Abstract
Older adults in the U.S. are interested in maintaining independence, aging at home longer, and staying active. Their substantial size, market share, and household wealth sparked the interest of investors and developers in remote monitoring, smart homes, ambient-assisted living, tracking, applications, and sensors via the IoT. This study used the unified theory of acceptance and use of technology extended (UTAUT2). The overarching research question was: “To what extent do performance, effort, influence, conditions, motivation, price, and habit affect older adults’ behavioral intent to use IoT technologies in their homes?” The research methodology for this study was a nonexperimental correlation of the variables that affect older adults’ intention to use IoT-enabled technologies in their homes. The population was adults 60 plus years in northern Virginia. The sample consisted of 316 respondents. The seven predictors cumulatively influenced older adults’ behavioral intent to use IoT-enabled technologies, F(7, 308) = 133.50, p < 0.001, R2 = 0.75. The significant predictors of behavioral intention to use IoT technologies were performance expectancy (B = 0.244, t(308) = 4.427, p < 0.001), social influence (B = 0.138, t(308) = 3.4775, p = 0.001), facilitating conditions (B = 0.184, t(308) = 2.999, p = 0.003), hedonic motivation (B = 0.153, t(308) = 2.694, p = 0.007), price value (B = 0.140, t(308) = 3.099, p = 0.002), and habit (B = 0.378, t(308) = 8.696, p < 0.001). Effort expectancy was insignificant (B = −0.026, t(308) = −0.409, p = 0.683). This study filled the gap in research on older adults’ acceptance of IoT by focusing specifically on that population. The findings help reduce the risk of solutions driven by technological and organizational requirements rather than the older adults’ unique needs and requirements. The study revealed that older adults may be susceptible to undue influence to adopt IoT solutions. These socioeconomic dimensions of the UTAUT2 are essential to the information technology field because the actualizing of IoT-enabled technologies in private homes depends on older adults’ participation and adoption. This research is beneficial to IoT developers, implementers, cybersecurity researchers, healthcare providers, caregivers, and managers of in-home care providers regarding adding IoT technologies in their homes.
1. Introduction
The Internet of Things (IoT) extends the Internet, connecting it to people and physical environments through the distribution of uniquely addressed devices with embedded sensors, actuators, and the capabilities to receive or send data [1,2]. These systems are called “smart” systems [3,4], cyber physical systems [5,6], and in the healthcare industry, they are more specifically referred to as ambient-assisted living systems AALS [7]. AALS are living environments that utilize information communication technology to monitor ambient conditions, persons’ activities, and collect data [8,9]. The growing healthcare needs of older adults have led providers and technicians to seek technological approaches to enhance healthcare, patient comfort, experience, quality of life, and safety; reduce costs; and provide warnings [1,2,8,10,11]. The healthcare industry has rapidly sought to adopt IoT technological advances [6,12,13], including wearable devices, implantable devices, wireless communications, and remote monitoring [10].
Researchers have identified many security vulnerabilities in these devices, such as boot process vulnerabilities [11], hard coded passwords [12,13], and firmware/software vulnerabilities [14,15]. Older adults are more vulnerable to threats introduced by the Internet. A recent study found that more than 67% of older adults have been victims of a scam or hack [16]. The vulnerabilities coupled with the pervasive connectivity of IoT devices significantly increases risk [1]. The IoT connects living and inanimate objects, where an attack or failure could lead to physical damage or loss of life [17,18,19]. The topic for this research study was older adults’ behavioral intention to use IoT technologies in their homes to improve safety, health, quality of life, and independence despite the risks [20].
1.1. Background of the Problem
In 2015, adults 50 years and older made up approximately 40% of the population, were the fastest growing demographic adopting Internet-enabled technologies [10], and accounted for more than half of consumer spending [11]. Older adults in the U.S. are interested in maintaining independence, aging at home longer, and staying active [11]. Their substantial size, market share, and household wealth sparked the interest of investors and developers in remote monitoring, smart homes, ambient-assisted living, tracking, applications, and sensors via the IoT. The academic research indicated that the use of IoT technologies in the home would improve older adults’ safety, independence, life quality, and health [8,12,13,14,15]. However, more than half of this demographic group use older cell phones and desktop computers, 30% do not use the Internet [10], and more than 80% have not upgraded or adopted the latest technological implementations, such as tablets, smartphones, or laptops [15]. Most of the academic research on IoT-enabled technologies for older adults centered on technological and organizational challenges from the perspective of developers and healthcare professionals and did not consider the proposed consumers’ needs and requirements [16].
While researchers have performed a fair number of studies on technology acceptance, most researchers approached the topic using models developed for the business context. The majority of the researchers used the technology acceptance model TAM [17,18,19] and the unified theory of acceptance and use of technology UTAUT [20,21], which were developed to measure technology acceptance in business environments where technology adoption is involuntary. The TAM posited that a person’s perceived usefulness and perceived ease of use of the technology were good predictors of that individual’s intention to use technology in a business context [18].
Venkatesh et al. [22] developed the UTAUT by evaluating and synthesizing several widely accepted technology adoption models such as the TAM, the social cognitive theory, the theory of planned behavior (TPB), a combination of TAM and TPB, the innovation diffusion theory, the motivation model, and the theory of reasoned action. The results of this work added the constructs of technology performance expectancy, effort expectancy, social influence to use the technology, and facilitating conditions, which were moderated by gender, age, experience, and voluntariness of use to affect behavioral intention and use. Although Venkatesh et al. [22] developed the UTAUT for business use, researchers dropped the voluntariness of use construct and reported that all other predictors significantly affected behavioral intention to use when moderated by age [20].
Researchers using TAM and UTAUT attempted to make their studies more relevant to the consumer context by adding constructs such as price, anxiety, and attitude, but the results were contradictory to prior evidence [23]. Existing research on UTAUT focused on four types of extensions: new extrinsic components, modeling tools, moderating components, and outcomes [9,14,24,25,26]. An overwhelming percentage of researchers only administered their surveys via the Internet, ignoring the whole portion of the demographic group without Internet [16,17,27,28,29,30].
1.2. Statement of the Problem
A recent theoretical analysis of research on the topic of technology acceptance revealed several recommendations for future research [31,32]. According to this research, most studies from 2003 to 2014 identified changes to UTAUT but did not add extensions to the theory for new concepts, focal areas, or phenomena. The identified problem was that developers and healthcare providers focused their research on technological and organizational challenges without considering whether older adults would accept the technology as designed and use the solutions. The findings of the research suggested that researchers used UTAUT and UTAUT2, refining the context factors that affect use by linking features to individual outcomes and use, and conducting multilevel research to explore the impacts of environment, organization, and locational contextual factors. Previous research indicated that researchers should incorporate events to examine the implications of changing states of user perceptions, patterns of use, and individual outcomes. Symptoms of the problem include a focus on requirements from the developer perspective devoid of users [8,33]; including technical specifications [34,35,36]; and organizational requirements [7,16,37].
However, researchers ignored the end users and deviations of these perspectives, their acceptability, and the usability of the technology in the context of their limitations [8,17]. Results indicated that as age increased, the differences in learning new technologies were more pronounced by gender. Older men relied on habits as the experience, and older women valued the availability of knowledge, resources, and technical support as crucial to accepting a new technology [38]. From the consumer perspective, behavioral intentional positively affected use as moderated by experience with the technology. What was not yet known was how the UTAUT2 applied to technologies beyond the mobile Internet in different applications and age groups. Research indicated that other relevant aspects which may increase the applicability of UTAUT2 to a broader perspective of technology use-case scenarios were unknown [39]. The desire of older adults to age in place longer, their increasing healthcare needs, significant market share of this demographic, and an understanding of their unique perspectives of the technologies are essential to understanding their intention to adopt and use IoT technologies in their homes from a consumer context [30].
1.3. Purpose of the Study
Most of the recent academic literature on technology acceptance stems from a misaligned design. For example, researchers studying technology acceptance in a business setting used a consumer model, and vice versa. In many of the studies that purported to focus on older adults’ technology acceptance, this age group made up the smallest portion of the sample. Few studies on older adults’ acceptance of technology explicitly targeted older adults, and even fewer attempted to recruit participants who did not have Internet in their homes. This study explicitly investigated older adults’ acceptance of IoT in the consumer context using the UTAUT2, correcting these previous research design flaws and gaps in the literature. The purpose of this nonexperimental correlation research design was to explain the extent to which performance expectancy, effort expectancy, social influence, facilitating conditions, hedonic motivation, price value, and habit affect northern Virginians’ (age 60 and up) intention to use emerging IoT technologies in their homes. The study did not require participants to have experience with, or knowledge of, IoT technologies. The researcher recruited the target population via Internet surveys through SurveyMonkey™. The study used the UTAUT2 model to measure the perspectives of 316 adults age 60 and older in the northern Virginia area through SurveyMonkey™. Multiple regression analysis revealed that habit, performance expectancy, facilitating conditions, hedonic motivation, social influence, and price value were statistically significant in predicting behavioral intent to use IoT technologies to age in place. These dimensions of the UTAUT2 are essential to the information technology field because the implementation of IoT-enabled technologies in private homes depends on older adults’ participation and adoption [30].
1.4. Significance of the Study
The outcome of this study contributes to cybersecurity by confirming the applicability and significance of the UTAUT2 for IoT technology acceptance in the consumer context. It also further tested UTAUT2 specifically for older adult usage of these technologies. IoT-enabled technology developers and healthcare providers pursued Internet-enabled capabilities and solutions without considering the constructs and relationships shown to predict adoption decisions [8,31,40]. Older adults experienced visual changes, decreased memory capabilities, and mobility changes that affected their ability and willingness to use technology [41,42,43,44]. This research on older adults’ adoption of Internet-enabled technologies is beneficial to IoT developers, implementers, and healthcare providers of IoT technologies for use in older adults’ homes [8,15,45,46].
The study has theoretical implications for cybersecurity in the prediction of older adults’ acceptance of IoT-enabled technologies and reducing the risk of solutions driven by technological and organizational capabilities rather than user needs and requirements [16,17,47]. This study specifically analyzed how performance expectancy, effort expectancy, social influence, facilitating conditions, hedonic motivation, price value, and habit influence older adults’ intention to use IoT-enabled technologies in their homes [8,31]. These socioeconomic dimensions are critically important to the information technology field because the actualizing of IoT-enabled technologies in private homes depends on older adults’ participation and adoption [30,37].
1.5. Research Questions
The objective of this research study was to validate older adults’ acceptance and use of IoT technology using the UTAUT2 from a consumer context. The research questions identified the predictors, or independent variables, of the outcome, behavioral intention to use, the dependent variable [30].
- Research Question 1: To what extent do performance, effort, influence, conditions, motivation, price, and habit affect older adults’ behavioral intent to use emerging Internet-enabled technologies in their homes?
- Research Question 2: To what extent does performance affect older adults’ behavioral intent to use emerging Internet-enabled technologies in their homes?
- Research Question 3: To what extent does effort affect older adults’ behavioral intent to use emerging Internet-enabled technologies in their homes?
- Research Question 4: To what extent does influence affect older adults’ behavioral intent to use emerging Internet-enabled technologies in their homes?
- Research Question 5: To what extent do conditions affect older adults’ behavioral intent to use emerging Internet-enabled technologies in their homes?
- Research Question 6: To what extent does motivation affect older adults’ behavioral intent to use emerging Internet-enabled technologies in their homes?
- Research Question 7: To what extent does price affect older adults’ behavioral intent to use emerging Internet-enabled technologies in their homes?
- Research Question 8: To what extent does habit affect older adults’ behavioral intent to use emerging Internet-enabled technologies in their homes?
1.6. Definition of Terms
This section provides definitions for each variable in the research questions, the constructs, and an operational definition of each [30].
Behavioral intent to use was a construct of the degree to which an individual would use a technology.
Conditions was the variable that measured the construct facilitating conditions as an ordinal interval on a Likert scale from 1 to 7, where 1 was strongly disagree and 7 was strongly agree [22,38].
Effort expectancy is the extent that a consumer found the use of technology easy [22].
Effort was the variable that measured the construct of effort expectancy as an ordinal interval on a Likert scale from 1 to 7, where 1 = strongly disagree and 7 = strongly agree [22,38].
Facilitating conditions was the construct in which consumers perceive the training, resources, and support were available to them to perform a behavior [22]. Prior research has shown that when modified by age and gender, facilitating conditions influences behavior intention to use technology for older women [38].
Habit was the construct defined as an outcome that was learned after a long period of extensive practice and was stored in long term memory to override other behavioral patterns [48]. Older men who were experienced with technology were less likely to use newer technology [38].
Habit was the variable that measured the construct of habit as an ordinal interval on a Likert scale from 1 to 7, where 1 = strongly disagree and 7 = strongly agree [48].
Health condition was a demographic variable for the participant to self-identify their health condition including excellent, very good, good, fair, poor/chronically ill, or terminally ill for determining inclusion/exclusion criteria.
Hedonic motivation was the construct of the extent to which consumers experienced enjoyment from or perceived the use of technology as fun [49]. In the consumer context, hedonic motivation was a more significant predictor of behavioral intention to use technology than performance expectancy.
Influence was the variable that measured the construct social influence as an ordinal interval on a Likert scale from 1 to 7, where 1 = strongly disagree and 7 = strongly agree [22,38].
Internet was a demographic variable to determine whether the participant had Internet access in their home.
Internet of Things extends the Internet, connecting it to people and physical environments through the distribution of uniquely addressed devices with embedded sensors, actuators, and the capabilities to receive or send data [1,2].
Motivation was the variable that measured the construct hedonic motivation as an ordinal interval on a Likert scale from 1 to 7, where 1 = strongly disagree and 7 = strongly agree [49].
Northern Virginia is more than 1300 square miles and borders Washington, DC, and Maryland [50].
Performance expectancy was the construct of the extent to which a person would benefit from using technology in performing an activity [22,38].
Performance was the variable that measured the construct of performance expectancy as an ordinal interval on a Likert scale from 1 to 7, where 1 = strongly disagree and 7 = strongly agree [22,38].
Price value was the construct of the extent to which consumers made a cognitive trade-off between the benefits of adopting technology and the cost of using it [51].
Price was the variable that measured the construct of price value as an ordinal interval on a Likert scale from 1 to 7, where 1 = strongly disagree and 7 = strongly agree.
Social influence was the construct of the degree to which consumers perceived that those persons vital to them believed that they should use a specific technology [22].
Use was the variable that measured the construct of behavioral intention to use as an ordinal interval on a Likert scale from 1 to 7, where 1 = strongly disagree and 7 = strongly agree [38].
1.7. Research Design
The research methodology for this study was a nonexperimental correlation of the variables that affect older adults’ behavioral intention to use emerging IoT-enabled technologies in their homes to increase safety, quality of life, and independence. This design was appropriate because IoT technologies, in the context of the research problem, were nascent, and according to the academic literature, none of the pilot studies reached real world capability [15,52]. This nonexperimental correlational survey determined the significant predictors of older adult intention to use IoT-enabled technologies in their homes.
To reflect the population accurately, of which 30% do not have Internet access, the researcher attempted to conduct online and in-person recruitment. Online recruitment occurred through SurveyMonkey™ and in-person recruitment was attempted with a senior community center to reach potential participants without Internet access. The goal was to recruit 70% of the participants online and the remainder in-person through informational meetings at the senior community center. However, the researcher was unsuccessful in obtaining persons who met the inclusion criteria of not having Internet service in their homes. Having already collected the online responses, the researcher noted that there were respondents who did not have Internet access in their homes and still responded to the online survey. Therefore, the researcher modified the recruitment strategy to be online only.
The research design used a stratified random sampling procedure. The population was stratified by location and age before selecting the sample to ensure that it reflected the proportion of the population [53]. The data were collected electronically via SurveyMonkey™ (Effective as of 1 July 2021, SurveyMonkey Inc. became Momentive Inc., Portland, OR, USA). The data were exported from SurveyMonkey™ and imported into the Statistical Package for the International Business Machines Corporation’s (IBM) Social Services (SPSS) version 24 software program, Armonk, New York, NY, USA. The basic design of this study was correlational with more than two independent variables and one dependent variable so the multiple regression statistical method was used [30,54].
1.8. Assumptions and Limitations
The assumptions and limitations of this research study stemmed from the specific target population, the theoretical philosophy on voluntary consumer acceptance of technology, and the UTAUT2 instrument used to test the hypotheses. The researcher made assumptions for this study regarding the selection of an appropriate theoretical perspective, participants’ familiarity with IoT devices, and accurate data analysis to answer the research question. The results of this study relied on an assumption of the researcher’s integrity because, although nonexperimental correlational designs include significant process rigor, a researcher could reject a null hypothesis inaccurately and thus skew the results [30].
1.8.1. General Methodological Assumptions
The researcher assumed that adopting a theoretical model based on a consumer behavior would better predict older adults’ behavioral intention to use IoT technologies than one developed for the business context, where adoption was involuntary, and the adopters had no cost burden. The researcher assumed that the validity and reliability of the model were valid in this study. The underlying research philosophy for this study was positivist. The ontological assumption of this study was realistic, seeking cause and effect in the real world. The researcher’s axiological assumption was value free. The epistemological premise of the study was that the researcher and participants were independent [30].
1.8.2. Theoretical Assumptions
The UTAUT2 assumes the people are responsible for incurring the cost of using technology and can independently choose to use it. The model assumes that performance expectancy, effort expectancy, social influence, facilitating conditions, hedonic motivation, price value, and habit with technology influences consumer behavioral intention and use behavior [38]. The theoretical model predicted that technology adoption and use were modified by age, gender, and experience. The theoretical framework of the UTAUT2 included the assumptions for multivariate linearity, normal distribution, and homoscedasticity [30].
1.8.3. Assumptions about Measures
The UTAUT2 used Likert ordinal interval scales from 1 to 7, where 1 = strongly agree, 4 = neither agree nor disagree, and 7 = strongly disagree. A preliminary linear regression was performed to check the assumptions of normal distribution, linearity, homogeneity of variances, and additivity [54]. Multiple regression/correlation statistical data analysis were conducted using the SPSS program to create a sampling plan, design a sample, and perform sampling. The strata for clustering were the demographic variable Internet (capturing whether the participant had it) and gender. The researcher sought a sample size of 300 to reach 0.95 statistical power, and the confidence intervals to detect a small effect size. Although multivariate modeling and multiple regression have statistical rigor for objective results, a researcher could reject a null hypothesis inaccurately and thus skew the results [30].
1.8.4. Assumptions on Participants
The methodological inference of the study was that the participants would answer truthfully, with enough qualifying responses to attain statistical power, and that the target population would grant permission for the study. The recruiting strategy included participants both with and without the Internet in their homes to develop a sampling frame in which every participant had an equal chance to be selected and the results were statistically significant. The study assumed that participants could read at the eighth-grade level in English [30].
1.8.5. Familiarity with IoT Devices
The researcher assumed that not all the target population would be familiar with IoT devices or their development and implementation to extend older adults’ ability to age at home longer. The researcher provided an explanation of the IoT and a vignette in video form of how these technologies help older adults. The researcher assumed that this would be enough information to provide participants with an understanding of the IoT to provide informed responses to the survey [30].
1.9. Limitations
The researcher identified the following weaknesses regarding this study.
1.9.1. Limitations of the Researcher
The researcher lacked extensive experience executing research studies and performing multiple regression. The researcher performed well in the statistical analyses coursework and strictly followed the guidance and methods. The researcher documented the steps in the dissertation research plan. Additionally, the research committee provided expert advice and recommendations to achieve validity [30].
1.9.2. Limitations of the Design
The research focused on the target population in a region of the eastern coast of the United States. This area is also part of a large metropolitan area where most older adults have Internet access in their homes. These facts made it challenging to obtain the appropriate number of participants without Internet access for the study and could limit the generalization of the results. The SurveyMonkey™ poll was limited to the metropolitan area on the east coast and initially had a 67% abandonment rate yielding only four valid responses. The SurveyMonkey™ support team contacted the researcher and recommended redistributing the survey to their panel partner, CINT. The results were a 77% completion rate and receipt of 517 responses. The researcher recruited participants online; however, the use of SurveyMonkey™ limited participants to those who work with the organization for online collection [30]. The UTAUT2 instrument used Likert scales to measure the constructs for behavioral intention to use technology. The research derived meaning from the numbers, but could not convey the perceptions, beliefs, or the context of participants [55,56]. The correlational nature of this study was limited because participants were exposed to the IoT technologies in an anecdotal rather than a realistic manner [30].
1.10. Delimitations
The research design was developed to specifically address delimitations that were identified in the literature review. The selection of the target population and how participants were recruited directly related to studies purporting to be related to older adults but, in reality, had few older adults or were sampled for convenience [57]. The inclusion of the question as to whether the respondent had Internet in their home was included with the demographic questions to ensure that these older adults were appropriately represented. Most of the academic studies on older adults’ acceptance of technology were administered online but did not include a question about Internet access at home. Additionally, the UTAUT2 was selected for its consumer context because most researchers used either the TAM or the UTAUT, which were developed for business use [58]. This study did not investigate actual use of IoT technologies, gender differences, or generational differences [30].
1.11. Organization of the Remainder of this Article
Section 2 provides a synthesis of the academic research findings from the study’s literature review on the IoT to age in place, technology acceptance models, IoT experimentation, and older adults’ acceptance of IoT. Section 3 details the methods and procedures of the execution of this study. This section necessarily mirrors some of the content included in Section 1 so that specific processes are understood by the reader and in the context of execution. More robust information regarding the population, the sample, inclusion/exclusion criteria, data collection, analyses, validity, reliability, and the ethical considerations of the study are provided. Section 4 presents the results of the study, including a detailed description of the sample, hypothesis tests, and a summary of the main statistical findings. Section 5 assesses whether the study addressed the research problem and provides an interpretation of the results in the context of previous findings in the field. The section also discusses the meaning of the findings and makes recommendations for future research opportunities [30].
2. Literature Review
In 2008, practitioners, academia, and researchers gathered for the first time to discuss the practical applications of IoT, experimentation results, and to brainstorm their ideas [59]. The academic research on IoT acceptance before 2011 was almost nonexistent and disjointed [60]. Researchers almost exclusively focused on technical implementations for various industries, surveys of progress, or reported experimentation results to industry inquiries [61,62]. Researchers focused on explaining consumer acceptance of technology using models and theories developed to predict user acceptance in a business context (e.g., TAM and UTAUT). The UTAUT2, which was designed to predict consumer adoption [38], was seldom used, and when it was, not all of the constructs were tested, such as price value. Because research on this topic was nascent, the researcher expanded the set of terms associated with the problem to discover adequate academic studies. This section describes the researcher’s search methodology, the theoretical orientation for the study, provides a literature review, a critical analysis of the findings, and a critique of the research methods employed in the studies [30].
2.1. Theoretical Orientation for the Study
The theoretical orientation for this research study was the UTAUT2 developed by Venkatesh et al. [49], who revised the original UTAUT [22] to apply to consumer situations. The researchers retained the constructs of performance expectancy, effort expectancy, social influence, and facilitating conditions, adding the constructs of hedonic motivation, price value, and habit [38]. They retained the moderating variables of gender, age, and experience from the UTAUT, but dropped the voluntariness moderator because consumer use is entirely by choice. The researchers added hedonic motivation (enjoyment) because previous research indicated that it was a critical factor in consumer use [49]. They added price value because consumers assumed the cost burden of purchasing the technology rather than businesses. The researchers added habit as a moderating variable because previous studies showed that it was a significant predictor of consumers using technology (as cited in [38]). Many of the studies evaluated in the literature review were experimental in nature, pilots, qualitative inquiries, or broadly categorized the technologies as IoT outside of the home environment. The researcher did not evaluate the actual use of IoT technologies.
The UTAUT2 contrasted former results, because hedonic motivation and price value were statistically significant in predicting consumer adoption over performance expectancy in the business realm. Of note concerning the study, price value and facilitating conditions were shown to significantly impact an older woman’s intention to adopt a technology [38]. Additionally, older men who had used the technology more regularly relied on their habitual experiences and paid less attention to new changes in the environment [30].
2.2. Review of the Literature
The researcher developed this literature review by analyzing the scholarly research focused on older adults’ technology acceptance, IoT developments for them to age at home longer, and the context in which researchers applied the theories. The focus of this study was older adults’ voluntary acceptance of IoT technologies in their home to realize the purported benefits. Not all older adults had Internet access in their homes, the latest smartphone, or tablet technologies [43,63]. Older adults may not have comprehended the price burden to purchase the services and technologies to enable their use. Older adults were growing faster than any other population group, were predicted to reach 71 million by 2030, and to overwhelm the healthcare industry due to insufficient assisted living infrastructures and healthcare professionals to support them [64]. The deployment of IoT into the healthcare industry resulted in a 41% increase in economic growth, the largest of any market, and was purported to allow older adults to age in their own homes longer, safer, and with more independence [15,23,63,65].
This section provides a review of the literature supporting the selected research design. First, the Internet of Things as a concept is introduced so that the reader may better understand how healthcare providers and developers experimented and piloted the technologies. The second section introduces the concept and research into aging in place. This section provides an overview of the academic studies using various technology acceptance models highlighting the misalignment of the research designs, studies on IoT and aging in place, explicit research with older adults to age in place, acceptance of IoT, and IoT adoption challenges. The third section synthesizes the academic research on applying IoT to age in place. Section four provides a critique of previous research. Section five provides a synthesis of the literature review [30].
2.2.1. The Internet of Things and Aging in Place
The introduction to Section 1 provided a high-level explanation of the Internet of Things (IoT). This section provides more details and context into the IoT as it relates to the technologies for older adults to age in their homes longer, increase safety, security, and maintain quality of life standards. The IoT is the concept that virtual and physical objects (e.g., refrigerators, stoves, and carbon monoxide monitors) have unique identifiers, are connected to the Internet, and communicate with each other [26,66,67]. In the context of aging in place, a human could also be connected to, and automatically communicate with, objects through a wearable or implanted medical device [68]. Heartbeat, glucose, respiration, or temperature monitors have been used to continuously monitor patient vitals and send that data to a cloud environment where a health practitioner could retrieve and analyze it [69,70,71].
In addition to objects and humans, the IoT connects animals, plants, buildings, automobiles, and scooters [72]. This ubiquitous communication enabled new healthcare solutions for aging adults, such as IoT-based rehabilitation, telemedicine, and activity tracking [73,74]. Sensors, actuators, networking, wireless, computers, and software were combined to collect, send, receive, process, and analyze data. These technologies combined with preventative healthcare were viewed as the optimal means to ensure that older adults remained healthy and active, supporting their independence [8,17].
The ratio of adults above the age of 60 to working age adults in the U.S. was increasing significantly, and organizations expect the total number of older adults to exceed the number of persons under the age of 18 by 2035 [75]. Researchers studying life expectancy across 35 countries reported that an increase in older adults would be a global reality [76,77]. If these predictions are correct, older adults will comprise 30% of the population and will likely continue to increase due to a consistent decline in population growth [75]. As people age, their vision, hearing, cognitive, and physical abilities may decline, which can contribute to unsafe conditions. These include wandering outside the home at night, forgetting to turn off the stove, falling in the bathroom, or tripping over an object.
The rapid growth of the aging population, their naturally declining health, and the increasing demand on healthcare providers spurred research into technologies that could be used by older adults to maintain independence, health, safety, and quality of life [73,74,77,78]. Researchers combined IoT technologies in different ways for older adults to monitor their home environments, provide safety alerts, communicate over the Internet, and overcome disabilities [21,74,78,79]. Virtual assistants such as Alexa, Amazon Echo, and Google Home enabled vision impaired persons to obtain news, set reminders, and communicate with others [80].
The academic literature on IoT solutions to age in place longer focused heavily on technologies, frameworks, and experiments driven by industry requirements (e.g., healthcare, or technical developers) rather than the needs of the older adults [70,71,74,81]. Several themes emerged from synthesizing the academic literature, which correlated some of the constructs of the UTAUT. These included effort expectancy, behavioral intention to use, performance expectancy, facilitating conditions, habit, and price value. Many researchers did not demonstrate an understanding of older adults’ characteristics and the barriers to their acceptance of technology. Older adults had less experience with and confidence in using newer technologies [82,83,84]. They preferred to continue using old, outdated technologies instead of adopting the newer [15,43,63,85]. Most of the IoT solutions proposed or experimented with required newer technologies and user familiarity with them [81,83,86,87].
In some cases, the older adults were physically unable to manipulate the technology. They required training, ongoing technical support, coaching, and experience with new technologies before they adopted [15,43,84,88]. Older adults who suffered from cardiovascular disease, heart failure, stroke, chronic illness, with a fall history, or diminishing capabilities were more willing to adopt new technologies to compensate as a perceived benefit [45,46,63,65,89]. Older adults were sensitive to the cost of new technologies, which was an adoption barrier [83,84,90]. Many of the researchers did not limit their target population to older adults, which made up a small percentage of the samples [39,45,74,91,92]. Finally, most of the researchers did not demonstrate an understanding of their chosen technology acceptance model’s designed context. Researchers investigated consumer adoption with corporate adoption models and vice versa [30,67,93,94,95,96].
2.2.2. Conflicting Technology Acceptance Models in Research
The main topic of this research was technology acceptance, and to investigate this problem one needed to assess technology acceptance theories. Research on technology acceptance began when different industries were looking to leverage computing in their business processes, which was a significant investment [97]. Employees were not familiar with the technology, and industries were hesitant to invest in computing that would not be adopted or used by personnel. Researchers lacking a technology acceptance theory turned to behavioral decision theory, or the study of decision-making, which was rooted in probability studies and risk taking psychology [98]. Researchers used the behavior decision theory, qualitatively and quantitatively. Businesses financed research to understand the cost and effort of adopting technology in their processes and to measure users’ perceptions of the involuntary technology, which led to the development of the technology acceptance model TAM [99]. Davis [100] eventually established the reliability and validity of the model, where perceived usefulness and perceived ease of use forecasted user intention to use technology in businesses. Since then, the TAM has been one of the most used models in predicting intention to use from the corporate and consumer perspective, although not designed for the later.
In 2003, Venkatesh et al. developed a unified theory that leveraged the contributions of many theoretical models developed up to that time. They evaluated each of these models, synthesizing them to develop the unified theory of acceptance and use of technology (UTAUT). However, the contextual focus was still on business organizations where technology acceptance is involuntary. The researchers developed, tested, and validated the survey instrument for reliability. The predictor variables were performance expectancy, effort expectancy, social influence to use technology, facilitating conditions, which represents training and support, and behavioral intention. The moderating variables were gender, age, experience with the technology, and voluntariness of use. The dependent variable of the model was use behavior. The researchers’ results indicated that performance expectancy, effort expectancy, and social influence of the users of the technology to improve their job effectiveness were direct predictors of intention to use from a business perspective. Many researchers have continued to use the UTAUT to predict consumer intention and adoption, even though it was designed to predict use in the business context.
The UTAUT was combined with the TAM and other theories by researchers, adding such constructs as personal innovativeness, device anxiety, ubiquity value, and cognitive feedback [101]. Regardless, the TAM and the UTAUT were developed and demonstrated as reliable for involuntary business situations. A recent survey of the academic literature on technology to assist older adults showed that more than 60% of the studies used no theory, 20% used the TAM, and 8% used the UTAUT [62]. A more recent and contextually appropriate theory was developed, and explicitly designed for voluntary consumer technology acceptance (UTAUT2).
From a theoretical and practical perspective, researchers used technology acceptance models and theories developed within a business environment to apply to noncorporate contexts with varying and conflicting results. Researchers studying technology acceptance used the UTAUT, UTAUT2, TAM, and qualitative discovery methods. The results were difficult to correlate because the researchers used a variety of constructs and often used a model or theory to predict technology acceptance out of the contextual environment for which they were developed. Researchers used the models inconsistently, resulting in variations of the predictors, as shown in Table 1 [30].

Table 1.
Synthesis of consumer contextual studies.
Researchers identified performance expectancy, effort expectancy, social influence, and habit as the most significant predictors, with habit identified as such in three studies, and the others occurred as significant in two studies. Findings for the second most influential predictors were just as varied as the primary. Additionally, only four of the studies included the construct, price value, and it was only significant in one. The variance in the findings provides a researcher with cause to scrutinize the research designs more closely.
Ain et al. [102] explored students’ acceptance of a learning management system (LMS) with the UTAUT2. In this study, the educational institution chose the learning management system and provided it to the students, who had no choice in purchasing the tool or using it. The researchers removed the price value construct and substituted learning value. Learning value and social influence were the most significant predictors of behavioral intention, followed by performance expectancy. A similar study by Nair et al. [106] using UTAUT2 showed that performance expectancy and habit were the most significant and positive predictors of behavioral intention. Researchers also reported that price value in the context of students’ fees was a significant predictor.
Magsamen-Conrad et al. [20] performed a UTAUT study investigating whether there were multigenerational differences in adopting tablet technology. Researchers developed the UTAUT for the business environment where acceptance of the technology is involuntary, and performance expectancy was the single most significant predictor to acceptance [16]. Magsamen-Conrad et al. [20] reported that the most significant generational differences to tablet adoption were effort expectancy, facilitating conditions, and performance expectancy, which were all significant in the UTAUT2, indicating that the researchers should have used the later. Gao et al. [104] investigated users’ adoption of wearable fitness technology using the consumer focused UTAUT2 and added a construct for risk. Although the researchers used a consumer-focused theory, they did not include the constructs of hedonic motivation, price value, or habit, which were significant predictors in the UTAUT2. They reported that participants’ perceived privacy risk had the most significant and negative impact on their behavioral intention to use the devices over social influence.
However, it had a positive statistical significance. Effort expectancy was a significant predictor, and consistently so when the technology was health related. This construct was the only one from the UTAUT2 that was not rejected and found to be significant in the study by Koivumäki et al. [91] on acceptance of databased preventative healthcare services. Koivumäki et el. did not test the construct price value because there was no known cost model for the healthcare services at the time of the study. As one might expect of an emerging technological market, many of the IoT solutions studied were technical proof of concepts or experimentations. Much of the academic research literature on IoT technology to help older adults age at home longer focused on IoT for human activity monitoring [2,71,81,107,108], remote healthcare [39,87,109], and the technical challenges caused by the implementation of IoT in these environments [25,30,110,111].
2.2.3. Explicit IoT Research for Older Adults to Age in Place
An increasing number of IoT technologies called smart home devices were in the consumer market explicitly designed for older adults. These included remote monitoring, automatic stove shutoff, voice activated assistants, smart phone applications to control lights, and emergency alert systems. Arthanat et al. [46] examined older adult ownership of these types of smart home devices. The researchers explicitly targeted the population of adults 60 years or older. Women ages 60 to 70 years old who had an impairment, fall history, and were experienced with technology were early adopters of the devices. The researchers reported that the IoT technologies promoted or used in experiments for older adults to age in place longer were the least desired by them. Older adults rejected remote home monitoring, using a smartphone to control appliances, motion activated cameras, voice activated assistants, and emergency alerting systems.
Conversely, they reported that a significant number of older adults in the study were using carbon monoxide alarms, manually programmable or automatic set thermostats, motion sensing lights, and backup generators. The results indicated that older adults who were concerned about safety were interested in purchasing water leak detectors, backup generators, and automatic shutoff technologies for the stove. However, they did not own these technologies at the time of the study. This study confirmed others in that older adults who perceived their independence or health declining were more likely to adopt the solutions to compensate for their condition [15,46,63,65]. The adoption of technology also presumes that the beneficiaries (older adults) will have Internet access in their homes or use a smartphone to go online [46,112].
Irizarry et al. [112] studied older adults’ perceptions of a health portal as a means for them to receive laboratory results, communicate with caregivers, and ask questions. The themes that emerged support many other studies. The researchers reported that older adults required training and support for technology (facilitating conditions). Many of the study’s participants stated they had little to no experience with computers and no Internet access in their homes. Although persons in the U.S. are increasingly using their smartphones to go online over in-home broadband [113], prior research showed that older adults held onto older technology longer than younger persons, as previously stated [15,63]. Seriously or chronically ill participants found the health portal convenient for obtaining lab results. Still, they felt their conditions were too complicated to effectively communicate with caregivers through secure messaging as the only means [112]. They perceived the portal as a poor substitute for direct interaction with clinical personnel.
Researchers reported that technology contributed to further isolation of older adults and less communication with the broader community in several studies [15,58,65,83,84]. Developers of IoT solutions for adults to age in place longer should consider the potential isolation caused by implementing remote monitoring sensors, pushing health portals as a single solution, and supplementing caregivers with autonomous robots. The Technology in Later Life study was designed to determine if there was a digital divide between rural and urban adults aged 70 and above in the U.K. and Canada [114]. This qualitative study found that facilitating conditions, access to technology, and security influenced older adults’ technology use. Detractors to technology use were apprehensions, lack of interest, and difficultly in learning how to use it [30].
2.2.4. Older Adults’ Acceptance of IoT to Age in Place
Cardiovascular disease, heart failure, stroke, chronic illness, a fall history, or diminishing capabilities were shown to positively influence older adults to adopt new technologies [45,46,63,65,89]. In the U.S., cardiovascular disease is the primary cause of death and rising healthcare costs for older adults, and as much as 30% were hospitalized again within a month [90]. Healthcare providers and researchers started investigating the use of mobile health capabilities for home based cardiac rehabilitation instead of the traditional center-based approach [90,115]. A center-based cardiac rehabilitation approach proved to play an essential role in preventing secondary cardiovascular disease events. However, more than 80% of the patients eligible for the services in the U.S. did not participate, and only 50% of the doctor referred patients participated [115]. Additionally, older adults were under referred and, a significant number of those who were, did not complete the rehabilitation sessions required.
In the European Union (EU), approximately 30% of cardiovascular disease patients received rehabilitative treatment, and few older adults willingly participated [88]. Many of the researchers purported that the home-based option would increase patient participation [104,106]. The academic literature discussed several ongoing trials and clinical studies [88,115,116]. For example, researchers in Australia published their trial results indicating that patients who used a smartphone-based home method were 30% more likely to participate in rehabilitation, and 32% more likely to complete the intervention as prescribed (as cited in [115]).
Researchers recently published results from a four-year observational study on cardiac rehabilitation in elderly patients across western Europe [117]. The researchers of the European Cardiac Rehabilitation programs in the Elderly (EU-CaRE) assessed the effectiveness of cardiac rehabilitation centers in eight European Union countries for adults 65 years and older. The research design included patients who declined traditional cardiac rehabilitation and randomly assigned to either the experimental group or the control group. The experimental group received personalized in-home mobile cardiac rehabilitation, and the control group received no intervention [88]. The in-home cardiac rehabilitation approach included a smartphone, heartrate monitoring, and coaching. Results indicated that after six months of the in-home rehabilitation, older adults’ vitals and health significantly improved as compared to those in the control group who received no rehabilitative care [117]. These results indicated the importance of understanding older adults’ perceptions of the proposed solutions [30].
2.2.5. IoT Adoption Challenges
The most prominent barrier to adopting IoT technologies to age in place was that most researchers approached the subject from the perspective of healthcare providers or technologists [71,81,107,108,118]. The academic literature showed that older adults were reluctant to change to newer technologies [63,85,119], lacked sufficient experience [41,82,83,84], required extensive support [15,41,43,84,88], and resisted adoption unless they were seriously ill, impaired, or suffered a chronic illness [45,46,63,65,89]. These findings indicated that as their health declined, older adults were more inclined to adopt and use newer technologies, regardless of their experience with it, knowledge of it, and the associated risks. Sixty-seven percent of older adults fell victim to an online scam, malicious software, or a hack [120]. The most common and successful attack vector used by adversaries was through people [121]. These facts raise ethical considerations and concerns that healthcare providers, IoT researchers, and developers should recognize and dealt with [30].
The academic literature on IoT solutions to age in place longer focused heavily on technologies, frameworks, and experiments driven by industry requirements (e.g., healthcare or technology developers) rather than the needs of the older adults [2,70,71,74,81]. Solutions driven by technological and organizational capabilities, and developed without user involvement will not likely meet their needs and requirements [16,17,47]. In addition, the researchers focused on technical solutions neglected the social issues of increased isolation and exclusion [14,85,119,122,123]. A few recent research efforts specifically focused on involving older adults in the development and design of IoT solutions to counter this barrier to adoption [41,42,124].
2.3. Synthesis of Research Findings
Older adults with an impairment, fall history, cardiovascular disease, heart failure, stroke, chronic illness, or experienced with technology were more willing to adopt new technologies to compensate [45,46,63,65,89]. Older women with those experiences were early adopters of the devices [46]. IoT solutions built on newer technologies were the least preferred by older adults to age in place longer. They rejected remote home monitoring, smartphones, apps to control appliances, motion activated cameras, voice activated assistants, and emergency alerting systems. They preferred to continue using old, outdated technologies instead of adopting the newer [15,43,63,85,125]. Most of the IoT solutions proposed or experimented with required newer technologies and user familiarity with them [81,83,86,87].
Most of the technical, experimental, and pilot solutions proposed or studied appeared biased that older adults would find the IoT technologies beneficial, and would accept them without hesitation [26,71,126]. Older adults required training, technical support, and coaching with new technologies before they adopted [15,43,84,88]. The high cost of new technologies was shown to be an adoption barrier [83,84,90]. Most of the researchers did not properly align the technology acceptance model with the use case of their study, and many did not explicitly limit their target population to older adults [45,74,91,92].
Older adults concerned about safety were interested in purchasing water leak detectors, backup generators, and automatic shutoff technologies for the stove [46]. Older adults experiencing health decline or a loss of independence were more likely to adopt the solutions to compensate for their condition [15,46,63,65]. These findings confirmed that effort expectancy, performance expectancy, facilitating conditions, habit, and price value are significant and consistent predictors of older adults’ behavioral intention to use technology. The findings legitimized the methodological strengths of this study using the UTAUT2, explicitly recruiting older adults as the target population, and including participants who did not have Internet access in the home [30].
2.4. Critique of Previous Research Methods
The academic literature showed that researchers used models and theories that did not align with their research problem, target population, or context. There were numerous instances where researchers used the business focused UTAUT and TAM in consumer studies and the consumer focused UTAUT2 in business studies [19,67,94,96,127]. There were numerous weaknesses with respect to the measures, population, sample, recruitment strategies, and ethics that resulted in misaligned research designs [30].
2.4.1. Appropriateness of Measures
It was difficult to evaluate the appropriateness of some of the measures, because many of the researchers used technology models out of context, did not consistently use all the variables, and combined other variables. Those studies that used the UTAUT2 in the correct context had Cronbach’s and not less than 0.30, indicating internal reliability [32,54,92,103,125]. The validity of the UTAUT2 was established [31], but several researchers added new constructs to the model, requiring them to conduct pilot studies to ensure the validity of the new models [92,103,125]. A recently developed new theory specifically explained whether older adults would adopt smart technologies to compensate for declining health or environmental concerns. The theoretical model developed by Golant [65] proposed four predictors to adoption, although it has not been tested for reliability or validity. The predicters were (1) the stress level of the person, (2) their resilience level, (3) external information sources, and (4) internal information sources [30].
2.4.2. Population and Sample
Researchers purporting to measure older adults, as a specific target audience, did not exclusively include them in the study, or they made up a small portion of the participants [2,81]. More broadly speaking, most studies on technology acceptance had few older adults as participants [45,74,91,92,103]. Some researchers weakened the generalizability of their study because they performed a convenience or purposive sample [32,46,95,112,125]. This is a type of nonprobability sampling and is the least reliable of all the techniques [128]. Some authors cited this approach as appropriate because they incorrectly viewed their study as exploratory [105]. Researchers developed IoT solutions for remotely monitoring older adults, but did not test them with this population [2,70,71,81,86]. Other researchers did not ensure the proportionality of socioeconomical and gender status in their samples [15,84].
2.4.3. Recruitment Strategy
With the exception of qualitative studies [63,83,129], most researchers only recruited participants online through alumni associations and elder specific venues [21,42,74,93,114]. A small number of those that did recruit online included a question to determine if participants had Internet access in their home [46,112], which is important because IoT solutions to age in place require it, and it is an additional cost burden to the consumers [30].
2.5. Summary
The literature clearly indicated that for older adults to accept IoT technologies to age in place, they would require extensive training and practice, or facilitating conditions [82,83,84]. It was also clear that despite their rejection of new technologies, as adults age and experience diminished physical, mental, and visual acuity, they tend to adopt technology to compensate, performance expectancy [15,42,43,44,63]. Most of the IoT solutions proposed required newer technologies and users to be familiar with them [81,83,86,87].
Most of the technical, experimental, and pilot solutions that were proposed or studied appeared biased that older adults would find the IoT technologies beneficial and would accept them without hesitation [26,71,126]. The high cost of new technologies was shown to be an adoption barrier [83,84,90]. These findings confirm that most appropriate model for studying older adults’ adoption of IoT technologies to age in place longer is the UTAUT2. It was important to ensure that older adults with and without Internet were included in the study because those that did not have Internet access would have to purchase it before they could implement IoT solutions in their home. The literature also demonstrated a significant difference in the results of studies that explicitly sought older participants and those that did not. Because older adults with a terminal illness or mental disorder were more vulnerable than others were, they should not be able to participate in the study [30]. Section 3 builds upon the findings of this literature review and details the research methodology design.
3. Methodology
This section discusses the statistical power of the study, the validity, and the reliability of the instrument. The researcher provides specific details on how participant recruitment, the selection criteria, how she collected, protected, and analyzed participants’ data. Finally, this section discusses the ethical considerations taken in planning and executing the study.
3.1. Purpose of the Study
The purpose of this study was to determine the extent to which performance expectancy, effort expectancy, social influence, facilitating conditions, hedonic motivation, price value, and habit affect northern Virginians’ behavioral intention to use emerging IoT technologies in their homes. Much research on the acceptability of IoT-enabled technologies for older adults to age at home longer focused on developer requirements, technical requirements, and organizational requirements. There was little research on the aspects of acceptability, consumer experience, price, and usability. As demonstrated in the literature review, most researchers did not specifically seek out the older adult population in their designs or attempt to include older adults without the Internet in their homes.
This research tested the UTAUT2 within the context of older adults’ acceptance of IoT technologies in their homes and determined the extent to which there were significant relationships. The researcher selected the target population to ensure that potential participants without the Internet in their homes could participate in the study. The researcher provided a scenario video and transcript that demonstrated how the industry envisioned using the technologies, and the costs participants would incur. The survey presented a cost estimate of implementing IoT technologies in their homes. This study sought to fill the gaps identified in the literature review, to purposely target older adults, appropriately use the UTAUT2 in a consumer context, and include adults without Internet in their homes so that the results would be generalizable to the public [30].
3.2. Research Hypotheses
The objective of this research study was to validate older adults’ acceptance and use of IoT technology using the UTAUT2 from a consumer context. The research questions identified the predictors (independent variables) of the outcome, behavioral intention to use (dependent variable). All hypotheses were annotated with an “H” and then a subscript of either “0” for the null hypothesis or an “A” for the alternate hypothesis [30].
Hypothesis 10.
Performance, effort, influence, conditions, motivation, price, and habit will not have a statistically significant relationship with older adults’ behavioral intent to use Internet-enabled technology in their homes.
Hypothesis 1A.
Performance, effort, influence, conditions, motivation, price, and habit will have a statistically significant relationship with older adults’ behavioral intent to use Internet-enabled technology in their homes.
Hypothesis 20.
Performance will not have a statistically significant relationship with older adults’ behavioral intent to use Internet-enabled technology in their homes.
Hypothesis 2A.
Performance will have a statistically significant relationship with older adults’ behavioral intent to use Internet-enabled technology in their homes.
Hypothesis 30.
Effort will not have a statistically significant relationship with older adults’ behavioral intent to use Internet-enabled technology in their homes.
Hypothesis 3A.
Effort will have a statistically significant relationship with older adults’ behavioral intent to use Internet-enabled technology in their homes.
Hypothesis 40.
Influence will not have a statistically significant relationship with older adult’s behavioral intent to use Internet-enabled technology in their homes.
Hypothesis 4A.
Influence will have a statistically significant relationship with older adults’ intent to use Internet-enabled technology in their homes.
Hypothesis 50.
Conditions will not have a statistically significant relationship with older adults’ behavioral intent to use Internet-enabled technology in their homes.
Hypothesis 5A.
Conditions will have a statistically significant relationship with older adults’ behavioral intent to use Internet-enabled technology in their homes.
Hypothesis 60.
Motivation will not have a statistically significant relationship with older adults’ behavioral intent to use Internet-enabled technology in their homes.
Hypothesis 6A.
Motivation will have a statistically significant effect on older adults’ behavioral intent to use Internet-enabled technology in their homes.
Hypothesis 70.
Price will not have a statistically significant relationship with older adults’ intent to use Internet-enabled technology in their homes.
Hypothesis 7A.
Price will have a statistically significant relationship with older adults’ behavioral intent to use Internet-enabled technology in their homes.
Hypothesis 80.
Habit will not have a statistically significant relationship with older adults’ behavioral intent to use Internet-enabled technology in their homes.
Hypothesis 8A.
Habit will have a statistically significant relationship with older adults’ behavioral intent to use Internet-enabled technology in their homes.
3.3. Research Design
The methodology used for this study was a nonexperimental correlation of the variables that affect older adults’ intention to use IoT-enabled technologies in their homes and to age in place longer. In this context, older adults would elect to purchase the technologies or not. Venkatesh et al. [38] developed the UTAUT2 to assess the factors influencing consumers to adopt technologies. The literature review demonstrated that the most appropriate design for this study in a consumer context was the UTAUT2 with an explicitly targeted older adult population. Because IoT-enabled technologies are relatively nascent, the researcher provided a video and its transcript to the participants explaining the IoT and how they could benefit from its use. The video/transcript presented a scenario of how a daughter used IoT technologies to help her 77-year-old mother be safer, healthier, and more independent despite the distance between them. In this study, the researcher chose to exclude the modifying variables, gender, age, and experience, and use behavior. The literature review demonstrated that regardless of gender, as persons age and experience sickness or limiting factors, they are more likely to adopt technology. The target population for this study was older adults, and the researcher did not assume respondents would have any experience with the technology or that they used it. The researcher adapted the construct relationship model for this study in Figure 1 from the original UTAUT2 [30].
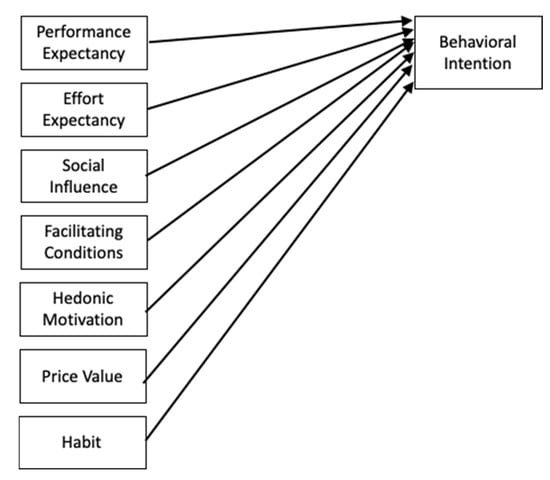
Figure 1.
Construct relationship model for the study. Note. Adapted from “Consumer Acceptance and Use of Information Technology: Extending the Unified Theory of Acceptance and Use of Technology” by V. Venkatesh, J. Y. Thong, and X. Xu, 2012, MIS Quarterly, 36(1), pp. 157–178. Copyright © 2012, Regents of the University of Minnesota. Adapted with permission.
3.4. Target Population and Sample
Pew Research Center estimated that 30% of older adults in the U.S. did not have Internet access [4]. To reflect this in the study, the researcher developed a two-pronged approach to recruitment: online and in-person. The researcher partnered with a senior community center and received permission to work with the site. The goal was to recruit 30% of the participants (those without Internet) in-person at the senior community center through informational meetings and the remainder online. The researcher received permission from the senior community center to perform in-person recruiting [30].
3.4.1. Population
Northern Virginia had more than 2.5 million people. Sixty-two percent of the residents had a Bachelor’s degree or higher, which is almost double the U.S. national average [50]. From an ethnicity perspective, nearly half of the residents were minorities. Fifty percent of northern Virginia’s population were females, and adults over the age of 65 represented 15% of the total population [50]. At the state level, 18% of Virginians did not have broadband Internet subscriptions in their homes [130]. Because of northern Virginia’s robust infrastructure and proximity to Washington, DC, the researcher expected the number of northern Virginia residents without Internet in their homes to be lower than the state average [30].
3.4.2. Sample
The inclusion criteria were adults ages 60 years and older, living in a personal residence in the northern Virginia area. The exclusion criteria were persons under the age of 60; in hospice or 24-hour care; terminally ill; those diagnosed with a mental health condition; and those refusing the informed consent form. The online instrument was developed with logic so that the survey would automatically end if the person met any of the exclusion criteria or did not meet all the inclusion criteria. The researcher launched the study and obtained some responses; however, the SurveyMonkey™ Audience support team contacted the researcher due to a high abandonment rate. The support team recommended using their panel partner Cint, based on the target population of the study.
The in-person recruitment activities and materials targeted potential participants who did not have the Internet in their homes. However, the researcher was unsuccessful in recruiting potential participants without the Internet in their homes in the Washington DC metropolitan area. Having already collected the online responses and screened the data, the researcher noted that there were respondents who indicated that they did not have Internet access in their homes and still participated in the online survey. Therefore, the researcher modified the recruitment strategy to be online only and released a third survey with Cint through SurveyMonkey™. The study collected some demographic data but did not use that data to focus on a specific group. The basic design of this study was correlational with more than two independent variables and one dependent variable, so the multiple regression statistical method was appropriate [54]. The researcher chose the sample size to result in a 95% statistical power with a small effect [30].
3.4.3. Power Analysis
The researcher calculated the sample size with G*Power a priori for multiple linear regression where α = 0.05, the statistical power was 0.95, a small effect size (0.15), and yielded a minimal sample size of 153 participants [131]. However, statistical regression has the potential to produce ungeneralizable results, and a researcher should have 40 cases per independent variable, which in this study would determine the sample size to be 280 [132]. The first survey had a 74% abandonment rate, a 14% disqualification rate, and many of the responses were incomplete. After conferring with dissertation committee members regarding the probability of obtaining enough valid responses, the researcher increased the sample size to 300 [30].
3.5. Procedures
This study used a sample of older adults in northern Virginia to analyze the statistical significance of the UTAUT2 instrument’s constructs, which influenced older adults’ adoption of IoT-enabled technologies to age at home longer. The survey included a video and transcript explaining the IoT and how it helped older adults live independently longer, and safer. The study presented recruits with an informed consent form, and they had to click on a consent button before they could progress to the demographic questions. The researcher developed the questionnaire with a logic that it terminated if the recruit did not click on the consent button. The researcher collected the data electronically by exporting it from SurveyMonkey™, and importing it into the Statistical Package for the Social Services (SPSS) software program version 24 for multiple regression analysis [30].
3.5.1. Participant Selection
The solicitations for the study’s participants targeted the area’s adults who were 60 years and older. Several procedures were employed to ensure the validity of the response. The first validation mechanism presented to participants before the survey was the informed consent form. If the participant clicked on the “I consent” button, then they progressed to the demographic and survey questions. If they clicked on the “I do not consent” button, then they were redirected to the disqualification page. The second validation mechanism was the demographic portion of the survey itself. If the participant indicated that they were younger than 60, terminally ill, living in an assisted living facility, or diagnosed with a mental health disorder, then they were redirected to the disqualification page and unable to proceed to the survey. The researcher made these selections in the “Design Survey” section of SurveyMonkey™. A researcher would, for example, enter the question, format it (e.g., multiple choice), and under the “Options” menu, check the box to require an answer. It is the researcher’s responsibility to ensure that every question for which he wishes to collect data requires a response. Otherwise, the results will be inconsistent and the dataset of little use. For questions relating to the inclusion and exclusion criteria, the researcher would navigate to the “Logic” menu and for each of the answers under the column “If answer is” to the disqualifying question in the multiple choice and select “Disqualification Page” under the column “Then skip to” and click the Save button [30].
After the initial 74% survey abandonment rate and change to the Cint audience, the rate decreased to 41%, and the completeness of the surveys increase proportionately. The disqualification mechanisms were put in place to protect potentially vulnerable participants, such as terminally ill or mentally disabled persons. The rationale for these exclusion criteria was that research has shown that older, disabled, and persons needing care demonstrated a significantly higher intention to adopt technology than healthy persons did [30]. As humans age, they are less likely to use technology unless it can specifically address a health issue or improve their declining physical acuity [20,44].
3.5.2. Protection of Participants
The researcher considered the protection of the participants throughout the research design to ensure the ethical and fair treatment of all potential respondents. Beginning with the recruitment strategy, the researcher provided that older adults could take part in the study, whether they had Internet access or not so that the research and the results would not contribute to the digital divide, but would ensure equality of access [14,123]. Additionally, this approach made the study’s findings generalizable to the broader population, unlike prior research on this topic [32,67]. Previous studies did not include participants without Internet access in their homes, ignoring about 10% of the population [58,133]. The researcher did not induce likely respondents into participation. The survey collected background and demographic data, such as education level, age, gender, and relationship status to screen potential participants; however, it did not collect personally identifiable information (PII). This ensured that the participants’ privacy and anonymity were preserved throughout the data collection process. Potential participants chose their subjective health status (e.g., poor, fair, good, very good, or excellent). They indicated whether they had a chronic illness [63], which was a strong predictor of technology adoption [39]. For this reason, the researcher did not exclude persons with poor health or chronic illness from the study. Persons in hospice, 24 hour care, or who were terminally ill were not permitted to participate in the survey to protect these vulnerable individuals [30].
3.5.3. Data Collection
The researcher adapted the UTAUT2 survey [38] with the author’s permission, changing the technology from mobile to IoT-enabled technologies. The online instrument presented an informed consent notification page to respondents, and they had the option to accept or reject the terms. Respondents who agreed to the consent terms continued onto the demographic questions, but those that did not accept consent were disqualified and unable to continue. If the respondents did not meet any of the exclusion criteria and met all the inclusion criteria, then they continued onto the survey. This functionality was accomplished by adding logic with the SurveyMonkey™ tools. Demographic questions included fields to validate inclusion and exclusion criteria and all questions required an answer. No person associated with this study stood to benefit from it, and there was no conflict of interest related to it. Before the data collection began, the researcher established full disc encryption on an external hard drive where the data were to be stored. The researcher made a copy of the dataset on a compact disc in case of file corruption [30].
3.5.4. Data Analysis
The researcher exported the survey data from SurveyMonkey™ into a Microsoft Excel file, which did not contain PII, as SurveyMonkey™ did not collect that data. The researcher imported the data into SPSS. The data were continuous, not categorical, and the research questions were looking for relationships between the variables, rather than differences. As there was more than one independent variable assessed to explain relationships, multiple regression was the most appropriate statistical method [54,134]. The researcher performed exploratory analysis and created several graphical charts to test the assumptions of multicollinearity, linearity, multivariate normality, and homoscedasticity. A scatterplot of the standardized residuals against the predicted values was performed to test the assumptions of linearity and homoscedasticity. A P–P plot of regression standardized residuals was used to interpret the cumulative probability of the variables against normal distribution, testing normality. Finally, the Durbin–Watson statistic was used to test for independent residuals. With the assumptions met, the researcher fit the model and performed the final statistical analysis [30].
3.5.5. Descriptive Statistics
The mean (M) was the statistical model used to summarize the data. To calculate the mean, the sum of the Likert scores measured for each variable are divided by the number of records, resulting in the average score for that variable, or the measure of central tendency [54]. The mean value is hypothetical, and as such, the linear model does have some error. The error is referred to as standard deviation (SD), which is a measure of the degree of a variable’s deviation (error) from the mean. A small SD indicated that the value was close to the mean, and a larger SD indicated the variable was further from the mean.
Multiple regression was performed with seven predictors and one outcome variable. The predictors were performance, effort, influence, conditions, motivation, price, and habit. The outcome variable was behavioral intent to adopt technology. The correlation matrix contains the Pearson correlation coefficient of every pair of variables. The coefficients measure the relationships between the predictor and the outcome variables. The coefficient of determination, , is the correlation coefficient squared, and is a measure of the variability of the predictors on the outcome variable. The adjusted provided the researcher with an indication of how well the linear model generalized, and the closer and adjusted were, the more generalizable the model. The F-statistic represents increments of improvement in the model’s ability to predict the outcome. The measurement for determining which independent variables were the most important was the standardized beta for each, where the high betas were the most important predictors [134]. Table 2 shows the correlations between the constructs and demonstrates the instrument’s reliability to measure what the researchers intended it to [38].

Table 2.
Construct correlations indicating instrument reliability.
3.5.6. Hypothesis Testing
This study used a statistical linear model to predict the outcome (i) from the predictor variables (X). In the equation shown below, the b-values quantify the relationship between the outcome (use) and each predictor variable (X). In the equation, is the value of the outcome when the predictor equals zero.
Having fit the linear model to the observed data, one can estimate the parameters (b) using the ordinary least squares regression [54]. The F-statistic represents the variance in the model compared to the error in the model. SPSS calculates the F-statistic by dividing the mean sum of squares by the degrees of freedom. One uses the F-statistic to calculate the significance of the coefficient of determination (R2) using the equation below, where N was number of participants, and k was the number of predictors. The resulting F-statistic tests the null hypotheses that R2 equals zero.
3.6. Instrument
The instrument used in this study consisted of 32 multiple choice questions, and a seven-point Likert scale from 1 = strongly agree, 2 = agree, 3 = somewhat agree, 4 = neither agree or disagree, 5 = somewhat disagree, 6 = disagree, and 7 = strongly disagree [38]. The survey collected demographic data from participants, including zip code, gender, age range, education, living conditions, relationship status, health condition, Internet service, and mental health disorder.
The researcher obtained permission to modify and use the UTAUT2 instrument from the author, and changed the technology from “mobile Internet” to “IoT-enabled devices” [38]. The researcher added a video and a transcript to explain to participants how the IoT could be used to age in place. In this way, each participant had a basic understanding of the technology before completing the survey questions. The researcher also added an explanation of the services and costs associated with adopting IoT in the home. Table 3 lists the instrument’s constructs, variable measurement, type, and the number of questions on the survey. Appendix A provides the complete instrument used in this study [30].

Table 3.
Instrument data collection details.
3.7. Ethical Considerations
Every researcher must address the ethical considerations of studying human beings to ensure that they treat persons with respect, justice, and beneficence [135]. Older adults considering the procurement of IoT technologies to age in place present researchers with some unique ethical challenges they should not ignore. Older adults required more training and practice with new technologies than younger people, and most of the IoT solutions to age in place longer required more modern technologies like a smartphone, Raspberry Pi, or tablet [81,90]. The IoT solutions required Internet access, but few researchers attempted to recruit older adults without the Internet in their homes. Most researchers seemed to assume that older adults would accept solutions as they were developed and purchase Internet access to age in place [71]. Older adults typically had a fixed income, and the cost burden for these solutions was on them. This research design specifically sought to include older adults without Internet access. This study focused on a consumer context, so the researcher used the UTAUT2 model.
Older adults were late adopters of new technologies, and research showed that they were more willing to adopt if they suffered a fall, were sick, had declining abilities, or wanted increased safety [15,63]. The instrument presented each participant with a consent form describing the purpose of the study, how their responses would be used, and protected. If a participant did not agree to the consent form’s conditions, indicated they were terminally ill, or had a mental health disorder, they were automatically taken to a disqualification page and not permitted to complete the study. The demographic questions did not ask for any personally identifiable information (PII), and SurveyMonkey™ did not provide any in the results. Each participant’s identity was protected because PII was not obtained or associated with completed surveys. The demographic data collected did not have any unique characteristics that linked to one individual.
Every participant received the same introduction video and transcript describing the IoT and a scenario on how it would help older adults age in place longer. The survey also explained what an Internet Service Provider was and the associated monthly costs should they procure such services. Persons participated regardless of whether they had experience using the technologies or not. The Capella University Institutional Review Board (IRB) approved the informed consent form, survey, and demographic questions. Responses collected in this study were kept on an encrypted external hard drive and were only shared with the researcher’s mentor as required by the program [30].
4. Results
This section presents the descriptive statistics of the sample, the statistics performed to test the hypotheses, and the results to answer the research questions and test the associated hypotheses.
4.1. Description of the Sample
Participants for the study were recruited from the northern Virginia area, which is more than 1300 square miles and borders Washington, DC, and Maryland [50]. In this region, persons 65 years or older make up 11% of the total population [130]. The researcher obtained the sample from SurveyMonkey™ and specifically targeted the region. The survey collected the age range, gender, educational level, living conditions, general health conditions, and whether the respondent had Internet access in the home. Three-hundred responses were purchased from SurveyMonkey™ to retrieve a sufficient sample, and 517 responses were stored on an external hard drive enabled with full disc encryption. Some of the survey questions were used to exclude those persons who attested to having a mental health condition, terminal illness, or were under the age of 60. Data screening was performed according to the methodology described in Section 3, eliminating the records that were missing data in the survey. The survey presented the informed consent to participants first. If the participant did not consent then they could not continue to answer the demographic questions; however, an incomplete record was still created. The second section of the survey presented demographic questions. They included additional exclusion and inclusion criteria questions such as age, living conditions, having a mental health condition, or terminal illness. After screening the responses against the inclusion and exclusion criteria, the final sample consisted of 316 responses. Multiple regression was performed using the SPSS software version 24 to determine the extent to which there was a relationship between the constructs of performance expectancy, effort expectancy, social influence, facilitating conditions, hedonic motivation, price value, habit, and behavioral intent to use IoT technology. The survey divided the age ranges into three categories and provided an “other” fill in the blank field. Sixty-two percent of the respondents were in the age range of 60 to 69 years.
Appendix B displays the data collected on the sample. These data were used to provide an additional layer of screening to ensure no vulnerable participants were included in the study and that each participant met the inclusion and did not meet the exclusion criteria. Sixty-two percent of the respondents were between 60 and 69 years old, 34% were 70 to 79 years old, and 4% over the age of 80. Sixty-three percent of the respondents were females, which was slightly higher than the U.S. average of 56% [130]. More than 40% of the respondents had a bachelor’s degree or higher, consistent with this region’s residents [50], but higher than the national average of 31% [130,136]. Twenty-six percent of the respondents had some college education, but no degree. The distribution of the respondents’ reported living conditions demonstrated that no respondents resided in assisted living facilities. The survey was modified with permission to inquire whether respondents had Internet access in their homes, but excluded any question related to their experience with IoT technologies to age in place. More than 90% of the sample had in-home Internet services consistent with the northern Virginia region at 93% [50]. The final demographic variable the researcher collected on respondents was relationship status. More than 50% were married, 15% widowed, 18% divorced, 13% single, and 3% single, but cohabitating with another person.
Table 4, the frequency table of respondents’ mental health conditions, showed that no respondent disclosed having a mental health disorder. All participants in the study met the inclusion criteria and did not meet any of the exclusion criteria [30].

Table 4.
Frequency table for mental health disorder.
4.2. Hypothesis Testing
The section describes the researcher’s process for interpreting the results of the analysis and hypotheses testing. The researcher performed multiple linear regression in SPSS version 24 to perform the analysis. The assumptions of multicollinearity, normality, linearity, and homoscedasticity to fit the linear model were tested. It is critical that the assumptions are met because if they are not, bias would be introduced into the analysis and skew the results, resulting in an inaccurate rejection of the null hypotheses [30].
4.2.1. Multicollinearity
The model measured each construct using several questions in the survey. If two of the predictors were perfectly correlated, then it was not possible to determine how much of the variance each represented [54]. To meet the assumption of multicollinearity, the predictor variables should not correlate r ≥ 0.80, and the correlations between each predictor variable and the dependent variable should be r ≥ 0.30 [54]. The correlations between the predictor values were below 0.80 and the correlations between the independent variables and dependent variable were greater than 0.30. The data met the assumption of multicollinearity [30].
4.2.2. Linearity and Homoscedasticity
The researcher checked the assumptions of linearity and homoscedasticity together by interpreting an SPSS plot of the standardized residuals (ZRESID) against the predicted values (ZPRED). The data were not curved, were in the center of the chart, and generally made the shape of a square [54]. The data met the assumptions of linearity and homoscedasticity as shown in Figure 2 [30].
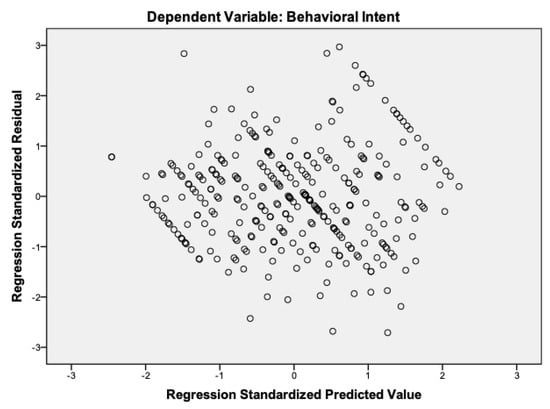
Figure 2.
Scatterplot of the standardized residuals against predicted values.
4.2.3. Normality
The parameter estimates for normal distribution were tested by interpreting a chart of the cumulative probability of the variables against that of a normal distribution, known as a P–P plot and shown in Figure 3. The chart was generated by the SPSS program. The data were close to zero, indicating normality [54].
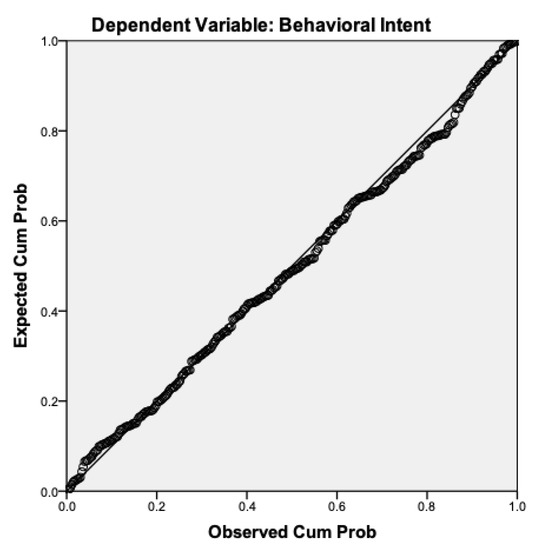
Figure 3.
Normal P–P plot of regression standardized residuals.
4.2.4. Independent Residuals
The Durbin–Watson statistic was used to test that the residuals’ values were independent. The statistical measure from this test can range from zero to four, and for this assumption to be met, the value should be close to two [54]. As the number of predictor variables affects the size of the Durbin–Watson statistic, the resulting statistic should be greater than one or less than three. The model’s Durbin–Watson statistic was 1.641 as shown in the SPSS output in Table 5 and the analysis met the assumption criteria. The statistical analysis data were used to determine that the assumptions were met, which indicated that the model could continue being evaluated and the results interpreted to accept or reject the null hypothesis. The was the variance that the predictors explained in the linear model. The F statistic measured the effect of variation relative to unmeasured factors in the linear model. The probability (p) was the value of obtaining an F result at least as large as the observation if the null hypotheses were true [54].

Table 5.
Model summary b.
SPSS was used to calculate the summary statistics, means, standard deviations, minimum, maximum, skewness, and kurtosis for performance expectancy, effort expectancy, social influence, facilitating conditions, hedonic motivation, price value, habit, and behavioral intent to use as shown in Table 6.

Table 6.
Summary statistics.
SPSS was also used to determine the reliability of each research variable by evaluating the Cronbach’s alpha (α) coefficients, where a value greater than 0.7 is acceptable [54]. The constructs had good reliability as shown in Table 7 where all were higher than 0.8.

Table 7.
Reliability results.
4.2.5. Summary of Hypothesis Testing
The correlation matrix was calculated among the research variables using SPSS and all were statistically related at the p < 0.001 level as shown in Table 8.

Table 8.
Correlations among research variables.
To understand whether two variables are correlated and the effect size, the researcher used the resulting correlation coefficients to accept or reject the null hypotheses as summarized in Table 9 and discussed in detail by research question and the associated hypotheses. The correlation coefficients are the effect size. Performance, social influence, facilitating conditions, hedonic motivation, price value, and habit were statistically significant in predicting older adults’ behavioral intention to use IoT-enabled technologies in their homes.

Table 9.
Linear regression results.
4.2.6. Hypothesis 1 Results
The SPSS results of the linear regression model revealed that the seven predictors cumulatively influenced older adults’ behavioral intent to use IoT-enabled technologies, F(7, 308) = 133.50, p < 0.001, R2 = 0.75. The model explained approximately 75% of the variability in older adults’ behavioral intention to use Internet-enabled technologies by performance, influence, conditions, motivation, price, and habit. Table 10 provides a summary of the research questions and null hypotheses acceptance or rejection decisions. Although SPSS results indicated that on its own, effort expectancy was not a significant predictor, the model was significant. The hypothesis (H10) that these predictors would not influence use was rejected.

Table 10.
Statistical significance summary of null hypotheses.
4.2.7. Hypothesis 2 Results
Performance expectancy had a statistically significant relationship with older adults’ behavioral intent to use Internet-enabled technology in their homes. In the SPSS regression, performance significantly predicted use, B = 0.244, t(308) = 4.427, p < 0.001 (see Table 10). The null hypothesis (H20) that performance will not influence use was rejected.
4.2.8. Hypothesis 3 Results
Effort expectancy did not have a statistically significant effect on older adults’ behavioral intent to use Internet-enabled technologies, B = −0.026, t(308) = −0.409, p = 0.683 (see Table 10). The null hypothesis (H30) that effort will not influence use was accepted.
4.2.9. Hypothesis 4 Results
Social influence had a statistically significant effect and predicted older adults’ behavioral intent to use Internet-enabled technologies, B = 0.138, t(308) = 3.4775, p = 0.001 (see Table 10). The null hypothesis (H40) that influence will not influence use was rejected.
4.2.10. Hypothesis 5 Results
Facilitating conditions significantly predicted older adults’ behavioral intent to use IoT-enabled technologies, B = 0.184, t(308) = 2.999, p = 0.003 (see Table 10). The null hypothesis (H50) that conditions would not influence use was rejected.
4.2.11. Hypothesis 6 Results
Hedonic motivation significantly predicted older adults’ behavioral intent to use IoT-enabled technologies, B = 0.153, t(308) = 2.694, p = 0.007 (see Table 10). The null hypothesis (H60) that motivation will not influence use was rejected.
4.2.12. Hypothesis 7 Results
Price value significantly predicted older adults’ behavioral intention to use IoT-enabled technology, B = 0.140, t(308) = 3.099, p = 0.002 (see Table 10). The null hypothesis (H70) that price will not influence use was rejected.
4.2.13. Hypothesis 8 Results
Habit significantly predicted older adults’ behavioral intent to use IoT-enabled technologies, B = 0.378, t(308) = 8.696, p < 0.001 (see Table 10). The null hypothesis (H80) that habit will not influence use was rejected.
4.2.14. Summary of Results
This section detailed the results of the study on older adults’ behavioral intention to adopt IoT-enabled technologies to age in place longer. A detailed description of the sample and its demographic characteristics were provided, which corresponded well to the demographics expected in the region of northern Virginia. The reliability testing and variable correlations results were provided. A clear description of how the data were screened and prepared for multiple regression analysis was provided. The model explained 75% of the variability of predicting older adults’ behavioral intention to use IoT-enabled technologies in their homes. Only the predictor effort did not have a statistically significant effect on older adults’ behavioral intent to use IoT-enabled technologies. Based on the standardized betas, habit and performance expectancy were the strongest predictors of older adults’ behavioral intent to use IoT-enabled technology to age at home longer, making up 62% of the variability. The remaining statistically significant predictors were social influence, facilitating conditions, hedonic motivation, and price value. The null hypothesis for research question three was accepted, but all other null hypotheses were rejected. Section 5 discusses these results, provides conclusions, implications, and recommendations for future research.
5. Discussion, Implications, and Recommendations
From a theoretical perspective, this study demonstrated that the UTAUT2 explains the behavioral intention to use technology in the consumer context. The findings showed that the researchers could use the UTAUT2 to predict the adoption of many emerging and existing technologies beyond mobile. The study also demonstrated the importance of developing a research design to align with the research questions in the proper context (e.g., business versus consumer). This section will compare the findings of the study to previous research findings.
5.1. Performance Expectancy
This study focused on older adults accepting technology to compensate for an age or health related decline in capability, and not explicitly related to happiness. This study confirmed previous findings that, although older adults tended to favor more familiar technology when faced with diminished abilities, sickness, or a severe health condition, they were more inclined to adopt new technology to compensate [15,42,63]. Despite this, if researchers proposed technology to substitute for human interaction, communication of complex health issues, or more isolation from society, older adults were not likely to adopt it [15,83]. The study implied that if older adults perceived IoT-enabled solutions as useful, enabling, increasing quality of life, safety, and independence they are more likely to accept them into their homes.
5.2. Effort Expectancy
The insignificance of effort expectancy is important because it demonstrates that even if a device is easy to use and interaction with it is understandable, older adults will not use the technology to age in place. This study found that older adults did not believe that learning to use IoT technologies would be easy. Neither did they perceive their interactions with the technologies to be clear or understandable. The results indicated that older adults did not believe they could become skillful in using IoT-enabled devices. The insignificance of effort expectancy may be attributable to the fact that the scenario and devices presented were anecdotal, and participants did not actually experience the devices firsthand.
5.3. Social Influence
Family members and peers who demonstrated new technologies positively influenced older adults to adopt them [63]. An older adult who values or is influenced by a family member or healthcare provider is more likely to use IoT devices recommended by those persons. Older adults who suffered a grave health issue perceived new technologies as a benefit [46,65,89], and this study’s findings indicated that these persons would be more susceptible to social influence to adopt.
5.4. Facilitating Conditions
As demonstrated in the literature review, older adults required training, technical support, and coaching to adopt new technologies [15,43,88]. Older adults will not likely accept an IoT device or solution that does not provide resources or requires the adoption of the latest technologies. Because older adults tend to hang onto devices much longer, designers and developers should consider these technologies in IoT-enabled solutions, rather than only incorporating the latest devices or technologies.
5.5. Hedonic Motivation
Older adults who perceived the smart keychain, smart power sockets, and electronic healthcare account fun, enjoyable, and entertaining were more likely to use them. Participants perceived that smart power sockets could help them remain autonomous and increase safety. Older adults understood that they could use a smart keychain to take independent walks without being afraid that they could not call for help. The results suggest that older adults enjoy IoT-enabled devices that extend their ability to live and perform activities more safely and independently.
5.6. Price Value
The findings of this study indicated that the price of newer technologies was a significant predictor of technology acceptance. Participants in the study indicated that the average cost of USD80 to USD95 a month for Internet, smartphone, and data package was reasonable and provided value to them. The findings in this study validated that UTAUT2 is a useful model for predicting the behavioral intention to adopt technology in a consumer context.
5.7. Habit
The academic research indicated that older adults preferred older, more familiar technologies than the newer tablets or smartphones [43,63,85]. The findings of this study indicated that older adults in northern Virginia, who had a habit of using IoT technology and perceived a benefit in doing so, were more likely to adopt it to increase their quality of life, independence, and safety for aging in place. Although the findings were significant, there were several limiting factors.
5.8. Recommendations for Further Research
This section describes the identified future research recommendations developed from the data analysis, based on the identified delimitations, and on a reflection of the research design.
5.8.1. Recommendations Developed from the Data
Future research could study how much social influence affected older adults’ acceptance of IoT technologies when a healthcare provider prescribed it versus a family member’s recommendation for safety reasons. Future research on this topic could include older adults that are using long term care to understand the extent of the difference in technology adoption preferences from those that are not.
The extreme and extended social distancing mandated during the COVID-19 pandemic may have changed older adults’ perceptions of IoT technologies. Future research into the technologies and changes which older adults made in response to the epidemic and to decrease the digital divide could further explain how life-threatening conditions change older adults’ perceptions of technology and devices. For example, understanding how many older adults used applications to order groceries or food before COVID 19 versus after, or how many older adults procured Internet services as a direct result of the pandemic.
5.8.2. Recommendations Based on Delimitations
The research design explicitly sought older adults over the age of 60, limiting the ability to identify perception differences as people age. A researcher could expand the design methodology, including other age groups, to identify any generational differences in behavioral intention to use IoT technology to age in place. Additionally, a researcher could expand the generalizability of this study, focusing on a more rural area.
5.8.3. Recommendations from the Research Design
Future research could include a longitudinal or experimental study surveying participants without IoT technologies, implementing the technologies, allowing them to interact with them, and then surveying them again. This approach will help determine if effort expectancy is genuinely insignificant in predicting behavioral intent to use and the actual use of the IoT-enabled technology to age in place longer.
Future research could also evaluate perception differences based on gender and age, as these significantly modify the outcome variables in the UTAUT2. The analysis could identify the age range at which participants are no longer interested in aging at home. A summary of responses could determine the optimum age range for candidates to age in place and a cutoff age range for those who should not be permitted to do so. A researcher could also revise the research design to solicit participation from more than one third party survey organization.
5.9. Conclusions
The purpose of this research was to explain the extent to which performance expectancy, effort expectancy, social influence, facilitating conditions, hedonic motivation, price value, and habit affected the behavioral intention of older adults in northern Virginia to use emerging IoT technologies to age at home longer. The study used the UTAUT2 model to measure the perspectives of 316 adults age 60 and older in the northern Virginia area through SurveyMonkey™. Multiple regression analysis revealed that habit, performance expectancy, facilitating conditions, hedonic motivation, social influence, and price value were statistically significant in predicting behavioral intent to use IoT technologies to age in place. The two most significant predictors were habit and performance expectancy, which explained 62% of the variance in the linear model. This study filled the gap in research on older adults’ acceptance of IoT by focusing specifically on that population. The study contributes to the field by considering the constructs and relationships shown to predict adoption decisions. The findings help reduce the risk of solutions driven by technological and organizational requirements rather than the older adults’ unique needs and requirements. The study revealed that older adults may be susceptible to undue influence to adopt IoT solutions. These socioeconomic dimensions of the UTAUT2 are essential to the information technology field because the actualizing of IoT-enabled technologies in private homes depends on older adults’ participation and adoption.
Author Contributions
Conceptualization, C.L.P.; methodology, C.L.P.; validation, C.L.P.; formal analysis, C.L.P.; investigation, C.L.P.; resources, C.L.P.; data curation, C.L.P.; writing—original draft preparation, C.L.P.; writing—review and editing, S.S.M.R.; visualization, C.L.P.; supervision, S.S.M.R.; project administration, C.L.P. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
The study was conducted in accordance with the Declaration of Helsinki and approved by the Institutional Review Board of Capella University (2018-1071, 4 February 2019).
Informed Consent Statement
Informed consent was obtained from all subjects involved in the study.
Data Availability Statement
The data presented in this study are available on request from the corresponding author. The data are not publicly available.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
The researcher modified this instrument with permission from “Consumer Acceptance and Use of Information Technology: Extending the Unified Theory of Acceptance and Use of Technology” by V. Venkatesh, J. Y. Thong, and X. Xu, 2012, Management Information Systems Quarterly, 36(1), pp. 157–178. Copyright © 2012, Regents of the University of Minnesota. Adapted with permission.
The following scale was be presented for all questions (1–32).
1 = strongly agree, 2 = agree, 3 = somewhat disagree, 4 = neither agree or disagree, 5 = somewhat disagree, 6 = disagree, and 7 = strongly disagree.
Choose the best response to the following statements by circling either a 1 (strongly agree), 2 (agree), 3 (somewhat disagree), 4 (neither agree or disagree), 5 (somewhat disagree), 6 (disagree), or 7 (strongly disagree).
Appendix A.1. Performance Expectancy
- I find IoT-enabled devices useful in my daily life.
- Using IoT-enabled devices helps me accomplish things more quickly.
- Using IoT-enabled devices increases my quality of life, safety, and independence.
Appendix A.2. Effort Expectancy
- Learning how to use IoT-enabled devices is easy for me.
- My interaction with IoT-enabled devices is clear and understandable.
- I find IoT -enabled devices easy to use.
- It is easy for me to become skillful at using IoT-enabled devices.
Appendix A.3. Social Influence
- People who are important to me think that I should use IoT-enabled devices.
- People who influence my behavior think I should use IoT-enabled devices.
- People whose opinions that I value prefer that I use IoT-enabled devices.
Appendix A.4. Facilitating Conditions
- I have the resources necessary to use IoT-enabled devices.
- I have the knowledge necessary to use IoT-enabled devices.
- IoT-enabled devices are compatible with other technologies I use.
- I can get help from others when I have difficulties using IoT-enabled device.
Appendix A.5. Hedonic Motivation
- Using IoT-enabled devices is fun.
- Using IoT-enabled devices is enjoyable.
- Using IoT-enabled devices is very entertaining.
Internet services are additional communication services. They may be added by your existing telephone service provider as an additional cost. The average cost of Internet services ranges from USD35 to USD50 per month. Smartphones can be purchased starting at an average cost of USD300 or be charged on a monthly basis over a 24-month period. Average smartphone data plans begin at USD30 a month. Therefore, the average additional cost for Internet in your home, a smartphone, and data plan would be USD80 to USD95 a month.
Appendix A.6. Price Value
- IoT-enabled device is reasonably priced.
- IoT-enabled device is a good value for the money.
- At the current price, IoT-enabled device provides a good value.
Appendix A.7. Habit
- The use of IoT-enabled devices has become a habit for me.
- I am addicted to using IoT-enabled devices.
- I must use IoT-enabled devices.
Appendix A.8. Behavioral Intention
- I intend to use IoT-enabled devices in the future.
- I will always try to use IoT-enabled devices in my daily life.
- I plan to continue to use IoT-enabled devices frequently.
Appendix A.9. Use
Please choose your usage frequency for each of the following:
- Text messaging
- Video messaging
- Electronic mail
- Browse websites
- Watching videos on computer or smartphone
- Social interaction (e.g., Facebook, Instagram, etc.)
Note: Frequency range from never, 1–3 times a week, 4–6 times a week, every day, several times a day, to many times per day.
Appendix B

Table A1.
Collected data on sample.
Table A1.
Collected data on sample.
| Variable | Category | Frequency | Percent |
|---|---|---|---|
| Age | |||
| 60–69 | 197 | 62 | |
| 70–79 | 107 | 34 | |
| 80–89 | 12 | 4 | |
| Gender | |||
| Female | 199 | 63 | |
| Male | 117 | 37 | |
| Education | |||
| Less than high school | 5 | 1 | |
| High school or GED | 60 | 19 | |
| Some college | 84 | 27 | |
| Associate degree | 36 | 11 | |
| Bachelor’s degree | 65 | 21 | |
| Graduate degree | 66 | 21 | |
| Living conditions | |||
| Assisted living | 0 | 0 | |
| Live with family | 16 | 5 | |
| Rent home | 66 | 21 | |
| Own home | 234 | 74 | |
| Health conditions | |||
| Terminally ill | 0 | 0 | |
| Poor/chronically ill | 7 | 2 | |
| Fair | 83 | 26 | |
| Good | 116 | 37 | |
| Very good | 83 | 26 | |
| Excellent | 27 | 9 | |
| Internet in home | |||
| Yes | 287 | 90 | |
| No | 29 | 10 | |
| Relationship status | |||
| Married | 161 | 51 | |
| Widowed | 47 | 15 | |
| Divorced | 58 | 18 | |
| Single | 40 | 13 | |
| Single, cohabitating | 10 | 3 |
References
- Riazul-Islam, S.M.; Daehan, K.; Humaun Kabir, M.; Hossain, M.; Kyung-Sup, K. The internet of things for health care: A comprehensive survey. IEEE Access 2015, 3, 678–708. [Google Scholar] [CrossRef]
- Biagetti, G.; Crippa, P.; Falaschetti, L.; Orcioni, S.; Turchetti, C. Human activity monitoring system based on wearable sEMG and accelerometer wireless sensor nodes. BioMed. Eng. OnLine 2018, 17, 63–80. [Google Scholar] [CrossRef] [PubMed]
- Ahmed, K.B.; Bouhorma, M.; Ahmed, M.B. Age of big data and smart cities: Privacy trade-off. Int. J. Eng. Trends Technol. 2014, 16, 298–304. [Google Scholar] [CrossRef]
- Boyes, H. Cybersecurity and cyber-resilient supply chains. Technol. Innov. Manag. Rev. 2015, 5, 28–34. [Google Scholar] [CrossRef]
- Hennebert, C.; Santos, J.D. Security protocols and privacy issues into 6LoWPAN stack: A synthesis. IEEE Internet Things J. 2014, 1, 384–398. [Google Scholar] [CrossRef]
- Miorandi, D.; Sicari, S.; De Pellegrini, F.; Chlamtac, I. Internet of things: Vision, applications and research challenges. Ad Hoc. Netw. 2012, 10, 1497–1516. [Google Scholar] [CrossRef]
- Al Ayubi, S.U.; Pelletier, A.; Sunthara, G.; Gujral, N.; Mittal, V.; Bourgeois, F.C. A mobile app development guideline for hospital settings: Maximizing the use of and minimizing the security risks of "bring your own devices" policies. JMIR mHealth uHealth 2016, 4, 1–12. [Google Scholar] [CrossRef]
- Al-Shaqi, R.; Mourshed, M.; Rezgui, Y. Progress in ambient assisted systems for independent living by the elderly. Springerplus 2016, 2016, 1–20. [Google Scholar] [CrossRef]
- Jaschinski, C. Ambient assisted living: Towards a model of technology adoption and use among elderly users. In Proceedings of the 2014 ACM International Joint Conference on Pervasive and Ubiquitous Computing: Adjunct Publication, Seattle, WA, USA, 13–17 September 2014; pp. 319–324. [Google Scholar]
- Pew Research Center. Internet/Broadband Fact Sheet. Available online: http://www.pewinternet.org (accessed on 25 July 2018).
- AARP. The Longevity Economy: How People over 50 Are Driving Economic and Social Value in the US; AARP: Washington, DC, USA, 2016; p. 29. [Google Scholar]
- Dutton, W.H. Putting things to work: Social and policy challenges for the internet of things. J. Policy Regul. Strategy Telecommun. Inf. Media 2014, 16, 1–21. [Google Scholar] [CrossRef]
- Gitlow, L. Technology use by older adults and barriers to using technology. Phys. Occup. Ther. Geriatr. 2014, 32, 271–280. [Google Scholar] [CrossRef]
- Jones, S.; Hara, S.; Augusto, J. eFRIEND: An ethical framework for intelligent environments development. Ethics Inf. Technol. 2015, 17, 11–25. [Google Scholar] [CrossRef]
- Mitzner, T.L.; Savla, J.; Boot, W.R.; Sharit, J.; Charness, N.; Czaja, S.J.; Rogers, W.A. Technology adoption by older adults: Findings from the PRISM trial. Gerontologist 2018, 59, 34–44. [Google Scholar] [CrossRef] [PubMed]
- de Almeida, J.P.L.; Farias, J.S.; Carvalho, H.S. Drivers of the technology adoption in healthcare. Braz. Bus. Rev. 2017, 14, 336–351. [Google Scholar] [CrossRef]
- Bilbao, A.; Almeida, A.; López-de-Ipiña, D. Promotion of active aging combining sensor and social network data. J. Biomed. Inform. 2016, 64, 108–115. [Google Scholar] [CrossRef] [PubMed]
- James, T.; Pirim, T.; Boswell, K.; Reithel, B.; Barkhi, R. Determining the intention to use biometric devices: An application and extension of the technology acceptance model. J. Organ. End User Comput. 2006, 18, 1–24. [Google Scholar] [CrossRef]
- Saare, M.A.; Hussain, A.; Yue, W.S. Conceptualizing mobile health application use intention and adoption among Iraqian older adults: From the perspective of expanded technology acceptance model. Int. J. Interact. Mob. Technol. 2019, 13, 28–41. [Google Scholar] [CrossRef]
- Magsamen-Conrad, K.; Upadhyaya, S.; Joa, C.Y.; Dowd, J. Bridging the divide: Using UTAUT to predict multigenerational tablet adoption practices. Comput. Hum. Behav. 2015, 50, 186–196. [Google Scholar] [CrossRef] [PubMed]
- Pal, D.; Funilkul, S.; Charoenkitkarn, N.; Kanthamanon, P. Internet-of-things and smart homes for elderly healthcare: An end user perspective. IEEE Access 2018, 6, 10483–10496. [Google Scholar] [CrossRef]
- Venkatesh, V.; Morris, M.G.; Davis, G.B.; Davis, F.D. User acceptance of information technology: Toward a unified view. MIS Q. 2003, 27, 425–478. [Google Scholar] [CrossRef]
- Chen, K.; Chan, A.A.H.S. Predictors of gerontechnology acceptance by older Hong Kong Chinese. Technovation 2014, 34, 126–135. [Google Scholar] [CrossRef]
- Popescu, D.; Popescu, S.; Bodi, S. A conceptual framework concerning education as factor of elders’ acceptance for smart assistive technologies. In Proceedings of the Balkan Region Conference on Engineering and Business Education, Sibiu, Romania, 19–22 October 2017; pp. 275–283. [Google Scholar]
- Hassanzadeh, A.; Xu, Z.; Stoleru, R.; Gu, G.; Polychronakis, M. PRIDE: A practical intrusion detection system for resource constrained wireless mesh networks. Comput. Secur. 2016, 2016, 114–132. [Google Scholar] [CrossRef]
- Rajput, D.S.; Gour, R. An IoT framework for healthcare monitoring systems. Int. J. Comput. Sci. Inf. Secur. 2016, 14, 451–455. [Google Scholar]
- Kaur, J.; Kaur, K. Internet of things: A review on technologies, architecture, challenges, applications, future trends. Int. J. Comput. Netw. Inf. Secur. 2017, 9, 57–70. [Google Scholar] [CrossRef]
- Li, S.; Xu, L.D.; Zhao, S. The internet of things: A survey. Inf. Syst. Front. 2015, 17, 243–259. [Google Scholar] [CrossRef]
- Xu, T.; Wendt, J.B.; Potkonjak, M. Security of IoT systems: Design challenges and opportunities. In Proceedings of the 2014 IEEE/ACM International Conference on Computer-Aided Design, San Jose, CA, USA, 3–6 November 2014; pp. 417–423. [Google Scholar]
- Phibbs, C.L. The Impact of Motivation, Price, and Habit on Intention to Use IoT-Enabled Technology: A Correlational Study. Ph.D. Thesis, Capella University, Minneapolis, MN, USA, 2021. [Google Scholar]
- Venkatesh, V.; Thong, J.Y.L.; Xin, X. Unified theory of acceptance and use of technology: A synthesis and the road ahead. J. Assoc. Inf. Syst. 2016, 17, 328–376. [Google Scholar] [CrossRef]
- Macedo, I.M. Predicting the acceptance and use of information and communication technology by older adults: An empirical examination of the revised UTAUT2. Comput. Hum. Behav. 2017, 75, 935–948. [Google Scholar] [CrossRef]
- Heer, T.; Garcia-Morchon, O.; Hummen, R.; Keoh, S.L.; Kumar, S.S.; Wehrle, K. Security challenges in the IP-based internet of things. Wirel. Pers. Commun. 2011, 61, 527–542. [Google Scholar] [CrossRef]
- Duan, L.; Zhang, Y.; Chen, S.; Wang, S.; Cheng, B.; Chen, J. Realizing IoT service’s policy privacy over publish/subscribe-based middleware. Springerplus 2016, 5, 1615–1646. [Google Scholar] [CrossRef]
- Haux, R.A.; Hein, A.; Kolb, G.; Künemund, H.; Eichelberg, M.; Appell, J.E.; Appelrath, H.J.; Bartsch, C.; Bauer, J.M.; Becker, M.; et al. Information and communication technologies for promoting and sustaining quality of life, health and self-sufficiency in ageing societies—Outcomes of the lower saxony research network design of environments for ageing. Inform. Health Soc. Care 2014, 39, 166–187. [Google Scholar] [CrossRef]
- Alvarez-de-la-Concepción, M.A.; Soria-Morillo, L.M.; Álvarez-García, J.A.; González-Abril, L. Mobile activity recognition and fall detection system for elderly people using Ameva algorithm. Pervasive Mob. Comput. 2017, 34, 3–13. [Google Scholar] [CrossRef]
- Khatoun, R.; Zeadally, S. Smart cities: Concepts, architectures, research opportunities. Commun. ACM 2016, 59, 46–57. [Google Scholar] [CrossRef]
- Venkatesh, V.; Thong, J.Y.; Xu, X. Consumer acceptance and use of information technology: Extending the unified theory of acceptance and use of technology. MIS Q. 2012, 36, 157–178. [Google Scholar] [CrossRef]
- Barsaum, P.; Berg, P.; Hagman, A.; Scandurra, I. Internet of things technology for remote healthcare: A pilot study. In Proceedings of the 14th Scandinavian Conference on Health Informatics, Gothenburg, Sweden, 6–7 April 2016; pp. 43–48. [Google Scholar]
- Morga, J.; Rahman, S. Exploring facets of trust in older adult decisions to adopt mobile commerce. Int. J. Eng. Technol. 2018, 7, 4954–4961. [Google Scholar] [CrossRef]
- Wang, S.; Bolling, K.; Mao, W.; Reichstadt, J.; Jeste, D.; Kim, H.-C.; Nebeker, C. Technology to support aging in place: Older adults’ perspectives. Healthcare 2019, 7, 60. [Google Scholar] [CrossRef] [PubMed]
- Pappas, M.A.; Demertzi, E.; Papagerasimou, Y.; Koukianakis, L.; Voukelatos, N.; Drigas, A. Cognitive-based e-learning design for older adults. Soc. Sci. 2019, 8, 6. [Google Scholar] [CrossRef]
- Piper, A.M.; Brewer, R.; Cornejo, R. Technology learning and use among older adults with late-life vision impairments. Univers. Access Inf. Soc. 2017, 16, 699–711. [Google Scholar] [CrossRef]
- van Heek, J.; Himmel, S.; Ziefle, M. Privacy, data security, and the acceptance of AAL-systems: A user specific perspective. In Proceedings of the ITAP: International Conference on Human Aspects of IT for the Aged Population, Vancouver, BC, Canada, 9–14 July 2017; pp. 38–56. [Google Scholar]
- Hsu, C.L.; Lin, J.C. An empirical examination of consumer adoption of internet of things services: Network externalities and concern for information privacy perspectives. Comput. Hum. Behav. 2016, 62, 516–527. [Google Scholar] [CrossRef]
- Arthanat, S.; Wilcox, J.; Macuch, M. Profiles and predictors of smart home technology adoption by older adults. OTJR Occup. Particip. Health 2018, 39, 247–256. [Google Scholar] [CrossRef]
- Zinner, T.; Wamser, F.; Leopold, H.; Dobre, C.; Mavromoustakis, C.; Garcia, N. Matching requirements for ambient assisted living and enhanced living environments with networking technologies. In Ambient Assisted Living and Enhanced Living Environments: Principles, Technologies and Control; Dobre, C., Mavromoustakis, C.X., Garcia, N.M., Goleva, R.I., Mastorakis, G., Eds.; Elsevier: Amsterdam, The Netherlands, 2017; pp. 91–121. [Google Scholar]
- Lustig, C.; Konkel, A.; Jacoby, L.L. Which route to recovery? Psychol. Sci. 2004, 15, 729–735. [Google Scholar] [CrossRef]
- Brown, S.A.; Venkatesh, V. Model of adoption of technology in households: A baseline model test and extension incorporating household life cycle. MIS Q. 2005, 29, 399–426. [Google Scholar] [CrossRef]
- Northern Virginia Regional Commission. NOVA Region Dashboard. Available online: https://www.novaregiondashboard.com/people (accessed on 1 October 2020).
- Dodds, W.B.; Monroe, K.B.; Grewal, D. Effects of price, brand, and store information on buyers’ product evaluations. JMR J. Mark. Res. 1991, 28, 307. [Google Scholar]
- Rashidi, P.; Mihailidis, A. A survey on ambient-assisted living tools for older adults. IEEE J. Biomed. Health Inform. 2013, 17, 579–590. [Google Scholar] [CrossRef] [PubMed]
- Creswell, J.W. Research Design: Qualitative, Quantitative, and Mixed Methods Approaches; Sage Publications: Los Angeles, CA, USA, 2014. [Google Scholar]
- Field, A. Discovering Statistics Using IBM SPSS Statistics; SAGE Publications Inc.: Thousand Oaks, CA, USA, 2018. [Google Scholar]
- Mannheim, I.; Schwartz, E.; Xi, W.; Buttigieg, S.C.; McDonnell-Naughton, M.; Wouters, E.J.M.; van Zaalen, Y. Inclusion of older adults in research and design of digital technology. Int. J. Environ. Res. Public Health 2019, 16, 3718. [Google Scholar] [CrossRef]
- Choy, L.T. The strengths and weaknesses of research methodology: Comparison and complimentary between qualitative and quantitative approaches. Int. Organ. Sci. Res. J. Humanit. Soc. Sci. 2014, 19, 99–104. [Google Scholar] [CrossRef]
- Gaitán, A.; Peral, P.; Jerónimo, R. Elderly and Internet banking: An application of UTAUT2. J. Internet Bank. Commer. 2015, 20, 1–23. [Google Scholar]
- Chipps, J.; Jarvis, M.A. Technology-assisted communication in older persons in a residential care facility in South Africa. Inf. Dev. 2016, 33, 393–405. [Google Scholar] [CrossRef]
- Floerkemeier, C.; Langheinrich, M.; Fleisch, E.; Mattern, F.; Sarma, S.E.E. The Internet of Things: First International Conference, IOT 2008, Zurich, Switzerland, 26–28 March 2008; Springer: Berlin/Heidelberg, Germany, 2008. [Google Scholar]
- Dlodlo, N.; Foko, T.; Mvelase, P. The state of affairs in internet of things research. Electron. J. Inf. Syst. Eval. 2012, 15, 244–258. [Google Scholar]
- Atzori, L.; Morabito, G. The internet of things: A survey. Comput. Netw. Intern. J. Comput. Telecommun. Netw. Arch. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Vichitvanichphong, S.; Talaei-Khoei, A.; Kerr, S.; Amir Hossein, G. Assistive technologies for aged care. Inf. Technol. People 2018, 31, 405–427. [Google Scholar] [CrossRef]
- Peek, S.T.; Luijkx, K.G.; Vrijhoef, H.J.; Nieboer, M.E.; Aarts, S.; van der Voort, C.S.; Rijnaard, M.D.; Wouters, E.J. Origins and consequences of technology acquirement by independent-living seniors: Towards an integrative model. BMC Geriatr. 2017, 17, 189–200. [Google Scholar] [CrossRef]
- United Nations. World Population Prospects: Key Findings & Advance Tables (2017 Revision); Department of Economic and Social Affairs, Population Division: New York, NY, USA, 2017. [Google Scholar]
- Golant, S.M. A theoretical model to explain the smart technology adoption behaviors of elder consumers (Elderadopt). J. Aging Stud. 2017, 42, 56–73. [Google Scholar] [CrossRef]
- Ray, P.P. Internet of robotic things: Concept, technologies, and challenges. IEEE Access 2016, 4, 9489–9500. [Google Scholar] [CrossRef]
- Dong, X.; Chang, Y.; Wang, Y.; Yan, J. Understanding usage of internet of things (IOT) systems in China. Inf. Technol. People 2017, 30, 117–138. [Google Scholar] [CrossRef]
- Jackson, G.; Rahman, S. Exploring challenges and opportunities in cybersecurity risk and threat communications related to the Medical Internet of Things (MIoT). arXiv 2019, arXiv:1908.00666. [Google Scholar] [CrossRef]
- Kotz, D.; Fu, K.; Gunter, C.; Rubin, A. Security for mobile and cloud frontiers in healthcare. Commun. ACM 2015, 58, 21–23. [Google Scholar] [CrossRef]
- Mora, N.; Grossi, F.; Russo, D.; Barsocchi, P.; Hu, R.; Brunschwiler, T.; Michel, B.; Cocchi, F.; Montanari, E.; Nunziata, S.; et al. IoT-based home monitoring: Supporting practitioners’ assessment by behavioral analysis. Sensors 2019, 19, 3238. [Google Scholar] [CrossRef]
- Grgurić, A.; Mošmondor, M.; Huljenić, D. The SmartHabits: An intelligent privacy-aware home care assistance system. Sensors 2019, 19, 907. [Google Scholar] [CrossRef]
- Tremblay, M.; Hess, J.P.; Christenson, B.M.; McIntyre, K.K.; Smink, B.; van der Kamp, A.J.; de Jong, L.G.; Döpfer, D. Customized recommendations for production management clusters of North American automatic milking systems. J. Dairy Sci. 2016, 99, 5671–5680. [Google Scholar] [CrossRef]
- Yin, Y.; Zeng, Y.; Chen, X.; Fan, Y. The internet of things in healthcare: An overview. J. Ind. Inf. Integr. 2016, 1, 3–13. [Google Scholar] [CrossRef]
- Kim, S.; Kim, S. User preference for an IoT healthcare application for lifestyle disease management. Policy 2018, 42, 304–314. [Google Scholar] [CrossRef]
- United States Census Bureau. Older People Projected to Outnumber Children for the First Time in U.S. History (Release No. CB18-41). 2030 Marks Important Demographic Milestones for U.S. Population; United Statues Census Bureau: Silver Spring, MD, USA, 2018.
- Kontis, V.; Bennett, J.E.; Mathers, C.D.; Li, G.; Foreman, K.; Ezzati, M. Future life expectancy in 35 industrialised countries: Projections with a Bayesian model ensemble. Lancet 2017, 389, 1323–1335. [Google Scholar] [CrossRef]
- Pal, D.; Triyason, T.; Funilkul, S.; Chutimaskul, W. Smart homes and quality of life for the elderly: Perspective of competing models. IEEE Access 2018, 6, 8109–8122. [Google Scholar] [CrossRef]
- Hmida, H.B.; Braun, A. Enabling an Internet of things framework for ambient assisted living. In Ambient Assisted Living: Advanced Technologies and Societal Change; Mand, R.W.B., Ed.; Springer Cham: Frankfurt, Germany, 2017; pp. 181–196. [Google Scholar]
- Mahadevaswamy, U.B.; Durgad, Z. IoT based smart health monitoring system. i-Manag. J. Electron. Eng. 2019, 9, 8–23. [Google Scholar] [CrossRef]
- Marston, H.; Samuels, J. A review of age friendly virtual assistive technologies and their effect on daily living for carers and dependent adults. Healthcare 2019, 7, 49. [Google Scholar] [CrossRef]
- Awais, M.; Raza, M.; Ali, K.; Ali, Z.; Irfan, M.; Chughtai, O.; Khan, I.; Kim, S.; Ur Rehman, M. An internet of things based bed-egress alerting paradigm using wearable sensors in elderly care environment. Sensors 2019, 19, 2498. [Google Scholar] [CrossRef]
- Cavallo, F.; Esposito, R.; Limosani, R.; Manzi, A.; Bevilacqua, R.; Felici, E.; Di Nuovo, A.; Cangelosi, A.; Lattanzio, F.; Dario, P. Robotic services acceptance in smart environments with older adults: User satisfaction and acceptability study. J. Med. Internet Res. 2018, 20, e264. [Google Scholar] [CrossRef]
- Keidser, G.; Matthews, N.; Convery, E. A qualitative examination of user perceptions of user-driven and app-controlled hearing technologies. Am. J. Audiol. (Online) 2019, 28, 993–1005. [Google Scholar] [CrossRef]
- Vaportzis, E.; Giatsi Clausen, M.; Gow, A.J. Older adults perceptions of technology and barriers to interacting with tablet computers: A focus group study. Front. Psychol. 2017, 8, 1687. [Google Scholar] [CrossRef]
- Moret-Tatay, C.; Beneyto-Arrojo, M.J.; Gutierrez, E.; Boot, W.R.; Charness, N. A Spanish adaptation of the computer and mobile device proficiency questionnaires (CPQ and MDPQ) for older adults. Front. Psychol. 2019, 10, 1165. [Google Scholar] [CrossRef]
- Mongkolnam, P.; Booranrom, Y.; Watanapa, B.; Visutarrom, T.; Chan, J.H.; Nukoolkit, C. Smart bedroom for the elderly with gesture and posture analyses using Kinect. Maejo Int. J. Sci. Technol. 2017, 11, 1–16. [Google Scholar]
- Maksimović, M.; Vujović, V.; Perišić, B. Do it yourself solution of Internet of Things healthcare system: Measuring body parameters and environmental parameters affecting health. J. Inf. Syst. Eng. Manag. 2016, 1, 25–39. [Google Scholar] [CrossRef]
- Prescott, E.; Meindersma, E.P.; van der Velde, A.E.; Gonzalez-Juanatey, J.R.; Iliou, M.C.; Ardissino, D.; Zoccai, G.B.; Zeymer, U.; Prins, L.F.; Van’t Hof, A.W.J.; et al. A European study on effectiveness and sustainability of current cardiac rehabilitation programmes in the elderly: Design of the EU-CaRE randomised controlled trial. Eur. J. Prev. Cardiol. 2016, 23, 27–40. [Google Scholar] [CrossRef] [PubMed]
- Cajita, M.I.; Hodgson, N.A.; Lam, K.W.; Yoo, S.; Han, H. Facilitators of and barriers to mHealth adoption in older adults with heart failure. CIN Comput. Inform. Nurs. 2018, 36, 376–382. [Google Scholar] [CrossRef] [PubMed]
- Widmer, R.J.; Allison, T.G.; Lennon, R.; Lopez-Jimenez, F.; Lerman, L.O.; Lerman, A. Digital health intervention during cardiac rehabilitation: A randomized controlled trial. Am. Heart J. 2017, 188, 65–72. [Google Scholar] [CrossRef]
- Koivumäki, T.; Pekkarinen, S.; Lappi, M.; Väisänen, J.; Juntunen, J.; Pikkarainen, M. Consumer adoption of future MyData-based preventive ehealth services: An acceptance model and survey study. J. Med. Internet Res. 2017, 19, e7821. [Google Scholar] [CrossRef]
- Tavares, J.; Oliveira, T. Electronic health record patient portal adoption by health care consumers: An acceptance model and survey. J. Med. Internet Res. 2016, 18, e5069. [Google Scholar] [CrossRef]
- Hauk, N.; Hüffmeier, J.; Krumm, S. Ready to be a silver surfer? A meta-analysis on the relationship between chronological age and technology acceptance. Comput. Hum. Behav. 2018, 84, 304–319. [Google Scholar] [CrossRef]
- Li, J.; Ma, Q.; Chan, A.H.S.; Man, S.S. Health monitoring through wearable technologies for older adults: Smart wearables acceptance model. Appl. Ergon. 2019, 75, 162–169. [Google Scholar] [CrossRef]
- Nilsen, M.L.; Morrison, A.; Lingler, J.H.; Myers, B.; Johnson, J.T.; Happ, M.B.; Sereika, S.M.; Dabbs, A.D. Evaluating the usability and acceptability of communication tools among older adults. J. Gerontol. Nurs. 2018, 44, 30–39. [Google Scholar] [CrossRef]
- Portz, J.D.; Bayliss, E.A.; Bull, S.; Boxer, R.S.; Bekelman, D.B.; Gleason, K.; Czaja, S. Using the technology acceptance model to explore user experience, intent to use, and use behavior of a patient portal among older adults with multiple chronic conditions: Descriptive qualitative study. J. Med. Internet Res. 2019, 21, e11604. [Google Scholar] [CrossRef]
- Edelman, F. Manager, computer systems, and productivity. MIS Q. 1981, 5, 1–19. [Google Scholar] [CrossRef]
- Edwards, W. Behavior decision theory. Annu. Rev. Psychol. 1961, 12, 473–498. [Google Scholar] [CrossRef] [PubMed]
- Davis, F.D. A Technology Acceptance Model for Empirically Testing New End-User Information Systems: Theory and Results. Ph.D. Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 1985. [Google Scholar]
- Davis, F.D. Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Q. 1989, 13, 319–340. [Google Scholar] [CrossRef]
- Nikou, S.A.; Economides, A.A. Mobile-based assessment: Investigating the factors that influence behavioral intention to use. Comput. Educ. 2017, 109, 56–73. [Google Scholar] [CrossRef]
- Ain, N.; Kaur, K.; Waheed, M. The influence of learning value on learning management system use: An extension of UTAUT2. Inf. Dev. 2015, 32, 1306–1321. [Google Scholar] [CrossRef]
- Chipeva, P.; Cruz-Jesus, F.; Oliveira, T.; Irani, Z. Digital divide at individual level: Evidence for eastern and western European countries. Gov. Inf. Q. 2018, 35, 460–479. [Google Scholar] [CrossRef]
- Gao, Y.; He, L.; Luo, Y. An empirical study of wearable technology acceptance in healthcare. Ind. Manag. Data Syst. 2015, 115, 1704–1723. [Google Scholar] [CrossRef]
- Hew, J.J.; Lee, V.H.; Ooi, K.B.; June, W. What catalyses mobile apps usage intention: An empirical analysis. Ind. Manag. Data Syst. 2015, 115, 1269–1291. [Google Scholar] [CrossRef]
- Nair, P.K.; Ali, F.; Leong, L.C. Factors affecting acceptance & use of ReWIND. Interact. Technol. Smart Educ. 2015, 12, 183–201. [Google Scholar] [CrossRef]
- Antón, M.A.; Ordieres-Meré, J.; Saralegul, U.; Sun, S. Non-invasive ambient intelligence in real life: Dealing with noisy patterns to help older people. Sensors 2019, 19, 3113. [Google Scholar] [CrossRef]
- Du, Y.; Lim, Y.; Tan, Y. A novel human activity recognition and prediction in smart home based on interaction. Sensors 2019, 19, 4474. [Google Scholar] [CrossRef] [PubMed]
- Koceska, N.; Koceski, S.; Zobel, P.B.; Trajkovik, V.; Garcia, N. A telemedicine robot system for assisted and independent living. Sensors 2019, 19, 834. [Google Scholar] [CrossRef] [PubMed]
- Bravo, J.; Cook, D.J.; Riva, G. Ambient intelligence for health environments. J. Biomed. Inform. 2016, 64, 207–210. [Google Scholar] [CrossRef] [PubMed]
- Cahill, J.; Portales, R.; McLoughin, S.; Nagan, N.; Henrichs, B.; Wetherall, S. IoT/sensor-based infrastructures promoting a sense of home, independent living, comfort and wellness. Sensors 2019, 19, 485. [Google Scholar] [CrossRef] [PubMed]
- Irizarry, T.; Shoemake, J.; Nilsen, M.L.; Czaja, S.; Beach, S.; DeVito Dabbs, A. Patient portals as a tool for health care engagement: A mixed-method study of older adults with varying levels of health literacy and prior patient portal use. J. Med. Internet Res. 2017, 19, e7099. [Google Scholar] [CrossRef]
- Pew Research Center. Mobile Technology and Home Broadband 2019. Available online: https://www.pewresearch.org (accessed on 29 February 2020).
- Marston, H.R.; Genoe, R.; Freeman, S.; Kulczycki, C.; Musselwhite, C. Older adults’ preceptions of ICT: Main findings from the technology in later life (TILL) study. Healthcare 2019, 7, 86. [Google Scholar] [CrossRef]
- Bostrom, J.; Sweeney, G.; Whiteson, J.; Dodson, J.A. Mobile Health and Cardiac Rehabilitation in Older Adults; 0160-9289; National Institute on Aging: Bethesda, MD, USA, 2019; pp. 1–9.
- Kato, S.; Ando, M.; Kondo, T.; Yoshida, Y.; Honda, H.S.; Maruyama, S. Lifestyle intervention using Internet of Things (IoT) for the elderly: A study protocol for a randomized control trial (the BEST-LIFE study). Nagoya J. Med. Sci. 2018, 80, 175–182. [Google Scholar] [CrossRef]
- Prescott, E.; Mikkelsen, N.; Holdgaard, A.; Eser, P.; Marcin, T.; Wilhelm, M.; Gil, C.P.; González-Juanatey, J.R.; Moatemri, F.; Iliou, M.C.; et al. Cardiac rehabilitation in the elderly patient in eight rehabilitation units in Western Europe: Baseline data from the EU-CaRE multicentre observational study. Eur. J. Prev. Cardiol. 2019, 26, 1052–1063. [Google Scholar] [CrossRef]
- Negin, F.; Brémond, F. An unsupervised framework for online spatiotemporal detection of activities of daily living by hierarchical activity models. Sensors 2019, 19, 4237. [Google Scholar] [CrossRef]
- Fox, G.; Connolly, R. Mobile health technology adoption across generations: Narrowing the digital divide. Inf. Syst. J. 2018, 28, 995–1019. [Google Scholar] [CrossRef]
- Home Instead. Two-Thirds of Seniors Have Been Scammed Online: Survey. Available online: https://www.homeinstead.com/ (accessed on 4 April 2019).
- Makhdoom, I.; Abolhasan, M.; Lipman, J.; Liu, R.P.; Ni, W. Anatomy of threats to the internet of things. IEEE Commun. Surv. Tutor. 2018, 21, 1636–1675. [Google Scholar] [CrossRef]
- Marcelino, I.; Laza, R.; Domingues, P.; Gómez-Meire, S.; Fdez-Riverola, F.; Pereira, A. Active and assisted living ecosystem for the elderly. Sensors 2018, 18, 1246. [Google Scholar] [CrossRef] [PubMed]
- Stahl, B.C.; Timmermans, J.O.B.; Mittelstadt, B.D. The ethics of computing: A survey of the computing-oriented literature. ACM Comput. Surv. 2016, 48, 1–38. [Google Scholar] [CrossRef]
- Chadborn, N.H.; Blair, K.; Creswick, H.; Hughes, N.; Dowthwaite, L.; Adenekan, O.; Pérez Vallejos, E. Citizens’ juries: When older adults deliberate on the benefits and risks of smart health and smart homes. Healthcare 2019, 7, 54. [Google Scholar] [CrossRef]
- Loukaka, A.; Rahman, S. Discovering New Cyber Protection Approaches From a Security Professional Prospective. Int. J. Comput. Netw. Commun. 2017, 9, 13–25. [Google Scholar] [CrossRef]
- Marques, G.; Pitarma, R. An indoor monitoring system for ambient assisted living based on internet of things architecture. Int. J. Environ. Res. Public Health 2016, 13, 1152. [Google Scholar] [CrossRef] [PubMed]
- Rahim, S.A.; Gopalan, P.N.A.P.; Rahman, N.A.A. An empirical study on acceptance of telecare health services in Malaysia [Special Edition]. Glob. Bus. Manag. Res. 2017, 9, 13–28. [Google Scholar]
- Sekaran, U.; Bougie, R. Research Methods for Business: A Skill-Building Approach; John Wiley and Sons: West Sussez, UK, 2013. [Google Scholar]
- Middlemass, J.B.; Vos, J.; Siriwardena, A.N. Perceptions on use of home telemonitoring in patients with long term conditions—Concordance with the health information technology acceptance model: A qualitative collective case study. BMC Med. Inform. Decis. Mak. 2017, 17, 89–100. [Google Scholar] [CrossRef]
- United States Census Bureau. Explore Census Data; United States Census Bureau: Suitland-Silver Hill, MD, USA, 2020.
- Faul, F.; Erdfelder, E.; Buchner, A.; Lang, A.G. Statistical power analyses using G*Power 3.1: Tests for correlation and regression analyses. Behav. Res. Methods 2009, 41, 1149–1160. [Google Scholar] [CrossRef]
- Tabachnick, B.G.; Fidell, L.S. Using Multivariate Statistics; Pearson Education: Boston, MA, USA, 2007. [Google Scholar]
- Ramón-Jerónimo, M.A.; Peral-Peral, B.; Arenas-Gaitán, J. Elderly persons and Internet use. Soc. Sci. Comput. Rev. 2013, 31, 389–403. [Google Scholar] [CrossRef]
- Mertler, C.A.; Reinhart, R.V. Advanced and Multivariate Statistical Methods: Practical Application and Interpretation, 6th ed.; Routledge: New York, NY, USA, 2017. [Google Scholar]
- Department of Health Education and Welfare. The Belmont Report: Ethical Principles and Guidelines for the Protection of Human Subjects of Research; Department of Health Education and Welfare: Washington, DC, USA, 1979.
- Roberts, A.W.; Ogunwole, S.U.; Blakeslee, L.; Rabe, M.A. The Population 65 Years and Older in the United States: 2016; United States Census Bureau: Suitland-Silver Hill, MD, USA, 2016; p. 25.
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).