1. Introduction
More smart devices are connecting to the Internet every day to improve our daily lives. Internet of Things (IoT) forecasts suggest that there will be more than 25.4 billion connected devices by 2030 [
1]. The growth of IoT will provide multiple benefits for companies and individuals. However, as IoT networks become more popular, they become attractive to malicious actors, and therefore, security issues start to appear.
Many malicious actors try to attack smart devices due to weak or no security measures implemented by manufacturers [
2,
3]. A set of 33 vulnerabilities in TCP/IP stacks were found recently, affecting millions of IoT devices of over 150 device manufacturers [
4]. Four open source TCP/IP stacks were affected, which are found in multiple operating systems (OSes) such as Contiki and Nut/OS [
5]. This set of new flaws is called “Amnesia:33” from the fact that the number of vulnerabilities is 33, and most of them might be exploited to carry out denial-of-service (DoS) attacks and remote code execution (RCE). Protecting IoT devices and networks using approaches such as cryptographic protocols and traditional intrusion detection systems (IDS) is not always feasible. Limited computational power and limited energy are characteristics of a smart device. Ensuring confidentiality, availability, and integrity of IoT networks requires new solutions that take into account their limitations.
The routing protocol for low-power and lossy networks (RPL) [
6] is a protocol designed for resource-constrained devices. It was proposed by the Internet Engineering Task Force (IETF) ROLL (routing over low power and lossy networks) working group [
7]. Existing works show that RPL is vulnerable to many attacks, and countermeasures are proposed by several researchers [
8,
9]. The RPL-based attacks focus on exploiting the limitations of power and the lossy environment in which IoT devices operate. Some examples are selective forwarding, blackhole, rank, and version attacks [
10,
11]. Usually, an IDS is deployed as a detection mechanism in the network.
In this paper, the impact of combined rank and blackhole attacks is studied by implementing them in Contiki-NG and simulating them in the Whitefield framework. Malicious devices attack the RPL-based network by advertising false rank and dropping packets of child nodes. As a result, the network has poor performance and devices exhaust their energy.
A novel security framework for RPL-based IoT networks (SRF-IoT) is also designed and proposed to mitigate RPL-based routing attacks. IoT devices that utilise RPL protocol use an objective function (OF) to help them choose the best parent that provides a route to sink/border router (BR). SRF-IoT provides a trust-based OF, called SRF-OF, so that nodes choose the most trusted parent and avoid malicious actors in a network. Moreover, an external IDS, called SRF-IDS, aims to provide smart devices with trust metrics. It consists of an SRF-IDS root that plays the role of BR and SRF-IDS detectors that have promiscuous mode enabled for capturing network packets. Trust metrics are essential for the operation of the trust-based mechanism during parent selection. We combine the trust-based OF and IDS methods to detect attackers with the help of nodes. Specifically, each node computes the trust value of its direct neighbours based on the information collected from an SRF-IDS detector. In this way, do not waste power for network monitoring. The best parent of each node is selected based on the calculated trust value. Devices with high trust value are chosen as parents, whereas those with lower trust values are avoided. The Whitefield simulator is a new framework that is used for SRF-IoT evaluation. Additionally, it provides more realistic results than the Cooja simulator, Contiki-NG’s embedded simulator, and allows deploying large scale scenarios with minimum effort.
One of the novelties of our approach is that a successful combination of trust-based and IDS-based methods is achieved. Most studies propose mitigation schemes for RPL routing attacks using either the former or the latter method. Combining the two approaches enhances the detection performance and allows easier detection of attackers. Furthermore, it is straightforward to add mitigation methods for additional RPL attacks. Another benefit is that nodes’ energy consumption is minimised. This is because nodes operate normally without any watchdog mechanism as in other trust-based solutions. SRF-IDS, made of an external set of detectors, monitors the network and provides the nodes with trust metrics.
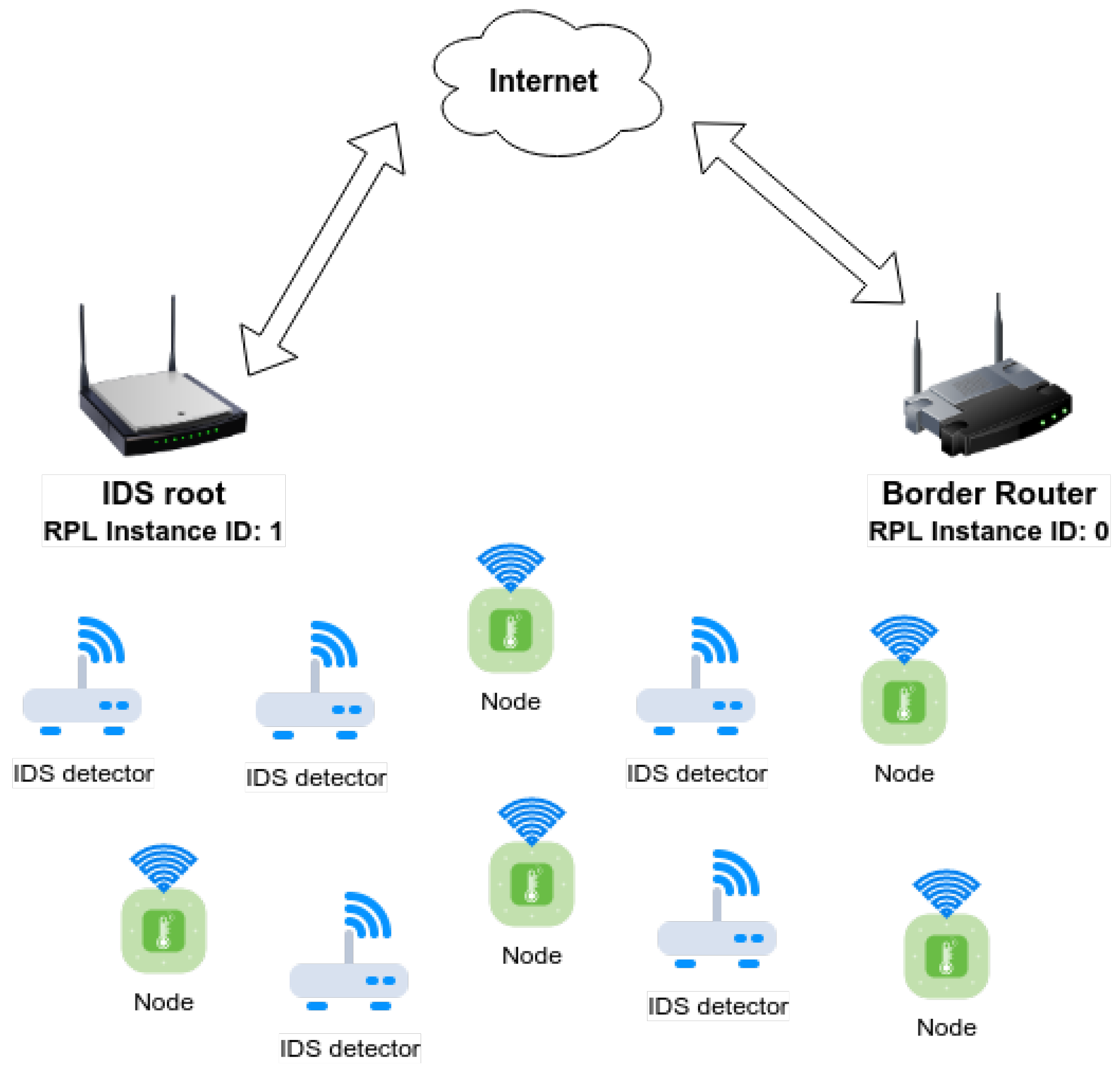
Another novelty of our approach is the deployment of SRF-IDS along with the normal network. In order to monitor the neighbouring network without interruptions, SRF-IDS is deployed in a different RPL instance than the normal network. SRF-IDS is an improved version of the prototype proposed in our earlier work [
12]. It consists of a centralised router that hosts detection module and acts as a firewall, whereas decentralised detectors are responsible for traffic monitoring, and local detection. Alerting monitored nodes with trust metrics is also the task of SRF-IDS detectors. RPL protocol was altered to allow communication between SRF-IDS detectors and monitored devices. The specification of the RPL protocol should be modified to allow the operation of SRF-IDS with other systems.
The key contributions of this paper are as follows:
In our previous work [
12], an initial IDS prototype was presented. SRF-IDS, an enhanced threshold-based IDS, is developed and deployed in this paper. It uses an overlay approach to provide a separate mechanism to monitor devices and help neighbouring nodes isolate malicious actors.
A novel security framework for RPL-based IoT networks (SRF-IoT) has been designed and proposed to avoid routing attacks, including a combination of rank and blackhole attacks. The framework consists of the threshold-based IDS, called SRF-IDS, and a trust-based OF, called SRF-OF. It has been implemented in the RPL protocol and evaluated in various scenarios under routing attacks.
Experimental results demonstrate that the SRF-IoT framework can effectively detect and help nodes to avoid malicious nodes. Our proposed framework showed 92.8% PDR, an almost five times reduction in the number of packets dropped, and a threefold decrease in the number of parent switches in scenarios with active blackhole and rank attacks. A new simulator, called Whitefield framework, which combines the NS-3 simulator with the Contiki-NG operating system, is used for evaluating the SRF-IoT framework. To our knowledge, this is the first work in the literature in which the Whitefield framework is used as the main simulation tool.
The rest of the paper is organized as follows. In
Section 2, we provide the required background information, including an overview of the RPL protocol, attacks against it, and IDS-based, trust-based, and protocol-based mitigation methods suggested for various RPL attacks. In
Section 3, we describe our proposed SRF-IoT framework, including the general operation and the network topology of the system. In
Section 4, the various processes and the design of the SRF-IoT framework is described in detail, including the improved external IDS, the procedure of gathering, calculating, monitoring, and updating trust metrics from the IDS, and the detection mechanism. In
Section 5, we describe the algorithms and implementation details of the SRF-IoT framework, including the communication module and the development of SRF-OF and trust in RPL-lite, as well as the studied attacks in Contiki-NG, namely the rank and blackhole attacks. In
Section 6, we present the evaluation of our SRF-IoT framework, including the scenarios and considered simulation settings, the configuration of evaluation metrics, and the evaluation results. A comparison of the observed results with related works is also provided. Finally,
Section 7 concludes the paper and discusses relevant future work.
4. SRF-IoT Design
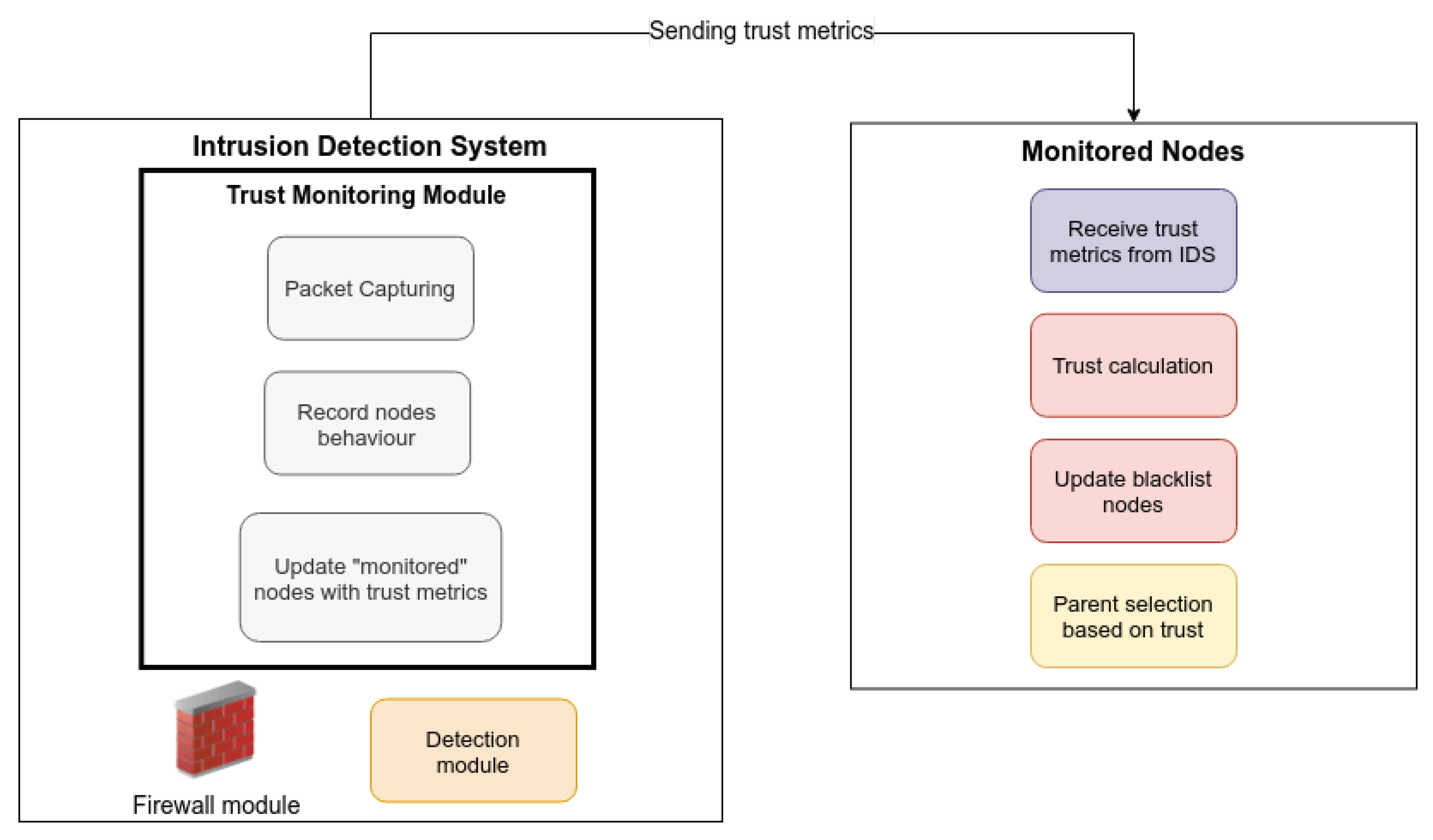
The proposed framework consists of an anomaly-based intrusion detection system (SRF-IDS) and an improved trust-based version of RPL protocol. The IDS from our previous work is enhanced to allow the operation with the monitored network. Moreover, decisions are taken in a distributed way. Apart from IDS, the RPL protocol is modified to consider trust values as method of evaluation for parent selection. We define the following terms:
Monitored network: The network that is being monitored by the SRF-IDS.
Monitored nodes: The nodes that belong to the network that is being monitored by SRF-IDS.
Neighbour: The node Nb is a neighbour of Na only if Nb is in transmission (TX) range of Na. That means Nb could provide a route to sink/BR.
Below, the various processes and the design of SRF-IoT scheme are described in detail.
4.1. External SRF-IDS
A main component of SRF-IoT scheme is the external SRF-IDS. It consists of two types of devices: an SRF-IDS root and SRF-IDS detectors. The SRF-IDS root is actually a router responsible for taking final decisions for malicious nodes, whereas SRF-IDS detectors are sensor devices operating in promiscuous mode to gather information from the monitored network.
One of the novelties of this work is the ability of SRF-IDS to operate independently in a different RPL instance without interfering with the monitored network. This is achieved by using a unique RPL InstanceID in packets, only for SRF-IDS nodes. We revised our hybrid-based IDS from previous work [
12,
30,
31] by adding more detection mechanisms for RPL-based attacks, allowing local decision-making by SRF-IDS detectors, and enabling communication between SRF-IDS detectors and neighbour RPL networks. Specifically, the new SRF-IDS can monitor a network for blackhole and rank attackers. However, the actual detection is done by the monitored nodes themselves and not by SRF-IDS. A malicious actor usually combines blackhole and rank attacks so that nodes select the attacker as parent, and then all packets going through the attacker are dropped. To detect blackhole attackers, SRF-IDS detectors are deployed near the devices of the monitored network so that network packets are captured and analysed. After processing network traffic, SRF-IDS detectors can decide locally if a suspicious node exists or not, and in the former case an alert with useful metrics is sent to nearby monitored devices. Hence, SRF-IDS operates in a decentralised way to combat malicious actors more efficiently.
Another feature is that SRF-IDS detectors are able to send RPL control messages to IoT devices in the monitored network to inform about the possible attacker. Implementing this required a minor modification in the monitored devices so they can correctly parse the SRF-IDS RPL packet. Also, a different RPL InstanceID was needed as discussed in
Section 3.2. In this way, a communication between the SRF-IDS network and the monitored network is achieved and malicious nodes are isolated. As an extra security feature, the SRF-IDS root has an embedded firewall to block malicious IPs. In case a malicious node is detected, its IP is forwarded to the SRF-IDS root for blacklisting. For other attacks, such as DIS flooding, SRF-IDS detectors report suspicious nodes to the SRF-IDS root for further decision making [
12].
4.2. Gathering Information from SRF-IDS
The first and most important process of the system is to collect information about the network. SRF-IDS is responsible for this, using the deployed SRF-IDS detectors. Specifically, SRF-IDS detectors capture network traffic from monitored networks and save packet metadata in a local database. An algorithm then runs to confirm if packets are forwarded or not to the next hop. The outcome of the algorithm is communicated with the devices belonging to the monitored network for further processing. Only monitored devices that are in TX range of SRF-IDS detectors will receive the metrics. Operating SRF-IDS in promiscuous mode in a different RPL instance is a novelty that allows easy deployment like a plug-n-play system. Additionally, no extra energy is consumed from smart devices in the monitored network to sniff any traffic. All the processing is done in SRF-IDS detectors, and only useful metrics are transferred to monitored network. It is important to note here that nodes in the monitored network can be benign or malicious. SRF-IDS detectors will try to communicate with any type of neighbour in its TX range because it is impossible to know which node is an attacker or not. We assume that SRF-IDS packets will be encrypted to avoid being exploited by attackers.
4.3. Calculating Trust
The calculation of trust value of a node until time
T occurs in this process. The formula to calculate the direct trust that device
Da holds for device
Db until time period
T is given by
DT(Da,Db)T. The number of packets successfully transmitted between devices
Da and
Db until time period
T is given by
PTab(T). The total number of packets forwarded by device
Db on behalf of device
Da until time period
T is given by
PFba(T). Intuitively, the higher the number of packets
Db drops (i.e.,
PTab(T) − PFba(T)) the lower the trust
Da has in
Db should be. In order to be able to compare between devices, we normalised this by dividing it to the total number of packets that
Db forwards. Therefore, now the higher the proportion of the number of packets
Db drops to the total number of packets forwarded by
Db (i.e.,
[PTab(T) − PFba(T)]/PFba(T)), the lower the trust
Da has in
Db should be. The outcome of this formula, i.e.,
[PTab(T) − PFba(T)]/PFba(T), ranges between 0 (if all packets are forwarded) and infinity (if
Da sends many packets, but none are forwarded). Normalisation was the next step so that we get a value between 1 and 0, with 1 corresponding to the former case (maximum trust) and 0 corresponding to the latter case (minimum trust). In order to achieve it, the following function was used:
The above function takes x = 0 to f(x) = 1 and to f(x) = 0. The value achieved from [PTab(T) − PFba(T)]/PFba(T) needs to be scaled to reflect varying degrees of trust in different situations. For example, if a device is initially forwarding all packets, it has high trust value. In a later moment, if it behaves maliciously and drops the packets, its trust value should be reduced. For this purpose, a weight factor w is added before applying the f function. A weight factor is added to the equation to punish or reward nodes that may change packet forwarding behaviour accordingly.
Based on the previous explanations, direct trust calculations are computed as follows:
which is the result of multiplying the numerator and denominator of initial formula
f by
PFba(T). Weight factor
w can take the following values:
where
represents the number of packets forwarded, sniffed by SRF-IDS, for the specified node at time
t. To calculate the total number of packets forwarded until time
T we use:
The parameter node_verifiedT means that a node is verified by SRF-IDS that is behaving normally until moment T. We use this indicator to increase the weight factor so that a node is trusted by benign nodes, whereas an unverified node has a smaller weight. The fourth case has a condition that w is smaller if the node is verified, forwards packets, and the total number of packets forwarded are greater than the minimum number of forwarded packets (minimum_fw). The value of minimum_fw is 5, and it is used as an indicator to check if a node keeps forwarding packets after the initial verification. If a node is verified but the total number of forwarded packets are less than this parameter, weight becomes zero and trust is 100%. This ensures that a verified benign node will be fully trusted until it reaches the threshold minimum_fw. Weight is then applied in the formula.
Weight factor plays an important role because trust value depends on the obtained behaviour of the node. The general idea of weight factor is to use it in the OF formula so that a high trust score is calculated for an unverified node that behaves normally, keep the trust score at same levels if a node keeps forwarding packets to avoid unnecessary parent switches, and assign low trust score once a node does not or selectively forwards data packets. The values were chosen after various experiments so that a fair and balanced value is calculated for each node by the OF. The methodology followed was to initially assign zero weight was for fully trusted nodes and 1 to malicious nodes. However, simulation results showed that SRF-IDS detectors were not accurate in detecting malicious attackers. This happened especially in cases where a device is trusted initially and later attacks the network. Therefore, we decided to create different weight values with specific conditions to represent different cases and to improve the detection performance. As the network starts forming, we wanted to give all devices the chance to have high trust value. For this reason, initially the weight factor is 0.6 if nodes do not forward packets and are not verified. Moreover, in the case where nodes are still unverified but some packets are forwarded, the weight value increases by 0.2. This was done to stop nodes that behave suspiciously at the beginning but later behave normally. In the other case where a node is treated as benign and then becomes an attacker, we wanted to lower trust immediately. That is why the value of weight factor was 0.85. In the last case, we assigned 0.5 to weight factor to balance the trust value and assign a fair value to the node that is verified as benign. The zero weight factor, as explained, is assigned to a verified benign node which has not reached the minimum packets forwarded threshold and it is fully trusted.
The verification of a node is done with the help of the SRF-IDS component. The SRF-IDS detector keeps the following fields in a structure for a monitored neighbour node:
PFba = the total number of packets forwarded from device Db on behalf of device Da.
dstIPa = an array of IP addresses that device Da is usually sending the packets. The value is taken from the destination IP field in the packet.
verifiedIPa = a field indicating if the IP address of a node is verified or not. Initially, all nodes are unverified until SRF-IDS verifies them. A node is verified if it forwards a packet to next hop.
4.4. Monitoring/Updating Trust
Keeping the trust value up to date is significant to avoid interruption of network operation from malicious actors. Hence, SRF-IDS constantly monitors the network and sends updated metrics to the monitored nodes. SRF-IDS sends the updated metrics in two modes: interval-based and trickle-based. Interval-based transmission occurs every 3 min from SRF-IDS detectors to devices in monitored network so that malicious nodes are identified in a short time. Before packet transmission, SRF-IDS detectors verify that new metrics are actually available to send to monitored nodes; otherwise they skip the procedure.
Trickle-based transmission is based on RPL trickle timer implementation for transmitting DIO packets [
35]. Trickle timer is a dynamic mechanism embedded into RPL that tries to minimise the transmission of RPL control packets. SRF-IDS detectors send packets with updated metrics each time the trickle timer resets. Sending packets in two different modes ensures that SRF-IDS packets arrive successfully and at the proper time to monitored nodes to choose their best parent. Without any metrics, benign nodes use MRHOF. Once a benign monitored node receives a packet from SRF-IDS, it calculates candidate parent’s confidence value based on the new measurements. Metrics for monitored nodes are stored in SRF-IDS detectors and they are reset every 15 min to avoid storage capacity problems.
Trust values have different scales as shown in
Table 2. We defined the interval for the first three trust levels to be 25 because the weight factor may affect the calculations and cause rapid changes to the trust value. As a result, a big interval was needed to avoid unnecessary changes when the best parent algorithm is executed. In the higher levels of “High Trust” and “Full Trust”, the interval is defined to be 11 and 14, respectively. There is no specific reason for the interval. However, it is important to note that once a node reaches a trust value of 76 or more, it is considered trusted and the weight factor becomes zero. Therefore, the node will be in the “Full Trust” scale. If trust falls below the
min_threshold (less than 26), then a device is considered malicious and it is blacklisted. In addition, RPL local repair is triggered to allow nodes find new parents. In the opposite case, if a node is blacklisted and the trust value is above 50, the node is removed from the list of malicious nodes. Initially, trust value 63 is assigned by default to all nodes joining the network. This is to allow nodes to choose the best parent using other metrics, such as rank, until trust metrics become available. Lists with malicious nodes are stored locally in each benign node so that parent selection algorithm avoids blacklisted nodes. In the case where a node stops attacking, the SRF-IDS will recalculate it’s trust value. However, weights are adjusted and the node will gradually become fully trusted.
4.5. Identifying Malicious Nodes
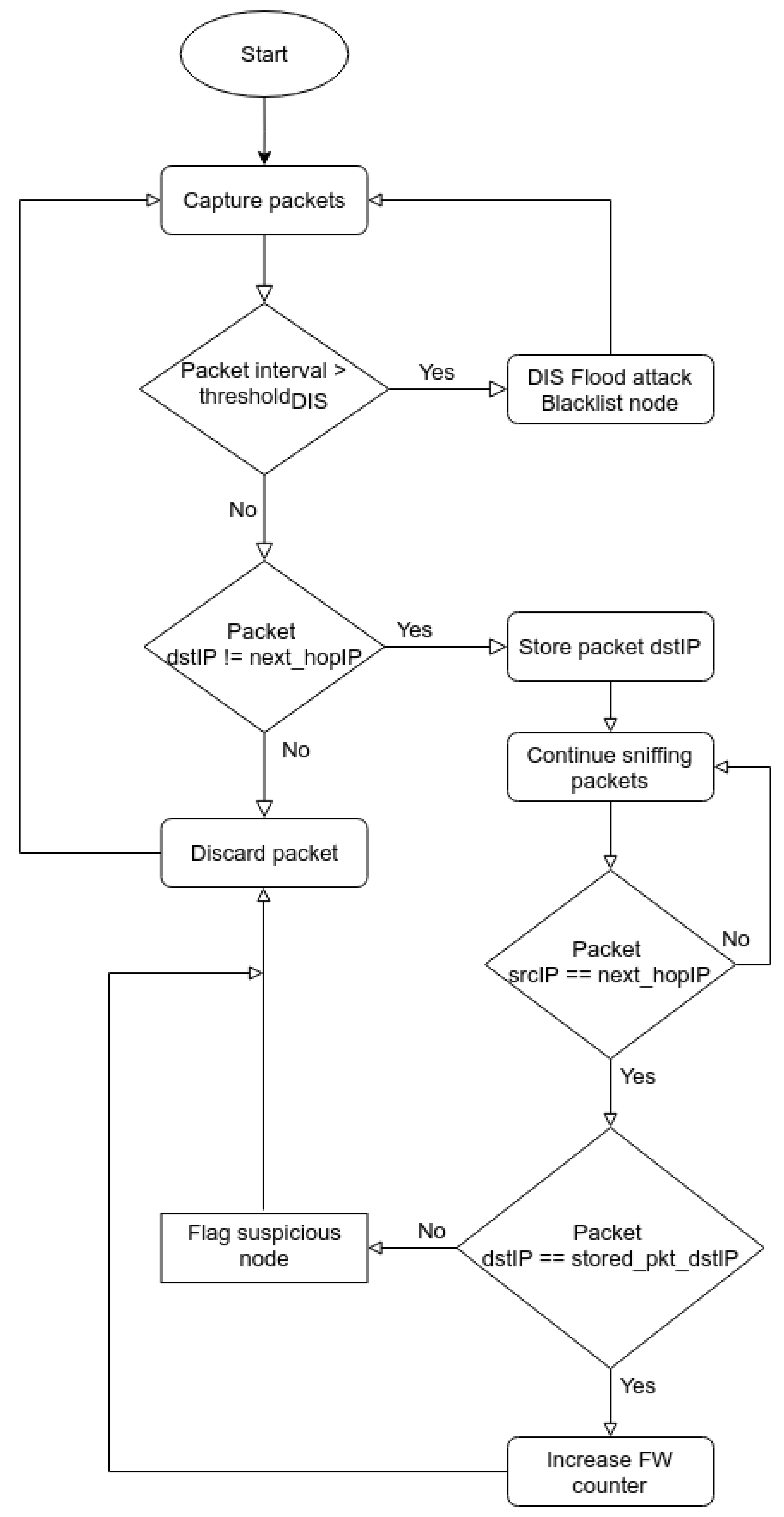
In case a node starts attacking the network using blackhole and rank attacks, SRF-IDS will immediately notice this behaviour in the packet forwarding metric. A packet is then sent to the monitored network so that nodes will assign a low trust for these neighbours. The algorithm used by SRF-IDS detectors to detect the various routing attacks is shown in
Figure 3. The procedure starts by enabling a promiscuous mode in SRF-IDS detectors to start sniffing network traffic. Once a packet is captured, its packet type is checked and proper thresholds are used to determine if the network is under DIS flooding attack. Specifically, if the packet interval is above the predefined
thresholdDIS, then the SRF-IDS detector alerts the network administrator for a possible DIS flooding attack, the node is reported to the SRF-IDS root for blacklisting, and the SRF-IDS detector continues packet sniffing. If the packet interval is at normal levels, the packet is checked if it needs to be forwarded by the received node. This is done by checking the destination IP (
dstIP) field to be different with the next hop IP (
next_hopIP). In the case where
dstIP is equal to the received node IP, the packet is discarded and the procedure restarts. Otherwise, the
dstIP is stored in a table for further checks. SRF-IDS detectors continue to sniff packets in order to decide if the neighbouring node actually forwards the packets. This is translated into the following condition: if the captured packet source IP (
srcIP) is equal to
next_hopIP then it means the neighbour (next hop) node transmitted the packet. The next check is to validate the destination node. If the stored packet IP (
stored_pkt_dstIP) is equal to the new destination IP (
dstIP) then the packet is forwarded correctly, and the node’s packet counter is increased by one point. In case
srcIP equals
next_hopIP but the
dstIP is not expected, it means the packet is not forwarded, and the SRF-IDS flags the device as a possible malicious node. The last step is to discard the packet and continue capturing network packets for other nodes.
6. Experimental Evaluation of SRF-IoT Framework
The evaluation of the SRF-IoT framework is presented in this section. The scenarios explored are initially described along with the simulation tools. Next, metrics and relevant configurations used are presented. Evaluation results are described in detail in the last subsection.
6.1. Scenarios
We examined three main scenarios: normal, malicious using MRHOF as OF, and malicious using SRF-OF as OF. Specifically, a normal scenario is an environment without any attackers. Nodes are operating normally and are using the default MRHOF to choose a parent.
In the malicious scenario, one or more attackers exist, and all nodes are using the default MRHOF. This scenario is studied to understand the impact that rank and blackhole attacks have in the network. The last malicious scenario is simulating an environment where again benign and one or more compromised nodes exist but nodes are using the new implemented objective function called SRF-OF. SRF-IDS operates in a different RPL instance, and, thus, nodes are using the default MRHOF. SRF-IDS is deployed in all scenarios only for comparison reasons as we increase SRF-IDS detectors in the network to find the optimal case. SRF-IDS detectors capture metrics only and do not help in parent selection in normal and BHR scenarios.
The different types of nodes used in our simulations are shown in
Table 3. As can be seen, SRF-IDS nodes have different RPL InstanceID than other nodes. In addition, Sink/BR and SRF-IDS Root play the role of sink for both networks. Benign and malicious nodes are configured to join the network and start sending UDP packets to BR once the DODAG network is formed. However, malicious nodes start attacking the network after 2 min.
The number of nodes deployed in each scenario is presented in
Table 4. There are 30 benign nodes in all scenarios and six malicious nodes in the malicious scenarios. A varying number of SRF-IDS detectors are deployed in the network to study and find the optimised number of detectors to avoid the attackers. In normal and malicious scenarios with MRHOF, SRF-IDS detectors are deployed with the Trust Monitoring module disabled. SRF-IDS is deployed in these two scenarios for comparisons and to help us generate results. The Trust Monitoring module, as noted in previous sections, is enabled only when the SRF-IoT scheme is evaluated and, thus, monitored nodes use the SRF-OF.
6.2. Simulation Tools
Several simulators are being used in the literature. In many studies, Contiki-NG is simulated using a Cooja simulator [
37], which is included in the Contiki OS. In our previous work [
12,
31], Cooja was used for emulating hardware. However, as the network becomes larger, the need for more CPU and memory resources increases. These issues are resolved with a new simulator, called the Whitefield framework [
38]. According to its author, Whitefield provides a simulation environment for wireless sensor networks by combining realistic PHY/MAC layer simulation with the native mode use of popular IoT operating systems. In our case, we use Contiki-NG as the OS, which provides the network layer and above, whereas the NS-3 simulator provides the PHY/MAC/RDC layer. Moreover, Whitefield generates logs and pcap files for each simulation. This is really useful for monitoring and auditing simulation results. The only drawback of using Whitefield is that deployed nodes are native processes running in NS-3 and not emulated hardware. Therefore, monitoring energy consumption or other hardware-specific metrics is not possible.
6.3. Configuration and Metrics
The settings and metrics utilised for evaluation purposes of the SRF-IoT framework are discussed in this subsection. We considered the median value in our calculations as it is robust against outliers. In many experiments, due to the random behaviour of the attackers, observed results differ significantly. Therefore, to get a more realistic picture of the results and avoid outliers, we used median value. The metrics used are the following:
Median Packet Delivery Ratio (PDR): Indicates the median value of the ratio of the total number of unicast packets received by BR up to the total number of unicast packets generated by all benign and malicious nodes. It does not include UDP re-transmitted packets.
Median Parent Switch: Presents the median value of the number of parent switches that benign and malicious nodes execute during the simulation. A parent switch happens to select a better route to the BR. Changing parent results to changing the rank of a node.
Median Packets Dropped: Shows the median percentage of packets dropped by the attackers during the simulation. Malicious nodes drop all types of packets that normally should be forwarded to next hop.
Median IDS Packet Overhead: Indicates the median percentage of the SRF-IDS detector’s packets sent to SRF-IDS root and the monitored network during simulation. The value is calculated from the number of packets exchanged in N repetitions.
Below, the mathematical definitions for the metrics are provided. Let
be the packet delivery ratio for repetition
r where
Rcvd is the total number of packets received at BR,
k is the number of node sending the packets,
n is the total number of nodes, and
Pk is the total number of packets sent from node
k. The Median PDR,
E[DRpkt], is given by:
where
r is the repetition number,
m is the total number of repetitions for each simulation, and
Median(S) is the median value of the set
S. Packet delivery ratio from all repetitions are included in the set
S to calculate the
Median(S) value.
The Median Parent Switch,
E[PS], is given by:
where
Pk the parent switch of node
k,
PSr the sum of parent switches for repetition
r,
r the number of repetitions for each simulation, and
Median(PS) is the median value of the set
PS. The set
PS contains all parent switches for all repetitions so that the
Median(PS) value is calculated.
The Median Packets Dropped,
E[Dpkt], is given by:
where
Dropr the total packets dropped in repetition
r,
TAk the total number of packets transmitted from node k including multicast and unicast packets,
Dr the percentage of packets dropped in repetition
r,
m the number of repetitions for each simulation, and
Median(D) is the median value of set
D. The total packets dropped from all repetitions are included in set
D so that the
Median(D) is calculated.
The Median IDS Packet Overhead,
E[IDS], is given by:
where
k is the number of node sending the packets,
n is the total number of nodes,
TAk in (10) is the total transmitted packets from node k including multicast and unicast packets,
Sentr is the sum of packets sent in repetition
r,
a is the number of SRF-IDS detector,
b is the total number of SRF-IDS detectors
IDSa is the total number of SRF-IDS packets sent from SRF-IDS detector
a to SRF-IDS root,
m is the total number of repetitions for each simulation,
Ir the SRF-IDS packet overhead percentage in repetition
r, and
Median(I) is the median value of set
I. The calculated values from all repetitions are added in set
I to calculate the
Median(I) value.
Regarding simulation configuration, the simulator called Whitefield framework provides a configuration file in which proper settings were defined. In that file, various simulation options can be defined by the user. The options used are shown in
Table 5. Simulation execution time is defined as 60 min. Normal and SRF-IoT scenarios using SRF-OF are repeated 10 times, whereas malicious scenarios using MRHOF are repeated only four times. The reason for repeating the malicious scenarios only four times is that SRF-IDS had the TM module disabled, and no significant difference was observed when the scenarios were repeated four or more times. Regarding normal and SRF-IoT scenarios, the number of repetitions is higher as the observed results varied, and we wanted a large sample for analysis. SRF-IDS detectors in normal and SRF-IoT scenarios are used only to capture traffic and calculate metrics based on the observed measurements. Consequently, using more SRF-IDS detectors allow us to collect a large sample for analysis. In contrast, SRF-IoT scenarios have SRF-IDS deployed with TM enabled. This is to investigate how well the proposed security framework isolates attackers and find the recommended number SRF-IDS detectors that have to be deployed in a network for best protection. The seed number plays a significant role in simulations. It affects the behaviour of the nodes regarding processing and packet transmission times. Therefore, we use random seed in each repetition so that the Whitefield simulator produces random results in each run. The simulator’s default configuration of MAC packets re-transmissions is three times, and the maximum number of packets waiting in the buffer in the MAC layer is 20.
6.4. Evaluation Results
Evaluation results from simulating the SRF-IoT scheme are presented in this subsection. From this point, we reference to malicious scenario using MRHOF as BHR scenario, normal scenario using MRHOF as normal scenario, and malicious scenario using SRF-OF as SRF-IoT scenario.
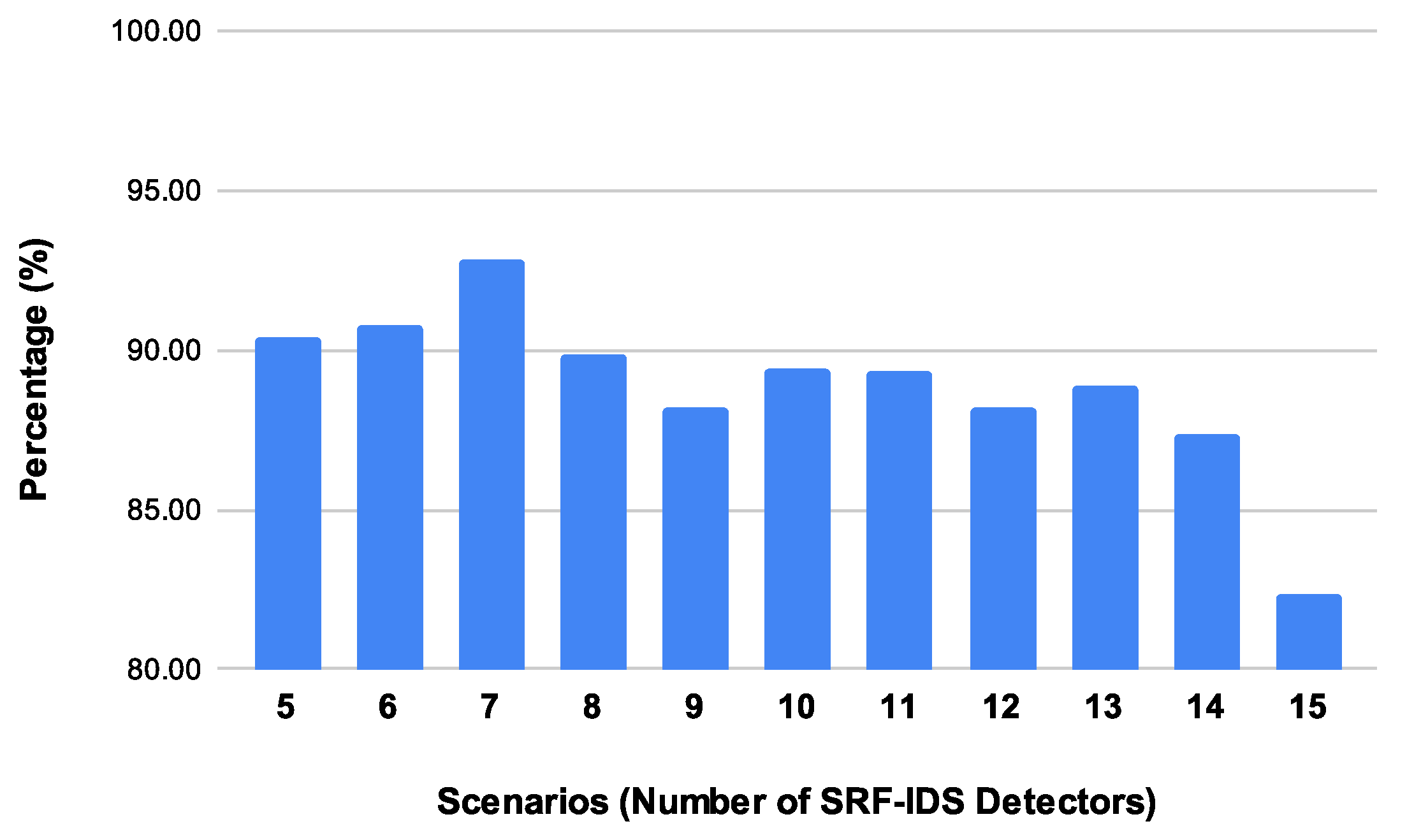
Starting with
Figure 4, the Median (PDR) of SRF-IoT framework is presented for scenarios where 5 to 15 SRF-IDS detectors are deployed. Overall, PDR in monitored network is kept at high levels with the help of the SRF-IoT framework. This can be clearly identified from the figure, as the median PDR starts from 90.8% when 5 detectors are deployed, then reaches the maximum of 92.8% in scenario with 7 detectors, and then the PDR declines as the number of detectors increases, reaching the minimum of 82.4% with 15 SRF-IDS detectors. This is expected because multiple SRF-IDS detectors generate extra overhead in the network and monitored nodes may receive other nodes’ metrics, not related to their direct neighbours. Therefore, monitored nodes drop more unrelated packets, reducing the PDR metric.
A comparison of the Median PDR of different scenarios is shown in
Figure 5. Normal scenario has a median value of almost 95% in all simulated cases, whereas in the BHR scenario this percentage drops more than 15%. This big difference shows how attackers can degrade the performance of the network. Comparing the median number of PDR in SRF-IoT scenarios versus normal scenarios, we can see that a small difference of a minimum 5% and maximum 13% exist. This means that as more SRF-IDS detectors are deployed, the SRF-IoT framework’s performance declines. However, those results indicate that SRF-IoT framework can assist nodes to avoid extra processing and energy overhead and operate in the same levels as in normal scenarios.
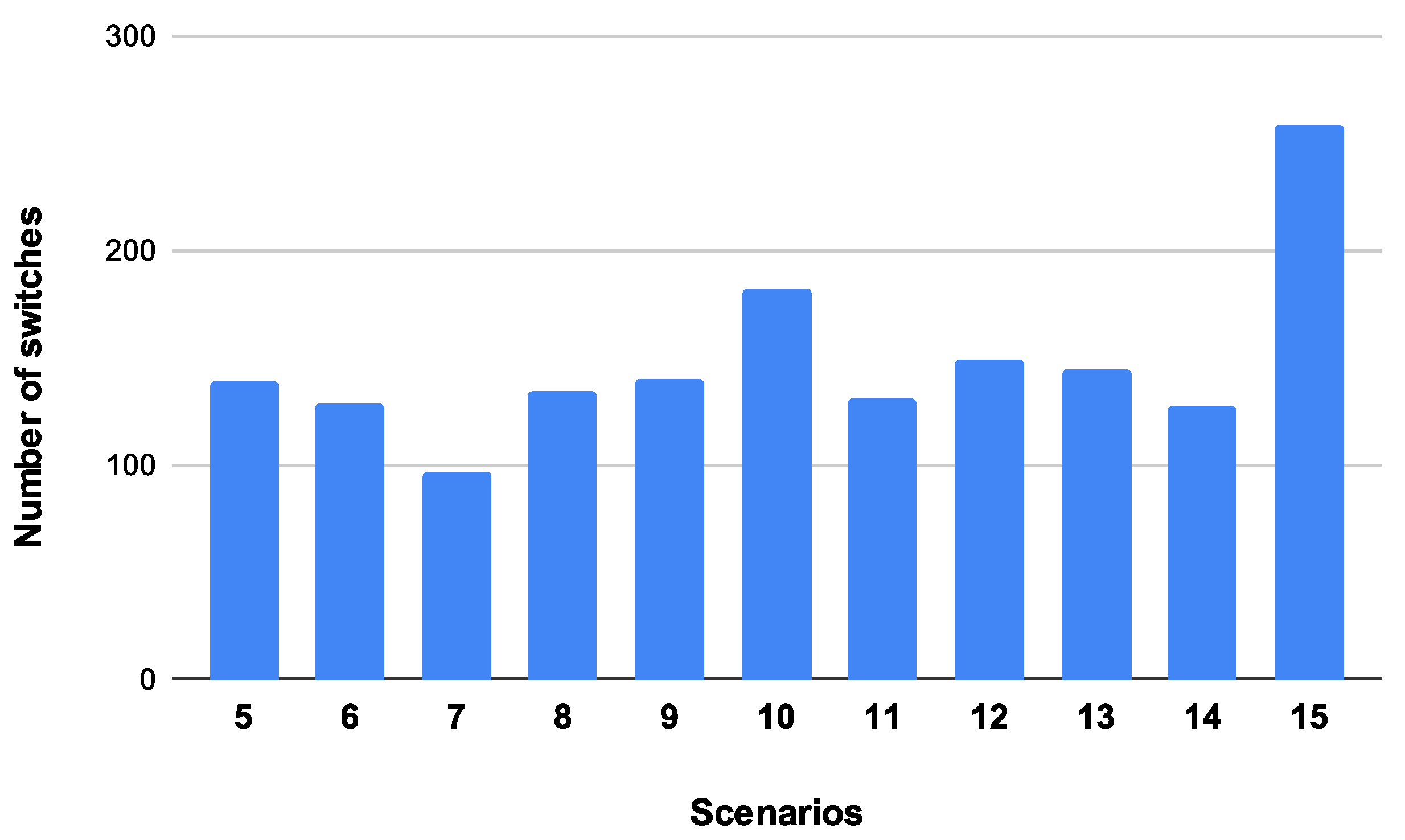
Looking at the Median Parent Switch in
Figure 6, results depict that our proposed framework requires fewer than 200 parent switches when deploying fewer than 15 SRF-IDS detectors. Specifically, the bar chart shows that SRF-IoT scheme has a median of 140 parent changes with 5 deployed SRF-IDS detectors, declining to 97 changes with 7 detectors, and then going up to 258 when SRF-IDS detectors are 15. It is clear that when having more than 12 SRF-IDS detectors, parent changes are almost doubled. An explanation is that as we increase SRF-IDS nodes, multiple detectors monitor similar nodes, and they send multiple metrics for the same monitored nodes. This could lead to high or low trust values which in turn leads to parent changes. The normal scenario indicates that parent switch should occur fewer than three times per node on average.
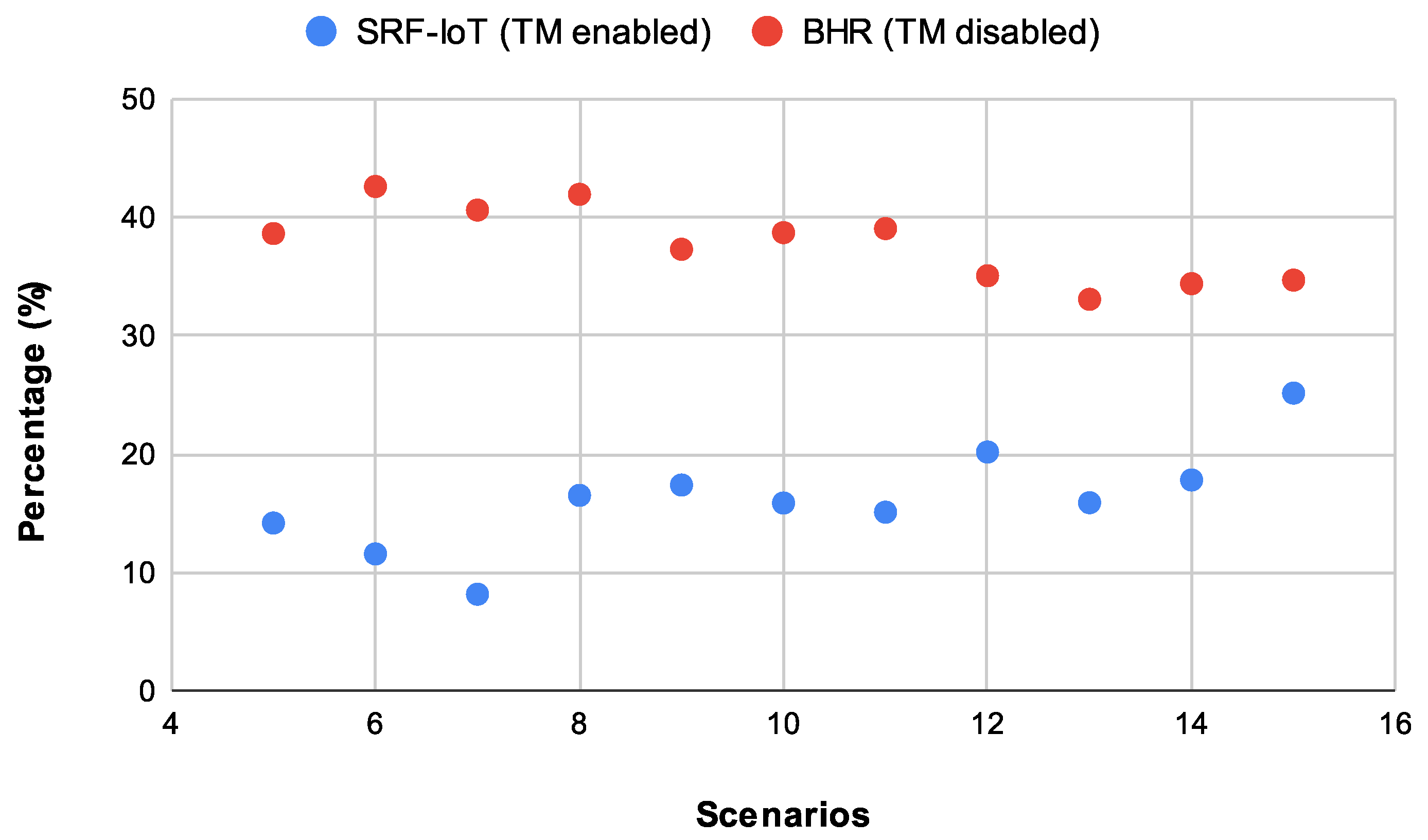
Figure 7 compares the values of the Median Parent Switch metric for three different scenarios: SRF-IoT, BHR, and normal. Generally speaking, the scatter chart indicates that SRF-IoT framework achieves low parent changes, with a small increase from the levels of normal scenarios. Looking more closely, using the SRF-OF, nodes change parents almost three times less than in BHR. Attacking the network causes approximately 600 parent changes on average, whereas in SRF-IoT we have fewer than 190 switches, and in normal scenarios we have a median of 30 switches. The only exception is the case with 15 SRF-IDS detectors in which SRF-IoT sees a surge in parent changes. The high parent switch number explains the low PDR that we previously saw in that scenario. Assuming the selected parent is an attacker, we expect to have more dropped packets, affecting the PDR metric. This means malicious actors successfully affect the network performance using rank and blackhole attacks. Another conclusion is that the SRF-IoT scheme drastically reduces parent switches in almost all cases, and even in the worst case it keeps the network more stable than in BHR scenario in which both PDR and parent switches metrics are high.
The Median Packets Dropped obtained after deploying 5 to 15 detectors in SRF-IoT and BHR scenarios are displayed on
Figure 8. Looking at the BHR scenario, the median percentage of packets dropped is initially 38.6% when 5 SRF-IDS detectors are deployed. The percentage fluctuates around 40% until the scenario with 12 SRF-IDS detectors, in which the percentage declines to 35%. This is related to the previous parent switch metric because in scenarios with higher packets dropped, more parent changes occur. Regarding the SRF-IoT scenario, it has an increasing trend of dropping packets as the number of SRF-IDS detectors becomes larger. A median of 14.2% of the packets are dropped when five SRF-IDS detectors are deployed, falling to 8.2% with seven detectors and then rising to 16.5% with eight detectors. The median value then remains at the same level apart from the scenarios with 12 and 15 SRF-IDS detectors in which the median dropped packets climb up to 20.2% and 25%, respectively. Therefore, our framework may assist the network to avoid blackhole attackers and reduce dropped packets.
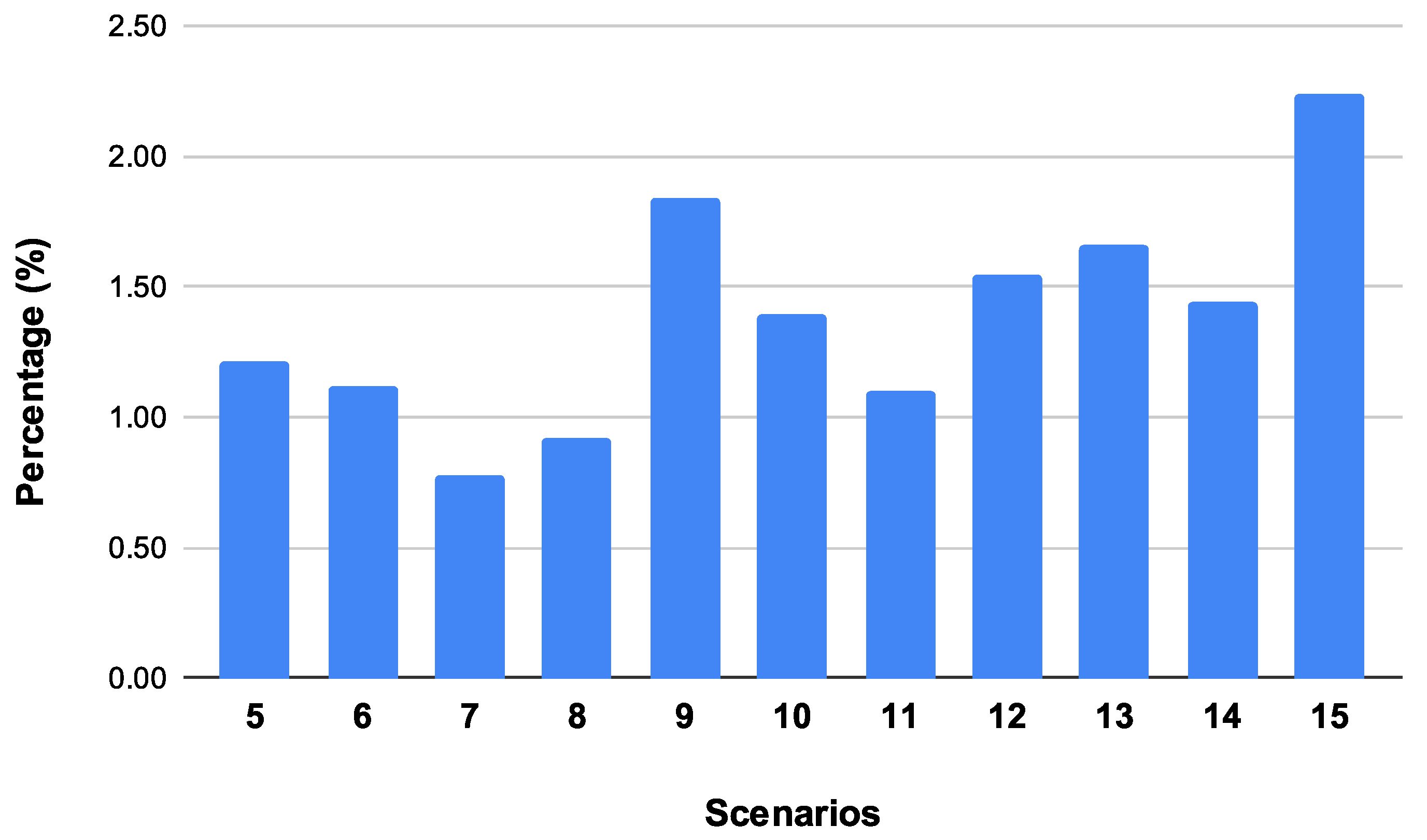
As a last metric, the Median SRF-IDS Packet Overhead is illustrated in
Figure 9. In all scenarios, SRF-IDS generates less than 2.5% traffic overhead in the network. The only case where the SRF-IDS packet overhead is relatively high is in the scenario with 15 SRF-IDS detectors. The median value reaches 2.2% because the monitored nodes are trying to avoid attackers. We have the highest median parent switches in this scenario—the number of dropped packets is also increasing, and thus, SRF-IDS detectors attempt to help monitored nodes by sending them trust metrics. All the previous metrics indicate that the monitored network is greatly affected by attackers in that specific scenario. Generally, the number of packets sent from SRF-IDS detectors depends on the number of monitored nodes. For example, SRF-IDS detectors that are deployed near multiple nodes of the monitored network send more packets in order to update nodes with trust metrics. In our case, SRF-IDS nodes are randomly deployed in the simulated scenarios. As depicted in the column chart, SRF-IDS helps monitored nodes avoid attackers with very low packet overhead. A relatively high packet overhead percentage is depicted in the scenario with nine SRF-IDS detectors. The reason for the high median percentage in the scenario with nine detectors in comparison with other scenarios such as 13 or 14 SRF-IDS detectors is that in the specific case, the SRF-IDS detectors detect malicious attackers in the network and try to help monitored nodes by sending them many packets to alert neighbouring nodes. Some of these packets are lost and others are received by benign nodes. As a result, nodes receiving those alerts try to change parents, and, thus, the median parent switch metric shown in
Figure 6 is also high in this scenario.
In conclusion, the experimental evaluation of the SRF-IoT framework against rank and blackhole attackers showed higher PDR, lower packets dropped, as well as lower parent switches in comparison to the malicious scenarios where SRF-IoT had TM disabled. Results indicate that the proposed framework can aid nodes to choose the proper nodes as parents and avoid the compromised ones. According to the evaluation results, deploying seven SRF-IDS detectors in a network with at least 36 nodes generates the best results, assuming that one-sixth of them might be compromised. Moreover, results depicted that deploying 5 to 10 SRF-IDS detectors still helps the IoT network to isolate and avoid attackers.
6.5. Comparison with Related Works
This section focuses on the discussion and the comparison of the results obtained from the proposed SRF-IoT framework with other similar studies.
In
Table 6, a comparison of our work with four similar studies is presented. Specifically, the evaluation results from the studies of MRTS [
24], SRPL-RP [
26], and SecTrust-RPL [
26,
28] are compared with our proposed SRF-IoT framework. The metrics used in the comparison are the PDR, parent switches, and packets dropped. In addition, the total number of nodes deployed in each experiment is compared.
The related works that are used for comparison purposes explore rank or blackhole attackers in medium scale networks. As we wanted to have a similar basis for comparing all the related studies, the results from
Section 6 are referenced and used. That specific section evaluates the SRF-IoT framework in a scenario where 30 benign nodes are deployed, and 6 nodes launch a combination of blackhole and rank attacks. Thus, simulations have similar configurations with the other work.
As it can be seen from
Table 6, most of the studies provide the PDR metric, whereas only one of them provides the parent switch and another one the packets dropped metrics. In our work, we provide all of the aforementioned metrics. Looking at the PDR metric, the highest PDR value is achieved by SRPL-RP with 98.48% in a small network of 16 nodes plus the 4 rank attackers. The second highest PDR value is from our SRF-IoT framework, which achieves 92.8% in a network of 30 benign nodes plus 6 attackers that launch combined blackhole and rank attacks. The MRTS study follows with a PDR up to 90% in a network with 27 nodes plus the 3 blackhole attackers. SecTrust-RPL exhibits the lowest PDR with a value of 80%, with the same number of nodes are deployed in the network as in MRTS. Comparing the rest of the metrics, parent switches of the SRF-IoT framework are slightly more than the 80 switches observed in the MRTS work. Regarding packets dropped, our work keeps the percentage near 8%, which is very low in comparison with the 22–23% recorded in the SecTrust-RPL study.
All in all, it has been shown that the proposed SRF-IoT is an effective solution that achieves the best results among the current related studies that deploy fewer nodes and study only single attacks. SRF-IoT was evaluated in a larger network than other studies using a combination of blackhole and rank attacks and demonstrates superior performance in most cases. Nevertheless, given the variation in the results with the variation in the number of detector nodes, the study of the application of machine learning techniques to dynamically optimise the number of detector nodes could be considered as a future enhancement.