Highlights
What are the main findings?
- To solve the challenges of targeted energy flexibility and hunting safety cases, we have provided here the novel concept of trustworthy communities with experimental solutions. The conceptual solutions rely on a hierarchical model consisting of shared trust infrastructure, security control channel, verifiable credentials, and hierarchical identity management, on top of which smart contracts-based communities can be established.
- An evaluation of the trustworthy communities’ solutions was carried out in the energy flexibility case, where energy flexibility resources of one simulated and two real buildings were aggregated by a flexibility aggregation platform for trading in an energy flexibility marketplace. Respectively, the provided solutions were evaluated in the hunting safety case, where hunting safety smart phone application of a hunter and smart watch of person exchanged presence and location information for preventing hunting accidents.
What is the implication of the main finding?
- The evaluations indicate that conceptual solutions for trustworthy communities fulfil their purpose and contribute towards making energy flexibility trading and hunting safety possible and trustworthy enough for participants. This means that the provided solutions were applicable in two different cases from different application domains. The validation showed that the provided community solutions worked in a real-time manner with the physical assets in a functional sense.
- However, performance and scalability aspects were not considered, and thus they require further research and enhanced test set-ups. In addition, further studies related to community applications, verifiable credentials with wallets, sharing values and incentives, authorized trust networks, dynamic trust situations, time-sensitive behavior, autonomous operations with smart contracts, and security assessments and applicability are needed.
Abstract
The aim of this research has been to enable the management of trustworthy relationships between stakeholders, service providers, and physical assets, which are required in critical energy and mobility cyber–physical systems (CPS) applications. The achieved novel contribution is the concept of trustworthy communities with respective experimental solutions, which are developed by relying on verifiable credentials, smart contracts, trust over IP, and an Ethereum-based distributed ledger. The provided trustworthy community solutions are validated by executing them in two practical use cases, which are called energy flexibility and hunting safety. The energy flexibility case validation considered the execution of the solutions with one simulated and two real buildings with the energy flexibility aggregation platform, which was able to trade the flexibilities in an energy flexibility marketplace. The provided solutions were executed with a hunting safety smartphone application for a hunter and the smartwatch of a person moving around in the forest. The evaluations indicate that conceptual solutions for trustworthy communities fulfill the purpose and contribute toward making energy flexibility trading and hunting safety possible and trustworthy enough for participants. A trustworthy community solution is required to make value sharing and usage of critical energy resources and their flexibilities feasible and secure enough for their owners as part of the energy flexibility community. Sharing the presence and location in mobile conditions requires a trustworthy community solution because of security and privacy reasons, but it can also save lives in real-life elk hunting cases. During the evaluations, the need for further studies related to performance, scalability, community applications, verifiable credentials with wallets, sharing of values and incentives, authorized trust networks, dynamic trust situations, time-sensitive behavior, autonomous operations with smart contracts through security assessment, and applicability have been detected.
1. Introduction
Industries are increasingly using cyber services that rely on monitoring and controlling physical devices over communication networks. Such systems are also known as cyber–physical systems, which typically use a distributed information processing loop, where the monitoring and controlling of physical devices operate over heterogeneous communication networks and use autonomous computing means to provide smart information-based services for users. When several players are involved in such a cyber–physical system, a lack of digital trust causes great critical challenges. For example, smart use of energy resources, such as electric vehicles, heating of buildings, and solar power plants, is very critical in terms of digital trust, but they can also be very valuable in the energy markets. Digital services relying on the presence and location of people at home, in traffic, or in the archipelago opens several possibilities for innovation. However, the lack of privacy and trust seems to impede them. More specifically, the digital trust challenge is related to the critical relationships between people, service systems, and physical devices. The referred services are today usually tightly coupled with the applied embedded products and specific service provider (SP) clouds [1,2]. However, the referred embedded products and/or exposed information may be owned by stakeholders other than the referred SP. In addition, the referred owners may have specific security and privacy requirements, trust relationships, and contracts related to the access and use of the information and the devices. In the preceding/parallel research of this work, we have contributed solutions for required digital trust and successfully evaluated the solutions in a safety-critical use case related to remote driving [3]. In this research, we apply the respective types of trust solutions and focus on enabling trustworthy communities, which is the main contribution area of this research.
The starting points of this research have been the challenges and needs for trustworthy communities in real industrial cases related to energy and mobility. Building new energy production resources is expensive and slow, and simultaneously, energy consumption is increasing quite rapidly due to new needs arising, e.g., from electric mobility. On the other hand, there are more and more new types of smaller-scale energy production resources, such as solar power plants, whose energy production capabilities are not properly under the control of the energy stakeholders for natural reasons. The load balancing in the electric grid is very essential, and it is usually reached today using the (automatic) energy resources controlled directly by grid operator(s) for stabilizing the demand and response. However, achieving the balance can be expensive in the peak energy consumption hours of a day when more production needs to be rapidly added to keep the load balance in the grid. The smart use of energy resources, such as heat pumps, charging of electric vehicles (EVs), energy storage, and control of energy consumption, could enable lowering the peak loads in the electric grid. The energy consumption and production situation could be monitored, and controlling the use of energy resources could be organized in a smart way. The capability to up or downscale energy consumption or production is called energy flexibility. Enabling such energy flexibility requires smart aggregation as well as digital trust solutions with agreed contracts; flexibility trading with values or incentives needs to be shared. The contract-based communities and smart aggregation are required because the tradable unit in the energy flexibility markets is bigger than the flexibility potential offered by the energy resources in a building, and therefore, many of them need to be combined to make trading possible.
The mobile domain typically includes considering various kinds of mobile objects such as vehicles (like EVs), wireless devices, sensors, and actuators, as well as mobility-required communication infrastructure. These physical mobile assets are then used by a specific service provider to offer services for the owners of the referred mobile objects or users of the services, which are based on the information exposed to such devices. The potential application field is quite large, and therefore, we have focused here on an example scenario called hunting safety. In such a case, the challenge is that there may also be other people moving in the area where the hunters are operating. It is obvious that when people are moving around in the same area in the forest with different aims, they are not aware of each other. Such a situation can be very dangerous; there is a high risk of hunting accidents. The presence and location of mobile devices could be used for the creation of warnings for hunters to prevent them from accidentally killing other people; however, the sharing of presence and locations is a very sensitive privacy and trust-related challenge. Therefore, there is a need for trustworthy communities to share the required presence and location information between the group of people joining in the hunting and other people moving in forests.
During the analysis of prior art (see Section 2.3 for more details), several potential technologies that could offer some partial solutions were found. However, a lack of proper solutions for trustworthy communities applicable to the targeted energy flexibility and hunting safety cases was detected. Several researchers have discussed the applications of a decentralized blockchain-based framework as the basis for some kind of community [4,5,6,7]. Also, the Zero Trust framework has been applied to secure collaborative systems [8]. A system of parking communities relying on trusted groups of vehicles helping each other to securely find parking in the respective community area [9]. Based on these studies, it is seen that the application of the term community has been a little bit fuzzy, e.g., referring even to local community areas, local markets, people, or physical assets. Our approach is different in the sense that we have clarified the concept of trustworthy communities to rely on a layered model consisting of shared trust infrastructure, security control channel, verifiable credentials, and identities, on top of which the contracts-based communities between the physical objects, people and service systems of various organizations can be combined to establish a community dynamically and to consider hierarchy. It is obvious that in such hierarchical communities, the management of identities is very important. Usually, identities are stored and controlled by various organizations separately, which means that users need to have access credentials separately for each of them, who may also host users’ owned data. Federated identity management has been proposed to remove the organizational burden of managing identity and the burden on users to manage several identity-related credentials for several systems. Self-Sovereign identity management allows users to control their identity-related data; for example, digital wallets [10], usage of peerDIDs [11], and DIDComm [12] solutions have been discussed. There is also a concept of decentralized autonomous organization (DAO) [13]. Both DAOs and the provided solutions apply smart contracts as the basis for community establishment; however, there are some essential differences. In DAO, the community is formed autonomously when participants join the DAO [14], while in our solution, the community is established by an administrator who can be any person or organization identified in an acceptable way by means of decentralized PKI, verifiable credentials, and authorized root of trust. The DAO has a built-in consensus mechanism for different contract proposals and voting on them as a majority decision using tokens, while in our solution, the decision-making is handled by an administrator. Furthermore, in DAO, contracts are automatically enforced when a predetermined threshold is exceeded [14], while in our solution, contracts are enforced by an authorized administrator.
Summarizing, the contribution of this research is related to the research and development of the conceptual solutions of trustworthy communities for critical energy and mobility CPS applications. The applied research method has been experimental: first, the challenges of the focused application cases were analyzed, and then the concepts for trustworthy communities were studied and defined. After that, the conceptual solutions, relying on verifiable credentials, smart contracts, trust over IP, and Ethereum-based distributed ledger, have been prototyped. Finally, the validation of the conceptual solutions has been carried out in the energy flexibility and hunting safety cases, and evaluations have been performed against the challenges detected in the referred real critical energy and mobility applications.
The reminder of this paper is organized as follows. The research methods are clarified in Section 2. The concepts of trustworthy communities with their key building blocks are clarified in Section 3. The experimental solutions are described in Section 4. The evaluation of the conceptual solutions is clarified in Section 5. Finally, the concluding remarks are presented in Section 6.
2. Methods
The applied research methods for the concept development are clarified in this section, following an analysis of challenges detected in energy flexibility and hunting safety cases and a discussion on prior art related to the concept of trustworthy communities’ development.
2.1. Research Challenge and Methods
Usually, the building automation system provider offers services for monitoring and controlling the energy-sensitive resources of a building, Figure 1. The energy distribution operator and energy seller organizations provide services for energy-related services, and the electricity consumption point is tightly linked with a specific smart meter and is usually mounted in a building under the control of the energy distribution operator. The consumption point is usually also bound to the owner of the building or apartment so that the invoices can be directed accordingly. However, the owner and users of the building (e.g., tenant) and the automation system provider controlling energy-sensitive resources can be different than the referred energy stakeholders. In addition, the owner (or user) may want to join the energy flexibility community with other such owners and make combined actions in the energy flexibility markets.
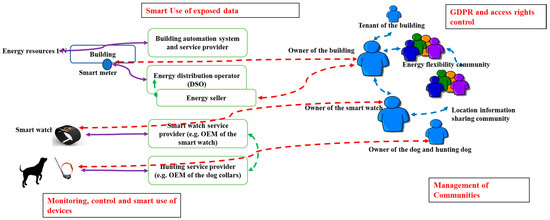
Figure 1.
A view to the context of the challenges and the research question—How do we take care of the required trustworthy relationships and communities between stakeholders when monitoring, controlling, and using devices, and when do we use exposed data in a smart way? Solid violet lines in the figure represent device management carried by companies, dashed lines represent relationships requiring some kind of contracts, e.g., between companies (dashed green lines), between people and companies (dashed red lines), between people or organizations (dashed blue lines).
People may use smartwatches to obtain measures for their body and wellness conditions. The smart watch-related services are usually provided by a specific service provider, who also is usually the OEM of smart watches, Figure 1. The hunting dog collars and hunting services are also usually provided by a specific service provider, which is/can be different than the smart watch service provider. The owner and user of the referred physical devices are typically different than the referred service providers. However, the owner may want to share information such as the presence and location of the physical device with a certain group of other stakeholders, but that is not the case for the others because of the privacy protection needs.
These two different cases demonstrate the context of the research challenges of this work, Figure 1. Both cases include the same kind of challenges: monitoring, control, and smart use of the devices, smart use of the exposed data, GDPR and access rights control, and management of communities. The term communities refers here to the relationships of stakeholders, service providers, and physical devices/resources. Thus, we have defined the main research question of this work as follows: How do we take care of the required trustworthy relationships and communities between stakeholders when monitoring, controlling, and using devices, and when do we use exposed data in a smart way?
The applied research method has been experimental and described in the following. First, the challenges for energy flexibility and hunting safety were analyzed, and then analysis of prior art solutions was carried out as a parallel process for the development. Based on all this information, the step-by-step prototyping of the solutions for trustworthy communities was carried out. First, a simulation of resources was applied, and then some selected physical resources were considered in the validation. For example, in the last evaluation step of the provided solutions, the energy-sensitive resources of one simulated building and two real buildings were used in the energy flexibility aggregation and simulated trading in the energy flexibility marketplace. The real physical devices (test versions of smartwatch and hunting dog collar) were applied to validate solutions in the hunting safety case.
2.2. Challenges of the Critical Energy and Mobility CPS Applications
2.2.1. Energy Flexibility Case
Energy is a limited resource all over the world, and therefore, the efficient use of all the available energy resources is important. Building new energy production resources is expensive and slow, and simultaneously, energy consumption is increasing quite rapidly due to the needs arising, e.g., from electric mobility. On the other hand, there are more and more new types of smaller-scale energy production resources, such as solar power plants, whose energy production capabilities are not properly under the control of the energy stakeholders for natural reasons. The load balancing in the electric grid is very essential, and today, it is usually reached due to the automatic energy resources controlled by grid operator(s). However, achieving the balance can be very expensive, and it is visible during the peak hours of the day in the form of very high energy prices. Therefore, it is estimated that the capability to control energy consumption and production during such peak hours could be beneficial. Such capabilities are here called energy flexibility, which refers to down or upscale energy consumption and production. Today, the EU is also driving toward establishing energy flexibility markets, and there are emerging energy flexibility marketplaces. Let us take an example related to the management of energy-sensitive resources in buildings, Figure 2. The buildings have automation devices to control, e.g., the heating and cooling of the building (Energy Flexibility Requirement 4 (EF-R4)), which are currently working quite much under the control of the local user (EF-R7). There are also automation service providers who may provide more smart monitoring and control related to specific energy resources (EF-R8) for the energy management of the building (A, B, C). There may also be some possibilities for control actions of specific energy resources (EF-R4) via the smart energy meter provided by the local distribution service operator (DSO) for the building and the site owner (EF-R3). Concerning energy flexibility, it is essential to consider the needs of the owners and even tenants of the building. Because they pay the energy cost for the energy seller, it is important that they get some monetary value or incentives (EF-R1) for making practical actions to lower consumption or increase production (EF-R7). The consumers and prosumers also require more detailed capabilities to monitor and control energy resources, providing such energy flexibility (EF-R7). In addition, there is quite a significant lack of energy flexibility aggregation functions that can interact with the energy market (EF-R5, EF-R6). The smallest tradeable unit in the energy flexibility market seems to be bigger than what an individual building/site can offer. In addition, the process of forecasting future production and consumption is quite a demanding process. Therefore, smart energy flexibility aggregation capabilities are needed, and the stakeholders owning energy flexibility resources need to combine their flexibilities to be involved in the energy flexibility markets, e.g., to establish energy communities (EF-R2). In addition, each of the referred stakeholders needs to get monetary benefits or incentives to motivate them to offer their flexibility in the energy flexibility markets.
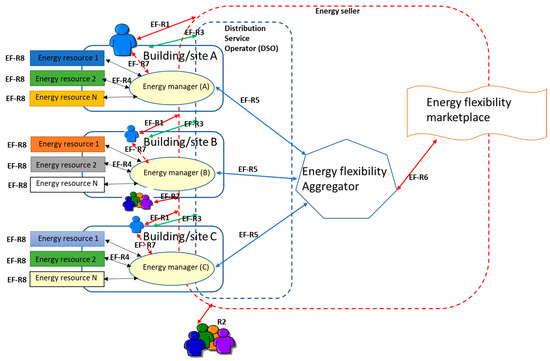
Figure 2.
A view to the requirements of the energy flexibility case.
2.2.2. Hunting Safety Case
The mobile domain typically includes various kinds of wireless devices, which are tightly coupled with the specific service provider cloud for making reliable management, monitoring, and control of the devices (Hunting safety requirement, HS-R1) and providing services relying on the data exposed from the devices (HS-R3), Figure 3. Typically, the owners of the devices can apply smart services to the devices via the service provider clouds (HS-R2). Let us take an example relying on the targeted hunting safety case. Hunting in the forests can be dangerous for people (e.g., picking berries, walking, and cycling) moving around in the same area as the hunters in the forest. There is a high risk of hunting accidents, which seems to happen every now and then when using the current technological practices. Currently, there is a service provider (e.g., SP 1 in Figure 3) who provides services relating to smart watches. Another service provider (e.g., SP 2 in Figure 3 offers services exposed from hunting dog collars, which are used for tracking hunting dogs in the forest. There is typically a group of hunters involved in the elk hunting, and therefore the SP 2 offers such hunting community services for the defined group (G1) (HS-R4), where the hunters can follow the presence and locations of themselves and the dogs in the forest using their smart phones (HS-R7). Group sports (G2) can happen in the same area under control of the SP 1 (HS-R4).
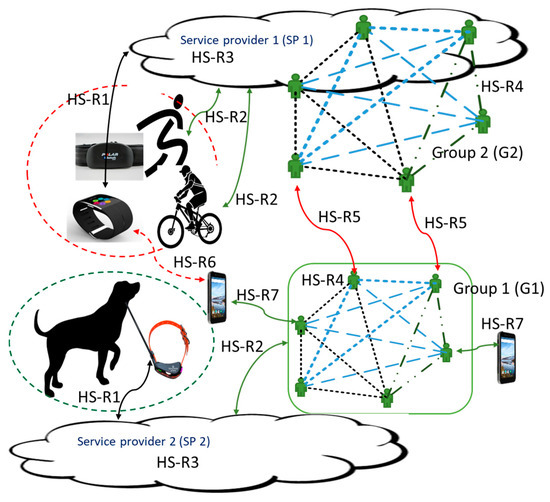
Figure 3.
A view to the requirements for mobile services in the hunting safety case.
When looking at the situation in the forests during hunting, it is obvious that the defined groups (G1, G2) or individual members of G2 can operate in the same area in wireless ad hoc conditions. It is estimated to be beneficial that the devices in these conditions would be able to inform each other about the presences and locations (HS-R6). This would enable the hunters to know that there is someone moving in the surroundings and require them to stop hunting to prevent accidentally killing other people moving in the area. However, sharing presence and location information is very privacy sensitive because it may reveal the presence and location of a person to unfriendly people. Information sharing between the devices can be business-sensitive for the service providers, and compromising the security of the device products may even challenge the whole business of the service provider/device manufacturer. This is because compromising the privacy of their customers’ information may result in penalties being paid, reputation being lost, and an end to sales. But there is a need to share privacy-sensitive presence and location information between devices, service systems, and users to make hunting safer. There are technologies available for sharing such data, e.g., Bluetooth, which allows broadcasting and connection type of channels for exchanging information in ad conditions in the forests. However, there is a need for contracts to be agreed upon between participants of the communities to make hunting safety possible (HS-R5).
2.3. A Discussion on Prior Art
We speak about digital trust, communities, and cyber–physical systems in this research. When focusing on the technical meaning of these terms, several important required technologies need to be considered, such as data spaces, identification, smart contracts, distributed ledgers, and community management. Cyber–physical systems typically apply various kinds of IoT platforms to enable services from the physical assets that they are hosting. Information sharing usually happens directly between the enterprise systems using APIs. A view of the prior art around our research question is provided in the rest of this section. There are several existing approaches for data spaces such as GAIA-X [15,16,17], IDS/MDS [18], MyData [19], and Energy Web [20,21]. International Data Spaces (IDS) is an open-source federated data space reference architecture model, which is coordinated by the International Data Spaces Association (IDSA). One example of conceptual federated data spaces is Gaia-X, which supports the goals of interoperability of services, data portability, and data sovereignty as articulated in the European data strategy and addresses a requirement gap in existing infrastructure models [22,23]. The first implementation of Gaia-X is Catena-X, a data space for the automotive industry. For the mobility sector, Mobility Data Space (MDS) brings together people who offer mobility data with people who need it to develop and run new business models. Another solution is a data space for sharing data in the supply chain, Smart Connected Supplier Network (SCSN).
GAIA-X approach tries to avoid monolithic, centralized authorization and rather approach the problem via the use of decentralized, federated identifiers and services. It does not provide centralized data storage, either. Instead, each company decides for itself where its data is stored, as well as who may process it and for what purpose [15,16,17]. The MyData approach leans toward decentralized operation, which suggests the use of self-sovereign identities (SSI) with technology support provided by operators to help users remain in control of their data. The MyData approach to authorization and permissions is to keep them separate from the data flow and allocate verifying the operation to the data operator. MyData model can have many such data operators. The reference architecture model of IDSA has IDS connectors as components for joining heterogeneous partner data sources to a common ecosystem. IDS relies on centralized certification authority where the trustworthiness of participants is ensured, which leads to a high level of trust but a heavy onboarding process relying on centralized identification, authentication, and authorization. Energy Web does not have central authentication, and the solution is based on decentralized, blockchain-anchored identities, decentralized identifiers, verifiable claims, and smart contracts. User control over their data is the core principle of self-sovereign identities. With DIDs and verifiable claims, trust establishment is fine-grained and based on selective exposure of personal data. The application of self-sovereign seems to ease GDPR compliance and make data sharing to third parties be decided by the users. The concept of an application registry with identities and verifiable claims in a way establishes the possibility of setting up a community for a specific geographical area of the local energy grid. We have applied the decentralized operation of the MyData model because it is well in-line with the needs of owners and SPs to be in control of their data. In addition, decentralized, blockchain-anchored identities, decentralized identifiers, verifiable claims, and smart contracts have been applied because of support for solving the digital trust challenges.
The Verifiable Credentials Data Model 1.0 of the World Wide Web Consortium (W3C) specification applies decentralized identifiers (DIDs) for the creation of a basis for digital trust [24,25,26]. Applying DIDs and distributed ledger technologies makes it possible to avoid dependence on centralized registers/certificate authorities for key management, called decentralized public key infrastructure (PKI) [27,28]. The system works so that a holder (person, item, service, etc.) obtains a decentralized identifier (DID) together with its public key from a reliable provider, who also stores it in some type of verifiable data registry, such as distributed ledger (DLT). DLT refers to the storage, distribution, and exchange (sharing) of data among the users of private or public distributed computer networks located in multiple sites [29]. One example of DLT is blockchain, which is the underlying technology of Bitcoin [30]. Blockchain is a linked-list type of data structure, which is updateable only via consensus among most existing peers in the network, and thus, there is not a single CA controlling the ledger. Each block contains a set of transactions and their hash, with a link to the previous block hash. Only after successful consensus can a new block be added to the chain. A blockchain can tackle the problem of sensitive information and is considered as a new privacy protection tool [31]. Another type of DLT is the directed acyclic graph (DAG), where each transaction is represented as a node that is linked to one or several other transactions. An example of a DAG application is IOTA [29,32,33,34], which calls its distributed ledger the Tangle. After the holder has obtained the DID with its public key from a reliable provider, the holder requests verifiable credentials from various issuers who, after determining that the credentials can be granted, use their private key to digitally sign the credential (and any other cryptographic material needed to verify the issuer’s credentials), and issue it to the holder to store in their digital wallet. Note that to preserve privacy, this issuance process does not need to involve any interaction with a verifiable data registry—in other words, no personal data needs to be written to a blockchain or third-party data repository. The process can be fully confidential between the issuer and the holder. Later, when the holder needs to gain access to some resource controlled by a verifier, the verifier requests digital proof of one or more credentials from the holder. If the holder consents, the holder’s wallet generates and returns the proofs to the verifier. Since the proof contains the issuer’s DID, the verifier can use it to read the issuer’s public key and other cryptographic data from the verifiable data registry. In the final step, the verifier uses the issuer’s public key to verify that the proofs are valid and that the digital credential has not been tampered with [35]. For example, Findy, a public-private organization operating in Finland, has developed a respective trust system and data-sharing network, which is applied as a test network testing various scenarios related to the verifiable credentials used in separate roles of the trust triangle [36]. We have also applied this approach in the preceding/parallel research of this work successfully in a safety-critical use case related to remote driving [3]. Because the energy flexibility and hunting safety cases requires also high-level confidence of the involved stakeholders and users, the benefits of this kind of trust model are obvious, and therefore, it has also been applied here as the starting point. The essential novelty in this research is that we have provided conceptual solutions for communities built on top of the digital trust model.
Let us discuss a bit more about the prior art related to a slightly fuzzy notion of communities in this field of research. Several researchers have spoken about some forms of communities and the technologies applied in their solutions; some examples are in the following paragraphs. For energy trading, Sachdev et al. [4] propose a secure and decentralized blockchain-based framework in a community. A blockchain provides a decentralized, digital, and distributed ledger that allows transparent and secure information sharing among the peer-to-peer network. The solution utilizes the Ethereum blockchain and smart contracts for energy trading among the members of a small community without any trusted third entity and adopts features to achieve data integrity, confidentiality, and user identity privacy. Eisele et al. [5] present a blockchain-based platform that provides key mechanisms required for arbitrating resource consumption across different applications of smart and connected communities. These applications provide the capability to exchange not only data but also resources, which raises the concerns of integrity and trust. One of the case studies of the proposed transaction management platform applies to the problem of energy trading within a microgrid.
There are also other researchers who propose using blockchain solutions as the basis for communities. For example, Hong [6] presents a decentralized smart community system architecture based on blockchain technology to comprehensively optimize trust-based smart city applications for all community-building stakeholders and service models. Smart communities are often accompanied by huge data flow and sharing, which has troubled data security. Blockchain provides a good solution to solve the problem of data sharing security. Blockchain has tamper-evident, transparency, and traceability, which can effectively protect and track data flow and ensure that the data has not been tampered with. Zhou et al. [7] propose a peer-to-peer electricity trading method of community microgrid considering user preference differences in a blockchain environment. The proposed method can effectively promote the consumption of distributed energy resources and reduce the electricity cost of users.
Other proposed models include N’Goran et al. [8], who present a Zero-Trust framework for securing collaborative systems. It provides a hierarchical architecture to secure exchanges within and between organizations. And it provides a decentralized management system for user and organization identities through decentralized identifiers and a blockchain registry. In addition, the approach suggests a trust inference technique to assess trust between organizations. Furthermore, the proposed framework includes a mechanism for specifying and monitoring collaboration contracts and defining access policy rules. Timpner et al. [9] present a system of parking communities, which provides a distributed and dynamic means to establish trusted groups of vehicles that help each other to securely find parking in their respective community area. Reliance on a trusted central party or road-side units is not required. Its features include a distributed trust model for parking applications as well as encrypted and signed request-response communication.
Identity management needs to be considered when using a system provided by some organization. In traditional centralized identity management, organizations issue credentials to their users, permitting them to use their systems. The user’s identity-related data are stored and controlled by the organization. Users must trust organizations for identification and data management. Also, users need to repeat this for each system they use. Federated identity management removes the organizational burden of managing identity and the burden on users to manage several identity-related credentials for several systems. However, the user does not have control of data because the identity-related data of a user is held by the federated identity provider. Self-Sovereign identity management lets users control their identity-related data. Users are completely independent of third parties and decide for themselves which identity data they share with whom, as all identity data is securely stored only with the individual user in their digital wallets [10]. For example, SICPA Digital lab has created a Python-based environment [37] that can be used to test and evaluate the usage of peerDIDs [11] (subtype of W3C decentralized identifiers or DIDs) together with DIDComm [12], which is a mechanism that concentrates on communication between two entities that know each other’s DID.
There is also a concept of decentralized autonomous organization (DAO) [13], which is a blockchain-based system that enables people to coordinate and govern themselves by a set of self-executing rules deployed on a public blockchain, and whose governance is decentralized, independent from central control. For example, Sharma et al. [38] present a concept where DAOs are used to organize renewable energy communities by means of community-level joint ownership of energy infrastructure to help reduce the wealth leak in communities. DAOs are purely digitally existing for decentralized rule-based decision-making; DAOs are built on blockchain technology, which enables secure and transparent bookkeeping and transaction processing. Both DAOs and the provided solutions apply smart contracts; however, there are some essential differences. In DAO, the community is formed autonomously when participants join the DAO [14], while in our solution, the community is established by an administrator who can be any person or organization identified in an acceptable way by means of decentralized PKI, verifiable credentials, and authorized root of trust. The DAO has a built-in consensus mechanism for different contract proposals and voting on them as a majority decision using tokens [14], while in our solution, the decision-making is handled by an administrator. Furthermore, in DAO, contracts are automatically enforced when a predetermined threshold is exceeded [14], while in our solution, contracts are enforced by an administrator.
In summary, several potential technologies that could offer some partial solutions were found during the prior art analysis. However, a lack of proper solutions for trustworthy communities applicable to the targeted energy flexibility and hunting safety cases was detected. We have here contributed the novel concept of trustworthy communities, which relies on a layered model consisting of shared trust infrastructure, security control channel, verifiable credentials, and hierarchical identity management, on top of which the contracts-based communities can be established. The communities can be dynamically established and maintained between the physical objects, people, and service systems of various organizations. The provided solution supports hierarchical combinations so that, e.g., an individual identified person can represent him or herself, the employer, and a number of communities. In addition, certain physical resources owned by the person can be linked to the specific community, while some other physical resources stay under the sole control of the person. The identity of an individual person is ensured using the wallet application, which holds the private key applied in operation with the trust infrastructure. The smart contract establishing a community is signed by the admin person of the community, and the other persons or communities can join the referred community by signing in via their wallet application. The smart contracts with verifiable credentials are stored in the blockchain. The proposed solutions also include a dashboard type of situation monitoring tool, which opens views to the community and contract hierarchies, allowing data sharing relationships between resources and content of blockchain stored data. The secure control channel can be applied to negotiate the security control parameters for the end-to-end data flow between resources.
3. Concept of Trustworthy Communities
3.1. Conceptual Model
The conceptual model of trustworthy communities is depicted in Figure 4. The model has been divided into three parts: trust control services, secure data exchange services, and community applications. The community applications need first to ensure trust between all the required entities using trust control services, and then information-based interaction between the community applications and the related resources using secure data exchange services can be started. As the result of the trust control services phase, the secure data exchange can happen either directly between the community application-related entities or by applying some kind of message broker for help, e.g., in one-to-many communications, without any or at least minimized additional overhead. The main contribution area of the trustworthy communities concept is related to the trust control services, which are here defined to contain levels called communities, identities, verifiable credentials, security control channels, and shared trust infrastructure.
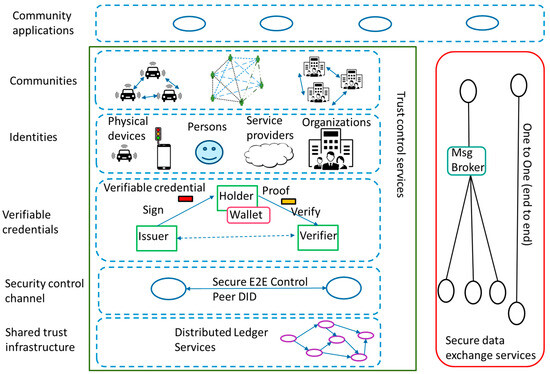
Figure 4.
The conceptual model of trustworthy communities.
The community level is related to the relationships between physical assets (resources), people, and organizations. The aim of this level is to ensure that there is a relationship of trust established between the resources, people, and organizations that plan to operate together in some community application. The identities’ level is important to ensure unique identifiers for resources, persons, service providers, and organizations. For example, the root of trust for the identities of persons can be ensured using passports given by authorities, which are then applied by, e.g., bank applications. Organizations need to have some identity given by authorities such as the VAT number. The physical assets usually have unique product numbers given by their manufacturers. It is essential to point out that these identities are usually given by a specific organization following its own policies. Such identities shall always be proofed by a certificate or verified otherwise. The application of the verifiable credentials method has been selected to ensure the means to provide credentials from the issuers to holders, store the credentials in wallets, and check the credential proofs by the verifier(s). The security control channel is related to exchanging security control data between the entities in an end-to-end manner and in a secure way by using the Trust over IP type of Peed DID method. The control data can include credentials, security keys, or other cryptographical material, or meta information on the data stream related to the real data flow, which is required to be exchanged between the entities of the community application. The shared trust infrastructure is needed for storing the transactions related to trust relationships between resources, people, organizations and community applications, smart contracts, verifiable credentials, and other security, privacy, and safety-related critical events (traces monitored from the system) so that they cannot be changed after they are verified and stored into the distributed ledger.
3.2. Communities
The term communities here refers to a group of entities that have an agreed trust relationship with specific rules for collaboration. The aim of this level is to ensure that there is a trust relationship established between the resources, people, and organizations that plan to operate together in some community application. A set of example communities and their relationships is depicted in Figure 5. The basic element of a community can be a person (A) who can join to be part of an organization type of community (B). Some organizations may have some regulations-based role with rights for law enforcement; therefore, they are called authorities here (F). Other types of such organizations are service providers (SP), manufacturers (DM), and building/site communities (E).
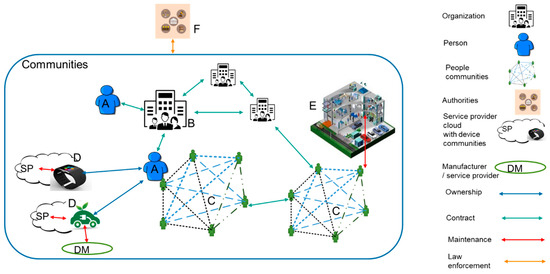
Figure 5.
Examples of communities, resources, and related relationships.
A person or an organization can own resources such as physical devices/products, facilities, or information (D). Persons and organizations can establish new communities themselves with any other people or organizations (C). A community can be dynamic in the sense that a person or an organization can join and leave it at any time. The dynamic trust relationships are established using smart contracts (SC) for decentralized autonomous organization (DAO) type method for establishing community contracts between the involved stakeholders. After signing the community contract, the stakeholder and the community application share tokens so that the community application can be used by the stakeholder and the community application can use the allowed resources of the stakeholder. The allowed resource usage shall be agreed upon within the SC, or a specific data-sharing SC shall be agreed upon between members of the community.
3.3. Identities
It is important to ensure unique identifiers for stakeholders and for physical and information resources. Some kind of the root of trust is needed for the stakeholders, and a kind of hierarchical structure can be seen as depicted in Figure 6. The root of trust for the identities of persons can be ensured using social security numbers and passports given by authorities, which can then be applied by banks to give bank identifiers to persons. Organizations typically need to have so-called VAT numbers given by authorities in order to operate commercially. The dynamically established community can have a specific community identifier linked with the admin person of the community and a token given to each member of the community. Traditionally, the stakeholders have been identified using a username and password combination in digital services. However, this is not enough anymore; some kind of two-way authentication is needed, e.g., a PKI-type method with Wallet applications. The physical resources usually have unique product identifiers given by their manufacturers. It is essential to point out that these identities are usually hosted by a specific organization following its own policies. Such identities shall always be proofed by a certificate, a secure element in the product, or verified otherwise. In addition, the information type of resources can be bound to physical resources, as depicted in Figure 6.
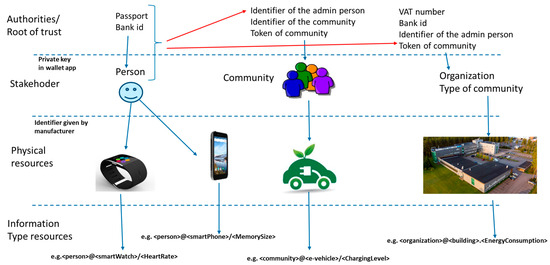
Figure 6.
An example hierarchy of identities.
3.4. Verifiable Credentials
The identities have a meaning only if they can always be proofed by a certificate or verified otherwise. The application of the verifiable credentials method has been selected to ensure the means to provide credentials from the issuers to holders, storing the credentials to wallets, and checking the credential proofs by the verifier(s) [15]. This method relies on the W3C model of decentralized identifiers (DIDs), and verifiable credentials relying on the use of PKI public/private keys is usually depicted in the form of a trust triangle, Figure 7 [3,24]. An issuer (person, item, service, etc.) obtains and stores its DID with the related public key and any related cryptographic proof to a verifiable data registry. Then, the issuer signs the verifiable credential related to the requested certificate content using the issuer’s private key and gives it to the credential requester (the holder), who can store the verifiable credential in their wallet or some trustworthy file storage. When some organization (verifier) needs to ensure that the holder has a certain certificate, it can request digital proof of one or more credentials from the holder. The holder can then sign and provide the proof to the verifier using the holder’s DID and private key, the certificate content in full or just the requested part, and the signature received from the issuer. In this way, the verifier can be sure that the holder is who he/she claims to be and not anybody else.
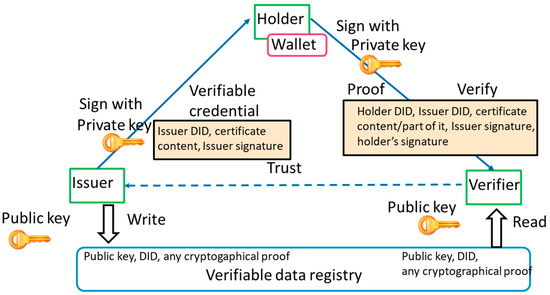
Figure 7.
The trust triangle. When the verifier trusts the Issuer (dashed line), trust can be established with the Holder (solid line) [2,3].
The verifier can then find the holder’s and issuer’s public keys from the verifiable data registry. Finally, the verifier can use the public keys to ensure that the proof was generated by the holder for the specific request, to ensure that the digital signature in the proof was given by the issuer indicating the proof is valid, and to check that the hash of the content is correct. After the application of this W3C DID methodology, it is assumed that there is a high level of trust that the system actors are what they claim to be. As a result of this process, the stakeholders have verifiable credentials in their wallet apps, and those credentials can always be verified by relying on the verifiable data registry.
3.5. Security Control Channel
The main principles of the security control channel are depicted in Figure 7. It is required that the participating entities have first created digital trust and negotiated the applied security control data (green arrow in the Figure 8) before the actual application-related end-to-end (E2E) messaging/data flow (red arrow in Figure 8) can be started. The creation of digital trust refers to the use of the decentralized identifiers (DIDs), public/private keys, and verifiable credentials as described in Section 3.4, which is depicted as the digital trust connector (digital trust services) bubble in Figure 8. Such digital trust services are needed to ensure the basis for exchanging the security control data between the entities. The security control data can include the needed security parameters in initiating the secure E2E) data flow, such as credentials, security keys, or other cryptographical material, quality of service (QoS) requirements, and meta information on the secure E2E data stream. The security control data exchange can be performed using, e.g., DIDComm protocol [16,17]. The content of the security control messages is encrypted so that only the trusted peer entities are able to decrypt the messages and expose the security- and data-related parameters needed in exchanging E2E data. It is estimated that when the control data for security has been exchanged, the overhead in the E2E data exchange can be minimized, and QoS and the required security level can be achieved.
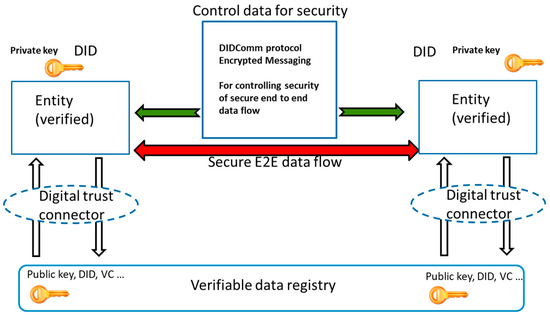
Figure 8.
Control data for security to establish a secure end-to-end data flow among physical entities.
3.6. Shared Trust Infrastructure
A key element in the proposed concept of trustworthy communities is the application of a verifiable data registry for storing trust-related information in a reliable manner. The trust-related information refers, for example, to contract type of relationships between verifiable entities such as people, organizations, resources, and communities. The contracts need to be immutable so that when they have been agreed upon and signed by the entities, they shall be stored with timestamps so that they cannot be changed, modified, or compromised by anyone afterward and are thus authentic in a proofed way. The application of blockchain/distributed ledger technologies (DLTs) has been selected as the basis for the verifiable data registry; more specifically, the smart contract concept of Ethereum technology is applied [39]. An example view of a verifiable data registry with the application of Ethereum type of smart contracts is depicted in Figure 9. The transactions are always signed by an entity with a private key, which is usually hosted as the private wallet application together with other verifiable credentials (VCs) with the application of decentralized identifiers (DIDs). A transaction can be a value transfer to the recipient entity, trigger the execution of the smart contract (SC) program, or initiate an SC as a transaction. When signed, the transactions are stored in the blockchain infrastructure (Ethereum in this case), which is a chain of linked blocks that cannot be changed after they have been added to the blockchain [39]. A small amount of Ether (cryptocurrency), referred to as the “value” or “gas” in Figure 9, is needed to pay the cost required to store the transaction into the blockchain.
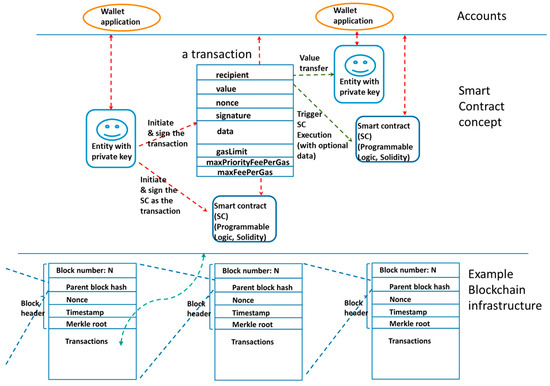
Figure 9.
An example view of a verifiable data registry with application of Ethereum type of smart contracts.
4. Solutions for Trustworthy Communities
4.1. Structure of Experimental Solutions for Trustworthy Communities
The main structure of the experimental solutions (CPSHub@vtt) developed is depicted in Figure 10. The realized trust control services (CPSHub block in the center of Figure 10) have been divided into three basic functional blocks. They are called trust and community services, distributed ledger services, and messaging services. The dashed blocks in the surroundings represent the key-related elements of the solutions. The CPSHub system is a web-based application where the end-user shall register with basic identification data and access an account via the wallet application (Metamask). The wallet application hosts the private key and the Ether cryptocurrencies (“gas”) owned by the user, and it is also used for the signing of the contracts of the user. A specific mobile contract web application enables users to sign or unsign contracts, attach credentials with contracts, and show the status of signed contracts. The CPSHub enables the creation of communities that are used, e.g., to define resources and devices and to establish communities including creation of framework and data sharing contracts for ensure trustworthy sharing of data between communities and agreed parties. The data sharing between the allowed entities can be carried out in a one-to-many way using MQTT-based messaging or in a one-to-one way that is agreed upon using a security control channel (Didcomm/PeerDID protocol) between the endpoints. In both cases, the CPSHub disables the data sharing if contracts between participants of the community become invalid.
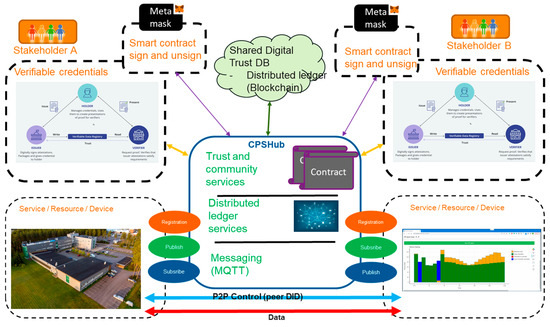
Figure 10.
Structure of the experimental solutions (CPSHub@vtt) for the trustworthy communities.
The basic operating procedures of the CPSHub are called registration, resource/device-, topic-, community-, framework contract-, and data sharing contract creation. In addition, CPSHub provides capabilities to visualize trust-related data stored in the verifiable data registry/blockchain, as well as the connector services to be applied with the peerDID/didcomm security control channel between the services/resources/devices.
4.2. Trust and Community Services
An essential component of the trustworthy communities concept is called trust and community services. An example view of it is represented here using the screenshot of the CPSHub user interface (CPSHub UI), which is used for controlling the concept operation from the user perspective, Figure 11. The main procedures executed via the CPSHub UI are registration, community creation, resource creation, framework contract creation, and data sharing contract creation.
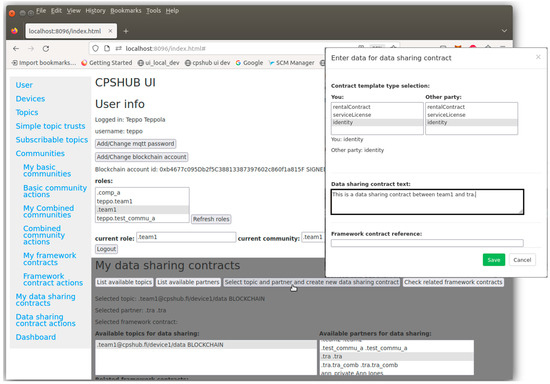
Figure 11.
An example view of trust and community services is represented here by the CPSHub user interface.
In the registration phase, a user creates an account for CPSHub UI by defining basic credentials (username and password) for logging in. After that, the user connects his wallet application (Metamask) account present in his web browser to the CPSHub UI account. This enables the signing of various contracts using the wallet application via the CPSHub UI. During the community creation procedure, a user, as an administrator (admin) representative of the community, establishes a community and invites other users to join it. The invited users shall sign the community contract when they accept the invitation. Communities can also join and form communities, which are here called combined communities. A community joins the combined community when the admin of the community accepts and signs the invitation initiated by the combined community creator (the admin of the combined community).
Resource creation refers here to the definition and creation of devices and MQTT topics into the CPSHub. The resources are created so that they are bound with the different roles of their controlling stakeholders in the CPSHub system. Such differing roles can be, e.g., private user, community, and combined community. The resources are used to specifically define what data is shared and in which role it is shared.
Framework contracts are created between various communities. They may contain, for example, general agreements that are followed by referring data-sharing contracts. The creation of other contracts thus becomes easier as the need for rewriting contract text decreases. Data-sharing contract creation involves defining, for example, contract parties, resources, and verifiable credential types for contract signers. In addition, contract text describing the contract can be added as well as an optional reference to the existing framework contract.
4.3. Smart Contract Services
The smart contract services are needed to control the procedures for smart contract management, make, update, and write the smart contract data into the local storages and into the blockchain as transactions, and take care of the smart contract expiration services. The smart contract refers to a computer program that consists of code and data, and it is stored in the blockchain as a transaction. The smart contracts are here created and deployed on the blockchain using Web3 libraries [40]. Using the libraries, a specific application binary interface (ABI) is applied to change or read smart contract data. This application’s binary interface changes the data stored in the contract from the plain language format to the binary format used by the smart contract, and correspondingly, the data to be read from binary format to plain language.
A central component of the solution is the contract manager service, which allows users to create new smart contracts, attach members to them, and store real-time information in smart contracts and their members in a local database. It also interacts with the blockchain and interfaces smart contracts deployed in the blockchain. The contract manager also holds ABI files, which are different smart contract templates, and distributes them to other applications that want to communicate with smart contracts or create new smart contracts. The contract manager’s local database holds verifiable presentations (VPs) attached to smart contracts and uses a verifier service to verify the validity of the verifiable presentations. The contract manager also monitors credential expiration dates/times and possible revocations in real-time and forwards this information to trust and community services.
The contract manager is realized as a web application called a mobile contract client. An example view of it is represented using the screenshot of the smart contract client user interface, Figure 12. With the contract client, the user can edit contract member and community member data in a smart contract and a blockchain, sign and unsign contracts using the Metamask extension/wallet application, retrieve credentials from issuers, and sign them to the verifiable presentations with a private key, and finally attach them to the smart contracts. By using the contract client application, the user can also set the desired validity period for the contract. Each signing or unsigning of a smart contract produces a new transaction block in the blockchain. If necessary, these transaction blocks can be traced afterward when the user account ID and contract ID are known. The contract manager helps in maintaining this information as well. In addition, the contract manager contains query routines for querying old transactions from the blockchain on a user basis or contract basis.
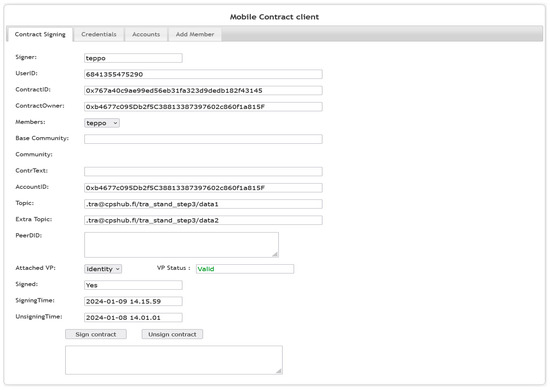
Figure 12.
An example view of the smart contract application user interface.
4.4. Messaging Services
An experimental realization of the messaging services is depicted in Figure 13. The messaging services include one-to-many data transfer using publish-subscribe methods with MQTT broker, which is combined to work with CPSHub so that the messaging is allowed only when the contract is valid. The one-to-one type of data transfer is also supported, and it is realized by enabling the security control channel. The purpose of the security control channel is to enable the exchange of secure control data (E2E) between two entities. Both entities need to deploy the digital trust connector (CPSHub connector) that implements the actual control data channel between the two entities. Before usage of the security control channel is possible, a data sharing contract shall be created and signed in the CPSHub server by the owner representatives of the two entities, admin persons, and violet lines shown in Figure 13. When an entity is started, the CPSHub connector attached to it registers into CPSHub; see trust control messaging shown using green color in Figure 12. In registration, the entity using the CPSHub connector is bound with the data sharing contract. After the registration of both entities had occurred, CPSHub connectors establish a secure DIDComm pipe between them, orange line shown in Figure 12. Consequently, entities can start communicating with other entities using CPSHub connectors. The created secure DIDComm peerDID pipe can be applied for security control, and it can be used by means of CPSHub connectors. CPSHub connectors can cease to deliver messages if the contract becomes invalid, and thus blocking also the end to end data transfer.
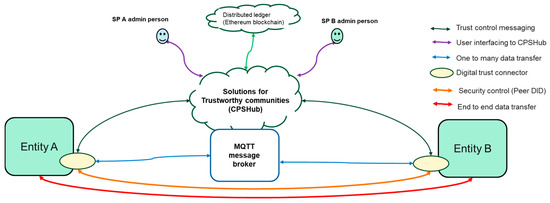
Figure 13.
A view to the messaging services of CPSHub.
4.5. Visualising Trust Related Data
CPSHub dashboard shows the hierarchy and relations of users, communities, roles, contracts, devices, and topics in tree format. Users can open tree nodes one by one, or the whole tree. Users can choose the number of tree nodes to show, for example, just communities and contracts. Figure 14 shows the dashboard where user John belongs to the Brisk community and has one community contract and one data-sharing contract. User Mary also belongs to the Brisk community. Users Bob and Alice belong to the ClubX community, and they link to users John and Mary, who have the same data-sharing contract.
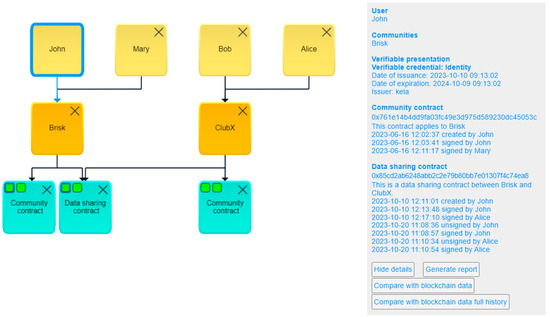
Figure 14.
An example view of CPSHub dashboard.
The information box on the right side of the dashboard shows the most important information about the selected node. For example, for the selected user, the information box shows communities, verifiable presentations, and contracts of the selected user. The same information can be used to generate a report, which can be opened in Microsoft Excel. The dashboard also enables checking the consistency of the CPSHub data with the blockchain data.
5. Evaluation
5.1. Evaluation Process
The evaluation of the conceptual solutions has been carried out in an experimental and step-by-step manner using specific energy flexibility and hunting safety scenarios as the test cases. First, a simulation of resources was applied in the prototyping of the solutions, and then some selected physical resources were considered in the validation. In the last evaluation step, the real physical resources were connected with the solutions of trustworthy communities, and the scenarios were executed in a manner that is envisioned in real ecosystems related to energy flexibility and hunting safety. In the energy flexibility scenario, energy-sensitive resources of one simulated building and two real buildings were used in the energy flexibility aggregation and simulated trading in the energy flexibility marketplace. The real physical devices (test versions of smart watch and hunting smart phone application) were applied in the validation of solutions in the hunting safety case. The rest of this section overviews the test setups and explains the key evaluation results found during the evaluation process.
5.2. Evaluation Results from Energy Flexibility Case
A view of the setup of the energy flexibility case for testing experimental solutions for trustworthy communities is depicted in Figure 15. The setup consists of energy-sensitive resources of buildings, solutions for trustworthy communities, and a flexibility aggregation platform operating and interacting with the wholesale flexibility marketplace. The energy-sensitive resources of each building (e.g., lighting, heat pump control, solar power) are controlled by the building energy manager (BMA), who operates in interaction with solutions for trustworthy communities (CPSHub) and energy flexibility aggregation platform. BMA and energy flexibility aggregation platform (FA) interact first with the CPShub (green lines in Figure 15), following the users’ control actions (red line in Figure 15). The users’ control actions are related to the creation and signing of community contracts, data sharing, and use of the energy-sensitive resources of buildings related to establishing energy flexibility communities. When all the required contracts have been made and verified, the BMAs and the FA platform can negotiate the available flexibilities for certain timeframes for the next 24 h (orange lines in Figure 15). The FA platform selects the most applicable flexibilities relying on the interaction with the energy flexibility marketplace, fixes the trades, and then sends control commands to the respective BMAs to request execution according to the trade.
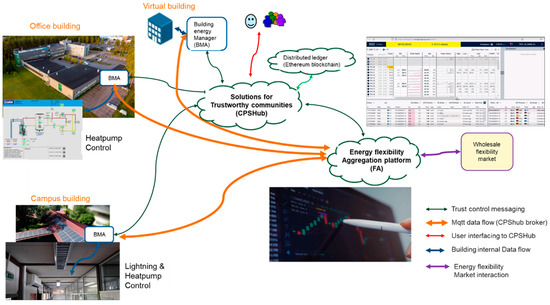
Figure 15.
A view to the setup of the energy flexibility case for testing experimental solutions for trustworthy communities.
A CPSHub dashboard view of the community and data-sharing contracts that are needed to enable the aggregation and trading of energy flexibilities is depicted in Figure 16. These contracts are created and signed according to the users’ control actions (red lines in Figure 15), and thus, they are willing to allow the use of the energy sensitive resources (lightning, heat pump control, etc.) to realize the required lowering or increasing of the use of energy. Each organization forms a community, and, e.g., users Pasi R and Jussi L are the members of the VTT community, see Figure 16. In this case, the organizations (VTT and veka) establish the energy flexibility community flexcommunity. Later, the energy flexibility community makes a framework contract with the FA community remi so that the FA is allowed to aggregate and trade the energy flexibilities of the allowed flexcommunity resources. Respective data-sharing contracts are then created to enable the required data sharing between the FA and the resources linked with the flexcommunity.
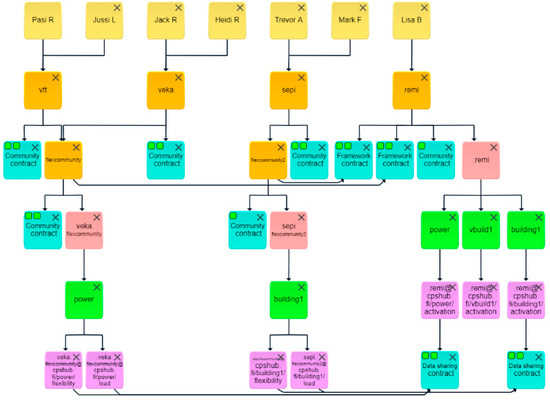
Figure 16.
A view of the users, communities, roles, topics, devices, contracts, and data-sharing relationships applied in the energy flexibility case.
The key evaluation findings are shortly clarified in the following:
- BMAs: The implementation was carried out in a light manner; however, the connector to CPSHub was carried out in a successful manner, and the flexibility potentials were defined and exchanged to FA in a successful manner. The control commands from FA were received correctly, and BMA was able to act accordingly to control the lightning and heat pump operation.
- FA platform: The connector to CPSHub successfully operated as well as the interaction with the BMAs. The FA was able to aggregate the energy flexibility capabilities of buildings to the tradable blocks in the wholesale energy flexibility market. To enable buildings to offer their flexibility potential to the flexibility market, the FA platform needs to aggregate flexibility potentials received from several buildings since the flexibility potential of individual buildings is typically significantly less than the market requirements. The FA was able to effectively integrate the flexibility potentials of buildings into the flexibility market. The flexibility potentials provided by buildings were able to enhance the system load profile so that it could lead to lower electricity prices and higher service reliability.
- CPSHub: The design and implementation are proofed to enable the basic capabilities of the trustworthy communities concept. CPSHub UI was capable of building and managing the quite versatile community and contract system required by the use case. Real-time monitoring of the agreements and data flow was proved to work in issue cases that were triggered deliberately. The real-time monitoring of contract approvals was based on the contract manager service, which monitored approval expirations and possible deletions in real time. At the dashboard, the energy flexibility safety case has quite a large number of nodes, and a better dashboard view is obtained by selecting to show only those roles that have devices.
5.3. Evaluation Results from Hunging Safety Case
A view of the setup of the hunting safety case for testing experimental solutions for trustworthy communities is depicted in Figure 17. The test setup consists of two service providers; here, they are called a hunting service provider (HSP) and a Sport and Wellness service provider (SWSP) with their provided apps and physical device products. The HSP and SWSP service systems are using CPShub connectors to interact with solutions for trustworthy communities (CPSHub). The trust control messaging (dark green lines) is executed according to the contracts made under control by the HSP and SWSP admin persons (red lines). After the contract has been completed and signed, the CPSHub connectors are able to establish the security control channel relying on the Didcomm/PeerDID methodology for the use of the HSP and SWSP service systems. The security control channel is then used to exchange the identities of the devices allowed and keys required to exchange information based on the agreed contract. Then, this information can be applied by the HSP app and SWSP smart watch in the ad hoc conditions in the forests where hunting happens in a dynamic manner. The SWSP smart watch broadcasts its presence and location using a Bluetooth low-energy broadcast channel. The HSP app is able to receive and decrypt the information, send warnings, and show the location of the person on the map. Then, the hunter is able to get a warning and stop the hunting even if the person is not physically visible.
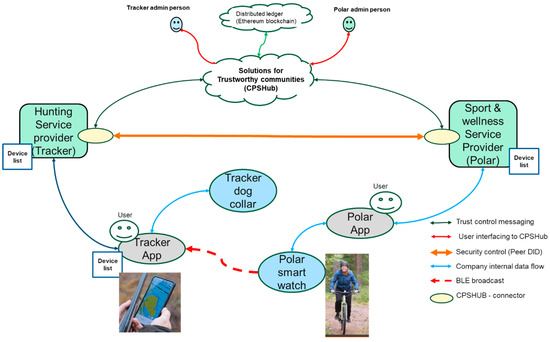
Figure 17.
A view to the setup of the hunting safety case for testing experimental solutions for trustworthy communities.
A dashboard view of the community and data-sharing contracts, which are needed for enabling hunting safety, is depicted in Figure 18. In the test case, the HSP community hunting has two members, Teppo T, and Kalle K. The SWSP community sport has users Jussi K and Alice J.
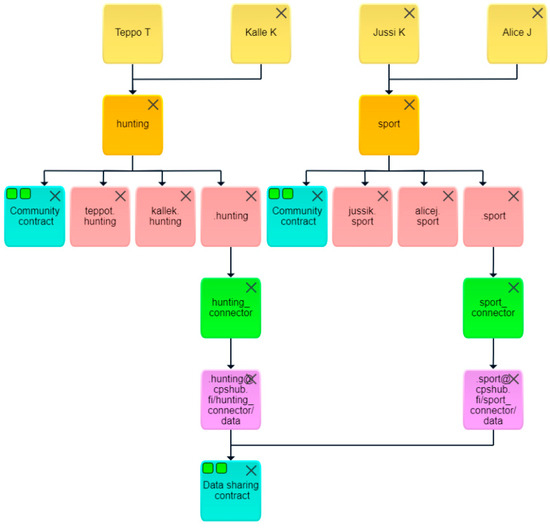
Figure 18.
A view of the users, communities, roles, topics, devices, contracts, and data-sharing relationships applied in the hunting safety case.
The key evaluation findings are shortly clarified in the following:
- HSP, HSP app, and dog collars: The dog collar sends the dog’s location data to the HSP database, from where it is visualized with the HSP app. The HSP app also listens to the BLE broadcast messages sent by the Smart Watches and displays their location information on the map screen. The presentation of BLE data details on the map screen depends on the user identification and status of the contract.
- SWSP, SASP app, and SASP smart watches: The smart watch sends the location information to the SWPS database and also as a BLE broadcast message to the nearby area. The data collected by the smartwatch in the SWPS database can be visualized with the SASP app.
- CPSHub: The design and implementation are proofed to enable the basic capabilities of the trustworthy communities concept. CPSHub UI was capable of handling simpler community and contract structures required by the use case without a major struggle. Security control channel was proved to easily transfer the sensitive E2E control data to initiate and control the E2E data flow.
- Authorization of the data traffic of the security control channel was managed using the contract manager service, which monitored authorization expirations and possible deletions in real time.
- At the dashboard, the hunting safety case is compact and shows the hierarchy and relations of all nodes immediately in a clear way.
5.4. Evaluation against the Identified Requirements
The evaluation of the trustworthy communities’ conceptual solutions is carried out by discussing the evaluation results against the challenges/requirements of energy flexibility (See Section 2.2.1 and especially the Figure 2) and hunting safety case (see Section 2.2.2 and especially the Figure 3).
Evaluation against the challenges/requirements of the energy flexibility case:
- EF-R1 (Value/incentives for the user/owner): The provided solutions apply the Metamask wallet application for signing purposes, which enables the creation of trust that the specific user/owner has approved the contract using his/her private key. However, any mechanisms for sharing value or giving incentives in the specific application cases have not been studied in detail. However, the referred trustworthy signing with the Metamask wallet application creates a solid basis for future research on such value sharing and incentives.
- EF-R2 (Energy communities for flexibility aggregation): The provided solutions enable the creation of communities for the needs of people/organizations to combine the flexibilities of their energy resources in order to scale flexibility potentials to be bigger enough to be traded in the energy flexibility marketplace(s).
- EF-R3 (Controlling energy resources via smart energy meters by DSO and the owner/user): The DSOs can typically control some selected energy resources in the state of the practice systems. However, considering the owner/users’ consumption needs in a dynamic way has been a challenge. The provided solutions enable down- or up-scaling consumption according to the dynamic market situation and needs of the owners/users.
- EF-R4 (Controlling the energy-sensitive automation resources, e.g., the heating and cooling of the building): The provided solution uses the building energy manager to estimate the available energy flexibilities and execute control actions toward the energy resources of the building.
- EF-R5–R6 (Energy flexibility aggregation functions to interact with the energy market): The energy flexibility aggregation platform of Enerim has been successfully applied as part of the solutions to aggregate energy flexibilities of buildings and experimentally traded them in the local energy flexibility marketplace.
- EF-R7 (Smart capabilities to monitor and control the energy resources locally for energy flexibility added value for prosumers and consumers): The provided solution uses a building energy manager, who is able to estimate the potential energy flexibilities of the building energy resources for the next 24 h in a smart way. The prosumers and consumers can join the energy communities that take part in the trading of these flexibilities. In this way, they can get added value from their local energy resources.
- EF-R8 (Smart monitoring and control of energy resources provided by automation service providers): Automation service providers usually have the best capabilities to smartly use their provided automation devices to control specific energy resources. This is taken into consideration in the provided solution by enabling energy communities and applying verifiable credentials to create a basis of trust and share added value.
Evaluation against the challenges/requirements of the hunting safety case:
- HS-R1 (Tight coupling with specific service provider cloud for making reliable management, monitoring, and control of the devices): We have taken this requirement as the starting point for the research because the specific service provider knows best how to operate with the device products. The security of reliable management, monitoring, and control of devices is an essential part of the challenge for the digital trust focused on in this research; however, we also consider the involved other stakeholders, such as owners of the devices, and their agreements with other stakeholders.
- HS-R2 (The owners of the devices can apply smart services of the devices via the service provider clouds): The provided solutions consider the owners of the resources to be essential controllers of the access rights to both devices and the exposed data/information. To enable this, the capabilities for digital trust and methods for relationships, i.e., creation and management of communities, have been developed. These solutions have been successfully evaluated in the hunting safety case.
- HS-R3 (Providing services relying on the data exposed from the devices): The provided solutions consider the owners of the resources to be essential controllers of the access rights to both devices and the exposed data/information. To enable this, the capabilities for trustworthy communities have been developed, and the solutions have been successfully evaluated in the hunting safety case.
- HS-R4 (Different SPs offer community services for separate groups in the same area): The hunting service provider (HSP) and Sport & Wellness service provider (SWSP) are currently offering services for group of stakeholders, e.g., HSP for elk hunters, SWSP for sport/wellness groups. These groups or individuals of the groups can be physically in the same area. The provided solutions enable the management of digital trust, as well as methods for relationships and access rights management by means and solutions for trustworthy communities. These solutions proved to be operational level in the hunting safety case.
- HS-R5 (Contracts to be agreed upon between participants of the communities for making hunting safety possible): The provided solutions enable the creation of communities and data-sharing contracts between participants of the communities. After creation, the contracts are signed by all participants using the Metamask wallet application and stored in the distributed ledger as transactions. These solutions worked quite well in the demonstration of the hunting safety case.
- HS-R6 (Sharing of the presences and locations between devices in a controlled manner): The sharing of presences and locations between smartwatches and smartphones of hunters was made possible in the hunting safety case by means of the provided trustworthy communities solutions. The access control was agreed upon by means of smart contracts between participants, and the required identification information and security secrets were negotiated by means of the security control channel.
- HS-R7 (Following the presence and locations of assets using smartphone): The presence and locations of the assets can be followed using the means provided by the HSP and SWSPs in the hunting safety case. The development of applications for the members of trustworthy communities still requires quite a few future research items.
5.5. A Discussion
The gradual development of CPSHub UI by adding new features step-by-step was seen to be successful. It enabled the implementation of new features while simultaneously testing the existing ones. The focus of the development was on the fundamental functionality and components of the system rather than on fine-tuning the user interface.
Contract Manager service was developed to handle status information and verifiable credential information of smart contracts and their verification in real time. Real-time data of the contract manager is stored in the service’s memory, but it is also backed up to the database. Over time, the amount of information that has become unnecessary increases the size of the data and may slow down the speed of the service at the same time unless a mechanism is developed to remove the information that has become unnecessary.
CPSHub dashboard presents the hierarchy and relations of users, communities, roles, contracts, devices, and topics clearly for compact use cases. For bigger use cases, there can be too many tree nodes to show, and dashboard users may find it better to restrict the number of nodes to show. The CPSHub dashboard could be further developed so that a graphical presentation could be utilized for creating communities, resources, and contracts.
6. Concluding Remarks
When initiating this research, the challenges of energy and mobility CPS applications related to trustworthy relationships between stakeholders, service providers, and physical assets were estimated to be very hard. This is because of the large number of physical devices, service providers, and owner/privacy/business sensitive data, involving both individual and company owners, and especially the dynamic relationships between them. During the analysis of prior art, several potential technologies that could offer some partial contributions were found; however, there were a lack of proper solutions to the challenges with the targeted critical application cases. We relied on verifiable credentials, smart contracts, trust over IP, and Ethereum-based distributed ledger technologies and applied them in a novel way to create solutions for trustworthy communities solutions applicable in the targeted energy flexibility and hunting safety cases.
The validation of the provided solutions was conducted in a step-by-step way; it was simulated and then applied to real physical assets. The energy flexibility case validation considered the execution of the solutions with one simulated and two real buildings, with the energy flexibility aggregation platform, which was able to trade the flexibilities in an energy flexibility marketplace. The provided solutions were executed with a hunting safety smartphone application for a hunter and the smartwatch of a person moving around in the forest. The evaluations indicate that conceptual solutions for trustworthy communities fulfill the purpose and contribute toward making energy flexibility trading and hunting safety possible and trustworthy enough for participants. This means that the provided solutions were applicable in two different cases from different application domains. The validation showed that the provided community solutions worked in a real-time manner with the physical assets, in a functional sense. However, performance and scalability aspects were not considered, and thus, further research and enhanced test setups are needed. In addition, the need for further studies related to community applications, verifiable credentials with wallets, sharing of values and incentives, authorized trust networks, dynamic trust situations, time-sensitive behavior, and autonomous operations with smart contracts through security assessment and applicability, have been detected.
Author Contributions
J.L. have contributed to all the sections of this article. J.H., J.P., V.K. and J.R. have contributed mainly to Section 4 and Section 5 and also to Section 2.3 and Section 3 to some extent. All authors have read and agreed to the published version of the manuscript.
Funding
This article is based on the research actions executed within the ITEA 18008 TIoCPS project (https://itea4.org/project/tiocps.html, accessed on 12 May 2024).
Data Availability Statement
Data is contained within the article.
Acknowledgments
Acknowledgments are offered for all partners of the TIoCPS project for collaborations.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Latvakoski, J.; Heikkinen, J. A Trustworthy communication hub for Cyber-physical systems. Future Internet 2019, 11, 211. [Google Scholar] [CrossRef]
- Latvakoski, J.; Roelands, M.; Tilvis, M.; Genga, L.; Santos, G.; Marreiros, G.; Vale, Z.; Hoste, L.; van Reamdonck, W.; Zannone, N. Horisontal Solutions for Cyber-Physical Systems evaluated in Energy Flexiblity and Traffic Accident Cases. M2Mgrids Project Publication. 34p. Available online: https://itea3.org/project/result/download/7344/Horizontal%20Solutions%20for%20Cyber-Physical%20Systems%20evaluated%20in%20Energy%20Flexibility%20and%20Traffic%20Accident%20cases.pdf (accessed on 6 September 2024).
- Latvakoski, J.; Kyllönen, V.; Ronkainen, J. Decentralised IOTA-Based Concepts of Digital Trust for Securing Remote Driving in an Urban Environment. IoT 2023, 4, 582–609. [Google Scholar] [CrossRef]
- Sachdeva, S.; Fatehaj, L.; Tan, S.; James, J.; Ajayi, O.; Saadawi, T. A Blockchain based Framework for Secure and Decentralized Energy Trading in a Community. In Proceedings of the 2023 IEEE International Conference on Industrial Technology (ICIT), Orlando, FL, USA, 4–6 April 2023; pp. 1–8. [Google Scholar]
- Eisele, S.; Laszka, A.; Mavridou, A.; Dubey, A. SolidWorx: A Resilient and Trustworthy Transactive Platform for Smart and Connected Communities. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1263–1272. [Google Scholar]
- Hong, J. ChainComm: A Framework for Future Communities Based on Blockchain. In Proceedings of the 2022 IEEE 8th International Conference on Computer and Communications (ICCC), Chengdu, China, 9–12 December 2022; pp. 1324–1328. [Google Scholar]
- Zhou, K.; Xing, H.; Zhang, Z. P2P Electricity Trading Method in Community Microgrid and Blockchain Environment. In Proceedings of the 2022 IEEE 6th Conference on Energy Internet and Energy System Integration (EI2), Chengdu, China, 11–13 November 2022; pp. 1668–1671. [Google Scholar]
- N‘goran, K.; Brou, A.; Pandry, K.; Tetchueng, J.; Kermarrec, Y.; Asseu, O. Zero Trust Security Strategy for Collaboration Systems. In Proceedings of the 2023 International Symposium on Networks, Computers and Communications (ISNCC), Doha, Qatar, 23–26 October 2023; pp. 1–6. [Google Scholar]
- Timpner, J.; Schürmann, D.; Wolf, L. Trustworthy Parking Communities: Helping Your Neighbor to Find a Space. IEEE Trans. Dependable Secur. Comput. 2016, 13, 120–132. [Google Scholar] [CrossRef]
- Naik, N.; Jenkins, P. Self-Sovereign Identity Specifications: Govern Your Identity Through Your Digital Wallet using Blockchain Technology. In Proceedings of the 2020 8th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), Oxford, UK, 3–6 August 2020; pp. 90–95. [Google Scholar]
- Hardman, D.; Curran, S.; Curren, S. (Eds.) Peer DID Method Specification v1.0 Draft. Available online: https://identity.foundation/peer-did-method-spec/index.html (accessed on 6 September 2024).
- Curren, A.; Looker, T.; Terbu, O. (Eds.) DIDComm Messaging v2.x Editor’s Draft. Available online: https://identity.foundation/didcomm-messaging/spec/ (accessed on 17 January 2024).
- Hassan, S.; De Filippi, P. Decentralized Autonomous Organization. Internet Policy Rev. 2021, 10, 1–10. [Google Scholar] [CrossRef]
- Ghavi, A.; Qureshi, A.; Weinstein, G.; Schwartz, J.; Lofchie, S.; Frank, F. A Primer on DAOs, Harvard Law School Forum on Corporate Governance. 2022. Available online: https://corpgov.law.harvard.edu/2022/09/17/a-primer-on-daos/ (accessed on 6 September 2024).
- Gaia-X. Available online: https://gaia-x.eu/ (accessed on 6 September 2024).
- Project GAIA-X: A Federated Data Infrastructure as the Cradle of a Vibrant European Ecosystem; German Federal Ministry for Economic Affairs and Energy (BMWi): Berlin, Germany, 2019.
- GAIA-X and IDS. Available online: https://internationaldataspaces.org/wp-content/uploads/dlm_uploads/IDSA-Position-Paper-GAIA-X-and-IDS.pdf (accessed on 6 September 2024).
- Dataspace Connector. Available online: https://international-data-spaces-association.github.io/DataspaceConnector/ (accessed on 6 September 2024).
- MyData. Available online: https://mydata.org/ (accessed on 6 September 2024).
- Energy Web. Available online: https://www.energyweb.org/ (accessed on 6 September 2024).
- Energy Web Switchboard. Available online: https://switchboard.energyweb.org/welcome (accessed on 6 September 2024).
- Jurmu, M.; Niskanen, I.; Kinnula, A.; Kääriäinen, J.; Ylikerälä, M.; Räsänen, P.; Tuikka, T. Exploring the Role of Federated Data Spaces in Implementing Twin Transition within Manufacturing Ecosystems. Sensors 2023, 23, 4315. [Google Scholar] [CrossRef] [PubMed]
- Otto, B. A Federated Infrastructure for European Data Spaces. Commun. ACM 2022, 65, 44–45. [Google Scholar] [CrossRef]
- World Wide Web Consortium (W3C). Decentralized Identifiers (DIDs) v1.0—Core Architecture, Data Model, and Representations. W3C Proposed Recommendation 3 August 2021. 2021. Available online: https://www.w3.org/TR/did-core/ (accessed on 28 April 2022).
- Sovrin. Self-Sovereign Identity and IoT. Sovrin Foundation SSI in IoT Task Force. 2020. Available online: https://sovrin.org/wp-content/uploads/SSI-in-IoT-whitepaper_Sovrin-design.pdf (accessed on 28 April 2022).
- Kronfellner, B.; Merey, T.; Beron, D.; Terbu, O. Me, Myself and (SS)I. Boston Consulting Group. 2021. Available online: https://web-assets.bcg.com/6b/6d/84e00cad4c939c870d833b96321c/white-paper-me-myself-ssi.pdf (accessed on 28 April 2022).
- Shi, J.; Zeng, X.; Han, R. A Blockchain-Based Decentralized Public Key Infrastructure for Information-Centric Networks. Information 2022, 13, 264. [Google Scholar] [CrossRef]
- Housley, R. Public Key Infrastructure (PKI). Available online: https://doi.org/10.1002/047148296X.tie149 (accessed on 2 January 2023).
- Liu, X.; Farahani, B.; Firouzi, F. Distributed Ledger Technology. In Intelligent Internet of Things; Springer: Cham, Switzerland, 2020; pp. 393–431. ISBN 978-3-030-30367-9. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 22 November 2022).
- Wang, X.; Garg, S.; Lin, H.; Kaddoum, G.; Hu, H.; Hossain, M.S. A Secure Data Aggregation Strategy in Edge Compuring and Blockchain-Empored Internet of Things. IEEE Internet Things J. 2022, 9, 14237–14246. [Google Scholar] [CrossRef]
- IOTA Introduction. Available online: https://wiki.iota.org/get-started/introduction/iota/introduction/ (accessed on 6 September 2024).
- Green, M. Hash-Based Signatures: An Illustrated Primer. Available online: https://blog.cryptographyengineering.com/2018/04/07/hash-based-signatures-an-illustrated-primer/ (accessed on 23 November 2022).
- Silvano, W.F.; Marcelino, R. IOTA Tangle: A cryptocurrency to communicate Internet-of-Things data. Future Gener. Comput. Syst. 2020, 112, 307–319. [Google Scholar] [CrossRef]
- Trust over IP Foundation. Introduction to Trust over IP. Version 2.0. 17 November 2021. Available online: https://trustoverip.org/wp-content/uploads/Introduction-to-ToIP-V2.0-2021-11-17.pdf (accessed on 22 November 2022).
- Findy. Available online: https://findy.fi/en/ (accessed on 6 September 2024).
- SICPA Digital Lab. Implementation of the Peer DID Method Specification in Python. Available online: https://github.com/sicpa-dlab/peer-did-python/ (accessed on 6 September 2024).
- Sharma, D.; Thompson, A.; Känsälä, K. EnergyDAO—Decentralised Autonomous Organisation for Energy Community Governance—VTT’s Research Information Portal VTT White Paper. 2023. Available online: https://cris.vtt.fi/en/publications/energydao-decentralised-autonomous-organisation-for-energy-commun (accessed on 6 September 2024).
- Buterin, V. Ethereum: A Next-Generation Smart Contract and Decentralized Application Platform. Ethereum Whitepaper. 2014. Available online: https://ethereum.org/content/whitepaper/whitepaper-pdf/Ethereum_Whitepaper_-_Buterin_2014.pdf (accessed on 17 January 2014).
- Infura. Web3 Libraries. ConsenSys Inc. 2024. Available online: https://docs.infura.io/api/learn/web3-libraries (accessed on 6 September 2024).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).