P.; Tserpes, K. Graph neural networks for representing multivariate resource usage: A multiplayer mobile gaming case-study. Int. J. Inf. Manag. Data Insights 2023, 3, 100158. [Google Scholar] [CrossRef]
- DeCusatis, C.; Liengtiraphan, P.; Sager, A.; Pinelli, M. Implementing zero trust cloud networks with transport access control and first packet authentication. In Proceedings of the 2016 IEEE International Conference on Smart Cloud (SmartCloud), New York, NY, USA, 18–20 November 2016; pp. 5–10. [Google Scholar]
- Sanders, M.; Yue, C. Automated least privileges in cloud-based web services. In Proceedings of the Fifth ACM/IEEE Workshop on Hot Topics in Web Systems and Technologies, San Jose, CA, USA, 14 October 2017; pp. 1–6. [Google Scholar]
- Mehraj, S.; Banday, M.T. Establishing a zero trust strategy in cloud computing environment. In Proceedings of the 2020 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 22–24 January 2020; pp. 1–6. [Google Scholar]
- Kerman, A.; Borchert, O.; Rose, S.; Tan, A. Nist Special Publication 1800-35E—Implementing a zero trust architecture. Natl. Inst. Stand. Technol. (NIST) 2020, 1, 1. Available online: https://www.nccoe.nist.gov/sites/default/files/2022-12/zta-nist-sp-1800-35e-preliminary-draft.pdf (accessed on 15 August 2023).
- Hussain, F.; Li, W.; Noye, B.; Sharieh, S.; Ferworn, A. Intelligent service mesh framework for api security and management. In Proceedings of the 2019 IEEE 10th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 17–19 October 2019; pp. 0735–0742. [Google Scholar]
- Li, W.; Lemieux, Y.; Gao, J.; Zhao, Z.; Han, Y. Service mesh: Challenges, State of the Art, and Future Research Opportunities. In Proceedings of the 2019 IEEE International Conference on Service-Oriented System Engineering (SOSE), San Francisco, CA, USA, 4–9 April 2019; pp. 122–1225. [Google Scholar]
- Kim, E.; Han, J.; Kim, J. Visualizing Cloud-Native AI+ X Applications employing Service Mesh. In Proceedings of the 2020 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 21–23 October 2020. [Google Scholar]
- Benzaid, C.; Alemany, P.; Artych, R.; Asensio, R.; Chollon, G.; Kalalas, C.; de Oca, E.M.; Palma, N.P.; Zarca, A.M.; Pascual, H.R.; et al. INSPIRE-5Gplus’s White Paper on Intelligent Security Architecture for 5G and Beyond Networks, Version 2.0. 2022. Available online: https://5g-ppp.eu/wp-content/uploads/2022/11/INSPIRE-5Gplus_White_Paper_HLA_2.0.pdf (accessed on 15 August 2023).
- Morgan, W. Service Mesh: A Critical Component of the Cloud Native Stack. 2017. Available online: https://www.cncf.io/blog/2017/04/26/service-mesh-critical-component-cloud-native-stack/#:~:text=tl%3Bdr%3A%20A%20service%20mesh,of%20the%20cloud%20native%20stack (accessed on 15 August 2023).
- Theodoropoulos, T.; Kafetzis, D.; Violos, J.; Makris, A.; Tserpes, K. Multi-Agent Deep Reinforcement Learning for Weighted Multi-Path Routing. In Proceedings of the 3rd Workshop on Flexible Resource and Application Management on the Edge, Orlando, Florida, USA, 20 June 2023; pp. 7–11. [Google Scholar]
- Chandramouli, R.; Butcher, Z. NIST Special Publication 800-204A—Building secure microservices-based applications using service-mesh architecture. NIST Spec. Publ. 2020, 1, 1. Available online: https://csrc.nist.rip/external/nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-204A.pdf (accessed on 15 August 2023).
- Harlicaj, E. Anomaly Detection of Web-Based Attacks in Microservices. Master’s Thesis, Aalto University, Espoo, Finland, 2021. Available online: https://aaltodoc.aalto.fi/bitstream/handle/123456789/109316/master_Harlicaj_Eljon_2021.pdf (accessed on 15 August 2023).
- Baye, G.; Hussain, F.; Oracevic, A.; Hussain, R.; Kazmi, S.A. API security in large enterprises: Leveraging machine learning for anomaly detection. In Proceedings of the 2021 International Symposium on Networks, Computers and Communications (ISNCC), Dubai, United Arab Emirates, 31 October–2 November 2021; pp. 1–6. [Google Scholar]
- Benmerar, T.Z.; Theodoropoulos, T.; Fevereiro, D.; Rosa, L.; Rodrigues, J.; Taleb, T.; Barone, P.; Tserpes, K.; Cordeiro, L. Intelligent Multi-Domain Edge Orchestration for Highly Distributed Immersive Services: An Immersive Virtual Touring Use Case. In Proceedings of the 2023 IEEE International Conference on Edge Computing and Communications (EDGE), Chicago, IL, USA, 2–8 July 2023; pp. 381–392. [Google Scholar]
- Miller, L.; Mérindol, P.; Gallais, A.; Pelsser, C. Towards secure and leak-free workflows using microservice isolation. In Proceedings of the 2021 IEEE 22nd International Conference on High Performance Switching and Routing (HPSR), Paris, France, 7–10 June 2021; pp. 1–5. [Google Scholar]
- Wang, W.; Yongchareon, S. Security-as-a-service: A literature review. Int. J. Web Inf. Syst. 2020, 16, 493–517. [Google Scholar] [CrossRef]
- Iovene, M.; Jonsson, L. Defining AI Native: A Key Enabler for Advanced Intelligent Telecom Networks. 2023. Available online: https://www.ericsson.com/en/reports-and-papers/white-papers/ai-native (accessed on 15 August 2023).
- Lovén, L.; Leppänen, T.; Peltonen, E.; Partala, J.; Harjula, E.; Porambage, P.; Ylianttila, M.; Riekki, J. EdgeAI: A Vision for Distributed, Edge-native Artificial Intelligence in Future 6G Networks. 2019. Available online: https://api.semanticscholar.org/CorpusID:232030033 (accessed on 15 August 2023).
- Bao, S.; Sun, W.; Xu, H. A Native Intelligent and Security 6G Network Architecture. In Proceedings of the 2022 IEEE/CIC International Conference on Communications in China (ICCC Workshops), Foshan, China, 11–13 August 2022; pp. 395–400. [Google Scholar]
- Sarker, I.H.; Furhad, M.H.; Nowrozy, R. Ai-driven cybersecurity: An overview, security intelligence modeling and research directions. SN Comput. Sci. 2021, 2, 1–18. [Google Scholar] [CrossRef]
- Theodoropoulos, T.; Maroudis, A.C.; Violos, J.; Tserpes, K. An encoder-decoder deep learning approach for multistep service traffic prediction. In Proceedings of the 2021 IEEE Seventh International Conference on Big Data Computing Service and Applications (BigDataService), Oxford, UK, 23–26 August 2021; pp. 33–40. [Google Scholar]
- Musa, K.M. Evaluating Security-as-a-Service (SECaaS) Measures to Increase the Qual-ity of Cloud Computing. Int. J. Sci. Eng. Appl. (IJSEA) 2017, 6, 350–359. [Google Scholar]
- Fatima, B.M.D.I.M. Security-as-a-service in Cloud Computing (SecAAS). Int. J. Comput. Sci. Inf. Secur. (IJCSIS) 2017, 15, 2. [Google Scholar]
- Torkura, K.A.; Sukmana, M.I.; Cheng, F.; Meinel, C. Leveraging cloud native design patterns for security-as-a-service applications. In Proceedings of the 2017 IEEE International Conference on Smart Cloud (SmartCloud), New York, NY, USA, 3–5 November 2017. [Google Scholar]
- Benzaid, C.; Alemany, P.; Ayed, D.; Chollon, G.; Christopoulou, M.; Gür, G.; Lefebvre, V.; de Oca, E.; Munoz, R.; Ortiz, J.; et al. White paper: Intelligent security architecture for 5g and beyond networks. INSPIRE-5Gplus 2020. Available online: https://zenodo.org/records/4288658 (accessed on 15 August 2023).
- Johnson, J. Automating the OODA loop in the age of intelligent machines: Reaffirming the role of humans in command-and-control decision-making in the digital age. Def. Stud. 2023, 23, 43–67. [Google Scholar] [CrossRef]
- Moradi, N.; Shameli-Sendi, A.; Khajouei, A. A scalable stateful approach for virtual security functions orchestration. IEEE Trans. Parallel Distrib. Syst. 2021, 32, 1383–1394. [Google Scholar] [CrossRef]
- Salva-Garcia, P.; Chirevella-Perez, E.; Bernabe, J.B.; Alcaraz-Calero, J.M.; Wang, Q. Towards automatic deployment of virtual firewalls to support secure mMTC in 5G networks. In Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Paris, France, 29 April–2 May 2019; pp. 385–390. [Google Scholar]
- Nugraha, Y.; Martin, A. Cybersecurity service level agreements: Understanding government data confidentiality requirements. J. Cybersecur. 2022, 8, tyac004. [Google Scholar] [CrossRef]
- Laszewski, T.; Arora, K.; Farr, E.; Zonooz, P. Cloud Native Architectures: Design High-Availability and Cost-Effective Applications for the Cloud; Packt Publishing Ltd.: Birmingham, UK, 2018. [Google Scholar]
- Schneider, M.; Abeck, S. Engineering Microservice-Based Applications Using an Integration Platform as a Service. In Proceedings of the 2023 IEEE International Conference on Service-Oriented System Engineering (SOSE), Athens, Greece, 17–20 July 2023; IEEE Computer Society: Los Alamitos, CA, USA, 2023; pp. 124–129. [Google Scholar] [CrossRef]
- Calcote, L.; Butcher, Z. Istio: Up and Running: Using a Service Mesh to Connect, Secure, Control, and Observe; O’Reilly Media: Newton, MA, USA, 2019. [Google Scholar]
- Khatri, A.; Khatri, V. Mastering Service Mesh: Enhance, Secure, and Observe Cloud-Native Applications with Istio, Linkerd, and Consul; Packt Publishing Ltd.: Birmingham, UK, 2020. [Google Scholar]
- Raptis, T.P.; Passarella, A. A Survey on Networked Data Streaming with Apache Kafka. IEEE Access 2023. [Google Scholar] [CrossRef]
- Debeau, E.; Quintuna-Rodriguez, V. ONAP: An open source toolkit for zero touch automation. In Design Innovation and Network Architecture for the Future Internet; IGI Global: Hershey, PA, USA, 2021; pp. 212–249. [Google Scholar]
- OSM, E. OpenSourceMANO. Available online: https://osm.etsi.org/8 (accessed on 15 August 2023).
- Zhao, S.; Talasila, M.; Jacobson, G.; Borcea, C.; Aftab, S.A.; Murray, J.F. Packaging and sharing machine learning models via the acumos ai open platform. In Proceedings of the 2018 17th IEEE International Conference on Machine Learning and Applications (ICMLA), Orlando, FL, USA, 17–20 December 2018; pp. 841–846. [Google Scholar]
- Turnbull, J. Monitoring with Prometheus; Turnbull Press: Brooklyn, NY, USA, 2018. [Google Scholar]
- Lahmadi, A.; Beck, F. Powering monitoring analytics with elk stack. In Proceedings of the 9th International Conference on Autonomous Infrastructure, Management and Security (Aims 2015), Ghent, Belgium, 22–25 June 2015. [Google Scholar]
- Rizvi, S.; Orr, R.; Cox, A.; Ashokkumar, P.; Rizvi, M.R. Identifying the attack surface for IoT network. Internet Things 2020, 9, 100162. [Google Scholar] [CrossRef]
- Zhang, M.; Wang, L.; Jajodia, S.; Singhal, A. Network attack surface: Lifting the concept of attack surface to the network level for evaluating networks’ resilience against zero-day attacks. IEEE Trans. Dependable Secur. Comput. 2018, 18, 310–324. [Google Scholar] [CrossRef]
- Theisen, C.; Munaiah, N.; Al-Zyoud, M.; Carver, J.C.; Meneely, A.; Williams, L. Attack surface definitions: A systematic literature review. Inf. Softw. Technol. 2018, 104, 94–103. [Google Scholar] [CrossRef]
- IBM. Cost of a Data Breach Report 2022. Available online: https://www.ibm.com/downloads/cas/3R8N1DZJ (accessed on 15 August 2023).
- Chernyshev, M.; Baig, Z.; Zeadally, S. Cloud-Native Application Security: Risks, Opportunities, and Challenges in Securing the Evolving Attack Surface. Computer 2021, 54, 47–57. [Google Scholar] [CrossRef]
- Souppaya, M.; Morello, J.; Scarfone, K. Application Container Security Guide; Technical Report; National Institute of Standards and Technology: Gaithersburg, MA, USA, 2017. [Google Scholar]
- Spielmann, D.; Sokolowski, D.; Salvaneschi, G. Extensible Testing for Infrastructure as Code. In Proceedings of the Companion Proceedings of the 2023 ACM SIGPLAN International Conference on Systems, Programming, Languages, and Applications: Software for Humanity (SPLASH Companion’23), Cascais, Portugal, 22–27 October 2023. [Google Scholar] [CrossRef]
- Shaikh, F.A.; Siponen, M. Information security risk assessments following cybersecurity breaches: The mediating role of top management attention to cybersecurity. Comput. Secur. 2023, 124, 102974. [Google Scholar] [CrossRef]
- Li, J. Vulnerabilities mapping based on OWASP-SANS: A survey for static application security testing (SAST). arXiv 2020, arXiv:2004.03216. [Google Scholar] [CrossRef]
- Zhao, L.; Chen, S.; Xu, Z.; Liu, C.; Zhang, L.; Wu, J.; Sun, J.; Liu, Y. Software Composition Analysis for Vulnerability Detection: An Empirical Study on Java Projects. In Proceedings of the 31st ACM Joint European Software Engineering Conference and Symposium on the Foundations of Software Engineering (ESEC/FSE ’23), San Francisco, CA, USA, 3–9 December 2023. [Google Scholar]
- Vulnerabilities, C. Common Vulnerabilities and Exposures (CVE) Database. Available online: https://cve.mitre.org/ (accessed on 15 August 2023).
- Imtiaz, N.; Thorn, S.; Williams, L. A comparative study of vulnerability reporting by software composition analysis tools. In Proceedings of the Proceedings of the 15th ACM/IEEE International Symposium on Empirical Software Engineering and Measurement (ESEM), Bari, Italy, 11–15 October 2021; pp. 1–11. [Google Scholar]
- Theodoropoulos, T.; Makris, A.; Korontanis, I.; Tserpes, K. GreenKube: Towards Greener Container Orchestration using Artificial Intelligence. In Proceedings of the 2023 IEEE International Conference on Service-Oriented System Engineering (SOSE), Athens, Greece, 17–20 July 2023; pp. 135–139. [Google Scholar]
- Staron, M.; Abrahão, S.; Penzenstadler, B.; Hochstein, L. Recent Research Into Infrastructure as Code. IEEE Softw. 2023, 40, 86–88. [Google Scholar] [CrossRef]
- De Vicente Mohino, J.; Bermejo Higuera, J.; Bermejo Higuera, J.R.; Sicilia Montalvo, J.A. The application of a new secure software development life cycle (S-SDLC) with agile methodologies. Electronics 2019, 8, 1218. [Google Scholar] [CrossRef]
- Pitchford, M. The ‘Shift Left’ Principle. New Electron. 2021, 54, 18–21. [Google Scholar] [CrossRef]
- Rahman, A.; Partho, A.; Morrison, P.; Williams, L. What questions do programmers ask about configuration as code? In Proceedings of the 4th International Workshop on Rapid Continuous Software Engineering, Gothenburg, Sweden, 29 May 2018; pp. 16–22. [Google Scholar]
- Cankar, M.; Petrovic, N.; Pita Costa, J.; Cernivec, A.; Antic, J.; Martincic, T.; Stepec, D. Security in DevSecOps: Applying Tools and Machine Learning to Verification and Monitoring Steps. In Proceedings of the Companion of the 2023 ACM/SPEC International Conference on Performance Engineering, New York, NY, USA, 15–19 April 2023; pp. 201–205. [Google Scholar]
- Duarte, A.; Antunes, N. An empirical study of docker vulnerabilities and of static code analysis applicability. In Proceedings of the 2018 Eighth Latin-American Symposium on Dependable Computing (LADC), Foz do Iguacu, Brazil, 8–10 October 2018; pp. 27–36. [Google Scholar]
- Jacob, M. Checkmarx Announces First GenAI-powered AppSec Platform, Empowering Developers and AppSec Teams to Find and Fix Vulnerabilities Faster–Global Security Mag Online 2023. Available online: https://www.globalsecuritymag.com/Checkmarx-Announces-First-GenAI-powered-AppSec-Platform-Empowering-Developers.html (accessed on 15 August 2023).
- Sönmez, F.Ö.; Kiliç, B.G. Holistic web application security visualization for multi-project and multi-phase dynamic application security test results. IEEE Access 2021, 9, 25858–25884. [Google Scholar] [CrossRef]
- Jobin, T.; Kanjirapally, K.; Babu, K.S.; Scholar, P. Owasp Zed Attack Proxy. In Proceedings of the National Conference on Emerging Computer Applications (NCECA), Kottayam, India, 17 June 2021; p. 106. [Google Scholar]
- Mallisetty, S.B.; Tripuramallu, G.A.; Kamada, K.; Devineni, P.; Kavitha, S.; Krishna, A.V.P. A Review on Cloud Security and Its Challenges. In Proceedings of the 2023 International Conference on Intelligent Data Communication Technologies and Internet of Things (IDCIoT), Bengaluru, India, 5–7 January 2023; pp. 798–804. [Google Scholar] [CrossRef]
- German, K.; Ponomareva, O. An Overview of Container Security in a Kubernetes Cluster. In Proceedings of the 2023 IEEE Ural-Siberian Conference on Biomedical Engineering, Radioelectronics and Information Technology (USBEREIT), Yekaterinburg, Russia, 15–17 May 2023; pp. 283–285. [Google Scholar]
- Maruszczak, A.; Walkowski, M.; Sujecki, S. Base Systems for Docker Containers-Security Analysis. In Proceedings of the 2022 International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 22–24 September 2022; pp. 1–5. [Google Scholar]
- Sonnekalb, T.; Heinze, T.S.; Mäder, P. Deep security analysis of program code: A systematic literature review. Empir. Softw. Eng. 2022, 27, 2. [Google Scholar] [CrossRef]
- Banerjee, K.; Agarwall, D.; Bali, V.; Sharma, M.; Prajwal, S.S.; Arsh, M. A Survey on Kubernetes Policy Report Custom Resource Definition Kube-Bench Adapter. In Advances in Data and Information Sciences; Springer: Singapore, 2022; pp. 315–322. [Google Scholar] [CrossRef]
- Sedano, W.K.; Salman, M. Auditing Linux Operating System with Center for Internet Security (CIS) Standard. In Proceedings of the 2021 International Conference on Information Technology (ICIT), Amman, Jordan, 14–15 July 2021; pp. 466–471. [Google Scholar] [CrossRef]
- Korontanis, I.; Makris, A.; Theodoropoulos, T.; Tserpes, K. Real-time Monitoring and Analysis of Edge and Cloud Resources. In Proceedings of the 3rd Workshop on Flexible Resource and Application Management on the Edge, Orlando, FL, USA, 20 June 2023; pp. 13–18. [Google Scholar]
- Tan, J. Ensuring Component Dependencies and Facilitating Documentation by Applying Open Policy Agent in a DevSecOps Cloud Environment. 2022. Available online: https://aaltodoc.aalto.fi/handle/123456789/117364 (accessed on 15 August 2023).
- Team, A. Advanced Maryland Automatic Network Disk Archiver (Amanda), (1992–Present). Available online: https://www.amanda.org/ (accessed on 15 August 2023).
- Ferreira, M.; Brito, T.; Santos, J.F.; Santos, N. RuleKeeper: GDPR-Aware Personal Data Compliance for Web Frameworks. In Proceedings of the 2023 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 21–25 May 2023; pp. 2817–2834. [Google Scholar]



| Key Aspects of Security in Cloud-Native Services | ||||||
|---|---|---|---|---|---|---|
| Prior Surveys | Access Management | Data Security | Security Monitoring and Incident Response | Container and Microservice Security | Orchest. Platform Security | DevSecOps Practices |
| Secure cloud infrastructure: a survey on issues, current solutions, and open challenges [21]. | ✓ | ✓ | ✓ | × | × | × |
| Security in cloud computing: opportunities and challenges [22]. | ✓ | ✓ | ✓ | × | × | × |
| A survey on security challenges in cloud computing: issues, threats, and solutions [23]. | ✓ | ✓ | ✓ | × | × | × |
| A survey on secure cloud: security and privacy in cloud computing [24]. | ✓ | ✓ | ✓ | × | × | × |
| Secure cloud computing for critical infrastructure: a survey [25]. | ✓ | ✓ | ✓ | × | × | × |
| State-of-the-art survey on cloud computing security challenges, approaches, and solutions [26]. | ✓ | ✓ | × | × | × | × |
| A comprehensive survey on security in cloud computing [27]. | ✓ | ✓ | × | × | ✓ | × |
| A survey of security issues for cloud computing [28]. | ✓ | ✓ | ✓ | × | × | × |
| A survey on cloud security issues and techniques [29]. | ✓ | ✓ | × | × | × | × |
| Cloud computing security: a survey [30]. | ✓ | ✓ | ✓ | × | × | × |
| A survey on cloud computing security: issues, threats, and solutions [31]. | ✓ | ✓ | ✓ | × | × | × |
| A survey of cloud computing security challenges and solutions [32]. | ✓ | ✓ | ✓ | × | × | × |
| Cloud computing security challenges and solutions: a survey [33]. | ✓ | ✓ | × | × | × | × |
| Cloud computing security: a survey of service-based models [34]. | ✓ | ✓ | ✓ | × | × | × |
| Cloud security threats and solutions: a survey [35]. | ✓ | ✓ | × | × | × | × |
| Understanding the challenges and novel architectural models of multi-cloud native applications: a systematic literature review [36]. | ✓ | ✓ | ✓ | ✓ | × | ✓ |
| Key Aspects | Features |
|---|---|
| Access Management | Strong Access Controls Network Segmentation Secure Communication |
| Data Security | Secure Communication Data Encryption Disaster Recovery, Incident Response, and Data Backup |
| Security Monitoring and Incident Response | Disaster Recovery, Incident Response, and Data Backup Continuous Monitoring and Intrusion Detection Process Automation |
| Orchestration Platform Security | Process Automation Vulnerability Management Configuration Management |
| Container and Microservice Security | Process Automation Vulnerability Management Configuration Management Continuous Security Testing |
| DevSecOps Practices | Vulnerability Management Configuration Management Continuous Security Management |
| Key Features | Solutions |
|---|---|
| Strong Access Controls | Service Mesh |
| Zero-Trust Architecture (ZTA) | |
| Native AI and Security as a Service (SECaaS) | |
| Security Risk Profiling and Mitigation | |
| Network Segmentation | Zero-Touch Network and Service Management (ZSM) |
| Zero-Trust Architecture (ZTA) | |
| Service Mesh | |
| Data Encryption | Service Mesh |
| Native AI and Security as a Service (SECaaS) | |
| Security Risk Profiling and Mitigation | |
| Secure Communication | Zero-Touch Network and Service Management (ZSM) |
| Zero-Trust Architecture (ZTA) | |
| Service Mesh | |
| Shift Left and Static Testing Techniques for Enhancing Security | |
| Continuous Monitoring and Intrusion Detection | Zero-Trust Architecture (ZTA) |
| Service Mesh | |
| Autonomic and Cognitive Security Management | |
| Shift Left and Static Testing Techniques for Enhancing Security | |
| Continuous Security, Data Preserving, and Data Compliance | |
| Disaster Recovery, Incident Response, and Data Backup | Zero-Touch Network and Service Management (ZSM) |
| Service Mesh | |
| Security Risk Profiling and Mitigation | |
| Shift Left and Static Testing Techniques for Enhancing Security | |
| Continuous Security, Data Preserving, and Data Compliance | |
| Process Automation | Zero-Touch Network and Service Management (ZSM) |
| Service Mesh | |
| Security Aware Orchestration | |
| Shift Left and Static Testing Techniques for Enhancing Security | |
| Vulnerability Management | Security Risk Profiling and Mitigation |
| Shift Left and Static Testing Techniques for Enhancing Security | |
| Continuous Security, Data Preserving, and Data Compliance | |
| Configuration Management | Zero-Touch Network and Service Management (ZSM) |
| Shift Left and Static Testing Techniques for Enhancing Security | |
| Continuous Security Testing | Security Risk Profiling and Mitigation |
| Continuous Security, Data Preserving, and Data Compliance | |
| Shift Left and Static Testing Techniques for Enhancing Security |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Theodoropoulos, T.; Rosa, L.; Benzaid, C.; Gray, P.; Marin, E.; Makris, A.; Cordeiro, L.; Diego, F.; Sorokin, P.; Girolamo, M.D.; et al. Security in Cloud-Native Services: A Survey. J. Cybersecur. Priv. 2023, 3, 758-793. https://doi.org/10.3390/jcp3040034
Theodoropoulos T, Rosa L, Benzaid C, Gray P, Marin E, Makris A, Cordeiro L, Diego F, Sorokin P, Girolamo MD, et al. Security in Cloud-Native Services: A Survey. Journal of Cybersecurity and Privacy. 2023; 3(4):758-793. https://doi.org/10.3390/jcp3040034
Chicago/Turabian StyleTheodoropoulos, Theodoros, Luis Rosa, Chafika Benzaid, Peter Gray, Eduard Marin, Antonios Makris, Luis Cordeiro, Ferran Diego, Pavel Sorokin, Marco Di Girolamo, and et al. 2023. "Security in Cloud-Native Services: A Survey" Journal of Cybersecurity and Privacy 3, no. 4: 758-793. https://doi.org/10.3390/jcp3040034
APA StyleTheodoropoulos, T., Rosa, L., Benzaid, C., Gray, P., Marin, E., Makris, A., Cordeiro, L., Diego, F., Sorokin, P., Girolamo, M. D., Barone, P., Taleb, T., & Tserpes, K. (2023). Security in Cloud-Native Services: A Survey. Journal of Cybersecurity and Privacy, 3(4), 758-793. https://doi.org/10.3390/jcp3040034










