Highlights
What are the main findings?
- Developed a two-stage hierarchical planning model incorporating cyber insurance to bolster the resilience of ICT-integrated multi-energy systems against cyberattacks. This model effectively reduces operation costs by 29.0% and mitigates load shedding by 0.68 MWh, as demonstrated in simulation studies on a 33-20 distribution multi-energy grid system.
- Utilized a distributionally robust optimization approach, leveraging conditional value at risk (CVaR), to handle the emergent and uncertain nature of cyberattacks, making the problem tractable through sample average approximation techniques.
What is the implication of the main finding?
- The inclusion of cyber insurance in energy management strategies offers a proactive and financially viable approach to managing cyber risks, ensuring the continuity and resilience of smart city operations. This approach facilitates better preparedness and response to potential cyber incidents.
- The proposed model provides a valuable framework for city managers, aiding in making informed decisions regarding the procurement of cyber insurance and the implementation of real-time defense strategies. This not only enhances the economic performance and operational stability of smart city energy systems but also promotes a collaborative approach between insurers and energy system operators, setting a precedent for future research and development in the field of cyber risk management for ICT-integrated multi-energy systems.
Abstract
The proliferation of information and communication technologies (ICTs) within smart cities has not only enhanced the capabilities and efficiencies of urban energy systems but has also introduced significant cyber threats that can compromise these systems. To mitigate the financial risks associated with cyber intrusions in smart city infrastructures, this study introduces a two-stage hierarchical planning model for ICT-integrated multi-energy systems, emphasizing the economic role of cyber insurance. By adopting cyber insurance, smart city operators can mitigate the financial impact of unforeseen cyber incidents, transferring these economic risks to the insurance provider. The proposed two-stage optimization model strategically balances the economic implications of urban energy system operations with cyber insurance coverage. This approach allows city managers to make economically informed decisions about insurance procurement in the first stage and implement cost-effective defense strategies against potential cyberattacks in the second stage. Utilizing a distributionally robust approach, the study captures the emergent and uncertain nature of cyberattacks through a moment-based ambiguity set and resolves the reformulated linear problem using a dynamic cutting plane method. This work offers a distinct perspective on managing the economic risks of cyber incidents in smart cities and provides a valuable framework for decision making regarding cyber insurance procurement, ultimately aiming to enhance the financial stability of smart city energy operations.
1. Introduction
Following the high expectations that modern grids will benefit from information and communication technologies (ICTs), cyber security issues have also become non-negligible concerns, threating the security and economy of grid operations [1,2]. An FDI attack involves the deliberate manipulation of data within energy-management systems [3]. Unlike conventional cyberattacks that aim to disrupt system operations through denial-of-service or direct damage to the infrastructure, FDI attacks are more insidious [4,5]. They subtly alter the data used for decision-making processes in energy systems, leading to erroneous system operations, inefficient resource allocation, and potentially hazardous conditions. The methodologies employed in FDI attacks are diverse and they are evolving. Common strategies include tampering with sensor readings, corrupting data communication channels, and exploiting vulnerabilities in data-aggregation processes. These methods are designed to bypass conventional detection systems, making FDI attacks particularly challenging to identify and counter [6,7]. State estimation (SE) plays a vital part in detecting false data injection (FDI) attempts via filtering out inaccuracies from measurements [8]. In the realm of power system operations, SE plays a pivotal role. It involves the application of algorithms to deduce the most likely state of an electrical network [9] by utilizing observed measurements like voltages and power flows [10]. This process is critical in ensuring accurate and reliable data for grid management [11]. However, these measurements are susceptible to various sources of errors [12,13]. These errors could stem from instrument inaccuracies, data transmission issues, or even deliberate manipulations, as observed in cyberattacks. Inaccurate measurements can lead to incorrect decisions in grid management, making the grid vulnerable to inefficiencies, instability, or even systemic failures [14]. Therefore, understanding and improving state estimation is essential in bolstering the robustness of power systems against such vulnerabilities. Nevertheless, stealthily designed FDI attacks are able to compromise the measurement without being detected [15]. Recent history has witnessed several high-profile intrusions into power grid systems. There has been a wide variety of reports demonstrating the significant FDI-based cyber threats. Ukraine experienced major power outages affecting nearly 250,000 people due to cyberattacks. While these attacks primarily involved malicious software to gain control of and disable critical power infrastructure, they exposed systemic vulnerabilities in the grid’s cybersecurity. Such vulnerabilities could potentially be exploited by FDI attacks, where false data are injected to manipulate the grid’s operational decisions, leading to similar, if not more severe, disruptions [16]. The Olympic Destroyer malware incident during the Winter Olympics in Pyeongchang demonstrated the potential for cyber threats to disrupt critical infrastructure, including power grid systems. This event serves as a poignant reminder that, if FDI attacks were to target similar vulnerabilities, they could manipulate data to cause operational chaos without the immediate detection typically associated with more overt forms of cyberattacks [17]. The activities of the SandWorm group, which included spear-phishing and exploiting zero-day vulnerabilities, primarily targeted energy companies and critical infrastructure operators. This group’s method of compromising power grid systems signals a risk that is also pertinent in the context of FDI attacks [18].
1.1. Related Work
In order to mitigate the attack consequences, existing works have provided valuable insights to explore effective mitigation models [19]. The authors of [20] studied a trust value determination framework to indicate the trustworthiness of the obtained measurements. Distributed energy resources rely on the trust values of the control protocols to decelerate and mitigate FDI attacks. The authors of [21] attempted to design a two-stage detection and mitigation approach against electric vehicle (EV) switching attacks to avoid grid instability conditions. A back propagation neural network approach is applied to detect and delay the abnormal switching request. In [22], a hybrid FDI-mitigation scheme based on ensemble empirical mode decomposition is devised for concurrent attacks in DC microgrids. An event-driven mitigation method is adopted to eliminate the attack signal with the reconstruction of trustworthy signals. To enhance the robustness of cyber–physical control systems, the authors of [23] designed a reactive attack-mitigation method. The attack is formulated via a Markov decision process, and a Q-learning-based linear approximation is employed to solve the problem. A diversified software deployment for cyber risk mitigation is studied in [24] under the exposure of coordinated cyberattacks. A long-term optimization model ensures the expected minimal risk considering the worst-case scenario. The authors of [25] proposed a robust incentive-reduction strategic model against financially motivated FDI attacks, which targets the very short term load predictor and deceives the system operator with an uneconomic operation scheme. However, the existing literature solely relies on the emergency response measure to mitigate the attack consequences, which can be strengthened by involving pre-attack risk-management approaches, considering the likelihood of potential cyberattacks. The work in [26] is crucial as it addresses a timely and critical issue—the vulnerability of low-voltage distribution grids to cyberattacks precipitated by the increased integration of EV charging stations. One of the most commendable aspects of this paper is its focus on using the IEEE European Low-Voltage Test Feeder (ELVTF) as a standard model. This choice is particularly praiseworthy because it allows for a highly relevant and standardized approach to simulation, ensuring that the results are robust, reliable, and widely applicable. By utilizing the ELVTF, the study not only enhances its credibility but also contributes significantly to standardizing cybersecurity assessments within the smart grid domain.
It is unrealistic to cover and defend against all cyber threats due to their unforeseeable and catastrophic nature. Cyber insurance is designed to mitigate the financial losses that are incurred by cyber risks, offering a mechanism for managing the economic impact of cyberattacks, e.g., data breaches and malicious cyberattacks from hackers [27]. The insured party needs to pay the premium regularly, whilst the insurer is responsible for indemnity to cover the financial losses induced by cyberattacks. It is anticipated that the market size of commercial-based cyber insurance will reach into the multimillions by 2028. The American International Group (AIG) is a cyber insurance corporation at the forefront of the industry; it has offered protection services against cyber risks since the late 1990s. The CyberEdge policy is a well-known customized cyber insurance product which is a comprehensive cyber-risk-management solution, offering standalone schemes for business companies [28]. After the cyber disaster that was launched against the Colonial Pipeline in May 2021, U.S. energy companies started to realize the importance of purchasing cyber insurance. The insurance premium of the energy sector used to be the lowest across all industries. However, insurance companies have already prepared to increase premiums by between 25% and 40% due to the increasing severity of attacks and the unprecedented growth of the market [29].
Prior studies that have investigated cyber insurance management for power grids have been limited to single-stage operation models. The authors of [30] established an actuarial model to eliminate the riskiness and enhance the cyber insurance markets of power grids. A semi-Markov process (SMP) is applied to model the random cyber intrusion process, followed by sequential Monte Carlo simulations to assess the grid interruptions. As for applications in vehicle-to-grid systems, the authors of [31] adopted cyber insurance to mitigate the risks of high energy costs induced by EV charging against the unavailability of data transmission. The original problem is transformed into an optimization problem. An optimal charging and insurance buying policy is obtained. The authors of [32] devised a coalitional insurance investment framework as an alternative to the traditional insurance managed by third-party companies. The transmission operators serve as both the insured parties and the insurers. To hedge the economic losses against cyberattacks for EV charging stations, the authors of [33] proposed an optimal insurance premium scheme for insurers. A coherent risk assessment approach is incorporated into the mechanism design to guarantee its robustness. However, existing works are limited in modelling EV charging behavior and energy trading against cyber intrusions; additionally, they failed to incorporate the complete grid structure information and grid physical constraints. Since cyber insurance management for energy grids is still at the very early stages, further exploration is required to effectively mitigate the cyber risks.
The authors of [34] explored an integrated risk-management strategy that combines insurance and security investments to reduce overall security expenses. It evaluates the optimal investment under different insurance policies and concludes that the effectiveness of mixed strategies depends on factors like potential loss and vulnerability, often reverting to insurance-alone approaches under specific conditions. The authors of [35] investigated whether cyber insurance can enhance network security through a market-based analysis, including regulated monopolistic and competitive markets. The findings suggest that, while unique market equilibriums exist in both market types, their efficiency and impact on improving network security vary, with challenges highlighted in monopolistic markets due to issues around contract discrimination and insurer profitability. The authors of [36] presented analytical models for optimizing cybersecurity spending and cyber insurance, focusing on their effectiveness in reducing cyber threats. The study emphasizes the importance of private sector involvement in countering cybercrimes and proposes innovative cyber insurance approaches; these would be particularly beneficial for small- and medium-sized enterprises, through customized, threat-specific coverage and risk management support. The authors of [37] presented a mathematical analysis of cyber insurance in a non-competitive market, addressing concerns about cyber insurance leading to reduced security investments. The authors demonstrate that, with the right pricing strategy, it is possible to ensure that security investments remain high, even with insurance. Their theoretical analysis, supported by CARA and CRRA utility functions, provides insight into balancing insurance with maintaining robust security measures. This study investigates the dynamics of self-defense investments in Internet security in the context of cyber insurance coverage. The authors of [38] proposed a mathematical framework for understanding how cooperative and non-cooperative Internet users decide on their self-defense investments under full and partial insurance coverage. The results indicate that cooperative behavior enhances self-defense investment efficiency, and that partial insurance coverage motivates more prudent self-defense investments compared to full coverage. In this comprehensive survey [27], the authors provide an in-depth analysis of the burgeoning field of cyber insurance. They discuss its peculiarities, provide a formal background, and review the existing literature on the topic. The paper explores the applicability of cyber insurance in various technological systems, identifies unique challenges in this market, and proposes directions for future research, making it a valuable resource for understanding the landscape of cyber insurance.
The Distributionally Robust Optimization (DRO) method is developed to hedge against the system uncertainties for energy management, including renewable generation fluctuation, load variation, natural disasters, etc. The authors of [39] applied DRO to evaluate the operation costs affected by uncertain wind generation and EV charging delays. A linear decision rule model is adopted to approximate the second-stage formulation, assuming that real-time decisions are an affine relationship of uncertainty realizations. In [40], a DRO-based chance-constrained program is utilized to account for the load uncertainty in a multistage distribution-expansion planning model. The intractable nonlinear constraints are reformulated into second-order conic constraints. DRO is effective in mitigating the overfitting effects and in reducing the estimation errors of classical stochastic optimization to characterize a single distribution. DRO also contributes to weakening the over-conservativeness of robust optimization.
The implementation of effective cyber insurance management for insured parties is faced with numerous challenges. These include the unpredictability of demand for security services [41], the inherent uncertainty of the severity of cyber risks [42], and the prohibitive costs of insurance premiums [43]. To date, no power grid utility providers have purchased cyber insurance coverage, largely due to the difficulties associated with the design of a comprehensive cyber-risk-assessment and -mitigation program [44]. The lack of a one-size-fits-all approach to cyber insurance, with each customer having unique requirements and needs, exacerbates the problem. The challenge of unpredicted demand for security services is particularly acute as cyber threats continue to evolve at an exponential pace, making it difficult to anticipate future security needs [45]. Furthermore, the unpredictable nature of cyber risks, combined with the lack of historical data, makes it challenging to estimate the potential impact of a cyberattack [46]. This lack of certainty is reflected in the high cost of cyber insurance premiums, which, in turn, makes it difficult for power grid utility providers to justify the investment. Given these challenges, it is crucial to design customized solutions for cyber insurance management that effectively contain risk. This could involve a combination of risk transfer mechanisms, such as insurance coverage, and risk-mitigation strategies.
1.2. The Proposed Approach and Novelties
This work introduces a cyber insurance model specifically designed for ICT-integrated multi-energy systems to mitigate the risks associated with cyberattacks, particularly false data injection (FDI) threats. Tailored to meet the critical needs of these systems, the model covers immediate post-attack expenses such as system diagnosis, component isolation, and restoration, focusing on risks to data and control systems that may disrupt operations. It calculates premiums based on the system’s risk profile, incorporating factors like complexity and past cyber incidents. The model strategically combines risk management with financial tools to ensure continuous operation, which is crucial for multi-energy systems. Additionally, it proposes a novel two-stage hierarchical cyber insurance planning (TCIP) model that optimizes insurance costs and operational efficiencies through risk transfer and real-time defense strategies. The TCIP model employs a moment-based Distributionally Robust Optimization (DRO) method, ensuring adaptability to FDI threats. Its effectiveness is demonstrated through simulations in a 33-20 distribution multi-energy grid (MEG) system, showing significant reductions in load shedding and operational costs.
This paper introduces a novel, cooperative, risk-management strategy that revolutionizes traditional approaches to cyber risk in power grid systems. Unlike conventional methods that primarily focus on financial risk transfer, this innovative strategy fosters a dynamic collaboration between insurers and grid operators, embedding proactive and reactive measures to robustly counteract cyber threats. The insurer’s involvement extends beyond mere post-incident financial restitution; it encompasses active participation in incident management, supplying specialized expertise and advanced cybersecurity technologies that are critical for rapid and effective incident response. This collaborative effort not only expedites the recovery process but also minimizes downtime and operational disruptions. Insurers contribute their extensive knowledge and resources, which are crucial for swiftly identifying, containing, and mitigating cyberattacks. This enables grid operators to customize their response strategies to specific threats, significantly enhancing the system’s defensive capabilities. Moreover, the mutual engagement in developing and implementing comprehensive cybersecurity protocols, conducting thorough risk assessments, and maintaining ongoing system monitoring ensures that vulnerabilities are preemptively identified and addressed. The strategy introduced in this paper promotes a shared-responsibility framework, where both insurers and the insured party actively participate in the intricate web of decision making and risk management. This approach not only enhances immediate response capabilities but also bolsters long-term system resilience against cyber threats. It represents a paradigm shift in the understanding of cyber insurance, positioning it as a vital, integrated component of holistic cyber risk-management strategies for power grids. This cooperative risk management model is not just a theoretical construct but a practical, innovative solution that significantly advances the security and robustness of power systems, offering a blueprint for future approaches to infrastructure protection. In Figure 1, a graphical summary illustrates the multifaceted rationale behind our study, highlighting the complex interplay between enhancing cybersecurity, optimizing economic outcomes, and advancing research methodologies in smart city energy systems. The first segment of the diagram emphasizes the critical need for robust cybersecurity measures to address inherent vulnerabilities and minimize the economic impacts of cyber incidents on the interconnected infrastructure of smart cities. This protection is essential in preventing operational disruptions and costly recoveries following cyber threats. The second segment focuses on the strategic implementation of cyber insurance as a financial risk management tool, which not only transfers financial risks to insurers but also enhances cost efficiency and encourages proactive technological investments. This ensures that smart cities can maintain resilience while fostering economic stability. The third segment outlines our commitment to advancing the knowledge and methodologies in cyber risk management. It depicts how empirical insights from our study inform policy making and promote an interdisciplinary approach, integrating cybersecurity, insurance economics, and energy management to effectively tackle the challenges faced by smart city infrastructures. Together, these elements provide a comprehensive understanding of the reasons why this research is critical, serving as a foundation for further investigation and development in the field.
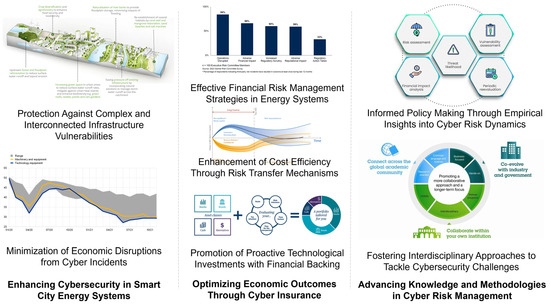
Figure 1.
A graphical summary of the research motivations.
In conclusion, this work presents a significant contribution to the field of cyber insurance management for ICT-enabled multi-energy grids, offering a comprehensive and effective solution for mitigating cyber threats.
- ✓
- In comparison to prior studies in the realm of cyber insurance management for electric vehicle charging stations or local energy systems, the present work encompasses a more comprehensive scope; it takes a full array of physical constraints and system functionalities into account, including optimal power flow, generator dispatch, and energy-balancing conditions. The proposed cyber insurance framework does not merely represent a risk-transfer solution; rather, it represents a cooperative risk-management strategy for energy system operators.
- ✓
- Cyberattacks in power systems are known to trigger a cascade of effects that propagate through interconnected subsystems. Previous work in the realm of MEGs has not considered the implications of such attacks on cyber insurance management. To address this, the present work leverages optimal coordination of system interdependencies in order to mitigate attack consequences and minimize losses.
- ✓
- Given the lack of historical data and the unpredictable nature of cyberattacks, a novel two-stage DRO method is adopted to estimate the potential impact of such attacks and formulate the total cost of the TCIP model. Unlike traditional SMP methods, the DRO approach seeks an optimal solution under the worst-case uncertainty distribution and provides robust mitigation against cyberattacks.
The subsequent sections of this paper are arranged as follows: Section 2 provides an overview of detection bypassing and cyber intrusion principles; Section 3 formulates the TCIP model; Section 4 outlines the DRO method and its solution procedures; Section 5 presents case studies to test the performance of the TCIP model; the paper concludes in Section 6.
2. Modeling of Cyber Intrusions in Energy Systems
This section illustrates how the stealthily designed FDI attacks are executed to introduce erroneous data into system measurements, thereby causing disruptions in the operations and decision-making processes of the energy systems. State estimation is widely used for detecting the redundant measurements and eliminating erroneous signals [47]. Equation (1) demonstrates nonlinear measurement between meter measurements, , and state variable , where denotes the measurement errors. The Jacobian matrix is denoted as . This manipulation of data typically occurs without detection, as FDI attacks are designed to mimic legitimate data patterns. These attacks introduce discrepancies that can lead to incorrect system operations, affecting energy distribution and stability. The process of state estimation, therefore, is crucial for identifying and correcting these deviations by providing a mathematical method of estimating the actual system states based on the measurements received.
Weighted least squares (WLS) is widely used for bad data detection; it estimates the values of the model parameters based on ordinary least squares and linear regression. WLS estimates the unknown values in the regression function via minimizing the sum of squared deviations of errors and functional portion of the model [48]; in (2), is assumed to follow normal distribution with zero mean and diagonal covariance matrix D = diag(, , …, ). WLS is a refinement of the ordinary least squares, incorporating weights into the regression to account for variations in data quality or informational content. This method is particularly effective in contexts where measurement errors vary significantly across data points, allowing for more accurate estimation by giving less weight to data points with higher variances. In energy system monitoring, where measurements can be influenced by a variety of error sources, applying WLS helps in minimizing the influence of these errors on the estimation process. By optimizing the weights assigned to each measurement based on their estimated precision, represented by the diagonal elements of matrix D, WLS finetunes the parameter estimation process to improve the robustness and reliability of the state estimation. The objective of the WLS in this context is to minimize the sum of the weighted squared differences between observed measurements and those predicted by the model, which leads directly into the formulation of Equation (2).
The derivation of the optimal solution involves computing the pseudo-inverse of the matrix formed by the product of the transpose of the Jacobian matrix, H, the inverse of the covariance matrix, D, and H again. This calculation method leverages the generalized least squares approach, which assigns weights to the measurements optimally according to their respective variances to minimize estimation errors. The resulting solution, represented by Equation (3), provides the most statistically efficient estimate of the state variables, assuming that the errors are normally distributed and independent.
When an FDI attack is launched, erroneous measurements are manipulated. Bad data detection utilizes residual to detect the measurements that have been tampered with. When follows the normal distribution; is proved to follow the distribution. is considered as a bad data measurement when is larger than the threshold ζ.
The attacker strategically crafts a vector that will alter the system’s measurements in a subtle—yet impactful—way. This attack vector, denoted as a, is designed to seamlessly integrate with the normal data flow, making detection challenging. It is computed by multiplying the Jacobian matrix H by a nonzero vector, c, which represents specific alterations in state variables that are intended to mislead the state estimation process.
During an FDI attack, the actual measurements z are altered by the addition of the attack vector a, resulting in manipulated measurements, . This alteration impacts the estimated state, , which adjusts to due to the deceptive data. Consequently, the residual , which reflects the difference between manipulated measurements and the recalculated estimates, remains ostensibly unchanged, masking the presence of the attack.
When , corresponding to , is smaller than the threshold ζ, then is also smaller than the threshold ζ, since and . Accordingly, the attack is successful, evading the detection of the bad data.
3. The Proposed Cyber Insurance Planning Model
3.1. Objective Function
The objective functions are made with the intention of minimizing the total cost that stems from both the cyber insurance planning and the operation cost to defend against the possible FDI; the objective functions are formulated in the first and second stages, respectively. Equation (7) formulates the objective function in the first stage, seeking to minimize the cyber insurance planning cost , where and indicate the power load amount covered by the insurance; and represent the unit cost of the insurance premium. Equation (8) presents the second-stage operation objective function, including the costs of power and gas generation , the usage of gas turbine costs , the storage costs , and the load-shedding costs during the operation to respond to the energy supply shortage that was caused by the FDI attacks.
3.2. Constraints
Overall, the power distribution system is radially structured and the DistFlow equation is applied for power flow modelling [49]. Power and gas systems are intertwined through energy converters. These are accounted for in the Weymouth equations for gas systems.
The output constraints of power distributed generators (DGs) , gas sources , gas turbines , and power market injection are stated in (9). Meanwhile, the reactive power output of DGs is ensured in (10). Constraint (11) sets the upper and lower bounds for the charging/discharging power ( and ) of battery storage systems. Constraint (12) indicates the current battery state is based on the state of the last time period , where and are the efficiencies.
Constraints (14) and (15) establish the relationship between voltage and power flow, where and are the voltages of intital and terminal buses on a same line; the active and reactive power flow are represented by and ; the resistance and reactance are denoted as and . Followed by the power flow expression are the magnitude constraints of the power flow in (16) and (17).
Similar to (11)–(13), Equations (18)–(20) show the gas storage modelling, where is the charging/discharging power at time t, is the remaining gas storage capacity, the operational efficiencies are represented by and . In [50], the Weymouth gas flow equations are given, where is the pressure; the pressure at the initial and terminal gas nodes is and ; is the Weymouth equation constant; the gas flow is denoted as .
Constraints (25) and (26) are the explicit modelling of FDI attacks. To successfully evade detection, the overall sum of the manipulated load deviation has to be unchanged, and the deviation magnitude must be limited to being within a safety range. Active and reactive power balance constraints are presented in (27) and (28), where represents the renewable generation uncertainty; the load demand is ; the P2G conversion is . In (29), the gas balance constraint at each node is given.
4. Distributionally Robust Decision Making
DRO is used for FDI scenario deduction, and it implements rational decision making for the proposed TCIP. The two-stage TCIP model is given as follows:
where x and y are the decision variables of the first and second stages. and represent the objective functions. Equation (31) is the compact form of the first-stage constraints. The explicit second-stage objective and abstract constraint are shown in (32) and (33). Note that uncertainties are addressed in the second stage and ξ ≔ (d, B, C, h) for notation simplicity.
The ambiguity set is used to capture a family of uncertainty distributions supported by the empirical data. In this paper, a moment-based ambiguity set is applied for cyberattack scenario deduction.
First derive the Lagrange function of the inner maximization problem sup .
It is obvious that, when Q(x, ξ) − λ0 − ∑m λφξφ > 0, sup F(P, λ) = ∞. Accordingly, the inequality in (36) holds.
As a consequence, the Lagrange dual of sup is given as follows:
The equivalent form of (37)–(39) is shown as (40)–(43), which is deemed as the distributionally robust counterpart of (30).
Equations (40)–(43) can be reformulated as (44) by eliminating λ0.
Then, establish a CVaR-based sample average approximation model for the above distributionally robust counterpart, as stated in [51]. Note that CI represents the confidence interval and is the loss threshold; [x]+ picks the larger value between x and 0.
Then, the CVaR approximation is applied to replace the min- sup structure by recalling (44)–(46). Due to the difficulty that is encountered when calculating the integrals in the CVaR approximation, a SAA method is adopted. The CVaR-based SAA model is given in (48)–(50), where ξ1, …, ξ are the independent samples and belong to ξ ∈ Θ.
To solve the problem in (48)–(50), a stochastic dual dynamic programming (SDDP) method is adopted, which is tailored for solving multistage stochastic programming problems [52]. It aims to establish a linear approximation for Q(x, ξj). The dual form of (32) and (33) is firstly derived as follows:
Note that α is the dual solution of (32) and (33). The linear approximation of Q(x, ξ) is derived as follows:
where Uk(x, ξ) and Rk(x, ξ) are defined as (56) and (57). When x and ξ are fixed, Q(x, ξ) must be larger than or equal to its supporting planes, i.e., Q(x, ξ) ≥ Rk(x, ξ).
Finally, the SDDP method for solving (53)–(55) is given in Figure 2. In the proposed SDDP approach, the sequence of solving the second-stage problem before the first-stage problem is integral to the methodology. This structured sequence optimizes decision-making processes under uncertainty. By initially addressing the second-stage problem, decision variables and stochastic parameters are utilized to derive the dual solutions and the primal solutions . This strategy allows for the capture and quantification of the impacts of various uncertainties on the system’s performance before finalizing the first-stage decisions.
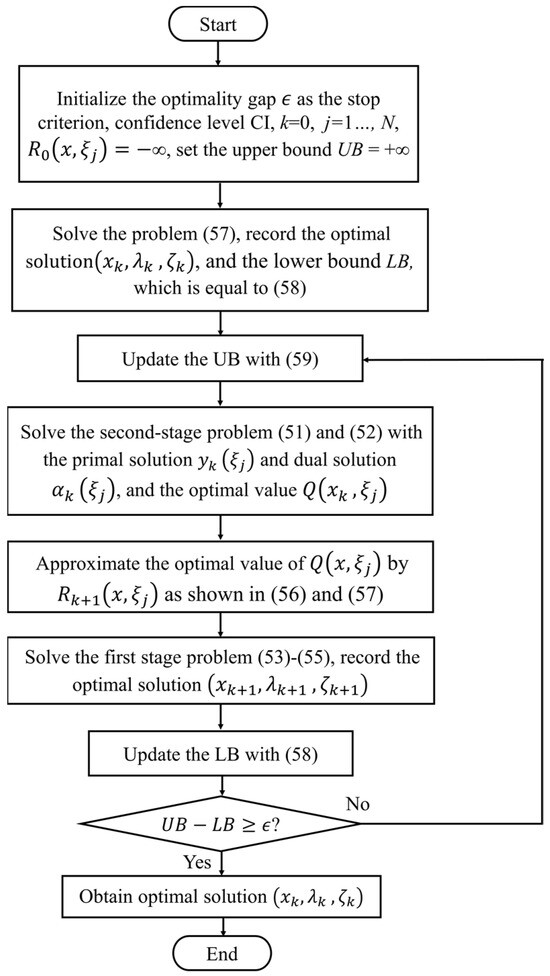
Figure 2.
The SDDP approach, presented as the solution algorithm.
This preemptive solving of the second-stage problem provides essential insights into the conditional value functions and their gradients, which are critical for accurately updating the policy approximation in the first-stage problem. Consequently, first-stage decisions can be more effectively optimized to account for the range of possible future scenarios, thereby enhancing the robustness of the overall system against uncertainties. The results from the second-stage problem serve as foundational inputs for refining the decision rules applied in the first stage, , ensuring that the approach is both proactive and responsive to changing conditions.
The lower bound and upper bound problems are
5. Case Studies
To test the proposed TCIP model in strengthening the system’s cyber security, a simulation-based case study was performed on an urban distribution grid consisting of an IEEE 33-bus power system connected to a 20-node gas system, as described in Figure 3. Figure 4 shows the power load demand profile. This system contains three conventional DGs and four renewable energy sources. The system also includes battery and gas storage for flexible operation. Based on the previous research, the insurance premium is USD 864/MWh and the load shedding penalty is USD 968/MWh [32]. Table 1 and Table 2 demonstrate the technical parameters of the power and gas generators. The established simulations are executed using MATLAB R2021b with a MOSEK 10.0.33 solver on a laptop with an Intel Core i7-1250 CPU and 16 GB of RAM.
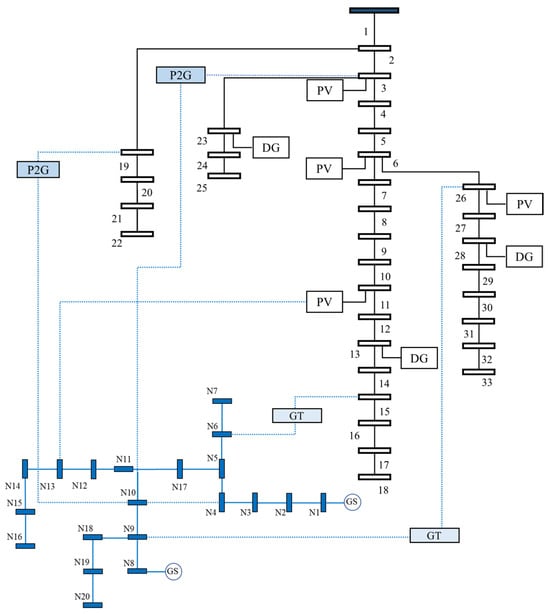
Figure 3.
The topology of the test system.
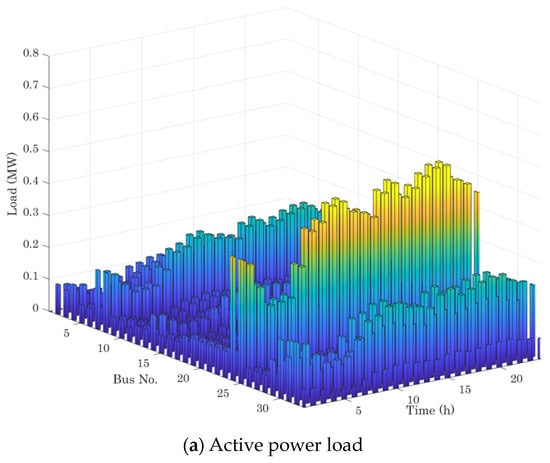
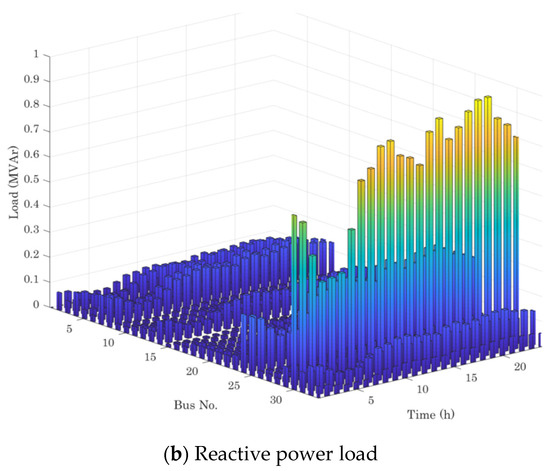
Figure 4.
The load demand profile.

Table 1.
Parameters of gas generators.

Table 2.
Parameters of traditional DGs.
To highlight the merit of the proposed TCIP, six cases were designed in the evaluation, as follows:
- Case I: Baseline case.
- Case II: Limiting the insurance purchase amount by 20%.
- Case III: Limiting the insurance purchase amount by 50%.
- Case IV: Increasing the insurance price by 25%.
- Case V: Increasing the insurance price by 50%.
- Case VI: Omitting the renewable generation uncertainty.
The load shedding consequences are examined under a spectrum of scenarios, characterized by varying attack intensities and the overall system loads shown in Figure 5, Figure 6 and Figure 7. The findings demonstrate that, as the attack level and system load increase, the resulting load shedding also increases across all scenarios. It is noted that the most severe load shedding occurs in Case III, with a total of 21.9 MWh, while the least significant load shedding is observed in Case I, at 19 MWh. This highlights the finding that limiting the insurance purchase amount has an adverse impact on the security of the system’s operation. Furthermore, the observations indicate that the rate of the load shedding increment is relatively slow when the system load is low, but increases significantly as the system load rises.
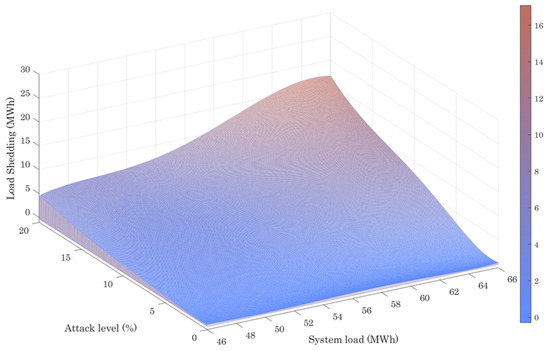
Figure 5.
Power load shedding results under Case I.
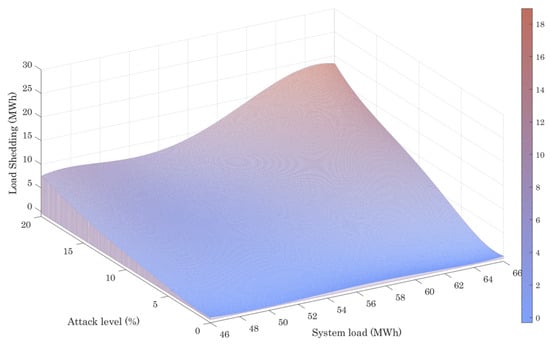
Figure 6.
Power load shedding results under Case II.
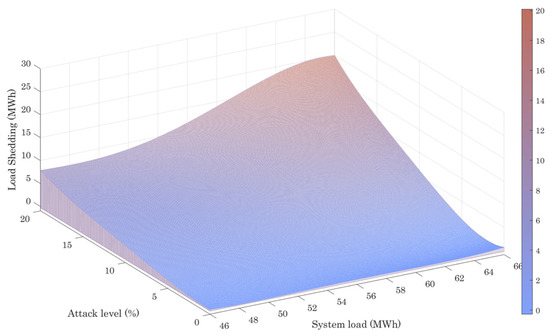
Figure 7.
Power load shedding results under Case III.
Table 3 shows the operation cost results for all the cases in terms of the two separated stages. Cases I–III are used to test the impact of the insurance purchase amount on the operation cost. Case II shows a noticeable increase in the first-stage results, with a 19.8% increase when compared to Case I. A considerable increase can be seen in the expected second-stage results of Case II, which exhibits a 44.7% increase when compared to Case I. The total results reflect the finding that Case II provides a 20.7% improvement over Case I. A comparison between Case II and Case III highlights the following finding: Case III exhibits a slight increase in the first-stage results, with a 7.7% rise when compared to Case II. The expected second-stage results of Case III show a marginal improvement, with a 2.8% increase when compared to Case II. The above findings indicate that limiting the cyber insurance purchase amount will inevitably cause the operation costs to increase.

Table 3.
Operational costs for all cases.
Cases IV and V are set to test the influence of the insurance premium on economic performance. The total operation cost is USD 365,991 under Case IV when the premium is increased by 25%. In addition, in Case V, an extra 4.7% cost increase is noted when the premium is increased by a further 25%. Case V displays a slight growth in the first-stage result, with a 3.6% increase when compared to Case IV. The operation cost result is also examined without considering the uncertainty of renewable generation in Case VI. It can be seen that the second-stage result is reduced by USD 5620.
As for the interplay between the cyber insurance amount and the premium and their effect on the load shedding results, the findings are displayed in Figure 8a,b; the findings reveal that a reduction in the insurance amount leads to a proportional rise in power load shedding. Specifically, there is a 0.12 MWh and 0.68 MWh increase in load shedding under Cases II and III, respectively. However, the results also highlight the importance of a well-structured insurance plan. When insurance coverage is carefully planned, it allows for real-time emergency response to prioritize the protection of uninsured loads, ultimately reducing the overall load shedding amount. As for the impact of the insurance premium on load shedding, the results show that an increase in the insurance premium results in an increase in load shedding; this is indicated by the 11.8% increase that was observed when an additional premium of 25% is applied. The study provides valuable insights into the relationship between the cyber insurance amount and the premium and their effects on the load shedding results. The results demonstrate the need for a well-planned insurance strategy to minimize the impact of load shedding, as well as highlighting the trade-off between the insurance premium and the load shedding outcomes.
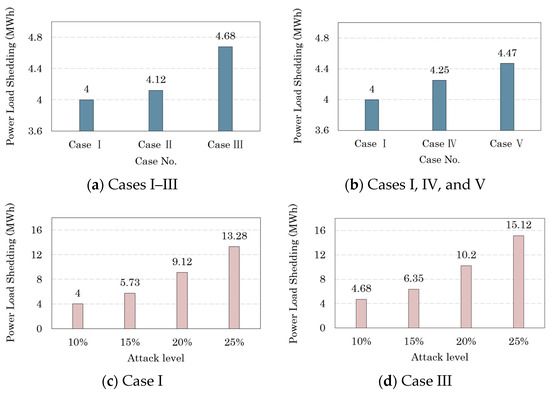
Figure 8.
Load shedding comparison under different scenarios.
The influence of varying attack levels on the power load shedding results is presented in Figure 8c,d. It can be observed that a higher attack level results in a corresponding increase in load shedding. This can be attributed to the direct and proportional relationship between the attack level and the detrimental impact on the power system. The findings show that an attack level of 25% results in a load shedding amount of 13.28 MWh and 15.12 MWh for Cases I and III, respectively. These results highlight the significance of robust security measures and the need for an efficient response strategy to mitigate the consequences of cyberattacks on the energy system.
6. Comparative Analysis of Cybersecurity Methodologies
This study integrates and applies the methodologies from two recent research papers, adapting their innovative approaches to unique scenarios for a comprehensive comparative analysis [30,32]. Initially, the coalitional cyber insurance model presented in the first referenced paper was applied to a collaborative framework among multiple energy system operators within a simulated smart city environment [32]. This model enables the formation of a risk-sharing coalition, where premiums are calculated based on shared data regarding vulnerabilities and historical cyber incident data, thereby attempting to mitigate the financial impact across all participating entities. Additionally, the actuarial framework, using semi-Markov processes, is incorporated, modeling the durations and state transitions of the cyberattacks that are affecting the smart city’s energy infrastructure [30]. This adaptation involves developing a stochastic model to assess the interdependencies among cyber risks across the integrated energy systems, employing Monte Carlo simulations to predict the impact and effectiveness of the proposed insurance schemes under various cyberattack scenarios. Through these applications, the proposed approach not only leverages the existing theoretical advancements but also enhances them by tailoring their implementation to fit the specific context and challenges of the scenarios. The outcomes of applying these methods are then meticulously compared with the results derived from the proposed proprietary method, focusing on several key performance indicators, such as risk mitigation efficiency, cost reduction, operational resilience, and recovery capabilities. This comparative analysis seeks to underline the advantages and potential limitations of each approach, providing a nuanced understanding of their applicability and effectiveness in real-world settings. By methodically evaluating these adapted methodologies against the proposed approach, the study aims to demonstrate the superiority, or in certain cases, the complementary nature of the proposed method, offering valuable insights into the strategic management of cyber risks in critical infrastructure environments.
In Table 4, a comparative analysis of performance metrics across three different methodologies applied to cyber risk management in power systems is presented. The table focuses on two key performance indicators: cost reduction and risk mitigation efficiency. Cost reduction (%) is calculated as the percentage decrease in the total financial expenditure associated with managing and mitigating cyber risks compared to a baseline scenario without the implemented method. Risk mitigation efficiency (%) measures the effectiveness of a method in reducing the frequency and severity of cyber incidents, thereby maintaining system stability and operational continuity. The proposed DRO method demonstrates superior performance in both metrics compared to the other two methodologies. It achieves a cost reduction of 12.5%, which is 2.3% higher than that achieved by the Coalitional Cyber Insurance Model and 3.8% higher than the Actuarial Cybersecurity Framework. This indicates a more efficient allocation and utilization of resources under the DRO method, potentially leading to significant savings in operational costs for power systems. In terms of risk mitigation efficiency, the DRO method also leads with an 82.3% efficiency rate, surpassing the Coalitional Cyber Insurance Model by 6.8% and surpassing the Actuarial Cybersecurity Framework by 11.5%. This enhanced efficiency underscores the effectiveness of the DRO method in not only identifying and responding to cyber threats but also in maintaining system stability and reducing potential disruptions caused by such threats. The results underscore the DRO method’s robustness and adaptability in handling the uncertainties and dynamics of cyber threats more effectively than the other tested methods. The superior performance of the DRO method in both cost reduction and risk mitigation efficiency positions it as a promising approach for enhancing the cyber resilience of power systems. These findings advocate for its consideration and potential implementation in real-world scenarios; here, reducing costs while effectively managing risks is of paramount importance.

Table 4.
Performance metrics comparison.
Table 5 presents a detailed comparison of financial resilience metrics among the three distinct methodologies that were applied to cyber risk management within power systems. This table focuses on three critical financial indicators: cost reduction, risk mitigation efficiency, and the cost–benefit ratio. Cost reduction (%) is quantified as the percentage reduction in financial outlays necessary for managing cyber risks, reflecting how each method economizes on cyber risk management expenses. Risk mitigation efficiency (%) assesses the effectiveness of each method in reducing the likelihood and impact of cyber threats, an effort which is crucial for maintaining operational integrity. The cost–benefit ratio offers insight into the economic efficiency of the investments, calculated by comparing the costs incurred to the benefits gained, expressed as a ratio. The proposed Distributionally Robust Optimization (DRO) method exhibits the highest performance across all the metrics, with a cost reduction of 14.3%, a risk mitigation efficiency of 40.6%, and a cost–benefit ratio of 1:4.2. These results indicate the superior cost management of the DRO method, in addition to its exceptional balance of expenditure versus payoff, suggesting an optimal allocation of resources for maximum return on investment. In comparison, the Coalitional Cyber Insurance Model and the Actuarial Cybersecurity Framework show lower efficacies, with cost reductions of 12.8% and 10.9%, risk mitigation efficiencies of 35.4% and 30.7%, and cost–benefit ratios of 1:3.5 and 1:2.9, respectively. This analysis highlights the DRO method’s superior capability in providing robust financial management and risk-mitigation strategies, making it a more compelling choice for enhancing the financial resilience of power systems against cyber threats. The superior metrics associated with the DRO method demonstrate its potential for broad implementation in sectors requiring stringent risk-management frameworks, where effective cost management and high returns on security investment are paramount.

Table 5.
Financial resilience metrics.
The comparative analysis outlined in Table 4 and Table 5 conclusively demonstrates the distinct advantages of the proposed DRO method over the methodologies presented in the Coalitional Cyber Insurance Model and the Actuarial Cybersecurity Framework. Primarily, the DRO method excels in both financial efficiency and operational effectiveness, achieving a 12.5% reduction in cost and an 82.3% increase in risk mitigation efficiency, which are substantial improvements over the other methods. Furthermore, the financial resilience metrics solidify the DRO method’s superiority, with a cost reduction of 14.3%, a risk mitigation efficiency of 40.6%, and an impressive cost–benefit ratio of 1:4.2, significantly outpacing the other models. These results underscore the DRO method’s capability to not only manage costs more effectively but also enhance the operational stability of power systems under cyber threats. This is achieved through an innovative optimization approach that better adapts to the complexities and dynamics of modern cyber environments, allowing for more precise risk assessments and more effective allocation of resources. The higher cost–benefit ratio indicates a more efficient investment return, which is critical for energy companies operating under tight financial constraints and facing diverse cyber threats. The superior performance of the DRO method, particularly in managing and mitigating risks while optimizing financial inputs, positions it as a robust solution for enhancing cyber resilience. This is crucial for power systems where the consequences of cyber incidents can be severe, affecting not only the financial bottom line but also the reliability of critical infrastructure. The adaptability and effectiveness of the DRO method make it an optimal choice for real-world applications, offering significant improvements over existing methods in both mitigating cyber risks and enhancing the economic and operational resilience of power systems.
7. Concluding Remarks
In conclusion, this study presents a groundbreaking framework for effectively managing cyber risks in ICT-integrated multi-energy systems. The novel integration of cyber insurance into a two-stage hierarchical planning model offers a unique and effective approach to cyber risk management, ensuring the long-term profitability and continuity of energy system operations. The optimization model balances the trade-off between energy system operation and cyber insurance coverage, enabling energy system operators to make informed decisions and implement effective defense strategies against potential cyberattacks. The results indicate that purchasing cyber insurance helps to reduce operational costs by 29.0% and load shedding by 0.68 MWh when 50% of buses are covered. This framework has the potential to revolutionize the field of cyber risk management, serving as a valuable reference for energy system operators and enhancing the economic performance of energy systems. With its practical applications, this work sets the stage for further research and development in the area of cyber insurance and risk management in ICT-integrated multi-energy systems.
This study underscores the importance of integrating cyber insurance into urban governance strategies to enhance the management of cyber risks in ICT-integrated multi-energy systems. It is recommended that urban governance bodies promote policies that support the adoption of cyber insurance, providing guidelines on risk assessment, premium calculations, and coverage standards specific to the energy sector’s needs within smart cities. By incentivizing energy operators through financial supports such as tax reductions and grants, and fostering partnerships between them and insurance providers, cities can ensure more stable and economically efficient energy system operations. This proactive approach not only reduces operational costs and minimizes load shedding during cyber incidents but also sets a foundation for ongoing improvement in risk management practices, adapting to emerging cyber threats and enhancing the overall resilience and economic performance of urban energy infrastructures.
This study, while comprehensive in its approach to developing a cyber-resilient energy management model for smart cities, presents several limitations that should be acknowledged. Firstly, the proposed model relies heavily on the accuracy and reliability of the data used, including the assumptions made about cyber threat patterns and the behavior of energy systems under attack. Variations in these datasets can significantly impact the outcomes of the model. Secondly, the application of the two-stage SDDP method, while effective in this context, may not be directly transferable to other types of multi-energy systems with different operational and structural characteristics. This limits the generalizability of the findings and may necessitate modifications to the model to suit other specific contexts or configurations. Furthermore, the integration of cyber insurance as a risk management tool is based on current market conditions and regulatory environments, which are subject to change. Changes in these areas could affect the model’s applicability and effectiveness in real-world scenarios.
To further advance the study of cyber-resilient energy-management systems, specific areas for future research have been identified. One pivotal area involves the exploration of adaptive cyber insurance models that can dynamically adjust to changing cyber threat landscapes and evolving regulatory frameworks. Such models would provide more robust risk-management strategies that are capable of responding to the rapid advancements in cyberattack methodologies. Additionally, the development of more sophisticated predictive analytics for identifying potential cyber threats before they impact the energy system is recommended. Integrating artificial intelligence and machine learning techniques could enhance the predictive capabilities of the proposed model, enabling more proactive mitigation strategies. Another frontier for future research is the quantitative evaluation of the impact of cyberattacks in the context of novel technological integrations within power systems. Building upon the foundational work conducted in this study, subsequent investigations will focus on technologies such as energy communities and virtual power plants, particularly exploring the concept of virtual islanding [53]. Future research will specifically investigate how virtual islanding can mitigate the effects of cyber threats on energy systems, with a focus on scenarios involving the substantial integration of renewable energy sources. By implementing a series of cyberattack simulations on systems employing virtual islanding, the study will assess the robustness of this approach under varying attack vectors.
Author Contributions
Conceptualization, A.P.Z. and F.X.F.; methodology, F.X.F.; software, A.P.Z.; validation, A.P.Z., F.X.F. and M.A.; formal analysis, A.P.Z. and F.X.F.; investigation, F.X.F.; resources, M.A.; data curation, M.A.; writing—original draft preparation, A.P.Z. and F.X.F.; writing—review and editing, A.P.Z. and M.A.; visualization, A.P.Z. and M.A.; supervision, A.P.Z. and M.A.; project administration, A.P.Z.; funding acquisition, M.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Researchers Supporting Project grant number RSPD2024R635. And The APC was funded by Researchers Supporting Project (Project number: RSPD2024R635), King Saud University, Riyadh, Saudi Arabia.
Data Availability Statement
The data can be requested via contacting the authors.
Acknowledgments
The authors would like to acknowledge the support provided by Researchers Supporting Project (Project number: RSPD2024R635), King Saud University, Riyadh, Saudi Arabia.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
| ICT | Information and Communication Technologies |
| FDI | false data injection |
| SE | state estimation |
| EV | electric vehicle |
| DC | direct current |
| DRO | Distributionally Robust Optimization |
| SMP | semi-Markov process |
| CVaR | conditional value at risk |
| SAA | sample average approximation |
| MEGs | multi-energy grids |
| TCIP | two-stage hierarchical cyber insurance planning |
| DG | distributed generator |
| SDDP | stochastic dual dynamic programming |
| QoS | quality of service |
| AI | artificial intelligence |
| SCADA | supervisory control and data acquisition |
| IoT | Internet of Things |
| NIST | National Institute of Standards and Technology |
| ISO | International Organization for Standardization |
| NERC | North American Electric Reliability Corporation |
| CPS | cyber–physical systems |
| P2G | power to gas |
| CI | confidence interval |
References
- Sun, C.-C.; Hahn, A.; Liu, C.-C. Cyber security of a power grid: State-of-the-art. Int. J. Electr. Power Energy Syst. 2018, 99, 45–56. [Google Scholar] [CrossRef]
- Boakye-Boateng, K.; Ghorbani, A.A.; Lashkari, A.H. Implementation of a Trust-Based Framework for Substation Defense in the Smart Grid. Smart Cities 2024, 7, 99–140. [Google Scholar] [CrossRef]
- Zhao, P.; Cao, Z.; Zeng, D.D.; Gu, C.; Wang, Z.; Xiang, Y.; Qadrdan, M.; Chen, X.; Yan, X.; Li, S. Cyber-Resilient Multi-Energy Management for Complex Systems. IEEE Trans. Ind. Inform. 2022, 18, 2144–2159. [Google Scholar] [CrossRef]
- Zhao, P.; Li, S.; Hu, P.J.H.; Cao, Z.; Gu, C.; Xie, D.; Zeng, D.D. Coordinated Cyber Security Enhancement for Grid-Transportation Systems With Social Engagement. IEEE Trans. Emerg. Top. Comput. Intell. 2022, 1–15. [Google Scholar] [CrossRef]
- Alasali, F.; Itradat, A.; Abu Ghalyon, S.; Abudayyeh, M.; El-Naily, N.; Hayajneh, A.M.; AlMajali, A. Smart Grid Resilience for Grid-Connected PV and Protection Systems under Cyber Threats. Smart Cities 2024, 7, 51–77. [Google Scholar] [CrossRef]
- Bitirgen, K.; Filik, Ü.B. A hybrid deep learning model for discrimination of physical disturbance and cyber-attack detection in smart grid. Int. J. Crit. Infrastruct. Prot. 2023, 40, 100582. [Google Scholar] [CrossRef]
- Tian, J.; Wang, B.; Li, J.; Konstantinou, C. Datadriven false data injection attacks against cyber-physical power systems. Comput. Secur. 2022, 121, 102836. [Google Scholar] [CrossRef]
- Li, B.; Xiao, G.; Lu, R.; Deng, R.; Bao, H. On Feasibility and Limitations of Detecting False Data Injection Attacks on Power Grid State Estimation Using D-FACTS Devices. IEEE Trans. Ind. Inform. 2020, 16, 854–864. [Google Scholar] [CrossRef]
- Yao, H.; Xiang, Y.; Liu, J. Virtual Prosumers’ P2P Transaction Based Distribution Network Expansion Planning. IEEE Trans. Power Syst. 2023, 39, 1044–1057. [Google Scholar] [CrossRef]
- Vincent, E.; Korki, M.; Seyedmahmoudian, M.; Stojcevski, A.; Mekhilef, S. Detection of false data injection attacks in cyber–physical systems using graph convolutional network. Electr. Power Syst. Res. 2023, 217, 109118. [Google Scholar] [CrossRef]
- Yang, J.; Xiang, Y. Deep Transfer Learning based Surrogate Modeling for Optimal Investment Decision of Distribution Networks. IEEE Trans. Power Syst. 2023, 39, 2506–2516. [Google Scholar] [CrossRef]
- Xiang, Y.; Lu, Y.; Liu, J. Deep reinforcement learning based topology-aware voltage regulation of distribution networks with distributed energy storage. Appl. Energy 2023, 332, 120510. [Google Scholar] [CrossRef]
- Panagiotis, F.; Taxiarxchis, K.; Georgios, K.; Maglaras, L.; Ferrag, M.A. Intrusion Detection in Critical Infrastructures: A Literature Review. Smart Cities 2021, 4, 1146–1157. [Google Scholar] [CrossRef]
- Su, Q.; Wang, H.; Sun, C.; Li, B.; Li, J. Cyber-attacks against cyber-physical power systems security: State estimation, attacks reconstruction and defense strategy. Appl. Math. Comput. 2022, 413, 126639. [Google Scholar] [CrossRef]
- Aoufi, S.; Derhab, A.; Guerroumi, M. Survey of false data injection in smart power grid: Attacks, countermeasures and challenges. J. Inf. Secur. Appl. 2020, 54, 102518. [Google Scholar] [CrossRef]
- Gjesvik, L.; Szulecki, K. Interpreting cyber-energy-security events: Experts, social imaginaries, and policy discourses around the 2016 Ukraine blackout. Eur. Secur. 2022, 32, 104–124. [Google Scholar] [CrossRef]
- Pawlak, P. Protecting and defending Europe’s cyberspace. Hacks Leaks Disrupt. Russ. Cyber Strateg. ISS Chaillot Pap. 2018, 148, 103–115. [Google Scholar]
- Sun, Y.; Chai, J.; Li, W.; Ren, Y. Research on the Evaluation Index System and Methodology for the Construction of Ecological Civilization Model Cities—Yancheng City as an Example. Open J. Bus. Manag. 2022, 10, 1549–1568. [Google Scholar] [CrossRef]
- Wei, F.; Wan, Z.; He, H. Cyber-attack recovery strategy for smart grid based on deep reinforcement learning. IEEE Trans. Smart Grid 2019, 11, 2476–2486. [Google Scholar] [CrossRef]
- Mustafa, A.; Poudel, B.; Bidram, A.; Modares, H. Detection and Mitigation of Data Manipulation Attacks in AC Microgrids. IEEE Trans. Smart Grid 2020, 11, 2588–2603. [Google Scholar] [CrossRef]
- Kabir, M.E.; Ghafouri, M.; Moussa, B.; Assi, C. A Two-Stage Protection Method for Detection and Mitigation of Coordinated EVSE Switching Attacks. IEEE Trans. Smart Grid 2021, 12, 4377–4388. [Google Scholar] [CrossRef]
- Zhang, J.; Sahoo, S.; Peng, J.C.H.; Blaabjerg, F. Mitigating Concurrent False Data Injection Attacks in Cooperative DC Microgrids. IEEE Trans. Power Electron. 2021, 36, 9637–9647. [Google Scholar] [CrossRef]
- Lakshminarayana, S.; Karachiwala, J.S.; Teng, T.Z.; Tan, R.; Yau, D.K.Y. Performance and Resilience of Cyber-Physical Control Systems With Reactive Attack Mitigation. IEEE Trans. Smart Grid 2019, 10, 6640–6654. [Google Scholar] [CrossRef]
- Zhang, Z.; Huang, S.; Chen, Y.; Li, B.; Mei, S. Diversified Software Deployment for Long-Term Risk Mitigation in Cyber-Physical Power Systems. IEEE Trans. Power Syst. 2022, 37, 377–387. [Google Scholar] [CrossRef]
- Liu, C.; Zhou, M.; Wu, J.; Long, C.; Kundur, D. Financially Motivated FDI on SCED in Real-Time Electricity Markets: Attacks and Mitigation. IEEE Trans. Smart Grid 2019, 10, 1949–1959. [Google Scholar] [CrossRef]
- Mokarim, A.; Gaggero, G.B.; Marchese, M. Evaluation of the Impact of Cyber-Attacks Against Electric Vehicle Charging Stations in a Low Voltage Distribution Grid. In Proceedings of the 2023 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Glasgow, UK, 31 October–3 November 2023; pp. 1–7. [Google Scholar] [CrossRef]
- Marotta, A.; Martinelli, F.; Nanni, S.; Orlando, A.; Yautsiukhin, A. Cyber-insurance survey. Comput. Sci. Rev. 2017, 24, 35–61. [Google Scholar] [CrossRef]
- Fuhrman-Wenman, T. Cyber Insurance in International Mergers and Acquisitions. Denver Law Rev. Forum 2016, 93, 361–376. [Google Scholar]
- Mott, G.; Turner, S.; Nurse, J.R.C.; MacColl, J.; Sullivan, J.; Cartwright, A.; Cartwright, E. Between a rock and a hard(ening) place: Cyber insurance in the ransomware era. Comput. Secur. 2023, 128, 103162. [Google Scholar] [CrossRef]
- Liu, Z.; Wei, W.; Wang, L.; Ten, C.W.; Rho, Y. An Actuarial Framework for Power System Reliability Considering Cybersecurity Threats. IEEE Trans. Power Syst. 2021, 36, 851–864. [Google Scholar] [CrossRef]
- Niyato, D.; Hoang, D.T.; Wang, P.; Han, Z. Cyber Insurance for Plug-In Electric Vehicle Charging in Vehicle-to-Grid Systems. IEEE Netw. 2017, 31, 38–46. [Google Scholar] [CrossRef]
- Lau, P.; Wang, L.; Liu, Z.; Wei, W.; Ten, C.W. A Coalitional Cyber-Insurance Design Considering Power System Reliability and Cyber Vulnerability. IEEE Trans. Power Syst. 2021, 36, 5512–5524. [Google Scholar] [CrossRef]
- Acharya, S.; Mieth, R.; Konstantinou, C.; Karri, R.; Dvorkin, Y. Cyber Insurance Against Cyberattacks on Electric Vehicle Charging Stations. IEEE Trans. Smart Grid 2021, 13, 1529–1541. [Google Scholar] [CrossRef]
- Mazzoccoli, A.; Naldi, M. Robustness of Optimal Investment Decisions in Mixed Insurance/Investment Cyber Risk Management. Risk Anal. 2020, 40, 550–564. [Google Scholar] [CrossRef]
- Pal, R.; Golubchik, L.; Psounis, K.; Hui, P. Will cyber-insurance improve network security? A market analysis. In Proceedings of the IEEE INFOCOM 2014-IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 235–243. [Google Scholar] [CrossRef]
- Wang, S.S. Integrated framework for information security investment and cyber insurance. Pac. Basin Financ. J. 2019, 57, 101173. [Google Scholar] [CrossRef]
- Martinelli, F.; Orlando, A.; Uuganbayar, G.; Yautsiukhin, A. Preventing the Drop in Security Investments for Non-competitive Cyber-Insurance Market. In Risks and Security of Internet and Systems; Cuppens, N., Cuppens, F., Lanet, J.L., Legay, A., Garcia-Alfaro, J., Eds.; Springer: Cham, Switzerland, 2018; pp. 159–174. [Google Scholar]
- Pal, R.; Golubchik, L. Analyzing Self-Defense Investments in Internet Security under Cyber-Insurance Coverage. In Proceedings of the 2010 IEEE 30th International Conference on Distributed Computing Systems, Genoa, Italy, 21–25 June 2010; pp. 339–347. [Google Scholar] [CrossRef]
- Lu, X.; Chan, K.W.; Xia, S.; Shahidehpour, M.; Ng, W.H. An Operation Model for Distribution Companies Using the Flexibility of Electric Vehicle Aggregators. IEEE Trans. Smart Grid 2021, 12, 1507–1518. [Google Scholar] [CrossRef]
- Zare, A.; Chung, C.Y.; Zhan, J.; Faried, S.O. A Distributionally Robust Chance-Constrained MILP Model for Multistage Distribution System Planning With Uncertain Renewables and Loads. IEEE Trans. Power Syst. 2018, 33, 5248–5262. [Google Scholar] [CrossRef]
- Ning, X.; Jiang, J. Design, Analysis and Implementation of a Security Assessment/Enhancement Platform for Cyber-Physical Systems. IEEE Trans. Ind. Inform. 2022, 18, 1154–1164. [Google Scholar] [CrossRef]
- Yang, J.; Zhou, C.; Yang, S.; Xu, H.; Hu, B. Anomaly Detection Based on Zone Partition for Security Protection of Industrial Cyber-Physical Systems. IEEE Trans. Ind. Electron. 2018, 65, 4257–4267. [Google Scholar] [CrossRef]
- Tsohou, A.; Diamantopoulou, V.; Gritzalis, S.; Lambrinoudakis, C. Cyber insurance: State of the art, trends and future directions. Int. J. Inf. Secur. 2023, 22, 737–748. [Google Scholar] [CrossRef]
- Xie, H.; Sun, X.; Fu, W.; Chen, C.; Bie, Z. Risk management for integrated power and natural gas systems against extreme weather: A coalitional insurance contract approach. Energy 2023, 263, 125750. [Google Scholar] [CrossRef]
- Lu, K.D.; Zeng, G.Q.; Luo, X.; Weng, J.; Luo, W.; Wu, Y. Evolutionary Deep Belief Network for Cyber-Attack Detection in Industrial Automation and Control System. IEEE Trans. Ind. Inform. 2021, 17, 7618–7627. [Google Scholar] [CrossRef]
- Jiang, W.; Song, Z.; Zhan, J.; Liu, D.; Wan, J. Layerwise Security Protection for Deep Neural Networks in Industrial Cyber Physical Systems. IEEE Trans. Ind. Inform. 2022, 18, 8797–8806. [Google Scholar] [CrossRef]
- Jorjani, M.; Seifi, H.; Varjani, A.Y. A Graph Theory-Based Approach to Detect False Data Injection Attacks in Power System AC State Estimation. IEEE Trans. Ind. Inform. 2021, 17, 2465–2475. [Google Scholar] [CrossRef]
- Wang, G.; Yin, S.; Kaynak, O. An LWPR-Based Data-Driven Fault Detection Approach for Nonlinear Process Monitoring. IEEE Trans. Ind. Inform. 2014, 10, 2016–2023. [Google Scholar] [CrossRef]
- Zhang, Q.; Ma, Z.; Zhu, Y.; Wang, Z. A Two-Level Simulation-Assisted Sequential Distribution System Restoration Model With Frequency Dynamics Constraints. IEEE Trans. Smart Grid 2021, 12, 3835–3846. [Google Scholar] [CrossRef]
- García-Marín, S.; González-Vanegas, W.; Murillo-Sánchez, C. MPNG: A MATPOWER-Based Tool for Optimal Power and Natural Gas Flow Analyses. IEEE Trans. Power Syst. 2022, 39, 5455–5464. [Google Scholar] [CrossRef]
- Golodnikov, A.; Kuzmenko, V.; Uryasev, S. CVaR regression based on the relation between CVaR and mixed-quantile quadrangles. J. Risk Financ. Manag. 2019, 12, 107. [Google Scholar] [CrossRef]
- Lan, G. Correction to: Complexity of stochastic dual dynamic programming. Math. Program. 2022, 194, 1187–1189. [Google Scholar] [CrossRef]
- Bonfiglio, A.; Bruno, S.; Martino, M.; Minetti, M.; Procopio, R.; Velini, A. Renewable Energy Communities Virtual Islanding: A Novel Service for Smart Distribution Networks. In Proceedings of the 2024 IEEE/IAS 60th Industrial and Commercial Power Systems Technical Conference (I&CPS), Las Vegas, NV, USA, 19–23 May 2024; pp. 1–8. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).