A Gap Analysis of the Adoption Maturity of Certificateless Cryptography in Cooperative Intelligent Transportation Systems
Abstract
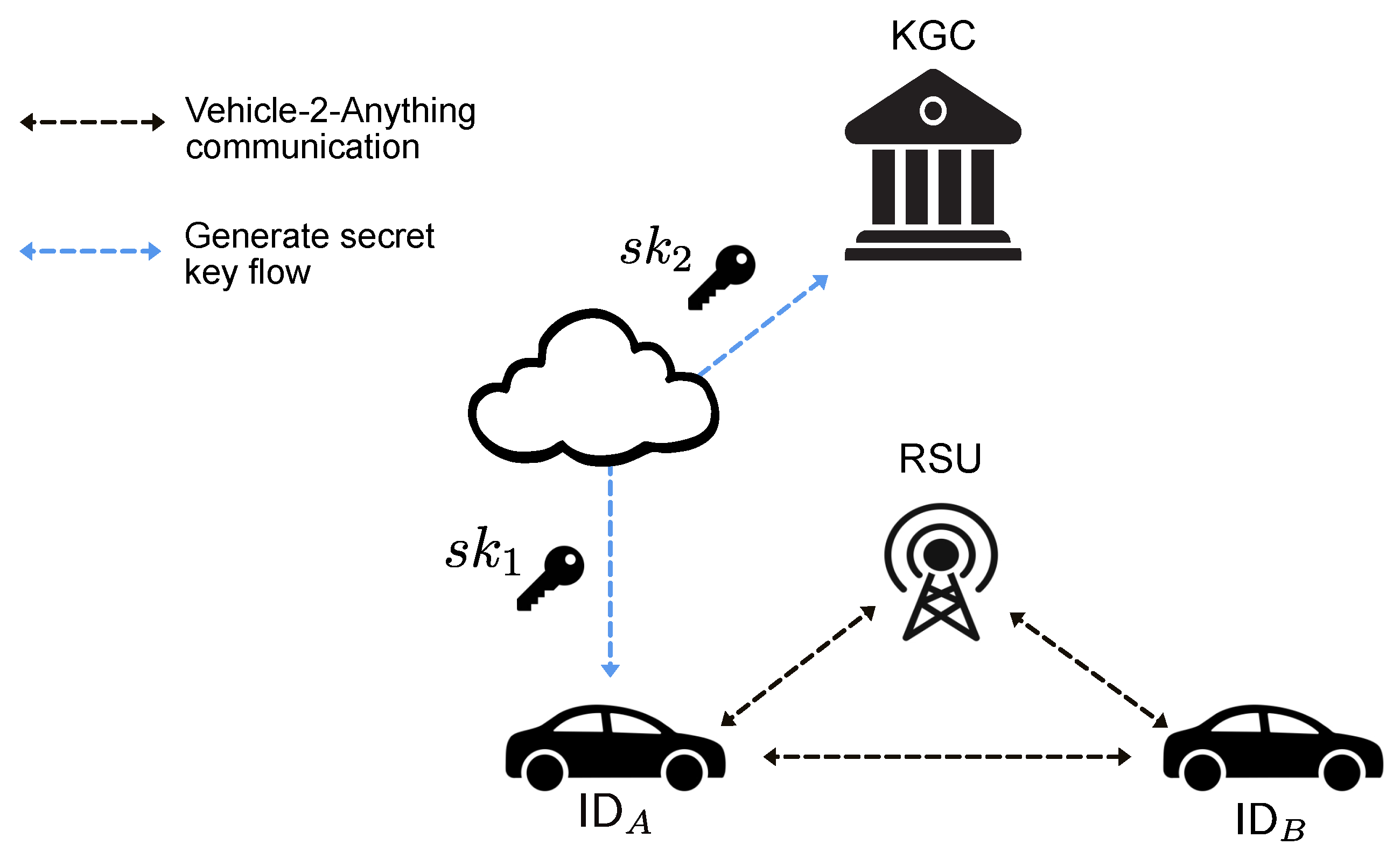
:1. Introduction
2. Cryptographic Systems in Intelligent Transport Systems
3. Certificateless Cryptography
4. Innovation-Decision Model
5. Technology Readiness
6. Research Approach
6.1. Literature Analysis
- Each article was scored with CLC technical readiness level points (CLC-TRL) using the proposed translation table found in Table 1.
- The aggregated scoring of CLC-TRL for each specified sub-field in CLC was computed where the final score was a majority scoring, i.e., if the majority of the articles had score n, that would be the final scoring.
- Each author processed step 1 and step 2 independently, then cross-checked the results and summarized the final CLC-TRL assessment.
6.2. Technology Readiness Levels
6.3. Empirical Data Collection and Analysis
- What are the reasons for (not) adopting new cryptographic systems (e.g., certificate-less) to ITS?
- −
- What motivates the adoption of (new) cryptographic systems for ITS?
- −
- If you were to decide today, would you be in favor of implementing certificate-less cryptography in ITS? Why or why not?
- −
- Do you think these motivations/reasons may change in the future?
- Why do(n’t) you think this will happen?
- Have you ever experienced that a decision to adopt a cryptographic system was later reversed (e.g., going from adoption to rejection, or the other way around)?
- −
- What was the reason for reversing the decision?
- −
- Why do you think that argument was made?
- −
- What would have needed to be different for this decision (not) to have been made?
7. Results
7.1. Current State of Research in CLC for C-ITS
7.2. Specialist Interviews
7.2.1. Interviewee Alpha
7.2.2. Interviewee Beta
7.2.3. Interviewee Gamma
7.3. Interview Summary
8. Discussion
8.1. Gap 1: Proof of Concepts
8.2. Gap 2: Best Practices
8.3. Gap 3: Stakeholders and Standardization
8.4. Technology Readiness Assessment
8.5. Future Research
8.6. Threats to Validity
9. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| C-ITS | Cooperative ITS |
| CLC | Certificateless Cryptography |
| CL-PKC | Certificateless Public Key Cryptography |
| ITS | Intelligent Transport Systems |
| TRL | Technology Readiness Level |
| V2X | Vehicle-to-Anything |
| VANET | Vehicular Ad-Hoc Network |
References
- Petit, J.; Shladover, S.E. Potential cyberattacks on automated vehicles. IEEE Trans. Intell. Transp. Syst. 2014, 16, 546–556. [Google Scholar] [CrossRef]
- Paulsen, C.; Byers, R. Glossary of Key Information Security Terms; Technical Report NIST IR 7298r3; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2019. [Google Scholar] [CrossRef]
- Lundgren, M.; Bergström, E. Dynamic interplay in the information security risk management process. Int. J. Risk Assess. Manag. 2019, 22, 212–230. [Google Scholar] [CrossRef]
- ISO/IEC 27005; Information Technology-Security Techniques -Information Security Risk Management. International Organization for Standardization: Geneva, Switzerland, 2013.
- Haqaf, H.; Koyuncu, M. Understanding key skills for information security managers. Int. J. Inf. Manag. 2018, 43, 165–172. [Google Scholar] [CrossRef]
- Anderson, A.B.; Ahmad, A.; Chang, S. Competencies of cybersecurity leaders: A review and research agenda. ICIS 2022 Proc. 2022, 9, 1967–1983. [Google Scholar]
- Salin, H.; Lundgren, M. Towards Agile Cybersecurity Risk Management for Autonomous Software Engineering Teams. J. Cybersecur. Priv. 2022, 2, 276–291. [Google Scholar] [CrossRef]
- Wall, J.D.; Palvia, P.; D’Arcy, J. Theorizing the behavioral effects of control complementarity in security control portfolios. Inf. Syst. Front. 2021, 24, 1–22. [Google Scholar] [CrossRef]
- Lundgren, M.; Bergström, E. Security-related stress: A perspective on information security risk management. In Proceedings of the 2019 International Conference on Cyber Security and Protection of Digital Services (Cyber Security), Oxford, UK, 3–4 June 2019; pp. 1–8. [Google Scholar]
- Boss, S.R.; Kirsch, L.J.; Angermeier, I.; Shingler, R.A.; Boss, R.W. If someone is watching, I’ll do what I’m asked: Mandatoriness, control, and information security. Eur. J. Inf. Syst. 2009, 18, 151–164. [Google Scholar] [CrossRef]
- Ogbanufe, O.; Crossler, R.E.; Biros, D. The valued coexistence of protection motivation and stewardship in information security behaviors. Comput. Secur. 2023, 124, 102960. [Google Scholar] [CrossRef]
- Wright, C.S. Software, vendors and reputation: An analysis of the dilemma in creating secure software. In Proceedings of the Trusted Systems: Second International Conference, INTRUST 2010, Beijing, China, 13–15 December 2010; Revised Selected Papers 2. Springer: Berlin/Heidelberg, Germany, 2011; pp. 346–360. [Google Scholar]
- Dalal, R.S.; Howard, D.J.; Bennett, R.J.; Posey, C.; Zaccaro, S.J.; Brummel, B.J. Organizational science and cybersecurity: Abundant opportunities for research at the interface. J. Bus. Psychol. 2022, 37, 1–29. [Google Scholar] [CrossRef]
- Bergström, E.; Lundgren, M. Stress amongst novice information security risk management practitioners. Int. J. Cyber Situational Aware. 2019, 4, 128–154. [Google Scholar] [CrossRef]
- Mankins, J.C. Technology readiness levels. White Pap. April 1995, 6, 1995. [Google Scholar]
- Rogers, E.M. Diffusion of Innovations; Simon and Schuster: New York, NY, USA, 2010. [Google Scholar]
- NIST SP 800-53; Security and Privacy Controls for Information Systems and Organizations. Technical Report. Edition: Revision 5, National Institute of Standards and Technology: Gaithersburg, MD, USA, 2020. [CrossRef]
- Al-Riyami, S.S.; Paterson, K.G. Certificateless Public Key Cryptography. In Proceedings of the Advances in Cryptology—ASIACRYPT 2003, Taipei, Taiwan, 30 November–4 December 2003; Laih, C.S., Ed.; Springer: Berlin/Heidelberg, Germany, 2003; pp. 452–473. [Google Scholar]
- NordicWay 3. NordicWay 2 and NordicWay 3. 2022. Available online: https://www.nordicway.net (accessed on 14 May 2022).
- C-Roads. C-Roads - The Platform of Harmonised C-ITS Deployment in Europe. 2022. Available online: https://www.c-roads.eu, (accessed on 14 May 2022).
- UNISIG. On-line Key Management FFFIS: Subset-137. 2015. Available online: https://www.era.europa.eu/system/files/2023-01/sos3_index083_-_subset-137_v100.pdf (accessed on 1 February 2022).
- European Telecommunications Standards Institute. ETSI TS 102 941 V1.4.1: Intelligent Transport Systems (ITS); Security; Trust and Privacy Management. 2021. Available online: https://www.etsi.org/standards (accessed on 23 February 2022).
- Hammi, B.; Monteuuis, J.P.; Petit, J. PKIs in C-ITS: Security functions, architectures and projects: A survey. Veh. Commun. 2022, 38, 100531. [Google Scholar] [CrossRef]
- European Comission. INTELLIGENT TRANSPORT SYSTEMS—Cooperative, Connected and Automated Mobility (ITS-CCAM) and Electromobility. 2022. Available online: https://joinup.ec.europa.eu/collection/rolling-plan-ict-standardisation/intelligent-transport-systems-cooperative-connected-and-automated-mobility-its-ccam-and-0 (accessed on 23 February 2022).
- IEEE Standard for Information Technology– Local and Metropolitan Area Networks–Specific Requirements–Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment 6: Wireless Access in Vehicular Environments. IEEE Std 802.11p-2010 (Amendment to IEEE Std 802.11-2007 as amended by IEEE Std 802.11k-2008, IEEE Std 802.11r-2008, IEEE Std 802.11y-2008, IEEE Std 802.11n-2009, and IEEE Std 802.11w-2009) 2010; pp. 1–51. Available online: https://ieeexplore.ieee.org/document/5514475 (accessed on 29 June 2023).
- IEEE Std 1609.0-2019 (Revision of IEEE Std 1609.0-2013); IEEE Guide for Wireless Access in Vehicular Environments (WAVE) Architecture. IEEE: Piscataway, NJ, USA, 2019; pp. 1–106. Available online: https://ieeexplore.ieee.org/document/8686445 (accessed on 29 June 2023).
- US Department of Transportation. Intelligent Transportation Systems Joint Program Office: ITS Cybersecurity Research Program. 2023. Available online: https://www.its.dot.gov (accessed on 28 March 2022).
- FoxIT. Black Tulip Report of the Investigation into the DigiNotar Certificate Authority Breach. Technical Report, 2012. Available online: https://www.researchgate.net/publication/269333601_Black_Tulip_Report_of_the_investigation_into_the_DigiNotar_Certificate_Authority_breach?channel=doi&linkId=5486fcf80cf268d28f06fa61&showFulltext=true (accessed on 10 August 2023).
- Malik, M.; Kamaldeep.; Dutta, M. On the Applicability of Certificateless Public Key Cryptography (CL-PKC) for Securing the Internet of Things (IoT). In Proceedings of the International Conference on IoT Inclusive Life (ICIIL 2019), Nitttr Chandigarh, India, 19–20 December 2020. [Google Scholar]
- Manivannan, D.; Moni, S.S.; Zeadally, S. Secure authentication and privacy-preserving techniques in Vehicular Ad-hoc NETworks (VANETs). Veh. Commun. 2020, 25, 100247. [Google Scholar] [CrossRef]
- Khan, S.; Luo, F.; Zhang, Z.; Rahim, M.A.; Ahmad, M.; Wu, K. Survey on Issues and Recent Advances in Vehicular Public-Key Infrastructure (VPKI). IEEE Commun. Surv. Tutor. 2022, 24, 1574–1601. [Google Scholar] [CrossRef]
- Nayak, P.; Swapna, G. Security issues in IoT applications using certificateless aggregate signcryption schemes: An overview. Internet Things 2023, 21, 100641. [Google Scholar] [CrossRef]
- Sahin, I. Detailed review of Rogers’ diffusion of innovations theory and educational technology-related studies based on Rogers’ theory. Turk. Online J. Educ. Technol.-TOJET 2006, 5, 14–23. [Google Scholar]
- Parasuraman, A. Technology Readiness Index (TRI) a multiple-item scale to measure readiness to embrace new technologies. J. Serv. Res. 2000, 2, 307–320. [Google Scholar] [CrossRef]
- Holden, R.J.; Karsh, B.T. The Technology Acceptance Model: Its past and its future in health care. J. Biomed. Inform. 2010, 43, 159–172. [Google Scholar] [CrossRef]
- Pandeya, G.R.; Daim, T.U.; Marotzke, A. A Strategy Roadmap for Post-quantum Cryptography. In Roadmapping Future: Technologies, Products and Services; Daim, T.U., Ed.; Springer International Publishing: Cham, Switzerland, 2021; pp. 171–207. [Google Scholar] [CrossRef]
- Ma, C.; Colon, L.; Dera, J.; Rashidi, B.; Garg, V. CARAF: Crypto Agility Risk Assessment Framework. J. Cybersecur. 2021, 7, tyab013. [Google Scholar] [CrossRef]
- Levy, Y.; Ellis, T.J. A systems approach to conduct an effective literature review in support of information systems research. Informing Sci. 2006, 9, 81–212. [Google Scholar] [CrossRef]
- Schultze, U.; Avital, M. Designing interviews to generate rich data for information systems research. Inf. Organ. 2011, 21, 1–16. [Google Scholar] [CrossRef]
- Reynolds, T.J.; Gutman, J. Laddering theory, method, analysis, and interpretation. J. Advert. Res. 1988, 28, 11–31. [Google Scholar]
- Liu, X.; Wang, Y.; Li, Y.; Cao, H. PTAP: A novel secure privacy-preserving & traceable authentication protocol in VANETs. Comput. Netw. 2023, 226, 109643. [Google Scholar] [CrossRef]
- Genc, Y.; Aytas, N.; Akkoc, A.; Afacan, E.; Yazgan, E. ELCPAS: A new efficient lightweight certificateless conditional privacy preserving authentication scheme for IoV. Veh. Commun. 2023, 39, 100549. [Google Scholar] [CrossRef]
- Wang, Z.; Zhou, Y.; Qiao, Z.; Yang, B.; Gu, C.; Xu, Y.; Zhang, M. An Anonymous and Revocable Authentication Protocol for Vehicle-to-Vehicle Communications. IEEE Internet Things J. 2023, 10, 5114–5127. [Google Scholar] [CrossRef]
- Yan, X.; Ma, M.; Su, R. Efficient Group Handover Authentication for Secure 5G-Based Communications in Platoons. IEEE Trans. Intell. Transp. Syst. 2023, 24, 3104–3116. [Google Scholar] [CrossRef]
- Tan, H.; Zheng, W.; Vijayakumar, P. Secure and Efficient Authenticated Key Management Scheme for UAV-Assisted Infrastructure-Less IoVs. IEEE Trans. Intell. Transp. Syst. 2023, 24, 1–12. [Google Scholar] [CrossRef]
- Zhou, Y.; Cao, L.; Qiao, Z.; Xia, Z.; Yang, B.; Zhang, M.; Zhang, W. An efficient identity authentication scheme with dynamic anonymity for VANETs. IEEE Internet Things J. 2023, 10, 10052–10065. [Google Scholar] [CrossRef]
- Zhou, X.; Luo, M.; Vijayakumar, P.; Peng, C.; He, D. Efficient Certificateless Conditional Privacy-Preserving Authentication for VANETs. IEEE Trans. Veh. Technol. 2022, 71, 7863–7875. [Google Scholar] [CrossRef]
- Ali, I.; Chen, Y.; Faisal, M.; Li, M. Certificateless Signature-Based Authentication Scheme for Vehicle-to-Infrastructure Communications Using Bilinear Pairing. In Efficient and Provably Secure Schemes for Vehicular Ad-Hoc Networks; Springer Nature: Singapore, 2022; pp. 91–119. [Google Scholar] [CrossRef]
- Zheng, L.; Feng, T. Research on a Vehicle Authentication and Key Transmission Protocol Based on CPN. Symmetry 2022, 14, 2398. [Google Scholar] [CrossRef]
- Imghoure, A.; El-Yahyaoui, A.; Omary, F. ECDSA-based certificateless conditional privacy-preserving authentication scheme in Vehicular Ad Hoc Network. Veh. Commun. 2022, 37, 100504. [Google Scholar] [CrossRef]
- Wang, Y.; Liu, Y.; Tian, Y. ISC-CPPA:Improverd-Security Certificateless Conditional Privacy-Preserving Authentication Scheme With Revocation. IEEE Trans. Veh. Technol. 2022, 71, 12304–12314. [Google Scholar] [CrossRef]
- Yan, X.; Ma, M.; Su, R. A Certificateless Efficient and Secure Group Handover Authentication Protocol in 5G Enabled Vehicular Networks. In Proceedings of the ICC 2022—IEEE International Conference on Communications, Seoul, Republic of Korea, 16–20 May 2022; pp. 1678–1684. [Google Scholar] [CrossRef]
- Mukathe, K.D.; Wu, D.; Ahmed, W. Secure and Efficient Blockchain-Based Certificateless Authentication Scheme for Vehicular Ad-Hoc Networks (VANETs). In Proceedings of the 2022 4th International Conference on Applied Machine Learning (ICAML), Changsha, China, 23–25 July 2022; pp. 302–307. [Google Scholar] [CrossRef]
- Gupta, D.S.; Karati, A.; Saad, W.; da Costa, D.B. Quantum-Defended Blockchain-Assisted Data Authentication Protocol for Internet of Vehicles. IEEE Trans. Veh. Technol. 2022, 71, 3255–3266. [Google Scholar] [CrossRef]
- Palaniswamy, B.; Ansari, K.; Reddy, A.G.; Das, A.K.; Shetty, S. Robust Certificateless Authentication Protocol for the SAE J1939 Commercial Vehicles Bus. IEEE Trans. Veh. Technol. 2023, 72, 4493–4509. [Google Scholar] [CrossRef]
- Jiang, Y.; Zhang, K.; Qian, Y.; Zhou, L. Anonymous and Efficient Authentication Scheme for Privacy-Preserving Distributed Learning. IEEE Trans. Inf. Forensics Secur. 2022, 17, 2227–2240. [Google Scholar] [CrossRef]
- Qi, J.; Gao, T.; Deng, X.; Zhao, C. A pseudonym-based certificateless privacy-preserving authentication scheme for VANETs. Veh. Commun. 2022, 38, 100535. [Google Scholar] [CrossRef]
- Zhao, Y.; Dan, G.; Ruan, A.; Huang, J.; Xiong, H. A Certificateless and Privacy-Preserving Authentication with Fault-Tolerance for Vehicular Sensor Networks. In Proceedings of the 2021 IEEE Conference on Dependable and Secure Computing (DSC), Aizuwakamatsu, Japan, 30 January–2 February 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Liang, Y.; Liu, Y. Analysis and Improvement of an Efficient Certificateless Aggregate Signature With Conditional Privacy Preservation in VANETs. IEEE Syst. J. 2023, 17, 664–672. [Google Scholar] [CrossRef]
- Gong, Z.; Gao, T.; Guo, N. PCAS: Cryptanalysis and improvement of pairing-free certificateless aggregate signature scheme with conditional privacy-preserving for VANETs. Ad Hoc Netw. 2023, 144, 103134. [Google Scholar] [CrossRef]
- Wang, H.; Wang, L.; Zhang, K.; Li, J.; Luo, Y. A conditional privacy-preserving certificateless aggregate signature scheme in the standard model for VANETs. IEEE Access 2022, 10, 15605–15618. [Google Scholar] [CrossRef]
- Cahyadi, E.F.; Su, T.W.; Yang, C.C.; Hwang, M.S. A certificateless aggregate signature scheme for security and privacy protection in VANET. Int. J. Distrib. Sens. Netw. 2022, 18, 15501329221080658. [Google Scholar] [CrossRef]
- Samra, B.; Fouzi, S. New efficient certificateless scheme-based conditional privacy preservation authentication for applications in VANET. Veh. Commun. 2022, 34, 100414. [Google Scholar] [CrossRef]
- Chen, Y.; Chen, J. CPP-CLAS: Efficient and Conditional Privacy-Preserving Certificateless Aggregate Signature Scheme for VANETs. IEEE Internet Things J. 2022, 9, 10354–10365. [Google Scholar] [CrossRef]
- Wei, G.; Qin, Y.; Fu, W. Secure and Efficient Certificateless Authentication Key Agreement Protocol in VANET. In Emerging Information Security and Applications; Chen, J., He, D., Lu, R., Eds.; Springer Nature Switzerland: Cham, Switzerland, 2022; pp. 160–172. [Google Scholar]
- Yang, J.; Li, F.; Zhang, Z. Research on NTRU-based Anonymous Authentication and Key Negotiation Protocol for VANETs. In Proceedings of the 2022 7th International Conference on Cyber Security and Information Engineering (ICCSIE), Brisbane, Australia, 23–25 September 2022; pp. 104–108. [Google Scholar] [CrossRef]
- Dai, C.; Xu, Z. Pairing-Free Certificateless Aggregate Signcryption Scheme for Vehicular Sensor Networks. IEEE Internet Things J. 2023, 10, 5063–5072. [Google Scholar] [CrossRef]
- Guo, R.; Xu, L.; Li, X.; Zhang, Y.; Li, X. An Efficient Certificateless Ring Signcryption Scheme With Conditional Privacy-Preserving in VANETs. J. Syst. Archit. 2022, 129, 102633. [Google Scholar] [CrossRef]
- Niu, S.; Shao, H.; Hu, Y.; Zhou, S.; Wang, C. Privacy-Preserving Mutual Heterogeneous Signcryption Schemes Based on 5G Network Slicing. IEEE Internet Things J. 2022, 9, 19086–19100. [Google Scholar] [CrossRef]
- Xie, Z.; Chen, Y.; Ali, I.; Pan, C.; Li, F.; He, W. Efficient and Secure Certificateless Signcryption Without Pairing for Edge Computing-Based Internet of Vehicles. IEEE Trans. Veh. Technol. 2023, 72, 5642–5653. [Google Scholar] [CrossRef]
- Yang, Y.; Zhang, L.; Zhao, Y.; Choo, K.K.R.; Zhang, Y. Privacy-Preserving Aggregation-Authentication Scheme for Safety Warning System in Fog-Cloud Based VANET. IEEE Trans. Inf. Forensics Secur. 2022, 17, 317–331. [Google Scholar] [CrossRef]
- Ullah, I.; Khan, M.A.; Khan, F.; Jan, M.A.; Srinivasan, R.; Mastorakis, S.; Hussain, S.; Khattak, H. An Efficient and Secure Multimessage and Multireceiver Signcryption Scheme for Edge-Enabled Internet of Vehicles. IEEE Internet Things J. 2022, 9, 2688–2697. [Google Scholar] [CrossRef]
- Ali, I.; Chen, Y.; Ullah, N.; Afzal, M.; HE, W. Bilinear Pairing-Based Hybrid Signcryption for Secure Heterogeneous Vehicular Communications. IEEE Trans. Veh. Technol. 2021, 70, 5974–5989. [Google Scholar] [CrossRef]
- Altaf, F.; Maity, S. PLHAS: Privacy-preserving localized hybrid authentication scheme for large scale vehicular ad hoc networks. Veh. Commun. 2021, 30, 100347. [Google Scholar] [CrossRef]
- Xiong, W.; Wang, R.; Wang, Y.; Wei, Y.; Zhou, F.; Luo, X. Improved Certificateless Aggregate Signature Scheme Against Collusion Attacks for VANETs. IEEE Syst. J. 2023, 17, 1098–1109. [Google Scholar] [CrossRef]
- Moni, S.S.; Manivannan, D. CREASE: Certificateless and REused-pseudonym based Authentication Scheme for Enabling security and privacy in VANETs. Internet Things 2022, 20, 100605. [Google Scholar] [CrossRef]
- Zheng, H.; Luo, M.; Zhang, Y.; Peng, C.; Feng, Q. A Security-Enhanced Pairing-Free Certificateless Aggregate Signature for Vehicular Ad-Hoc Networks. IEEE Syst. J. 2022, 1–12. [Google Scholar] [CrossRef]
- Sripathi Venkata Naga, S.K.; Yesuraj, R.; Munuswamy, S.; Arputharaj, K. A Comprehensive Survey on Certificate-Less Authentication Schemes for Vehicular Ad hoc Networks in Intelligent Transportation Systems. Sensors 2023, 23, 2682. [Google Scholar] [CrossRef] [PubMed]
- Cahyadi, E.F.; Hwang, M.S. A Comprehensive Survey on Certificateless Aggregate Signature in Vehicular Ad Hoc Networks. IETE Tech. Rev. 2022, 39, 1265–1276. [Google Scholar] [CrossRef]
- Bergström, E.; Lundgren, M.; Ericson, Å. Revisiting information security risk management challenges: A practice perspective. Inf. Comput. Secur. 2019, 27, 358–372. [Google Scholar]
- Lundgren, M. Rethinking capabilities in information security risk management: A systematic literature review. Int. J. Risk Assess. Manag. 2020, 23, 169–190. [Google Scholar] [CrossRef]
- Wangen, G.; Snekkenes, E. A taxonomy of challenges in information security risk management. In Proceedings of the Norwegian Information Security Conference/Norsk informasjonssikkerhetskonferanse-NISK 2013-Stavanger, Stavanger, Norway, 18–20 November 2013; Akademika Forlag: Bergen, Norway, 2013. [Google Scholar]
- Schatz, D.; Bashroush, R.; Wall, J. Towards a more representative definition of cyber security. J. Digit. Forensics Secur. Law 2017, 12, 8. [Google Scholar] [CrossRef]



| NASA TRL | CLC in C-ITS Translation: CLC TRL |
|---|---|
| TRL 1: basic principles | Only theoretical work is proposed, very few papers in the field. |
| TRL 2: technology concept | Theoretical work combined with comparative analysis with other technologies are given. |
| TRL 3: first experiments | There are several proof-of-concepts in at least a laboratory environment or simulations. |
| TRL 4: validation in lab | There are several proof-of-concepts using corresponding or similar C-ITS equipment, but not used in real infrastructure. |
| TRL 5: validation on site | Proof-of-concepts exists where the technology is tested in real C-ITS equipment in study- or pre-pilot sites. |
| TRL 6: component validation | Protocols are implemented and partially tested at real pilot C-ITS sites with real traffic. |
| TRL 7: system validation | Protocols are implemented and fully tested at real pilot C-ITS sites with real traffic. |
| TRL 8: tested and implemented | Protocols are implemented and fully tested at real pilot C-ITS sites with real traffic, and evidence for feasibility is presented. |
| TRL 9: proven in mission | Protocols are implemented and ready for scaled deployment in operating C-ITS sites. |
| Interviewee | Role | Experience |
|---|---|---|
| Alpha | Digital strategist ITS/C-ITS | Cybersecurity, ITS/C-ITS > 20 years |
| Beta | PKI specialist | Cybersecurity, PKI, C-ITS > 10 years |
| Gamma | C-ITS specialist | IT-architecture, ITS/C-ITS > 5 years |
| Gaps | Description | Going Forward |
|---|---|---|
| Proof-of-Concepts | Various concepts of CLC-based solutions have been proposed, such as for authentication [41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58], aggregated signing [44,59,60,61,62,63,64], key agreement [65,66], and signcryption [67,68,69,70,71,72,73]. However, common for these proposals is that they have either been tested in a controller lab environment [42,47,48,59,64,74] or only theoretically [41,43,45,49,50,52,53,60,62,63,65,66,67,73,75], typically using a desktop or laptop computer. This has lead to quite similar, theoretical performances as they are based on matching setups (e.g., using MIRACL lib. Omnet++, Veins simulations, etc.); even more so when the same PoC are used between authors [43,44,45,52,53,67]. Hence, little is still known about performance in a production-like environment and context. | Based on the interviews, one way of going forward to counter this gap would be to encourage collaborative (government and/or international funded) C-ITS project initiatives in which new technological advancements can be developed, tested and assessed. Such initiatives could provide an alternative source of cryptography knowledge in the organisations and aid buy-in for testing new technologies and PoC among practitioners and stakeholders alike. |
| Best-Practices | A clearly identified gap is the lack of professional and academic-level cryptography knowledge in the organization; from the interviews, this was frequently mentioned as a barrier for further developments of new security mechanisms. Practitioners from interview Alpha, Beta, and Gamma, stayed à jour with new developments in cryptography by Internet searches and third-party providers recommendations, which tended to gravitate around already-established best-practices. | Beyond employee training, education, and recruitment of relevant competences within organisations, science communication plays a role in affecting the practitioners individual ‘awareness-knowledge’. Bridging academia and industry—e.g., by extended networking and increased collaboration between industry and academia—could, similarly, influence standardization projects. |
| Stakeholders and Standardization | Although the academic research in CLC for C-ITSs is increasing, there is little overlap with standardization bodies, which are typically focused on traditional solutions. As noted from the interviews, stakeholders tend to rely on approved standardization requirements, which could therefore affect a broader comprehension, development and adoption of CLC-systems by the industry. | Further harmonization of terms, security models, nomenclature, and grouping of protocols in CLC for C-ITSs is needed to better bridge industry, standardization bodies, and academic work on the topic. |
| Subfield | PoC Lab | PoC Industry | Reference Data | CLC-TRL |
|---|---|---|---|---|
| 2023 Q1 | ||||
| Authentication | 33% | 0% | [41,42,43,44,45,46] | 3 |
| Aggregated signatures | 66% | 0% | [59,60,75] | 3 |
| Key agreement | 0% | 0% | [65] | 1 |
| Signcryption | 0% | 0% | [67] | 2 |
| 2022 | ||||
| Authentication | 66% | 0% | [47,48,49,50,51,52,53,54,55,56,57,76] | 3 |
| Aggregated signatures | 60% | 0% | [61,62,63,64,77] | 3 |
| Key agreement | 0% | 0% | [66] | 1 |
| Signcryption | 100% | 0% | [68,69,70,71,72] | 4 |
| Surveys | [32,78,79] |
| Id | Key Takeaway |
|---|---|
| 1 | It is crucial to have individuals with competency in cryptography within the organization, to not only understand but also drive and push innovation, despite the complexities of these new technologies. |
| 2 | The involvement and support of standardization bodies are indispensable for ensuring a wide acceptance and implementation of new security controls. |
| 3 | A factor that slows down the willingness and ability to adopt new security controls such as CLC is the lack of key takeaways 1 and 2. |
| 4 | Organizations can become stuck with previously implemented and accepted security solutions, e.g., traditional PKI, hence do not tend to explore new options that are not officially accepted (in standardization documents). |
| 5 | Improved proof-of-concepts of CLC-based solutions are needed, to speeding up adoption of such new security controls. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Salin, H.; Lundgren, M. A Gap Analysis of the Adoption Maturity of Certificateless Cryptography in Cooperative Intelligent Transportation Systems. J. Cybersecur. Priv. 2023, 3, 591-609. https://doi.org/10.3390/jcp3030028
Salin H, Lundgren M. A Gap Analysis of the Adoption Maturity of Certificateless Cryptography in Cooperative Intelligent Transportation Systems. Journal of Cybersecurity and Privacy. 2023; 3(3):591-609. https://doi.org/10.3390/jcp3030028
Chicago/Turabian StyleSalin, Hannes, and Martin Lundgren. 2023. "A Gap Analysis of the Adoption Maturity of Certificateless Cryptography in Cooperative Intelligent Transportation Systems" Journal of Cybersecurity and Privacy 3, no. 3: 591-609. https://doi.org/10.3390/jcp3030028
APA StyleSalin, H., & Lundgren, M. (2023). A Gap Analysis of the Adoption Maturity of Certificateless Cryptography in Cooperative Intelligent Transportation Systems. Journal of Cybersecurity and Privacy, 3(3), 591-609. https://doi.org/10.3390/jcp3030028







